Key Takeaways
- Quorum is a permissioned blockchain built on Ethereum, designed specifically for enterprise use where data privacy and access control are non-negotiable.
- Private transactions in Quorum allow sensitive business data to stay visible only to authorized participants, while the blockchain still maintains an immutable audit trail.
- Its permissioned network model means only verified organizations can join, significantly reducing the risk of unauthorized data exposure.
- Quorum uses advanced cryptographic techniques and a dedicated transaction manager (Tessera) to encrypt data both at rest and during transmission.
- Customizable privacy settings give businesses the flexibility to define exactly who can see what, making it adaptable across industries like finance, healthcare, and supply chain.
- Nadcab Labs, with over 8 years of hands-on blockchain experience, specializes in deploying Quorum-based solutions that meet real-world enterprise privacy requirements.
When businesses move to blockchain, one of the first questions that comes up is privacy. Public blockchains like Ethereum offer transparency and decentralization, but that openness creates a problem for companies handling sensitive data. Financial records, patient health information, supply chain contracts, and government documents cannot sit on a ledger where anyone can read them. That is the gap Quorum was built to fill.
Quorum is an enterprise-grade blockchain platform originally developed by JPMorgan Chase. It takes the core technology of Ethereum and wraps it with a privacy layer that allows organizations to run confidential transactions on a shared network. Think of it this way: you get the trust and immutability of a blockchain, but without exposing private business data to every participant on the network.
Over the past few years, enterprise blockchain adoption has picked up across sectors. Banks use it for cross-border payments. Hospitals use it to share patient data securely. Manufacturers use it to track components across global supply chains. In all these cases, the common thread is a need for privacy, and that is exactly what Quorum delivers. If you are exploring how blockchain fits into your business, working with a blockchain company that understands these privacy layers can make a significant difference in how smoothly the adoption goes.
This article breaks down the specific ways Quorum handles privacy in blockchain transactions. We will look at the mechanisms, how they work together, and why they matter for businesses operating in regulated industries.
Why Privacy Is the Biggest Challenge in Enterprise Blockchain
Public blockchains operate on a simple principle: everyone sees everything. Every transaction, every wallet balance, every smart contract interaction is visible on the ledger. For cryptocurrency trading or open-source projects, that level of transparency works fine. But for businesses, it is a deal-breaker.
Consider a bank processing a loan. The borrower’s financial details, credit checks, and loan terms cannot be visible to every node on the network. Or think about a pharmaceutical company sharing clinical trial data with a regulator. That data is subject to strict laws like HIPAA and GDPR. Putting it on a public ledger would violate those regulations on day one.
This is not just a theoretical concern. A 2023 report by Deloitte found that over 60% of enterprises cited data privacy as the primary barrier to blockchain adoption. The technology itself was not the problem. The privacy model was.
Quorum was built from the ground up to address this specific challenge. It does not try to retrofit privacy onto a public blockchain. Instead, it redesigns the architecture so that privacy is baked into every layer, from how transactions are processed to how smart contracts execute and how nodes communicate with each other.
