Key Takeaways
- Permissioned blockchains restrict network access to approved participants through centralized authorization, while permissionless blockchains allow anyone to join and participate without restrictions.
- Permissioned blockchains offer greater control, faster transaction processing, and regulatory compliance, but sacrifice decentralization and trustlessness.
- Permissionless blockchains provide true decentralization, censorship resistance, and trustless operation, but require more energy consumption and face scalability challenges.
- Enterprise applications like supply chain and banking typically favor permissioned architectures, while cryptocurrency and decentralized finance applications require permissionless systems.
- Bitcoin and Ethereum exemplify permissionless blockchains, while Hyperledger Fabric and JPMorgan Coin represent permissioned enterprise solutions.
- Hybrid models combining permissioned and permissionless characteristics are emerging as organizations seek to balance control with decentralization benefits.
The fundamental architecture of a blockchain determines who can participate in the network, validate transactions, and access data. This distinction separates blockchain systems into two primary categories: permissioned and permissionless. Permissioned blockchains restrict network access to approved participants through centralized authorization mechanisms, while permissionless blockchains allow anyone with internet access to join, validate transactions, and participate in governance. This architectural choice profoundly impacts a system’s security model, scalability, regulatory compliance, and real-world applicability. Organizations implementing blockchain solutions must understand these distinctions because selecting the wrong architecture can result in systems that fail to meet compliance requirements, suffer from inadequate decentralization, or experience unnecessary operational complexity.
The blockchain ecosystem is witnessing strong adoption across decentralized finance, gaming, and data analytics, supported by both permissionless and permissioned architectures. Permissionless blockchains such as Ethereum and Bitcoin continue to dominate open innovation in DeFi, enabling peer-to-peer financial services, decentralized exchanges, flash loans, and synthetic assets without centralized intermediaries. These systems are projected to drive DeFi growth beyond USD 1.55 trillion by 2034. In parallel, permissioned blockchains are increasingly adopted by enterprises for controlled data sharing, governance, and compliance in sectors such as healthcare, logistics, and financial analytics. Blockchain gaming is also expanding rapidly, with market forecasts projecting growth from USD 8.5 billion in 2023 to USD 314.3 billion by 2030, driven by NFT-based ownership and play-to-earn models.
This comprehensive guide explains the key differences between permissioned and permissionless blockchains, how each functions technically, real-world examples of each architecture, security and governance trade-offs, and how to select the appropriate blockchain type for your organization’s requirements. By the end, you will understand which architecture best suits different applications, from enterprise supply chain systems to decentralized financial protocols, and recognize the fundamental trade-offs between control and decentralization. If you are new to this topic, start by learning the basics of blockchain technology to build a strong foundation before exploring advanced concepts.
What is a Permissioned Blockchain?
Definition
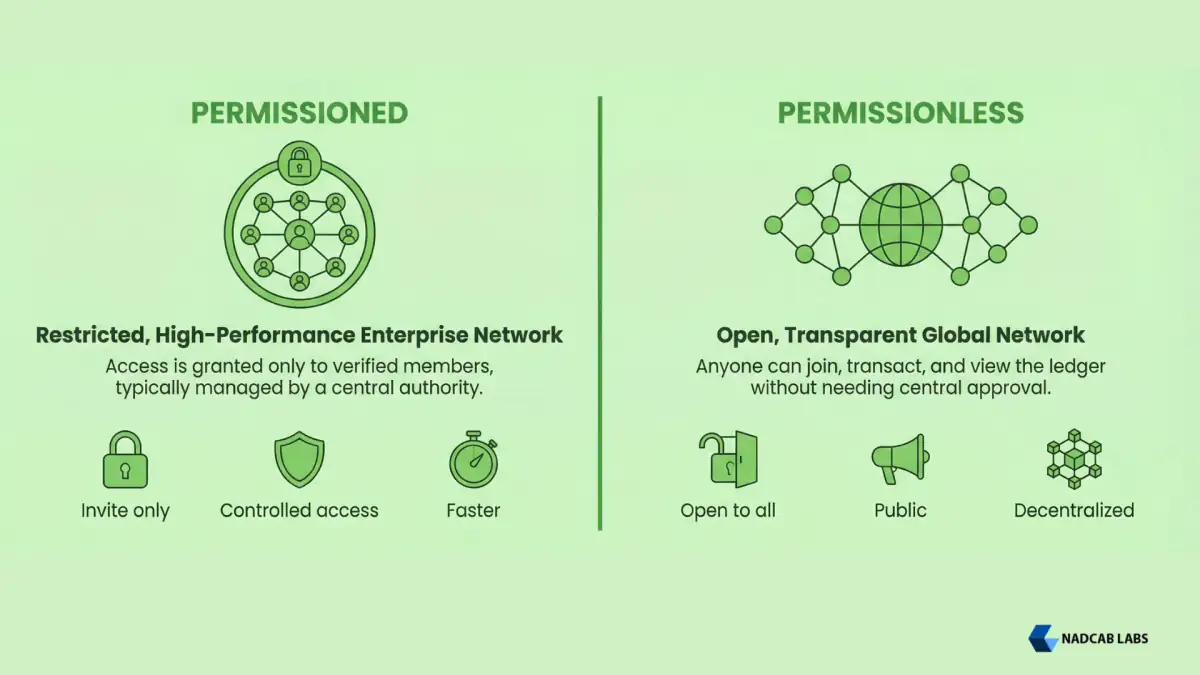
A permissioned blockchain is a distributed ledger system where network access, transaction validation authority, and data participation are restricted to approved participants. Organizations control who can join the network through administrative processes, digital identities, and access credentials, enabling centralized governance while maintaining the immutability and transparency benefits of blockchain technology.
