Key Takeaways
- Double spending occurs when digital assets are fraudulently used in multiple transactions simultaneously, threatening blockchain integrity.
- Consensus mechanisms like Proof of Work and Proof of Stake serve as the primary defense against double spending attacks.
- Cryptographic hashing creates tamper-proof links between blocks, making historical transaction modification practically impossible.
- Network validation through distributed nodes ensures no single entity can manipulate transaction records.
- Smart contracts automate transaction verification and enforce spending rules without human intervention.
- Combining multiple prevention strategies creates layered security that makes double spending economically and technically unfeasible.
The rise of digital currencies brought a unique challenge that traditional banking never faced directly. When you hand someone a physical dollar bill, that money physically leaves your possession. But digital information can be copied endlessly. This fundamental difference created what we now call the double spending problem, and solving it became the cornerstone achievement of blockchain technology.
Understanding how blockchain prevents double spending is not just technical curiosity. It is essential knowledge for anyone building, investing in, or using cryptocurrency systems. The methods used to prevent this type of fraud form the backbone of trust in decentralized networks. Without these protections, digital currencies would have no more value than copied files on a computer.
What Exactly is Double Spending?
Double spending happens when someone successfully spends the same digital currency unit more than once. Imagine sending the same ten dollars to two different people at exactly the same moment. In traditional banking, centralized systems catch this immediately because a single authority controls the ledger. But in a decentralized network with no central authority, this becomes genuinely tricky.
The attack typically works like this. A malicious user initiates two transactions using the same funds simultaneously. One transaction pays a merchant for goods or services. The other transaction sends the same funds back to a wallet the attacker controls. If both transactions get confirmed, the attacker keeps both the purchased goods and their original funds.
This vulnerability existed in every digital payment system before blockchain. Early attempts at digital cash failed precisely because they could not solve this problem without resorting to centralized control. The breakthrough came when Satoshi Nakamoto introduced Bitcoin and its underlying blockchain technology in 2008, offering the first decentralized solution to double spending.
Why Double Spending Prevention Matters
The consequences of successful double spending attacks extend far beyond individual financial losses. They strike at the fundamental trust that makes any currency system work. When people cannot trust that received payments are final, commerce grinds to a halt.
Consider what happens to a cryptocurrency network where double spending becomes possible. Merchants stop accepting payments because they cannot trust transaction finality. Investors lose confidence and withdraw their holdings. The currency value plummets as nobody wants to hold an asset that can be duplicated at will. The entire ecosystem collapses.