Also Read: Enterprise Blockchain Applications Guide
Top Ways Quorum Improves Privacy in Blockchain Transactions
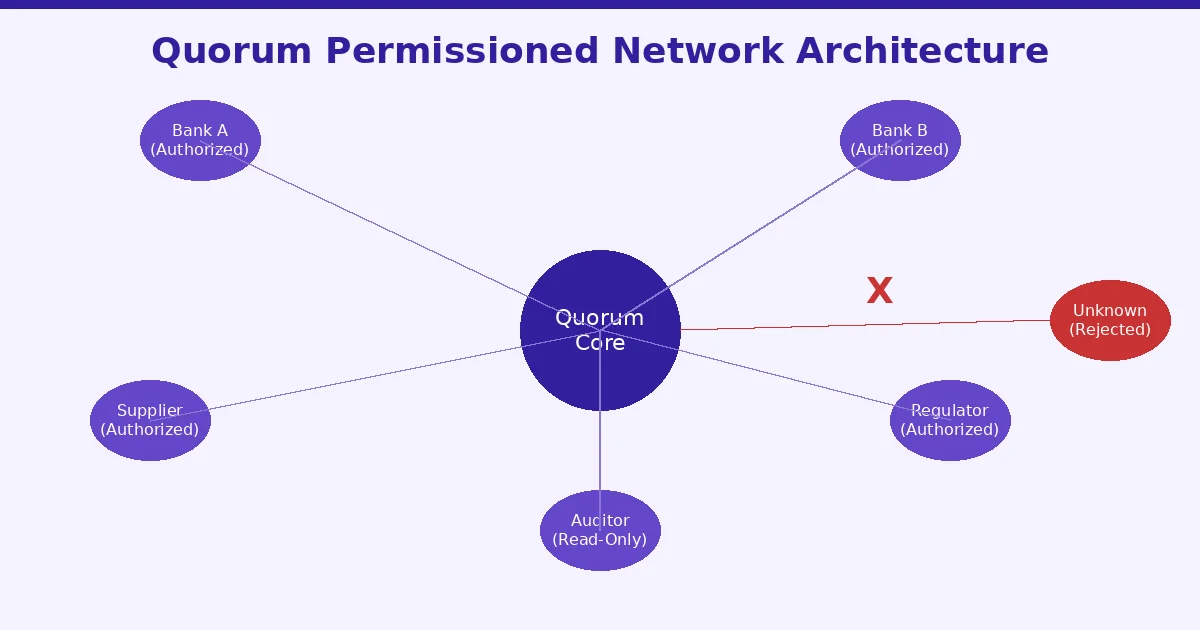
Quorum does not rely on a single trick to protect data. It uses a layered approach where multiple privacy mechanisms work together. Below, we walk through each one and explain how it functions in practice.
1. Private Transactions
This is the feature that gets the most attention, and for good reason. In Quorum, you can mark a transaction as “private” when you send it. When you do this, the actual transaction data (the payload) gets encrypted and sent only to the participants you specify. Everyone else on the network sees that a transaction happened, but they cannot see what was in it.
Here is how it works in practice. Say Company A is sending a payment to Company B on a Quorum network that also includes Company C and Company D. When Company A marks the transaction as private and lists only Company B as a recipient, Companies C and D will see a hash of the transaction on the public state trie. But the actual details, the amount, the contract terms, the business logic, remain invisible to them.
The system that makes this possible is called Tessera (formerly known as Constellation). Tessera is a standalone privacy manager that handles the encryption, distribution, and storage of private transaction data. It runs alongside each Quorum node and communicates only with the Tessera instances of authorized participants. This separation of concerns is important because it means the privacy layer does not slow down the main blockchain processing.
For industries like trade finance, where multiple banks might share a network but individual deal terms must stay confidential, this feature is not just helpful. It is essential. If you are looking into how state channels in blockchain compare to Quorum’s private transactions for off-chain privacy, the key difference is that Quorum keeps everything on-chain but encrypted, while state channels move interactions off-chain entirely.
2. Private Contract Data
Private transactions protect the data you send. Private contract data goes a step further and protects the business logic itself. In Quorum, smart contracts can be deployed as private contracts, meaning the code, the state, and the execution results are only visible to the specified participants.
This matters more than people realize. On a public blockchain, anyone can read a smart contract, reverse-engineer the logic, and figure out the business rules encoded in it. For enterprises, those business rules often represent proprietary processes, pricing algorithms, or compliance workflows. Exposing them would be like publishing your internal operating procedures on the internet.
When you deploy a private contract on Quorum, the contract bytecode is encrypted and distributed through Tessera, just like a private transaction. The contract’s state is maintained separately on each authorized node. Unauthorized nodes do not even know the contract exists in any meaningful way. They have no access to the code, the state, or the execution history.
A good example of this in action is insurance. An insurer and a reinsurer might have a smart contract that automatically calculates claim payoffs based on certain triggers. The formula used for those calculations is proprietary. With Quorum’s private contract feature, that formula stays between the two parties, even though they share the network with dozens of other organizations. Understanding the basics of smart contract testing on blockchain security can help teams ensure these private contracts work correctly before deployment.
3. Permissioned Network
Quorum runs as a permissioned blockchain. That means you cannot just download the software, spin up a node, and join the network. Every participant must be approved before they can connect. This is the first and most fundamental layer of privacy because it controls who is even in the room.