In permissioned blockchains, the network operator or consortium establishes rules governing participation. Before users can access the network or validate transactions, they must obtain explicit authorization through an identity verification process. This contrasts sharply with permissionless systems, where anyone can participate anonymously. Permissioned networks typically employ white-listing mechanisms where approved addresses receive network access credentials, and removing participants requires administrative action.
The permissioned model allows organizations to implement role-based access controls. Different participants might have different permissions, such as full node operators, transaction validators, auditors with read-only access, or regular users limited to specific transaction types. This granular control enables organizations to enforce compliance requirements and operational policies directly within the blockchain architecture.
How Permissioned Blockchains Work
Step 1: Identity and Authorization
Prospective participants request access to the network and undergo identity verification by the network administrator or consortium. Upon approval, participants receive digital certificates or credentials confirming their authorization status.
Step 2: Transaction Submission
Authorized participants submit transactions digitally signed with their credentials. The network validates that the submitter holds valid authorization before accepting the transaction into the memory pool.
Step 3: Validation by Approved Nodes
Only approved validator nodes process transactions. The network operator selects trusted nodes with strong security infrastructure to validate transactions and maintain the distributed ledger, reducing the number of nodes required compared to permissionless systems.
Step 4: Consensus Among Permissioned Validators
Validators reach consensus using optimized protocols like Byzantine Fault Tolerance or Practical Byzantine Fault Tolerance. Since validators are known and trusted, the network can achieve consensus much faster than permissionless systems requiring Proof of Work.
Step 5: Block Creation and Distribution
Once consensus is reached, a validator creates a new block containing approved transactions and distributes it to all authorized network participants. The immutable record is updated across all nodes, maintaining consistency and transparency within the approved network.
What is a Permissionless Blockchain?
Definition
A permissionless blockchain is a distributed ledger system that allows anyone with internet access to participate in the network without prior authorization. Participants can join, submit transactions, validate blocks, and access the complete ledger without requesting permission from a central authority, embodying the core principle of decentralized trust.
Permissionless blockchains operate on the principle of complete openness. Any individual can download the blockchain software, synchronize the network data, and begin participating as a full node. Transaction validators (called miners or validators, depending on the consensus mechanism) compete to validate transactions without requiring administrative approval. This open participation model means permissionless networks maintain no official list of approved participants.
The permissionless architecture enables censorship resistance and true decentralization. No single entity can prevent users from accessing the network, submitting transactions, or validating blocks. This property makes permissionless blockchains particularly valuable for applications requiring financial censorship resistance, such as remittances to countries with capital controls or decentralized finance protocols that must operate without central shutdown risk.
How Permissionless Blockchains Work
Step 1: Anonymous Participation
Any individual who downloads blockchain software and begins participating immediately. No registration, identity verification, or approval process is required. Users can create wallet addresses pseudonymously or use existing addresses to submit transactions.
Step 2: Transaction Broadcasting
Participants broadcast transactions to the peer-to-peer network. The network accepts transactions from any sender without verifying identity, though transactions must include valid cryptographic signatures proving sender authorization.
Step 3: Open Validation Competition
Any participant can become a validator (miner or block producer) without permission. Validators compete using the network’s consensus mechanism, such as Proof of Work, requiring computational power, or Proof of Stake, requiring cryptocurrency holdings.
Step 4: Decentralized Consensus
The network reaches consensus through economic incentives and cryptographic verification rather than trust in known validators. Thousands of independent nodes validate transactions using the established Proof of Work or Proof of Stake rules.
Step 5: Transparent Distribution
Successfully validated blocks propagate across the entire network, and all participants can independently verify every transaction. The immutable record remains accessible to anyone, ensuring complete transparency and auditability.
