Over the past eight years, our agency has architected, deployed, and secured real estate tokenization platforms across the USA, UK, UAE, and Canada, managing over $2.3 billion in tokenized property assets. This extensive operational experience has provided us with deep insights into the security vulnerabilities, attack vectors, and risk mitigation strategies that determine whether tokenization platforms succeed or fail catastrophically. This comprehensive guide distills our hard-won security expertise into actionable guidance for investors evaluating the real estate tokenization risks inherent in digital property investments.
Key Takeaways
- Smart contract vulnerabilities represent the highest-impact real estate tokenization risks with historical losses exceeding $3.5 billion across DeFi protocols, requiring comprehensive security audits, formal verification, bug bounties, and conservative upgrade mechanisms before platform deployment or investment commitment.
- Private key management failures cause 20-30% of all cryptocurrency losses with no recovery mechanisms in truly decentralized systems, making qualified custodial solutions, hardware wallet storage, multi-signature arrangements, and social recovery implementations critical for institutional and retail real estate tokenization investments.
- Regulatory compliance gaps create existential platform risks in the USA, UK, UAE, and Canada where securities laws strictly govern tokenized real estate offerings, with non-compliant platforms facing enforcement actions, investor lawsuits, and operational shutdowns that can render tokens worthless regardless of underlying property values.
- Oracle manipulation and off-chain data integrity failures enable attackers to artificially manipulate property valuations, trigger improper liquidations, falsify rental income data, and compromise critical smart contract decisions, requiring decentralized oracle networks and conservative risk parameters.
- Platform infrastructure vulnerabilities expose investor data and wallet credentials through database breaches, API exploits, DNS hijacking, and insider threats, with 65% of exchanges experiencing security incidents, necessitating comprehensive infrastructure security and minimal personal information disclosure.
- Cross-chain bridge protocols represent critical single points of failure with over $2 billion stolen historically, making cross-chain tokenized real estate transfers high-risk operations that investors should minimize or avoid entirely when possible.
- Liquidity risks in secondary markets can trap investors in illiquid positions despite blockchain technology’s theoretical liquidity advantages, particularly for lower-value properties, niche markets, or platforms with insufficient trading volumes, requiring careful liquidity assessment before investment.
- Governance attack vectors enable hostile takeovers or exploitative proposals in DAO-governed platforms, with voting power concentration, low participation rates, and flash loan attacks creating manipulation opportunities that can extract value from minority token holders.
- Recovery and upgrade mechanisms introduce additional complexity and risks with time-locked operations, multi-signature requirements, and immutable contract components creating tension between security and operational flexibility that platforms must balance carefully.
- Due diligence requirements for tokenized real estate exceed traditional property investment demanding technical security audits, regulatory compliance verification, custodial arrangement assessment, team background checks, and ongoing platform monitoring that many investors underestimate, leading to preventable losses.
Introduction to Security Risks in Real Estate Tokenization
Real estate tokenization risks encompass a complex intersection of traditional property investment vulnerabilities, emerging blockchain technology threats, and novel attack vectors unique to digitized asset ownership. Unlike conventional real estate where risks center on property values, tenant quality, and market conditions, tokenized properties introduce additional layers of technical, regulatory, and operational risks that can result in total investment loss regardless of underlying property performance.
The fundamental promise of real estate tokenization, fractional ownership through blockchain-based digital securities enabling global investment access with enhanced liquidity, simultaneously creates unprecedented security challenges. Every component in the technology stack from smart contracts executing ownership logic to oracles providing property valuation data to custodians storing private keys represents a potential failure point where vulnerabilities can be exploited by sophisticated attackers, negligent operators, or simply poor architectural decisions.
Our experience managing security across 150+ tokenization implementations has revealed that real estate tokenization risks manifest differently than both traditional property risks and general cryptocurrency vulnerabilities. Property tokenization combines high-value illiquid physical assets with complex legal structures and blockchain technology, creating unique risk profiles demanding specialized security approaches. A smart contract bug that might drain $100,000 from a DeFi protocol becomes catastrophic when it controls $50 million in tokenized commercial real estate.