This is why every serious blockchain project invests heavily in double spending prevention. The security measures are not optional features. They are existential requirements for any digital currency that wants to maintain value and utility over time.
Types of Double Spending Attacks
Attackers have developed several methods to attempt double spending. Understanding these attack vectors helps in appreciating why multiple prevention layers are necessary.
| Attack Type | Method | Difficulty | Prevention |
|---|---|---|---|
| Race Attack | Sending conflicting transactions simultaneously | Low | Wait for confirmations |
| Finney Attack | Pre-mining blocks with fraudulent transactions | Medium | Multiple confirmations |
| 51% Attack | Controlling majority of network hashrate | Very High | Decentralization, high hashrate |
| Vector76 Attack | Combining race and Finney attack techniques | High | Incoming connection disabling |
Consensus Mechanisms: The First Line of Defense
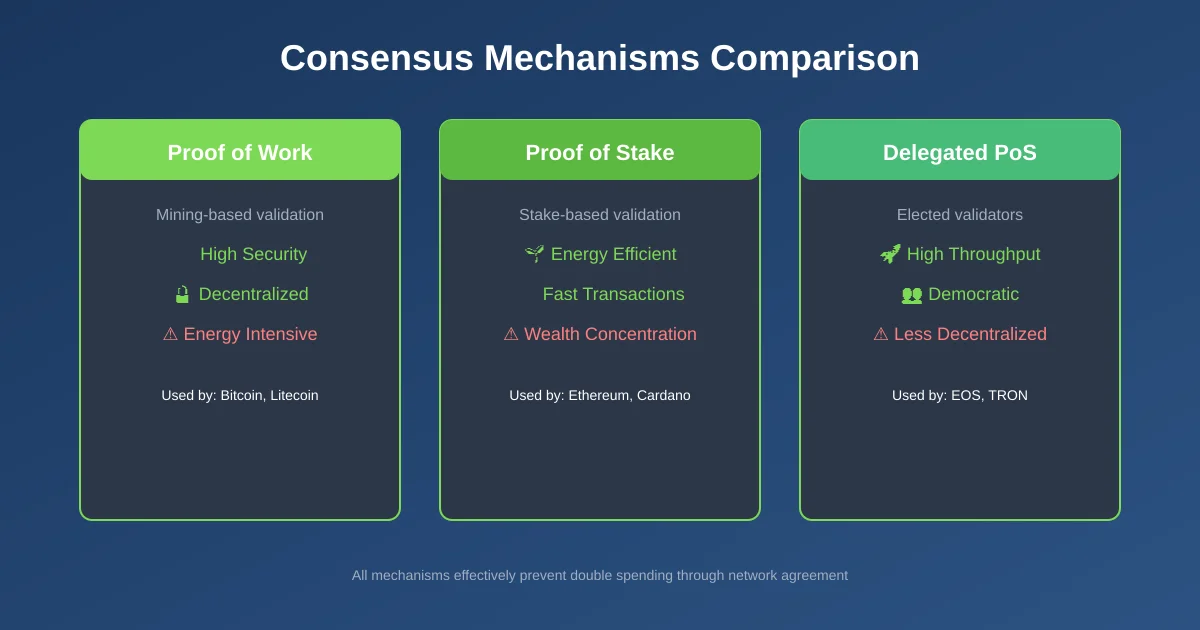
Consensus mechanisms form the primary defense against double spending in blockchain networks. These protocols ensure that all participants in the network agree on which transactions are valid and in what order they occurred. Without consensus, different nodes could have conflicting versions of transaction history, making double spending trivial.
Proof of Work
Proof of Work requires miners to solve complex mathematical puzzles before adding new blocks to the chain. This process demands significant computational resources and electricity. The difficulty ensures that rewriting transaction history would require redoing all the computational work for every block since the fraudulent transaction.
Bitcoin uses Proof of Work, and according to Wikipedia’s documentation on proof of work, the system makes fraudulent blocks extremely expensive to produce. An attacker would need to control more than half the total network computing power to have any realistic chance of double spending. For Bitcoin, this would require billions of dollars in hardware and electricity costs.
Proof of Stake
Proof of Stake takes a different approach. Instead of competing through computational power, validators stake their own cryptocurrency as collateral. If a validator approves fraudulent transactions, they lose their stake. This creates direct financial consequences for dishonest behavior.
Ethereum transitioned to Proof of Stake, requiring validators to lock up 32 ETH. Attempting double spending would risk losing this entire stake, making attacks economically irrational. The mechanism also makes it easier to identify and punish bad actors since their identity is tied to their staked funds.
Cryptographic Hashing: Creating Tamper-Proof Records
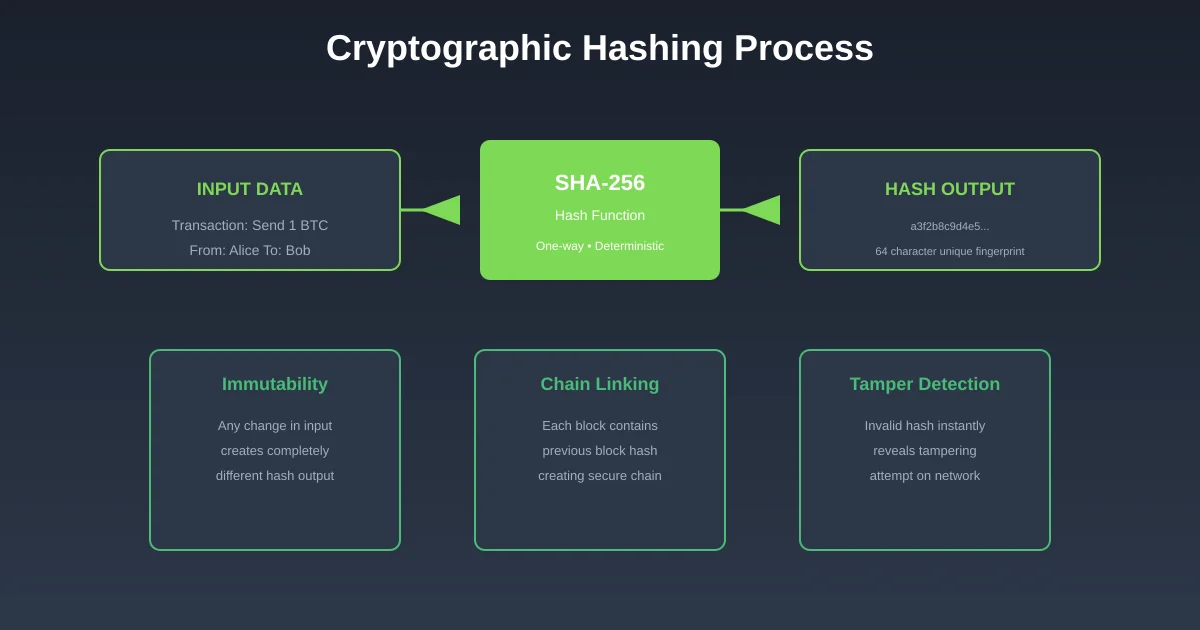
Cryptographic hash functions provide the technical foundation for blockchain immutability. These mathematical functions take any input data and produce a fixed-length output called a hash. The process has several properties that make it perfect for preventing transaction manipulation.
