Key Takeaways
- Different blockchain types (public, private, consortium, and hybrid) solve different business problems, so choosing the right architecture is more important than choosing the most popular one.
- Public blockchains offer maximum transparency and decentralization but face scalability and cost challenges, making them ideal for open ecosystems like crypto and DeFi.
- Private and consortium blockchains provide better performance, privacy, and governance, which makes them more suitable for enterprises, financial institutions, and regulated industries.
- Hybrid blockchains deliver flexibility by allowing organizations to keep sensitive data private while still benefiting from public verification and trust.
- Permissioned vs permissionless design directly impacts security, governance, scalability, and compliance, so this decision should align with your regulatory and operational needs.
- A successful blockchain implementation depends on aligning technology choices with business goals, performance requirements, and long-term scalability rather than following trends.
Blockchain technology has revolutionized how organizations manage data, verify transactions, and build trust across networks. However, not all blockchains work the same way. Understanding the different types of blockchain is essential for choosing the right solution for your business needs.
Understanding Blockchain Fundamentals
At its core, blockchain is a distributed ledger technology that records transactions across multiple computers (called nodes) in a network. Unlike traditional centralized databases maintained by a single authority, a blockchain ledger is replicated across all network participants, creating transparency and redundancy. Each participant holds an identical copy of the ledger, and new transactions are added to blocks that are cryptographically linked to previous blocks, forming an immutable chain. This decentralized approach eliminates the need for a central intermediary, allowing direct peer-to-peer transactions while maintaining security and data integrity.
The fundamental components of blockchain technology include consensus mechanisms, cryptographic hashing, smart contracts, and network nodes. Consensus mechanisms are protocols that allow distributed nodes to agree on the validity of transactions without trusting a central authority. Cryptographic hashing ensures data integrity by converting transaction data into unique digital fingerprints that cannot be altered without detection. These components work together to create a trustless environment where participants can transact confidently, knowing that the technology itself guarantees accuracy and prevents fraud. To gain a deeper understanding of these blockchain components, it is recommended to first obtain a comprehensive overview of blockchain technology.
What Are the Different Types of Blockchain?
Blockchain Types
The four main types of blockchain networks are public, private, consortium, and hybrid. Each type serves distinct purposes and addresses specific organizational challenges. The choice between them depends on your requirements for decentralization, privacy, scalability, and control.
The fundamental difference between these blockchain types lies in how they balance three key factors: access control, transparency, and governance structure. Public blockchains prioritize openness and decentralization, while private blockchains emphasize control and privacy. Consortium and hybrid blockchains offer middle-ground solutions for collaborative environments that need selective transparency.
Public Blockchain: Open and Decentralized
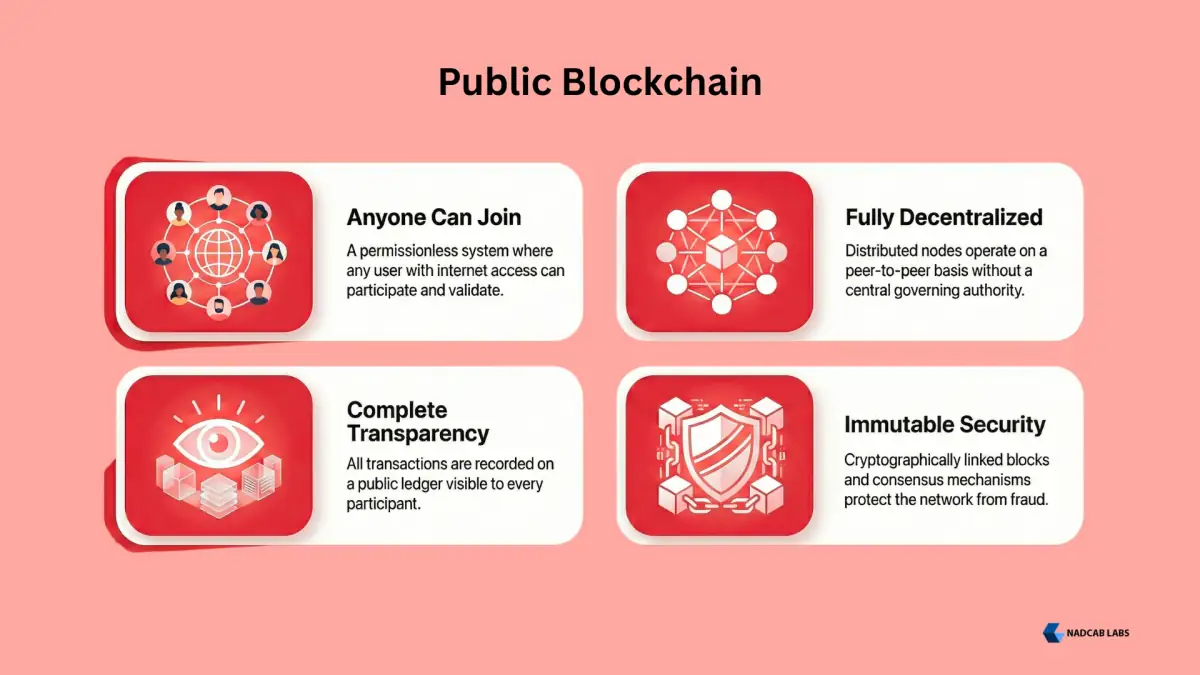
A public blockchain is an open network where anyone with an internet connection can join, validate transactions, and view the complete ledger. No central authority controls access or decides who can participate.
