Key Takeaways
- A 51% attack occurs when a single entity controls more than half of a blockchain network’s consensus power and gains the ability to manipulate transactions.
- The primary risk of a 51% attack is double-spending, where attackers reverse transactions after receiving goods or services.
- Smaller blockchain networks are significantly more vulnerable because it is cheaper to acquire a majority of hash power or staking control.
- Proof of Stake systems reduce 51% attack risk by requiring attackers to acquire the majority of the token supply, which dramatically increases cost.
- Renting hash power through marketplaces makes many smaller Proof of Work networks vulnerable to low-cost attacks.
- Successful 51% attacks damage not only finances but also reputation, adoption, and long-term network credibility.
- Decentralization is the strongest defense. More independent validators or miners directly increase network security.
Imagine controlling a bank with one simple goal: steal as much money as possible. Now imagine doing it by controlling just over half of the bank’s computers instead of breaking in through the vault. That’s what a 51% attack does to blockchain networks. It’s one of the most fundamental vulnerabilities in decentralized systems, and understanding it is critical for anyone building or investing in blockchain technology.
In May 2018, Bitcoin Gold suffered exactly this fate. Attackers gained control of the majority of the network’s mining power and carried out a $18 million theft through double-spending. In August 2020, Ethereum Classic experienced a similar attack, losing $5.6 million. These were not theoretical attacks in research papers. They were real exploits that devastated actual users and damaged confidence in entire blockchain networks.
The question is not whether 51% attacks can happen. The question is how to prevent them from happening to your blockchain network. This comprehensive guide explains what a 51% attack is, why it’s dangerous, how attackers execute them, and most importantly, the practical strategies you can implement to protect your blockchain from this existential threat.
What is a 51% Attack in Blockchain?
Definition
A 51% attack occurs when a single entity or group controls more than half of a blockchain network’s consensus power through mining in Proof of Work or staking in Proof of Stake. This control allows the attacker to manipulate transaction ordering, block new transactions, and reverse their own recent transactions through double-spending, weakening the network’s security, trust, and decentralization.
The critical insight is that blockchain networks depend on consensus. In decentralized systems, no single authority can impose rules. Instead, the network reaches agreement through a consensus mechanism. If one entity controls more than 50 percent of the network’s power, it can unilaterally impose its version of the truth, effectively breaking the consensus mechanism and destroying the network’s security guarantees.
A 51% attack in blockchain is dangerous because:
- Attackers control transaction validation and can decide which transactions are confirmed or rejected
- The blockchain becomes manipulable, and historical transactions can be rewritten
- Trust collapses as users realize the network cannot guarantee security
- Network value drops as investors flee due to compromised security
Unlike hacking into a single computer, a 51% attack does not steal anyone’s private keys or exploit software bugs. Instead, it exploits the fundamental mathematics of blockchain consensus by demonstrating that whoever controls the majority of network power controls the network itself.
Read Also: What Is Blockchain and How Does Blockchain Technology Work?
The Mechanics of a 51% Attack: How Attackers Execute This Exploit
Understanding exactly how a 51% attack works requires understanding blockchain consensus. Let’s walk through the step-by-step process attackers use to exploit this vulnerability.
