Key Takeaways
- Property token custody architecture directly impacts security, regulatory compliance, and investor confidence in tokenized real estate platforms across global markets.
- Multi-signature wallets provide transparent on-chain governance with verifiable approval workflows but create visible attack surfaces for sophisticated adversaries.
- MPC custody eliminates single points of failure through distributed key generation and threshold signing without ever reconstructing complete private keys.
- Gas costs differ significantly between architectures, with MPC producing standard single-signature transactions while multi-sig requires multiple on-chain verifications.
- Key rotation and recovery mechanisms vary substantially, with MPC enabling seamless updates while multi-sig typically requires wallet migration procedures.
- Regulatory frameworks in USA, UK, UAE, and Canada increasingly recognize both custody models when implemented with proper controls and audit capabilities.
- Institutional investors prefer custody solutions offering insurance coverage, SOC 2 compliance, and segregated storage regardless of underlying cryptographic architecture.
- Hybrid architectures combining MPC operational efficiency with multi-sig governance oversight represent emerging best practices for enterprise Property Token Custody tokenization.
- Smart contract integration capabilities influence custody selection, with multi-sig offering native compatibility while MPC requires additional signature verification layers.
- Future custody standards will likely mandate interoperability between architectures, enabling platforms to leverage strengths of both approaches simultaneously.
Understanding Property Token Custody in Real Estate Tokenization
Property token custody represents the foundational infrastructure layer that secures digital ownership records in real estate tokenization platforms. Unlike traditional property ownership where title companies and government registries maintain records, tokenized real estate relies on blockchain-based tokens that require cryptographic key management. The custody architecture determines who can authorize transfers, how ownership changes are validated, and what safeguards protect against unauthorized access.
Our agency has spent over eight years implementing property token custody solutions for clients across USA, UK, UAE, and Canada. This experience reveals that custody architecture decisions made during platform design fundamentally shape operational capabilities, regulatory compliance pathways, and investor confidence levels. Choosing between MPC and multi-signature approaches requires understanding technical tradeoffs alongside business requirements.
