Ever wondered what actually happens behind the screen when someone joins a Bitcoin MLM network, makes a purchase, or receives a commission? The answer involves a fascinating blend of blockchain technology, distributed databases, smart automation, and security protocols all working together in real time.
This is not your typical overview article. We are going to open up the hood and look at every component that makes Bitcoin MLM software tick. From the code running on servers to the blockchain transactions settling on the network, you will understand exactly how these platforms operate at a technical level.
At Nadcab Labs, we have been building cryptocurrency solutions for over 8 years. In that time, we have seen MLM platforms succeed spectacularly and fail miserably. The difference almost always comes down to the technology choices made during development. This guide shares what we have learned so you can make informed decisions whether you are building, buying, or evaluating Bitcoin MLM software.
Key Takeaways
- Bitcoin MLM platforms use a layered architecture where frontend, backend, database, and blockchain components each handle specific tasks while communicating through secure APIs.
- Smart contracts eliminate manual commission processing by automatically calculating and distributing payments when predefined conditions are met.
- Security is not a single feature but a framework spanning network protection, encryption, authentication, and wallet management with hot and cold storage separation.
- Scalability must be designed from day one because successful MLM networks can grow from hundreds to hundreds of thousands of users within months.
- Modern deployment uses cloud infrastructure with CI/CD pipelines enabling rapid updates and consistent uptime across global user bases.
- Compliance features including KYC, AML monitoring, and detailed audit logs are legal necessities that protect both platform operators and participants.
Introduction to Bitcoin MLM Software from a Tech Perspective
Think of traditional MLM software as a well-organized office building. Now imagine that building needs to connect directly to a global financial network that operates 24 hours a day, processes irreversible transactions, and has no customer service department. That is the challenge Bitcoin MLM software developers face.
The Bitcoin network does not care about your business hours or your compensation plan. It processes blocks roughly every 10 minutes, charges variable fees based on network congestion, and requires multiple confirmations before transactions should be considered final. Your software must adapt to these realities rather than fight against them.
What makes this particularly interesting from an engineering standpoint is the need to bridge two very different worlds. On one side, you have users who expect instant feedback, clear dashboards, and mobile-friendly interfaces. On the other side, you have a decentralized blockchain that operates on its own timeline. The technology stack must reconcile these expectations while maintaining accuracy and security.
For a foundational understanding of these systems, our detailed breakdown of how crypto MLM systems work covers the business logic side of the equation.
Core Architecture of Bitcoin MLM Systems
Good architecture is like a well-designed city. Each district has its purpose, roads connect them efficiently, and the whole system can grow without tearing everything down and starting over. Bitcoin MLM platforms follow this principle through layered design.
The separation of concerns is not just academic theory. When your commission calculation service needs an upgrade, you should be able to deploy it without touching the user interface. When blockchain APIs change, your database schema should remain unaffected. This modularity saves countless hours during maintenance and reduces the risk of updates breaking unrelated features.