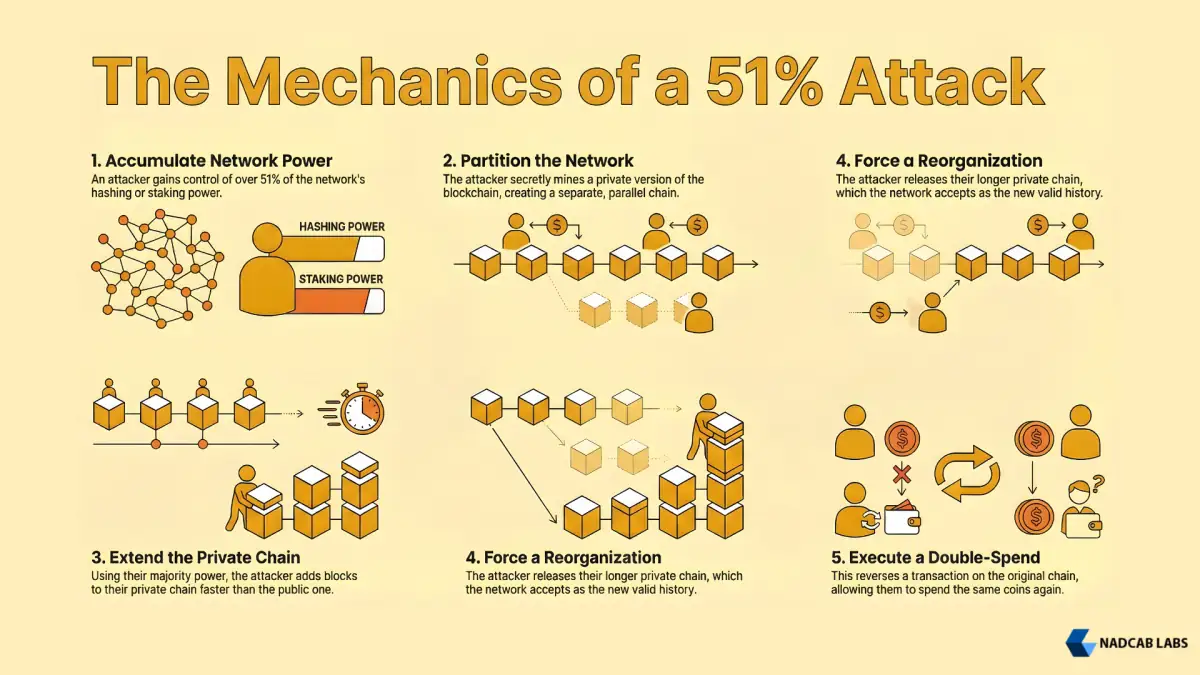
Step 1: Accumulating Network Power
The attacker’s first objective is to gain control of more than 50 percent of the network’s computing or staking power. In Proof of Work systems, this means acquiring mining hardware or gaining control of mining pools. In Proof of Stake systems, this means acquiring and staking the majority of the cryptocurrency.
For Bitcoin, this is prohibitively expensive. According to recent estimates, controlling 51 percent of Bitcoin’s hash rate would require approximately $7.9 billion in ASIC (Application-Specific Integrated Circuit) mining equipment alone, plus millions more in ongoing electricity costs. This economic barrier is precisely why Bitcoin has never suffered a successful 51% attack despite 16 years of operation.
However, smaller blockchains are dramatically more vulnerable. Bitcoin Gold and Ethereum Classic both suffered successful 51% attacks despite having established user bases and significant market capitalization. The difference lies in their hashrate. Smaller networks have fewer miners, making it feasible to rent mining power for hours and conduct attacks.
Step 2: Network Partitioning
Once the attacker has accumulated the majority power, they execute a deliberate network split. The attacker’s miners separate from the main network while maintaining internal communication within their group. The main network continues mining and processing transactions, but the attacker’s group privately mines an alternative version of the blockchain simultaneously.
From the outside, this looks like normal network operation. Other miners have no idea that a hidden blockchain is being mined in parallel with the real one.
Step 3: Accelerated Chain Extension
Because the attacker controls more than 50 percent of total hash power, their private blockchain grows faster than the main network’s blockchain. The attacker’s chain accumulates blocks at a faster rate than the legitimate network.
For example, if the attacker controls 51 percent of hash power and the legitimate network controls 49 percent, the attacker’s chain will grow approximately 51 percent faster. After 10 blocks on the main network, the attacker’s private chain has roughly 10.4 blocks.
After several hours of this separation, the attacker’s private chain becomes longer than the main network’s chain. This is crucial because blockchain consensus rules state that the longest chain is the valid chain.
Step 4: Forced Reorganization
The attacker then broadcasts their longer chain to the network. All nodes follow the consensus protocol rule and switch to the longest chain. The legitimate chain gets orphaned. All transactions that were confirmed on the legitimate network are now reversed and removed from the canonical blockchain.
This means transactions that seemed confirmed are suddenly erased. The cryptocurrency that was transferred in those transactions is no longer transferred. The attackers can now spend the same coins again.
Step 5: Double Spending
With transactions reversed, the attacker can now perform double-spending. They purchase goods or services with cryptocurrency, and while the transaction is processing, they use their majority power to mine their private chain that reverses that transaction. When they broadcast the longer chain, the transaction disappears from the blockchain.
The attacker gets to keep both the goods or services and the cryptocurrency. They have spent the same coins twice.
Real World Examples: 51% Attacks That Actually Happened
The theoretical threat of 51% attacks became a reality multiple times in blockchain history. These real-world examples demonstrate the practical dangers and financial consequences.