Effective property token custody must balance security against operational efficiency. Overly complex custody workflows create friction that discourages legitimate transactions while insufficient controls expose assets to theft or unauthorized transfers. The optimal architecture depends on portfolio size, investor sophistication, regulatory environment, and integration requirements with existing real estate management systems.
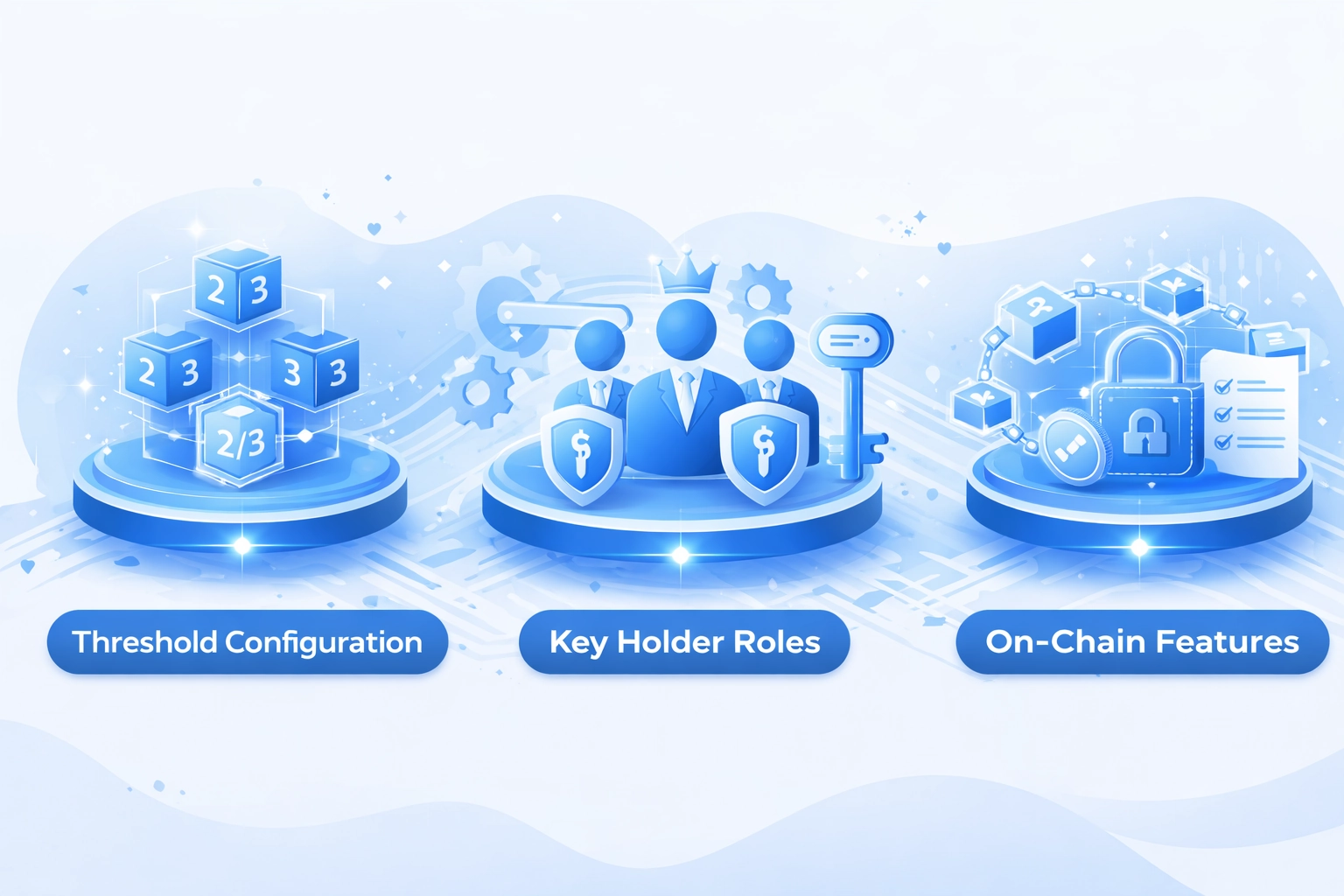 Defining Multi-Signature Wallet Architecture in Property Tokenization
Defining Multi-Signature Wallet Architecture in Property Tokenization
Multi-signature architecture distributes transaction authorization across multiple independent key holders.
Threshold Configuration
- 2-of-3 for standard operations
- 3-of-5 for high-value transfers
- 4-of-7 for institutional portfolios
- Custom thresholds per asset class
Key Holder Roles
- Asset manager operational key
- Compliance officer approval key
- Legal custodian verification key
- Emergency recovery key holder
On-Chain Features
- Transparent signature verification
- Auditable approval history
- Native smart contract support
- Immutable governance records
Explaining Multi-Party Computation for Digital Property Token Custody
Multi-Party Computation represents a cryptographic breakthrough enabling multiple parties to jointly compute functions over their inputs without revealing those inputs to each other. In property token custody, MPC allows distributed key generation where no single party ever possesses the complete private key. Instead, each participant holds a key share that contributes to signature generation through secure computation protocols.
The fundamental security advantage of MPC lies in eliminating the existence of a complete key at any point in the custody lifecycle. Traditional approaches require assembling complete keys for signing, creating vulnerability windows. MPC protocols compute valid signatures through collaborative computation among share holders without any participant learning others’ shares or reconstructing the full key. This mathematical guarantee provides stronger theoretical security than threshold schemes requiring key assembly.
Leading institutional custody providers serving Dubai financial centers and North American markets have increasingly adopted MPC for its operational flexibility. Key shares can be rotated without changing wallet addresses, thresholds can be adjusted dynamically, and new participants can be added or removed without asset migration. These capabilities prove essential for enterprise Property Token Custody tokenization platforms managing evolving stakeholder relationships.
