Key Takeaways
- Blockchain security combines cryptographic hashing, distributed consensus, and encryption to create tamper-resistant networks protecting trillions in digital assets.
- No major blockchain has ever been successfully hacked at the protocol level, though exchanges and wallets remain vulnerable attack targets.
- Cryptographic hash functions transform any input into a fixed-length output, making data verification instant while alteration detection automatic.
- 51 percent attacks require controlling the majority of network computing power, costing millions of dollars against established blockchains like Bitcoin and Ethereum.
- Private keys provide sole ownership proof through asymmetric encryption, meaning whoever controls the keys controls the assets.
- Smart contract vulnerabilities have caused billions in losses, demonstrating that code security matters as much as protocol security.
- Blockchain immutability ensures that once data is confirmed, altering it requires recalculating every subsequent block faster than the entire network.
- Defense in depth strategies combining hardware security, multi signature wallets, and regular audits provide the strongest protection.
Since Bitcoin launched in 2009, major blockchain networks have processed over one billion transactions worth trillions of dollars without a single successful hack of the underlying protocol. This remarkable security record stems from the fundamental architecture combining blockchain cryptography, distributed consensus, and economic incentives that make attacks prohibitively expensive. While cryptocurrency exchanges and individual wallets have suffered breaches, the core blockchain technology itself has proven extraordinarily resilient against the constant attacks it faces daily.
Understanding blockchain security reveals why this technology has earned trust for securing everything from digital currencies to supply chains, medical records, and government systems. The security model differs fundamentally from traditional databases that rely on perimeter defenses and access controls. Instead, blockchains assume the network will face constant attacks and design security into every layer of the architecture. This guide explains how blockchain security works through cryptography, hashing, and protection mechanisms, examines whether blockchain can be hacked, identifies the real vulnerabilities that attackers exploit, and provides practical strategies for securing blockchain assets and applications.
What is Blockchain Security?
Definition
Blockchain security refers to the comprehensive risk management systems, cryptographic protocols, and architectural designs that protect blockchain networks from unauthorized access, data manipulation, and cyberattacks. This includes the inherent security features built into blockchain architecture, such as cryptographic hash functions, asymmetric encryption, and distributed consensus, combined with external security practices like secure key management, smart contract auditing, and network monitoring.
The security of blockchain emerges from multiple reinforcing layers rather than any single protection mechanism. At the foundation lies cryptography that ensures data integrity and ownership verification. Above this sits the distributed architecture that eliminates single points of failure. The consensus mechanism adds economic security by requiring attackers to expend massive resources. Finally, the immutable ledger structure makes historical tampering detectable and impractical.
Unlike traditional centralized systems, where security depends on keeping attackers out, blockchain cybersecurity assumes attackers will participate in the network and designs the system so that malicious behavior becomes economically irrational. This fundamental shift in security philosophy explains why blockchains can operate as open, permissionless networks while maintaining integrity that closed systems struggle to achieve.
Core Security Pillars of Blockchain Technology
The blockchain in the cybersecurity context relies on four fundamental pillars that work together to create a secure, trustless system. Understanding these pillars reveals why blockchain security differs so dramatically from traditional database protection.
The Security Framework of Blockchain Technology
Cryptographic Hashing
Encryption Applied
Broadcast to Network
Consensus Validates
Added to Chain
1. Cryptographic Hash Functions
The blockchain hash function serves as the digital fingerprint for all data on the network. Hash functions take any input, whether a single character or an entire database, and produce a fixed-length output called a hash or digest. Bitcoin uses SHA256, which produces a 256-bit (64 hexadecimal characters) output regardless of input size.
Blockchain hashing provides several critical security properties:
- Deterministic: The same input always produces the same hash output
- One Way: Computing a hash from input is fast, but finding an input that produces a specific hash is computationally infeasible
- Avalanche Effect: Changing even one bit of input completely changes the output hash
- Collision Resistant: Finding two different inputs that produce the same hash is practically impossible
Each block contains the blockchain hash of the previous block, creating a chain where altering any historical data changes all subsequent hashes. This chain structure makes tampering immediately detectable because the altered block hash would no longer match what the next block expects.
2. Asymmetric Encryption and Digital Signatures
Blockchain encryption relies on asymmetric cryptography using mathematically linked key pairs. Each user generates a private key (kept secret) and a public key (shared openly). The private key can sign transactions that anyone can verify using the public key, but no one can forge signatures without the private key.