Quorum’s permissioning model operates at multiple levels. At the network level, a node must be whitelisted to connect. At the organization level, permissions define what each entity can do, whether they can create contracts, send transactions, or only read data. At the account level, individual users within an organization can have their own set of permissions.
This three-tier structure gives network administrators fine-grained control. A regulator, for instance, might have read access to all transactions for auditing purposes but no ability to initiate new transactions. A supplier in a supply chain network might only see data related to their shipments. This layered approach to access control is similar in philosophy to how DPoS in blockchain systems manage validator participation, though Quorum applies the concept more broadly to data visibility.
The benefit of a permissioned network is not just privacy. It also simplifies compliance. When you know exactly who is on your network, it becomes much easier to meet KYC (Know Your Customer) and AML (Anti-Money Laundering) requirements. Regulators can be given their own node with appropriate access levels, making audits straightforward.
Quorum vs Public Blockchain: Privacy Comparison
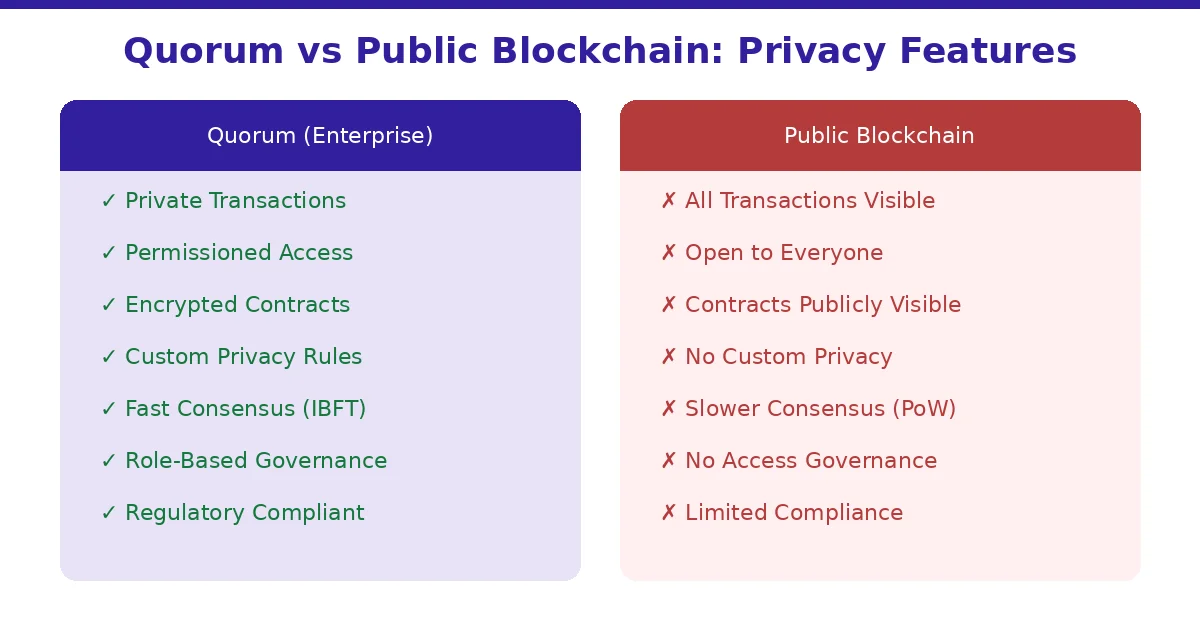
| Feature | Quorum (Permissioned) | Public Blockchain |
|---|---|---|
| Transaction Visibility | Only authorized parties see details | All participants see all transactions |
| Network Access | Invitation and approval required | Open to anyone |
| Smart Contract Privacy | Contract code and state can be private | All contracts publicly readable |
| Consensus Speed | Fast (IBFT, Raft) with seconds finality | Slower (PoW/PoS) with minutes to finality |
| Regulatory Compliance | Built-in KYC/AML support | Pseudonymous, hard to enforce |
| Data Encryption | End-to-end via Tessera | Data stored in plaintext on-chain |
| Governance | Role-based, customizable | Community-driven, no access controls |
4. Advanced Cryptographic Techniques
Beyond the architectural privacy features, Quorum uses strong cryptography to protect data at every stage. The encryption is not an add-on or optional module. It is woven into how data moves through the network.
