Key Takeaways
- Smart contract vulnerabilities represent the primary attack vector in real estate tokenization, with reentrancy exploits, logic flaws, and inadequate access controls enabling unauthorized token manipulation and fund drainage across platforms in USA, UK, UAE, and Canadian markets.
- Private key compromise remains the most devastating single-point security failure, granting attackers irreversible control over tokenized property assets without possibility of transaction reversal, requiring hardware wallet adoption and multi-signature implementations for institutional-grade protection.
- Admin key security creates centralized vulnerability exposing platforms to existential threats including unlimited token minting, contract upgrades to malicious versions, and complete platform control, necessitating multi-signature governance and time-locked administrative functions for enterprise deployments.
- Infrastructure vulnerabilities beyond blockchain layer including API exploits, cloud misconfigurations, and database breaches expose investor personal data and enable platform manipulation, requiring comprehensive security audits across entire technology stack beyond smart contract reviews alone.
- Regulatory compliance failures amplify security risks by preventing access to institutional security frameworks, limiting operational jurisdictions, and creating legal ambiguity that attracts sophisticated attackers expecting reduced recourse in non-compliant tokenization platforms across major markets.
- Oracle manipulation risks enable artificial property valuation inflation and improper liquidation triggers through compromised price feeds, requiring decentralized oracle networks with cryptographic verification and multi-source data aggregation for accurate real estate valuations in tokenized environments.
- Wallet integration vulnerabilities create attack surfaces through malicious dApp approvals, phishing interfaces, and compromised browser extensions that bypass smart contract security, demanding comprehensive transaction preview mechanisms and regular approval auditing by investors.
- Comprehensive audit processes including third-party security reviews, formal verification, economic exploit analysis, and continuous post-deployment monitoring represent non-negotiable requirements for platforms managing tokenized real estate assets exceeding ten million dollars in total value locked.
Introduction to Security Risks in Real Estate Tokenization
Real estate tokenization security vulnerabilities have emerged as critical concerns as the global market for blockchain-based property investment surpasses $2.4 billion in transaction volume across major markets including the United States, United Kingdom, United Arab Emirates, and Canada. Our agency’s eight years of experience deploying secure tokenization platforms has revealed that security architecture represents the fundamental determinant of platform viability, investor confidence, and regulatory approval in this rapidly evolving sector where traditional real estate assets intersect with blockchain technology’s inherent risks.
The transformation of illiquid real estate assets into digital tokens traded on blockchain networks introduces unprecedented security challenges spanning smart contract vulnerabilities, cryptographic key management failures, infrastructure exploits, regulatory compliance gaps, and oracle manipulation risks that traditional property investment never encountered. Unlike conventional real estate transactions protected by legal frameworks, title insurance, escrow services, and reversible banking systems, tokenized properties rely entirely on immutable smart contracts and cryptographic security where single vulnerabilities can enable instant, irreversible theft of millions in investor capital without legal recourse.
Real estate tokenization security vulnerabilities manifest across multiple interconnected layers including blockchain protocol risks, smart contract code defects, wallet integration weaknesses, centralized infrastructure exploits, governance mechanism failures, and regulatory non-compliance creating legal exposure. Each layer presents distinct attack surfaces requiring specialized security expertise, comprehensive audit processes, continuous monitoring systems, and rapid incident response capabilities that most tokenization platforms inadequately address during development and deployment phases.
The financial impact of security vulnerabilities in blockchain real estate extends beyond direct asset theft to encompass platform reputation destruction, regulatory enforcement actions, investor litigation, market confidence erosion, and operational shutdown requirements following major incidents. High-profile exploits across DeFi protocols have demonstrated that single smart contract vulnerabilities can drain entire platform treasuries within minutes, while infrastructure breaches expose sensitive investor data triggering GDPR violations in European markets and securities law infractions in United States jurisdictions.
Critical Security Challenge Categories
Smart Contract Layer
Reentrancy attacks, logic flaws, access control failures, upgrade vulnerabilities, and economic exploits in immutable contract code controlling property ownership and fund distribution.
Cryptographic Security
Private key compromise, admin key exposure, multi-signature failures, seed phrase theft, and wallet integration weaknesses enabling irreversible asset theft and platform control loss.
Infrastructure Vulnerabilities
API exploitation, cloud misconfigurations, database breaches, DNS hijacking, DDoS attacks, and backend system compromises exposing investor data and enabling platform manipulation.
Oracle Manipulation
Property valuation data poisoning, price feed compromise, flash loan attacks, centralized oracle dependency, and time-series manipulation affecting liquidations and trading.
Regulatory Compliance
Securities law violations, KYC/AML failures, data privacy breaches, cross-border regulatory conflicts, and investor protection inadequacies creating legal vulnerability across jurisdictions.
Governance Mechanisms
Centralized control risks, multi-signature failures, time-lock bypass vulnerabilities, voting manipulation, and emergency response inadequacies during security incidents and exploit scenarios.
Understanding these interconnected vulnerability categories enables platform developers, institutional investors, and regulatory bodies to implement comprehensive security frameworks addressing real estate tokenization security vulnerabilities unique threat landscape where traditional property investment risks converge with blockchain technology’s nascent security challenges requiring specialized expertise across cryptography, smart contract development, infrastructure security, and regulatory compliance in evolving global markets.
Why Security Is Critical in Tokenized Real Estate Assets
Security represents the foundational pillar determining viability, investor adoption, regulatory approval, and long-term sustainability of tokenized real estate platforms managing assets worth hundreds of millions across United States, United Kingdom, Dubai, and Canadian markets. Unlike traditional property investment where multiple institutional safeguards including title insurance, legal frameworks, banking intermediaries, and government registries provide security layers, tokenized real estate relies entirely on cryptographic security and smart contract integrity where single vulnerabilities enable instant, irreversible theft without recourse or recovery mechanisms available in conventional transactions.
The immutable nature of blockchain technology amplifies security criticality in real estate tokenization security vulnerabilities because deployed smart contracts cannot be modified to patch vulnerabilities discovered post-launch, forcing expensive and complex migration processes that disrupt investor confidence, trigger regulatory scrutiny, and potentially invalidate existing token ownership records. This permanent deployment characteristic means that security must be comprehensively validated before launch through extensive third-party audits, formal verification processes, economic exploit modeling, and bug bounty programs rather than relying on iterative improvement approaches acceptable in traditional software development.
Regulatory compliance across major jurisdictions including SEC oversight in United States, FCA requirements in United Kingdom, DFSA regulations in Dubai, and provincial securities authorities in Canada mandates robust security controls protecting investor capital and personal data as preconditions for platform authorization. Real estate tokenization security vulnerabilities that enable investor fund theft, personal data exposure, or market manipulation constitute securities law violations triggering enforcement actions, operational shutdowns, management liability, and potential criminal prosecution beyond civil penalties, making security excellence a legal imperative rather than optional enhancement.
Security Impact Dimensions in Tokenized Real Estate
Financial Impact
- Direct investor capital loss through theft exploits
- Platform treasury drainage via smart contract vulnerabilities
- Market value collapse following security incidents
- Litigation costs and investor compensation obligations
- Insurance premium increases or coverage denial
Regulatory Consequences
- Securities law violations and enforcement actions
- Operational shutdown orders from authorities
- Data privacy breach penalties under GDPR/CCPA
- Management liability and potential prosecution
- Jurisdictional access restrictions in key markets
Reputational Damage
- Permanent platform credibility destruction
- Institutional investor withdrawal and avoidance
- Media coverage amplifying negative perception
- Blockchain community blacklisting effects
- Future fundraising impossibility after incidents
Operational Disruption
- Emergency platform shutdown during incident response
- Smart contract migration complexity and costs
- Investor communication crisis management
- Technical team diversion from development roadmap
- Partnership dissolution and vendor terminations
Market Confidence
-
- Sector-wide investor confidence erosion
- Regulatory scrutiny intensification across industry
- Institutional adoption timeline delays
- Traditional real estate industry skepticism
- Competitive disadvantage versus conventional investment
Strategic Implications
- Technology partner relationship terminations
- Property acquisition pipeline disruption
- Secondary market liquidity collapse
- Platform valuation destruction in funding rounds
- Competitive positioning loss in emerging market
The cascading consequences of real estate tokenization security vulnerabilities extend beyond immediate financial losses to encompass existential threats including permanent platform closure, management legal liability, investor litigation spanning multiple jurisdictions, regulatory prohibition from operating in major markets, and sector-wide reputation damage impeding broader blockchain real estate adoption. Major security incidents create precedents that regulators cite when restricting tokenization activities, institutional investors reference when rejecting blockchain exposure, and traditional real estate professionals invoke when resisting digital transformation initiatives.
Institutional capital allocation to tokenized real estate platforms fundamentally depends on demonstrable security excellence validated through comprehensive third-party audits, insurance coverage availability, regulatory compliance certification, and operational track records without security incidents. Platforms failing to achieve institutional-grade security standards remain confined to retail investor markets with limited capital pools, high volatility, and constrained growth potential compared to competitors successfully attracting pension funds, family offices, sovereign wealth entities, and real estate investment trusts requiring enterprise security guarantees before deploying significant capital into blockchain-based property investments.
Smart Contract Vulnerabilities in Real Estate Tokenization
Smart contract vulnerabilities constitute the primary attack vector enabling catastrophic exploitation of tokenized real estate platforms, with historical precedents demonstrating that single code defects can drain entire platform treasuries worth tens of millions within minutes through automated exploit scripts. Real estate tokenization security vulnerabilities in smart contract layer manifest through reentrancy attacks enabling recursive fund withdrawal, integer overflow/underflow manipulating token balances, access control failures allowing unauthorized administrative functions, logic flaws in ownership transfer mechanisms, and upgrade vulnerabilities introducing malicious contract versions through proxy patterns inadequately secured.