This encrypted blockchain architecture enables trustless ownership verification. When you send cryptocurrency, you sign the transaction with your private key. Network nodes verify your signature using your public key, confirming you authorized the transfer without needing to know your private key. The mathematics of elliptic curve cryptography ensures that deriving a private key from a public key would take longer than the age of the universe with current computing technology.
3. Distributed Consensus Mechanisms
Consensus mechanisms enable thousands of independent nodes to agree on the current state of the blockchain without trusting each other. Proof of Work (used by Bitcoin) requires miners to expend computational resources to propose blocks, while Proof of Stake requires validators to lock up economic stake as collateral for honest behavior.
These mechanisms create economic security by making attacks expensive. To successfully attack Bitcoin, an adversary would need to control over 51 percent of global mining power, currently requiring billions of dollars in hardware plus ongoing electricity costs. The economic cost exceeds potential gains, making attacks irrational for profit-motivated attackers.
4. Decentralized Network Architecture
The distributed architecture eliminates single points of failure that plague centralized systems. Thousands of nodes independently verify every transaction and maintain complete copies of the blockchain. An attacker cannot compromise the network by targeting any single server, organization, or geographic location.
This decentralization means blockchain for cybersecurity provides unprecedented resilience. Even if half the network nodes went offline simultaneously, the remaining nodes would continue operating normally. The Bitcoin network has maintained over 99.98 percent uptime since launch, a reliability record unmatched by any centralized service.
Key Security Features of Blockchain
Beyond the fundamental pillars, blockchain technology incorporates numerous security features that protect data integrity, ensure transaction validity, and prevent common attack vectors.
| Security Feature | How It Works | Protection Provided |
|---|---|---|
| Immutability | Hash chains link blocks, so changing one invalidates all subsequent blocks | Prevents historical data tampering and provides permanent audit trails |
| Transparency | All transactions are visible to network participants in real time | Enables independent verification and eliminates hidden manipulation |
| Trustless Verification | Mathematical proofs replace trust in institutions or individuals | Removes counterparty risk and enables transactions between strangers |
| Pseudonymity | Addresses not directly linked to real-world identities | Provides privacy while maintaining transaction auditability |
| Finality | Confirmed transactions cannot be reversed or disputed | Eliminates chargebacks and settlement uncertainty |
Merkle Trees for Efficient Verification
Merkle trees enable efficient verification of large data sets by organizing transaction hashes into a tree structure. Each leaf node contains a transaction hash, and parent nodes contain hashes of their children, ultimately producing a single root hash representing all transactions. This structure allows nodes to verify specific transactions without downloading the entire block, enabling lightweight clients on mobile devices while maintaining security.
Nonce and Difficulty Adjustment
In Proof of Work systems, miners must find a nonce value that produces a block hash meeting the current difficulty target. The network automatically adjusts difficulty to maintain consistent block times despite changes in total mining power. This mechanism prevents attackers from suddenly overwhelming the network with hash power and ensures predictable block production.
Transaction Validation Rules
Every node independently validates transactions against protocol rules before accepting them. Invalid transactions, whether malformed, improperly signed, or attempting to spend nonexistent funds, are rejected immediately. This distributed validation means attackers cannot propagate invalid transactions even if they compromise some nodes.
Can Blockchain Be Hacked?
The question of whether blockchain can be hacked requires distinguishing between the core protocol and the broader ecosystem. The fundamental answer is that major blockchain protocols themselves have never been successfully hacked, but the systems built around them have suffered numerous breaches.
Is Blockchain Safe at the Protocol Level?
At the protocol level, is safe to answer with a qualified yes. No attacker has ever successfully altered Bitcoin transaction history or created invalid coins. The cryptographic and economic security properties make protocol level attacks impractical. Breaking SHA256 encryption would require computational resources exceeding what currently exists on Earth. Executing a 51 percent attack on Bitcoin would cost billions of dollars with uncertain success.
Where Blockchain Vulnerabilities Actually Exist
When asking can the blockchain be hacked, the honest answer is that attackers target weaknesses surrounding the blockchain rather than the blockchain itself:
- Cryptocurrency Exchanges: Centralized exchanges holding user funds have lost billions to hacks. The Mt. Gox breach in 2014 resulted in 850,000 Bitcoin stolen.
- Private Key Theft: Phishing attacks, malware, and social engineering steal private keys from individual users.
- Smart Contract Bugs: Vulnerabilities in smart contract code have enabled attackers to drain funds. The 2016 DAO hack exploited a reentrancy bug to steal 3.6 million ETH.
