Key Takeaways
- Blockchain technology protects transactions through decentralization, cryptography, and immutability, but it cannot protect your wallet access credentials.
- Your password is the single point of failure in an otherwise secure blockchain ecosystem. Weak passwords account for over 80% of crypto theft incidents.
- Two-factor authentication (2FA) adds a critical security layer that can prevent unauthorized access even when passwords are compromised.
- Private key management and seed phrase backup are development responsibilities that every blockchain project must address during execution.
- Phishing attacks remain the primary attack vector, targeting human behavior rather than blockchain infrastructure.
- Password managers and hardware wallets represent best practices for both individual users and enterprise blockchain deployments.
The blockchain industry has grown from a niche technology experiment to a global financial infrastructure handling trillions of dollars in transactions. Yet a surprising truth remains: the most sophisticated cryptographic system in history still depends on something as simple as your password. This creates a paradox that developers and users must understand.
When you build or use blockchain applications, you are working with technology that can resist nation-state level attacks on its core infrastructure. The distributed ledger, consensus mechanisms, and cryptographic foundations make direct attacks on the blockchain itself nearly impossible. However, the access point to your digital assets sits behind a password that might be guessable in seconds.
At Nadcab Labs, we have spent over 8 years developing blockchain solutions for enterprises and startups across multiple industries. Through this experience, we have observed that technical excellence in blockchain architecture means nothing if end-user security practices fail. This article breaks down both sides of this security equation from an execution and development perspective.
The Foundation: How Blockchain Actually Secures Your Assets
Before examining password vulnerabilities, you need to understand what blockchain does well. This knowledge helps developers build better systems and users make informed decisions about their security posture.
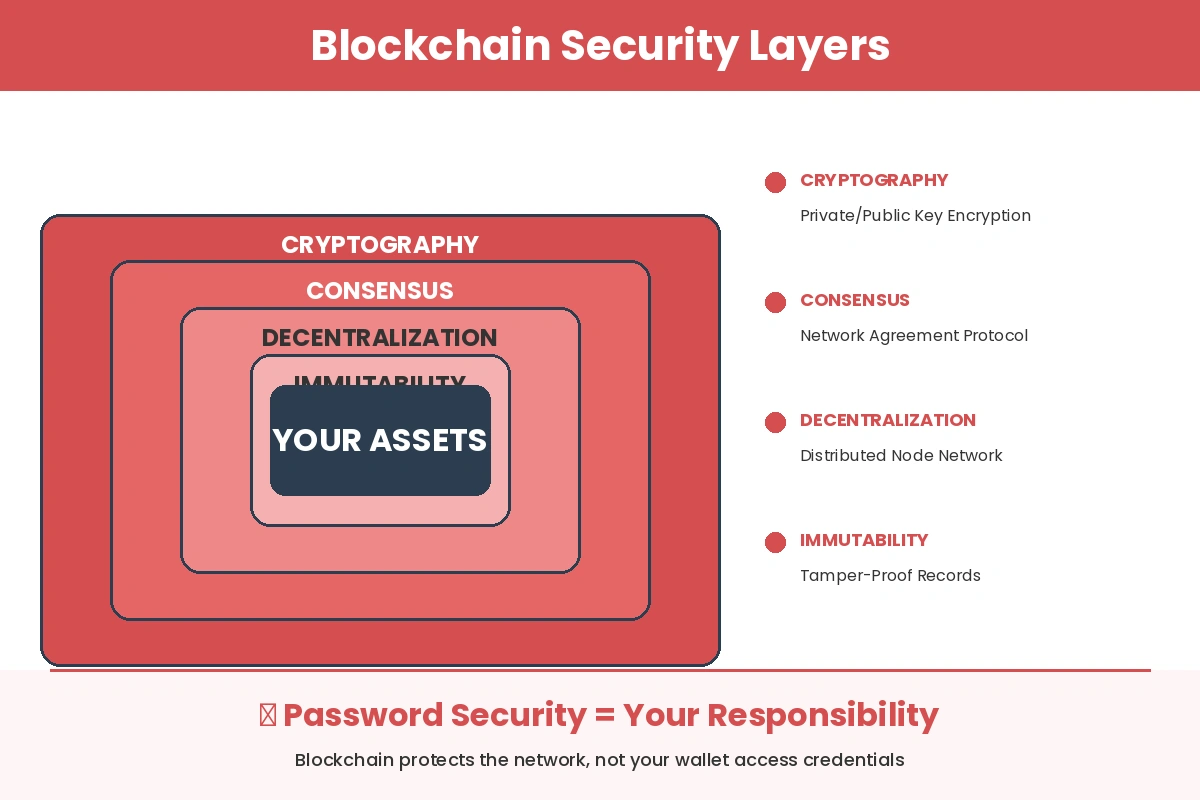
Blockchain security operates on multiple layers. Each layer addresses specific attack vectors and provides redundancy when other layers face challenges. The combination creates a system that has proven remarkably resistant to direct technical attacks since the launch of Bitcoin in 2009.