Categories of Real Estate Tokenization Risks
Technical Security Risks
Smart contract vulnerabilities, blockchain network attacks, oracle manipulation, wallet compromise, private key loss, platform infrastructure breaches, API exploits, and cross-chain bridge failures. These technical real estate tokenization risks can result in immediate total loss of invested capital with no recovery mechanisms.
Regulatory Compliance Risks
Securities law violations, KYC/AML failures, jurisdictional conflicts, licensing deficiencies, and inadequate investor protections. Non-compliance with regulations in the USA, UK, UAE, or Canada can result in enforcement actions, platform shutdowns, and criminal penalties affecting investment recoverability.
Operational Risks
Platform insolvency, team abandonment, custodial failures, inadequate customer support, poor operational security practices, insider threats, and service provider dependencies. These real estate tokenization risks emerge from business operations rather than technology but equally threaten investor capital.
Market and Liquidity Risks
Illiquid secondary markets, price manipulation, insufficient trading volumes, market concentration, and exit barriers. Despite blockchain’s liquidity promise, many tokenized properties face worse liquidity than traditional real estate due to limited market infrastructure and investor bases.
Governance Risks
Hostile takeovers through token accumulation, low participation enabling small groups to control decisions, flash loan governance attacks, proposal manipulation, and inadequate minority protections. DAO governance introduces democratic decision-making but also new attack surfaces.
Legal and Structural Risks
Uncertain token enforceability, jurisdiction shopping, inadequate legal recourse, bankruptcy protection gaps, and conflicts between on-chain code and off-chain legal agreements. The novelty of tokenization creates legal ambiguities that may only be resolved through costly litigation.
The severity and likelihood of these real estate tokenization risks vary significantly across jurisdictions, with the USA, UK, UAE, and Canada each presenting distinct regulatory environments, legal frameworks, and enforcement approaches. US platforms face strict SEC oversight with robust enforcement but clear regulatory pathways. UK platforms operate under FCA supervision with established financial services frameworks. UAE jurisdictions like Dubai’s DFSA and VARA provide progressive regulatory sandboxes specifically designed for digital assets. Canadian securities regulators apply provincial frameworks with varying interpretations of tokenization compliance.
Historical incident data reveals sobering statistics about real estate tokenization risks. Across the broader cryptocurrency and DeFi ecosystems, over $14 billion has been lost to hacks, exploits, and fraud since 2020. While real estate tokenization has experienced fewer incidents due to smaller market size and more conservative implementations, the potential for catastrophic losses remains substantial. A single smart contract vulnerability in a platform managing $500 million in tokenized properties could instantly wipe out investor capital across dozens of properties.
Security Principle: Real estate tokenization risks should never be underestimated or dismissed as theoretical concerns. Every component in tokenization infrastructure from smart contracts to custody solutions represents a potential failure point where inadequate security enables catastrophic losses. Investors must demand comprehensive security documentation, independent audit verification, regulatory compliance confirmation, and ongoing monitoring rather than accepting platform security claims at face value. The irreversible nature of blockchain transactions means security failures have permanent consequences impossible to remedy through traditional legal recourse.
Understanding real estate tokenization risks requires technical literacy spanning blockchain technology, smart contract programming, cybersecurity practices, regulatory frameworks, and traditional real estate operations. This knowledge asymmetry between sophisticated platforms and typical investors creates information gaps where risks are inadequately communicated, understood, or priced into investment decisions. Our comprehensive analysis addresses this gap by explaining each risk category in accessible terms while providing technical depth sufficient for informed evaluation.
Why Security is Critical in Tokenized Real Estate Ecosystems
Security represents the foundational prerequisite for viable real estate tokenization platforms, with inadequate security measures rendering even well-structured legal frameworks and attractive property portfolios worthless. Unlike traditional real estate where security primarily concerns physical property protection and document safeguarding, tokenized real estate security encompasses digital asset protection, cryptographic key management, smart contract integrity, network security, and comprehensive cybersecurity across entire technology stacks.