When a private transaction is created, the payload is encrypted using symmetric key encryption. The symmetric key itself is then encrypted with the public keys of the specified recipients. This dual-layer approach means that even if someone intercepts the data in transit, they cannot decrypt it without the correct private key. The system follows a standard cryptographic pattern called envelope encryption, which is the same approach used by major cloud providers for data security.
Tessera, the privacy manager, handles all of this automatically. It maintains each node’s key pairs, manages the encryption and decryption process, and stores encrypted payloads locally. The communication between Tessera instances happens over TLS (Transport Layer Security), adding another layer of encryption during data transmission.
For organizations dealing with highly sensitive data, this is not just about meeting a checkbox on a compliance form. It is about making sure that if any part of the infrastructure is compromised, the data remains protected. The concept is similar to how node synchronization in blockchain ensures data consistency, but here the focus is on maintaining confidentiality during that synchronization process.
5. Customizable Privacy Settings
One of the things that sets Quorum apart from other enterprise blockchains is how flexible its privacy settings are. Different businesses have different privacy needs, and Quorum lets you configure the system to match your specific requirements.
At the transaction level, you choose which participants can see each transaction. At the contract level, you define who can interact with a smart contract and what functions they can call. At the network level, you control which organizations can join and what roles they play. This granularity is unusual in blockchain platforms and is one of the reasons Quorum has gained traction in heavily regulated industries.
For example, in a multi-bank settlement network, Bank A might want to share transaction details with Bank B for a specific deal, while keeping those details hidden from Banks C, D, and E who are also on the network. With Quorum, this is straightforward. You specify the recipients when you submit the transaction, and the privacy manager handles the rest. No changes to the network configuration are needed.
This level of customization also extends to how data is stored and retained. Organizations can configure their Tessera instances to enforce data retention policies, automatically purging encrypted payloads after a specified period. This helps with regulatory requirements like the GDPR’s “right to be forgotten” provisions.
6. Transaction Privacy Management
Transaction privacy management in Quorum is not just about hiding data. It is about giving businesses tools to control exactly how privacy is applied, monitored, and audited across the network.
Quorum provides APIs that allow applications to manage privacy settings programmatically. This means privacy controls can be integrated directly into business workflows. An ERP system, for instance, can automatically set the correct privacy parameters when generating a purchase order, without requiring manual intervention from the user.
The platform also supports what is called “privacy marker transactions.” These are public transactions that serve as pointers to private transactions. They allow the network to maintain a consistent ordering of transactions (both public and private) while keeping private data confidential. This is a clever solution to a hard problem in distributed systems: how do you maintain consensus on a shared ledger when not everyone can see all the data?
For audit and compliance purposes, authorized auditors can be given access to specific private transactions after the fact. This means a company can operate with full privacy during normal business operations but still provide regulators with the access they need during an audit. It is a practical balance between privacy and accountability. Businesses working with decentralized identifiers will find that Quorum’s privacy management layer integrates well with identity verification systems.
