Key Takeaways
- A hash function converts any input data into a fixed-length unique code, acting as a digital fingerprint that makes tampering easy to detect.
- Blockchain uses hashing to link blocks together in a chain. If one block is altered, the hash changes and breaks the entire chain, alerting the network immediately.
- SHA-256, SHA-3, RIPEMD-160, Ethash, Scrypt, and Blake2 are the most common hash functions used across different blockchain platforms.
- Hash functions are one-way, meaning you cannot reverse-engineer the original data from the hash output, adding a strong layer of security.
- Hash rate measures how many hash calculations a network performs per second, directly affecting the difficulty of launching attacks on the blockchain.
- Challenges like collision avoidance, quantum computing threats, and performance optimization continue to push the development of more advanced hash functions.
If you have ever looked into how blockchain works under the hood, you have probably come across the word “hash” more than a few times. It sounds technical, and it is. But the idea behind it is surprisingly simple once you break it down. Hashing is one of the main reasons blockchain technology is trusted for everything from cryptocurrency transactions to supply chain tracking.
So what exactly does a hash do? And why does it matter so much for security? This article walks through the full picture. We will cover what hashing is, how different hash functions work, where they are used, and why they are so hard to break. Whether you are building on blockchain, investing in crypto, or just trying to understand the tech, this guide will give you a solid understanding of how hashing keeps blockchain networks safe.
If you are exploring the broader world of blockchain and its applications for businesses, you might find it useful to read about enterprise blockchain applications as a starting point.
What is Hashing in Blockchain?
Hashing is the process of running data through a mathematical function to produce a fixed-size string of characters. That output, called a hash or hash value, acts like a digital fingerprint for the data. No matter how big or small the input is, the output always has the same length. Feed in a single word, and you get a 64-character code. Feed in an entire book, and you still get a 64-character code.
Here is what makes it special for blockchain: the same input will always produce the same output, but even a tiny change in the input creates a completely different output. So if Alice sends 10 BTC to Bob, and someone later tries to change that to 15 BTC, the hash changes entirely. The network immediately knows something has been altered.
According to Wikipedia’s entry on cryptographic hash functions, a good hash function should be deterministic, fast to compute, and practically impossible to reverse. These properties are exactly what make hashing ideal for blockchain security.
Think of it like sealing an envelope with a wax stamp. If the stamp is broken when the letter arrives, you know someone opened it. The hash works the same way for digital data, except it is mathematically enforced and cannot be faked.