Decentralization: Removing the Single Point of Failure
Traditional financial systems store your data on centralized servers. If someone breaches that server, they potentially access millions of accounts. The 2017 Equifax breach exposed sensitive data of 147 million people through a single vulnerability in centralized infrastructure.
Blockchain eliminates this architectural weakness. Your transaction data exists across thousands of independent nodes worldwide. According to Wikipedia’s blockchain documentation, this distributed architecture means an attacker would need to simultaneously compromise the majority of network participants to alter any data.
For developers building on blockchain, this decentralization creates both opportunities and responsibilities. You gain inherent data integrity without building complex backup systems. However, you must design your applications to work within the constraints of distributed consensus, which affects transaction speed and cost structures.
The practical implication is significant. When Nadcab Labs architects a blockchain solution for enterprise clients, we leverage this distributed nature to eliminate single points of failure in data storage. The blockchain handles data integrity automatically, freeing development resources to focus on user experience and business logic.
Immutability: Why Past Transactions Cannot Be Changed
Once a transaction records on the blockchain, it becomes permanent. This immutability comes from cryptographic linking between blocks. Each block contains a hash of the previous block, creating a chain where altering any historical record would require recalculating every subsequent block.
The computational cost of such an attack grows exponentially with each new block added to the chain. On mature networks like Bitcoin or Ethereum, this cost exceeds the budget of even the most well-funded attackers. The math simply does not work in the attacker’s favor.
From an execution standpoint, immutability simplifies audit trails and compliance requirements. Financial transactions, supply chain records, and legal documents gain tamper-evident properties automatically. Our development teams at Nadcab Labs frequently implement these features for clients in regulated industries who need provable transaction histories.
Understanding the components of a blockchain helps developers appreciate how immutability emerges from the interaction between hashing, consensus, and distributed storage. It is not a single feature but a property that emerges from the system architecture.
Comparing Blockchain Security vs Traditional Database Security
The differences between blockchain and traditional database security affect everything from development costs to risk profiles. This comparison helps decision-makers understand where blockchain adds value and where traditional approaches might suffice.
| Security Aspect | Blockchain Architecture | Traditional Database |
|---|---|---|
| Data Storage | Distributed across thousands of nodes | Centralized servers with backups |
| Data Modification | Requires network consensus (51%+ nodes) | Admin access can modify any record |
| Audit Trail | Built-in, cryptographically verified | Requires separate logging systems |
| Single Point of Failure | None (distributed architecture) | Server, admin credentials, or network |
| Access Control | Cryptographic keys (user controlled) | Username/password (admin controlled) |
| Attack Surface | User credentials and smart contracts | Multiple (servers, network, credentials) |
This comparison reveals an important insight. Blockchain dramatically reduces infrastructure-level attack vectors but concentrates risk at the user credential level. Understanding this shift is essential for proper security planning. For a deeper technical comparison, explore our analysis of blockchain versus traditional database architectures.