Key Characteristics:
Public blockchains operate on these principles:
- Permissionless Access: Anyone can become a network node without requiring approval
- Complete Transparency: All transactions are visible to every participant
- Decentralized Governance: Consensus mechanisms like Proof of Work or Proof of Stake secure the network
- Immutable Records: Once transactions are recorded, they cannot be altered
- Pseudonymous Participation: Users are identified by wallet addresses rather than personal information
Advantages of Public Blockchains:
- High security due to widespread node distribution
- Complete transparency fosters accountability
- Resistance to censorship and external control
- Trustless environment where participants don’t need to know each other
- Strong cryptographic protection against fraud
Disadvantages of Public Blockchains:
- Slower transaction processing due to consensus requirements
- Higher energy consumption, especially with Proof of Work
- Limited scalability as the network size grows
- Variable transaction fees during peak demand
- Less suitable for confidential business data
Real-World Examples:
Bitcoin and Ethereum are the most prominent public blockchains. Bitcoin pioneered the concept with Proof of Work consensus, while Ethereum introduced smart contracts and later transitioned to Proof of Stake, significantly reducing energy consumption.
Use Cases:
Public blockchains excel in cryptocurrency exchanges, decentralized finance applications, digital asset trading, supply chain tracking, and crowdfunding platforms where openness and trustlessness are essential.
Private Blockchains
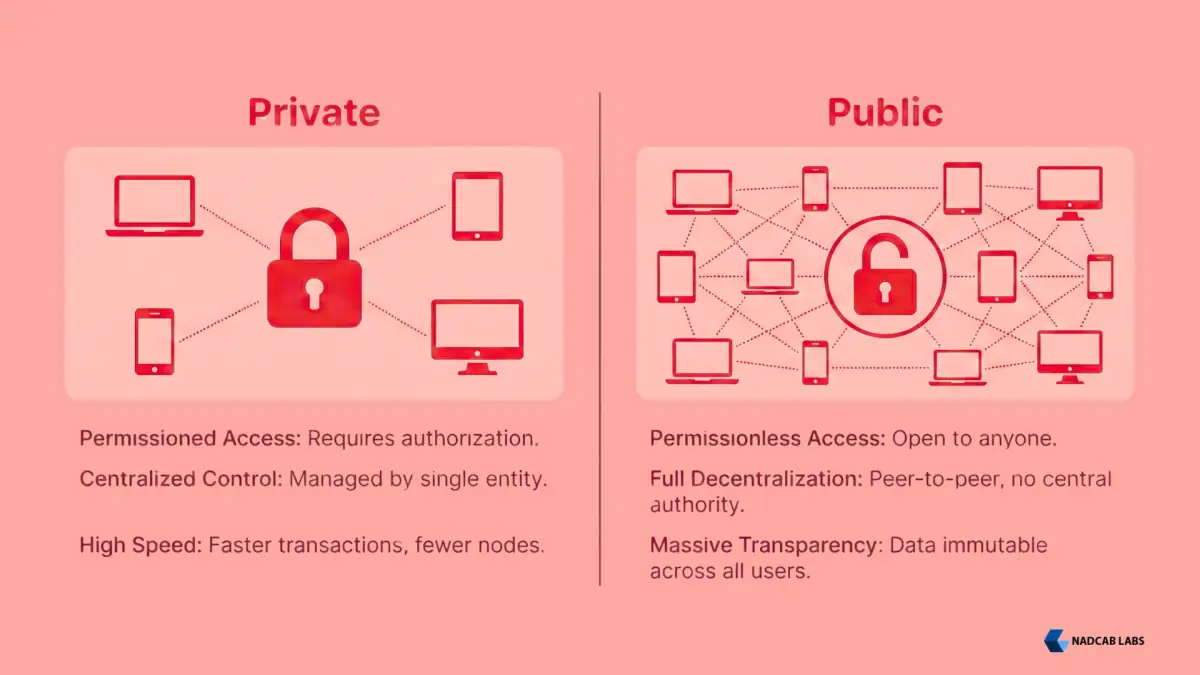
A private blockchain restricts access to authorized participants only. A single organization or consortium controls the network and determines who can join, validate transactions, and access data.