Reentrancy vulnerabilities represent particularly devastating smart contract exploits where malicious contracts recursively call victim contract functions before state updates complete, enabling attackers to drain funds beyond intended withdrawal limits. The infamous DAO hack stealing over $60 million through reentrancy attacks demonstrates catastrophic potential when real estate tokenization security vulnerabilities platforms fail to implement checks-effects-interactions patterns, reentrancy guards, and pull payment architectures protecting against recursive calling exploits that bypass balance verification logic.
| Vulnerability Type | Exploitation Mechanism | Potential Impact | Prevention Measures |
|---|---|---|---|
| Reentrancy Attack | Recursive function calls before state updates enabling multiple withdrawals exceeding balance | Complete treasury drainage, investor fund theft, platform insolvency | Checks-effects-interactions pattern, reentrancy guards, pull payment architecture |
| Integer Overflow/Underflow | Arithmetic operations exceeding variable limits wrapping to unexpected values | Unlimited token minting, balance manipulation, economic exploit | SafeMath libraries, Solidity 0.8+ built-in overflow checks, arithmetic validation |
| Access Control Failure | Missing or improper function modifiers allowing unauthorized administrative access | Platform takeover, malicious contract upgrades, token supply manipulation | Role-based access control, multi-signature requirements, function visibility audits |
| Logic Flaw Exploits | Business logic errors enabling unintended state transitions and value extraction | Ownership manipulation, dividend theft, transfer restriction bypass | Formal verification, extensive testing, economic modeling, peer review |
| Unchecked External Calls | Failed external calls not validated enabling state inconsistency exploitation | Silent failure exploitation, state desynchronization, fund loss | Return value validation, require statements, error handling implementation |
| Front-Running Vulnerabilities | Transaction ordering manipulation through mempool observation and gas bidding | Arbitrage exploitation, price manipulation, investor disadvantage | Commit-reveal schemes, batch auctions, fair ordering protocols |
| Timestamp Dependence | Miner manipulation of block timestamps affecting time-sensitive logic | Dividend distribution manipulation, vesting schedule exploitation | Block number usage, timestamp tolerance ranges, oracle time verification |
| Delegatecall Injection | Malicious library injection through delegatecall executing in contract context | Complete contract control, storage manipulation, fund theft | Library address verification, immutable library references, delegatecall restrictions |
Access control vulnerabilities enabling unauthorized execution of privileged functions represent catastrophic smart contract security failures in real estate tokenization security vulnerabilities platforms where administrative functions control token minting, property ownership transfers, dividend distributions, and platform upgrades. Inadequate implementation of role-based access controls, missing function modifiers, public visibility on administrative functions, and weak multi-signature requirements create attack surfaces where single compromised accounts or exploited authorization logic grants attackers complete platform control including ability to mint unlimited tokens diluting existing investor holdings.
Logic flaws in smart contract business logic create subtle vulnerabilities that sophisticated attackers exploit to manipulate ownership records, bypass transfer restrictions, extract value through economic exploits, and corrupt platform state without triggering obvious security alerts. These vulnerabilities often survive initial security audits because they require deep understanding of complex interaction patterns between multiple contract functions, edge cases in state transitions, and economic incentive structures that formal verification tools and automated testing frameworks inadequately model during pre-deployment validation processes.
Upgrade mechanisms in real estate tokenization security vulnerabilities smart contracts using proxy patterns introduce additional vulnerability surfaces where improper implementation enables attackers to replace contract logic with malicious versions, steal funds through unauthorized upgrades, or brick platforms by deploying incompatible contract versions. Transparent proxy patterns, UUPS proxies, and beacon proxies each present distinct security considerations requiring rigorous validation of upgrade authorization logic, storage layout compatibility verification, and initialization function protection against front-running exploits during upgrade transactions.
Inadequate Smart Contract Auditing Risks
Inadequate smart contract auditing represents one of the most prevalent real estate tokenization security vulnerabilities, with insufficient pre-deployment security validation directly contributing to majority of major exploits costing investors hundreds of millions in stolen assets across blockchain real estate platforms. Comprehensive third-party security audits from reputable firms specializing in smart contract analysis constitute non-negotiable requirements for platforms managing tokenized property assets, yet cost pressures, timeline constraints, and technical complexity frequently result in superficial audits missing critical vulnerabilities discovered only after exploitation occurs.
Single security audits from even reputable firms provide insufficient validation coverage for complex real estate tokenization security vulnerabilities platforms integrating multiple smart contracts, external protocol dependencies, oracle systems, and upgrade mechanisms. Industry best practices mandate multiple independent audits from different security firms, formal verification of critical contract functions, extensive fuzzing campaigns testing edge cases, economic modeling identifying exploit vectors, and public bug bounty programs incentivizing white-hat researcher discovery of vulnerabilities before malicious exploitation occurs in production environments.

The audit timing and scope critically impact real estate tokenization security vulnerabilities, with rushed audits conducted under tight deployment deadlines frequently missing complex vulnerabilities requiring deep analysis of contract interactions, economic incentive structures, and edge case scenarios. Audits should commence early in development lifecycle enabling iterative security improvements rather than treating security as final deployment checkpoint, and should encompass all contract code including libraries, dependencies, deployment scripts, upgrade mechanisms, and off-chain infrastructure components interacting with blockchain contracts.
Protect Your Platform from Real Estate Tokenization Security Vulnerabilities
Our security experts specialize in identifying and mitigating real estate tokenization security vulnerabilities. Get comprehensive audit services today.
Audit report transparency and remediation verification constitute essential components of credible security validation, yet many tokenization platforms selectively disclose audit findings, fail to implement recommended fixes, or deploy modified code after audits without re-validation. Industry best practices mandate public disclosure of complete audit reports including identified vulnerabilities and implemented remediations, third-party verification that high and critical severity findings received proper fixes, and commitment to re-auditing any significant code changes before production deployment in United States, United Kingdom, UAE, and Canadian jurisdictions where regulatory scrutiny increasingly demands demonstrable security due diligence.
Token Logic Flaws and Ownership Manipulation Risks
Token logic flaws in real estate tokenization security vulnerabilities smart contracts create devastating vulnerabilities enabling attackers to manipulate ownership records, bypass transfer restrictions, duplicate tokens, and corrupt property rights tracking without authorization. These vulnerabilities manifest through subtle programming errors in token minting logic, ownership transfer validation, balance tracking mechanisms, and approval systems that appear functional under normal operations but contain exploitable edge cases enabling sophisticated attackers to gain unauthorized control over tokenized property assets worth millions.[1]
Ownership manipulation exploits targeting token balance tracking represent particularly insidious real estate tokenization security vulnerabilities because they corrupt fundamental property rights records that blockchain platforms promise to maintain immutably and transparently. Attackers exploiting integer overflow vulnerabilities, race conditions in concurrent transactions, or flawed state update sequences can artificially inflate token balances, transfer tokens without proper authorization checks, or create duplicate ownership claims to same underlying property shares causing irreconcilable conflicts between recorded blockchain state and actual legal property ownership rights.
Common Ownership Manipulation Attack Vectors
Balance Inflation Exploits
- Integer overflow manipulation creating artificially high balances
- Reentrancy during transfer functions duplicating tokens
- Race conditions in concurrent balance updates
- Rounding errors in fractional ownership calculations
- Mint function exploits bypassing supply caps
Unauthorized Transfer Attacks
- Access control bypass enabling transfers without ownership
- Approval mechanism exploitation for unauthorized withdrawals
- Delegate transfer function vulnerabilities
- Signature verification flaws in meta-transactions
- Time-based restriction bypass through timestamp manipulation
Double-Spend Vulnerabilities
- Atomic transaction exploitation spending same tokens twice
- Cross-contract reentrancy duplicating token usage
- Flash loan attacks enabling temporary balance inflation
- State inconsistency between multiple contract interactions
- Oracle manipulation affecting transfer eligibility checks
Metadata Corruption Exploits
- Token URI manipulation affecting property information
- Ownership registry desynchronization attacks
- Property attribute modification without authorization
- Dividend entitlement record corruption
- Transfer history manipulation obscuring ownership trails
Supply Cap Bypass
- Mint function vulnerabilities exceeding maximum supply
- Burn mechanism bypass preventing supply reduction
- Total supply calculation errors in distributed minting
- Fractional token minting creating excessive granularity
- Upgrade exploitation introducing unlimited minting capability
Compliance Bypass Exploits
- KYC verification bypass enabling unverified transfers
- Accredited investor restriction circumvention
- Lock-up period enforcement bypass
- Geographic restriction evasion techniques
- Transfer limit manipulation exceeding regulatory caps
Transfer restriction bypass vulnerabilities enable attackers to circumvent critical compliance controls including accredited investor verification, geographic restrictions, lock-up periods, and transfer limits mandated by securities regulations in United States, United Kingdom, UAE, and Canadian jurisdictions. Real estate tokenization security vulnerabilities platforms implement complex transfer logic validating investor eligibility, regulatory compliance, and contractual restrictions before authorizing token movements, yet flaws in this validation logic create attack surfaces where sophisticated actors bypass controls through transaction structuring, contract interaction patterns, or exploit timing enabling unauthorized secondary market trading violating securities laws.