How a Private Transaction Moves Through Quorum: The Full Lifecycle
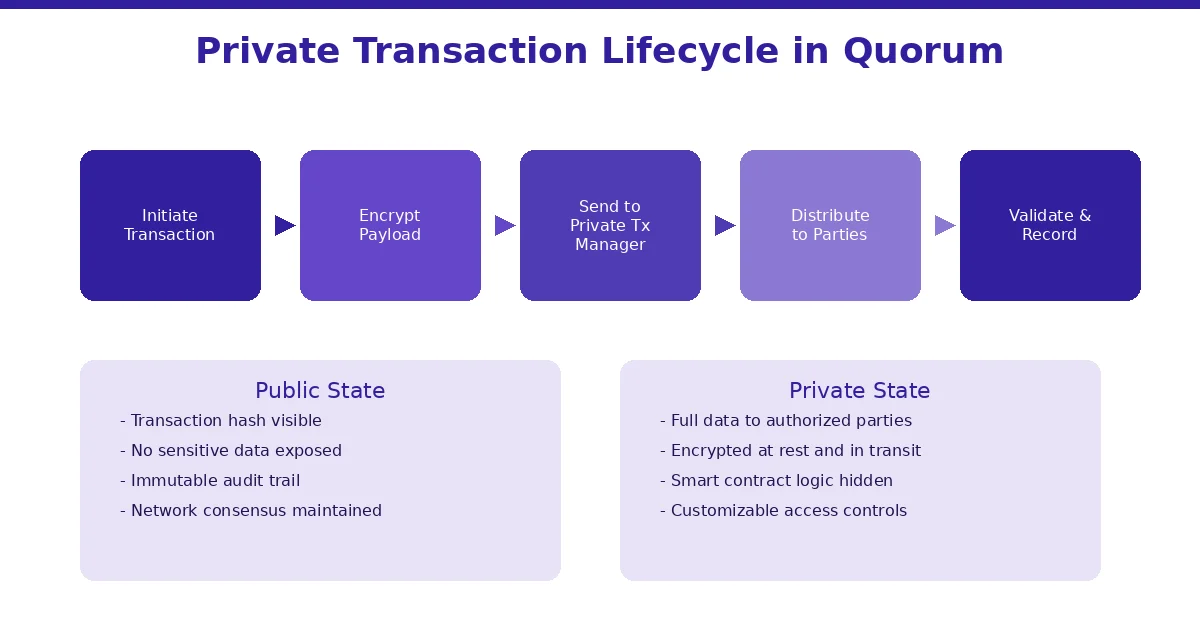
Understanding the lifecycle of a private transaction helps clarify how all these privacy features work together in practice. Here is what happens step by step when a private transaction is submitted on a Quorum network:
1Transaction Creation: The sending application creates a transaction and marks it as private, specifying the list of recipient public keys.
2Payload Encryption: The Quorum node sends the transaction payload to its local Tessera instance. Tessera encrypts the payload using a symmetric key and then encrypts that key for each specified recipient.
3Distribution: Tessera sends the encrypted payload and encrypted keys to the Tessera instances of the specified recipients over TLS-secured connections.
4Hash Replacement: The original transaction payload on the Quorum node is replaced with a hash of the encrypted payload. This hash is what gets submitted to the blockchain.
5Consensus: The network reaches consensus on the transaction, including the hash. All nodes agree on the order and validity of transactions, but non-participants only see the hash.
6Execution: Authorized nodes decrypt the payload using their private keys, retrieve the original transaction data, and execute it. The resulting state changes are stored privately on their nodes.
7Verification: The private state is maintained separately from the public state. Both states are valid, but the private state is only accessible to authorized participants.
This lifecycle shows why Quorum’s approach to privacy is considered robust. The actual sensitive data never touches the public ledger. What sits on the blockchain is a cryptographic hash that proves the transaction existed and was agreed upon, but reveals nothing about its contents. The approach is conceptually related to how Plasma in blockchain handles off-chain computation, but Quorum keeps the privacy management tightly integrated with the main chain rather than creating separate child chains.
Quorum Privacy Features: Detailed Breakdown
| Privacy Feature | What It Does | Best For | Technical Component |
|---|---|---|---|
| Private Transactions | Encrypts transaction data so only specified parties can read it | Financial settlements, trade finance | Tessera (Privacy Manager) |
| Private Contracts | Hides smart contract code and state from unauthorized nodes | Insurance, proprietary business logic | Private State Trie |
| Permissioned Access | Restricts who can join the network and what they can do | Regulated industries, multi-party consortiums | Enhanced Permissions Model |
| Envelope Encryption | Dual-layer encryption for payloads and keys | High-security environments, government | NaCl / libsodium cryptography |
| Custom Privacy Rules | Lets organizations define per-transaction and per-contract visibility | Healthcare, supply chain with multiple tiers | Tessera Configuration + API |
| Privacy Markers | Maintains transaction ordering without exposing private data | Any use case needing audit trails | Privacy Marker Transaction Protocol |
Real-World Examples of Quorum Privacy in Action
The privacy features we have discussed are not theoretical. They are being used by real organizations to solve real problems. Here are a few concrete examples that illustrate how Quorum’s privacy works in practice.
Interbank Settlement
Multiple banks share a Quorum network for settling interbank transactions. Bank A sends a payment to Bank B. The transaction is marked as private, with only Bank A and Bank B specified as recipients. The central bank, which also sits on the network as a regulator, is given auditor access. Other banks on the network see that a transaction occurred but cannot access its contents. The settlement is final in seconds, not days, and the privacy of the deal terms is maintained throughout.