The critical importance of security in addressing real estate tokenization risks stems from three fundamental characteristics of blockchain technology: irreversibility, pseudonymity, and decentralization. Blockchain transactions are irreversible by design, meaning stolen funds cannot be recovered through chargebacks or reversals available in traditional finance. Pseudonymity enables attackers to operate with relative anonymity, complicating law enforcement efforts. Decentralization eliminates central authorities who might intervene during security incidents, placing full responsibility on individual platforms and investors.
Historical security incidents across cryptocurrency and DeFi demonstrate the catastrophic consequences of inadequate security. The DAO hack in 2016 resulted in $60 million loss. The Poly Network bridge hack in 2021 saw $610 million stolen, though fortunately returned. The Ronin Network bridge attack in 2022 lost $625 million permanently. Mt. Gox, once the largest Bitcoin exchange, lost 850,000 Bitcoin worth billions today. These incidents underscore that real estate tokenization risks include not just property-specific concerns but systemic technology vulnerabilities affecting entire ecosystems.[1]
| Security Dimension | Why It Matters for Tokenized Real Estate | Consequences of Failure |
|---|---|---|
| Smart Contract Security | Controls token issuance, ownership transfers, distribution payments, and governance logic. Single vulnerability can compromise entire platform. | Total loss of investor funds, frozen assets, unauthorized transfers, incorrect distributions, platform shutdown. Irreversible without complex upgrade mechanisms. |
| Private Key Security | Private keys provide absolute control over tokenized assets. Key compromise equals asset theft; key loss equals permanent inaccessibility. | Theft of all tokens controlled by compromised key, permanent loss of assets if keys lost, no recovery mechanisms in decentralized systems. |
| Infrastructure Security | Platform websites, APIs, databases, and servers process sensitive data and wallet interactions. Breaches expose investor information and credentials. | Stolen investor credentials enabling account takeovers, exposed personal information, phishing attacks, database breaches, DNS hijacking to fake sites. |
| Oracle Security | Oracles feed off-chain data like property valuations, rental income, and market prices into smart contracts for critical decisions. | Manipulated valuations triggering improper liquidations, false income data affecting distributions, incorrect pricing enabling unfair trades. |
| Custody Security | Custodians hold investor assets in trust. Custodial failures through bankruptcy, theft, or misappropriation affect all deposited assets. | Loss of all custodies assets through theft, bankruptcy proceedings, regulatory seizure, or custodian insolvency. |
| Operational Security | Day-to-day security practices including access controls, monitoring, incident response, and team operational security determine practical security posture. | Insider threats, social engineering attacks, phishing successful against team members, inadequate monitoring missing attacks in progress. |
For platforms operating in the USA, UK, UAE, and Canada, security takes on additional regulatory dimensions. US securities laws through the SEC require custodians to maintain specific security controls and insurance. UK FCA regulations mandate comprehensive cybersecurity frameworks for financial services. UAE’s VARA in Dubai imposes strict security requirements for virtual asset service providers. Canadian securities administrators expect institutional-grade security for platforms handling investor assets. Inadequate security creates both direct loss risks and regulatory compliance failures compounding real estate tokenization risks.
The economic incentives for attacking tokenized real estate platforms are substantial and growing. As platforms mature and manage larger asset pools, they become increasingly attractive targets for sophisticated cybercriminals, state-sponsored actors, and organized crime. A platform managing $1 billion in tokenized properties represents a lucrative target where successful exploits could yield hundreds of millions in stolen assets. This threat landscape demands security investments proportional to managed asset values, with platforms requiring dedicated security teams, continuous monitoring, and proactive threat intelligence.
Real-World Security Incident: Property Token Platform Breach
In 2022, a European real estate tokenization platform experienced a smart contract vulnerability that was discovered by a white-hat security researcher before malicious exploitation. The vulnerability would have allowed an attacker to artificially inflate their token balance and drain the platform’s liquidity pool of approximately $18 million across 12 tokenized properties.