Approval mechanism vulnerabilities in ERC-20 and ERC-721 token standards create additional ownership manipulation risks where investors unknowingly grant unlimited spending permissions to malicious contracts that subsequently drain entire token holdings without explicit transaction authorization. The approve function design pattern requiring separate approval and transfer transactions creates user experience friction that many platforms attempt to streamline through unlimited approvals or batched transaction patterns, inadvertently creating persistent attack surfaces where historical approvals granted to compromised contracts remain exploitable indefinitely unless actively revoked.
Fractional ownership calculations in real estate tokenization security vulnerabilities introduce additional complexity where rounding errors, precision loss, and integer arithmetic limitations create exploitable discrepancies between total token supply and aggregate individual balances. These mathematical vulnerabilities enable attackers to extract value through repeated small transactions amplifying rounding errors, exploit precision mismatches between different contract functions, or manipulate dividend distribution calculations receiving disproportionate payment shares relative to actual ownership percentages held.
Wallet Integration Risks in Tokenized Real Estate Platforms
Wallet integration vulnerabilities represent critical real estate tokenization security vulnerabilities because they compromise the fundamental interface between investors and blockchain platforms, enabling attackers to drain funds, steal private keys, and manipulate transactions despite robust smart contract security. Real estate tokenization security vulnerabilities platforms integrate with third-party wallet providers including MetaMask, Ledger, WalletConnect, and Coinbase Wallet, creating complex trust boundaries where security depends not only on platform code but also wallet provider security, browser extension vulnerabilities, and user security practices beyond platform control.
Malicious dApp attacks exploiting wallet connection protocols represent prevalent threats where phishing websites mimicking legitimate tokenization platforms trick investors into connecting wallets and signing fraudulent transactions that drain approved tokens or grant unlimited spending permissions. WalletConnect protocol vulnerabilities, insufficient transaction preview mechanisms in wallet interfaces, and social engineering campaigns targeting investor urgency create attack vectors where users unknowingly authorize value transfers to attacker addresses despite comprehensive smart contract access controls preventing unauthorized direct theft.
Browser extension vulnerabilities affecting popular wallet providers create systemic risks where malicious browser extensions, compromised wallet provider updates, or supply chain attacks inject malicious code capable of stealing private keys, modifying transaction parameters, or exfiltrating sensitive user data across all platforms users access. The widespread adoption of MetaMask and similar browser-based wallets creates concentrated risk where single extension compromise potentially affects millions of users across countless tokenization platforms, requiring robust security monitoring, rapid incident response coordination, and alternative authentication methods reducing dependency on single wallet provider security.
WalletConnect protocol security depends on secure relay server operation, encrypted communication channels, and proper session management implementations that many platforms inadequately validate. Compromised relay servers can intercept transaction data, man-in-the-middle attacks can modify connection requests, and session hijacking exploits can enable attackers to impersonate legitimate users after initial authentication, creating attack surfaces beyond smart contract and private key security requiring comprehensive protocol-level security validation and alternative connection methods for high-value institutional transactions.
Private Key Exposure and User Wallet Compromise
Private key compromise represents the most catastrophic single-point security failure in real estate tokenization security vulnerabilities because stolen private keys grant attackers complete, irreversible control over associated tokenized property assets without possibility of transaction reversal or legal recourse available in traditional banking systems. Unlike conventional property ownership where title theft requires complex legal fraud, forged documents, and institutional failures across multiple verification checkpoints, blockchain property tokens transfer instantly upon private key compromise without intermediary approval, time delays, or reversal mechanisms creating permanent, unrecoverable investor losses.
Phishing attacks targeting tokenization platform users represent the most prevalent private key compromise vector, with sophisticated campaigns creating replica websites, fake email communications, and social media impersonation schemes tricking investors into entering seed phrases or private keys into attacker-controlled interfaces. These attacks exploit urgency psychology, authority impersonation, and technical confusion to bypass security awareness where even experienced cryptocurrency users fall victim when facing convincingly designed phishing sites mimicking legitimate platform branding, domain names with subtle typo squatting variations, and urgent security alerts fabricated to induce panic responses.
Private Key Compromise Threat Landscape
Phishing Attacks
- Replica platform websites harvesting credentials
- Email campaigns impersonating platform support
- Social media fake profiles offering assistance
- SMS phishing targeting mobile wallet users
- Discord and Telegram support scams
Malware and Keyloggers
- Clipboard hijacking modifying destination addresses
- Screen capture malware recording seed phrase entry
- Keylogger software capturing wallet passwords
- Remote access trojans enabling device control
- Fake wallet application installations
Physical Security Breaches
- Seed phrase paper backups stolen or photographed
- Hardware wallet physical theft without PIN protection
- Computer access during unlocked sessions
- Shoulder surfing during seed phrase entry
- Compromised home or office security
Social Engineering
- Fake support representatives requesting private keys
- Investment opportunity scams requiring wallet connection
- Romance scams targeting cryptocurrency holders
- Employment fraud requesting wallet verification
- Emergency notification schemes creating urgency
Cloud and Backup Compromise
-
- Cloud storage account breaches exposing seed phrases
- Email account compromise revealing backup information
- Password manager vulnerabilities exposing credentials
- Synchronization service interception
- Unencrypted backup discovery on compromised devices
Insider Threats
- Family member unauthorized wallet access
- Employee compromise in institutional settings
- Custodial service insider theft
- Platform employee abuse of admin privileges
- Third-party service provider data breaches
Malware infections on user devices create persistent private key theft risks through keyloggers recording seed phrase entry, clipboard hijacking malware modifying destination addresses during copy-paste operations, screen capture malware recording wallet interfaces during authentication, and remote access trojans granting attackers complete device control enabling direct wallet access. These malware variants specifically target cryptocurrency holders through infected downloads, compromised browser extensions, and supply chain attacks on popular software packages, requiring comprehensive endpoint security including antivirus software, hardware wallet usage, and dedicated secure devices for high-value cryptocurrency transactions.
Seed phrase backup vulnerabilities represent critical security weaknesses where investors attempting to protect against device loss inadvertently create additional attack surfaces through insecure storage methods including digital photographs stored in cloud services, unencrypted text files on compromised computers, password managers with weak master passwords, or physical paper backups in unsecured locations. Industry best practices mandate metal seed phrase backup storage in fireproof safes, distributed backup storage across multiple secure locations, consideration of Shamir Secret Sharing schemes splitting seed phrases across multiple custodians, and absolute prohibition on digital seed phrase storage regardless of encryption claims or cloud provider security assertions.
Hardware wallet adoption represents the most effective private key protection mechanism for tokenized real estate investors holding significant asset values, providing isolated key storage on dedicated devices resistant to remote attacks, malware infections, and phishing schemes. Ledger and Trezor hardware wallets store private keys in secure elements never exposing them to connected computers, require physical button confirmation for transaction signing preventing unauthorized remote execution, and provide secure seed phrase generation and backup processes reducing user error risks. However, hardware wallet security depends on authentic device procurement from official vendors rather than third-party marketplaces, firmware authenticity verification preventing malicious updates, and secure PIN protection preventing physical theft exploitation.
Risks from Third-Party Wallet Dependencies
Third-party wallet dependencies create systemic real estate tokenization security vulnerabilities because platform security becomes inextricably linked to external wallet provider security practices, update mechanisms, and operational continuity beyond platform control. Real estate tokenization security vulnerabilities platforms relying on MetaMask, WalletConnect, Coinbase Wallet, and similar third-party solutions inherit all security vulnerabilities present in these external systems including software bugs, supply chain compromises, service disruptions, and policy changes potentially affecting investor access to tokenized property assets without platform recourse or mitigation capability.
Wallet provider supply chain attacks represent emerging threats where compromised development processes, malicious insider actions, or dependency vulnerabilities inject malicious code into wallet provider updates affecting millions of users simultaneously. The 2023 incident where popular cryptocurrency wallet providers faced potential compromise through dependency vulnerabilities demonstrates how third-party wallet reliance creates concentrated risk where single supply chain failure potentially compromises entire ecosystem of tokenization platforms and investors depending on affected wallet infrastructure for transaction signing and asset custody across United States, United Kingdom, UAE, and Canadian markets.
| Dependency Risk Category | Specific Vulnerabilities | Impact on Platforms | Mitigation Strategies |
|---|---|---|---|
| Provider Service Disruption | Infrastructure failures, maintenance downtime, regulatory shutdown, business closure scenarios | Complete investor access loss, transaction execution impossibility, platform operational paralysis | Multi-wallet support, fallback authentication methods, emergency access protocols |
| Update and Version Incompatibility | Breaking API changes, deprecated features, forced migrations, compatibility failures | Platform functionality disruption, investor access barriers, emergency redevelopment requirements | Version pinning, compatibility testing, gradual migration planning, alternative provider readiness |
| Security Vulnerability Disclosure | Zero-day exploits, critical bugs, patch deployment delays, vulnerability window exploitation | Mass investor compromise, platform reputation damage, emergency shutdown requirements | Rapid incident response, platform-level protection mechanisms, investor communication protocols |
| Policy and Terms Changes | Service restriction changes, jurisdictional availability limitations, feature deprecations | Investor segment exclusion, market access loss, forced alternative adoption | Terms monitoring, diverse provider support, investor migration assistance programs |
| Data Privacy Concerns | Wallet provider data collection, tracking mechanisms, third-party data sharing | Investor privacy erosion, regulatory compliance risks, competitive intelligence leakage | Privacy-focused wallet alternatives, data minimization practices, transparency requirements |
| Centralization Risks | Single provider dominance, vendor lock-in, ecosystem control concentration | Negotiating disadvantage, price increase vulnerability, strategic dependency | Decentralized alternatives, open-source wallet options, in-house capabilities |
Wallet provider business continuity risks create scenarios where service shutdowns, regulatory enforcement actions, or bankruptcy proceedings abruptly terminate wallet provider operations leaving investors unable to access tokenized real estate assets through familiar interfaces. While blockchain’s decentralized nature theoretically enables alternative access methods using raw private keys, practical investor capability limitations, technical complexity barriers, and emergency situation stress substantially reduce successful alternative access achievement requiring tokenization platforms to maintain comprehensive contingency plans including multi-wallet support, emergency access procedures, and investor education programs enabling provider-independent asset access during crisis scenarios.
