
Key Takeaways
- Digital asset custody provides institutional-grade security infrastructure for cryptocurrency, tokens, and blockchain-based assets through multi-signature wallets, hardware security modules, and cold storage solutions protecting against theft and unauthorized access.
- Secure escrow functionality in digital asset custody enables trustless transactions between parties by holding assets until predetermined conditions are met, reducing counterparty risk and facilitating complex multi-party agreements across borders.
- Custodial models offer professional key management and regulatory compliance suitable for institutions, while non-custodial approaches provide maximum user control and autonomy ideal for technically sophisticated participants prioritizing self-sovereignty.
- Institutional custody platforms maintain 95-98% of assets in offline cold storage, implement geographic key distribution, provide crime insurance coverage up to $500 million, and achieve SOC 2 Type II certification ensuring enterprise security standards.
- Regulatory compliance for digital asset custody varies across jurisdictions, requiring money transmitter licenses in USA, FCA authorization in UK, VARA licensing in UAE Dubai, and provincial securities registration in Canada with comprehensive AML/KYC procedures.
- Multi-party computation (MPC) technology and smart contract-based escrow represent emerging innovations enabling threshold signatures without single points of failure and programmable automated release conditions enhancing security and operational efficiency.
- Digital asset custody platforms support diverse asset types including major cryptocurrencies, ERC-20 tokens, NFTs, security tokens, stablecoins, and assets across 50-200+ blockchain networks with unified custody and compliance frameworks.
- Cross-border escrow transactions benefit from blockchain’s borderless nature, 24/7 settlement capabilities, transparent audit trails, and reduced intermediary requirements compared to traditional international escrow creating efficiency gains and cost reductions.
Introduction to Digital Asset Custody in Modern Finance
The emergence of blockchain technology and digital assets has fundamentally transformed how value is stored, transferred, and managed in global financial systems. Digital asset custody represents the critical infrastructure enabling institutional participation in cryptocurrency markets by providing secure, compliant, and operationally robust solutions for holding and managing blockchain-based assets. As digital assets have evolved from experimental technology into a multi-trillion dollar asset class, custody solutions have matured to meet the sophisticated requirements of banks, asset managers, corporations, and high-net-worth individuals demanding institutional-grade security and regulatory compliance.
Over the past eight years, our experience serving clients across the United States, United Kingdom, United Arab Emirates, and Canada has demonstrated that effective digital asset custody requires much more than simple private key storage. Modern custody solutions must address complex challenges spanning cybersecurity, regulatory compliance, operational efficiency, disaster recovery, insurance coverage, and integration with traditional financial infrastructure. The stakes are extraordinarily high, as custody failures can result in permanent asset loss, regulatory violations, reputational damage, and significant financial liability affecting organizations and their stakeholders.
Digital asset custody has become particularly crucial for escrow applications where neutral third parties hold assets pending fulfillment of contractual obligations, verification of conditions, or dispute resolution between counterparties. Traditional escrow services, while well-established for real estate and M&A transactions, face significant limitations when applied to digital assets including 24/7 market operations, cross-border complexities, settlement speed requirements, and the unique security considerations inherent to blockchain-based value transfer. Purpose-built digital asset custody platforms address these challenges through specialized infrastructure combining cryptographic security, smart contract automation, and institutional operational frameworks.
The global digital asset custody market has experienced exponential growth, with assets under custody exceeding $400 billion across institutional platforms as traditional financial institutions, cryptocurrency-native firms, and specialized custody providers compete to serve this expanding market. This growth reflects increasing institutional adoption driven by improved regulatory clarity, enhanced security standards, comprehensive insurance availability, and recognition of digital assets as legitimate portfolio components deserving professional custody infrastructure comparable to traditional securities and commodities.
What Digital Asset Custody Means in the Web3 Era
Digital asset custody encompasses the secure storage, management, and administration of cryptographic private keys that control ownership and transfer rights for blockchain-based assets. Unlike traditional custody where financial institutions hold physical securities or maintain ledger entries in centralized databases, digital asset custody fundamentally involves safeguarding cryptographic keys that represent irrevocable control over assets recorded on distributed ledgers. This paradigm shift creates unique security requirements, as private key compromise enables immediate irreversible asset theft without the fraud detection and reversal mechanisms available in traditional banking systems.
The Web3 era has expanded digital asset custody beyond simple cryptocurrency storage to encompass diverse asset types including fungible tokens, non-fungible tokens, decentralized finance protocol positions, governance rights, staking derivatives, and tokenized real-world assets. Modern custody platforms must support multiple blockchain networks simultaneously, each with distinct technical characteristics, security considerations, and operational requirements. This multi-chain reality demands sophisticated infrastructure capable of managing keys across Ethereum, Bitcoin, Solana, Polygon, Avalanche, and dozens of other networks while maintaining consistent security standards and unified user experiences.
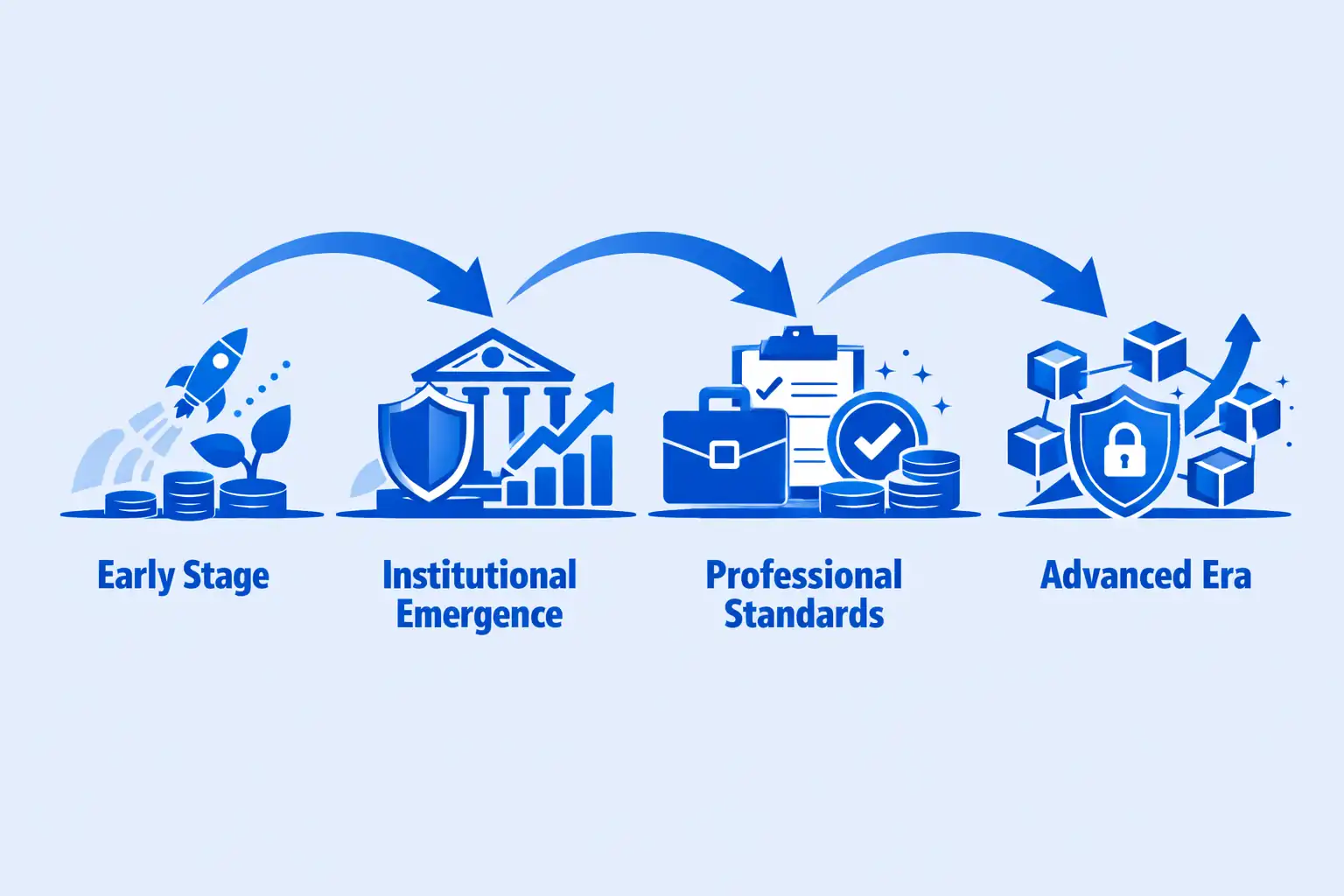
Evolution of Digital Asset Custody Standards
Early Stage (2013–2017)
- Basic hot wallet services with limited security
- Individual responsibility for key management
- Minimal regulatory framework or oversight
- Frequent exchange hacks and custody failures
- No insurance or institutional standards
Institutional Emergence (2018–2020)
- Qualified custodian designation requirements
- Introduction of cold storage and multi-signature
- First custody insurance policies available
- Regulatory licensing frameworks developed
- Institutional-grade platforms launched
Professional Standards (2021–2023)
- SOC 2 Type II certification standard practice
- Multi-party computation (MPC) adoption
- Comprehensive insurance up to $500M+
- Global regulatory compliance frameworks
- Integration with traditional finance systems
Advanced Era (2024–Present)
- Smart contract-based automated custody
- Cross-chain unified custody platforms
- AI-powered risk monitoring and fraud detection
- Institutional DeFi custody solutions
- Quantum-resistant cryptography preparation
Regulated & Tokenized Assets Era
- Custody support for security tokens and RWAs
- Integrated compliance and reporting engines
- Jurisdiction-aware custody enforcement
- On-chain corporate action handling
- Seamless issuer–custodian workflows
Future Custody Paradigm
- Policy-driven programmable custody
- Self-sovereign identity-based access
- Interoperable custody across TradFi and DeFi
- Regulator-node participation models
- Fully automated compliance-by-design
Professional digital asset custody extends beyond technical key management to encompass comprehensive operational frameworks including transaction authorization workflows, compliance monitoring, regulatory reporting, customer service, and integration with enterprise systems. Institutional custodians provide administrative services such as corporate action processing, staking and yield generation, tax reporting, and portfolio analytics that mirror traditional custody offerings while adapting to the unique characteristics of blockchain-based assets and decentralized protocols.
The distinction between custodial and non-custodial models represents a fundamental choice affecting security, convenience, regulatory compliance, and philosophical alignment with blockchain’s decentralization principles. Custodial models, where professional third parties manage keys on behalf of clients, offer convenience, recovery mechanisms, regulatory compliance, and institutional-grade security infrastructure at the cost of introducing counterparty risk and requiring trust in the custodian. Non-custodial approaches granting users complete control over private keys maximize autonomy and eliminate intermediary dependencies but place full responsibility for security on users who may lack technical expertise or operational safeguards to protect assets adequately.
For escrow applications specifically, digital asset custody must balance security, neutrality, and conditional release mechanisms ensuring assets are protected while enabling automated or manual release based on predetermined criteria. Escrow custody platforms implement segregated account structures, multi-signature authorization requiring consent from relevant parties, smart contract integration for automated condition verification, and dispute resolution procedures addressing scenarios where parties disagree about whether release conditions have been satisfied. These specialized requirements distinguish escrow custody from general asset storage and demand purpose-built infrastructure addressing the unique challenges of neutral third-party holding arrangements.
Why Secure Escrow Is Critical for Digital Asset Transactions
Secure escrow mechanisms address the fundamental challenge of counterparty risk in digital asset transactions where parties lack established trust relationships or enforceable legal recourse. The irreversible nature of blockchain transactions creates scenarios where buyers transferring payment have no guarantee of receiving goods or services, while sellers delivering value before payment face risk of non-payment. Traditional escrow services mitigate these risks in conventional commerce, but digital assets require specialized escrow infrastructure accounting for cryptographic security, 24/7 global markets, smart contract integration, and the speed of blockchain settlement.