How Does a Hash Function Actually Work?
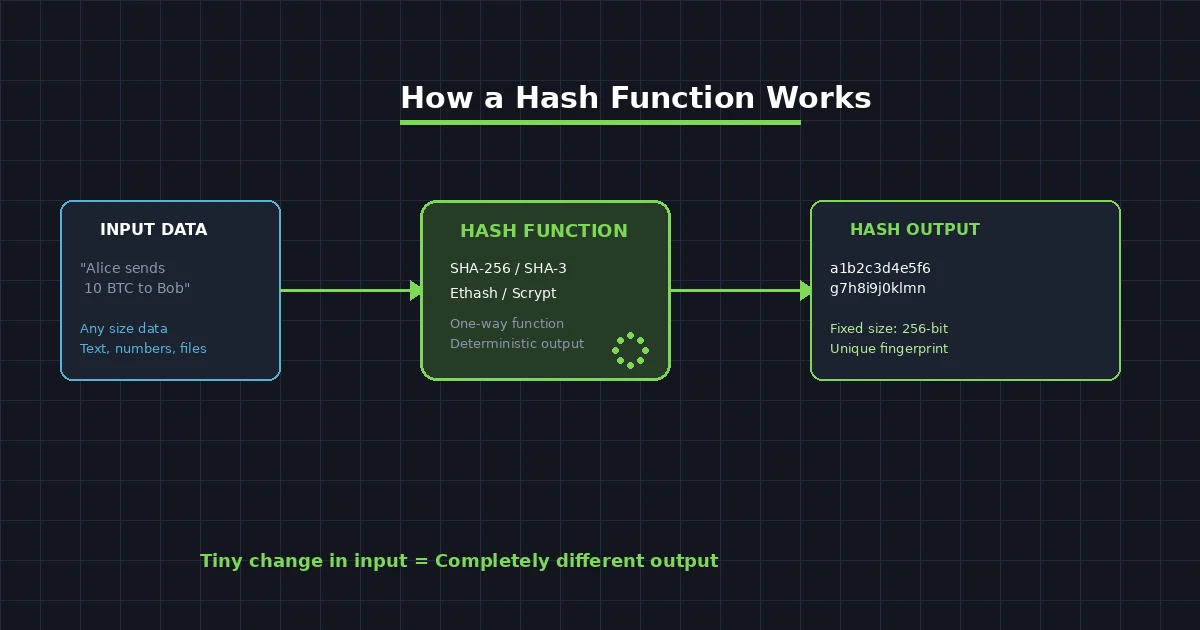
A hash function takes an input, also called a “message,” and passes it through a series of mathematical operations. These operations chop up, mix, and compress the data into a fixed-length output. The process is designed to be one-way. You can easily go from input to hash, but going from hash back to input is practically impossible.
Let us walk through a simplified version of how this works in blockchain:
Step 1: A transaction happens. For example, Alice sends 10 BTC to Bob. This transaction data, which includes the sender address, receiver address, amount, and timestamp, becomes the input.
Step 2: The hash function processes this data. It applies a series of bitwise operations, modular additions, and logical functions to scramble the data thoroughly.
Step 3: The function produces a hash output. In the case of SHA-256, which Bitcoin uses, the output is always a 256-bit number, typically displayed as a 64-character hexadecimal string.
Step 4: This hash is stored in the block along with the transaction data. It also includes the hash of the previous block, which is what creates the chain.
The key properties that make hash functions useful for blockchain are straightforward. They are deterministic, meaning the same input always gives the same output. They are fast to compute. They are collision-resistant, which means it is extremely unlikely that two different inputs will produce the same hash. And they exhibit the avalanche effect, where changing even one bit of the input changes roughly half the bits in the output.
Understanding these fundamentals is important when you look at how technologies like smart contract logic relies on hash-based verification to execute trustless agreements.
Core Properties of a Cryptographic Hash Function
| Property | What It Means | Why It Matters for Blockchain |
|---|---|---|
| Deterministic | Same input always produces the same output | Allows every node to independently verify transactions |
| Pre-image Resistant | Cannot reverse-engineer the input from the output | Protects transaction data from being exposed |
| Collision Resistant | Two different inputs should never produce the same hash | Prevents fraudulent transactions from mimicking legitimate ones |
| Avalanche Effect | Small change in input causes massive change in output | Makes tampering immediately visible to the network |
| Fast Computation | Hash can be calculated quickly | Keeps the network responsive and efficient |
| Fixed Output Length | Output is always the same size regardless of input size | Enables standardized storage and comparison across blocks |
These six properties are non-negotiable. If a hash function fails at any one of them, the entire security model of a blockchain could be compromised. That is why choosing the right hash function matters so much when building or auditing a blockchain network.