Bitcoin Gold (May 2018): $18 Million Double Spend
Bitcoin Gold, a Bitcoin fork launched in 2017, was attacked just one year later. Attackers gained control of the network’s mining power and executed a sophisticated double-spending attack over several weeks.[1]
The attack was only discovered when deposits at cryptocurrency exchange Bitfinex suddenly reversed. The exchange had credited thousands of Bitcoin Gold to an attacker’s account, and when the blockchain was reorganized, the coins disappeared. The attacker simultaneously kept the 1,700+ Bitcoin Gold in their wallet.
Total loss: Approximately $18 million
The attack damaged Bitcoin Gold’s reputation severely. It demonstrated that even established forks of Bitcoin with dedicated development teams and mining infrastructure were vulnerable to well-resourced attacks.
Ethereum Classic (August 2020): $5.6 Million Theft
Ethereum Classic suffered a massive 51% attack in August 2020, more than four years after launch.[2] The attack involved multiple blocks being reorganized, allowing attackers to reverse multiple transactions.
Cryptocurrency exchange Gate.io reported losing approximately $5.6 million in Ethereum Classic to the attackers. The exchange had deposited coins in confidence that the blockchain was secure, but the attack proved otherwise.
Notably, Ethereum Classic suffered repeated 51% attacks in 2020, indicating systematic vulnerability rather than a one-time incident.
Total identified loss: Approximately $5.6 million (though full losses were never fully documented)
Vertcoin (December 2018): $100,000 Attack
Vertcoin, a smaller cryptocurrency focused on being ASIC-resistant, was targeted by attackers who successfully executed a 51% attack. The attacker double-spent approximately 603 Vertcoin, equivalent to roughly $100,000.
This attack demonstrated that even modest-sized attacks ($100,000 in stolen value) were possible against smaller networks.
Horizen (Zen) (May 2018): Hashing Power Disruption
Horizen suffered a 51% attack where attackers took control of the network’s hashing power. Although the full financial impact wasn’t clearly documented, the attack demonstrated ongoing vulnerability across multiple blockchain networks.
The Economics of 51% Attacks: Why They’re Expensive But Not Impossible
A critical question arises: If 51% attacks are so dangerous, why don’t they happen more frequently?
The answer lies in economics. Executing a 51% attack requires substantial resources and carries significant risks.
Hardware Costs
For major blockchains like Bitcoin, acquiring 51 percent of hash power requires hundreds of thousands of specialized ASIC miners. These custom mining chips cost $5,000 to $15,000 each. To control Bitcoin’s network would require billions of dollars in equipment.
For smaller networks, costs are proportionally lower but still substantial. Bitcoin Gold and Ethereum Classic attacks cost hundreds of thousands of dollars in rented hash power.
Electricity Costs
Mining consumes staggering amounts of electricity. Bitcoin mining consumes approximately 120 terawatt hours annually, equivalent to Argentina’s total annual electricity consumption. Running enough mining equipment to control 51 percent of the network for hours would cost tens of thousands of dollars in electricity.
The Cost-Benefit Problem
Here’s the fundamental economic problem for attackers: the cost and effort of executing a 51% attack often exceeds the value they can extract.
For Bitcoin: Attacking the network would cost approximately $8 billion in equipment plus millions in electricity. The attacker could only double-spend their own coins, potentially gaining a few million dollars in value. This is economically irrational.
For smaller networks: The situation is different. Bitcoin Gold can be attacked for hundreds of thousands of dollars, and attackers can extract $18 million in value. This is economically rational and is exactly what happened.
The Renting Option
Specialized services like NiceHash allow attackers to rent hashing power on demand rather than purchasing equipment. This dramatically reduces the cost of attacks against smaller networks.
An attacker could rent 51 percent of Bitcoin Gold’s hashing power for hours, execute the attack, and disappear. The total cost might be just a few hundred thousand dollars, making the $18 million gain economically rational.
For major blockchains, even renting hashing power is prohibitively expensive. Renting 51 percent of Bitcoin’s hash power would cost millions of dollars per hour.
Consequences of Successful 51% Attacks: What Happens When Attacks Succeed
When a 51% attack succeeds, the damage extends far beyond the immediate financial theft.
Double Spending: The Primary Threat
The most direct consequence is double-spending. Attackers spend cryptocurrency, gain whatever goods or services they purchased, then reverse the transaction. They keep both the goods and the coins.