Digital asset escrow has become essential across numerous transaction types including over-the-counter cryptocurrency trades where buyers and sellers exchange large quantities outside public exchanges, tokenized asset sales involving real estate, art, or commodities represented on blockchains, merger and acquisition transactions with cryptocurrency consideration, cross-border payments requiring delivery-versus-payment settlement, and dispute resolution scenarios where contested funds must be held pending arbitration or legal proceedings. Each application demands robust custody infrastructure ensuring assets remain secure and accessible only under appropriate conditions.
Critical Benefits of Digital Asset Escrow
Critical Importance
Neutral custody removes dependency on either party honoring commitments, enabling trustless transactions between unknown counterparties across jurisdictional boundaries.
Critical Importance
Escrow prevents common fraud schemes including advance fee fraud, non-delivery scams, and payment disputes by ensuring assets are secured before transaction execution.
High Value
Smart contract integration enables programmatic asset release when verifiable conditions are met, reducing manual intervention and settlement delays.
High Value
Neutral custody provides structured mechanisms for resolving disagreements about condition fulfillment through arbitration, mediation, or legal proceedings.
Significant Value
Blockchain immutability combined with custody logging creates comprehensive verifiable records of escrow transactions supporting compliance and dispute resolution.
Significant Value
Digital escrow facilitates international transactions without traditional banking intermediaries, currency conversion complexities, or multi-day settlement delays.
The security architecture of digital asset escrow must address unique threats absent from traditional escrow including private key compromise, smart contract vulnerabilities, blockchain reorganizations, oracle manipulation, and protocol-level attacks that could enable unauthorized asset access or release. Professional escrow custody platforms implement defense-in-depth strategies combining cryptographic security, operational controls, insurance coverage, and legal frameworks creating multiple protective layers ensuring assets remain secure throughout the escrow period regardless of individual component failures.
Regulatory compliance represents another critical dimension of secure digital asset escrow, as many jurisdictions classify escrow services as money transmission or trust activities requiring specific licenses and operational standards. In the United States, escrow providers may need money transmitter licenses in multiple states, trust company charters, or federal banking licenses depending on transaction types and volumes. The United Kingdom requires FCA authorization for firms providing custody or escrow services, while UAE’s VARA framework in Dubai establishes specialized licensing for virtual asset service providers including custodians. Canada requires provincial securities registration or money services business licensing depending on asset types and business models. Compliance with these frameworks ensures legal operation and provides customers with regulatory protections and recourse mechanisms.[1]
The economic value proposition of digital asset escrow extends beyond security to encompass efficiency gains including reduced settlement times from days to hours or minutes, lower intermediary costs compared to traditional escrow services charging 1-3% of transaction value, 24/7 availability enabling global transaction execution regardless of business hours or holidays, and programmable automation reducing manual oversight requirements for routine condition verification. These benefits have driven adoption across industries including real estate, e-commerce, freelance services, intellectual property licensing, and supply chain finance where digital asset escrow creates operational advantages over legacy escrow infrastructure.
Core Components of a Secure Digital Asset Custody Framework
A comprehensive digital asset custody framework integrates multiple security layers, operational procedures, and technological components working synergistically to protect assets while enabling authorized access and transaction execution. The architecture must address the entire custody lifecycle from initial key generation through ongoing storage, transaction authorization, and eventually key retirement or migration. Each component introduces specific security considerations and operational requirements that professional custodians must manage through robust policies, technical controls, and continuous monitoring.
Hardware security modules (HSMs) form the foundation of institutional custody infrastructure by providing tamper-resistant environments for cryptographic key generation, storage, and signing operations. These specialized hardware devices implement physical security features making key extraction practically impossible even with physical access, undergo rigorous certification processes including FIPS 140-2 Level 3 or Level 4 validation, and maintain comprehensive audit logging of all cryptographic operations. Leading custodians deploy HSMs in geographically distributed configurations with redundancy ensuring continued operations despite individual device failures, natural disasters, or targeted attacks against specific facilities.
Essential Digital Asset Custody Architecture Components
Cryptographic Infrastructure
Hardware security modules certified to FIPS 140-2 Level 3+ standards for tamper-resistant key operations, secure key generation using hardware random number generators ensuring cryptographic strength, hierarchical deterministic (HD) wallet implementation enabling key derivation from master seeds, and threshold signature schemes distributing signing authority across multiple parties preventing single points of compromise. Geographic distribution of key material across multiple secure facilities creates resilience against localized threats while maintaining operational availability.
Access Control and Authorization
Multi-factor authentication requiring something users know (passwords), something they have (hardware tokens), and something they are (biometrics) for system access. Role-based access control limiting permissions based on job functions with principle of least privilege. Multi-signature transaction authorization requiring multiple independent approvals before execution. Time-locked operations preventing immediate execution of sensitive changes. Comprehensive audit logging capturing all access attempts, transaction authorizations, and administrative actions with immutable storage preventing tampering.
Cold and Hot Storage Architecture
Cold storage maintaining 95-98% of assets in offline environments completely isolated from network connectivity, housed in secure vaults with physical security controls, environmental protections, and access restrictions. Hot wallets retaining 2-5% of holdings for operational liquidity enabling routine withdrawals and transactions with enhanced monitoring, velocity limits, and automated threat detection. Warm storage providing intermediate security tier for assets requiring occasional access with air-gapped systems manually connected only when transactions are necessary.
Security Monitoring and Threat Detection
24/7 security operations center monitoring infrastructure, transaction patterns, and threat intelligence feeds for anomalous activity. Behavioral analytics establishing baselines for normal operations and alerting on deviations suggesting compromise or fraud attempts. Blockchain monitoring tracking on-chain activity for unauthorized transactions or suspicious patterns. Penetration testing and red team exercises simulating attack scenarios validating defensive capabilities. Incident response procedures defining escalation, containment, investigation, and recovery processes for security events.
Backup and Disaster Recovery
Encrypted backups of key material stored in geographically distributed locations with multiple redundancy levels ensuring key recoverability despite catastrophic facility losses. Mnemonic seed phrases or key shares secured in bank vaults, safety deposit boxes, or purpose-built secure storage facilities. Regular recovery testing validating that backup procedures work correctly and meet recovery time objectives. Business continuity planning addressing scenarios including facility destruction, personnel loss, extended infrastructure outages, and systematic attacks.
Compliance and Reporting Systems
Know-your-customer (KYC) verification integrating identity verification, document authentication, and database cross-referencing. Anti-money laundering (AML) screening against sanctions lists, politically exposed persons databases, and adverse media sources. Transaction monitoring analyzing patterns for suspicious activity requiring regulatory reporting. Regulatory reporting automation generating required filings for FinCEN, FCA, VARA, and other authorities. Attestation and audit trails supporting SOC 2, ISO 27001, and other certification requirements demonstrating control effectiveness.
The segregation of duties principle ensures that no single individual possesses sufficient authority or access to independently compromise custody security or misappropriate assets. Professional custody operations implement organizational structures where key generation, transaction approval, operational execution, and audit functions are performed by different personnel with independent oversight. This segregation extends to technical controls through multi-signature requirements, dual control procedures, and maker-checker workflows requiring separate parties to initiate and approve sensitive operations before execution.
Insurance coverage provides financial protection against losses from security breaches, operational errors, insider threats, or other custody failures despite robust preventive controls. Leading digital asset custodians maintain crime insurance policies from specialized underwriters covering theft, hacking, key compromise, and employee dishonesty with coverage limits ranging from $100 million to over $500 million. Policy terms define covered perils, exclusions, deductibles, claims procedures, and custodian responsibilities for maintaining security standards as insurance prerequisites. While insurance cannot prevent losses, it provides financial recourse and risk transfer mechanisms protecting clients and custodians from catastrophic financial impact of major security incidents.
Legal and contractual frameworks define custody relationships, establish liability allocations, specify service levels, and provide dispute resolution mechanisms governing custodian-client interactions. Comprehensive custody agreements address ownership rights confirming clients retain beneficial ownership despite custodian control of keys, liability limitations defining custodian responsibilities and client risk assumptions, indemnification provisions allocating legal defense costs and damages, termination procedures governing asset return if relationships end, and governing law selections determining applicable legal jurisdictions for dispute resolution. These contractual elements must align with regulatory requirements while providing adequate client protections and reasonable custodian liability management.
Role of Custodial vs Non-Custodial Models in Escrow Use Cases
The choice between custodial and non-custodial approaches for digital asset escrow fundamentally affects security assumptions, operational complexity, regulatory compliance, and user experience. Custodial escrow models employ professional third-party custodians who control private keys and manage asset security on behalf of transacting parties, offering convenience, regulatory compliance, dispute resolution procedures, and institutional-grade security infrastructure. Non-custodial escrow leverages smart contracts and multi-signature wallets enabling parties to maintain control over assets while implementing conditional release logic through cryptographic and code-based mechanisms without relying on trusted intermediaries.
Custodial escrow provides significant advantages for transactions involving institutional counterparties, regulatory compliance requirements, large asset values, or parties lacking technical sophistication to manage blockchain operations directly. Professional custodians offer recovery mechanisms if parties lose access credentials, customer support addressing questions and issues, insurance coverage protecting against losses, regulatory licenses providing legal assurance, and integration with traditional financial systems enabling fiat currency interactions. These benefits come at the cost of introducing counterparty risk requiring trust in the custodian’s security, operational integrity, and financial stability.
| Feature | Custodial Escrow | Non-Custodial Escrow | Hybrid Models |
|---|---|---|---|
| Key Control | Third-party custodian holds and manages all private keys with professional security infrastructure | Parties retain control through multi-sig wallets or smart contracts with distributed signing authority | Shared control between custodian and parties using threshold signatures or timelocks |
| Security Model | Enterprise security with HSMs, cold storage, insurance, SOC 2 certification, 24/7 monitoring | Cryptographic security through smart contracts, multi-sig, no trusted third party, code-is-law | Combined cryptographic and institutional security with redundant protective layers |
| Counterparty Risk | Introduces custodian risk; bankruptcy, hack, or fraud could affect asset access | Eliminates trusted third party; relies on smart contract security and party cooperation | Distributed risk across multiple parties and technical layers |
| Regulatory Compliance | Custodian handles KYC, AML, reporting; suitable for regulated institutions and jurisdictions | Parties responsible for own compliance; may not meet institutional regulatory requirements | Compliance services available with retained user control and autonomy |
| Dispute Resolution | Custodian mediates disputes, holds assets pending resolution, can enforce legal judgments | Requires unanimous consent or oracle input; limited flexibility for complex disputes | Structured escalation from automated to manual resolution with custodian intervention |
| Recovery Mechanisms | Account recovery through identity verification if credentials lost; customer support available | No recovery if keys lost; permanent asset loss risk without proper backup procedures | Social recovery or multi-party recovery schemes with balance of security and recoverability |
| Cost Structure | Service fees 0.05-2% annually, setup costs, transaction fees; premium pricing for services | Only blockchain gas fees; no ongoing service charges or intermediary costs | Moderate fees for optional services with base self-custody functionality |
| Best Use Cases | Institutional transactions, regulatory requirements, large values, non-technical users | Peer-to-peer transactions, maximizing autonomy, avoiding intermediaries, technical users | Balanced requirements needing both security and control with optional services |
Non-custodial escrow appeals to users prioritizing autonomy, minimizing intermediary dependencies, reducing costs, or operating in jurisdictions lacking robust custodian options. Smart contract-based escrow eliminates trust requirements by encoding release conditions directly in verifiable code that executes automatically when conditions are met. Multi-signature wallets distribute control across transaction parties and potentially neutral arbitrators who collectively authorize asset release through threshold signing mechanisms. These approaches align philosophically with blockchain’s decentralization principles and eliminate custodian failure risks, but demand technical sophistication, careful smart contract auditing, and robust key management practices from participants.