Types of Hash Functions Used in Blockchain
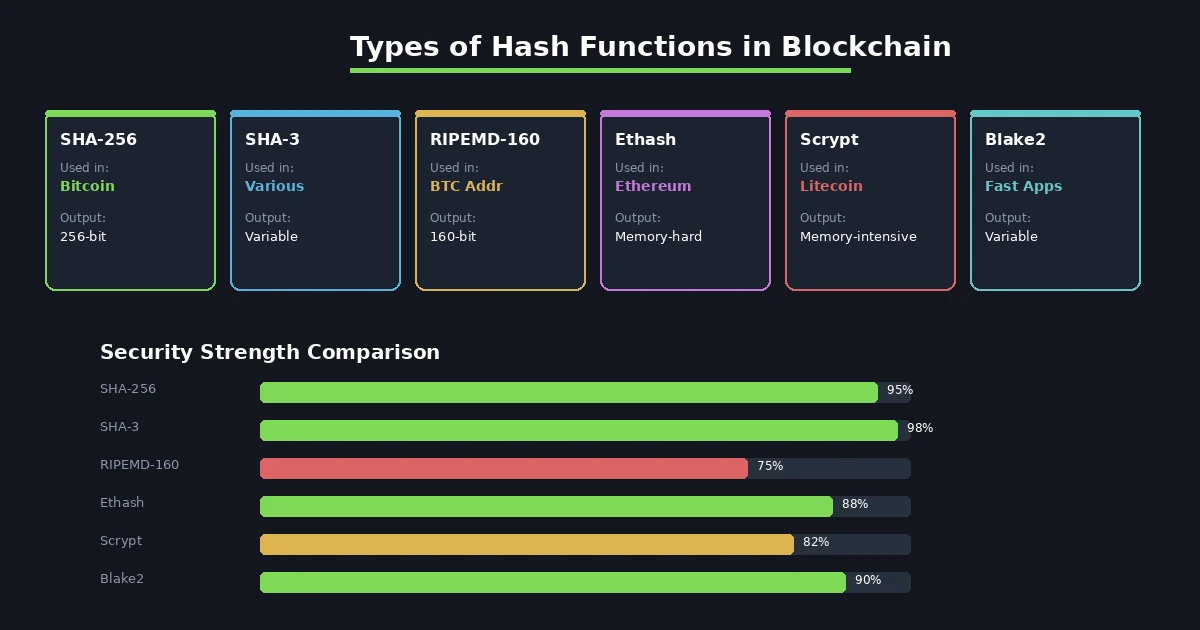
Not all blockchains use the same hashing algorithm. Different platforms have different priorities, whether that is raw security, mining fairness, or computation speed. Here is a breakdown of the most common ones and what sets them apart.
SHA-256 (Secure Hash Algorithm 256-bit)
SHA-256 is the backbone of Bitcoin. Every transaction, every block, and every proof-of-work calculation in Bitcoin relies on this function. It produces a 256-bit hash, which is a 64-character hexadecimal string. The U.S. National Security Agency designed it as part of the SHA-2 family, and it has been battle-tested for over two decades. Its strength lies in the fact that no one has ever found a practical collision, meaning no two different inputs have been shown to produce the same hash under real-world conditions.
SHA-3 (Secure Hash Algorithm 3)
SHA-3 was developed as a backup to SHA-2 in case vulnerabilities were found in the older algorithm. It uses a completely different internal structure called a sponge construction. Several newer blockchain projects have adopted SHA-3 because of its added resistance to length extension attacks, which is a weakness that SHA-2 based functions can theoretically be vulnerable to. It provides a higher ceiling of security for projects that want to plan ahead.
RIPEMD-160
Bitcoin uses RIPEMD-160 specifically for generating wallet addresses. After a public key is hashed with SHA-256, the result is hashed again with RIPEMD-160 to produce a shorter, 160-bit output. This double hashing approach provides both security and a shorter address format that is easier for users to handle. You can see this concept in action when you look at how a Bitcoin address is created from raw keys.
Ethash
Ethereum originally used Ethash for its proof-of-work mining before transitioning to proof-of-stake. Ethash was designed to be memory-hard, meaning it required large amounts of RAM to compute. This made it difficult for ASIC miners (specialized mining hardware) to dominate the network. The goal was to keep mining accessible to regular users with standard GPUs, promoting a more decentralized network.
Scrypt
Litecoin popularized Scrypt as an alternative to SHA-256. Like Ethash, Scrypt is memory-intensive. It was specifically designed to be resistant to brute-force attacks using specialized hardware. By requiring large amounts of memory, Scrypt levels the playing field between different types of mining equipment, making it more democratic in practice.