Permissioned vs Permissionless Blockchains: Key Differences
The distinction between permissioned and permissionless blockchains creates fundamental architectural differences affecting every aspect of system design, from transaction processing speed to security models to governance structures. Understanding these differences is critical for organizations evaluating blockchain technology.
| Characteristic | Permissioned Blockchains | Permissionless Blockchains |
|---|---|---|
| Network Access | Restricted to approved participants | Open to anyone with internet access |
| Validator Selection | Chosen by the administrator or the consortium | Any participant can validate transactions |
| Transaction Speed | Fast, typically 1-10 seconds | Variable, typically 10-600 seconds |
| Scalability | High (fewer validators required) | Lower (more nodes = more validation) |
| Energy Consumption | Low to moderate | Very high (especially Proof of Work) |
| Data Privacy | Controlled access to ledger data | Complete transparency to all participants |
| Regulatory Compliance | Easier to implement regulatory controls | Challenging due to anonymity and decentralization |
| Governance | Centralized (administrator or consortium) | Decentralized (community consensus) |
| Censorship Resistance | Low (operator can control transactions) | High (no single entity controls the network) |
| Trust Model | Trust in operator/consortium | Trustless through cryptography |
Real-World Examples of Permissioned Blockchains
Hyperledger Fabric
Developer: The Linux Foundation’s open-source project, widely used by enterprises
Architecture: Modular, permissioned framework with pluggable consensus mechanisms
Key Features: Identity management, role-based access control, private channels for confidential transactions
Enterprise Use: Supply chain tracking, healthcare records, financial settlement networks
JPMorgan Coin
Issuer: JPMorgan Chase, one of the world’s largest investment banks
Purpose: Instant payment settlement between institutional clients on JPMorgan’s private blockchain
Scale: Processes billions in daily interbank transfers, reducing settlement time from days to seconds
Advantage: Bank controls all validators, ensuring regulatory compliance and operational reliability
Corda
Developer: R3, created specifically for enterprise consortiums
Focus: Permissioned blockchain for financial institutions requiring high compliance standards
Participants: Used by major banks, insurance companies, and financial networks globally
Ripple XRP Ledger
Purpose: Cross-border payment network for financial institutions and banks
Consensus: Unique consensus mechanism with designated validator nodes, semi-permissioned model
Adoption: Hundreds of financial institutions use the network for real-time settlement
Real-World Examples of Permissionless Blockchains
Bitcoin
Launch: 2009, the original cryptocurrency and permissionless blockchain
Consensus: Proof of Work requiring computational power to validate transactions
Market Value: Over 600 billion dollars, demonstrating sustained permissionless blockchain adoption
Key Strength: Anyone can run a Bitcoin node and validate transactions without permission or identity verification
Ethereum
Launch: 2015, programmable permissionless blockchain enabling smart contracts
Consensus: Originally Proof of Work, transitioned to Proof of Stake in 2022
Ecosystem: Thousands of decentralized applications, DeFi protocols, and NFT projects built on permissionless infrastructure
Innovation: Demonstrated that permissionless blockchains can support complex applications beyond simple payments
Solana
Innovation: Permissionless blockchain optimized for high throughput and low transaction costs
Performance: Processes thousands of transactions per second while remaining fully permissionless
Consensus: Proof of History combined with Proof of Stake, enabling faster validation
Use Cases: When to Choose Permissioned vs Permissionless
Different blockchain use cases require different architectural choices. The decision between permissioned and permissionless blockchains depends on factors such as privacy requirements, regulatory obligations, scalability, and the level of decentralization needed. Understanding these distinctions helps organizations select the right blockchain model for their specific business and technical objectives.
Permissioned Blockchains Best For:
- Enterprise Supply Chain: Organizations need to track products through distribution networks while maintaining confidentiality and role-based access. Hyperledger Fabric enables suppliers, manufacturers, and retailers to verify product authenticity and provenance without revealing sensitive business data to competitors.
- Financial Settlement: Banks require fast, reliable transaction settlement with regulatory compliance controls. JPMorgan Coin and Corda enable institutions to settle billions daily while maintaining complete audit trails and regulatory reporting capabilities.
- Healthcare Records: Patient data privacy requires restricted access and identity verification. Permissioned blockchains enable healthcare providers to maintain secure medical records shared only with authorized providers and patients.
- Regulatory Compliance: Industries requiring Know Your Customer and Anti-Money Laundering controls benefit from permissioned architectures where identity verification happens at network entry.
Permissionless Blockchains Best For:
- Decentralized Finance (DeFi): Financial protocols must remain accessible to anyone globally without intermediaries or gatekeepers. Permissionless architectures enable lending platforms, decentralized exchanges, and yield farming protocols to serve millions of users without central control.