API stability and versioning risks manifest when wallet providers introduce breaking changes, deprecate features, or modify authentication flows disrupting tokenization platform functionality requiring emergency development sprints, investor communication campaigns, and temporary service restrictions during migration periods. Real estate tokenization security vulnerabilities platforms integrating deeply with specific wallet provider APIs face substantial technical debt when forced migrations occur, potentially requiring complete authentication system rebuilds, smart contract interaction pattern changes, and extensive regression testing validating functionality preservation across all platform features under tight timelines dictated by external provider deprecation schedules.
Diversified wallet provider support mitigates third-party dependency risks by enabling investors to choose preferred wallet solutions, providing fallback options during provider-specific issues, and reducing platform vulnerability to single provider failures. However, multi-wallet integration substantially increases development complexity, testing surface area, and ongoing maintenance burden requiring careful cost-benefit analysis balancing risk mitigation value against engineering resource constraints, quality assurance challenges, and user experience consistency maintenance across heterogeneous wallet provider capabilities and interface patterns in competitive tokenization markets.
Admin Key Compromise Scenarios in Tokenization Projects
Admin key compromise represents existential threats to real estate tokenization security vulnerabilities platforms because administrative private keys control critical platform functions including token minting authority, contract upgrade capabilities, emergency pause mechanisms, treasury fund management, and governance parameter modifications. Unlike individual investor private key compromise affecting single account holdings, admin key theft grants attackers complete platform control enabling unlimited token minting that instantly destroys all investor value through dilution, malicious contract upgrades replacing legitimate code with exploitative versions, or direct treasury drainage stealing platform reserves and investor funds held in escrow or liquidity pools.
Single administrator key storage in standard cryptocurrency wallets creates catastrophic centralization risks where phishing attacks, malware infections, or social engineering targeting single platform administrators enables complete platform compromise. Historical DeFi protocol exploits demonstrate how compromised admin keys facilitated theft of hundreds of millions in investor funds within minutes through malicious contract upgrades, unlimited token minting, or direct fund transfers that individual investors cannot prevent or reverse once unauthorized transactions execute on blockchain networks.
Critical Admin Key Compromise Attack Scenarios
Unlimited Token Minting
- Attackers mint billions of tokens instantly
- Existing investor holdings diluted to worthlessness
- Market flooding crashes token value completely
- Platform credibility permanently destroyed
- Recovery impossible without full contract migration
Malicious Contract Upgrades
- Legitimate contract replaced with exploitative version
- Ownership transfer logic modified enabling theft
- Fee structures changed to extract maximum value
- Dividend distribution redirected to attacker addresses
- Platform functionality completely compromised
Treasury Fund Drainage
- Direct transfer of platform reserves to attacker
- Investor escrow funds stolen without recourse
- Liquidity pool drainage crashing secondary markets
- Reserve backing for tokens completely eliminated
- Platform insolvency triggering immediate collapse
Governance Takeover
- Voting parameters modified to ensure attacker control
- Proposal thresholds adjusted preventing legitimate governance
- Time-locks removed enabling instant malicious changes
- Multi-signature requirements bypassed or replaced
- Democratic platform control permanently eliminated
Access Control Subversion
-
- Additional admin addresses granted to attacker accomplices
- Legitimate administrator access revoked
- Role-based permissions restructured favoring attackers
- Emergency controls disabled preventing incident response
- Persistent backdoors installed for future exploitation
Platform Ransomware
- Emergency pause activated freezing all transactions
- Ransom demanded for restoring platform functionality
- Investor panic selling crashes token values
- Regulatory intervention triggered by operational halt
- Platform reputation damage regardless of resolution
Multi-signature wallet requirements for administrative functions represent essential security controls mitigating admin key compromise risks by requiring multiple authorized signers to approve critical operations including contract upgrades, token minting, treasury transfers, and governance changes. Platforms implementing 3-of-5 or 4-of-7 multi-signature schemes substantially reduce single point of failure risks because attackers must compromise multiple independent administrator keys held by different individuals in separate security contexts rather than single target providing complete platform control, significantly increasing attack complexity and detection likelihood during prolonged compromise attempts.
Time-lock mechanisms delay administrative action execution providing community oversight windows where proposed contract upgrades, parameter changes, or treasury transfers remain pending for review periods enabling investors to detect malicious proposals and exit positions before execution. Time-locks ranging from 24 hours for minor changes to 7 days for major upgrades balance security oversight requirements against operational agility needs, with longer periods appropriate for high-value platforms managing substantial tokenized real estate assets in United States, United Kingdom, UAE, and Canadian markets where investor protection priorities justify reduced operational flexibility.
Hardware wallet storage for multi-signature participants substantially enhances admin key security by isolating individual signer keys in dedicated secure devices resistant to remote attacks, malware infections, and phishing schemes. However, hardware wallet logistics including device procurement, firmware verification, secure initialization, and backup management create operational complexity requiring comprehensive procedures, training programs, and redundancy planning ensuring critical administrative capabilities remain available during hardware failures, lost devices, or compromised participants requiring key rotation without platform operational disruption.
Centralized Control Risks in Token Issuance and Management
Centralized control mechanisms in real estate tokenization security vulnerabilities platforms create fundamental tension between operational efficiency requirements and decentralization principles underlying blockchain technology, with excessive centralization introducing single points of failure, regulatory scrutiny intensification, and trust requirement contradictions undermining blockchain’s core value propositions. Platforms concentrating authority over token issuance, transfer restrictions, upgrade mechanisms, and treasury management in hands of small administrator groups replicate traditional financial intermediary risks that blockchain solutions theoretically eliminate, creating vulnerability to administrator compromise, regulatory intervention, or insider malfeasance affecting investor interests.
Token issuance centralization enables platform administrators to unilaterally mint new tokens diluting existing investor holdings, modify supply parameters affecting token economics, or create privileged token classes with superior rights compared to public investor holdings. While some centralized control remains necessary for regulatory compliance including ability to freeze transfers to sanctioned addresses or implement court-ordered seizures, excessive authority concentration creates moral hazard where administrators face temptation to abuse powers for personal benefit, respond to external pressure compromising investor interests, or make expedient decisions prioritizing short-term platform survival over long-term investor value preservation.
Progressive decentralization strategies enable real estate tokenization security vulnerabilities platforms to balance operational efficiency requirements during early stages with long-term decentralization goals reducing centralized control risks as platforms mature, regulatory frameworks clarify, and community governance capabilities develop. Initial centralization facilitates rapid decision-making, regulatory compliance demonstration, and security incident response during vulnerable launch periods, with predetermined roadmaps committing to governance authority transfer as platform stability, investor base growth, and operational experience accumulation justify reduced administrator intervention necessity.
Governance token distribution models critically impact decentralization effectiveness, with concentrated token holdings in insider hands, whale dominance, or low participation rates creating nominal decentralization masking continued centralized control reality. Fair launch mechanisms, broad token distribution, voting power caps, delegation systems enabling expert participation, and quorum requirements ensuring representative decision-making constitute essential elements of meaningful governance decentralization preventing governance theater where theoretical community control fails to materialize due to practical participation barriers and influence concentration among small stakeholder groups.[2]
Regulatory compliance requirements in United States, United Kingdom, UAE, and Canadian jurisdictions create tensions with complete decentralization because securities regulators demand identifiable responsible parties capable of implementing court orders, responding to regulatory inquiries, and maintaining investor protection mechanisms. Practical decentralization approaches therefore retain minimal centralized controls necessary for regulatory compliance including ability to freeze transfers to sanctioned addresses, implement court-ordered seizures, and provide investor information to authorities during investigations, with transparent communication regarding these persistent centralization requirements preventing investor misunderstanding about decentralization extent and regulatory obligation implications.
Multi-Signature Failures and Governance Weaknesses
Multi-signature wallet implementation failures create critical real estate tokenization security vulnerabilities despite theoretical security improvements multi-sig mechanisms provide over single-key control. Common implementation errors including insufficient signer diversity, inadequate key management practices, compromised signer coordination channels, and flawed threshold configurations substantially reduce multi-signature security benefits, potentially creating false security confidence while maintaining exploitable vulnerabilities enabling sophisticated attackers to compromise multiple signers through coordinated campaigns or exploit operational procedures circumventing intended security controls during routine administrative operations.