Hybrid models combining elements of custodial and non-custodial approaches have emerged to balance security, user control, and operational flexibility. Examples include multi-signature arrangements where a custodian holds one key while parties retain others, requiring cooperation between custodian and users for transaction execution. Time-locked escrow implements automatic release after specified periods unless parties actively dispute, providing non-custodial default operation with custodial fallback for complex situations. These hybrid structures attempt to capture benefits from both paradigms while mitigating their respective weaknesses through thoughtful architecture and clear governance frameworks.
The appropriate model selection depends on transaction characteristics including asset values, party sophistication, regulatory requirements, dispute risk, and trust dynamics. High-value transactions between institutional counterparties in regulated industries typically demand custodial escrow providing insurance, compliance, and professional security. Peer-to-peer transactions between technically capable parties in jurisdictions with limited regulatory requirements may prefer non-custodial autonomy. Cross-border transactions involving parties in different regulatory environments might benefit from hybrid approaches accommodating diverse compliance needs while maintaining operational efficiency. Thoughtful model selection aligned with specific transaction requirements optimizes the balance between security, efficiency, and user experience.
How Digital Escrow Custody Works: Step-by-Step Process
Understanding the operational workflow of digital asset escrow custody clarifies how technical infrastructure, legal frameworks, and procedural controls combine to create secure neutral holding arrangements. The escrow lifecycle encompasses distinct phases from initial agreement and account creation through asset deposit, condition verification, release authorization, and final settlement. Each phase implements specific security controls, compliance checks, and operational procedures ensuring assets remain protected while enabling authorized release when appropriate conditions are satisfied.
The process begins with escrow agreement negotiation where transacting parties define release conditions, dispute resolution procedures, fees, timelines, and responsibilities. This agreement typically addresses the specific terms triggering asset release, verification methods proving condition fulfillment, party authorities for approving or objecting to release, dispute escalation procedures if parties disagree, fee allocation between participants, and liability frameworks governing custodian responsibilities. Well-drafted escrow agreements reduce ambiguity and provide clear operational guidance throughout the transaction lifecycle, minimizing disputes and enabling efficient execution.
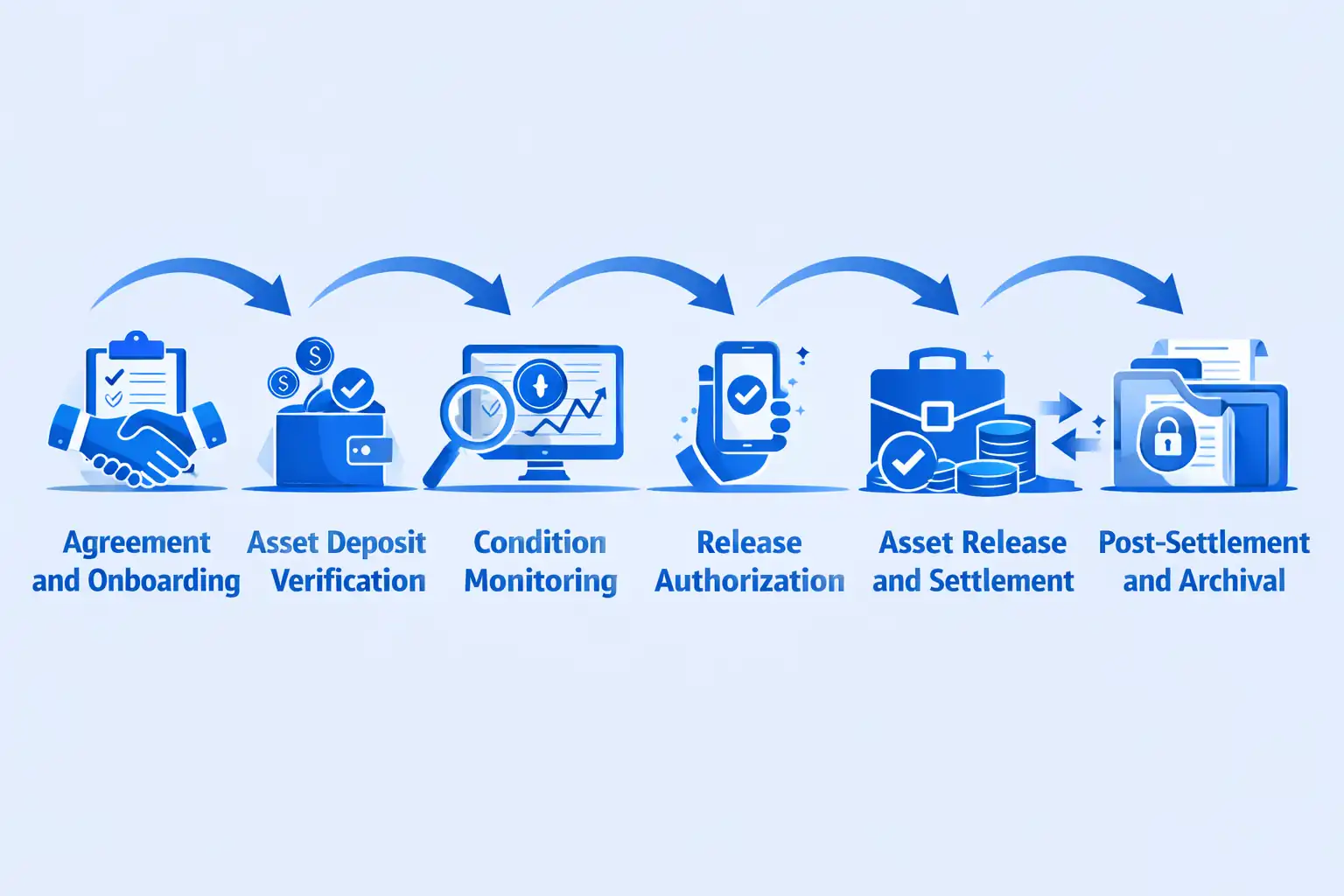
Digital Asset Escrow Custody Lifecycle
Phase 1: Agreement and Onboarding (Days 1-3)
Activities: Escrow agreement negotiation and execution, KYC verification for all parties, account creation with unique escrow identifiers, multi-signature wallet generation with distributed key control, fee payment and documentation execution.
Outputs: Signed escrow agreement, verified party identities, dedicated escrow wallet addresses, documented fee structure, established communication channels.
Phase 2: Asset Deposit and Verification (Days 3-5)
Activities: Depositing party transfers assets to escrow wallet address, blockchain confirmation of transaction receipt, custodian verification of correct asset types and amounts, issuance of deposit confirmation to all parties, activation of escrow hold period.
Outputs: Assets secured in escrow custody, blockchain transaction records, deposit receipt documentation, escrow status updates to parties.
Phase 3: Condition Monitoring (Ongoing)
Activities: Continuous monitoring of release conditions, oracle integration for automated condition verification, party notifications of status updates, document collection supporting condition fulfillment, compliance monitoring throughout hold period.
Outputs: Real-time escrow status dashboard, condition verification evidence, compliance audit trails, periodic status reports to stakeholders.
Phase 4: Release Authorization (Days 30-45 typical)
Activities: Condition fulfillment verification through smart contracts or manual review, authorization request submission by entitled party, multi-signature approval collection from relevant stakeholders, dispute window observation allowing objections, final release authorization confirmation.
Outputs: Release authorization decision, documented condition verification, signed approval records, transaction authorization prepared for execution.
Phase 5: Asset Release and Settlement (Days 45-47)
Activities: Transaction construction transferring assets to receiving party, multi-signature signing by authorized key holders, blockchain broadcast and confirmation, settlement verification, fee deduction and distribution, final documentation generation.
Outputs: Assets transferred to recipient, blockchain transaction confirmation, settlement statements, escrow completion certificates, archive of complete transaction records.
Phase 6: Post-Settlement and Archival
Activities: Final reconciliation and accounting, tax documentation generation if applicable, escrow account closure and key retirement, archival of transaction records for regulatory retention periods, participant satisfaction surveys and feedback collection.
Outputs: Complete audit trail, tax reporting documents, final invoices and receipts, securely archived transaction history, lessons learned documentation.
Throughout the escrow period, custodians maintain comprehensive audit trails documenting all activities, communications, authorizations, and transactions affecting the escrowed assets. These records serve multiple purposes including regulatory compliance demonstrating adherence to AML/KYC requirements, dispute resolution providing factual evidence if conflicts arise, operational oversight enabling quality control and process improvement, and risk management supporting analysis of escrow performance and identification of potential issues. Blockchain immutability complements traditional custody logging by creating tamper-evident records of on-chain activities that can be independently verified by any party.
Secure Your Digital Asset Custody Today
Partner with institutional-grade digital asset custody providers offering multi-signature security, insurance coverage, and regulatory compliance worldwide.
Dispute scenarios require special handling when parties disagree about whether release conditions have been satisfied or who should receive escrowed assets. Professional custody platforms implement structured dispute resolution procedures typically involving initial negotiation between parties facilitated by the custodian, escalation to mediation by neutral third parties if negotiation fails, potential arbitration through formal arbitration services if mediation proves unsuccessful, and ultimate resort to litigation in applicable legal jurisdictions as final recourse. Throughout dispute resolution, the custodian maintains asset security preventing unauthorized release while preserving all parties’ legal rights to pursue resolution through appropriate channels.
Security protocols during asset release demand particular attention as this represents the most sensitive phase where human error, system compromise, or procedural failures could enable unauthorized asset transfer. Leading custodians implement enhanced verification including independent confirmation that release authorizations match escrow agreement terms, multi-party approval from separate personnel preventing single-person fraud, transaction simulation and review before live execution, velocity limits restricting release amounts or frequencies preventing bulk unauthorized transfers, and post-execution monitoring detecting anomalous patterns suggesting compromise. These layered controls create defense-in-depth ensuring release occurs only under legitimate authorized circumstances.
Key Asset Types Managed Through Digital Custody Platforms
Modern digital asset custody platforms support diverse asset classes spanning cryptocurrencies, tokens, NFTs, and tokenized real-world assets, each with unique technical characteristics, security requirements, and operational considerations. The multi-asset capability of comprehensive custody solutions enables clients to consolidate holdings across different blockchain networks and asset types within unified security and compliance frameworks, reducing operational complexity while maintaining specialized handling appropriate for each asset category.