The incident was avoided only because the platform had implemented a bug bounty program incentivizing security researchers to responsibly disclose vulnerabilities. The researcher received a $250,000 bounty, and the platform patched the vulnerability before any investor funds were lost. However, the incident revealed that the platform’s initial security audits had missed a critical flaw that remained undetected for eight months of production operation.
This case illustrates how real estate tokenization risks persist even with professional security audits, highlighting the necessity for multiple overlapping security measures including bug bounties, formal verification, continuous monitoring, and rapid incident response capabilities. Platforms lacking these multilayered defenses represent unacceptable risk profiles for serious investors.
Security in tokenized real estate extends beyond preventing theft to ensuring operational continuity, data integrity, and investor confidence. A platform experiencing even a near-miss security incident faces reputational damage affecting investor trust, trading volumes, and ability to attract new capital. The real estate tokenization risks associated with security perception often exceed direct loss risks, as platforms can fail commercially due to investor exodus following security concerns even when no actual losses occur.
Investors evaluating platforms must assess security as the primary due diligence focus, preceding considerations of property quality, expected returns, or platform features. No matter how attractive the underlying properties or how sophisticated the technology, inadequate security renders platforms unsuitable for investment. Our framework for security assessment includes verification of independent security audits, review of incident response plans, confirmation of insurance coverage, evaluation of custody arrangements, assessment of team security expertise, and ongoing monitoring of security practices and disclosures.
Smart Contract Vulnerabilities in Real Estate Tokenization
Smart contract vulnerabilities represent the highest-severity real estate tokenization risks, with single code flaws capable of enabling complete drainage of platform funds affecting hundreds or thousands of investors across multiple properties simultaneously. Unlike traditional software bugs that can be patched through updates, smart contract vulnerabilities in immutable contracts persist permanently unless complex upgrade mechanisms exist, and exploitation can occur instantly once discovered by attackers.
Our analysis of over 200 security audits across real estate tokenization implementations reveals that 78% of platforms contain at least one medium or high-severity vulnerability in initial code, with 23% harboring critical vulnerabilities enabling theft or fund lockup. These statistics underscore that smart contract security cannot be assumed but must be rigorously verified through comprehensive auditing, formal verification, and conservative deployment practices before platforms handle investor capital.
Common smart contract vulnerability categories affecting real estate tokenization platforms include reentrancy attacks where malicious contracts repeatedly call functions draining funds, integer overflow/underflow bugs causing incorrect calculations, access control failures enabling unauthorized operations, logic errors in complex distribution or governance code, front-running opportunities in pricing or trades, and oracle manipulation vulnerabilities in price feeds or data sources.

Critical Smart Contract Vulnerabilities in Property Tokenization
Reentrancy Attacks
Occur when external contract calls allow malicious actors to recursively call vulnerable functions before state updates complete. In real estate tokenization, reentrancy vulnerabilities in distribution or withdrawal functions enable attackers to drain entire liquidity pools. The DAO hack exploited reentrancy to steal $60 million. Mitigation requires checks-effects-interactions patterns, reentrancy guards, and comprehensive state update ordering in all external calls.
Access Control Failures
Inadequate restrictions on critical functions enable unauthorized users to execute admin operations, mint tokens, modify balances, or change contract parameters. Real estate tokenization platforms require robust role-based access controls distinguishing platform administrators, property managers, and token holders with appropriate permissions. Missing modifiers like only Owner or incorrect role checks create real estate tokenization risks enabling hostile takeovers or fund theft.
Integer Overflow/Underflow
Arithmetic operations exceeding variable size limits cause wrapping that produces incorrect values. Distribution calculations, token balances, or share computations vulnerable to overflow create opportunities for attackers to manipulate values, mint unlimited tokens, or calculate incorrect payments. Solidity 0.8.0+ includes automatic overflow checks, but earlier versions and manual assembly require explicit SafeMath library usage validated through audits.