First, the same input always produces the same output. This determinism allows anyone to verify that data has not been altered. Second, even tiny changes to the input produce completely different outputs. Changing a single character in a transaction record would create an entirely different hash, immediately revealing the tampering.
Each block in a blockchain contains the hash of the previous block. This creates a chain where altering any historical transaction would require recalculating every subsequent block. Combined with consensus mechanisms that make block creation expensive, this chain structure makes historical modification practically impossible.
Professional blockchain companies implement these cryptographic protections at multiple levels. Transaction signatures use public key cryptography to prove ownership. Block headers contain Merkle roots that summarize all included transactions. The layered approach creates redundant verification that catches any tampering attempt.
Network Validation: Distributed Trust
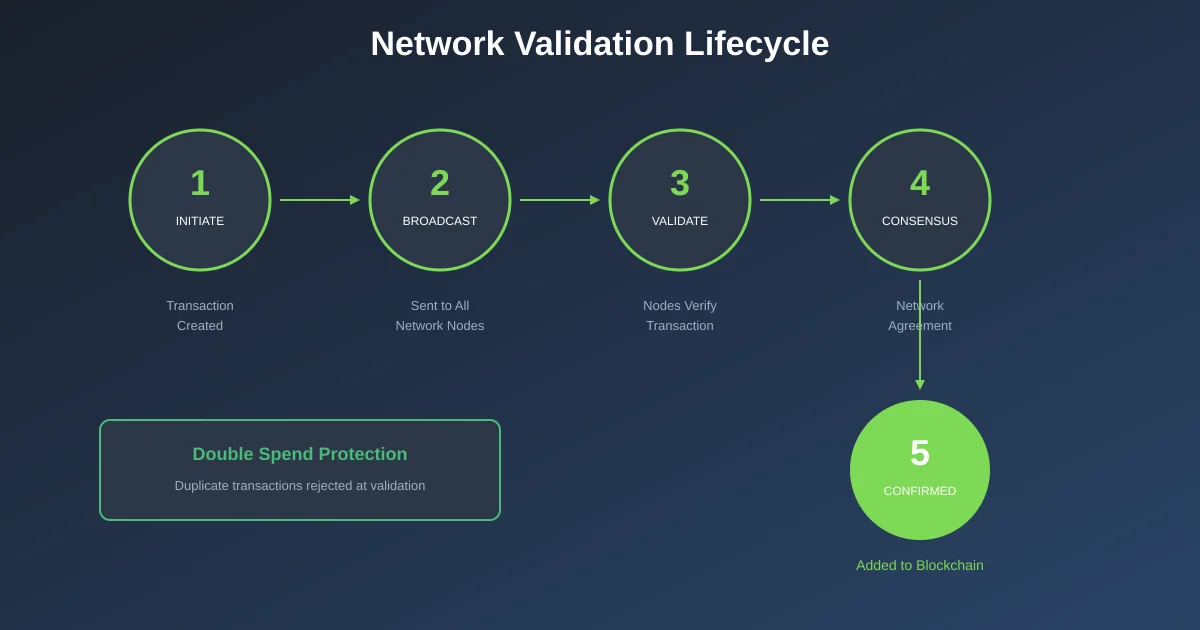
Decentralized validation distributes the responsibility for verifying transactions across thousands of independent nodes. No single entity controls which transactions get approved. This distribution eliminates the single points of failure that centralized systems have.
When you send a transaction on a blockchain network, it broadcasts to every connected node. Each node independently verifies the transaction against their copy of the ledger. They check that the sender actually owns the funds and has not already spent them. Only transactions that pass these checks get included in the pending transaction pool.
This redundant verification makes double spending attacks incredibly difficult. An attacker would need to fool not just one node but a majority of the entire network. With thousands of nodes operated by independent parties across the globe, coordinating such deception becomes practically impossible.