Cryptocurrency custody encompasses native blockchain assets including Bitcoin, Ethereum, and other layer-1 protocol tokens that serve as the foundation for their respective networks. These assets require network-specific technical expertise including understanding of UTXO versus account-based models, appropriate fee estimation for timely transaction confirmation, protocol upgrade management ensuring compatibility with network changes, and staking or consensus participation for proof-of-stake networks. Leading custody platforms support 50 to 200+ different cryptocurrencies, each requiring dedicated blockchain infrastructure, wallet implementations, and operational procedures tailored to specific technical characteristics.
| Asset Category | Examples | Technical Considerations | Custody Challenges |
|---|---|---|---|
| Layer-1 Cryptocurrencies | Bitcoin (BTC), Ethereum (ETH), Solana (SOL), Cardano (ADA), Polkadot (DOT) | Native network tokens, varying consensus mechanisms, protocol-specific wallet implementations, network upgrade compatibility | Multi-chain infrastructure, fee optimization, staking operations, hard fork management, replay attack protection |
| ERC-20 and Token Standards | USDC, USDT, UNI, LINK, stablecoins, utility tokens, governance tokens across Ethereum and compatible chains | Smart contract interactions, gas payment in native tokens, token approval mechanisms, standard interfaces (ERC-20, BEP-20, SPL) | Token contract verification, approval management, gas fee estimation, smart contract security assessment, cross-chain token variants |
| Non-Fungible Tokens (NFTs) | Digital art, collectibles, gaming items, domain names, membership tokens, event tickets, intellectual property rights | ERC-721/ERC-1155 standards, metadata storage (IPFS, Arweave), unique asset identification, transfer restrictions, royalty enforcement | Metadata preservation, provenance verification, collection management, marketplace integration, valuation for insurance/reporting |
| Security Tokens | Tokenized equities, real estate tokens, debt instruments, fund shares, revenue participation rights, asset-backed securities | Regulatory compliance automation, transfer restrictions, investor accreditation, corporate actions, dividend distributions, ERC-1400/3643 standards | KYC/AML integration, jurisdictional transfer controls, regulatory reporting, qualified custodian requirements, corporate action processing |
| DeFi Protocol Positions | Lending positions (Aave, Compound), liquidity pool tokens (Uniswap, Curve), staked assets, yield farming positions, derivatives | Smart contract interactions, protocol-specific logic, composability across protocols, yield accrual, impermanent loss exposure, liquidation risks | Protocol security assessment, position monitoring, automated rebalancing, gas optimization for complex operations, protocol upgrade management |
| Wrapped and Bridge Assets | Wrapped Bitcoin (WBTC), bridged USDC variants, cross-chain representations, synthetic assets, pegged tokens across networks | Bridge protocol security, peg maintenance, redemption mechanisms, cross-chain verification, custodian trust assumptions for wrapped assets | Bridge risk assessment, peg stability monitoring, redemption support, multi-chain portfolio tracking, de-pegging scenario management |
| Stablecoins | USDC, USDT, DAI, BUSD, fiat-backed and algorithmic stablecoins, centralized and decentralized variants across multiple chains | Collateralization mechanisms, issuer reserve verification, regulatory compliance, redemption procedures, peg stability monitoring | Issuer counterparty risk, regulatory uncertainty, de-pegging scenario planning, multi-chain stablecoin management, redemption support |
Security token custody demands specialized capabilities addressing regulatory compliance requirements that distinguish securities from general cryptocurrency assets. Security tokens representing equity, debt, real estate, or other regulated instruments require custodians to implement transfer restrictions enforcing investor accreditation, jurisdictional eligibility, and holding period compliance automatically through smart contract logic or manual verification procedures. Qualified custodian designation under securities regulations may be necessary depending on jurisdictional requirements and asset classifications, imposing additional capital, operational, and compliance obligations on custody providers serving security token markets.
NFT custody introduces unique challenges including metadata preservation ensuring associated artwork, documents, or content remains accessible despite decentralized storage dependencies, provenance verification tracking ownership history and authenticity through blockchain records, collection management organizing related NFTs within portfolio structures, and valuation determination for insurance and reporting purposes given illiquid markets and subjective value assessments. Institutional NFT custody platforms provide specialized interfaces, collection analytics, and marketplace integrations supporting professional management of non-fungible digital assets across art, gaming, intellectual property, and other categories.
DeFi protocol positions represent emerging custody challenges as institutional participants seek exposure to decentralized lending, liquidity provision, and yield generation opportunities. Custodians must support complex smart contract interactions, monitor protocol risks including smart contract vulnerabilities and economic attacks, manage liquidation risks for leveraged positions, optimize gas costs for frequent rebalancing operations, and track yield accrual across multiple protocols simultaneously. The composability of DeFi creates scenarios where assets flow through multiple protocols creating nested dependencies and amplified risk exposures requiring sophisticated monitoring and risk management capabilities beyond traditional custody functions.
Multi-Signature and MPC Wallets for Escrow Security
Multi-signature (multi-sig) and multi-party computation (MPC) technologies represent foundational security mechanisms for digital asset custody, particularly in escrow applications where distributed control and redundant authorization provide essential protection against unauthorized asset access. These cryptographic approaches eliminate single points of failure inherent in traditional single-key custody while enabling flexible authorization policies aligned with business requirements and risk tolerances. Understanding the technical characteristics, operational implications, and appropriate use cases for each approach enables informed custody architecture decisions.
Multi-signature wallets require multiple private keys to authorize transactions, with common configurations including 2-of-3 requiring any two of three designated keys, 3-of-5 requiring three of five keys, or custom m-of-n threshold arrangements matching specific governance requirements. This architecture distributes control across multiple parties or geographic locations, preventing any single compromised key from enabling unauthorized transactions. For escrow applications, multi-sig naturally implements shared control between buyer, seller, and neutral custodian, requiring cooperation for asset release while preventing unilateral action by any single party.
Multi-Signature vs Multi-Party Computation Comparison
Multi-Signature Architecture
- On-chain implementation requiring blockchain protocol support
- Transparent threshold requirements visible on blockchain
- Multiple complete private keys exist separately
- Each signer creates independent signature
- Higher on-chain transaction costs for complex schemes
- Native support varies across blockchain networks
MPC Technology Approach
- Off-chain computation with on-chain single signature
- Privacy-preserving threshold signatures externally
- No complete private key ever exists anywhere
- Distributed key shares combine for signing
- Standard transaction costs indistinguishable from single-sig
- Universal blockchain compatibility without protocol dependency
Multi-Sig Benefits
- Transparent on-chain verification of requirements
- Proven technology with extensive production history
- Simpler conceptual model easier to audit
- No coordination required between signers
- Key recovery possible with threshold key shares
- Well-understood security properties and limitations
MPC Benefits
- Universal blockchain support without protocol constraints
- Enhanced privacy with hidden authorization structure
- Dynamic key share refresh without address changes
- Cost efficiency matching single-signature transactions
- Flexible policy changes without on-chain modifications
- No complete private key vulnerability ever exists
Operational Trade-Offs
- Multi-sig requires signer coordination for each transaction
- MPC enables automated signing workflows
- Multi-sig setup complexity grows with signer count
- MPC scales efficiently across large organizations
- Multi-sig upgrades require contract changes
- MPC policy updates remain off-chain
Use Case Suitability
- Multi-sig suited for DAOs and treasury governance
- MPC preferred for institutional custody platforms
- Multi-sig ideal for transparent on-chain control
- MPC optimal for high-frequency operations
- Multi-sig favors simplicity over flexibility
- MPC supports enterprise-scale security models
Multi-party computation represents an advanced cryptographic technique enabling multiple parties to jointly compute signatures without any single party ever possessing a complete private key. The key is generated through distributed protocols creating shares held by different participants, with threshold numbers of shares sufficient to produce valid signatures through cryptographic computation. This approach provides security advantages over multi-sig by eliminating the complete private key from existence entirely, reducing single points of compromise. Additionally, MPC wallets create standard single-signature transactions on-chain indistinguishable from conventional transactions, providing privacy, universal blockchain compatibility, and cost efficiency advantages.
For escrow applications, both multi-sig and MPC enable essential security properties including distributed control preventing unilateral asset access, redundancy ensuring operations continue despite individual key loss, flexible threshold policies adapting to transaction risk profiles, and auditable authorization trails documenting which parties approved releases. The choice between approaches depends on factors including blockchain protocol support for native multi-sig, privacy requirements regarding authorization structures, transaction cost sensitivity, operational complexity tolerance, and institutional familiarity with each technology.
Implementation considerations for multi-signature escrow include careful key distribution across independent parties or geographic locations preventing correlated failures, clear documentation of signing authority and escalation procedures, secure key backup procedures ensuring threshold recovery remains possible despite individual key losses, and regular testing of signing workflows validating operational readiness. Common pitfalls include inadequate key geographic distribution creating single facility dependencies, unclear signing policies causing authorization delays, and insufficient backup procedures risking permanent asset loss if threshold keys are destroyed simultaneously.
MPC custody platforms have gained institutional adoption particularly among professional custodians seeking to combine maximum security with operational flexibility and blockchain compatibility. Leading MPC providers implement additional security features including dynamic key share refresh enabling periodic key rotation without changing blockchain addresses, policy engines defining complex authorization rules based on transaction characteristics, and integration with hardware security modules protecting individual key shares with tamper-resistant security. The computational overhead of MPC signing represents a tradeoff against enhanced security, though modern implementations achieve signing latency measured in seconds making them viable for most custody applications including time-sensitive escrow releases.
Smart Contract-Based Escrow in Digital Asset Management
Smart contracts enable programmable escrow arrangements where asset release conditions are encoded in verifiable code executed automatically by blockchain networks without requiring trusted intermediaries. This automation creates “trustless” escrow where parties rely on cryptographic verification and transparent code logic rather than custodian integrity, reducing intermediary dependencies while enabling complex conditional release logic impossible with traditional manual escrow. Smart contract escrow represents a paradigm shift in how custody and conditional transfers operate, though it introduces distinct security considerations and operational challenges requiring careful implementation.
The fundamental architecture of smart contract escrow involves deploying contracts that hold deposited assets, implement release condition logic, provide interfaces for condition verification, and enable authorized parties to trigger release when appropriate. Simple escrow contracts might release assets after a time period elapses, upon receiving oracle confirmation of external events, or when designated parties provide approval signatures. Complex implementations support multi-stage releases, partial distributions based on milestone completion, automatic refunds if deadlines expire, and integration with dispute resolution mechanisms including arbitration or governance voting.
Common Smart Contract Escrow Patterns
Time-Locked Escrow
Assets locked until specific timestamp or block number, then automatically releasable by designated recipient without requiring ongoing custodian involvement. Useful for vesting schedules, delayed payments, and deadline-based deliverables. Can include early release mechanisms requiring multi-party approval if parties agree to accelerate timeline. Simple to implement and audit with minimal attack surface. Common in token vesting, streaming payments, and scheduled transfers.
Milestone-Based Release
Funds released incrementally as project milestones are verified and approved. Buyer deposits full payment, with portions released as seller demonstrates completion through oracle inputs, multi-party confirmation, or verifiable on-chain events. Protects buyers from non-delivery while providing sellers progressive payment. Requires clear milestone definitions and verification mechanisms. Used extensively in freelance payments, development contracts, and phased deliverables. Can include dispute windows and arbitration escalation.
Atomic Swap Escrow
Cryptographic hash time-locked contracts enabling trustless cross-chain or same-chain asset exchanges without intermediaries. Party A locks assets with hash of secret, Party B locks their assets with same hash, Party A reveals secret to claim B’s assets, secret automatically unlocks A’s assets for Party B. Either both exchanges complete or both revert, preventing partial completion. Eliminates custodian risk entirely through cryptographic protocols. Commonly used for cryptocurrency exchanges, cross-chain transfers, and OTC trading.
Oracle-Dependent Conditional Release
Release triggered by external data feeds from blockchain oracles providing real-world information. Examples include insurance payouts based on weather data, sports betting settlements based on game outcomes, supply chain payments upon delivery confirmation, or commodity trades settling at market prices. Relies on oracle security and data accuracy. Decentralized oracle networks like Chainlink provide redundancy and manipulation resistance. Requires careful oracle selection and data verification design to prevent manipulation or incorrect releases.
Multi-Party Approval Escrow
Implements multi-signature logic in smart contracts requiring threshold approvals before release. Buyer, seller, and arbitrator each hold signing keys with 2-of-3 required for release. Normal transactions complete with buyer-seller agreement, disputes escalate to include arbitrator. Can implement tiered approval requirements based on transaction amounts. Provides balance between automation and human oversight. Common in high-value transactions, complex deliverables, and situations requiring expert judgment for condition verification.
Automatic Refund Mechanisms
Built-in refund logic returning assets to depositor if release conditions aren’t satisfied by deadline. Protects buyers from indefinite fund lockup if sellers fail to deliver. Can implement partial refunds with penalties for late delivery or partial completion. Requires careful deadline setting balancing buyer protection with seller fairness. Common in crowdfunding, pre-sales, and time-sensitive transactions where failure to deliver by deadline justifies automatic cancellation.