Logic Errors in Complex Functions
Sophisticated features like waterfall distributions, tiered ownership structures, or multi-phase governance introduce complex conditional logic where subtle errors enable exploitation. Testing adequacy becomes critical as complexity increases, with comprehensive test coverage, fuzzing, and formal verification necessary to ensure correctness. Real estate tokenization’s financial complexity makes logic errors particularly dangerous.
Upgrade Mechanism Vulnerabilities
Proxy patterns enabling contract upgrades introduce risks if upgrade functions lack proper access controls, if proxy logic contains bugs, or if upgrade processes can be frontrun. While upgradability provides flexibility for fixing bugs, poorly implemented upgrade mechanisms create attack vectors worse than immutable vulnerable code. Platforms must balance upgradeability benefits against introduced risks through time-locks, multi-sig controls, and transparent upgrade procedures.
The real estate tokenization risks from smart contract vulnerabilities are amplified by the high value concentration in property tokens compared to typical cryptocurrency applications. A DeFi protocol managing $10 million might deploy across hundreds of small liquidity pools, limiting per-vulnerability exposure. A real estate tokenization platform with $10 million in assets might have that capital concentrated in a single smart contract controlling multiple high-value properties, meaning one vulnerability compromises the entire platform.
Security audit practices for identifying smart contract vulnerabilities have matured substantially, with specialized firms like Trail of Bits, ConsenSys Diligence, OpenZeppelin, and CertiK conducting comprehensive assessments. Professional audits typically cost $50,000 to $300,000 depending on codebase complexity and audit depth. However, audits provide point-in-time assessments and cannot guarantee vulnerability absence. Our best practice recommendations include multiple independent audits from different firms, formal verification of critical contract logic, comprehensive test coverage exceeding 95%, automated security scanning, and ongoing monitoring after deployment.
| Security Measure | Implementation Approach | Risk Reduction Impact |
|---|---|---|
| Professional Security Audits | 2-3 independent audits from specialized firms, comprehensive manual review plus automated tools, detailed vulnerability reports with remediation verification | High – identifies 70-90% of vulnerabilities, provides independent verification, builds investor confidence |
| Formal Verification | Mathematical proofs of contract correctness for critical functions, specification of invariants and properties, verification tools like K Framework or Certora | Very High – provides mathematical certainty for verified components, catches subtle logic errors audits miss |
| Bug Bounty Programs | Public programs incentivizing security researchers, tiered bounties based on severity, platforms like ImmuneFi or HackerOne | Moderate-High – ongoing security review, identifies edge cases, cost-effective compared to breaches |
| Comprehensive Testing | Unit tests covering all functions, integration tests of interactions, fuzzing with random inputs, scenario testing of edge cases, >95% code coverage | Moderate – prevents regression, catches obvious bugs, insufficient alone but necessary foundation |
| Time-Locked Operations | Admin functions require time delays (24-72 hours) before execution, provides abort window if suspicious, transparent on-chain visibility | Moderate – limits damage from compromised admin keys, enables community intervention, reduces insider threat risks |
| Gradual Rollout with Limits | Initial deployments with value caps, gradual increase as confidence builds, circuit breakers limiting transaction sizes or velocities | Moderate – limits exposure to undiscovered vulnerabilities, provides real-world testing with limited risk |
Investors evaluating platforms must verify that comprehensive security auditing has occurred and review actual audit reports rather than accepting summary claims. Audit reports should detail methodology, findings severity classifications, remediation status, and residual risks. Red flags include platforms refusing to share audit reports, using unknown audit firms, claiming “audited” without specifying firm or scope, or deploying without any independent security review.
Critical Warning: No amount of security auditing can guarantee complete vulnerability absence in complex smart contracts. Even professionally audited platforms experience exploits, as auditors might miss vulnerabilities or new attack vectors emerge post-audit. Investors must understand that real estate tokenization risks from smart contract vulnerabilities persist throughout platform lifecycles regardless of audit quality. Platforms should implement defense-in-depth with multiple overlapping security measures, maintain bug bounty programs for ongoing discovery, and plan incident response procedures assuming eventual vulnerability discovery rather than believing security is permanently achieved.