Cryptography and Encryption: The Mathematical Shield
Blockchain relies on public-key cryptography to secure transactions. This system uses paired keys: a public key that others can see (similar to an email address) and a private key that only you control (similar to a password, but much more complex).
When you initiate a transaction, your wallet signs it with your private key. The network can verify this signature using your public key without ever seeing your private key. This mathematical relationship makes it computationally infeasible to derive a private key from a public key, even with unlimited resources.
The encryption standards used in blockchain have withstood decades of cryptanalysis. The SHA-256 hashing algorithm and ECDSA signature scheme used by Bitcoin represent some of the most battle-tested cryptographic tools available. Breaking these would require either fundamental advances in mathematics or quantum computers far more powerful than anything currently projected.
For developers, this cryptographic foundation simplifies security implementation. You do not need to build encryption systems from scratch. Instead, you integrate with established libraries and protocols. However, you must ensure that key management practices in your application do not introduce vulnerabilities. The cryptography is only as strong as its implementation.
The Vulnerability: Why Your Password Remains the Weak Link
Here is where the security narrative shifts dramatically. All the sophisticated protection described above guards your assets on the blockchain. But accessing those assets requires your password. And passwords are where human behavior meets cryptographic security.
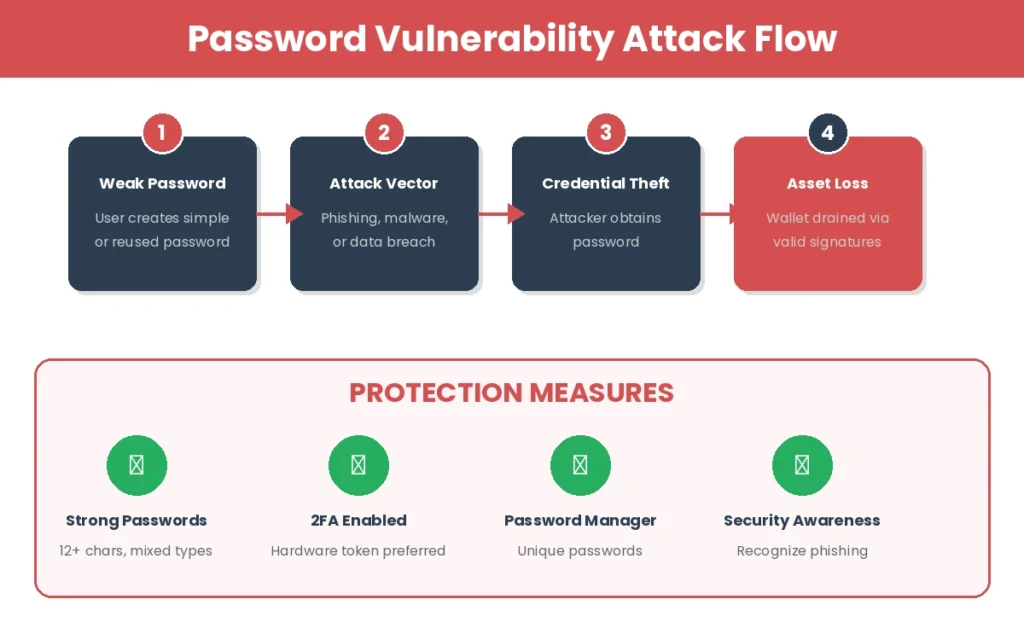
The blockchain does not store your password. It stores the cryptographic result of your private key. Your password unlocks the wallet software that holds your private key. If someone obtains your password, they unlock your wallet, access your private key, and control your assets. The blockchain will faithfully execute any transaction they sign with your private key because, mathematically, it looks legitimate.