- Censorship-Resistant Applications: Applications serving politically oppressed regions or addressing controversial topics require permissionless blockchains where no single entity can shut down service or censor transactions.
- Cryptocurrency and Digital Assets: True cryptocurrency systems require permissionless participation where value transfer occurs without central intermediaries. Bitcoin’s success proved the economic demand for censorship-resistant money.
- Web3 and Decentralized Applications: Applications requiring true decentralization and community governance benefit from permissionless models enabling anyone to participate in protocol development and decision-making.
Security Considerations
Permissioned Blockchain Security
Strengths: Permissioned blockchains achieve high security through validator selection, identity verification, and controlled access. Organizations can implement sophisticated security policies, audit mechanisms, and emergency controls. The known validator set enables legal accountability.
Risks: Single points of failure exist if a few validators control the network. Operator compromise could potentially alter transaction history. Insider threats pose risks if approved validators act maliciously. The centralized trust model requires strong organizational governance and security practices.
Permissionless Blockchain Security
Strengths: Permissionless blockchains achieve security through decentralization and economic incentives. An attacker must compromise the majority of validators or miners, requiring enormous computational or financial resources. No single entity can control the network or alter history.
Challenges: Large energy expenditures in Proof of Work systems create environmental concerns. Difficulty adjustments can create security fluctuations during network transitions. User error and exchange security represent significant real-world risks, though not network-level vulnerabilities.
Hybrid and Semi-Permissioned Models
Organizations increasingly recognize that pure permissioned or permissionless models represent extremes on a spectrum. Hybrid architectures combine elements of both to achieve specific objectives.
Semi-Permissioned Blockchains
Characteristics: Semi-permissioned systems like Ripple allow permissionless participation for users but restrict validator selection to known, trusted entities. This model balances decentralization with operational reliability.
Example: Ripple XRP Ledger enables anyone to hold and transfer XRP tokens permissionlessly while maintaining a curated list of validator nodes operated by financial institutions and trusted organizations.
Permissioned Access with Permissionless Validation
Some architectures restrict access to data or transaction submission but allow anyone to validate transactions. This model serves applications requiring controlled participation while maintaining validation decentralization and transparency.
Select the Right Blockchain Architecture for Your Organization
Whether you require enterprise-grade permissioned infrastructure or decentralized permissionless innovation, our blockchain consulting services help organizations evaluate architectural requirements and implement optimal solutions.
Final Take
The choice between permissioned and permissionless blockchains represents one of the most fundamental architectural decisions in blockchain technology. Permissioned blockchains enable enterprises to implement distributed ledger systems with regulatory compliance, operational control, and transaction speed. Permissionless blockchains enable true decentralization, censorship resistance, and trustless systems suitable for financial and social applications requiring no central authority.
Neither architecture is universally superior. The optimal choice depends on specific requirements. Organizations prioritizing speed, compliance, and control should evaluate permissioned solutions like smart contract platforms or consortium networks. Applications requiring decentralization, censorship resistance, and trustless operation need permissionless blockchains. Many organizations are discovering that hybrid models combining elements of both architectures provide an optimal balance.
The blockchain industry continues evolving with improvements addressing historical limitations. Permissionless networks implement scaling solutions to improve throughput and reduce energy consumption. Permissioned networks are adding decentralization features and governance mechanisms. This convergence suggests future systems may blend characteristics once thought to be mutually exclusive.
Frequently Asked Questions
Both offer security through different mechanisms. Permissionless blockchains achieve security through decentralization and economic incentives, making attacks extremely expensive. Permissioned blockchains achieve security through validator selection and identity verification. The better choice depends on threat models specific to your application.
Not typically. Permissioned systems require a central authority or consortium to approve participants. However, decentralization varies. A permissioned network with hundreds of independent validators is more decentralized than a permissionless network where a few mining pools control most hash power.
Enterprises prioritize regulatory compliance, data privacy, transaction speed, and operational control. Permissioned blockchains provide these through identity verification, role-based access controls, optimized consensus mechanisms, and known validator sets with legal accountability.
Permissionless blockchains make regulatory compliance challenging because operators cannot verify user identity or prevent specific transactions. However, applications built on permissionless blockchains can implement compliance layers. Exchanges and custodians typically verify customer identity while interfacing with permissionless systems.
The network operator can remove the malicious validator and potentially recover from the attack through administrative action. This capability distinguishes permissioned systems from permissionless networks, where removing attackers requires network consensus and is much more difficult.
Permissionless blockchains enable participation decentralization, but can suffer centralization in practice. Bitcoin mining concentrates in a few large pools, and Ethereum validators increasingly consolidate in staking providers. However, the absence of permission requirements means decentralization can improve over time through protocol changes and incentive adjustments.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