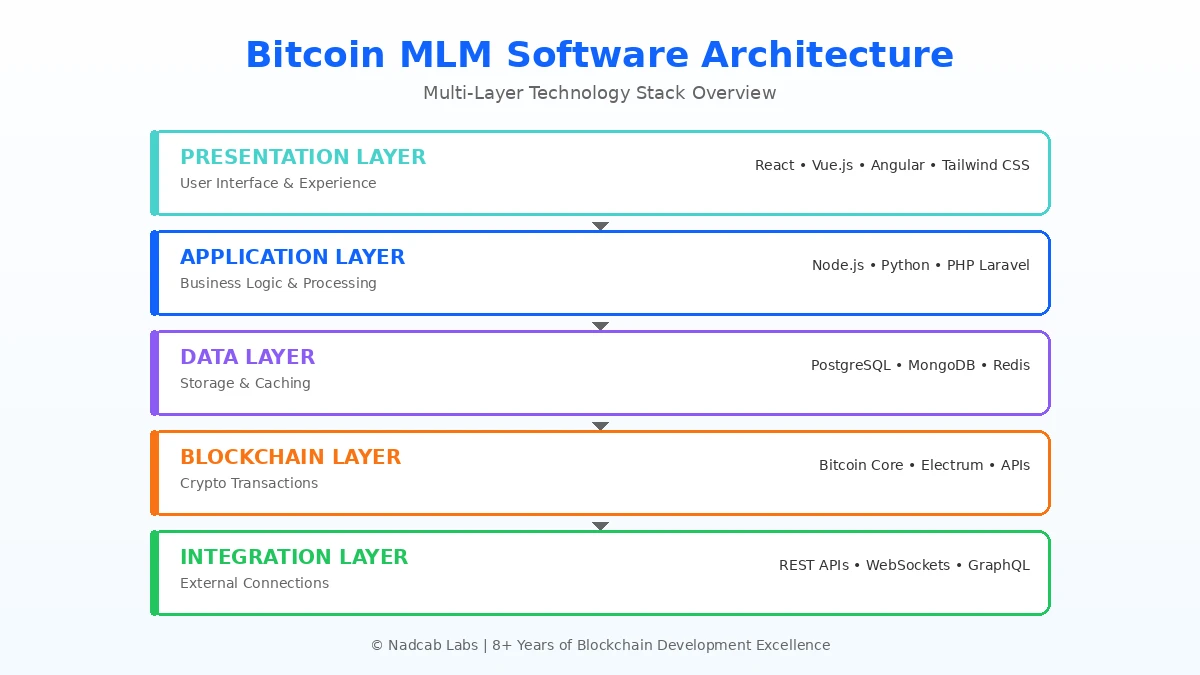
| Architecture Layer | What It Does | Common Technologies |
|---|---|---|
| Presentation Layer | Handles everything users see and click | React, Vue.js, Angular, Tailwind CSS |
| Application Layer | Runs business logic and processes requests | Node.js, Python Django, PHP Laravel |
| Data Layer | Stores and retrieves all platform information | PostgreSQL, MongoDB, Redis |
| Blockchain Layer | Manages crypto transactions and verification | Bitcoin Core, Electrum Server, BlockCypher |
| Integration Layer | Connects external services and APIs | REST APIs, WebSockets, GraphQL |
Each layer talks only to its neighbors through defined interfaces. The presentation layer never queries the database directly. The blockchain layer does not know anything about user interface design. This separation creates natural boundaries that make the system easier to test, debug, and scale.
Frontend Technologies Used in Bitcoin MLM Platforms
Your users do not care about your brilliant backend architecture. They care about whether they can check their commissions on their phone while waiting in line at the grocery store. The frontend is where all your technical sophistication either shines or falls flat.
React dominates the MLM platform space for good reasons. Its component model maps naturally to MLM interfaces. You build a commission card component once, then reuse it throughout the dashboard. The virtual DOM ensures smooth updates when real-time data flows in. And the ecosystem offers solutions for nearly every UI challenge you might encounter.
But choosing React is just the beginning. The real work involves designing information architecture that makes sense to users at different experience levels. A new member needs guidance and education. A seasoned network builder wants dense data and quick access to recruitment tools. The interface must serve both without becoming cluttered or confusing.
Real-world example: One platform we developed at Nadcab Labs reduced support tickets by 40% simply by redesigning the withdrawal flow. Users could see their pending, confirmed, and completed transactions in a visual timeline rather than a static table. Small interface improvements create massive operational savings.
Mobile responsiveness is non-negotiable. Our analytics across multiple platforms show 65-75% of user sessions happening on smartphones. If your genealogy tree is illegible on a 6-inch screen or your withdrawal button requires zooming, you will frustrate the majority of your users.
Backend Infrastructure and Server Architecture
The backend is where requests go to be processed, validated, transformed, and returned. It is also where most performance problems originate if not designed carefully. A Bitcoin MLM backend must handle everything from simple profile updates to complex multi-level commission calculations while interacting with external blockchain networks.
Microservices architecture has become the standard approach for platforms expecting significant growth. Instead of one massive application handling everything, you deploy separate services for authentication, user management, commission processing, wallet operations, notifications, and reporting. Each service can be developed, deployed, and scaled independently.
Here is why this matters: During a promotional campaign, your registration service might see 10x normal traffic while commission calculations remain steady. With microservices, you scale only the registration service. With a monolithic application, you scale everything or nothing.