Secure Your Blockchain Project Today
Need expert guidance on implementing double spending prevention? Nadcab Labs brings 8+ years of blockchain development experience to protect your digital assets and ensure transaction integrity.
Smart Contracts: Automated Enforcement
Smart contracts add programmable logic to blockchain transactions. These self-executing agreements automatically enforce transaction rules without requiring manual oversight. For double spending prevention, smart contracts can implement sophisticated verification that goes beyond basic balance checks.
A well-designed smart contract verifies available funds before executing any transfer. It checks transaction history to ensure the same funds have not been committed elsewhere. The contract executes atomically, meaning all conditions must be met or no part of the transaction occurs. This all-or-nothing approach prevents partial spending scenarios.
Smart contracts also enable time-locked transactions and multi-signature requirements. These features add extra verification layers for high-value transfers. A transaction might require approval from multiple parties or include a waiting period that allows for fraud detection before finalization.
Prevention Methods Comparison
Different prevention methods offer varying levels of security and have different trade-offs. Understanding these comparisons helps in designing comprehensive security strategies.
| Method | Security Level | Speed Impact | Cost | Best For |
|---|---|---|---|---|
| Proof of Work | Very High | Slow (10+ min) | High energy cost | Store of value networks |
| Proof of Stake | High | Fast (seconds) | Low energy | General purpose chains |
| Cryptographic Hashing | High | Minimal | Low | All blockchain systems |
| Smart Contracts | Medium-High | Moderate | Development cost | Complex transactions |
| Multi-Signature | Very High | Slow (human delay) | Low | High-value transfers |
The Historical Context of Blockchain Security
The history of blockchain is fundamentally a history of solving the double spending problem. Previous digital cash systems like DigiCash and e-gold failed because they relied on centralized authorities. These central points made them vulnerable to shutdown, fraud, and government interference.
Bitcoin changed everything by demonstrating that trustless consensus was possible. The combination of proof of work, cryptographic hashing, and distributed validation created a system where strangers could transact without needing to trust each other or any central authority. Every blockchain system since has built upon these foundational innovations.
Real World Attack Scenarios and Defenses
Understanding how attacks happen in practice helps appreciate why multiple defense layers matter. Consider a scenario where an attacker wants to double spend on a small merchant.
The attacker sends a transaction paying the merchant for goods. Simultaneously, they broadcast a competing transaction sending those same funds to their own wallet with a higher transaction fee. If the merchant accepts payment after zero confirmations, they might ship goods before the network decides which transaction is valid. The higher-fee transaction to the attacker’s wallet might win, leaving the merchant with neither payment nor goods.
The defense is straightforward but requires patience. Waiting for multiple block confirmations before considering payment final dramatically reduces risk. For Bitcoin, six confirmations provide extremely high security. For smaller transactions, even one or two confirmations provide adequate protection against most attack scenarios.
Confirmation Requirements by Transaction Value
Different transaction values warrant different confirmation thresholds. Here is a practical guide that many exchanges and merchants follow.
Small Transactions Under $1,000 typically require 1-2 confirmations. The economic incentive to attack such small amounts rarely justifies the effort and risk.
Medium Transactions Between $1,000 and $10,000 commonly require 3-4 confirmations. This provides stronger security while maintaining reasonable transaction speed.
Large Transactions Over $10,000 should wait for 6 or more confirmations. High-value transfers justify longer waiting periods for maximum security.
Building Comprehensive Security Strategies
Effective double spending prevention requires combining multiple methods into layered security. No single mechanism provides complete protection. The combination creates overlapping safeguards where each layer compensates for potential weaknesses in others.
A comprehensive strategy starts with choosing the appropriate consensus mechanism for your use case. High-security applications might favor established proof of work networks despite slower transaction speeds. Applications requiring fast finality might choose proof of stake alternatives while implementing additional verification layers.
Smart contract logic adds programmable verification that catches edge cases. Transaction monitoring systems detect suspicious patterns in real time. Multi-signature requirements for large transfers add human oversight. Together, these measures create defense in depth that makes successful attacks extremely unlikely.
Why Experience Matters in Blockchain Security
Implementing effective double spending prevention requires deep expertise in both cryptographic principles and practical blockchain development. Security vulnerabilities often hide in implementation details that only experienced developers recognize.
Nadcab Labs has spent over 8 years developing and securing blockchain systems across diverse industries. This hands-on experience has revealed how theoretical security measures sometimes fail in practice. Edge cases emerge that textbook descriptions never mention. Attack vectors appear that require creative defensive solutions.