How MPC and Multi-Sig Differ at the Cryptographic Level
Understanding cryptographic distinctions helps platform architects select appropriate custody models for specific property tokenization requirements. While both approaches distribute control, their underlying mechanisms create different security profiles and operational characteristics.
| Characteristic | Multi-Signature | MPC Custody |
|---|---|---|
| Key Existence | Multiple complete keys exist | No complete key ever exists |
| Signature Type | Multiple separate signatures | Single aggregated signature |
| On-Chain Footprint | Visible multi-sig contract | Standard wallet appearance |
| Protocol Layer | Smart contract enforced | Off-chain computation |
| Threshold Flexibility | Fixed at deployment | Dynamically adjustable |
Ownership Control Models in MPC vs Multi-Sig Systems
Ownership control models define how authority over Property Token Custody is distributed and exercised. Multi-signature systems implement explicit governance structures visible on-chain, where each signatory address represents a known entity with defined responsibilities. This transparency enables regulatory verification and investor due diligence but also reveals organizational structure to potential adversaries.
MPC custody enables more flexible ownership models where control distribution remains private. Key share holders can change without on-chain transactions, enabling confidential succession planning and dynamic governance adaptation. This privacy proves valuable for family offices and private wealth managers who prefer discretion about control arrangements for their tokenized real estate holdings.
Hybrid ownership models combine both approaches, using multi-sig for high-level governance decisions requiring transparency while employing MPC for operational transactions needing efficiency. Our implementations across London, Toronto, and Dubai financial centers increasingly adopt such layered architectures to satisfy both regulatory transparency requirements and operational privacy preferences.
Key Management Challenges in Tokenized Real Estate Custody
Key management represents the most operationally complex aspect of property token custody. Both MPC and multi-sig systems require secure key generation, protected storage, reliable backup, and controlled access procedures. The long-term nature of real estate investments, often spanning decades, demands custody solutions capable of surviving personnel changes, corporate restructurings, and evolving security threats.
Multi-signature key management challenges include coordinating geographically distributed signatories, maintaining hardware security modules across multiple locations, and ensuring key holder availability for time-sensitive transactions. Lost or compromised individual keys may require complete wallet migration, creating operational disruption and potential asset exposure during transition periods.
MPC key share management introduces different challenges including secure computation protocol maintenance, share refresh coordination, and ensuring cryptographic material consistency across distributed infrastructure. While MPC enables seamless key rotation, implementing these procedures correctly requires specialized expertise that many real estate platforms lack internally.
Threshold Signing and Key Fragmentation in MPC Custody
Threshold signing in MPC custody enables a subset of key share holders to produce valid signatures without requiring all participants. A 3-of-5 threshold configuration allows any three share holders to authorize transactions while two shares remain uninvolved. This flexibility supports operational continuity when individual participants are unavailable while maintaining security through distributed control requirements.[1]
Key fragmentation protocols in modern MPC implementations use sophisticated mathematical schemes ensuring shares reveal nothing about the complete key or other shares. Even sophisticated adversaries compromising multiple shares below the threshold cannot derive useful information about signing capabilities. This information-theoretic security provides stronger guarantees than computational security assumptions underlying traditional cryptographic approaches.
Proactive share refresh mechanisms periodically generate new shares representing the same underlying key, invalidating previously compromised material. This capability proves invaluable for long-term property token custody where key material may face exposure risks over extended holding periods spanning decades of real estate ownership.
Security Attack Surfaces in Multi-Sig Property Token Custody
Understanding attack vectors enables platform architects to implement appropriate countermeasures protecting tokenized real estate assets from sophisticated adversaries targeting high-value Property Token Custody portfolios.
| Attack Vector | Risk Level | Mitigation Strategy |
|---|---|---|
| Key Holder Collusion | High | Geographic and organizational separation |
| Smart Contract Exploit | Critical | Formal verification and audits |
| Social Engineering | Medium | Multi-channel verification protocols |
| Physical Key Theft | Medium | HSM storage and biometric access |
| On-Chain Visibility | Low | Privacy-preserving transaction batching |
How MPC Reduces Single-Point-of-Failure Risks
MPC fundamentally eliminates single points of failure by ensuring no complete key ever exists in any single location or at any single moment. Traditional custody approaches, including multi-signature, require complete keys to exist during signing operations. This key assembly creates vulnerability windows where adversaries could potentially capture complete cryptographic material through targeted attacks.
The distributed computation model means compromising any individual share holder or infrastructure component yields no actionable advantage to attackers. Even nation-state adversaries with unlimited resources cannot derive signing capability from partial shares below the threshold. This Property Token Custody proves especially valuable for property tokens representing assets in multiple jurisdictions where legal seizure might compel disclosure from individual custodians.