Signer selection and key distribution critically impact multi-signature effectiveness, with common failures including multiple keys controlled by single individual defeating multi-sig purpose, signers lacking technical expertise to validate transaction legitimacy enabling social engineering attacks, geographically concentrated signers vulnerable to simultaneous compromise, or insufficient operational procedures for secure transaction proposal review and approval coordination. Effective multi-signature implementations require truly independent signers with diverse security contexts, technical capability to understand proposed transactions, established communication protocols preventing rushed approval decisions, and geographic distribution reducing simultaneous physical compromise risks.
| Multi-Sig Failure Mode | Vulnerability Description | Security Impact | Prevention Approach |
|---|---|---|---|
| Insufficient Signer Independence | Multiple keys controlled by single individual or closely related parties defeating separation purpose | Single point of failure persists despite multi-sig appearance, compromised individual controls platform | Truly independent signers across organizations, jurisdictions, and security contexts with verification |
| Inadequate Threshold Configuration | Too low threshold (2-of-3) providing minimal security improvement or too high preventing operational efficiency | Insufficient compromise resistance or operational gridlock during signer unavailability | Risk-based threshold determination balancing security needs against operational requirements |
| Compromised Coordination Channels | Insecure communication platforms for transaction proposal discussion enabling attacker infiltration | Social engineering attacks impersonating legitimate proposals, rushed approval manipulation | Encrypted communication channels, identity verification protocols, mandatory waiting periods |
| Signer Technical Incompetence | Signers lack capability to validate transaction legitimacy enabling blind approval of malicious proposals | Rubber-stamp approvals defeating security purpose, successful social engineering attacks | Technical competence requirements, transaction simulation tools, expert consultation availability |
| Operational Procedure Bypass | Routine administrative tasks bypassing careful review through normalized approval patterns | Malicious transactions disguised as routine operations approved without scrutiny | Mandatory waiting periods, transaction categorization requiring different review depths |
| Key Loss and Recovery Failures | Lost signer keys without recovery mechanisms creating permanent operational inability | Platform lockout preventing critical operations, emergency response impossibility | Sufficient signer redundancy, documented recovery procedures, periodic key rotation testing |
| Geographic Concentration Risk | All signers located in same jurisdiction vulnerable to simultaneous legal action or physical compromise | Regulatory seizure affecting all signers, coordinated physical attacks, jurisdictional vulnerability | Geographic signer distribution across multiple jurisdictions with varying legal frameworks |
| Upgrade Mechanism Exploitation | Multi-sig wallet contract itself contains vulnerabilities enabling unauthorized signer changes | Complete multi-sig security bypass, attacker-controlled signers replacing legitimate ones | Audited multi-sig implementations, immutable signer configurations, upgrade time-locks |
Governance mechanism weaknesses beyond multi-signature failures create additional real estate tokenization security vulnerabilities including low voter participation enabling small stakeholder groups to control decisions, vote buying schemes concentrating governance power, flash loan governance attacks temporarily acquiring voting tokens to pass malicious proposals, and proposal ambiguity enabling unexpected outcomes when vague proposals receive approval without comprehensive impact understanding. Robust governance requires participation incentives, vote delegation mechanisms enabling expert representation, clear proposal specifications with simulation results, and emergency veto capabilities for obviously malicious proposals during time-locked execution windows.
Time-lock vulnerabilities in governance systems occur when implementation flaws enable bypass of intended delay periods, insufficient waiting durations fail to provide adequate community review windows, or emergency override mechanisms lack proper authorization controls. Governance time-locks should scale with proposal impact magnitude, with parameter tweaks requiring 24-48 hour delays while major contract upgrades demand 7-14 day review periods enabling comprehensive community analysis, third-party security reviews, and investor position adjustment before irreversible execution of significant platform changes affecting tokenized real estate asset values.
Emergency response governance creates challenging tradeoffs between security incident rapid response capabilities and decentralization principles, with completely decentralized systems potentially unable to quickly halt exploits during active attacks while excessive emergency powers enable administrator abuse during fabricated crises. Practical approaches implement security councils with limited emergency authorities like transaction pausing but not fund movement, require majority approval from independent council members for emergency actions, enforce maximum emergency pause durations before automatic resumption, and mandate transparent post-incident reporting explaining emergency action justifications and preventing authority normalization through routine emergency power usage.
Infrastructure-Level Security Vulnerabilities
Infrastructure-level security vulnerabilities affecting real estate tokenization security vulnerabilities platforms extend far beyond smart contract security to encompass entire technology stacks including API endpoints, database systems, cloud hosting environments, DNS infrastructure, CI/CD pipelines, and monitoring systems. These infrastructure vulnerabilities often receive insufficient security attention compared to smart contract auditing despite representing equally critical attack surfaces enabling investor data theft, platform manipulation, transaction interception, and service disruption attacks that compromise platform integrity regardless of smart contract security robustness implemented on blockchain layer.
API security vulnerabilities create primary infrastructure attack vectors where insufficient authentication mechanisms, injection vulnerabilities, rate limiting failures, and data exposure flaws enable unauthorized access to platform functionality, investor personal information, and administrative capabilities. Real estate tokenization security vulnerabilities platforms expose numerous API endpoints for wallet integration, transaction submission, property information retrieval, and administrative functions that attackers systematically probe for SQL injection vulnerabilities, broken authentication schemes, insufficient authorization checks, and sensitive data exposure opportunities requiring comprehensive API security frameworks including authentication token management, input validation, output encoding, and API gateway protection mechanisms.
Critical Infrastructure Security Layers
API Security Layer
- Authentication and authorization framework implementation
- Input validation preventing injection attacks
- Rate limiting protecting against abuse
- API gateway with WAF protection
- Comprehensive logging and monitoring
- Regular penetration testing and security assessments
Database Security
- Encrypted data at rest and in transit
- Parameterized queries preventing SQL injection
- Principle of least privilege for database access
- Regular backup validation and restoration testing
- Database activity monitoring and anomaly detection
- Network segmentation isolating database systems
Cloud Infrastructure
- Identity and access management hardening
- Cloud security posture management tools
- Misconfiguration detection and remediation
- Multi-region redundancy for availability
- Network security groups and firewalls
- Cloud audit logging and SIEM integration
DNS and Domain Security
- DNSSEC implementation preventing spoofing
- Domain registrar account security hardening
- DNS provider redundancy and monitoring
- SSL/TLS certificate management and monitoring
- CAA records restricting certificate issuance
- Anti-phishing domain monitoring services
CI/CD Pipeline Security
-
- Secure artifact repository with access controls
- Code signing and build attestation
- Dependency scanning for vulnerabilities
- Secrets management preventing credential exposure
- Immutable infrastructure deployment practices
- Production deployment approval workflows
Monitoring and Incident Response
- 24/7 security operations center monitoring
- Intrusion detection and prevention systems
- Incident response playbooks and testing
- Automated alert escalation procedures
- Post-incident forensics capabilities
- Regular disaster recovery drills
Cloud infrastructure misconfigurations represent pervasive vulnerabilities where improperly configured S3 buckets, overly permissive IAM policies, unencrypted databases, exposed administrative interfaces, and inadequate network segmentation create attack surfaces enabling data breaches, unauthorized access, and infrastructure compromise. Real estate tokenization security vulnerabilities platforms leveraging AWS, Azure, or Google Cloud infrastructure must implement comprehensive cloud security posture management tools continuously scanning for configuration drift, hardening identity and access management policies according to least privilege principles, encrypting data at rest and in transit, and maintaining network segmentation isolating sensitive systems from internet exposure and lateral movement attack paths.
Expert Consultation on Real Estate Tokenization Security Vulnerabilities
8+ years protecting tokenized real estate platforms from security vulnerabilities. Schedule your free real estate tokenization security assessment today.
DNS hijacking and domain compromise create catastrophic infrastructure vulnerabilities where attackers gaining control of platform domain names can redirect investors to phishing sites, intercept authentication credentials, steal private keys, and completely impersonate legitimate platforms without accessing any blockchain infrastructure. Domain registrar account security through strong authentication, registry lock services preventing unauthorized transfers, DNSSEC implementation preventing DNS response spoofing, and comprehensive SSL/TLS certificate monitoring detecting unauthorized issuance attempts constitute essential domain security controls protecting against these infrastructure-level attacks in United States, United Kingdom, UAE, and Canadian operational jurisdictions.
CI/CD pipeline security prevents supply chain attacks where compromised development infrastructure, malicious dependencies, or insider threats inject malicious code into production deployments affecting smart contracts, backend services, and frontend applications. Secure software development lifecycle practices including code review requirements, automated security scanning, dependency vulnerability checking, secrets management preventing credential exposure, code signing with verified attestation chains, and immutable infrastructure deployment patterns create defense-in-depth protecting against development pipeline compromise that could introduce backdoors, data exfiltration capabilities, or exploit code into production systems managing investor funds and sensitive data.
Cloud, API, and Backend Exploitation Risks
Backend system exploitation represents critical real estate tokenization security vulnerabilities because these centralized components manage investor authentication, transaction relay, property information storage, and administrative interfaces creating concentrated attack surfaces despite decentralized blockchain infrastructure. Sophisticated attackers increasingly target platform backends rather than attempting direct smart contract exploits because API vulnerabilities, database breaches, and cloud misconfigurations often provide easier attack paths enabling investor credential theft, transaction manipulation, and platform disruption without requiring deep blockchain security expertise or overcoming robust smart contract security controls.
SQL injection vulnerabilities in database query construction enable attackers to extract investor personal information, manipulate platform data, bypass authentication mechanisms, and execute arbitrary database commands potentially compromising entire backend systems. Despite SQL injection representing one of oldest and most well-understood web vulnerabilities, inadequate input validation, dynamic query construction without parameterization, and insufficient security testing continue enabling SQL injection exploits across tokenization platforms managing sensitive investor data subject to GDPR in Europe, CCPA in California, and securities law data protection requirements across United States, United Kingdom, UAE, and Canadian jurisdictions.
Authentication and session management vulnerabilities enable attackers to impersonate legitimate investors, hijack active sessions, bypass multi-factor authentication, or exploit weak password policies gaining unauthorized platform access. Robust authentication requires strong password requirements, multi-factor authentication mandatory for high-value accounts, secure session token generation and storage, appropriate session timeout configurations, protection against session fixation and hijacking attacks, and comprehensive audit logging of authentication events enabling anomaly detection and forensic investigation following suspected compromise incidents affecting investor accounts or administrative access.