Security risks in smart contract escrow demand rigorous attention as vulnerabilities can enable unauthorized asset release or permanent lockup. Critical security considerations include reentrancy attacks where malicious contracts recursively call escrow functions to drain assets, integer overflow/underflow enabling arithmetic exploits, access control flaws allowing unauthorized parties to trigger releases, oracle manipulation attacks providing false data to trigger conditions, and upgrade mechanism vulnerabilities if contracts include update functionality. Professional smart contract development requires formal verification, comprehensive testing, third-party security audits, bug bounty programs, and gradual deployment starting with limited value to validate security before scaling.
The immutability of blockchain creates challenges when escrow terms require modification after deployment or when unforeseen circumstances arise. Upgradeable contract patterns using proxy architectures enable logic updates while preserving asset storage and contract addresses, though they introduce centralization concerns and upgrade governance challenges. Alternative approaches include contract migration procedures moving assets to new escrow contracts with updated terms, though this requires party cooperation and creates operational complexity. Best practices favor deploying new escrow contracts for each transaction rather than reusing single contracts across multiple unrelated escrows, limiting blast radius of vulnerabilities and providing clean state for each arrangement.
Gas cost optimization represents an important consideration for smart contract escrow, particularly on networks with high transaction fees like Ethereum mainnet. Efficient contract design minimizes storage operations, optimizes loop structures, leverages assembly for performance-critical sections, and batches related operations to reduce transaction count. Layer-2 solutions including Polygon, Arbitrum, and Optimism provide lower-cost environments for smart contract escrow while maintaining Ethereum security through periodic settlement to mainnet. The appropriate deployment strategy balances security requirements, cost sensitivity, and desired settlement finality based on escrow transaction characteristics and party preferences.
Institutional-Grade Security Standards for Asset Custody
Institutional digital asset custody requires adherence to rigorous security standards comparable to traditional financial custody while addressing blockchain-specific threats and operational requirements. These standards encompass technical controls, operational procedures, personnel qualifications, physical security, and independent verification through audits and certifications. Meeting institutional security expectations enables custody providers to serve regulated financial institutions, asset managers, and corporations requiring demonstrable security assurance and regulatory compliance for fiduciary responsibilities.
SOC 2 Type II certification has emerged as the baseline security standard for digital asset custodians, providing independent verification of control effectiveness across security, availability, processing integrity, confidentiality, and privacy domains. Type II audits assess not just control design but operational effectiveness over extended periods, typically six to twelve months, demonstrating sustained security rather than point-in-time compliance. Leading custodians undergo annual SOC 2 audits by reputable accounting firms, address identified control deficiencies, and make audit reports available to clients and prospects enabling due diligence validation of security claims.
Institutional Security Standards and Certifications
SOC 2 Type II Compliance
Service Organization Control reports validating security, availability, processing integrity, confidentiality, and privacy controls over 6-12 month audit periods. Conducted by independent CPA firms following AICPA standards. Type II examines both control design and operational effectiveness. Annual audits demonstrate sustained compliance. Reports detail control objectives, testing procedures, and identified exceptions. Enables clients to verify custodian security without conducting redundant audits. Industry standard for institutional custody providers serving regulated entities.
ISO 27001 Certification
International standard for information security management systems (ISMS) providing comprehensive framework for protecting sensitive information. Requires documented policies, risk assessments, control implementation, internal audits, and continuous improvement. Certification involves external auditor examination and surveillance audits maintaining certification. Demonstrates commitment to security best practices recognized globally. Particularly valued by international clients and European institutions familiar with ISO frameworks. Complements SOC 2 with broader organizational scope.
Regular Penetration Testing
Quarterly or semi-annual penetration tests by professional security firms attempting to exploit vulnerabilities in infrastructure, applications, and operational procedures. Tests cover network security, web applications, API endpoints, social engineering resistance, and physical security. Findings categorized by severity with remediation timelines. Retest validation ensuring fixes are effective. Red team exercises simulating sophisticated attackers test detection and response capabilities. Results inform security improvements and demonstrate proactive vulnerability management to clients and regulators.
Digital Contract Security Audits
Comprehensive third-party audits of all smart contracts by specialized blockchain security firms before deployment and after significant updates. Auditors examine code for common vulnerabilities, logic errors, economic attacks, and protocol-specific issues. Formal verification techniques mathematically prove critical properties. Bug bounty programs incentivize ongoing vulnerability discovery. Public audit reports demonstrate transparency and enable client verification. Leading firms include Trail of Bits, ConsenSys Diligence, OpenZeppelin, CertiK, and Quantstamp with proven track records.
Crime Insurance Coverage
Comprehensive insurance policies covering theft, hacking, employee dishonesty, and operational errors with coverage limits from $100M to $500M+ from specialized insurers. Policies require custodians maintain specified security standards as coverage prerequisites. Coverage scope includes hot and cold wallet holdings, key compromise scenarios, and certain operational failures. Deductibles, exclusions, and claims procedures clearly documented. Multiple insurers distribute risk reducing dependency on single carrier. Annual policy renewals require security audits validating continued compliance with insurance requirements.
Regulatory Examinations
Regular examinations by financial regulators including state banking departments, FinCEN, FCA, VARA, or provincial securities commissions depending on licensing. Examiners review AML/KYC procedures, capital adequacy, operational controls, customer protection measures, and compliance with license conditions. Examination findings require corrective action plans with follow-up verification. Demonstrates regulatory oversight and accountability. Clean examination history indicates operational competence and regulatory cooperation. Examination readiness requires comprehensive documentation and control evidence.
Physical security measures protect hardware security modules, backup key material, and infrastructure hosting custody operations. Institutional facilities implement layered security including perimeter controls with fencing and surveillance, building access restrictions using badge systems and guards, server room environmental controls maintaining temperature and humidity, fire suppression systems protecting against equipment damage, and biometric access controls limiting critical system access to authorized personnel. Geographic distribution of key material and infrastructure across multiple secure facilities provides resilience against natural disasters, targeted attacks, or localized operational failures.
Personnel security begins with comprehensive background checks for all employees with access to custody systems or sensitive information, including criminal history verification, employment verification, credit checks, and reference validation. Ongoing security awareness training ensures staff understand threats, recognize social engineering attempts, follow security protocols, and report suspicious activities. Separation of duties prevents any individual from independently compromising security, with critical operations requiring collaboration between multiple employees. Access recertification processes periodically review and validate that access rights remain appropriate for current job responsibilities.
Incident response capabilities enable rapid detection, containment, investigation, and recovery from security events. Institutional custodians maintain 24/7 security operations centers monitoring systems, transaction patterns, and threat intelligence for anomalous activity suggesting compromise. Documented incident response plans define roles, escalation procedures, communication protocols, containment strategies, evidence preservation, and recovery procedures. Regular tabletop exercises and simulations test response capabilities and identify procedural gaps. Post-incident reviews analyze root causes, implement corrective actions, and update procedures preventing recurrence.
Compliance, KYC, and Regulatory Requirements in Custodial Escrow
Regulatory compliance represents a critical operational dimension for digital asset custody providers, particularly those offering escrow services across multiple jurisdictions. The regulatory landscape for digital asset custody varies significantly across markets, with the United States, United Kingdom, United Arab Emirates, and Canada each implementing distinct licensing requirements, operational standards, and ongoing obligations. Understanding and adhering to applicable regulations enables legal operation, provides customer protections, and facilitates institutional adoption by regulated entities requiring compliant custody partners.
In the United States, digital asset custodians may require state money transmitter licenses in each state where they serve customers, New York’s BitLicense for operations involving New York residents, federal registration as money services business with FinCEN, or trust company charters from states like South Dakota, Wyoming, or New York offering specialized digital asset trust frameworks. The regulatory pathway depends on business model specifics, with qualified custodian status under Investment Advisers Act requiring additional capital, operational, and examination requirements. Multi-state operations create complex compliance obligations requiring coordination across numerous state regulators with varying requirements and examination schedules.
| Jurisdiction | Primary Requirements | Licensing Authority | Key Obligations |
|---|---|---|---|
| United States | Money transmitter licenses, trust company charter, or qualified custodian status; FinCEN MSB registration; state-specific requirements | State banking departments, FinCEN, SEC for qualified custodians, NYDFS for BitLicense | AML program, SAR filing, capital requirements, cybersecurity standards, consumer protection, regular examinations |
| United Kingdom | FCA authorization for cryptoasset activities; compliance with Money Laundering Regulations; registration as cryptoasset business | Financial Conduct Authority (FCA), HM Revenue & Customs for MLR registration | Financial crime controls, customer due diligence, transaction monitoring, senior manager accountability, financial promotions compliance |
| UAE (Dubai) | VARA licensing for virtual asset service providers; DFSA authorization for DIFC operations; compliance with UAE AML framework | Virtual Assets Regulatory Authority (VARA), Dubai Financial Services Authority (DFSA) | AML/CFT controls, customer protection, market conduct standards, operational resilience, technology governance, ongoing supervision |
| Canada | Provincial securities registration for custody of securities; MSB registration with FINTRAC; compliance with PCMLTFA | Provincial securities commissions (OSC, BCSC, AMF), FINTRAC, CSA for securities custody | AML compliance program, client identification, record keeping, suspicious transaction reporting, cybersecurity safeguards |
Know-your-customer (KYC) verification forms the foundation of compliance programs, requiring custodians to collect and verify customer identity information, understand business nature and expected activity patterns, assess money laundering and terrorist financing risks, and maintain current customer information through periodic updates. KYC procedures typically include collection of government-issued identification, proof of address documentation, beneficial ownership disclosure for entities, sanctions screening against OFAC and other watchlists, and enhanced due diligence for higher-risk customers including politically exposed persons, customers from high-risk jurisdictions, or complex corporate structures obscuring ultimate beneficial ownership.
Anti-money laundering (AML) programs implement ongoing monitoring detecting and reporting suspicious activity that may indicate money laundering, terrorist financing, fraud, or other financial crimes. Transaction monitoring systems analyze patterns including rapid movement of funds, structuring to avoid reporting thresholds, transactions inconsistent with customer profiles, and connections to known criminal entities. Suspicious activity triggers enhanced review and potentially suspicious activity reports (SARs) filed with FinCEN in the United States, the National Crime Agency in the UK, the Financial Intelligence Unit in UAE, or FINTRAC in Canada. Custodians must balance effective financial crime detection with customer privacy and operational efficiency.
Travel rule compliance requires custodians transmitting cryptocurrency to collect and share originator and beneficiary information with counterparty financial institutions for transactions exceeding specified thresholds, typically $1,000 or $3,000 depending on jurisdiction. This requirement, derived from traditional wire transfer regulations, presents technical challenges in decentralized blockchain environments lacking standardized information exchange protocols. Industry solutions including Travel Rule Universal Solution Tool (TRUST) and others facilitate inter-custodian information exchange, though implementation remains complex particularly for transactions involving non-custodial wallets or unhosted addresses where beneficiary information may be unavailable.
Record keeping and reporting obligations require custodians maintain comprehensive documentation of customer identities, transaction histories, compliance decisions, and suspicious activity investigations for specified retention periods, typically five to seven years. Regulatory reporting includes currency transaction reports (CTRs) for large cash transactions in the United States, cross-border electronic funds transfer reports in Canada, and various other periodic and event-driven reports depending on jurisdiction and license type. Accurate reporting requires robust data management systems capturing required information, generating reports in prescribed formats, and ensuring timely submission to regulatory authorities.
Risk Management and Asset Protection Strategies
Comprehensive risk management frameworks enable digital asset custodians to identify, assess, monitor, and mitigate diverse threats affecting custody security and operational integrity. Effective risk management extends beyond cybersecurity to encompass operational risks from process failures or human error, counterparty risks from third-party dependencies, liquidity risks affecting ability to meet withdrawal demands, regulatory risks from compliance failures or regulatory changes, reputational risks from security incidents or service quality issues, and systemic risks from broader market disruptions or infrastructure failures.