Operational single points of failure also diminish with MPC. Hardware failures, personnel departures, or facility disasters affecting individual share holders do not compromise custody capabilities as long as threshold participants remain operational. This resilience supports business continuity requirements for institutional property portfolios managed across USA, UK, UAE, and Canadian operations.
Operational Complexity of MPC vs Multi-Sig Architectures
Operational complexity differs substantially between custody architectures, impacting staffing requirements, training investments, and ongoing maintenance costs. Multi-signature operations leverage well-understood procedures with established tooling ecosystems. Most blockchain platforms natively support multi-sig wallets, and operators can use standard interfaces without specialized cryptographic expertise.
MPC implementations require specialized infrastructure including secure computation servers, network connectivity between share holders, and protocol-specific software maintenance. Operational teams need understanding of threshold cryptography concepts to troubleshoot issues effectively. Vendor dependency often increases as proprietary MPC implementations may lack interoperability between providers.
However, day-to-day operations often prove simpler with MPC once infrastructure is established. Automated workflows can execute routine transactions without manual signature coordination. Multi-sig operations frequently require scheduling calls or managing asynchronous approval queues that introduce delays and friction for time-sensitive Property Token Custody transactions.
Gas Costs and On-Chain Footprint Comparison
Transaction costs significantly impact total cost of ownership for property token custody, especially for platforms processing high volumes of transfers, distributions, and governance operations.
| Cost Factor | Multi-Signature | MPC Custody |
|---|---|---|
| Deployment Cost | High (contract creation) | Standard (EOA address) |
| Per Transaction Gas | ~100,000+ gas units | ~21,000 gas units |
| Signature Storage | On-chain (expensive) | Off-chain (minimal) |
| Configuration Changes | Requires migration | No on-chain cost |
| Annual Savings Potential | Baseline | 60-80% reduction |
Recovery, Key Rotation, and Emergency Access Mechanisms
1. Incident Detection
Automated monitoring identifies anomalous activity or key holder unavailability triggering recovery protocols.
2. Emergency Assessment
Security team evaluates incident severity and determines appropriate recovery pathway based on predefined procedures.
3. Backup Activation
Retrieve encrypted backup materials from secure cold storage facilities under dual control access requirements.
4. Key Reconstruction
Combine backup shares or initiate MPC refresh protocol to restore operational signing capability securely.
5. Verification Testing
Execute test transactions on separate infrastructure to confirm restored custody capabilities function correctly.
6. Compromised Material Revocation
Invalidate potentially compromised keys or shares through rotation protocols or wallet migration procedures.
7. Operations Resumption
Restore normal custody operations with enhanced monitoring for potential follow-on attack attempts.
8. Post-Incident Review
Document lessons learned and implement procedural improvements to prevent recurrence of similar incidents.
Custody Compliance Requirements for Tokenized Real Estate
Regulatory compliance for property token custody varies significantly across jurisdictions, requiring platforms to navigate complex requirements while maintaining operational efficiency. USA regulations under SEC custody rules demand qualified custodians for securities, with ongoing debate about whether MPC and multi-sig solutions meet qualification standards. State-level money transmitter licensing adds additional complexity for platforms operating nationally.
UK FCA guidance requires firms holding client assets to maintain adequate organizational arrangements and internal controls. Custody solutions must demonstrate segregation of client assets, appropriate insurance coverage, and regular reconciliation procedures. Multi-signature approaches with transparent on-chain records often simplify audit requirements compared to MPC solutions requiring additional documentation of off-chain processes.
UAE regulators including DFSA and VARA have established progressive frameworks recognizing digital asset custody arrangements. Canadian provincial securities commissions increasingly align with international standards while maintaining domestic investor protection priorities. Platforms serving multiple jurisdictions must implement custody architectures satisfying the most stringent applicable requirements.
Regulatory Acceptance of MPC and Multi-Sig Custody Models
Regulatory attitudes toward custody architectures continue evolving as agencies gain experience evaluating digital asset infrastructure. Multi-signature custody benefits from longer operational history and established audit methodologies. Regulators understand how to verify multi-sig implementations through on-chain analysis and standard cryptographic assessments, reducing evaluation friction during licensing processes.