Pharmaceutical Supply Chain
A drug manufacturer tracks a shipment of temperature-sensitive medication from the factory to a hospital. Each handoff point (manufacturer, distributor, pharmacy, hospital) is a node on the Quorum network. The manufacturer shares batch details and quality certificates through private contracts. The distributor can verify authenticity but cannot see the pricing terms between the manufacturer and the hospital. The result is a verifiable chain of custody without compromising commercial confidentiality.
Government Identity Systems
A government agency uses Quorum to manage digital identity records. Citizens’ personal information is stored in private contracts accessible only to the relevant department. When a citizen applies for a service, the agency can verify their identity against the blockchain record without exposing personal data to other departments or external parties. This approach reduces fraud while complying with data protection laws. It pairs well with the broader concept of decentralized identifiers, where self-sovereign identity meets enterprise privacy needs.
Secure Your Enterprise Blockchain with Quorum
Need private, compliant, and high-performance blockchain solutions for your business? Let our experts design a Quorum-based architecture that fits your exact requirements.
How Quorum’s Consensus Mechanisms Support Privacy
Privacy and consensus are closely linked in blockchain design. The consensus mechanism determines how nodes agree on the state of the ledger, and in a privacy-focused system, the mechanism needs to work correctly even when not all nodes can see all the data.
Quorum supports two primary consensus mechanisms: Istanbul BFT (IBFT) and Raft. Both are designed for permissioned environments and handle the challenge of private data elegantly.
IBFT is a Byzantine Fault Tolerant protocol, meaning the network can reach agreement even if some nodes are acting maliciously or have gone offline. It requires a two-thirds majority of validators to confirm a block. In the context of privacy, IBFT validates the transaction hash (not the private payload), so consensus is reached on the fact that a valid transaction occurred, without requiring validators to access the private data.
Raft, on the other hand, is a crash fault tolerant protocol. It is simpler and faster than IBFT but does not protect against malicious actors. Raft works well in networks where all participants are trusted (like a consortium of banks that already have business relationships). It achieves consensus quickly, often in milliseconds, making it suitable for high-throughput applications. If you want to compare this approach with other consensus models, our guide on PoET for permissioned blockchain offers a useful comparison.
The choice between IBFT and Raft depends on the trust model of the network. For networks with higher trust levels, Raft delivers speed. For networks where participants might be adversarial, IBFT provides stronger guarantees. Either way, the privacy model remains the same because the private data never enters the consensus process directly.
Quorum Consensus Mechanisms Compared
| Parameter | Istanbul BFT (IBFT) | Raft |
|---|---|---|
| Fault Tolerance | Byzantine (handles malicious nodes) | Crash only (no malicious protection) |
| Speed | Seconds to finality | Milliseconds to finality |
| Best For | Semi-trusted consortiums | Fully trusted networks |
| Privacy Impact | Validates hashes, not payloads | Validates hashes, not payloads |
| Node Requirement | Minimum 4 validators (3f+1) | Minimum 3 nodes (leader + 2) |
Industries Where Quorum Privacy Matters Most
Not every blockchain application needs the level of privacy that Quorum provides. But for certain industries, it is a requirement, not a nice-to-have.
Financial Services lead the adoption curve. Banks, asset managers, and insurance companies deal with confidential financial data every day. Regulations like MiFID II in Europe and Dodd-Frank in the US mandate strict data protection. Quorum lets these organizations share a blockchain infrastructure for settlement and clearing while keeping deal terms private. If you are tracking how blockchain intersects with financial technology growth, our analysis of the fastest growing cryptos for big profits provides additional market context.
Healthcare is another natural fit. HIPAA in the United States requires that patient health information be protected with strict access controls. Quorum’s permissioned model and private transactions align directly with these requirements. Hospitals, insurers, and research institutions can share necessary data (like treatment records or clinical trial results) without exposing patient identities.
Supply Chain and Manufacturing benefit from Quorum’s ability to selectively share data. A manufacturer can share quality certificates with a buyer without revealing its supplier network. A logistics company can prove delivery without disclosing routing details. The privacy layers make it possible to build trust between parties who might also be competitors.