Message queues sit at the heart of reliable backend operations. When a user clicks “withdraw,” the system does not process the Bitcoin transaction synchronously and make them stare at a loading spinner. Instead, it validates the request, places it in a queue, confirms receipt to the user, and processes the actual blockchain transaction asynchronously. This pattern prevents timeouts and provides better user experience during peak loads.
Node.js excels for these workloads because of its non-blocking I/O model. While waiting for a database query or blockchain API response, the server handles other requests. Python with async frameworks like FastAPI offers similar benefits with arguably cleaner syntax for complex calculations.
Database Design and Data Storage Layers
Data is the lifeblood of any MLM platform. User records, transaction histories, network relationships, commission calculations, audit trails. Lose any of it, and you face both operational chaos and potential legal liability. The database layer deserves serious attention.
Most Bitcoin MLM platforms use a polyglot persistence approach. This fancy term simply means using different database types for different data characteristics. Financial transactions belong in a relational database with ACID guarantees. User preferences and configuration data fit naturally in document stores. Session information and caching benefit from key-value stores.
| Database Type | Ideal Use Cases | Popular Options |
|---|---|---|
| Relational (SQL) | Financial records, user accounts, transactions requiring consistency | PostgreSQL, MySQL, MariaDB |
| Document Store | User profiles, configurations, activity logs, flexible schemas | MongoDB, CouchDB, Firebase |
| Key-Value Cache | Sessions, rate limiting, real-time leaderboards, temporary data | Redis, Memcached, DynamoDB |
| Graph Database | Network hierarchies, referral chains, relationship traversal | Neo4j, Amazon Neptune, ArangoDB |
The genealogy structure presents unique database challenges. MLM networks are essentially giant trees or directed graphs where each node connects to a sponsor and potentially thousands of downline members. Querying “show me all members 7 levels deep under user X” can bring traditional databases to their knees if not optimized properly.
Graph databases like Neo4j handle these queries elegantly because they store relationships as first-class citizens rather than foreign keys requiring expensive joins. A query that takes 30 seconds in PostgreSQL might complete in milliseconds in Neo4j. For platforms expecting large networks, this performance difference becomes critical.
Understanding ROI and profitability in crypto MLM systems requires robust data infrastructure capable of producing accurate real-time calculations.
Build Your Bitcoin MLM Platform Right
Get expert guidance on architecture decisions that will scale with your success. Our team has built platforms serving millions of transactions.
Blockchain Integration and Bitcoin Network Connectivity
Here is where Bitcoin MLM software fundamentally differs from traditional platforms. You are not just tracking numbers in a database. You are interacting with a global, decentralized network that processes real value transfers. Getting this integration right is essential.
The first decision involves how to connect to the Bitcoin network. Running your own full node provides maximum independence and privacy. You validate transactions yourself without trusting third-party APIs. The tradeoff is resource requirements. A Bitcoin full node needs several hundred gigabytes of storage, decent bandwidth, and continuous uptime. For smaller platforms, managed API services like BlockCypher or Blockchain.com offer reliable alternatives.
Transaction lifecycle in practice:
1. User requests withdrawal → System validates balance and creates transaction
2. Transaction broadcasts → Sent to Bitcoin network, enters mempool
3. Confirmation monitoring → System watches for block inclusion
4. Threshold reached → After 3-6 confirmations, marked as complete
5. User notification → Email or push notification confirms completion
Fee estimation deserves special attention. Bitcoin transaction fees fluctuate based on network demand. During busy periods, fees can spike dramatically. Your system needs to monitor mempool conditions and calculate appropriate fees for different priority levels. Paying too little means stuck transactions and frustrated users. Paying too much wastes platform resources.
Deposit detection runs continuously through background processes. When users send Bitcoin to their assigned deposit addresses, the system must detect these transactions, wait for sufficient confirmations, and credit accounts accurately. This monitoring operates 24/7 without human intervention.
Crypto Wallet Integration and Payment Gateways
Wallets in a Bitcoin MLM context are not the smartphone apps you might be familiar with. Platform wallets are infrastructure components that manage cryptographic keys, generate addresses, sign transactions, and maintain security across potentially millions of dollars in user funds.