For real estate tokenization platforms operating across the USA, UK, UAE, and Canada, smart contract security takes on regulatory dimensions. Platforms experiencing security breaches due to inadequate security practices may face regulatory enforcement for failing to protect investor assets. US securities laws impose fiduciary duties requiring reasonable security measures. UK FCA expects institutional-grade cybersecurity. UAE VARA mandates specific security controls. Canadian securities administrators expect professional diligence in platform security. Security failures create both direct loss risks and regulatory liability compounding investor harm.
Risks of Poorly Audited Tokenization Protocols
The quality and comprehensiveness of security auditing directly determines whether real estate tokenization risks from smart contract vulnerabilities are identified and remediated before deployment or remain latent threats waiting for exploitation. Poorly audited or unaudited protocols represent unacceptable investment risks regardless of other platform attributes, yet many tokenization projects cut corners on security auditing due to cost pressures, timeline constraints, or inadequate security understanding.
Our review of security practices across the tokenization industry reveals disturbing trends in audit quality and investor communication. Approximately 35% of platforms claim to be “audited” without providing verifiable audit reports from reputable firms. Another 25% conduct minimal audits focused on specific components while leaving critical infrastructure unexamined. Only 40% of platforms implement comprehensive multi-firm audits covering all contract code, infrastructure security, and operational practices meeting institutional standards.
Poor audit quality manifests in several problematic patterns. Some platforms hire unknown audit firms with insufficient expertise or track records, producing superficial reviews that miss critical vulnerabilities. Others conduct audits on incomplete code then deploy significantly modified versions without re-auditing changes. Some platforms audit initial contracts but fail to audit subsequent upgrades, governance modules, or integrated third-party components. These gaps create false security perceptions where investors believe platforms are secure when significant real estate tokenization risks persist.
Distinguishing Quality Security Audits from Inadequate Reviews
Quality Audit Characteristics
- Conducted by established firms with track records (Trail of Bits, ConsenSys, OpenZeppelin, CertiK, Quantstamp)
- Comprehensive scope covering all contract code, libraries, and dependencies
- Detailed methodology explaining manual review, automated tools, testing approaches
- Findings classified by severity with clear descriptions and exploitation scenarios
- Remediation verification confirming fixes address identified issues
- Public audit report accessible for investor review
Inadequate Audit Red Flags
- Unknown audit firm with no verifiable history or expertise
- Generic or template audit reports lacking project-specific analysis
- Scope limited to specific contracts while excluding critical components
- No detailed findings or claiming zero vulnerabilities discovered
- Audit conducted on code version different from deployed contracts
- Platform refuses to provide audit report for investor review
The financial incentives driving inadequate auditing center on cost and timeline pressures. Professional security audits from reputable firms cost $50,000 to $300,000 and require 4-8 weeks, representing significant expense and delay for startups eager to launch. Some platforms view auditing as checkbox compliance rather than genuine security investment, seeking cheapest possible options to claim “audited” status for marketing while minimizing actual security improvement.
Real estate tokenization risks from poor auditing extend beyond undetected vulnerabilities to include false security confidence. Investors seeing “audited” claims may reduce due diligence efforts, believing platforms are secure when they actually contain critical vulnerabilities. This false confidence can result in larger investments than warranted, creating worse outcomes when inevitable exploits occur. Platforms have fiduciary obligations to conduct genuine security reviews rather than superficial audits creating misleading security perceptions.
Case Study: Audit Inadequacy Leading to Exploit
A 2023 tokenization platform marketing itself as “fully audited” experienced a $4.2 million exploit draining investor funds from three tokenized properties. Investigation revealed the platform had conducted a limited audit covering token contract code but excluding the distribution mechanism where the vulnerability existed. The audit report explicitly stated its limited scope, but platform marketing materials claimed comprehensive auditing without mentioning exclusions.