Your Wallet Is Your Access Point
Think of your cryptocurrency wallet as a secure vault with two locks. The first lock is the blockchain’s cryptographic system, which is essentially unbreakable. The second lock is your password, which might be as weak as your pet’s name followed by your birth year.
Research from Investopedia’s cryptocurrency analysis indicates that the vast majority of crypto theft occurs not through blockchain exploits but through compromised credentials. Attackers follow the path of least resistance, and that path almost always leads through user passwords.
This creates a development challenge. When building blockchain applications, you must design user authentication that balances security with usability. Too complex, and users write passwords on sticky notes. Too simple, and attackers gain easy access. Finding this balance requires understanding both cryptographic principles and human psychology.
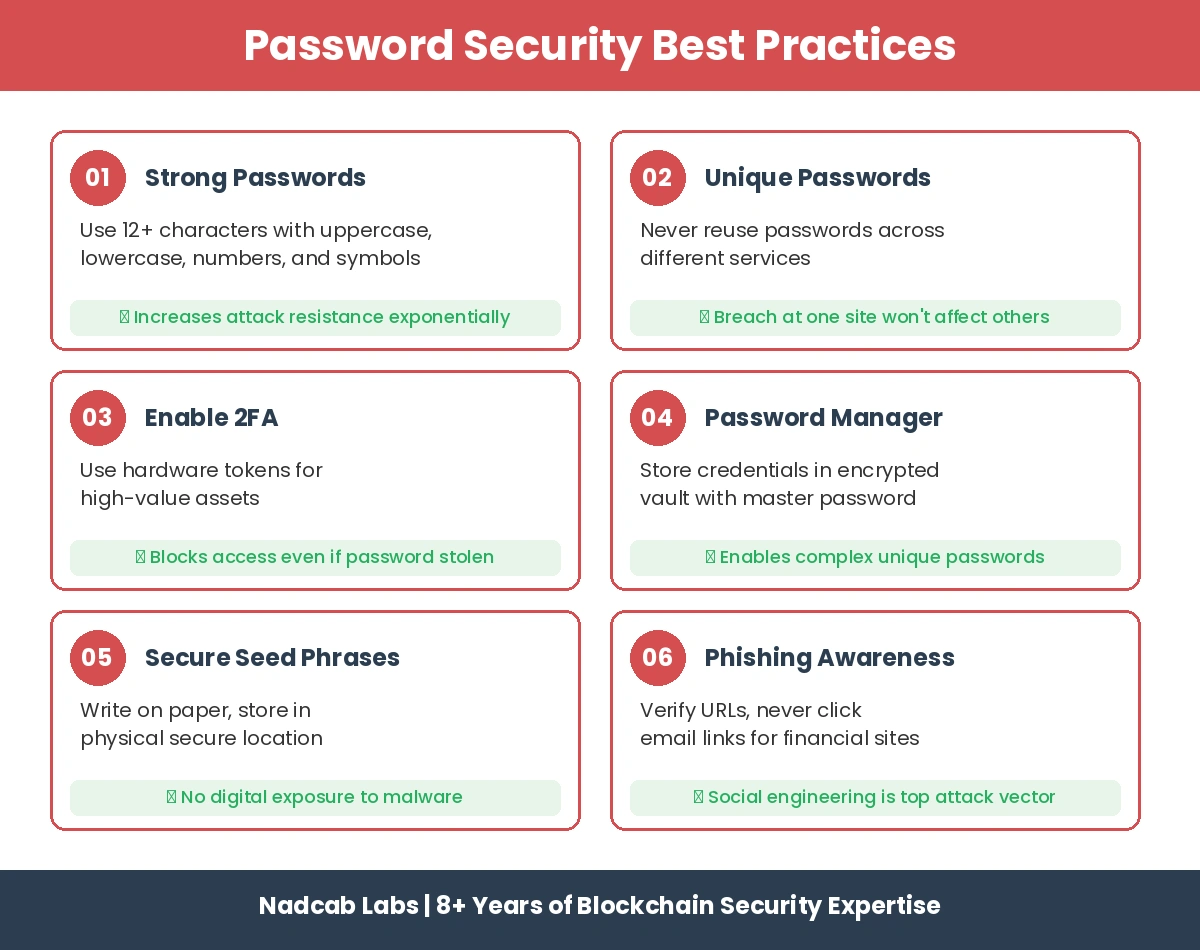
Phishing and Social Engineering: The Human Attack Vector
Technical defenses cannot protect against social manipulation. Phishing attacks create fake websites, emails, or messages that impersonate legitimate services. Users who fall for these attacks voluntarily hand over their credentials, bypassing every technical security measure.