Blake2
Blake2 is a newer hash function that prioritizes speed without sacrificing security. It outperforms SHA-256 and SHA-3 in benchmark tests while maintaining strong collision resistance. Several blockchain development teams have adopted Blake2 for applications where performance is critical. Its efficiency makes it particularly suitable for high-throughput blockchains that need to process many transactions per second.
Hash Function Comparison Table
| Hash Function | Output Size | Used By | ASIC Resistant | Speed | Best For |
|---|---|---|---|---|---|
| SHA-256 | 256-bit | Bitcoin | No | Fast | General security |
| SHA-3 | Variable | Various projects | Partially | Moderate | Future-proof security |
| RIPEMD-160 | 160-bit | Bitcoin (addresses) | No | Fast | Short address creation |
| Ethash | 256-bit | Ethereum (PoW era) | Yes | Slower | Decentralized mining |
| Scrypt | Variable | Litecoin | Yes | Slower | Fair mining access |
| Blake2 | Variable | Various DApps | Partially | Very Fast | High-throughput chains |
Picking the right algorithm depends on what the blockchain is trying to achieve. A network focused on maximum decentralization might lean toward Ethash or Scrypt, while a system that needs high throughput might choose Blake2. Bitcoin’s long track record with SHA-256 proves that a well-chosen hash function can stand the test of time.
How Hashing Secures Blockchain Networks
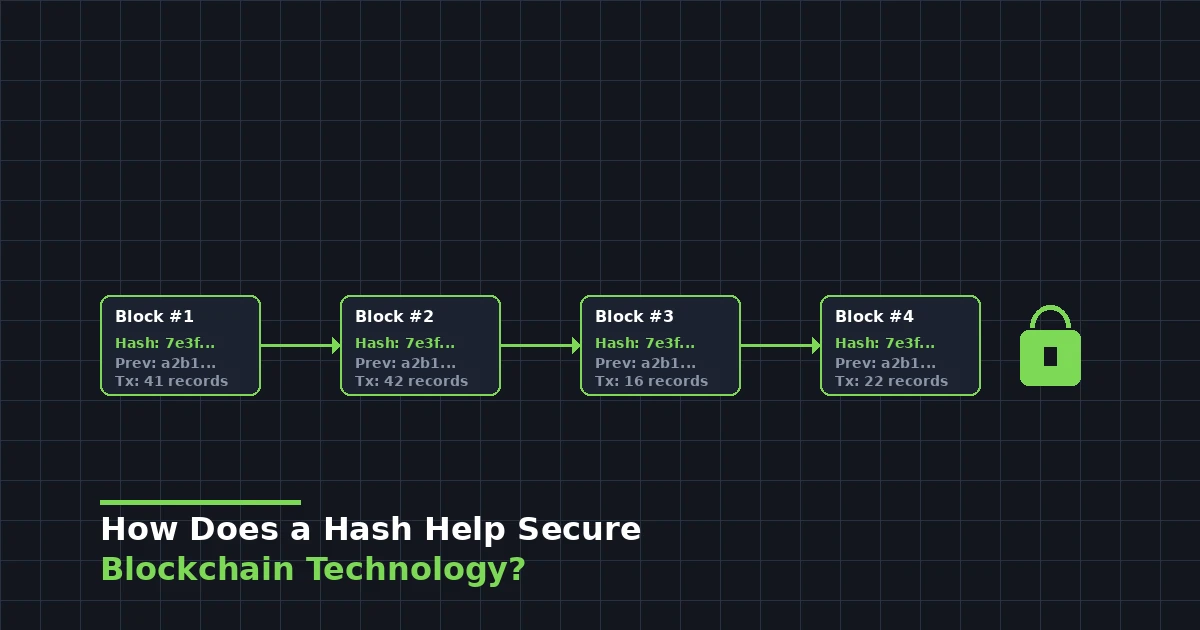
Hashing does not just protect individual pieces of data. It protects the entire structure of the blockchain. Here is how that works in practice.