The hot and cold wallet separation is standard practice for any serious platform. Hot wallets stay connected to the internet and handle daily operational needs. They hold enough Bitcoin to cover expected withdrawals for a reasonable period. Cold wallets store the bulk of funds completely offline, often in hardware security modules or air-gapped computers. Moving funds from cold to hot storage requires multiple approvals and manual processes.
Why this matters: If hackers compromise your hot wallet, they get whatever is in there. If 90% of funds are in cold storage, you have lost 10% instead of everything. Painful, but survivable.
Hierarchical Deterministic (HD) wallets following BIP32 and BIP44 standards enable generating unlimited unique addresses from a single master seed. Each user gets their own deposit address, making it trivial to track incoming payments and credit the correct accounts automatically. The alternative of manually managing individual keys becomes impractical at scale.
Payment gateway integration extends capabilities beyond Bitcoin. Services enable accepting Ethereum, stablecoins, and other cryptocurrencies while maintaining a unified internal accounting system. The platform converts everything to a common denomination for commission calculations regardless of which currency users deposit or withdraw.
Smart Contract Layer and Automation Stack
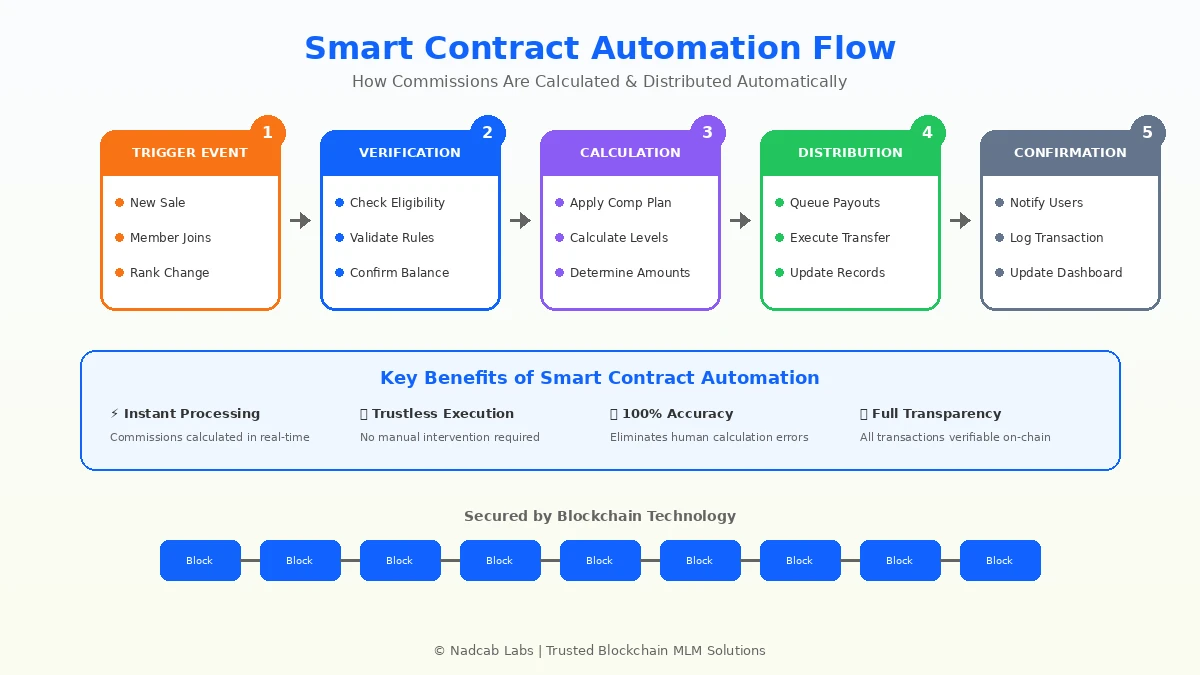
Automation transforms MLM operations from labor-intensive manual processes to efficient, trustless systems. While Bitcoin’s scripting language is limited compared to Ethereum, modern platforms achieve sophisticated automation through various approaches.