This happened at scale during the Bitcoin Gold attack, where attackers continuously deposited coins at exchanges, withdrew real cryptocurrency in return, then reorganized the blockchain to reverse the deposits.
Network Denial of Service
Attackers with majority power can simply stop confirming blocks from other miners. The network becomes unable to process transactions. Legitimate users cannot send or receive cryptocurrency.
This creates a denial of service attack where the entire network becomes unusable.
Transaction Reversal and Reorganization
Attackers can reverse any past transaction by reorganizing the blockchain. This applies not just to the attacker’s transactions but potentially any transactions they choose to reverse.
A payment you thought was final can be erased. Your coins can be spent even if you didn’t authorize the transaction.
Reputation Damage and Market Collapse
The reputational damage from 51% attacks is often more severe than the immediate financial losses. When users realize the network isn’t secure, they flee.
Bitcoin Gold lost 90 percent of its value in the months following the attack. Ethereum Classic, despite being a top 20 cryptocurrency, has never recovered confidence from its repeated attacks.
New users and investors avoid networks known to be vulnerable. Existing users withdraw their cryptocurrency. The network loses network effects and becomes increasingly worthless.
Preventing 51% Attacks: Practical Strategies for Blockchain Security
Preventing 51% attacks requires multiple complementary strategies. No single approach is perfect, but combined, they significantly reduce vulnerability.
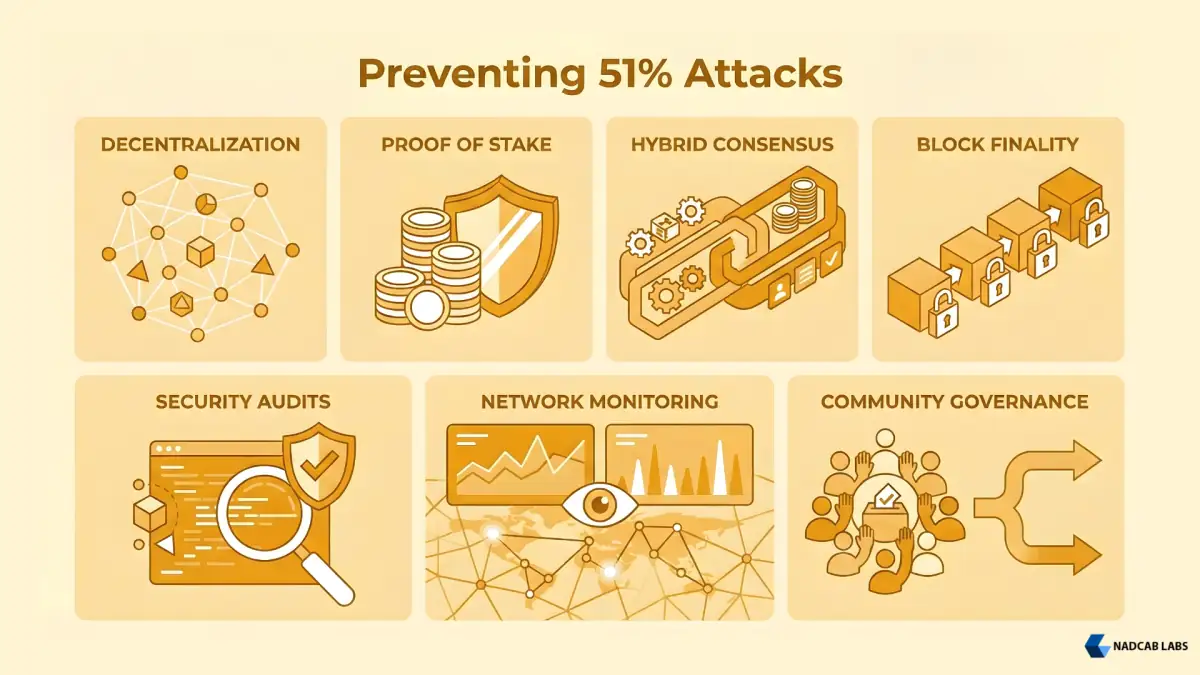
Strategy 1: Increase Network Decentralization
The most direct defense is making it harder for anyone to accumulate 51 percent of network power. This is accomplished by increasing the total number of independent miners and validators.