Every block in a blockchain contains three critical pieces of information: its own hash, the hash of the previous block, and the transaction data. The hash of the previous block is what links one block to the next, forming a chain. If you go back and change something in Block 5, its hash changes. But Block 6 still has the old hash of Block 5 stored in it. Now Block 6 is invalid because the hash it references no longer matches. The same goes for Block 7, Block 8, and every block after that.
To successfully tamper with the blockchain, an attacker would need to recalculate the hash for every single block from the point of alteration all the way to the end of the chain. On top of that, they would need to do this faster than the rest of the network is adding new blocks. On a network like Bitcoin, where thousands of miners are constantly working, this is computationally impossible. This is often referred to as the 51% attack problem, because an attacker would need to control more than half of the network’s total computing power to pull it off.
This chaining mechanism works hand in hand with how data is organized on the blockchain. For a deeper look at how transaction data is structured and verified at the account level, check out our explanation of the account trie in blockchain.
There is another layer to this as well. Blockchains use a structure called a Merkle tree (named after computer scientist Ralph Merkle) to organize the hashes of all transactions within a block. Each transaction is hashed individually. Then pairs of hashes are combined and hashed again, and this process repeats until a single hash remains. This final hash, called the Merkle root, is stored in the block header. If any single transaction in the block is altered, the Merkle root changes, making the tampering detectable without needing to check every transaction individually.
The Lifecycle of a Hash in a Blockchain Transaction
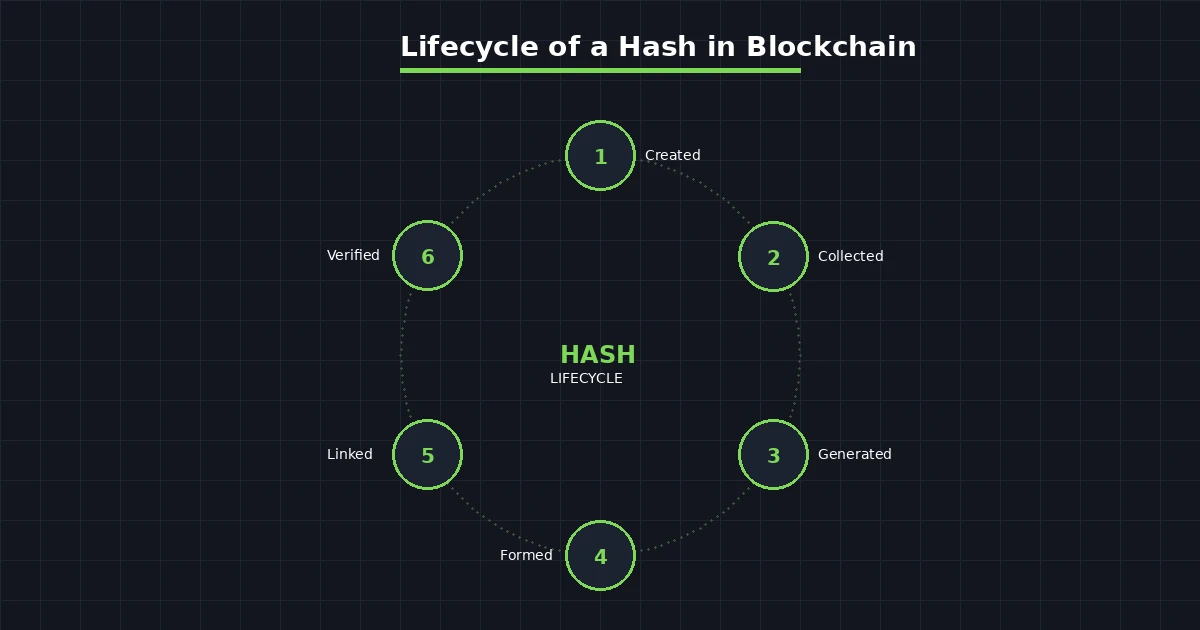
A hash does not just appear out of thin air. It goes through a clear series of stages from the moment a transaction is initiated to when the block is permanently added to the chain. Understanding this lifecycle helps explain why the system is so difficult to compromise.