Understanding the role of smart contracts in decentralized MLM reveals how this automation builds trust. When commission rules are encoded in verifiable contracts rather than hidden in company databases, participants can independently verify that payouts match the published compensation plan.
The automation stack typically operates on multiple time horizons. Real-time automation responds instantly to events. When a new member joins, the system immediately updates the sponsor’s network count and recalculates any volume-based qualifications. When a purchase completes, referral commissions calculate and queue for distribution within seconds.
Scheduled automation handles periodic processing. Daily jobs aggregate transactions and calculate commissions. Weekly jobs evaluate rank qualifications and process promotions. Monthly jobs generate statements and compile analytics reports. These scheduled tasks run during low-traffic hours to minimize system load impact.
For teams building custom automation, our technical guide on developing MLM smart contracts provides implementation details and code patterns.
The comprehensive smart contract architecture guide for crypto MLM covers design patterns that have proven reliable across multiple production deployments.
Security Infrastructure and Encryption Framework
Security in Bitcoin MLM software is not a feature you add at the end. It is a mindset that influences every design decision from the first line of code. These platforms hold real money. They are targets. Period.
Defense in depth means attackers must breach multiple independent layers to cause significant damage. Compromising the web application should not grant database access. Accessing the database should not reveal encrypted private keys. Stealing hot wallet funds should not touch cold storage. Each layer operates independently.
| Security Layer | Protection Measures | Threats Addressed |
|---|---|---|
| Network Perimeter | WAF, DDoS mitigation, intrusion detection, VPN for admin | Volumetric attacks, scanning, unauthorized access |
| Application | Input validation, parameterized queries, CSRF protection, rate limiting | SQL injection, XSS, CSRF, API abuse |
| Data | AES-256 encryption at rest, TLS 1.3 in transit, field-level encryption | Data breaches, man-in-the-middle attacks |
| Authentication | Multi-factor authentication, device fingerprinting, session management | Credential stuffing, account takeover, session hijacking |
| Wallet Security | Multi-signature requirements, cold storage, withdrawal delays, limits | Internal theft, compromised keys, large-scale fund extraction |
Two-factor authentication (2FA) stops most account takeover attempts in their tracks. Even when passwords leak through phishing or data breaches elsewhere, attackers cannot access accounts without the second factor. Time-based one-time passwords (TOTP) through authenticator apps provide better security than SMS codes.
Regular penetration testing identifies vulnerabilities before malicious actors find them. Professional security firms attempt to breach your system using the same techniques real attackers employ. Their findings guide remediation priorities and validate that your security measures actually work. At Nadcab Labs, we conduct quarterly security audits on every platform we maintain.
Encryption protects data even when other defenses fail. AES-256 encryption for sensitive database fields means that even if attackers download your entire database, they see meaningless ciphertext. Private keys never exist in plaintext on any server. Hardware Security Modules (HSMs) provide tamper-resistant key storage for the most critical operations.
Scalability and Performance Optimization Techniques
Success kills unprepared platforms. An MLM network that goes viral can grow from 1,000 to 100,000 users in weeks. If your infrastructure cannot scale proportionally, users experience slowdowns, timeouts, and errors at exactly the moment your reputation matters most.
Horizontal scaling adds more servers to handle increased load rather than upgrading to more powerful machines. This approach has no theoretical ceiling and provides redundancy. If one server fails, others continue serving requests while the problematic instance recovers. Auto-scaling groups automatically add or remove servers based on real-time demand metrics.
Caching strategy example: User profile data changes rarely but gets requested constantly. Storing profiles in Redis means 99% of profile requests never touch the database. Cache invalidation triggers only when profiles actually update. This simple pattern can reduce database load by orders of magnitude.
Database optimization becomes critical at scale. Indexes speed up common queries dramatically but slow down writes and consume storage. Query optimization identifies slow-running operations for improvement. Read replicas handle analytics and reporting queries, keeping the primary database focused on transactional workloads. Partitioning strategies distribute data across multiple database servers.
Content delivery networks (CDNs) cache static assets at edge locations worldwide. Instead of every user downloading JavaScript files from your origin server, they fetch cached copies from nearby CDN nodes. This reduces latency, saves bandwidth, and improves page load times globally. Services like Cloudflare or AWS CloudFront make CDN deployment straightforward.