The sophistication of these attacks has increased dramatically. Modern phishing campaigns use perfect copies of legitimate websites, SSL certificates that display the security padlock, and domain names that differ by a single character from real services. Even technically savvy users occasionally fall victim.
From an execution perspective, developers must build phishing resistance into their applications. This includes implementing domain verification, warning users about suspicious activities, and educating users about attack patterns. Security is not just a technical feature; it is an ongoing educational process.
Understanding how blockchain transaction verification works can help users identify legitimate transactions and spot fraudulent ones. Education remains the best defense against social engineering attacks.
Secure Your Blockchain Implementation
Build blockchain solutions with security at every layer. From smart contract audits to user authentication systems, our team delivers comprehensive protection for your digital assets.
Common Password Vulnerabilities in Blockchain Applications
Understanding specific vulnerabilities helps both developers and users protect their assets. The table below categorizes common password-related weaknesses and their potential impact.
| Vulnerability Type | Risk Level | Common Causes | Prevention Strategy |
|---|---|---|---|
| Weak Passwords | Critical | User convenience priority | Enforce complexity requirements |
| Password Reuse | High | Too many accounts to manage | Require unique passwords, suggest managers |
| Phishing Attacks | Critical | Sophisticated fake websites | 2FA, user education, domain verification |
| Keylogger Malware | High | Infected devices | Hardware wallets, secure boot |
| Credential Stuffing | Medium | Breached password databases | Breach monitoring, forced resets |
| Social Engineering | High | Human trust exploitation | Security awareness training |
Why Blockchain Cannot Protect Your Password
A common misconception holds that blockchain technology somehow extends its security properties to everything connected to it. This is not accurate, and understanding why helps set realistic expectations.
Blockchain operates on a specific domain: validating and recording transactions according to consensus rules. It has no mechanism to verify whether the person initiating a transaction is the legitimate owner or someone who stole their credentials. The blockchain sees only cryptographic signatures, and a valid signature from a stolen private key looks identical to a valid signature from a legitimate owner.
This design is intentional. Blockchain’s decentralized nature means no central authority can freeze accounts or reverse transactions. While this prevents censorship and arbitrary control, it also means no safety net exists when credentials are compromised. The responsibility shifts entirely to the user.
Consider this scenario. You use the same password for your email and your crypto wallet. An attacker breaches a minor website where you also used that email. They try your email and password combination on popular crypto exchanges. When they find a match, they initiate transfers to their own wallets. The blockchain executes these transactions perfectly because, from its perspective, everything is valid. Your assets are gone with no technical recourse.
Understanding blockchain architecture clarifies why these boundaries exist. The system was designed to be trustless and autonomous, which creates both its strengths and its limitations.
The Security Development Lifecycle for Blockchain Applications
Building secure blockchain applications requires integrating security considerations throughout the development process. This lifecycle approach ensures that password and credential security receives appropriate attention at every stage.
Phase 1: Requirements and Architecture
Security planning begins before writing any code. During this phase, development teams must define authentication requirements, identify potential attack vectors, and select appropriate security technologies. Questions to address include: What assets need protection? Who are the potential attackers? What is the acceptable balance between security and usability?