MPC acceptance has accelerated following successful institutional deployments and academic validation of underlying cryptographic protocols. Leading custody providers have obtained regulatory approvals in multiple jurisdictions using MPC architectures, establishing precedents that benefit subsequent applicants. However, some regulators remain cautious about proprietary MPC implementations lacking independent security audits.
Our experience helping clients navigate regulatory approvals in London, Dubai, Toronto, and New York suggests that custody architecture selection matters less than demonstrating comprehensive security controls, operational procedures, and risk management frameworks regardless of underlying technology choices.
Institutional-Grade Security Considerations for Property Token Custody
Selecting appropriate custody architecture requires systematic evaluation across multiple security dimensions.
Threat Modeling
Identify adversary capabilities and attack vectors specific to property portfolio value and investor profile.
Control Assessment
Evaluate technical and procedural controls against identified threats to determine residual risk levels.
Operational Fit
Assess architecture compatibility with transaction volumes, approval workflows, and team capabilities.
Vendor Evaluation
Review provider security certifications, insurance coverage, and track record with similar asset classes.
Integration Analysis
Determine custody solution compatibility with smart contracts, compliance systems, and reporting tools.
Future Scalability
Project growth requirements and verify architecture can scale without security degradation or migration needs.
Scalability of Custody Infrastructure for Large Property Token Custody Portfolios
Property tokenization platforms anticipating portfolio growth must select custody architectures capable of scaling without security compromises or operational disruptions. Multi-signature scalability is limited by on-chain transaction throughput and gas costs that increase with signatory counts. Large multi-sig configurations become impractical as coordination overhead and transaction costs multiply with portfolio expansion.
MPC architectures offer superior scalability characteristics for enterprise deployments. Off-chain computation means signature generation costs remain constant regardless of participant counts or transaction volumes. Automated MPC workflows can process thousands of transactions daily without manual intervention, supporting large Property Token Custody portfolios with diverse investor bases requiring frequent distributions and transfers.
Hybrid approaches segment custody by asset class or value threshold, applying multi-sig governance oversight for high-value transactions while using MPC efficiency for routine operations. This tiered architecture balances transparency requirements with operational scalability as portfolios grow across markets in USA, UK, UAE, and Canada.
Integration with Smart Contracts and Real Estate Platforms
Smart contract integration requirements significantly influence custody architecture selection. Multi-signature wallets deployed as smart contracts interact natively with other on-chain protocols, enabling seamless integration with token standards, automated distribution contracts, and governance mechanisms. This native composability simplifies building sophisticated Property Token Custody tokenization ecosystems leveraging existing DeFi infrastructure.
MPC custody produces standard signatures that smart contracts cannot distinguish from single-key wallets. While this provides privacy benefits, it may require additional verification layers for contracts expecting multi-party authorization evidence. Advanced integrations combine MPC signing with on-chain attestation contracts that record approval metadata without revealing participant identities.
Custody Architecture Impact on Investor Trust and Transparency
Investor confidence in property token custody directly correlates with transparency and verifiability. Multi-signature approaches enable investors to independently verify custody arrangements through blockchain explorers, observing signatory addresses and approval histories. This transparency builds trust through cryptographic verification rather than reliance on custodian representations.
MPC custody requires investors to trust custodian attestations about share distribution and threshold configurations since these details remain off-chain. Reputable MPC providers address this through independent audits, insurance coverage, and SOC 2 certifications that provide assurance without revealing operational details. Institutional investors increasingly accept MPC custody when accompanied by appropriate third-party validations.
 Use Cases Where Multi-Sig Custody Outperforms MPC
Use Cases Where Multi-Sig Custody Outperforms MPC
DAO Governance
- Transparent on-chain voting records
- Verifiable approval workflows
- Community auditability
Regulatory Compliance
- Clear audit trails
- Demonstrable controls
- Simple verification
Smart Contract Native
- Direct protocol integration
- On-chain composability
- Automated workflows
Scenarios Where MPC Becomes the Preferred Custody Model
MPC custody excels in high-volume operational environments where transaction costs and approval latency significantly impact user experience. Property Token Custody platforms processing frequent dividend distributions, secondary market trades, or automated rebalancing benefit from MPC’s gas efficiency and streamlined signing workflows that enable near-instantaneous transaction execution.