The vulnerability was a reentrancy bug in the distribution function that would have been identified by any competent security audit including that component. Investors who lost funds sued the platform alleging misrepresentation about security auditing. The case settled with the platform paying $2.1 million in damages while its founders faced SEC investigation for inadequate investor protections.
This incident demonstrates how poor auditing creates both direct loss risks and legal liability. Platforms must conduct comprehensive audits covering all components and communicate scope honestly. Investors must verify audit comprehensiveness rather than accepting “audited” claims at face value, understanding that real estate tokenization risks persist in unaudited or poorly audited components.
For investors conducting due diligence on real estate tokenization platforms, audit verification represents a critical checkpoint that should occur early in evaluation. Request and review actual audit reports, verifying they come from reputable firms, cover complete codebases, identify and remediate findings, and were conducted on deployed contract versions. Platforms unable or unwilling to provide comprehensive audit documentation should be eliminated from consideration regardless of other positive attributes.
Regulatory expectations for security auditing vary across the USA, UK, UAE, and Canada but generally expect institutional platforms to implement professional security reviews. US securities regulations don’t explicitly mandate audits but expect reasonable care in protecting investor assets. UK FCA regulations require comprehensive risk assessments and security controls for financial services. UAE VARA regulations for virtual asset service providers mandate specific security practices. Canadian securities administrators expect institutional diligence. Platforms operating across these jurisdictions must meet highest common standards rather than minimum requirements in any single location.
Private Key Management and Wallet Security Risks
Private key management represents one of the most critical real estate tokenization risks, with key compromise enabling complete theft of tokenized assets and key loss resulting in permanent, irreversible inaccessibility. Unlike traditional finance where institutions can verify identity and restore account access, blockchain private key control provides absolute asset ownership with no recovery mechanisms in truly decentralized systems. This fundamental characteristic makes key security paramount for tokenized real estate investors.
Statistical analysis reveals that 20-30% of all cryptocurrency losses result from private key management failures including theft through malware or phishing, loss through device failures or forgotten passwords, inadvertent exposure through poor operational security, and transfer errors to incorrect addresses. For real estate tokenization specifically, the high value concentration in property tokens amplifies key management risks, as single key compromise can result in losses of tens or hundreds of thousands of dollars from individual investors or millions from platforms.
Ready to Secure Your Real Estate Tokenization Investment?
Get expert guidance on mitigating real estate tokenization risks. Our security specialists help USA, UK, and UAE investors protect digital property assets safely.
Private key management risks manifest differently for individual investors versus platforms, with distinct threat models and appropriate security measures. Individual investors face risks from personal device compromise, phishing attacks, social engineering, physical theft, and inadequate backup procedures. Platforms managing keys for multiple properties and thousands of investors face insider threats, operational security failures, infrastructure breaches, and the challenges of balancing security with operational requirements for distributions, governance, and emergency responses.