At Nadcab Labs, our architecture reviews always include threat modeling exercises. We map potential attack paths and design defenses before implementation begins. This proactive approach costs far less than retrofitting security after launch.
Phase 2: Secure Development Practices
Implementation must follow secure coding standards. For password handling, this means never storing passwords in plain text, using modern hashing algorithms like bcrypt or Argon2, implementing rate limiting on login attempts, and validating all user inputs.
Development teams should also implement comprehensive logging for security-relevant events. Login attempts, password changes, and unusual activity patterns should all generate records that support incident investigation and pattern detection.
Choosing the right programming languages for blockchain development can also impact security outcomes. Some languages provide better support for secure coding practices than others.
Phase 3: Testing and Audit
Security testing must go beyond functional verification. Penetration testing attempts to bypass authentication. Code audits examine password handling logic for vulnerabilities. Smart contract audits verify that on-chain code cannot be exploited.
Third-party audits provide essential independent verification. Internal teams may overlook vulnerabilities due to familiarity bias. External auditors bring fresh perspectives and specialized expertise in finding security flaws.
Phase 4: Deployment and Monitoring
Launching a secure application is not the end of security work. Continuous monitoring detects anomalous patterns that might indicate attacks in progress. Regular security updates address newly discovered vulnerabilities. Incident response plans prepare teams to act quickly when breaches occur.
Understanding blockchain transaction throughput helps in designing monitoring systems that can keep pace with network activity without creating bottlenecks.
Best Practices for Password Security in Blockchain Contexts
Both developers building blockchain applications and users interacting with them should follow established password security practices. These recommendations come from years of industry experience and observed attack patterns.
Use Strong and Unique Passwords
Password strength directly correlates with resistance to brute force attacks. A 12-character password using uppercase letters, lowercase letters, numbers, and symbols has approximately 95 to the 12th power possible combinations. This makes systematic guessing computationally infeasible.
Uniqueness is equally important. Using different passwords for each service ensures that a breach at one site does not compromise all your accounts. This practice has become essential as credential stuffing attacks have industrialized.
Enable Two-Factor Authentication
Two-factor authentication requires something you know (password) and something you have (phone, hardware token). Even if attackers obtain your password, they cannot access your account without the second factor.
For high-value blockchain assets, hardware-based 2FA using devices like YubiKey provides stronger protection than SMS or app-based codes. Hardware tokens resist phishing attacks that can capture SMS codes through SIM swapping or app compromises.
Implement Password Managers
Password managers solve the human memory problem. They generate strong random passwords for each site, store them securely, and fill them automatically. Users need to remember only one master password to access all their credentials.
From a development perspective, applications should work smoothly with password managers. Auto-fill compatibility, proper form field labeling, and support for generated passwords improve security by making good practices easier to follow.
Secure Your Private Keys and Seed Phrases
Private keys and seed phrases represent the ultimate access credentials for blockchain assets. These should never be stored digitally where malware might access them. Physical storage in secure locations like safety deposit boxes provides protection against both digital and physical threats.
Seed phrase backup is particularly critical. Losing a seed phrase means losing access to all associated assets permanently. No password reset option exists on the blockchain.
Security Tools Comparison for Blockchain Users
Selecting appropriate security tools depends on the value of assets being protected, technical comfort level, and usage patterns. This comparison helps users and developers choose appropriate solutions.
| Security Tool | Protection Level | Best For | Limitations |
|---|---|---|---|
| Software Wallet | Basic | Small amounts, frequent transactions | Vulnerable to device compromise |
| Hardware Wallet | High | Large holdings, long-term storage | Physical loss risk, cost |
| Password Manager | High | Managing multiple accounts | Master password single point |
| SMS 2FA | Medium | Basic additional protection | SIM swapping vulnerability |
| App-Based 2FA | Good | Regular crypto users | Phone loss/theft risk |
| Hardware 2FA Key | Excellent | High-value assets, enterprises | Cost, compatibility issues |
The Role of Layer 1 Infrastructure in Security
The underlying blockchain infrastructure affects the security guarantees available to applications built on top of it. Layer 1 blockchain networks provide the foundational security that all applications inherit.