- Bridge Protocols: Cross-chain bridges connecting different blockchains have suffered major exploits totaling billions in losses.
Understanding whether a blockchain can be hacked means recognizing that security failures typically occur at integration points rather than core protocol layers. The blockchain hackable surface area exists primarily in applications, interfaces, and human elements rather than the underlying technology.
Blockchain Security Issues and Attack Vectors
Understanding blockchain security issues requires examining the specific attack vectors that threaten blockchain networks and their users. While hacking the blockchain protocol remains impractical, several attack types pose real risks.
| Attack Type | Mechanism | Risk Level | Mitigation |
|---|---|---|---|
| 51% Attack | Attacker controls majority hash power to reorganize blocks | Low for major chains, High for small chains | Increased confirmations, network growth |
| Sybil Attack | Creating multiple fake identities to gain network influence | Medium | Proof of Work/Stake makes identity creation costly |
| Eclipse Attack | Isolating a node by controlling all its connections | Medium | Multiple peer connections, peer diversity |
| Routing Attack | Intercepting network traffic to partition or delay blocks | Low to Medium | Encrypted connections, diverse routing paths |
| Smart Contract Exploit | Exploiting bugs in contract code to drain funds | High | Code audits, formal verification, bug bounties |
| Phishing Attack | Tricking users into revealing private keys or signing malicious transactions | Very High | User education, hardware wallets, verification |
51 Percent Attacks Explained
A 51 percent attack occurs when an attacker controls majority mining or staking power, enabling them to create an alternative blockchain history. The attacker can reverse their own transactions (enabling double spending) and prevent other transactions from confirming. However, they cannot steal funds from other addresses or create coins beyond protocol rules.
For Bitcoin, executing a 51 percent attack would require controlling more hash power than the rest of the world combined. The estimated cost exceeds 10 billion dollars in hardware alone, plus ongoing electricity costs of millions daily. Smaller blockchains with less security have suffered successful 51 percent attacks, with Ethereum Classic experiencing multiple attacks that enabled double spending of millions of dollars.
Smart Contract Vulnerabilities
Smart contracts introduce programmable logic to blockchains but also create new attack surfaces. Common vulnerabilities include reentrancy bugs (where contracts can be called repeatedly before state updates), integer overflow errors, access control failures, and oracle manipulation. The immutable nature of blockchain means buggy contracts cannot be easily patched after deployment.
Private Key Security Challenges
The encryption blockchain model places full responsibility for key security on users. Unlike traditional banking where institutions can reverse fraudulent transactions, blockchain transactions are final. Lost or stolen private keys result in permanent loss of associated funds. Studies estimate over 20 percent of all Bitcoin may be permanently inaccessible due to lost keys.
How Blockchain Security Works: Step by Step
Understanding how blockchain cybersecurity functions requires examining the complete lifecycle of a transaction from creation through final confirmation.
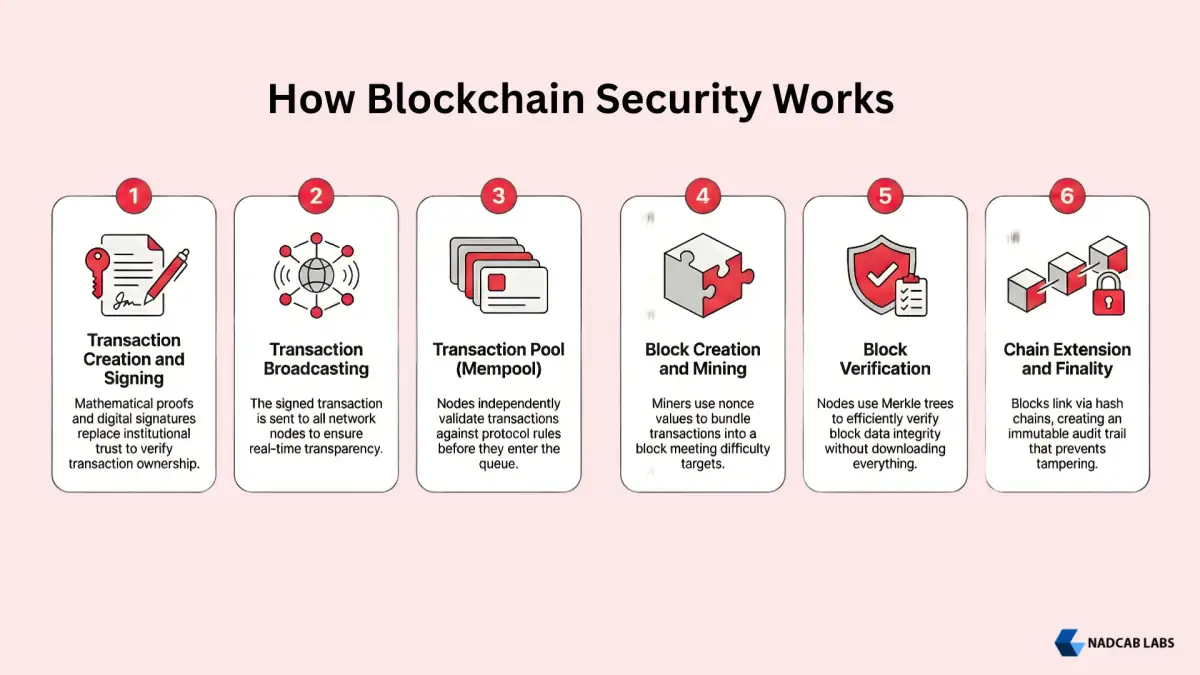
Step 1: Transaction Creation and Signing
When a user initiates a transaction, their wallet software creates a transaction message containing the recipient address, amount, and other relevant data. The wallet then signs this message using the sender’s private key, producing a cryptographic signature that proves authorization without revealing the private key itself.