In Proof of Work systems, encourage more miners to participate by:
- Supporting open source mining software
- Promoting mining pool diversity to prevent pools from becoming too large
- Maintaining an accessible mining difficulty so that diverse participants can compete
- Building community engagement among miners
In Proof of Stake systems, encourage more validators to participate by:
- Making validator setup simple and accessible
- Offering reasonable staking rewards
- Supporting validator infrastructure (node operators, staking services)
- Creating community governance where validators have a voice
Network decentralization is an ongoing process. Bitcoin’s strength comes from thousands of independent miners globally. Ethereum 2.0’s shift to Proof of Stake was partly motivated by making 51 percent attacks more expensive through distributed validation.
Strategy 2: Migrate to Proof of Stake
Switching from Proof of Work to Proof of Stake dramatically increases the cost of 51% attacks.
In Proof of Work, attackers need to acquire and operate expensive mining equipment. In Proof of Stake, attackers need to acquire and stake the majority of the cryptocurrency itself.
For major cryptocurrencies like Ethereum, acquiring 51 percent of all outstanding coins would cost tens of billions of dollars. The attacker would be betting everything on stealing value exceeding their investment, which is economically irrational.
Additionally, Proof of Stake includes slashing mechanisms where validators who misbehave have their staked coins partially or fully confiscated. This creates financial penalties that further deter attacks.
Notable implementation: Ethereum transitioned from Proof of Work to Proof of Stake in September 2022. This transition was motivated partly by security improvements alongside energy efficiency gains. Post-transition, attacking Ethereum through 51% attack would require acquiring tens of billions in ETH, making attacks economically infeasible.
Strategy 3: Implement Hybrid Consensus Mechanisms
Some networks use hybrid approaches combining Proof of Work and Proof of Stake. This leverages the advantages of both systems while mitigating the disadvantages.
For example, a hybrid system might use Proof of Work for block creation and Proof of Stake for finality. Attacking such a system requires controlling the majority power in both mechanisms simultaneously, which is significantly harder than controlling just one.
Strategy 4: Increase Block Finality
Longer finality periods (the time after which transactions cannot be reversed) increase attack difficulty.
If the network requires 100 block confirmations before considering a transaction final, attackers must maintain majority power for the time required to mine 100 blocks on their private chain while staying ahead of the main network. This extended timeline multiplies costs and risks.
Bitcoin’s design implicitly incorporates this strategy. While blocks are created every 10 minutes, users typically wait for 6 to 10 confirmations (60 to 100 minutes) before considering transactions final. This makes 51% attacks harder because attackers must sustain control longer.
Strategy 5: Regular Security Audits and Protocol Hardening
Comprehensive security audits identify potential weaknesses in consensus mechanisms and network design.
Effective audits examine:
- Consensus protocol assumptions and edge cases
- Possible attack vectors not yet discovered
- Network communication security
- Validator incentive alignment
- Economic game theory of the system
Based on audit findings, developers can implement protocol improvements that harden the network against attacks.
Strategy 6: Continuous Network Monitoring
Real-time monitoring detects suspicious activity, indicating potential 51% attacks:
- Unusual increases in hashing or staking power concentrated in a few entities
- Sudden transaction reversions or reorganizations
- Mining pool power concentration changes
- Validator distribution shifts
Early detection enables community response before attacks succeed. In the case of Ethereum Classic attacks, faster detection could have prevented some losses.
Strategy 7: Community Governance and Hard Fork Response
If a 51% attack occurs despite precautions, the community can respond through hard forks. This is the nuclear option, but it works.
When Bitcoin Gold was attacked, the community chose not to fork and accept the losses. Ethereum Classic also didn’t fork despite repeated attacks. However, technically, the community could coordinate a hard fork that invalidates the attacker’s chain and restores the legitimate history.
This requires community consensus and is messy, but it demonstrates that 51% attackers don’t have absolute power in decentralized networks because the community can override even the majority chain if consensus warrants it.
How Professional Blockchain Security Services Protect Networks
Protecting against 51% attacks requires specialized expertise. This is why many organizations partner with blockchain security providers. Professional blockchain security services provide:
- Comprehensive risk assessments identifying 51% attack vulnerability specific to your network
- Consensus mechanism design and optimization to prevent majority control scenarios
- Network architecture recommendations maximizing decentralization
- Security audit implementation examining protocol assumptions and attack vectors
- Continuous monitoring systems detecting suspicious activity patterns
- Incident response planning for attack scenarios
- Community education about network security and proper operational practices
- By hiring blockchain developers and security experts through blockchain development services, organizations ensure their networks benefit from battle-tested security practices and cutting-edge threat detection.