For a comprehensive market perspective, our analysis of cryptocurrency MLM software market trends and forecast helps contextualize infrastructure investments against industry growth projections.
API Layer and Third-Party Integrations
APIs are the universal translators that let different systems communicate. A well-designed API layer makes your platform extensible, enables mobile app development, supports partner integrations, and powers automated workflows that would otherwise require manual intervention.
REST APIs remain the workhorse for most integrations. Their simplicity and wide tooling support make them accessible to developers of varying skill levels. Each endpoint handles a specific operation. GET /users/{id} retrieves user data. POST /withdrawals initiates a new withdrawal. Consistent conventions make the API predictable and self-documenting.
GraphQL offers advantages for complex data requirements. Instead of multiple REST calls to assemble information from different resources, clients specify exactly what they need in a single request. This approach reduces network round trips and gives frontend developers flexibility without requiring backend changes for new data combinations.
Third-party integrations extend platform capabilities significantly. KYC verification services like Jumio or Onfido automate identity verification. Email providers like SendGrid or Mailgun handle transactional messaging at scale. Analytics platforms like Mixpanel or Amplitude track user behavior. Payment processors support fiat currency on-ramps. Each integration requires careful security evaluation and proper credential management.
API versioning protects existing integrations when you need to make breaking changes. Maintaining v1 endpoints while introducing v2 allows partners to migrate on their own timeline rather than forcing simultaneous updates across all consumers.
Cloud Hosting, DevOps, and Deployment Pipelines
Gone are the days of maintaining physical servers in data centers. Modern Bitcoin MLM platforms run on cloud infrastructure from AWS, Google Cloud, or Azure. Cloud hosting provides flexibility, global reach, managed services, and the ability to scale resources on demand.
Infrastructure as Code (IaC) defines server configurations in version-controlled files rather than manual setup procedures. Terraform scripts can recreate your entire infrastructure from scratch in minutes. This reproducibility eliminates configuration drift, enables rapid disaster recovery, and makes spinning up test environments trivial.
Deployment pipeline in action:
1. Developer pushes code → Changes go to version control (Git)
2. Automated tests run → Unit tests, integration tests, security scans
3. Build artifacts created → Docker images built and pushed to registry
4. Staging deployment → New version deployed to staging environment
5. Production release → After approval, rolling deployment to production
Kubernetes orchestrates container deployments at scale. It handles scheduling workloads across server clusters, automatically restarts failed containers, manages rolling updates without downtime, and scales services based on demand. The learning curve is steep, but the operational benefits justify the investment for platforms expecting significant traffic.
Monitoring and alerting close the feedback loop. Systems like Datadog, Prometheus, or CloudWatch collect metrics from every component. Dashboards show real-time system health. Alerts notify teams immediately when metrics exceed thresholds, enabling rapid response before users notice problems.
Real-Time Analytics, Reporting, and Monitoring Systems
Data transforms guesswork into informed decision-making. Real-time analytics help administrators identify trends, spot anomalies, and optimize strategies. Users expect to see their performance metrics immediately, not in end-of-day reports. Building this visibility requires thoughtful data infrastructure.
Application Performance Monitoring (APM) tracks response times, error rates, and resource utilization across all services. When a page suddenly takes 5 seconds to load instead of 500 milliseconds, you need to know immediately. Distributed tracing follows requests across microservices, pinpointing exactly where bottlenecks occur.
Business intelligence dashboards serve different stakeholders with relevant metrics. Administrators see network growth curves, transaction volumes, and commission distributions. Individual users view their personal statistics, team performance, and progress toward rank advancement. Executives monitor revenue trends, operational costs, and profitability metrics.
Log aggregation centralizes records from all system components. When investigating issues, teams search through unified logs rather than connecting to individual servers. Patterns in log data reveal bugs, security incidents, and optimization opportunities that would otherwise go unnoticed. Tools like ELK Stack (Elasticsearch, Logstash, Kibana) or Datadog Logs make this aggregation manageable.
Before selecting development partners, reviewing questions to ask MLM software developers helps ensure analytics capabilities meet your business intelligence needs.