Key Characteristics:
- Permissioned Access: Only vetted participants can join the network
- Restricted Transparency: Data visibility limited to authorized members
- Centralized Governance: Usually managed by one organization or entity
- Faster Transactions: Fewer nodes simplify consensus requirements
- Enhanced Privacy: Sensitive information remains confidential
Advantages of Private Blockchains:
- Fast transaction processing with minimal participants
- Lower operational costs compared to public networks
- Complete control over network rules and policies
- Enhanced privacy for sensitive business information
- Easy regulatory compliance management
Disadvantages of Private Blockchains:
- Reduced security due to centralized control
- Higher risk of fraud and data manipulation
- Limited decentralization defeats blockchain’s core principle
- Fewer nodes create single points of failure
- Requires trust in the controlling organization
Real-World Examples:
Hyperledger Fabric and Corda are enterprise-grade private blockchain platforms used by financial institutions and corporations for internal processes and inter-organizational collaboration.
Use Cases:
Private blockchains work well for internal auditing, employee voting systems, supply chain management within organizations, intellectual property management, and financial record keeping, where confidentiality is paramount.
Build Scalable Blockchain Solutions with Experts
From smart contracts to enterprise-grade Web3 platforms, our blockchain development team helps businesses create secure, high-performance, and future-ready blockchain products.
Consortium Blockchains
A consortium blockchain, also called a federated blockchain, is governed by multiple organizations working together. Unlike private blockchains controlled by one entity, consortium networks distribute control among members while maintaining restricted access.
Key Characteristics:
- Multi-Party Governance: Multiple organizations share control decisions
- Semi-Decentralized Structure: Decentralization exists at the organizational level, not the individual level
- Selective Transparency: Data visible to consortium members only
- Faster Processing: Limited participants enable quick consensus
- Balanced Privacy and Collaboration: Information shared securely among partners
Advantages of Consortium Blockchains:
- Improved trust through shared governance
- Faster transactions than public blockchains
- Scalability for multi-organization networks
- Clear data sharing boundaries
- Reduced costs through shared infrastructure
Disadvantages of Consortium Blockchains:
- Complex governance requirements across organizations
- Risk of collusion among members
- Compromise becomes necessary for consensus
- Less decentralization than public blockchains
- Higher setup and maintenance costs
Real-World Examples:
R3’s Corda and Tendermint power consortium solutions in banking, supply chain, and insurance industries, where multiple organizations need coordinated solutions.
Use Cases:
Consortium blockchains benefit supply chain collaborations across multiple companies, banking consortiums processing shared transactions, healthcare data sharing among providers, and insurance claim verification across industry partners.