Government and Public Sector applications range from voting systems to land registries. In these cases, the data is sensitive not because of commercial value but because of its impact on citizens. Quorum’s governance features ensure that only authorized government bodies can access and modify records, while citizens can verify their own data through controlled access mechanisms.
Energy and Utilities are increasingly adopting blockchain for peer-to-peer energy trading and grid management. Privacy matters here because energy consumption patterns can reveal sensitive information about businesses and individuals. Quorum allows energy companies to trade on a shared platform while keeping consumption data and pricing terms private. For organizations building cross-chain solutions in the energy sector, understanding sidechain peg mechanisms in blockchain can complement Quorum deployments.
How Nadcab Labs Delivers Quorum Privacy Solutions
With more than 8 years of experience building enterprise blockchain solutions, Nadcab Labs has worked extensively with Quorum across multiple industries. The team has deployed Quorum networks for financial institutions, healthcare providers, and supply chain operators, each with distinct privacy requirements and regulatory constraints.
What sets Nadcab Labs apart is not just technical capability but a deep understanding of how privacy requirements vary across business contexts. A banking consortium has very different needs from a hospital network, even though both need “privacy.” Nadcab Labs starts every engagement by mapping the client’s specific data flows, regulatory obligations, and participant trust models. From there, the team designs a Quorum architecture with the right combination of private transactions, permissioning rules, and encryption configurations.
The team’s experience includes configuring Tessera for high-availability environments, implementing custom permissioning smart contracts, setting up multi-tier access control for complex consortiums, and integrating Quorum nodes with existing enterprise systems like ERP and CRM platforms. They have also handled the often-overlooked operational aspects of enterprise blockchain, such as key management, node monitoring, and disaster recovery planning.
For organizations that are still in the evaluation phase, Nadcab Labs offers proof-of-concept engagements where they build a working Quorum prototype tailored to the client’s use case. This lets businesses test Quorum’s privacy features with real data before committing to a full deployment. Their track record of successful deployments, combined with ongoing support and optimization, makes them a reliable partner for any organization serious about enterprise blockchain privacy.
Whether you are building a new consortium network or migrating an existing system to a more privacy-focused platform, the combination of Quorum’s technology and Nadcab Labs’ hands-on expertise creates a solid foundation. You can learn more about their full range of services on the blockchain development company page.
Common Mistakes When Implementing Blockchain Privacy
Even with a platform as capable as Quorum, privacy does not happen automatically. Teams need to configure it correctly, and there are several common pitfalls that can undermine a deployment.
The first is treating all data the same way. Not everything needs to be private. Over-privatizing transactions can slow down the network and create unnecessary complexity. The right approach is to classify data by sensitivity and apply privacy controls accordingly. Public state for non-sensitive data, private transactions for confidential deals, and private contracts for proprietary business logic.
The second mistake is neglecting key management. Quorum’s encryption is only as strong as the keys that protect it. If private keys are stored insecurely, the entire privacy model collapses. Best practice is to use hardware security modules (HSMs) for key storage and to implement key rotation policies. This is an area where understanding orphan blocks in blockchain can help teams understand what happens when node configurations go wrong.
The third is failing to plan for network growth. A Quorum network that works well with five participants might face performance issues with fifty. Privacy features add computational overhead, and the Tessera communication load increases with each new participant. Capacity planning should account for future growth from the start.
Fourth, some teams forget to test privacy boundaries thoroughly. It is not enough to verify that private data is hidden during normal operations. Penetration testing should attempt to access private data through every possible vector, from direct node access to network traffic analysis. Rigorous smart contract testing on blockchain security is part of this process.
Integrating Quorum Privacy with Existing Enterprise Systems
One of Quorum’s practical strengths is that it does not require businesses to rebuild their technology stack from scratch. Because it is built on Ethereum, Quorum supports standard Ethereum tooling, including the Solidity programming language for smart contracts and web3.js for application development. This means existing Ethereum developers can work with Quorum with minimal retraining.
For enterprise integration, Quorum provides RESTful APIs through Tessera and the Quorum node itself. These APIs allow legacy systems to interact with the blockchain without needing to understand the underlying distributed ledger technology. A procurement system can submit private purchase orders to the blockchain, a payment system can trigger settlements, and a reporting tool can pull audit data, all through standard API calls.