DDoS attack vulnerabilities threaten platform availability where insufficient capacity planning, lack of rate limiting, absence of DDoS mitigation services, or architectural bottlenecks enable attackers to overwhelm platform infrastructure preventing legitimate investor access during critical market conditions. Real estate tokenization security vulnerabilities platforms must implement multi-layered DDoS protection including CloudFlare or similar content delivery networks absorbing application-layer attacks, rate limiting and traffic shaping at API gateways, auto-scaling infrastructure responding to traffic surges, and redundant architecture eliminating single points of failure that targeted attacks could exploit to achieve complete platform unavailability.
Data encryption requirements protect investor personal information, transaction details, and platform operational data both at rest in storage systems and in transit across networks. Regulatory compliance in United States, United Kingdom, UAE, and Canadian jurisdictions increasingly mandates encryption for sensitive personal data with violations triggering substantial penalties, while security best practices require end-to-end encryption for investor communications, TLS 1.3 for all network connections, encrypted database storage preventing data exposure during backup media theft, and comprehensive key management ensuring encryption key security receives protection commensurate with encrypted data sensitivity.
Infrastructure vs Smart Contract Risk Comparison
Understanding the comparative risk profiles between infrastructure-level vulnerabilities and smart contract security issues enables real estate tokenization security vulnerabilities platforms to allocate security resources appropriately across different threat categories. While blockchain advocates emphasize smart contract security as primary concern, practical deployment experience demonstrates that infrastructure vulnerabilities frequently provide easier attack paths with comparable or greater potential damage, requiring balanced security investment across both domains rather than disproportionate focus on smart contract security while neglecting traditional cybersecurity fundamentals in backend systems, cloud infrastructure, and API security.
| Risk Dimension | Smart Contract Risks | Infrastructure Risks | Mitigation Priority |
|---|---|---|---|
| Attack Complexity | High technical expertise required, blockchain-specific knowledge, exploit development complexity | Lower barrier to entry, standard web vulnerabilities, automated scanning tools available | Infrastructure requires immediate attention due to accessibility |
| Attack Reversibility | Immutable transactions, no reversal capability, permanent fund loss | Potential recovery through backups, incident response, system restoration | Smart contract irreversibility demands prevention focus |
| Vulnerability Detection | Specialized auditing firms, formal verification, limited automated tools | Mature scanning tools, established testing methodologies, widespread expertise | Infrastructure benefits from mature security ecosystem |
| Patch Deployment | Complex migration, investor impact, governance approval, upgrade mechanisms | Standard update procedures, minimal user disruption, rapid deployment capability | Infrastructure enables faster vulnerability remediation |
| Financial Impact | Direct fund theft, unlimited token minting, complete treasury drainage | Data breaches, service disruption, regulatory penalties, reputation damage | Both create existential threats requiring equal priority |
| Regulatory Scrutiny | Securities law violations, investor protection failures, novel regulatory questions | Data privacy violations, cybersecurity requirement failures, established compliance frameworks | Infrastructure violations more predictable but equally severe |
| Attacker Motivation | High-value targets, cryptocurrency direct access, laundering complexity | Personal data monetization, credential theft, ransomware deployment | Different threat actors require distinct security strategies |
| Defense Maturity | Evolving best practices, limited historical precedent, nascent security tools | Decades of security research, established frameworks, comprehensive tool ecosystem | Infrastructure leverages mature security knowledge |
The comparative analysis reveals that while smart contract vulnerabilities create irreversible fund loss risks demanding prevention-focused security approaches, infrastructure vulnerabilities often provide easier attack paths for less sophisticated adversaries using automated tools and well-documented exploitation techniques. Real estate tokenization security vulnerabilities platforms must therefore implement comprehensive security programs addressing both vulnerability categories rather than blockchain-centric security strategies neglecting traditional cybersecurity fundamentals that attackers increasingly exploit as primary platform compromise vectors when robust smart contract security prevents direct blockchain-layer attacks.
Security resource allocation should reflect balanced risk assessment considering attack likelihood, potential impact, detection capability, and remediation complexity across both infrastructure and smart contract domains. Platforms managing substantial tokenized real estate assets exceeding ten million dollars in value should maintain dedicated security teams covering both traditional cybersecurity expertise for infrastructure protection and blockchain-specific security specialists for smart contract auditing, with regular cross-training ensuring comprehensive threat understanding across both domains and coordination during security incidents potentially affecting multiple platform layers simultaneously.
Incident response capabilities must address both infrastructure and smart contract compromises with distinct procedures reflecting different remediation approaches, recovery timelines, and investor communication requirements. Infrastructure breaches may enable rapid response through system restoration from backups, credential rotation, and vulnerability patching with minimal investor disruption, while smart contract exploits demand complex migration procedures, governance approvals, potential fund recovery negotiations, and extensive investor communication explaining technical details and remediation plans in United States, United Kingdom, UAE, and Canadian jurisdictions with varying regulatory reporting requirements.
Regulatory and Compliance-Related Security Risks
Regulatory compliance failures amplify real estate tokenization security vulnerabilities by preventing access to institutional security frameworks, limiting operational jurisdictions, creating legal ambiguity around investor protections, and attracting sophisticated attackers who target non-compliant platforms expecting reduced legal recourse following theft. Securities regulations in United States administered by SEC, United Kingdom oversight by FCA, Dubai requirements from DFSA, and Canadian provincial securities authorities mandate comprehensive security controls protecting investor capital and personal data as preconditions for platform authorization, with non-compliance triggering enforcement actions potentially more damaging than security incidents themselves.
KYC and AML compliance requirements create tension with privacy-preserving blockchain principles while simultaneously introducing security vulnerabilities through centralized identity data storage. Real estate tokenization security vulnerabilities platforms must collect, verify, and securely store extensive investor personal information including government identification documents, proof of address, source of funds documentation, and beneficial ownership details creating attractive targets for data breaches, identity theft, and regulatory reporting failures. Secure KYC data management requires encryption at rest and transit, access controls limiting personnel exposure, audit logging tracking data access, retention policies minimizing storage duration, and incident response procedures addressing potential breaches under GDPR, CCPA, and similar data protection regulations.
Regulatory Compliance Security Framework
Securities Law Compliance
- Registration or exemption qualification verification
- Accredited investor verification mechanisms
- Transfer restriction enforcement technology
- Disclosure requirement fulfillment systems
- Ongoing reporting compliance infrastructure
- Regulatory audit trail maintenance
Data Privacy Protection
- GDPR compliance for European investors
- CCPA requirements for California residents
- Data minimization and purpose limitation
- Consent management and withdrawal mechanisms
- Data subject access request procedures
- Cross-border transfer compliance frameworks
AML/CFT Requirements
- Customer due diligence procedures
- Beneficial ownership identification
- Suspicious activity monitoring and reporting
- Sanctions screening against OFAC lists
- Transaction monitoring for unusual patterns
- Record retention meeting regulatory minimums
Cybersecurity Obligations
- NYDFS cybersecurity regulation compliance
- SEC cybersecurity disclosure requirements
- Incident notification timelines adherence
- Third-party risk management programs
- Penetration testing and vulnerability assessments
- Business continuity and disaster recovery
Investor Protection Standards
-
- Custody and safeguarding requirements
- Segregated investor fund management
- Conflict of interest disclosures
- Fair dealing and best execution obligations
- Complaint handling procedures
- Financial resource adequacy maintenance
Audit and Reporting
- Annual financial statement audits
- Smart contract audit documentation
- Regulatory examination cooperation
- Ongoing compliance attestations
- Material change event reporting
- Transparent disclosure maintenance
Cross-border regulatory complexity creates jurisdiction-specific security requirements where platforms operating across United States, United Kingdom, UAE, and Canadian markets must simultaneously comply with potentially conflicting data localization requirements, privacy standards, securities regulations, and cybersecurity mandates. GDPR’s strict data protection requirements may conflict with SEC investigation cooperation obligations, Canadian provincial securities variations create compliance complexity, and Dubai’s emerging tokenization framework introduces novel requirements that platforms must integrate into comprehensive compliance programs without creating security gaps through jurisdictional inconsistencies or regulatory arbitrage attempts.
Smart contract compliance features including transfer restrictions, investor verification requirements, and regulatory freeze capabilities introduce additional security considerations because these compliance mechanisms create privileged administrative functions that attackers may exploit or regulators may demand activate in ways affecting platform integrity. Balance between regulatory compliance capabilities and decentralization principles requires careful design ensuring compliance functions operate transparently with appropriate limitations, governance oversight, and investor protections preventing abuse while maintaining regulatory authority cooperation necessary for legal operation in major jurisdictions.
Regulatory reporting security requirements demand secure data transmission, audit trail preservation, and confidentiality maintenance when providing investor information, transaction data, and platform operational details to securities regulators, tax authorities, and law enforcement agencies. Secure regulatory reporting infrastructure requires encrypted communication channels, access controls limiting personnel exposure to sensitive regulatory data, comprehensive logging documenting information disclosures, legal review procedures ensuring appropriate disclosure scope, and investor notification mechanisms where privacy regulations mandate disclosure of personal data sharing with governmental authorities during investigations or compliance examinations.
Data Privacy and Investor Identity Protection Risks
Data privacy risks in real estate tokenization security vulnerabilities create fundamental tension between blockchain transparency principles and regulatory privacy requirements, with investor personal information, transaction histories, and property ownership records potentially exposed through blockchain analysis, platform breaches, or inadequate anonymization techniques. Unlike traditional real estate transactions where title records receive some privacy protection through governmental access controls, blockchain’s public transparency enables sophisticated analysis correlating wallet addresses with real-world identities, tracking investment patterns, and building comprehensive investor profiles that privacy regulations in United States, United Kingdom, UAE, and Canada increasingly restrict through GDPR, CCPA, and similar frameworks.