Professional guidance is particularly important for smaller networks vulnerable to rented hash power attacks. Security experts can recommend specific consensus changes, monitoring strategies, and community governance structures that significantly reduce attack feasibility.
Industry Perspective: Expert Insights on 51% Attack Risks
Leading blockchain security researchers consistently emphasize 51% attacks as a primary design concern.
Dr. Stuart Haber, Blockchain Researcher: “51% attacks represent the fundamental trade-off between decentralization and security. As networks grow more distributed, attacks become exponentially more expensive. The security of major networks like Bitcoin comes not from immunity to 51% attacks, but from economic infeasibility, making attacks irrational.”
Analysis from Chainalysis (2023): “Smaller blockchains remain vulnerable despite established markets. However, the shift toward Proof of Stake consensus and hybrid mechanisms is dramatically improving security. Networks post-Ethereum 2.0 transition represent fundamentally different attack economics compared to pure Proof of Work systems.”
The consensus among security experts is clear: 51% attacks remain possible but can be effectively mitigated through deliberate design choices and community focus on decentralization.
Conclusion
51% attacks represent the most fundamental security threat to blockchain networks. They exploit the core principle that blockchain security rests on majority consensus, asking the question: What happens if the majority is actually hostile?
The answer is devastating. Bitcoin Gold lost $18 million. Ethereum Classic suffered repeated attacks, damaging its reputation and market value. Smaller networks continue to remain vulnerable despite the high-profile attacks, creating opportunities for attackers.
The key insight is that 51% attacks exploit economics, not cryptography. Making attacks economically irrational through proper network design is the most effective prevention strategy.
Whether you’re building a new blockchain, securing an existing network, or evaluating blockchain platforms for adoption, understanding 51% attacks is critical. The difference between a secure network and a vulnerable one often comes down to architectural decisions made during design.
For organizations implementing blockchain solutions, professional guidance is essential. Blockchain development firms and blockchain developers with security expertise can help design networks that are inherently resistant to 51% attacks while maintaining the decentralization and transparency that make blockchain valuable.
The future of blockchain security depends on learning from past attacks and implementing the defense strategies detailed in this guide. Bitcoin’s 16-year attack-free record demonstrates that well-designed networks with strong security fundamentals can resist even well-resourced attackers.
FAQs: Common Questions About 51% Attacks
A 51% attack occurs when a single entity or coordinated group controls more than half of a blockchain network’s consensus power, either through hash rate in Proof of Work or staked tokens in Proof of Stake. This level of control allows the attacker to influence block creation, delay or censor transactions, and reverse their own recent transactions through double-spending. Such attacks weaken decentralization, disrupt transaction finality, and reduce trust in the network, with smaller blockchain networks being more vulnerable to this risk.
The “51” refers to 51 percent majority control. “Attack” refers to using this majority power to maliciously manipulate the network. The attack works because blockchain consensus depends on majority agreement. Whoever controls the majority can unilaterally decide what is valid.
A successful 51% attack destroys the fundamental security of blockchain networks. It allows attackers to:
- Double-spend the same coins multiple times
- Reverse transactions that were considered final
- Prevent legitimate transactions from confirming
- Damage reputation, causing network value collapse
Unlike traditional cyberattacks that exploit software bugs, 51% attacks exploit the fundamental mathematics of consensus.
Proof of Stake makes 51% attacks more expensive and difficult than Proof of Work. Instead of acquiring mining equipment, attackers must acquire and stake the majority of the cryptocurrency itself. For major networks, this is prohibitively expensive.
However, Proof of Stake is not immune to 51% attacks. Attackers with sufficient cryptocurrency could theoretically stake and attack. The difference is the economic barrier is much higher, and penalty systems (slashing) deter attackers more effectively.
Immediate response steps:
- Alert the community immediately so users are aware
- Investigate the extent and its impact
- Evaluate community consensus on response (hard fork vs. acceptance)
- If a hard fork is chosen, coordinate the community response
- Implement additional security measures to prevent recurrence
- Communicate transparently with users and investors
Professional support from blockchain security consultants and blockchain development companies is critical for coordinating effective responses to active attacks.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.