Stage 1: Transaction Creation. A user initiates a transaction. This could be sending cryptocurrency, recording a supply chain event, or executing a smart contract. The raw transaction data is assembled, including addresses, amounts, timestamps, and any other relevant metadata.
Stage 2: Data Collection. Multiple transactions are gathered into a pool called the mempool. Miners or validators select transactions from this pool to include in the next block. Priority often goes to transactions with higher fees.
Stage 3: Hash Generation. Each individual transaction is hashed. These hashes are then organized into a Merkle tree structure, ultimately producing a single Merkle root hash that represents every transaction in the block.
Stage 4: Block Formation. The block header is assembled. It includes the Merkle root, the hash of the previous block, a timestamp, the difficulty target, and a nonce (a number that miners adjust during the mining process). This entire header is then hashed to produce the block hash.
Stage 5: Chain Linking. The newly created block is linked to the existing chain by including the hash of the most recent block. This creates the unbreakable chain structure that gives blockchain its name.
Stage 6: Network Verification. Other nodes on the network verify the block by independently computing the hash and confirming it meets the required difficulty target. Once a majority agrees, the block is accepted and permanently recorded.
This lifecycle runs continuously. On Bitcoin, a new block is added roughly every 10 minutes. On other networks, it can be much faster. The constant cycle of hashing and verification is what keeps the network honest and tamper-proof. Ensuring that this data remains accessible and verifiable is why data availability layers have become an important area of blockchain development.
Hash Rate and Its Impact on Blockchain Security
Hash rate is a measure of how many hash calculations a blockchain network can perform per second. It is usually expressed in terms like terahashes per second (TH/s) or exahashes per second (EH/s). The higher the hash rate, the more computing power is being directed at securing the network.
Why does this matter? Because a higher hash rate makes it exponentially harder for a bad actor to launch an attack. To take over the Bitcoin network, for example, an attacker would need to match and exceed the combined computing power of every miner on the planet. As of recent data, Bitcoin’s hash rate consistently exceeds 500 EH/s. That is 500 quintillion hash calculations every single second. The energy and hardware costs required to compete with that are staggering.
Hash rate also plays a role in mining difficulty. Networks like Bitcoin automatically adjust their difficulty level based on the current hash rate. If more miners join the network and the hash rate goes up, the difficulty increases to ensure that new blocks are still found at the target interval. If miners leave and the hash rate drops, the difficulty decreases. This self-adjusting mechanism keeps the blockchain stable regardless of how many participants are active.
Hash Rate Levels and Their Security Implications
| Hash Rate Level | Network Security | 51% Attack Feasibility | Example Networks |
|---|---|---|---|
| Very Low (KH/s) | Minimal | Easily achievable | Small test networks |
| Low (MH/s to GH/s) | Vulnerable | Possible with rented hardware | Small-cap altcoins |
| Medium (TH/s) | Moderate | Expensive but not impossible | Mid-tier blockchains |
| High (PH/s to EH/s) | Strong | Practically infeasible | Bitcoin, Litecoin |
| Ultra High (500+ EH/s) | Maximum | Theoretically impossible | Bitcoin (current) |
For platforms that combine blockchain with real-world business models, such as cryptocurrency MLM software platforms, understanding hash rate is essential for choosing a blockchain network that offers enough security for the volume and value of transactions being processed.
Real-World Examples of Hashing in Action
Hashing is not just a theoretical concept. It works in real systems every day, and its impact is measurable.