Role of AI and Automation in Bitcoin MLM Infrastructure

Artificial intelligence is moving beyond buzzword status into practical applications within MLM platforms. Machine learning models analyze patterns, make predictions, and automate decisions that previously required human judgment or were simply impossible at scale.
Fraud detection represents the most mature AI application in this space. Models trained on historical data recognize suspicious patterns. Fake accounts created in bursts from similar IP addresses. Commission gaming through circular transactions. Withdrawal attempts from compromised accounts. When detected, the system automatically freezes suspicious activity for human review.
Practical AI applications in MLM platforms:
- Churn prediction identifying at-risk members before they leave
- Personalized recommendations for training content based on performance patterns
- Anomaly detection in transaction patterns suggesting fraud or system issues
- Chatbots handling routine support queries 24/7
- Sentiment analysis of community communications identifying emerging concerns
Predictive analytics forecast network growth, revenue projections, and resource requirements. Platform operators use these insights for capacity planning, marketing budget allocation, and proactive intervention with struggling network segments. Accurate predictions translate directly into better business outcomes and optimized spending.
Natural language processing powers intelligent support systems. Chatbots handle common questions about commissions, withdrawals, and account settings around the clock. Complex issues escalate seamlessly to human agents with full context. This automation reduces support costs while improving response times.
Compliance, Audit Logs, and Infrastructure Governance
Regulations vary by jurisdiction but ignoring them is not an option. Bitcoin MLM platforms must implement controls satisfying legal requirements while maintaining detailed records for potential audits. Proper governance protects platform operators, participants, and the long-term viability of the business.
Know Your Customer (KYC) verification confirms user identities before allowing significant transactions. Integration with services like Jumio, Onfido, or Shufti Pro automates document verification and facial recognition matching. Different verification tiers unlock corresponding transaction limits. Basic email verification for browsing. ID verification for deposits. Enhanced due diligence for large withdrawals.
Anti-Money Laundering (AML) monitoring flags transactions matching suspicious patterns defined by financial regulators. Large deposits, rapid fund movements, structuring to avoid reporting thresholds, and transactions with sanctioned addresses all trigger reviews. According to Investopedia’s AML overview, these controls are mandatory for any platform handling financial transactions.
Comprehensive audit logs record every significant system action. User logins with IP addresses and device fingerprints. Balance changes with before and after values. Commission calculations with full input parameters. Administrative actions with operator identification. These records support forensic investigations, regulatory audits, dispute resolution, and continuous improvement initiatives.
For those exploring token-based approaches, our guide on how to launch MLM with your own token addresses additional compliance considerations for tokenized platforms.
Future Technology Trends in Bitcoin MLM Software
Technology never stands still. The platforms that thrive long-term anticipate changes and adapt proactively rather than scrambling to catch up. Several emerging trends will reshape Bitcoin MLM software over the coming years.
| Technology Trend | Current Status | Expected Impact |
|---|---|---|
| Lightning Network | Growing adoption, improving tooling | Instant micropayments, sub-cent transaction fees |
| Decentralized Identity (DID) | Standards maturing, early implementations | User-controlled KYC, portable credentials |
| Cross-Chain Interoperability | Bridges operational, security improving | Seamless multi-blockchain token support |
| AI-Driven Personalization | Basic implementations available | Individualized user experiences at scale |
| Zero-Knowledge Proofs | Research advancing, pilots underway | Privacy-preserving compliance verification |
The Lightning Network addresses Bitcoin’s scalability limitations for everyday transactions. This second-layer protocol enables payments in seconds with fees measured in satoshis rather than dollars. For MLM platforms, Lightning opens possibilities for instant commission distribution and micro-payments that would be impractical on the main chain.
Decentralized identity standards will transform KYC processes. Instead of platforms storing copies of passports and utility bills, users will control cryptographic credentials verified by trusted issuers. Prove you are over 18 without revealing your birthdate. Prove your address without exposing the document. Privacy improves while compliance requirements are still met.
Zero-knowledge proofs enable verification without revelation. Prove you have sufficient balance without disclosing the exact amount. Prove you completed KYC without sharing personal documents. This technology promises to reconcile privacy with transparency in ways previously impossible.