Cybersecurity risk represents the most prominent threat to digital asset custody, with attackers persistently targeting custodians holding valuable cryptocurrency and token holdings. Attack vectors include network intrusions exploiting infrastructure vulnerabilities, spear phishing targeting employees with privileged access, insider threats from malicious or negligent personnel, supply chain attacks compromising third-party software or services, distributed denial of service disrupting operations, and social engineering manipulating staff into unauthorized actions. Defense-in-depth strategies implement multiple protective layers ensuring security despite individual control failures.
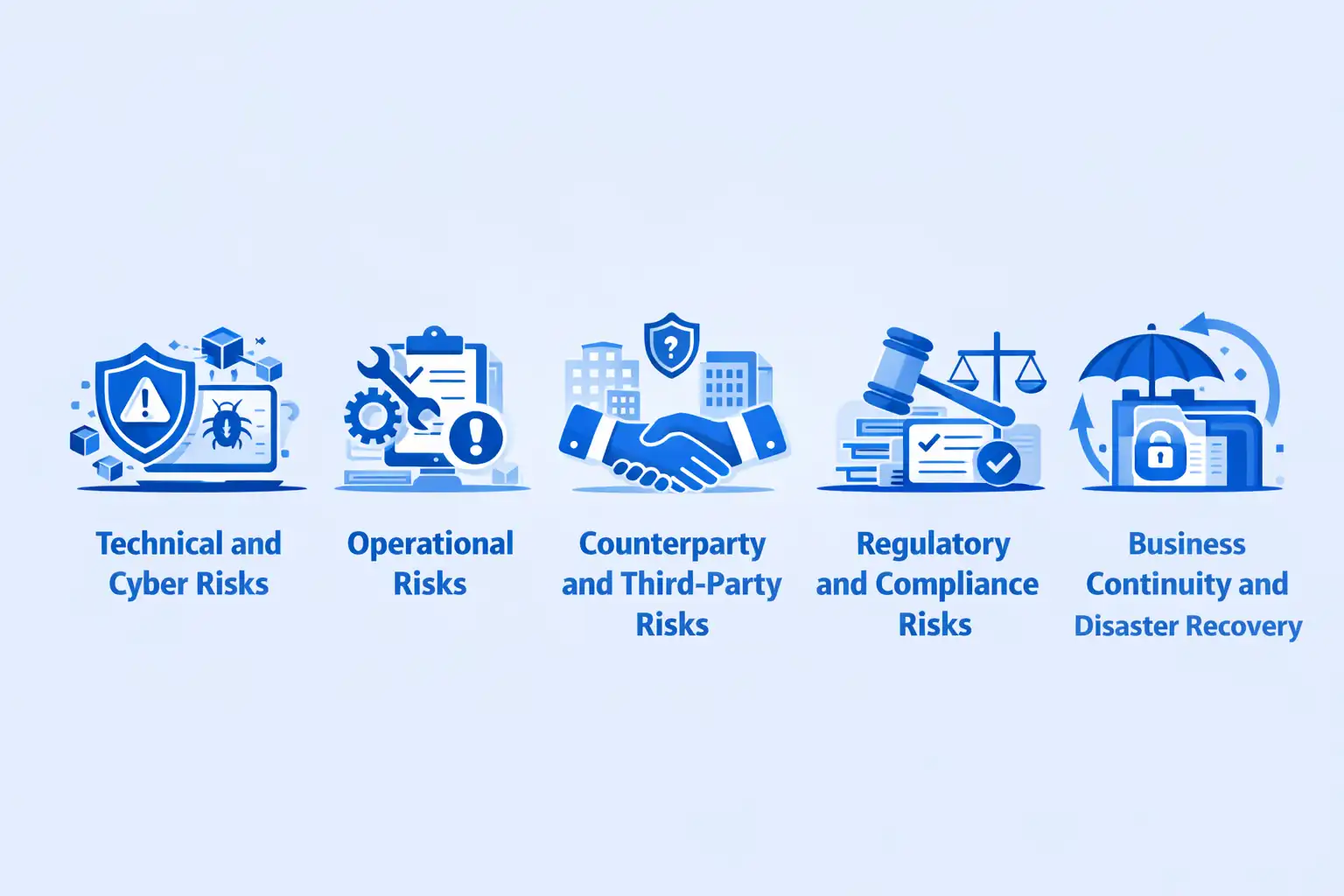
Digital Asset Custody Risk Framework
Technical and Cyber Risks
Threats: Hacking attempts, private key compromise, smart contract vulnerabilities, infrastructure failures, software bugs, blockchain reorganizations, cryptographic weaknesses.
Mitigations: Hardware security modules, cold storage, multi-signature controls, penetration testing, bug bounties, formal verification, redundant infrastructure, incident response capabilities, comprehensive insurance coverage.
Operational Risks
Threats: Human error in transaction processing, inadequate procedures, insufficient training, key management failures, backup failures, process breakdowns, inadequate capacity, documentation gaps.
Mitigations: Standardized procedures, comprehensive training, maker-checker workflows, transaction simulations, regular backup testing, capacity planning, process automation, continuous improvement programs, operational audits.
Counterparty and Third-Party Risks
Threats: Vendor security breaches, service provider failures, blockchain protocol vulnerabilities, oracle data manipulation, exchange counterparty defaults, insurance non-payment.
Mitigations: Vendor due diligence, contractual protections, diversification across providers, protocol security assessment, decentralized oracle networks, counterparty limits, insurance from multiple carriers, ongoing monitoring of third-party risk exposure.
Regulatory and Compliance Risks
Threats: License violations, AML/KYC failures, unauthorized activity, inadequate customer protection, regulatory changes, cross-border compliance gaps, examination findings.
Mitigations: Comprehensive compliance programs, legal counsel engagement, regulatory relationship management, compliance monitoring systems, staff training, multi-jurisdictional expertise, regulatory change tracking, examination readiness, corrective action responsiveness.
Business Continuity and Disaster Recovery
Threats: Natural disasters, facility failures, prolonged outages, pandemic impacts, key personnel loss, catastrophic security incidents, systemic market disruptions.
Mitigations: Geographic redundancy, backup key material in multiple locations, alternative facility arrangements, cross-trained personnel, documented recovery procedures, regular testing, crisis communication plans, pandemic preparedness, insurance covering business interruption.
Liquidity risk management ensures custodians can meet withdrawal requests during normal operations and stress scenarios. While digital asset custody fundamentally involves holding assets rather than deploying them, custodians offering additional services including staking, lending, or liquidity provision must carefully manage liquidity ensuring sufficient immediately available assets to satisfy redemption demands. Liquidity stress testing models extreme scenarios including simultaneous large withdrawals, market panic driving mass redemptions, or infrastructure failures preventing access to portions of holdings. Contingency funding plans define liquidity sources including cold storage withdrawal procedures, credit facilities from traditional banks, and potential asset liquidation strategies if normal liquidity proves insufficient.
Concentration risk arises when custody portfolios become overly dependent on specific blockchains, protocols, or asset types creating correlated exposure to shared vulnerabilities. Diversification across multiple blockchain networks reduces exposure to protocol-specific risks, though it increases operational complexity requiring expertise across diverse technical environments. Asset concentration limits prevent excessive exposure to individual tokens whose price volatility or security issues could disproportionately impact portfolio values. For custodians offering services beyond pure custody, exposure limits on DeFi protocols, staking operations, or lending activities prevent outsized losses from individual protocol failures.
Insurance represents a critical risk transfer mechanism providing financial protection despite robust preventive controls. Comprehensive digital asset insurance policies cover theft, hacking, employee dishonesty, and certain operational errors with coverage limits scaled to assets under custody. Policy terms require custodians maintain specified security standards including cold storage percentages, multi-signature controls, regular audits, and operational procedures as coverage prerequisites. Claims processes define notification requirements, loss documentation, investigation cooperation, and potential recovery obligations if stolen assets are later recovered. Insurance complements rather than replaces security controls, with premiums reflecting custodian security posture and claims history.
Use Cases of Digital Asset Custody in Modern Asset Management
Digital asset custody enables diverse applications across traditional finance, decentralized protocols, and emerging digital economies. Professional custody infrastructure has become essential for institutional participation in cryptocurrency markets, with use cases spanning investment management, corporate treasury, payment processing, decentralized finance, tokenized securities, and specialized escrow arrangements. Each application leverages custody’s core security and compliance capabilities while demanding specific features, integrations, or operational characteristics suited to particular business models and regulatory environments.
Investment management represents a primary custody use case as asset managers, hedge funds, and family offices allocate capital to digital assets requiring secure storage, regulatory compliance, and operational integration with existing portfolio management systems. Custody platforms serving investment managers provide portfolio analytics, performance reporting, tax documentation, integration with order management systems, and support for diverse investment strategies including long-only holdings, trading strategies, staking for yield, and DeFi protocol participation. Qualified custodian designation enables investment advisers to satisfy SEC custody rule requirements, facilitating digital asset inclusion in registered fund products and separately managed accounts.
Digital Asset Custody Application Scenarios
Institutional Investment
- Asset manager cryptocurrency exposure
- Hedge fund trading strategies
- Pension fund digital asset allocations
- Endowment portfolio diversification
- Family office wealth preservation
- Registered investment company products
Corporate Treasury Management
- Bitcoin treasury reserve holdings
- Stablecoin liquidity management
- Cross-border payment facilitation
- Cryptocurrency revenue acceptance
- Blockchain-based reward programs
- Digital asset compensation strategies
Exchange and Trading Platforms
- Customer asset segregation
- Hot wallet operational liquidity
- Cold storage security infrastructure
- Proof of reserves verification
- Regulatory custody compliance
- Institutional client separation
Tokenized Securities
- Real estate token custody
- Equity token holder services
- Debt instrument management
- Fund share tokenization
- Regulatory transfer restrictions
- Corporate action processing
Web3 & DeFi Protocols
- Protocol treasury asset custody
- DAO-controlled fund management
- Liquidity pool reserve protection
- Smart contract-controlled wallets
- Governance-triggered fund movements
- Risk-managed DeFi participation
Government & Regulated Entities
- Central bank digital asset custody
- Tokenized bond issuance programs
- Public sector blockchain initiatives
- Regulatory sandbox custody solutions
- State-backed digital asset reserves
- Compliance-first custody infrastructure
Corporate treasury applications have expanded as public companies including MicroStrategy, Tesla, Block, and others allocate portions of corporate reserves to Bitcoin and other digital assets. Treasury custody requires enterprise-grade security, multi-signature authorization aligning with corporate governance structures, integration with accounting systems for accurate financial reporting, and regulatory compliance supporting SEC disclosure obligations. Stablecoin custody enables corporations to maintain dollar-denominated liquidity in blockchain-native form facilitating instant cross-border payments, decentralized finance participation, or rapid conversion to other digital assets without traditional banking intermediaries and settlement delays.
Exchange platforms rely heavily on custody infrastructure segregating customer assets from operational holdings, implementing hot/cold wallet architectures balancing liquidity and security, and providing proof of reserves demonstrating assets backing customer balances. Recent exchange failures including FTX have heightened focus on custody transparency, asset segregation, and independent verification. Third-party custody solutions offer exchanges credibility advantages by demonstrating customer assets are held separately from exchange operational control, reducing commingling risks and providing regulatory assurance in jurisdictions requiring segregated customer asset custody.
Escrow services leverage custody infrastructure for diverse transaction types including OTC cryptocurrency trades between institutional counterparties, tokenized real estate sales, merger and acquisition payments, intellectual property licensing, freelance service payments, and dispute resolution scenarios. Digital asset escrow combines traditional escrow principles with blockchain-specific capabilities including smart contract automation, global accessibility, rapid settlement, transparent audit trails, and programmable release conditions. The 24/7 nature of cryptocurrency markets demands escrow services available beyond traditional business hours, with automated systems handling routine transactions while maintaining human oversight for complex situations or disputes.