The platform also supports deployment on major cloud providers, including AWS, Azure, and Google Cloud. This flexibility matters for enterprises that already have cloud infrastructure commitments. Teams evaluating cloud-based deployments might also benefit from understanding how different serverless options compare. Our comparison of Azure Functions vs AWS Lambda provides context on the cloud services that can complement a Quorum deployment.
For organizations building mobile interfaces on top of their blockchain infrastructure, the flexibility of Quorum’s API layer makes it straightforward to connect mobile applications with on-chain data. If you are considering this path, our guide on mobile app development covers the fundamentals of building connected mobile experiences.
What Comes Next for Quorum and Blockchain Privacy
The blockchain privacy landscape is evolving. Zero-knowledge proofs, secure multi-party computation, and homomorphic encryption are all areas of active research that could eventually be integrated into enterprise platforms like Quorum.
Quorum has already experimented with zero-knowledge proofs (ZKPs) through its ZSL (Zero-Knowledge Security Layer) protocol. ZKPs allow one party to prove to another that a statement is true without revealing any information beyond the fact that the statement is true. In the context of blockchain transactions, this could mean proving that a payment was valid without revealing the amount, the sender, or the recipient.
Interoperability is another area to watch. As more enterprises deploy private blockchains, the ability to transact across different networks will become important. Cross-chain privacy, where private data on one blockchain can be securely shared with another blockchain, is a hard problem that several projects are working on. Quorum’s modular architecture positions it well to adopt these capabilities as they mature.
Regulatory technology (RegTech) integration is also growing. Future versions of enterprise blockchains will likely include built-in compliance engines that automatically enforce data protection rules based on jurisdiction, industry, and transaction type. This would reduce the manual configuration work required today and make privacy compliance more automated and reliable.
Frequently Asked Questions
Quorum uses a dedicated privacy manager called Tessera that encrypts transaction payloads before they reach the blockchain. When a transaction is marked as private, the actual data is sent only to specified recipients through encrypted channels. Other network participants see a cryptographic hash on the ledger, which proves the transaction happened but reveals nothing about the contents. This separation of public and private state means businesses can share an infrastructure while keeping their sensitive data confidential.
Quorum is built directly on Ethereum, which gives it access to Ethereum’s mature development tools, Solidity smart contract language, and large developer community. While Hyperledger Fabric uses a modular architecture with channels for privacy, Quorum achieves privacy through its Tessera layer and permissioned network model while maintaining Ethereum compatibility. This means organizations already invested in Ethereum can transition to Quorum with less friction than switching to a completely different blockchain framework.
Yes, Quorum’s privacy architecture aligns well with major data protection regulations. Its permissioned network ensures only authorized entities access data, while private transactions and contracts keep sensitive information restricted to relevant parties. For GDPR, Tessera’s data retention settings can support right-to-erasure requirements. For HIPAA, the encryption and access control mechanisms protect health data from unauthorized disclosure. Regulatory nodes with audit-only access can be added for oversight.
Quorum transactions are significantly faster than public Ethereum because it operates in a permissioned environment with fewer nodes and more efficient consensus mechanisms. Using Istanbul BFT, transactions reach finality in a few seconds. With Raft consensus, finality can happen in milliseconds. Public Ethereum, depending on network congestion, can take anywhere from 15 seconds to several minutes. Quorum also eliminates gas fees and mining, so there is no competition for block space slowing things down.
Tessera is Quorum’s standalone privacy transaction manager that handles all the encryption and distribution of private data. It runs alongside each Quorum node and manages cryptographic keys, encrypts transaction payloads using envelope encryption, distributes encrypted data to authorized recipients over TLS connections, and stores encrypted payloads locally. Tessera is the component that actually enforces privacy at the data level, making it one of the most critical pieces of a Quorum deployment.
Nadcab Labs brings over 8 years of specialized experience in enterprise blockchain development, including extensive work with Quorum across banking, healthcare, and supply chain sectors. Their approach goes beyond just setting up nodes. They analyze each client’s specific data flows, regulatory requirements, and privacy needs before designing the architecture. Their team handles everything from Tessera configuration and custom permissioning to system integration and post-deployment support, backed by a track record of successful enterprise deployments.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