Bitcoin Transaction Verification: Every ten minutes, Bitcoin miners compete to find a hash that meets the network’s difficulty target. They take the block header data, add a nonce, and hash it. If the resulting hash starts with enough zeros to meet the target, the block is valid. If not, they increment the nonce and try again. This process, called proof of work, is repeated trillions of times per second across the network.
Ethereum Smart Contracts: Before Ethereum’s switch to proof-of-stake, Ethash was used to validate blocks. Even now, hashing remains central to Ethereum’s operation. Transaction data is hashed, state changes are recorded using hash-based tries, and contract interactions are verified through cryptographic proofs. Developers working on smart contract architecture need to understand how these hash-based data structures function at every level.
Supply Chain Tracking: Companies use blockchain hashing to track products from manufacturing to delivery. Each step in the supply chain creates a new transaction that is hashed and added to the blockchain. This creates an immutable record that any authorized party can verify.
Digital Identity: Some identity verification systems hash personal information to create unique identifiers. The original data is never stored on the blockchain, only the hash. This allows verification without exposing sensitive data.
Verification tools like block explorers let anyone look up a transaction hash and confirm that it was processed and recorded on the blockchain. This kind of transparency is one of the main reasons organizations trust blockchain for critical operations.
Challenges in Blockchain Hashing
Hashing is not perfect, and the technology faces several ongoing challenges that developers and security researchers are actively working on.
Collision Risk: While modern hash functions like SHA-256 have never had a practical collision, the theoretical possibility exists. As computing power grows, the margin of safety narrows. Google demonstrated a practical collision attack against SHA-1 in 2017, which is one reason the industry has moved to stronger algorithms. The concern is that SHA-256 could eventually face similar pressure, though that day appears to be far off.
Quantum Computing Threats: Quantum computers operate on fundamentally different principles than classical computers. A sufficiently powerful quantum computer could theoretically break certain cryptographic hash functions by solving the underlying mathematical problems much faster. Researchers are already working on quantum-resistant hash algorithms, but deploying them across existing blockchain networks is a massive undertaking. If you are interested in how blockchain is adapting to new technological shifts, take a look at how Solana’s blockchain innovations are pushing the boundaries of what distributed networks can do.
Energy Consumption: Proof-of-work mining, which relies heavily on repetitive hashing, consumes enormous amounts of electricity. Bitcoin’s energy usage has been compared to that of small countries. This has driven the search for more energy-efficient consensus mechanisms and hash functions that can deliver security without the environmental cost.
Performance vs. Security Trade-offs: Faster hash functions process more transactions per second, but they may sacrifice some security properties. Slower, more secure functions provide stronger protection but can bottleneck the network. Finding the right balance is an ongoing challenge, especially for blockchains that aim to handle thousands of transactions per second. Projects focused on gas optimization in smart contracts often deal directly with this tension between computational efficiency and security.
Implementation Errors: Even the best hash function can be undermined by poor implementation. Bugs in the code, improper use of salt values, or weak random number generation can introduce vulnerabilities that attackers can exploit. This is why working with experienced blockchain development professionals is essential for any serious project.
How Hashing Supports Decentralization
One of the less obvious but equally important roles of hashing is how it enables decentralization. In a centralized system, a single authority verifies and approves transactions. In a decentralized blockchain, every node on the network performs this verification independently. Hashing makes this possible because it provides a quick, reliable way for any node to check the validity of a block.
When a new block is broadcast to the network, each node takes the block data and runs it through the same hash function. If the resulting hash matches the one claimed by the block’s creator, the block is accepted. If it does not match, the block is rejected. This process takes milliseconds and requires no communication between nodes. Every participant can independently verify the truth without relying on anyone else.
This trustless verification is what makes blockchain different from traditional databases. No single entity controls the data, and no single entity can alter it without being caught. The math behind the hash function is the authority, not any person or organization. For businesses looking at decentralized business models, this property of hashing is the foundation that makes trustless networks viable.
Strengthen Your Blockchain With Expert Hash Management
Building a blockchain project? Get the hash function strategy, implementation, and security audit your network needs. Our team ensures your system is tamper-proof from day one.