The team has implemented consensus mechanisms, designed smart contract security patterns, and conducted security audits for numerous blockchain projects. This depth of experience translates into practical solutions that work in real-world conditions, not just in theory.
Future Developments in Double Spending Prevention
Blockchain security continues evolving as researchers develop new approaches and attackers find new vulnerabilities. Several promising developments are worth watching.
Zero-knowledge proofs enable transaction verification without revealing transaction details. This technology adds privacy while maintaining security. Sharding approaches divide networks into smaller pieces that can process transactions in parallel while maintaining overall security guarantees.
Layer 2 solutions like payment channels and rollups move some transactions off the main chain while inheriting its security properties. These approaches can dramatically increase transaction throughput without sacrificing double spending protection.
Practical Implementation Steps
For organizations looking to implement double spending prevention in their blockchain projects, here are practical steps to follow.
Assessment Phase: Evaluate your specific security requirements based on transaction values, speed needs, and user expectations. Different applications have different optimal trade-offs between security and usability.
Architecture Design: Choose appropriate consensus mechanisms and determine confirmation requirements. Design smart contract logic that enforces your specific business rules while preventing manipulation.
Implementation: Build with security-first mindset. Use established libraries and patterns. Avoid custom cryptography unless absolutely necessary. Have code reviewed by experienced developers.
Testing and Audit: Conduct thorough testing including deliberate attack simulations. Engage third-party security auditors to review the implementation before deployment.
Conclusion
Double spending prevention stands as one of blockchain technology’s greatest achievements. The combination of consensus mechanisms, cryptographic techniques, distributed validation, and smart contracts creates robust protection that has secured trillions of dollars in digital assets.
Understanding these prevention methods is essential for anyone building or using blockchain systems. The theoretical foundations explain why blockchain works. Practical implementation details determine whether a specific system actually achieves its security goals.
As blockchain technology continues maturing, double spending prevention will remain a central concern. New approaches will emerge, but the fundamental principles of consensus, cryptography, and distribution will continue forming the security backbone of decentralized systems.
Frequently Asked Questions
Double spending occurs when someone spends the same digital currency in multiple transactions simultaneously. This is dangerous because it undermines the fundamental trust in digital currency systems. If users could duplicate their coins at will, the currency would lose all value since supply would become infinite. Traditional banks prevent this through centralized ledgers, but blockchain networks need decentralized solutions. The entire cryptocurrency ecosystem depends on preventing double spending to maintain transaction integrity and currency value.
Proof of Work prevents double spending by making fraudulent block creation extremely expensive. Miners must solve complex mathematical puzzles requiring massive computational power. To double spend, an attacker would need to control more than 50 percent of the total network hashrate to rewrite transaction history. For Bitcoin, this would cost billions in hardware and electricity, making attacks economically irrational. The computational difficulty increases with more miners, strengthening security over time as networks grow larger.
The number of required confirmations depends on transaction value and network security. For Bitcoin, one confirmation provides reasonable security for small transactions under a thousand dollars. Medium transactions between one thousand and ten thousand dollars typically require three to four confirmations. Large transactions exceeding ten thousand dollars should wait for six or more confirmations. Each confirmation makes reversing transactions exponentially harder, as attackers would need to redo all computational work since the original transaction.
Smart contracts add programmable verification layers that enhance double spending prevention. They automatically check available balances before executing transfers and can implement atomic transactions where all conditions must be met or nothing executes. Smart contracts enable time-locked transactions, multi-signature requirements, and custom validation logic tailored to specific applications. While smart contracts alone cannot prevent all double spending, they complement consensus mechanisms by adding application-specific security rules that catch edge cases standard protocols might miss.
A 51 percent attack happens when a single entity controls more than half of a blockchain network’s computing power or stake. With majority control, attackers can create alternative transaction histories and force the network to accept their version as valid. They can spend coins, wait for confirmation, then create a longer chain without that transaction, effectively reversing it. Large networks like Bitcoin and Ethereum are generally safe because acquiring 51 percent control costs billions. Smaller networks remain more vulnerable to these attacks.
Experienced blockchain developers understand both theoretical security principles and practical implementation pitfalls. Security vulnerabilities often hide in subtle coding decisions that only experienced eyes catch. They recognize attack patterns from previous projects and implement defensive measures proactively. Experienced teams have encountered edge cases that documentation never mentions and developed solutions through real-world testing. For critical financial infrastructure, this expertise translates into systems that remain secure under actual attack conditions rather than just theoretical models.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