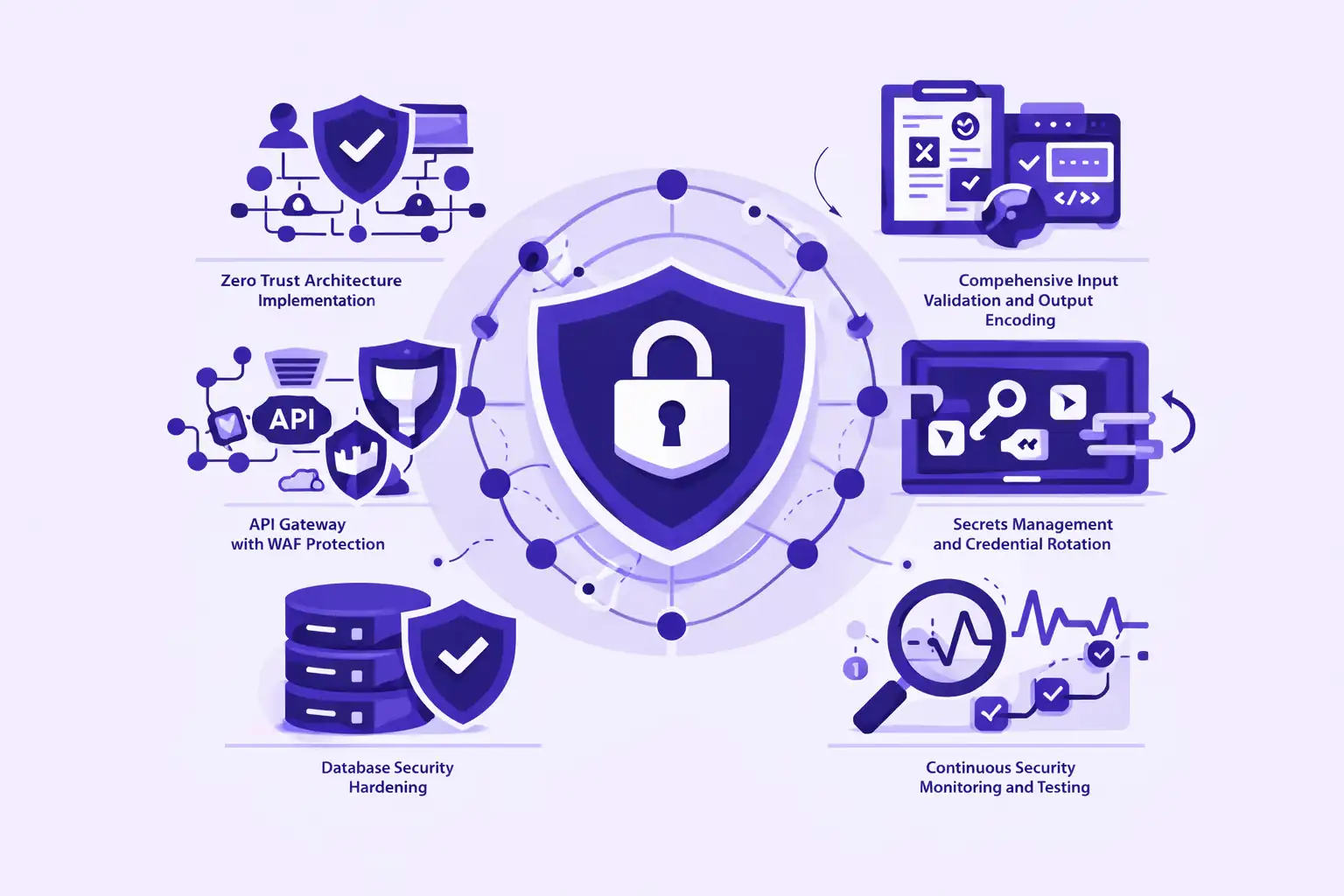
Identity verification data breaches represent catastrophic privacy failures because KYC information includes government identification documents, proof of address, financial statements, and beneficial ownership details that enable comprehensive identity theft, financial fraud, and targeted social engineering attacks against wealthy real estate investors. Real estate tokenization security vulnerabilities platforms accumulate extensive personal data across thousands of investors creating concentrated targets where single database breach exposes massive personal information volumes potentially affecting individuals across multiple jurisdictions with varying breach notification requirements, liability standards, and regulatory penalty frameworks that could bankrupt platforms following major incidents.
Blockchain analysis risks enable sophisticated observers to correlate public blockchain transaction data with investor identities through pattern analysis, exchange interaction tracking, and cross-referencing with publicly available information sources. While blockchain addresses provide pseudonymity rather than anonymity, determined analysts can often de-anonymize investors by tracking token flows, analyzing transaction timing patterns, correlating with property purchase announcements, or exploiting platform privacy failures exposing address-to-identity mappings. Privacy-preserving technologies including zero-knowledge proofs, confidential transactions, and privacy-focused blockchain layers offer technical solutions but introduce complexity and may face regulatory resistance in jurisdictions requiring transaction transparency for anti-money laundering compliance.
Investor consent management becomes complex when platforms must balance GDPR’s strict consent requirements with practical platform operation necessities, withdrawal consent implications for ongoing service delivery, and consent portability across jurisdictions with varying standards. Effective consent management requires granular consent controls enabling investors to approve specific data processing purposes, clear explanations of data usage implications, simple withdrawal mechanisms, and systems tracking consent status changes ensuring data processing only occurs with valid current consent meeting regulatory requirements in European Union, California, and other privacy-forward jurisdictions where tokenization platforms operate.
Data subject access requests under GDPR and similar regulations require platforms to provide investors comprehensive information about collected personal data, processing purposes, data recipients, storage duration, and automated decision-making logic within strict deadlines typically 30 days or less. Implementing efficient data subject access request procedures requires centralized personal data inventories, automated extraction capabilities, verification procedures preventing unauthorized access requests, and secure delivery mechanisms protecting personal information during disclosure while maintaining comprehensive audit trails documenting compliance with data subject rights including access, rectification, erasure, restriction, portability, and objection rights across United States, United Kingdom, UAE, and Canadian operational jurisdictions.
Risk Prevention Strategies for Secure Real Estate Tokenization
Implementing comprehensive risk prevention strategies requires real estate tokenization security vulnerabilities platforms to adopt defense-in-depth security architectures spanning smart contract security, infrastructure protection, operational security, regulatory compliance, and continuous monitoring creating multiple overlapping security layers that collectively prevent successful exploitation even when individual controls fail. Our eight years deploying secure tokenization platforms across United States, United Kingdom, UAE, and Canadian markets has demonstrated that security excellence demands sustained commitment, significant resource investment, specialized expertise recruitment, and organizational culture prioritizing security over expedient feature delivery or cost reduction pressures.
Smart contract security foundations require comprehensive pre-deployment validation including multiple independent third-party audits from reputable security firms specializing in blockchain protocols, formal verification of critical contract functions proving correctness under all possible conditions, extensive automated testing including fuzzing campaigns generating thousands of edge case scenarios, economic modeling identifying profitable attack vectors, and public bug bounty programs incentivizing white-hat researcher discovery of vulnerabilities before malicious exploitation. These validation activities should commence early in development lifecycle enabling iterative security improvements rather than treating audits as final deployment checkpoints discovering vulnerabilities too late for comprehensive remediation.
Security Implementation Lifecycle
Design Phase Security
- Threat modeling identifying attack surfaces early
- Security requirements specification
- Architecture review for security patterns
- Privacy impact assessment completion
- Regulatory compliance gap analysis
- Security-focused technology selection
Development Phase Security
- Secure coding guidelines enforcement
- Automated security scanning in CI/CD
- Peer code review with security focus
- Unit testing including security cases
- Dependency vulnerability monitoring
- Secrets management implementation
Pre-Deployment Validation
- Multiple independent security audits
- Penetration testing by ethical hackers
- Smart contract formal verification
- Bug bounty program launch
- Load and stress testing validation
- Disaster recovery procedure testing
Deployment Hardening
- Production environment isolation
- Infrastructure security configuration
- Monitoring and alerting activation
- Incident response team readiness
- Communication plan preparation
- Limited initial deployment scope
Operational Security
-
- 24/7 security operations monitoring
- Regular security assessment updates
- Vulnerability patch management
- Access review and certification
- Security awareness training
- Third-party risk management
Continuous Improvement
- Incident post-mortem analysis
- Security metrics tracking and reporting
- Emerging threat research monitoring
- Security architecture evolution
- Regulatory requirement adaptation
- Industry best practice adoption
Infrastructure security requires comprehensive protection across all technology layers including secure cloud configurations following least privilege principles, network segmentation isolating sensitive systems, API gateways with web application firewalls blocking common attacks, database encryption protecting investor data, secure CI/CD pipelines preventing supply chain compromise, and DNS security preventing domain hijacking. Regular penetration testing by independent security firms validates infrastructure security effectiveness, vulnerability scanning identifies configuration drift and software vulnerabilities, and security information and event management systems aggregate logs enabling anomaly detection and forensic investigation during incidents.
Operational security procedures govern day-to-day platform operation including secure key management through hardware wallets and multi-signature schemes, personnel security with background checks and security training, access controls limiting system exposure to minimum necessary personnel, change management processes preventing unauthorized modifications, incident response playbooks enabling rapid coordinated action during attacks, and business continuity plans ensuring operations continue during security incidents or infrastructure failures. These operational procedures require regular testing through tabletop exercises and simulated incidents validating team readiness and process effectiveness.