Developers choosing implementation technologies should review our comparison of programming languages for decentralized MLM to future-proof their choices.
Conclusion: Building a Reliable Bitcoin MLM Tech Stack
Building Bitcoin MLM software is genuinely difficult. It requires expertise across blockchain development, distributed systems, security engineering, user experience design, and regulatory compliance. Each layer presents unique challenges. The interactions between layers present even more.
The platforms that succeed long-term share common characteristics. They were built on solid architectural foundations allowing graceful scaling. They protected user funds through layered security rather than hoping for the best. They anticipated regulatory requirements rather than scrambling to retrofit compliance. They invested in real-time visibility enabling data-driven decisions.
Nadcab Labs brings over 8 years of specialized experience to cryptocurrency MLM software development. We have navigated the challenges described throughout this article repeatedly, learning what works and what fails in production environments serving thousands of users. Our team understands that technology decisions made during initial development echo throughout the platform’s entire lifetime.
The question is not whether to invest in quality infrastructure but whether you can afford not to. Cutting corners on security leads to breaches. Ignoring scalability leads to outages during growth spurts. Skipping compliance leads to legal problems. The platforms that flourish are those built right from the beginning.
Whether you are starting from scratch, modernizing an existing platform, or evaluating solutions from different vendors, the technology choices you make today determine your competitive position for years to come. Choose partners who understand both the technical complexities and business realities of Bitcoin MLM software development.
Frequently Asked Questions
The most effective technology stack combines JavaScript frameworks like React or Vue.js for building responsive frontend interfaces with Node.js or Python handling backend processing. PostgreSQL manages transactional data requiring strict consistency while MongoDB stores flexible configuration and user preferences. Redis provides lightning-fast caching and session management. For blockchain connectivity, platforms typically integrate Bitcoin Core nodes directly or use established API services like BlockCypher for transaction processing and wallet operations.
Smart contracts execute predefined commission rules automatically when specific triggering conditions occur within the system. When a new sale completes or a member joins the network, the contract immediately calculates payouts based on the compensation plan structure, verifies that recipients meet all eligibility requirements, and initiates transfers to qualifying upline members. This automation completely eliminates manual processing delays and human errors while ensuring consistent, verifiable application of commission rules across every single transaction processed by the platform.
Comprehensive security requires implementing multiple independent protective layers working together. Network security deploys web application firewalls and DDoS mitigation services. Application security enforces strict input validation, parameterized database queries, and rate limiting. Data protection uses AES-256 encryption for sensitive fields and TLS 1.3 for all communications. User authentication requires multi-factor verification through authenticator apps. Wallet security separates hot and cold storage with multi-signature requirements for large withdrawals. Regular penetration testing by professional security firms validates all measures function correctly.
Development timelines vary significantly based on complexity and customization requirements for each project. Basic platforms implementing standard features and common compensation plans typically require 3 to 4 months of focused development work. Platforms incorporating custom compensation structures, advanced analytics dashboards, and extensive third-party integrations generally take 6 to 8 months. Enterprise-grade solutions supporting multiple blockchain networks, sophisticated automation workflows, and comprehensive compliance systems often extend to 9 to 12 months for complete development, testing, and security auditing cycles.
Essential compliance requirements include KYC verification systems for confirming user identity through document checks and facial recognition, AML monitoring capabilities for detecting suspicious transaction patterns and potential money laundering activities, and comprehensive audit logging capturing every significant system action for regulatory reporting. Different jurisdictions impose varying documentation thresholds and specific requirements. Platforms must implement flexible compliance modules adaptable to regional regulations including data protection laws like GDPR in Europe and specific cryptocurrency licensing requirements in countries like the United States and Singapore.
Existing MLM platforms can integrate cryptocurrency payment support through carefully planned modular upgrades to their infrastructure. The process involves adding blockchain connectivity layers, implementing secure wallet management systems, updating payment processing workflows to handle crypto transactions, and modifying user interfaces to display cryptocurrency balances and transaction histories. However, fundamental architecture limitations in older systems may require significant refactoring or partial rebuilding. A professional technical assessment determines whether upgrading the existing platform or building fresh provides better long-term value and return on investment.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