The Future of Hashing in Blockchain
Hashing technology is not standing still. As blockchain networks grow and the threat landscape evolves, hash functions are being pushed to adapt as well.
The most significant area of research right now is post-quantum cryptography. Organizations like the National Institute of Standards and Technology (NIST) have been evaluating new cryptographic algorithms that can withstand attacks from quantum computers. Several of these candidates use hash-based signature schemes, which means hashing will remain central to blockchain security even in a post-quantum world.
There is also a push toward more energy-efficient hashing. As the environmental impact of proof-of-work mining has come under scrutiny, developers are looking for ways to reduce the energy cost of hash calculations without weakening security. Some newer consensus mechanisms minimize the amount of repetitive hashing required, while others use hash functions that are optimized for modern hardware to reduce power consumption per hash.
Zero-knowledge proofs are another area where hashing plays a growing role. These cryptographic protocols allow one party to prove they know a piece of information without revealing the information itself. Hash functions are used to create commitments and verify proofs in zero-knowledge systems, enabling privacy-focused blockchain applications like confidential transactions and anonymous voting.
According to Wikipedia’s overview of post-quantum cryptography, hash-based signatures are one of the leading candidates for quantum-resistant security because they rely on the well-understood hardness of hash function inversion rather than number-theoretic problems that quantum computers can solve efficiently.
Frequently Asked Questions
This situation is called a hash collision, and it is one of the biggest concerns in cryptographic security. If two different transactions produced the same hash, a malicious actor could potentially substitute one for the other without detection. Modern hash functions like SHA-256 are designed to make collisions statistically impossible. The probability of finding one by accident is roughly 1 in 2 raised to the power of 128, which is a number larger than the estimated atoms in the observable universe. No practical collision has ever been found for SHA-256.
No. Hash functions used in blockchain are specifically designed to be one-way functions. This means you can easily compute the hash from the input, but it is computationally infeasible to reconstruct the original input from the hash output alone. This property, called pre-image resistance, is fundamental to blockchain security. Even with the most powerful supercomputers currently available, reversing a SHA-256 hash would take longer than the age of the universe. This one-way property protects transaction details and private keys from being exposed.
The hash function directly impacts how fast a blockchain can process transactions and add new blocks. Faster hash functions like Blake2 can handle higher transaction throughput, making them suitable for blockchains that need to process thousands of operations per second. Slower, more memory-intensive functions like Scrypt and Ethash provide better resistance to specialized mining hardware but reduce overall processing speed. The trade-off between speed and security is one of the most critical design decisions when building a blockchain.
Bitcoin uses a double hashing approach for generating wallet addresses. A public key is first hashed with SHA-256 and then hashed again with RIPEMD-160. This two-step process serves two purposes. SHA-256 provides strong collision resistance and security. RIPEMD-160 then shortens the result to 160 bits, creating a more compact address that is easier for users to share and store. Using two different hash functions from different algorithm families also adds an extra layer of protection, since a weakness in one would not automatically compromise the other.
Quantum computers pose a theoretical threat to certain cryptographic systems, but the risk to hash functions is less severe than many people assume. Grover’s algorithm could reduce the effective security of a hash function by half, meaning SHA-256 would offer about 128 bits of security against quantum attacks instead of 256. While this is a reduction, 128 bits is still considered extremely strong. The bigger concern is for public key cryptography, not hashing. Blockchain developers are already researching quantum-resistant algorithms to prepare for this eventuality well in advance.
Businesses should conduct regular security audits of their blockchain systems to verify proper hash function implementation. This includes checking that the correct algorithm is being used, that salt values and nonces are generated using cryptographically secure random number generators, and that the hash outputs are being stored and compared correctly. Independent third-party audits are recommended, as internal teams may overlook issues they built themselves. Working with experienced blockchain development teams who specialize in cryptographic security is the most reliable way to ensure correct implementation.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