DeFi protocol participation through institutional custody enables regulated entities to access decentralized lending, liquidity provision, and yield generation opportunities while maintaining compliance and security standards. Custodians providing DeFi access implement protocol whitelisting approving specific smart contracts after security review, transaction simulation preventing unauthorized operations, automated monitoring detecting abnormal protocol behavior, and position management supporting rebalancing and risk management. This controlled DeFi access enables institutional participation in decentralized finance while addressing regulatory concerns about custody, compliance, and operational controls.
Benefits of Integrated Custody Solutions for Escrow Services
Integrated digital asset custody platforms combining secure storage, escrow functionality, compliance automation, and operational tools provide comprehensive solutions addressing the complete lifecycle of digital asset transactions. Integration eliminates friction from coordinating multiple specialized providers, reduces operational complexity through unified interfaces, ensures consistent security standards across functions, and enables sophisticated workflows leveraging multiple capabilities simultaneously. The benefits of integration become particularly apparent in complex scenarios requiring coordination between custody, escrow, compliance, and transaction execution functions.
Operational efficiency improvements from integrated custody solutions include single onboarding processes covering both general custody and escrow services, unified user interfaces reducing training requirements and operational errors, consolidated reporting providing comprehensive views across holdings and transactions, shared compliance infrastructure avoiding duplicate KYC/AML procedures, and streamlined workflows enabling direct transitions between custody and escrow states without external transfers. These efficiencies reduce operational overhead, accelerate transaction execution, and minimize coordination complexity particularly for organizations managing substantial digital asset volumes across multiple use cases.
Integrated Custody Platform Advantages
Critical Value
Consistent security controls across custody and escrow functions eliminate gaps from disparate systems while enabling centralized monitoring and incident response.
Critical Value
Shared KYC/AML infrastructure serves both custody and escrow, reducing duplicate verification while ensuring consistent compliance across all transactions.
High Value
Unified interfaces and workflows reduce training requirements, minimize coordination overhead, and accelerate transaction execution through seamless function integration.
High Value
Consolidated infrastructure reduces total cost of ownership versus separate custody and escrow providers through shared resources and economies of scale.
Significant Value
Unified reporting provides comprehensive visibility into holdings, escrow transactions, compliance status, and operational metrics through single dashboard.
Significant Value
Integrated platforms scale efficiently supporting growing asset volumes and transaction counts while enabling easy adoption of new capabilities as business needs evolve.
Security advantages of integrated platforms include centralized key management reducing attack surface versus multiple independent systems, consistent access controls and authentication across functions, unified security monitoring detecting threats holistically rather than function-specific blind spots, and coordinated incident response enabling rapid containment across all affected systems. Integration also facilitates advanced security features like automatic escrow fund movement to cold storage during hold periods, dynamic security policies adjusting based on transaction characteristics, and behavioral analytics leveraging patterns across custody and escrow activities to detect anomalies suggesting compromise or fraud.
Data integration enables sophisticated analytics and reporting impossible with siloed systems including comprehensive portfolio views combining custody holdings and escrow transactions, performance attribution analyzing returns across investment and operational uses, compliance dashboards aggregating KYC status, transaction monitoring alerts, and regulatory reporting across all activities, and business intelligence identifying patterns, trends, and optimization opportunities. These analytics support better decision-making, demonstrate regulatory compliance comprehensively, and provide stakeholders complete visibility into digital asset operations.[2]
API standardization within integrated platforms simplifies technical integration with external systems including accounting software, portfolio management platforms, ERP systems, and custom applications. Unified API access points reduce integration complexity versus connecting to multiple disparate providers, while consistent data formats and authentication mechanisms minimize development effort. Modern integrated custody platforms provide comprehensive API documentation, SDKs in popular programming languages, webhooks for event notifications, and sandbox environments enabling safe integration testing before production deployment.
Challenges in Scaling Secure Digital Asset Custody Systems
Scaling digital asset custody infrastructure to support institutional-grade operations serving thousands of customers managing billions in assets presents significant technical, operational, and organizational challenges. Growth strains custody systems across multiple dimensions including transaction throughput, data storage, customer onboarding velocity, support operations, compliance monitoring, and security monitoring. Successful scaling requires thoughtful architecture design, operational process optimization, technology selection balancing security with performance, and organizational capabilities supporting larger operational scope while maintaining service quality and security standards.
Technical scalability challenges begin with blockchain interaction infrastructure requiring robust node operations, transaction construction and broadcasting capabilities, confirmation monitoring, and state synchronization across multiple networks. Supporting 50+ blockchains demands substantial infrastructure including dedicated nodes for major networks, shared infrastructure for smaller chains, RPC endpoint management, and monitoring systems detecting node failures or synchronization issues. Transaction throughput requirements scale with customer activity, potentially requiring thousands of blockchain transactions daily during peak periods while maintaining security standards preventing unauthorized operations despite operational velocity.
Critical Scaling Challenges and Solutions
Database and Data Management Scaling
Challenge: Transaction histories, customer records, compliance documentation, and audit logs accumulate rapidly creating petabyte-scale data management requirements.
Solutions: Distributed database architectures, data partitioning strategies, archival procedures moving historical data to cost-effective storage, caching layers reducing database load, read replicas distributing query traffic, query optimization, and index management ensuring responsive performance despite growing data volumes.
Key Management at Scale
Challenge: Managing cryptographic keys for thousands of customers across dozens of blockchain networks while maintaining security, availability, and operational efficiency.
Solutions: Hierarchical deterministic wallet architectures deriving customer keys from master seeds, key pool management preemptively generating addresses, automated key rotation procedures, HSM clustering distributing cryptographic operations, and key lifecycle management automating generation, storage, usage tracking, and retirement across massive key inventories.
Compliance Monitoring Automation
Challenge: Manual compliance review becomes impossible at scale requiring automated transaction monitoring, sanctions screening, and risk assessment across thousands of customers and millions of transactions.
Solutions: Machine learning models detecting suspicious patterns, automated sanctions screening against updated watchlists, risk scoring algorithms prioritizing high-risk transactions for manual review, workflow automation routing alerts to appropriate personnel, and continuous monitoring systems operating 24/7 without manual supervision while escalating genuine risks appropriately.
Customer Support Scaling
Challenge: Supporting thousands of customers across time zones, languages, and technical sophistication levels while maintaining response quality and resolution times.
Solutions: Tiered support models with self-service documentation, chatbot triage, technical support specialists, and relationship managers for institutional clients. Knowledge base development capturing common issues and resolutions. Support ticket systems tracking issues through resolution. Performance metrics monitoring response times, resolution rates, and customer satisfaction enabling continuous improvement.
Organizational Growth Management
Challenge: Maintaining culture, security consciousness, operational excellence, and coordination as organizations grow from dozens to hundreds of employees.
Solutions: Comprehensive onboarding programs instilling security culture, documented procedures providing consistent operational guidance, regular training maintaining skills and awareness, clear organizational structures defining responsibilities, cross-functional collaboration mechanisms, and leadership development preparing personnel for expanded roles as organizations scale.
Performance optimization becomes critical as custody platforms scale, requiring careful attention to system architecture, code efficiency, resource utilization, and operational procedures. Microservices architectures decompose monolithic applications into specialized services scaling independently based on load patterns, with separate scaling for transaction processing, customer onboarding, reporting generation, and API services. Caching strategies reduce database and blockchain node load by storing frequently accessed data in memory, while content delivery networks accelerate global access to static resources. Load balancing distributes traffic across multiple servers preventing bottlenecks and providing redundancy ensuring continued operations despite individual server failures.
Cost management represents another scaling dimension as infrastructure, personnel, licensing, insurance, and compliance expenses grow with operational scope. Efficient resource utilization through autoscaling, reserved instance pricing for predictable workloads, and spot instances for fault-tolerant batch processing optimizes cloud infrastructure costs. Automation reduces personnel requirements for routine operations enabling human resources to focus on high-value activities requiring judgment and expertise. Strategic technology selection balances feature richness with total cost of ownership, avoiding over-engineering while ensuring adequate capabilities supporting current and anticipated future requirements.
Security scaling challenges include maintaining consistent security posture despite growing attack surface from additional systems, personnel, and complexity. Security automation through infrastructure as code, automated vulnerability scanning, configuration management, and security information and event management (SIEM) systems enables security monitoring keeping pace with operational growth. Security team scaling requires not just adding personnel but developing specialized expertise across diverse domains including blockchain security, infrastructure security, application security, compliance, and incident response. Regular security assessments and penetration testing validate that security controls remain effective despite organizational and technical evolution.
Custody Infrastructure for Cross-Border and High-Value Escrow
Cross-border digital asset escrow leverages blockchain’s borderless nature to facilitate international transactions without traditional correspondent banking relationships, foreign exchange complexity, or multi-day settlement delays. This capability creates significant value for global commerce, enabling efficient escrow arrangements between parties in different countries, supporting international M&A transactions, facilitating cross-border real estate transactions, and enabling global supply chain finance. However, cross-border operations introduce jurisdictional complexity, regulatory coordination requirements, and operational considerations demanding specialized custody infrastructure and expertise.
Multi-jurisdictional compliance represents the primary challenge for cross-border escrow, requiring custodians to understand and implement regulatory requirements across all relevant jurisdictions including where transacting parties are located, where the custodian operates, where assets are deemed to be held, and potentially where underlying assets represented by tokens are located. A transaction between a US buyer and UK seller using a UAE-licensed custodian for Bitcoin escrow may implicate regulations in all three jurisdictions plus potentially others depending on specific circumstances. Custodians serving cross-border transactions must maintain compliance expertise, legal counsel relationships, and operational capabilities across multiple regulatory regimes simultaneously.
Cross-Border Escrow Infrastructure Requirements
Multi-Jurisdictional Licensing
- Licenses covering key markets (USA, UK, UAE, Canada)
- Understanding of cross-border regulatory interactions
- Relationships with regulators across jurisdictions
- Legal counsel in multiple countries
- Compliance teams with international expertise
Language and Localization
- Multi-language platform interfaces and documentation
- Local currency pricing and reporting options
- Time zone coverage for global operations
- Culturally appropriate communication styles
- Local payment method integration
Settlement Infrastructure
- 24/7 blockchain operations supporting global markets
- Automated settlement eliminating time zone delays
- Multi-currency support including stablecoins
- Fiat on/off ramps in multiple countries
- FX rate transparency and execution
International Dispute Resolution
- Clear governing law and jurisdiction clauses
- International arbitration mechanisms
- Multi-jurisdictional enforcement capabilities
- Cultural sensitivity in conflict resolution
- Translation services for proceedings
Cross-Border Compliance Controls
- Jurisdiction-based transaction screening
- Sanctions and watchlist enforcement
- Dynamic compliance rule updates
- AML reporting across multiple regulators
- Audit-ready transaction traceability
Data Residency and Privacy Management
- Country-specific data storage requirements
- GDPR and international privacy compliance
- Controlled cross-border data transfers
- Encryption standards aligned with local laws
- Regulator-accessible audit data segregation
High-value escrow transactions require enhanced security measures, operational controls, and risk management procedures proportionate to asset values potentially reaching hundreds of millions of dollars. Institutional counterparties in major transactions demand demonstrable security through SOC 2 certification, insurance coverage adequate to transaction size, third-party validation of security controls, and proven track records managing similar values. Enhanced due diligence processes for high-value transactions include heightened KYC verification, source of funds investigation, beneficial ownership transparency, and potentially sanctions screening beyond standard automated procedures.
Transaction structuring for high-value escrow often employs multiple layers of protection including insurance coverage through multiple carriers distributing risk, multi-signature controls requiring numerous independent approvals, time-locked releases preventing immediate execution allowing final verification, partial releases staging distributions reducing single-point failure risks, and legal opinions confirming enforceability of escrow arrangements. These protections create redundancy ensuring transaction completion despite individual control failures while providing stakeholders confidence that substantial asset values receive appropriate safeguards throughout escrow periods.