Network security depends on factors including consensus mechanism, validator distribution, and economic incentives. Proof of Work networks like Bitcoin secure transactions through computational difficulty. Proof of Stake networks use economic bonds to discourage attacks. Each approach offers different security properties and trade-offs.
Developers selecting a blockchain for their applications must evaluate these infrastructure security properties. Building on a less secure network means inheriting its vulnerabilities regardless of how well the application itself is designed.
On-Chain Trading Security Considerations
Decentralized trading introduces additional security considerations beyond basic wallet protection. On-chain trading platforms require users to interact with smart contracts, which creates new attack surfaces.
Smart contract vulnerabilities have caused hundreds of millions of dollars in losses. Bugs in contract code can allow attackers to drain funds even when user passwords remain secure. This represents a different category of risk that requires different mitigation strategies.
Users should verify smart contract audits before interacting with DeFi protocols. Developers must invest in comprehensive testing and multiple independent audits before deploying contracts that handle user funds.
Gaming and NFT Platforms: Unique Security Challenges
The blockchain gaming industry faces unique security challenges. Players hold valuable in-game assets as NFTs, creating targets for attackers. The intersection of gaming accounts and crypto wallets creates complex attack surfaces.
Phishing attacks in gaming contexts often exploit social dynamics. Fake giveaways, compromised Discord servers, and impersonation of game developers are common attack vectors. The casual gaming context may lead users to lower their security guards compared to explicit financial applications.
Developers building blockchain games must consider these social attack vectors alongside technical security. Community moderation, verified communication channels, and user education become security features.
Real Estate and High-Value Asset Tokenization
Tokenizing high-value assets like real estate on blockchain raises the stakes for password security dramatically. A compromised wallet might represent not just cryptocurrency but ownership claims on physical property.
These applications require the highest security standards. Multi-signature wallets, time-locked transactions, and legal frameworks that recognize blockchain-based ownership while providing recovery mechanisms become essential considerations.
The development complexity increases significantly when designing systems that must interact with both blockchain infrastructure and traditional legal systems. Security failures in these contexts carry consequences beyond immediate financial loss.
The Historical Context: Learning from Past Incidents
Understanding the history of blockchain technology includes learning from its security incidents. Major exchange hacks, protocol exploits, and social engineering attacks have all contributed to the industry’s security knowledge base.
The 2014 Mt. Gox hack, which resulted in the loss of approximately 850,000 Bitcoin, demonstrated the consequences of centralized custody combined with poor security practices. This incident influenced the development of better custodial solutions and increased interest in self-custody wallets.
More recent attacks have targeted DeFi protocols, exploiting smart contract vulnerabilities rather than password weaknesses. These incidents show that security threats evolve, and defenses must evolve with them.
Architect vs Developer: Security Responsibilities
Security responsibilities differ between blockchain architects and developers. Architects design overall security frameworks and make strategic technology choices. Developers implement those designs and must follow secure coding practices at the implementation level.
Effective security requires both roles to fulfill their responsibilities. A brilliant architectural design fails if implementation introduces vulnerabilities. Careful implementation cannot compensate for fundamentally flawed architecture.
At Nadcab Labs, our teams include both specialized architects and experienced developers. This structure ensures that security receives attention at every level of abstraction, from high-level design through deployment.
Building Security-First Blockchain Solutions
The message throughout this analysis remains consistent: blockchain provides exceptional security for transaction validation and data integrity, but password security remains the user’s responsibility. Developers must design systems that support good security practices without imposing unrealistic burdens on users.