Step 2: Transaction Broadcasting
The signed transaction broadcasts to connected network nodes. Each receiving node performs initial validation, checking that the signature is valid, the sender has sufficient balance, and the transaction follows protocol rules. Valid transactions propagate across the network within seconds.
Step 3: Transaction Pool and Selection
Validated transactions enter the mempool (memory pool) where they wait for inclusion in a block. Miners or validators select transactions from the mempool, typically prioritizing those offering higher fees. This creates a fee market that naturally manages network congestion.
Step 4: Block Creation and Proof of Work
Miners assemble selected transactions into a candidate block, calculate the Merkle root, and begin the mining process. They repeatedly hash the block header with different nonce values until finding one that produces a hash meeting the difficulty target. This computationally intensive process creates the security guarantees of Proof of Work.
Step 5: Block Verification and Propagation
When a miner finds a valid block, they broadcast it to the network. Other nodes verify the block by checking the proof of work, validating all transactions, confirming the block builds on the current chain tip, and ensuring all protocol rules are followed. Valid blocks propagate across the network within seconds.
Step 6: Chain Extension and Finality
As subsequent blocks build on top of the confirmed block, the transaction gains increasing finality. Each additional block requires an attacker to redo more work to alter history. After six confirmations (about one hour on Bitcoin), transactions are considered irreversible for most practical purposes.
Blockchain Security by Network Type
Security characteristics differ significantly between blockchain types. Understanding these differences helps organizations choose appropriate blockchain architectures for their security requirements.
Public Blockchain Security
Public blockchains like Bitcoin and Ethereum derive security from massive decentralization and economic incentives. Anyone can participate, and security scales with network size. The tradeoff is that all transaction data is publicly visible, and performance is limited by the need for global consensus.
- Strengths: Maximum decentralization, censorship resistance, transparent verification
- Weaknesses: Limited throughput, public transaction visibility, slower finality
Private Blockchain Security
Private blockchains restrict participation to authorized entities, enabling higher performance and data privacy. However, this centralization reduces the security guarantees compared to public networks. The administrator controlling participant access becomes a potential single point of failure.
- Strengths: Higher throughput, data privacy, regulatory compliance easier
- Weaknesses: Centralized trust, fewer validators, potential for insider manipulation
Consortium Blockchain Security
Consortium blockchains balance decentralization and performance by distributing control among multiple known organizations. No single entity can manipulate the network, but the limited validator set means security depends on the honesty of identified participants rather than anonymous economic incentives.
Best Practices for Securing Blockchain Assets
Implementing robust blockchain cyber security practices protects against the real world vulnerabilities that threaten blockchain users and organizations.
Hardware Wallet Usage
Hardware wallets store private keys on dedicated secure devices that never expose keys to potentially compromised computers. Transactions are signed within the device itself, protecting against malware that might steal keys from software wallets. For significant holdings, hardware wallets provide essential protection against the most common attack vector.