Reputation and track record become particularly important for high-value escrow as counterparties seek assurance that custodians possess experience, expertise, and operational capabilities managing transactions of comparable scale and complexity. Custodians building high-value escrow practices cultivate references from satisfied clients, publish case studies demonstrating capabilities, obtain relevant certifications and accreditations, maintain transparent communication about processes and controls, and invest in relationship development with legal advisors, accountants, and other professionals serving high-net-worth clients and institutional counterparties who influence custody provider selection in major transactions.
Emerging Trends in Digital Asset Custody and Escrow Technology
The digital asset custody landscape continues evolving rapidly as technological innovations, regulatory developments, and market maturation drive new capabilities and business models. Emerging trends reshaping custody and escrow include artificial intelligence integration enhancing security and operations, quantum-resistant cryptography preparing for future threats, decentralized custody protocols, institutional DeFi integration, tokenization of traditional assets, and regulatory harmonization enabling global operations. Understanding these trends enables custody providers and users to anticipate future capabilities and prepare for ongoing industry evolution.
Artificial intelligence and machine learning applications in custody include fraud detection systems analyzing transaction patterns to identify anomalous activity suggesting compromise or unauthorized access, risk scoring algorithms assessing customer and transaction risks enabling proportionate due diligence, chatbot customer support handling routine inquiries freeing human agents for complex issues, predictive analytics anticipating operational needs and optimizing resource allocation, and automated compliance monitoring detecting potential violations requiring investigation. AI integration enhances operational efficiency while potentially improving security and compliance effectiveness beyond manual capabilities.
Future Directions in Digital Asset Custody
Quantum-Resistant Cryptography
Quantum computing advances threaten current cryptographic algorithms protecting digital assets, driving development of post-quantum cryptographic schemes resistant to quantum attacks. Leading custody providers are beginning implementations of quantum-resistant signature schemes, hybrid approaches combining classical and post-quantum algorithms, and preparing migration strategies for eventual quantum threats. Proactive quantum preparation protects long-term asset security as quantum computing capabilities mature over coming decades.
Institutional DeFi Integration
Custody platforms increasingly provide controlled access to decentralized finance protocols enabling institutional participation in lending, liquidity provision, and yield generation. Advanced implementations include protocol whitelisting, automated risk monitoring, position management tools, and compliance overlays ensuring DeFi participation meets institutional risk and regulatory requirements. This institutional DeFi custody bridges traditional finance and decentralized protocols while maintaining security and compliance standards.
Traditional Asset Tokenization
Custody infrastructure is expanding to support tokenized traditional assets including real estate, private equity, bonds, commodities, and art. These tokenized assets require custody solutions combining blockchain security with traditional asset servicing including corporate actions, distributions, regulatory compliance, and investor communications. Unified custody platforms managing both native digital assets and tokenized traditional assets create comprehensive solutions for diversified institutional portfolios.
Regulatory Framework Maturation
Global regulatory frameworks for digital asset custody continue maturing with increased clarity, standardization, and harmonization across jurisdictions. Markets in Crypto-Assets Regulation (MiCA) in Europe, comprehensive frameworks in Singapore and Switzerland, and evolving guidance in USA, UK, UAE, and Canada are creating more predictable regulatory environments. This maturation facilitates institutional adoption by reducing regulatory uncertainty while establishing consistent standards protecting investors and ensuring market integrity.
Enhanced Self-Custody Tools
Technology innovations are making self-custody more accessible and secure for sophisticated users through improved wallet interfaces, social recovery mechanisms, hardware wallet advances, and multi-device key management. Account abstraction on Ethereum and similar developments on other chains enable more flexible security models combining self-custody autonomy with usability improvements. These advances may shift balances between custodial and non-custodial approaches as self-custody becomes more practical for broader user bases.
Decentralized custody protocols attempt to combine benefits of professional custody with decentralization principles through distributed key management, threshold cryptography, and smart contract coordination. These hybrid approaches distribute custody responsibilities across multiple independent parties reducing single points of failure and censorship risks while maintaining professional security standards. However, decentralized custody introduces coordination complexity, governance challenges, and questions about legal accountability that must be resolved before institutional adoption at scale.
Interoperability standards enabling seamless custody operations across blockchain networks are emerging through initiatives including the Interledger Protocol, cross-chain bridge standards, and universal wallet interfaces. Enhanced interoperability reduces operational complexity for custodians supporting multiple networks while improving user experiences enabling unified portfolio management regardless of underlying blockchain diversity. Standardization efforts by industry organizations including the Global Digital Finance consortium and Crypto Council for Innovation aim to establish best practices and technical standards facilitating custody interoperability and operational consistency.
Future of Secure Escrow and Institutional Asset Management
The future of digital asset custody and escrow promises continued innovation, institutional adoption, and integration with traditional financial systems as blockchain technology matures and regulatory frameworks solidify. Institutional asset management increasingly incorporates digital assets as legitimate portfolio components, driving demand for custody infrastructure meeting fiduciary standards, regulatory requirements, and operational expectations comparable to traditional securities custody. This institutional adoption creates opportunities for specialized custody providers while raising performance, security, and compliance expectations across the industry.
The convergence of traditional and digital asset custody represents a significant trend as established financial institutions including banks, trust companies, and broker-dealers expand into digital asset services. These traditional institutions bring regulatory relationships, operational expertise, risk management frameworks, and client relationships that facilitate institutional adoption. Simultaneously, cryptocurrency-native custody providers are maturing their operations, obtaining traditional financial licenses, and building capabilities bridging digital and traditional asset classes. This convergence creates comprehensive custody solutions serving diversified portfolios across asset types.
Automation and programmability enabled by smart contracts and blockchain infrastructure will increasingly transform custody operations from manual processes to automated workflows. Smart contract-based custody enables programmable asset management including automated rebalancing, rule-based trading, algorithmic distribution of yield, and conditional transfers based on market conditions or external events. This automation reduces operational overhead, eliminates human error, enables sophisticated strategies previously impractical due to execution complexity, and creates new custody value propositions beyond simple asset storage.
Global accessibility represents both an opportunity and challenge for digital asset custody as blockchain enables truly borderless asset management while regulatory frameworks remain jurisdictionally fragmented. Future development may bring increased regulatory harmonization through international coordination, mutual recognition agreements, or standardized frameworks reducing compliance complexity for cross-border operations. Alternatively, persistent regulatory fragmentation may drive specialized custody models serving specific jurisdictional markets with limited cross-border capabilities.
The evolution of digital asset custody and escrow infrastructure reflects the broader maturation of blockchain technology from experimental innovation to institutional infrastructure supporting significant economic value. As custody solutions continue improving security, usability, compliance, and operational capabilities, they enable expanded use cases, institutional adoption, and integration with traditional finance. Organizations selecting custody partners today should evaluate not only current capabilities but also innovation roadmaps, regulatory adaptability, and strategic vision ensuring chosen partners can support evolving needs throughout multi-year relationships in this rapidly developing industry.
Drawing on eight years of experience serving clients across the United States, United Kingdom, United Arab Emirates, and Canada, we have witnessed digital asset custody transform from nascent infrastructure into sophisticated institutional platforms. The journey from early exchange hacks and custody failures to today’s SOC 2-certified, insured, multi-signature custody solutions demonstrates the industry’s remarkable progress. Yet significant opportunities remain as tokenization expands, institutional adoption accelerates, and custody infrastructure continues evolving to meet the sophisticated requirements of modern asset management in the digital age.
People Also Ask
Digital asset custody refers to the secure storage and management of cryptocurrency, tokens, NFTs, and other blockchain-based assets through specialized platforms that safeguard private keys and enable authorized transactions. Custodians employ advanced security measures including hardware security modules, multi-signature wallets, and cold storage to protect digital assets from theft, loss, or unauthorized access while providing institutional-grade infrastructure for asset management, regulatory compliance, and transaction execution across decentralized networks.
Custodial wallets are managed by third-party service providers who control the private keys and handle security on behalf of users, offering convenience and recovery options but requiring trust in the custodian. Non-custodial wallets give users complete control over their private keys and assets, providing maximum autonomy and eliminating counterparty risk but placing full responsibility for security and key management on the user. The choice depends on security preferences, technical expertise, and regulatory requirements.
Institutional-grade digital asset custody employs bank-level security including multi-signature authorization, hardware security modules, cold storage for majority holdings, comprehensive insurance coverage, 24/7 monitoring, and SOC 2 Type II certification. Leading custodians maintain 95-98% of assets in offline cold storage, implement geographic key distribution, conduct regular security audits, and provide crime insurance coverage up to $500 million or more. These measures create security standards comparable to traditional financial custody while addressing unique blockchain-specific vulnerabilities.
Digital asset custody providers must comply with jurisdiction-specific regulations including money transmitter licenses, trust company charters, or virtual asset service provider registrations depending on operational locations. In the USA, custodians may require state trust licenses or federal banking charters with FinCEN registration. UK custodians need FCA authorization, UAE requires VARA licensing in Dubai, and Canada mandates provincial securities registration. Requirements include AML/KYC procedures, capital adequacy, cybersecurity standards, and regular regulatory examinations.
Digital asset custody for escrow involves a neutral third-party custodian holding cryptocurrency or tokens until predetermined conditions are satisfied, protecting both parties in transactions. The custodian creates segregated accounts, implements multi-signature controls requiring authorization from relevant parties, verifies condition fulfillment through smart contracts or manual verification, and releases assets according to escrow terms. This structure provides security, reduces counterparty risk, enables dispute resolution, and creates transparent audit trails for complex transactions.
Digital asset custody platforms support diverse asset types including Bitcoin, Ethereum, and major cryptocurrencies, ERC-20 and other token standards, stablecoins like USDC and USDT, NFTs and digital collectibles, security tokens representing real-world assets, wrapped assets bridging different blockchains, and governance tokens for DeFi protocols. Advanced custodians offer multi-chain support spanning 50-200+ blockchain networks, enabling comprehensive portfolio management across the digital asset ecosystem with unified security and compliance frameworks.
Digital asset custody costs vary based on asset volume, service requirements, and provider tier, typically ranging from 0.05% to 2% annually of assets under custody. Enterprise solutions charge $5,000-$50,000 monthly base fees plus transaction fees of $10-$100 per operation and percentage-based fees on assets under management. Premium services including insurance, compliance support, staking, and white-glove service command higher fees. Some providers offer tiered pricing with volume discounts for holdings exceeding $10 million or $100 million.
Leading digital asset custodians maintain crime insurance policies covering theft, hacking, insider fraud, and key compromise with coverage limits ranging from $100 million to over $500 million from specialized insurers like Lloyd’s of London, Arch, and Coincover. Policies typically exclude market volatility losses and require custodians to maintain specific security standards. Insurance premiums reflect the custodian’s security posture, operational history, and coverage amounts, with some institutional clients requiring proof of insurance as a custody prerequisite.
Modern digital asset custody platforms offer extensive integration capabilities with traditional banking infrastructure, accounting systems, treasury management platforms, and portfolio management tools through APIs and standard protocols. Custodians provide fiat on-ramps and off-ramps, support wire transfers and ACH payments, generate reports compatible with enterprise accounting software, and integrate with tax reporting systems. This enables seamless workflows combining digital and traditional assets within unified operational frameworks meeting institutional requirements.
Reputable digital asset custodians structure holdings through bankruptcy-remote frameworks including qualified custodian designations, trust company charters, or special purpose vehicles ensuring client assets remain segregated from custodian corporate assets. In bankruptcy scenarios, client assets should be protected from creditor claims and returnable to rightful owners. However, asset recovery depends on proper legal structuring, accurate recordkeeping, and jurisdictional protections. This risk underscores the importance of selecting well-capitalized custodians with robust legal frameworks and regulatory oversight.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.