This balance requires ongoing attention. Security is not a feature to implement and forget but a continuous process of monitoring, updating, and adapting to new threats. The blockchain industry’s rapid evolution means that yesterday’s best practices may become tomorrow’s vulnerabilities.
Organizations seeking to implement blockchain solutions should partner with experienced development teams who understand both the technology’s capabilities and its limitations. With 8+ years of blockchain development experience, Nadcab Labs brings the expertise needed to build systems that leverage blockchain’s strengths while addressing its security boundaries.
Partner With Blockchain Security Experts
From architecture design to security audits, our team delivers blockchain solutions built on proven security principles. Protect your assets with expertise developed over 8+ years of successful implementations.
Conclusion
Blockchain technology represents a genuine advancement in digital security. Its decentralized architecture, cryptographic foundations, and immutable record-keeping solve problems that plagued centralized systems for decades. However, this technology operates within boundaries that users and developers must understand.
Your password remains the key to your digital vault. No amount of blockchain sophistication can protect assets if that key falls into the wrong hands. This reality places responsibility on both developers, who must build systems that support secure practices, and users, who must follow those practices consistently.
The good news is that securing passwords is a solved problem. Strong unique passwords, two-factor authentication, password managers, and hardware wallets provide effective protection. The tools exist. The knowledge exists. What remains is implementation and discipline.
As blockchain adoption continues to grow and digital assets become an increasingly significant part of the global economy, password security will only become more important. Those who take it seriously will protect their assets. Those who do not will learn expensive lessons. The choice, ultimately, belongs to each individual and organization.
Frequently Asked Questions
Blockchain distributes data across thousands of independent nodes rather than storing it on centralized servers. This eliminates single points of failure that attackers commonly target in traditional systems. Additionally, blockchain data cannot be modified once recorded because each block cryptographically links to previous blocks, creating tamper-evident records. Traditional databases rely on access controls administered by centralized authorities, while blockchain uses cryptographic keys controlled entirely by users.
Blockchain encryption protects data stored on the distributed ledger and verifies transaction authenticity. However, accessing your wallet requires a password that unlocks your private keys stored locally on your device. Attackers target this access point rather than attempting to break blockchain encryption directly. If someone obtains your wallet password through phishing, malware, or guessing, they can access your private keys and control your assets without ever attacking the blockchain itself.
Two-factor authentication requires two separate verification methods before granting account access. Typically this combines something you know like a password with something you possess like a phone or hardware token. For cryptocurrency wallets, 2FA prevents unauthorized access even when attackers obtain your password through data breaches or phishing attacks. Hardware-based 2FA devices like YubiKey provide stronger protection than SMS codes which can be intercepted through SIM swapping attacks.
Never store seed phrases or private keys digitally where malware might access them. Write your seed phrase on paper and store it in a secure physical location such as a home safe or bank safety deposit box. Consider splitting the phrase across multiple secure locations for redundancy. Hardware wallets provide secure storage for private keys by keeping them isolated from internet-connected devices. Never share your seed phrase with anyone, and be aware that legitimate services will never request it.
Attackers create fake websites that perfectly replicate legitimate cryptocurrency exchanges and wallet services, using similar domain names that differ by single characters. Fraudulent emails claiming account issues pressure users to click malicious links and enter credentials. Social media impersonation of crypto projects announces fake giveaways requiring wallet connections. Discord and Telegram scammers impersonate support staff to extract private keys. Always verify website URLs, never click email links for financial services, and remember that legitimate projects never request private keys.
Developers should implement modern password hashing algorithms like Argon2 or bcrypt rather than simple encryption. Rate limiting on login attempts prevents brute force attacks. Mandatory two-factor authentication for high-value operations adds crucial protection. Applications should integrate smoothly with password managers by using proper form field attributes. Security logging enables detection of suspicious patterns. Regular third-party security audits identify vulnerabilities before attackers exploit them. User education features within applications help users understand and follow security best practices.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.