Hybrid Blockchain: Best of Both Worlds
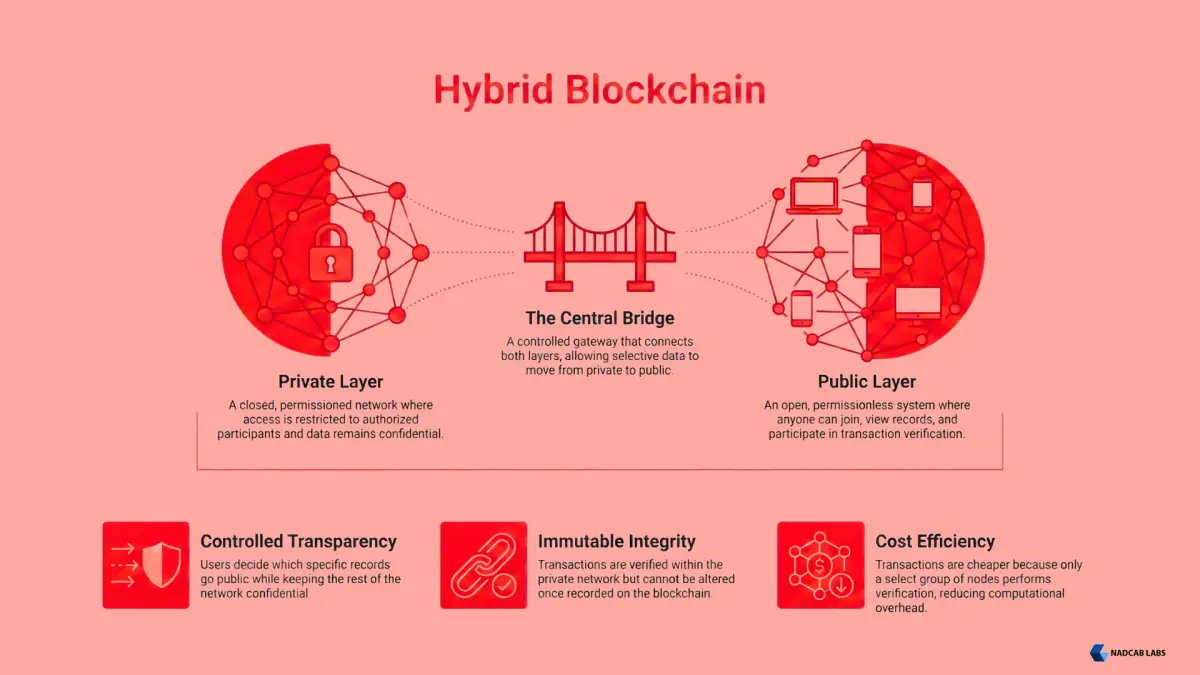
A hybrid blockchain combines features of public and private blockchains. Organizations control which data remains private and which becomes publicly verifiable, creating a flexible solution for regulated industries.
Key Characteristics:
- Selective Accessibility: Some functions are public, others private
- Customizable Privacy: Control over data exposure
- Smart Contract Protection: Transactions cannot be altered by the controlling organization
- Flexible Governance: Rules adapt to specific needs
- Audit Trail: Public verification of selected transactions
Advantages of Hybrid Blockchains:
- Flexibility for diverse requirements
- Strong security combining both models
- Regulatory compliance easier to achieve
- Transparency where needed, privacy where required
- Scalability and efficiency improvements
Disadvantages of Hybrid Blockchains:
- Complex management and maintenance
- Potential transparency gaps
- Implementation challenges
- Inconsistent user experience
- Higher development costs
Real-World Examples:
Ripple network and IBM’s blockchain solutions demonstrate hybrid approaches, enabling financial institutions to balance transparency with privacy needs.
Comparing Blockchain Types: Feature Analysis
Here’s how the four blockchain types compare across critical dimensions
| Feature | Public | Private | Consortium | Hybrid |
|---|---|---|---|---|
| Access Control | Open to all | Restricted access | Member-only | Selective |
| Decentralization | Fully decentralized | Centralized | Semi-decentralized | Partial |
| Transparency | Complete | Limited | Restricted to members | Customizable |
| Transaction Speed | Slower | Fast | Fast | Moderate to fast |
| Security | High (decentralized) | Lower (centralized) | Variable | High (layered) |
| Scalability | Limited | High | High | Moderate to high |
| Privacy | Pseudonymous | Strong | Strong | Strong |
| Governance | Community | Single entity | Collaborative | Organization-controlled |
| Energy Use | High (PoW) | Low | Low | Low to moderate |
| Use Cases | Crypto, DeFi | Enterprise | Financial networks | Regulated industries |
Choosing the Right Blockchain Type
Selecting the appropriate blockchain depends on answering these critical questions:
- Who controls the network? Choose public for decentralization or private for central control.