Regulatory compliance integration ensures security controls meet or exceed requirements across operational jurisdictions including securities law compliance for investor protection, data privacy adherence under GDPR and similar frameworks, anti-money laundering procedures preventing platform abuse, cybersecurity regulations like NYDFS requirements, and industry standards like SOC 2 providing independent validation of security control effectiveness. Compliance integration prevents situations where security measures inadequately address regulatory requirements or compliance activities undermine security architecture, requiring security and compliance teams to collaborate closely throughout platform development and operation in United States, United Kingdom, UAE, and Canadian markets.
Best Practices for Long-Term Security and Risk Mitigation
Long-term security excellence in real estate tokenization security vulnerabilities requires sustained organizational commitment transcending initial platform launch security efforts, recognizing that threat landscapes continuously evolve, new vulnerabilities emerge regularly, regulatory requirements change, and platform complexity increases over time demanding perpetual security investment and improvement. Platforms achieving multi-year operational track records without major security incidents demonstrate consistent security culture, adequate resource allocation, technical expertise retention, and adaptive security strategies responding to emerging threats rather than static security programs becoming obsolete as attack techniques advance.

Security governance establishes organizational structures, decision-making processes, and accountability frameworks ensuring security receives appropriate priority in resource allocation, feature development, and incident response decisions. Effective security governance includes board-level security oversight, dedicated chief information security officer with authority and budget, security steering committees with cross-functional representation, risk management frameworks quantifying security exposures, and key performance indicators measuring security program effectiveness enabling data-driven improvement and executive visibility into security posture evolution over time in competitive tokenization markets.
Security metrics and key performance indicators enable data-driven security program management measuring effectiveness, identifying improvement areas, and demonstrating security posture to investors and regulators. Relevant metrics include time to detect security incidents, vulnerability remediation timelines, audit finding closure rates, security training completion percentages, third-party risk assessment coverage, and incident response exercise frequency. These metrics should trend positively over time reflecting security program maturity and organizational security capability development rather than static baseline maintenance suggesting security stagnation.
Insurance coverage for cyber liability and smart contract risks provides additional investor protection layer acknowledging that despite comprehensive security measures, determined attackers may successfully compromise platforms requiring financial resources for incident response, investor compensation, regulatory penalty payment, and platform restoration. Obtaining insurance coverage itself validates security program effectiveness as insurers conduct thorough security assessments before policy issuance, with favorable rates and coverage terms reflecting strong security postures while platforms with inadequate security face coverage denial or prohibitive premium costs.
Community engagement and investor education reduce security risks by creating informed user base resistant to phishing attacks, understanding security best practices, making appropriate security tradeoff decisions, and providing valuable security feedback identifying suspicious activities or potential vulnerabilities. Regular security communications, educational content about common threats, platform security feature explanations, and investor security tool provision including approval management interfaces and transaction simulation capabilities empower investors to protect themselves while reducing platform support burden addressing security incident aftermath in United States, United Kingdom, UAE, and Canadian investor communities.
The evolution of real estate tokenization security vulnerabilities security demands ongoing investment, adaptation, and commitment as platforms mature, manage increasing asset values, face sophisticated adversaries, and operate under intensifying regulatory scrutiny. Platforms demonstrating security excellence through multi-year incident-free operations, transparent communication, comprehensive audit trails, and continuous improvement position themselves for long-term success capturing institutional capital flows, regulatory approval, and investor confidence essential for sustainable growth in emerging tokenized real estate markets across major global financial centers and investment hubs worldwide.
People Also Ask
The most common security vulnerabilities in real estate tokenization security vulnerabilities include smart contract exploits such as reentrancy attacks and logic flaws, inadequate access controls enabling unauthorized token manipulation, private key compromise through phishing or malware, oracle manipulation affecting property valuation data, and insufficient audit processes before deployment. Additionally, centralized points of failure in admin key management, weak wallet integration security, API vulnerabilities in backend infrastructure, and regulatory non-compliance creating legal exposure represent critical threat vectors that require comprehensive security frameworks to address effectively.
Smart contract vulnerabilities can catastrophically compromise tokenized real estate investments by enabling attackers to drain funds through exploits, manipulate ownership records to steal property tokens, freeze asset transfers leaving investors unable to liquidate positions, or alter dividend distribution logic to redirect rental income. Flaws like integer overflow, unchecked external calls, or improper access modifiers can allow malicious actors to mint unauthorized tokens, bypass transfer restrictions, or execute governance attacks. Since smart contracts are immutable once deployed, undetected vulnerabilities become permanent attack surfaces requiring expensive migration processes and potentially causing total investment loss.
Private keys serve as the fundamental security mechanism controlling ownership and transfer rights in tokenized real estate, functioning as cryptographic proof of asset ownership without reliance on intermediaries. Compromised private keys grant attackers complete control over associated tokens, enabling irreversible theft of valuable property shares. Unlike traditional real estate where ownership changes require legal documentation and title transfer processes, blockchain transactions executed with stolen private keys cannot be reversed or disputed. This makes private key security through hardware wallets, multi-signature schemes, key sharding, secure storage solutions, and comprehensive user education absolutely critical to preventing catastrophic asset loss in tokenization platforms.
Admin key compromises represent existential threats to real estate tokenization security vulnerabilities platforms by granting attackers privileged access to critical platform functions including token minting, transfer restrictions, upgrade mechanisms, and treasury controls. Compromised admin keys enable attackers to mint unlimited tokens diluting existing investor holdings, freeze legitimate transactions, upgrade contracts to malicious versions, drain platform treasuries, manipulate property valuation oracles, or completely halt platform operations. The centralized nature of admin keys creates single points of failure that, when exploited, can instantly destroy platform credibility, trigger investor panic, result in regulatory enforcement actions, and cause irreparable reputational damage requiring complete platform reconstruction.
Beyond smart contracts, tokenization platforms face substantial infrastructure vulnerabilities including API endpoints susceptible to injection attacks and unauthorized access, cloud storage misconfigurations exposing sensitive investor data, database systems vulnerable to SQL injection and data breaches, DNS hijacking redirecting users to phishing sites, DDoS attacks overwhelming platform availability, insecure communication protocols exposing transaction data, compromised CI/CD pipelines introducing malicious code, and weak authentication mechanisms enabling account takeovers. These infrastructure-level vulnerabilities often receive insufficient attention compared to smart contract security despite representing equally critical attack surfaces that can compromise investor funds, personal information, and platform integrity.
Regulatory compliance failures create significant security risks by exposing platforms to enforcement actions that can freeze operations and investor funds, attracting sophisticated attackers who target non-compliant platforms expecting reduced legal recourse, creating legal ambiguity around investor protections that enables fraud, preventing implementation of necessary security measures like KYC/AML that deter malicious actors, limiting access to institutional security infrastructure and insurance, and establishing environments where security corners are cut to avoid regulatory scrutiny. Non-compliance also prevents platforms from operating in regulated markets like the USA, UK, UAE, and Canada where investor protection frameworks provide additional security layers, forcing operations into jurisdictions with minimal oversight.
Inadequate smart contract auditing creates catastrophic risks including undetected critical vulnerabilities that attackers can exploit post-deployment, logic flaws enabling ownership manipulation and unauthorized token transfers, economic exploits allowing infinite token minting or value extraction, governance vulnerabilities permitting hostile takeovers, integration issues with external protocols creating attack vectors, gas optimization problems enabling denial-of-service attacks, and compliance gaps violating securities regulations. Without comprehensive third-party audits from reputable firms, formal verification of critical functions, extensive testing across attack scenarios, and continuous monitoring post-deployment, tokenization projects essentially deploy experimental code controlling millions in real estate assets with no validated security assurances.
Wallet integration vulnerabilities compromise investor security by creating attack surfaces where malicious dApps can drain approved tokens, phishing sites can trick users into signing unauthorized transactions, compromised wallet providers can expose private keys or transaction data, vulnerable browser extensions can inject malicious transaction parameters, insufficient transaction preview mechanisms can hide theft attempts, lack of spending limits can enable complete account drainage from single approvals, and inadequate revocation mechanisms can leave historical approvals exploitable indefinitely. These vulnerabilities are particularly dangerous because they exploit the trust relationship between users and their wallet interfaces, often bypassing smart contract security measures entirely.
Preventing oracle manipulation requires implementing decentralized oracle networks aggregating data from multiple independent sources, using cryptographic proofs verifying data authenticity and integrity, establishing deviation thresholds requiring significant consensus before accepting price updates, implementing time-weighted average pricing reducing impact of temporary manipulation, utilizing reputation systems penalizing oracles providing inaccurate data, deploying circuit breakers halting operations during anomalous price movements, maintaining multiple independent valuation methodologies for cross-validation, establishing governance processes for dispute resolution, and conducting regular audits of oracle infrastructure and data sources. These measures are critical because oracle manipulation can artificially inflate property valuations, trigger improper liquidations, or enable arbitrage attacks.
Investors can protect themselves by conducting thorough due diligence on platform security including reviewing smart contract audits from reputable firms, verifying regulatory compliance in relevant jurisdictions, assessing admin key management and governance structures, evaluating insurance coverage for smart contract risks, using hardware wallets for token storage, enabling multi-signature requirements for large transactions, regularly reviewing token approvals and revoking unnecessary permissions, diversifying across multiple platforms and properties, staying informed about platform security updates and incident responses, participating in governance to influence security decisions, and maintaining awareness of common attack vectors like phishing and social engineering targeting tokenization platform users.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.