Multi Signature Security
Multi signature wallets require multiple private keys to authorize transactions, eliminating single points of failure. A 2 of 3 multi signature setup means any two of three keyholders must sign to move funds. This protects against both single key compromise and loss while enabling organizational controls over shared assets.
Cold Storage Practices
Cold storage keeps private keys completely offline, eliminating network based attack vectors. Keys can be generated on air gapped computers, stored on paper or metal backups, and only brought online when needed for transactions. Major exchanges and institutions use cold storage for the majority of customer funds.
Smart Contract Security Measures
For organizations deploying smart contracts, security requires professional code audits by specialized firms, formal verification where possible, comprehensive testing including edge cases, bug bounty programs to incentivize responsible disclosure, and gradual deployment with value caps during initial phases.
Network Security Hygiene
Users should avoid public Wi-Fi when making transactions, verify wallet software authenticity before installation, enable two factor authentication on exchange accounts, regularly update all software, and remain vigilant against phishing attempts that mimic legitimate blockchain services.
Build Secure Blockchain Solutions with Expert Development
Whether you need secure smart contract development, blockchain security auditing, private network deployment, or enterprise blockchain solutions, our experienced development team delivers security-focused implementations tailored to your requirements. We combine deep cryptographic expertise with industry best practices to build blockchain systems you can trust.
Final Perspective
Blockchain security represents a fundamental advancement in how we protect digital assets and verify data integrity. The combination of cryptographic hashing, asymmetric encryption, distributed consensus, and economic incentives creates security properties that traditional centralized systems cannot match. The remarkable track record of major blockchain protocols, securing trillions in value without protocol-level breaches, demonstrates that this security model works in practice.
However, understanding blockchain cryptography and security requires recognizing that the ecosystem surrounding blockchains remains vulnerable. Exchanges, wallets, smart contracts, and human factors create attack surfaces that sophisticated adversaries successfully exploit. The question of whether can blockchain be hacked depends entirely on where you draw the system boundary. The core protocol remains extraordinarily robust while the applications built upon it require careful security engineering.
For organizations and individuals engaging with blockchain in cybersecurity contexts, success requires combining the inherent security of blockchain architecture with rigorous operational security practices. Hardware wallets, multi-signature setups, cold storage, smart contract audits, and user education together create a defense-in-depth that protects against the real-world threats facing blockchain users today. As blockchain technology continues to mature and adoption grows, these security practices will become standard elements of digital asset management and enterprise blockchain deployment.
Frequently Asked Questions
Yes, blockchain technology itself is extremely safe for storing valuable assets when proper security practices are followed. The cryptographic foundations and distributed architecture have protected trillions of dollars in assets without protocol-level breaches. However, user security practices matter enormously. Using hardware wallets, enabling multi-signature protection, and maintaining secure key backups are essential for protecting valuable holdings. Most losses result from user error, phishing, or compromised exchanges rather than blockchain technology failures.
Current quantum computers cannot hack blockchain encryption, but future quantum computers theoretically could break the elliptic curve cryptography used for digital signatures. The blockchain community is actively researching and developing quantum-resistant cryptographic algorithms. Bitcoin and other major blockchains would need to upgrade their signature schemes before quantum computers become powerful enough to pose a threat. Most experts estimate this is at least a decade away, providing ample time for migration to post-quantum cryptography.
Blockchain hashing and encryption serve different purposes. Hashing is a one-way function that converts any input into a fixed-length output (the hash). You cannot reverse a hash to find the original input. Hashing verifies data integrity and links blocks together. Encryption is a two-way function that transforms data so only authorized parties with the decryption key can read it. Blockchain uses hashing extensively for data integrity, while encryption primarily protects private keys and communication channels rather than on-chain data.
Blockchain security breaches target weaknesses surrounding the blockchain rather than the core technology. Centralized exchanges store user funds and can be hacked like any traditional system. Users fall victim to phishing attacks that steal private keys. Smart contracts contain bugs that attackers exploit. Bridge protocols connecting blockchains introduce new attack surfaces. The blockchain protocol remains secure, but the ecosystem of applications, services, and human factors creates vulnerabilities that attackers successfully exploit.
Blockchain prevents double spending through its consensus mechanism and chronological ordering of transactions. When you spend cryptocurrency, that transaction broadcasts to the network and enters the mempool. Miners include it in a block that references previous blocks, creating a clear timeline. If you try to spend the same funds twice, nodes recognize the second transaction attempts to spend already spent outputs and reject it as invalid. The distributed nature ensures no single party can approve conflicting transactions.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