- How important is transparency? Public blockchains maximize transparency, while private networks maintain confidentiality.
- What are your performance needs? Private and consortium blockchains process faster than public ones.
- What regulatory requirements exist? Hybrid and private blockchains make compliance easier.
- How many organizations participate? Consortium blockchains suit multi-party scenarios.
- What’s your budget? Public blockchains incur transaction fees but no infrastructure costs. Private blockchains require infrastructure investment.
Permissioned vs Permissionless: The Fundamental Distinction
Beyond these four types, blockchain networks divide into permissioned and permissionless categories based on access control.
Permissionless blockchains allow anyone to participate without permission. Bitcoin and Ethereum are permissionless networks where any node can join and validate transactions.
Permissioned blockchains require authorization from network administrators. Participants must obtain explicit approval before joining, viewing data, or validating transactions. Private blockchains are typically permissioned, as are many consortium networks.
This distinction fundamentally affects governance, security, and scalability characteristics. Permissionless systems offer censorship resistance but sacrifice privacy. Permissioned systems enable privacy and control but require trust in administrators.
Blockchain Solutions for Your Business
Whether you need enhanced security through decentralization or controlled efficiency through private networks, blockchain technology offers tailored solutions.
For organizations considering blockchain implementation, we provide comprehensive guidance through our services:
- Learn about blockchain development services for building custom blockchain solutions
- Explore Layer 1 Blockchain Development Services for foundational network creation
- Understand Layer 2 Rollups for scaling existing networks
- Consider Modular Blockchain architectures for flexibility
- Discover private blockchain services for confidential enterprise applications
Conclusion
The type of blockchain you select fundamentally shapes your system’s security, speed, privacy, and scalability characteristics. Public blockchains prioritize decentralization and transparency for applications requiring trust among strangers. Private blockchains provide control and efficiency for internal organizational use. Consortium blockchains enable multi-party collaboration while maintaining governance balance. Hybrid blockchains offer flexibility for regulated industries needing selective transparency.
Each blockchain type represents a distinct approach to solving data management challenges. The most successful blockchain implementations match the network type precisely to organizational requirements, ensuring optimal performance, security, and compliance for long-term success.
Understanding these differences empowers you to make informed decisions about blockchain technology adoption and implementation in your organization.
Frequently Asked Questions
Private, consortium, and hybrid blockchains are generally best suited for enterprise use cases because they offer better privacy, faster performance, and stronger governance control. Businesses handling sensitive data often prefer private networks where access is restricted. Companies looking to implement such solutions typically rely on private blockchain services and custom blockchain development services to build tailored architectures.
The four main types are public (open and decentralized), private (controlled and confidential), consortium (multi-organization governed), and hybrid (combining public and private features). Each serves different organizational needs.
A business should choose custom blockchain development when it needs specific features like custom governance rules, enhanced privacy, regulatory compliance, or performance optimization. Public blockchains like Ethereum may not always meet enterprise requirements, which is why many organizations invest in custom blockchain development services to design networks aligned with their exact operational goals.
Public blockchains offer the highest security due to widespread node distribution and decentralized consensus. The more nodes validating transactions, the harder it becomes for attackers to manipulate data.
A private blockchain is a permissioned network controlled by one organization. It allows faster transactions, more privacy, and better regulatory compliance but sacrifices decentralization and transparency compared to public blockchains.
Permissionless blockchains allow anyone to participate without approval, while permissioned blockchains restrict access to authorized participants only. This affects decentralization, privacy, and control.
Public blockchains are generally the most secure due to decentralization and cryptography. The larger the network of validators, the harder it is for attackers to manipulate transactions, making public blockchains highly resistant to tampering.
Hybrid blockchains allow organizations to choose which data stays private and which becomes publicly verifiable. Some transactions occur privately while others can be audited publicly.
These refer to blockchain layers: L1 is the base protocol (Bitcoin, Ethereum), L2 solutions improve scaling (Lightning Network), and L3 adds additional functionality. L2 is generally faster than L1, and L3 provides specialized services on top of L2.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.