Privacy-sensitive deployments favor MPC’s ability to conceal custody arrangements from on-chain observers. Family offices, private wealth managers, and institutional investors often prefer custody solutions that do not publicly reveal organizational structure or control distribution through visible multi-sig configurations.
Future Custody Standards for Real Estate Tokenization Platforms
Emerging standards will shape property token custody architecture across global markets.
Standard 1: Hybrid architectures combining MPC efficiency with multi-sig governance will become industry baseline for institutional platforms.
Standard 2: Interoperability protocols will enable seamless custody provider migration without asset transfer or wallet changes.
Standard 3: Regulatory harmonization across USA, UK, UAE, and Canada will establish consistent custody compliance requirements.
Standard 4: Insurance products specifically designed for tokenized real estate custody will standardize coverage terms and claim procedures.
Standard 5: Zero-knowledge proof integration will enable custody verification without revealing sensitive operational details to verifiers.
Standard 6: Account abstraction adoption will blur distinctions between custody models through programmable authorization logic.
Standard 7: Cross-chain custody solutions will support Property Token Custody deployed across multiple blockchain networks simultaneously.
Standard 8: AI-powered threat detection will enhance custody security through real-time behavioral analysis and anomaly identification.
Property Token Custody Compliance Checklist
Security Controls
- HSM key storage implemented
- Multi-factor authentication required
- Penetration testing completed
Operational Procedures
- Approval workflows documented
- Recovery procedures tested
- Incident response plan active
Regulatory Alignment
- Jurisdictional licenses obtained
- AML procedures implemented
- Audit reports available
Insurance Coverage
- Crime insurance active
- E&O coverage confirmed
- Coverage limits adequate
Secure Your Property Token Custody Infrastructure Today!
Partner with our custody experts who have implemented MPC and multi-sig solutions for $500M+ in tokenized real estate across global markets.
People Also Ask
Property token custody refers to the secure storage and management of digital tokens representing fractional ownership in real estate assets. Custody solutions protect private keys that control these tokens, ensuring only authorized parties can transfer or manage property holdings. Professional custody architecture prevents unauthorized access, theft, and loss while maintaining regulatory compliance. Both institutional investors and individual token holders across USA, UK, UAE, and Canada require robust custody infrastructure to safeguard their tokenized real estate investments.
Multi-signature custody requires multiple private keys to authorize any transaction involving Property Token Custody. Typically configured as 2-of-3 or 3-of-5 arrangements, this architecture distributes control among different parties such as asset managers, legal custodians, and compliance officers. Each signatory holds one key, and transactions only execute when the required threshold of signatures is collected. This approach prevents single points of failure and ensures proper governance oversight for valuable tokenized real estate assets.
Multi-Party Computation custody eliminates complete private keys by distributing cryptographic key shares among multiple parties who jointly compute signatures without reconstructing the full key. This approach offers enhanced security since no single party ever possesses the complete key. MPC custody provides flexibility for institutional Property Token Custody management, enabling dynamic threshold adjustments and seamless key rotation without changing wallet addresses, making it increasingly popular among sophisticated real estate tokenization platforms.
Security depends on implementation quality and operational requirements rather than architecture alone. Multi-signature provides transparent, auditable security through on-chain verification but creates visible attack surfaces. MPC offers stronger theoretical security through distributed computation but requires trust in off-chain processes. Most institutional Property Token Custody platforms in regulated markets prefer hybrid approaches combining both architectures, leveraging multi-sig transparency for governance while using MPC for operational efficiency and key management flexibility.
Property token custody must comply with securities regulations, anti-money laundering requirements, and digital asset custody rules specific to each jurisdiction. USA platforms must consider SEC and state money transmitter regulations, while UK operations fall under FCA oversight. UAE and Dubai follow VARA and DFSA frameworks, and Canadian platforms must meet provincial securities requirements. Custody providers typically require licensing, insurance coverage, segregated asset storage, and comprehensive audit trails to meet institutional and regulatory standards.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