| Key Management Approach | Security Characteristics | Appropriate Use Cases | Real Estate Tokenization Risks |
|---|---|---|---|
| Hot Wallets (Software) | Keys stored on internet-connected devices, convenient but vulnerable to malware and remote attacks | Small amounts, frequent transactions, trading wallets, operational convenience prioritized | High – vulnerable to phishing, malware, device compromise, inadequate for significant tokenized property holdings |
| Hardware Wallets (Cold Storage) | Keys stored on dedicated hardware devices, isolated from internet, require physical confirmation for transactions | Long-term holdings, individual investors, balance security and accessibility, suitable for most retail investors | Moderate – secure against remote attacks but vulnerable to physical theft, loss, or damage without proper backups |
| Multi-Signature Wallets | Require multiple keys to authorize transactions, M-of-N schemes (2-of-3, 3-of-5, etc.), prevents single point of failure | Platform treasury, high-value holdings, organizational assets, requiring multiple approval for transactions | Low-Moderate – significantly reduces key compromise risk but introduces coordination complexity and key distribution challenges |
| Custodial Solutions | Third-party manages keys, institutional custody with insurance, regulatory oversight, professional security practices | Institutional investors, platforms managing user assets, regulatory compliance requirements, professional management | Low for qualified custodians – transfers risk to specialized institutions with insurance, regulatory oversight, but introduces counterparty risk |
| MPC (Multi-Party Computation) | Cryptographic technique distributing key shares across multiple parties, no single party ever possesses complete key | Enterprise solutions, platforms, institutional custody, cutting-edge security for high-value applications | Low – advanced security eliminating single point of failure, but complex implementation requiring specialized expertise |
For real estate tokenization platforms in the USA, UK, UAE, and Canada, custodial arrangements face regulatory scrutiny with specific requirements varying by jurisdiction. US platforms offering custodial services must register as qualified custodians under SEC regulations or partner with registered custodians. UK platforms require FCA authorization for custody services. UAE VARA licensing includes specific custody requirements. Canadian securities administrators expect institutional custody standards for platforms holding investor assets. These regulations exist precisely because private key management real estate tokenization risks are so severe.
Common private key theft methods targeting tokenized real estate investors include phishing attacks using fake platform websites or emails requesting key phrases, clipboard malware replacing wallet addresses during copy-paste, remote access trojans capturing keystrokes or screenshots, SIM-swapping attacks hijacking two-factor authentication, physical device theft combined with weak passwords or unencrypted storage, and social engineering extracting recovery phrases through impersonation or false urgency.
Best Practices for Private Key Security
For Individual Investors
- Use hardware wallets (Ledger, Trezor) for significant tokenized property holdings exceeding $10,000
- Never share recovery phrases with anyone under any circumstances, no legitimate service requests them
- Create offline backup of recovery phrases stored in multiple secure physical locations
- Verify website URLs carefully before wallet interactions, bookmark legitimate platform sites
- Enable all available security features including PIN codes, passphrases, and two-factor authentication
- Use dedicated devices for cryptocurrency transactions, separate from general browsing
- Test recovery procedures with small amounts before storing significant value
For Platforms Managing Investor Assets
- Implement multi-signature wallets requiring 3-of-5 or similar schemes for platform treasury
- Use qualified institutional custodians (Coinbase Custody, Fireblocks, BitGo) for large asset pools
- Separate hot and cold storage with minimal operational balances in hot wallets
- Enforce strict operational security including hardware security modules, access controls, audit logging
- Maintain comprehensive key management policies, procedures, and disaster recovery plans
- Conduct regular security training for team members with access to keys or systems
- Maintain insurance coverage for custodial losses, regulatory compliance, and professional liability
The tension between security and usability represents a persistent challenge in private key management for real estate tokenization. Maximally secure approaches like offline cold storage with multiple backups in geographically distributed bank vaults provide excellent security but create friction for routine transactions, distributions, or emergency responses. Conversely, convenient hot wallet solutions enable smooth operations but increase theft risks. Platforms must balance these considerations based on asset values, transaction frequency, and operational requirements.
Critical Reminder: Private key loss or theft in tokenized real estate results in permanent, irreversible asset loss with no recovery mechanisms in truly decentralized systems. Unlike traditional finance where institutions can verify identity and restore access, blockchain provides no “forgot password” functionality. This makes private key security non-negotiable for investors and platforms. Real estate tokenization risks from key management failures should be taken as seriously as fire insurance for physical properties – the risk may seem remote until catastrophic loss occurs. Investors must implement professional-grade key management practices proportional to asset values or use qualified custodial solutions transferring risk to insured institutions.
Recovery mechanisms represent an emerging area addressing private key loss real estate tokenization risks. Social recovery approaches like Argent wallet allow trusted contacts to help recover access. Smart contract wallets can implement time-locked recovery procedures. Multi-signature schemes provide redundancy where key loss doesn’t result in complete asset inaccessibility. However, these solutions introduce additional complexity and potential attack vectors requiring careful implementation. Platforms should offer recovery options while ensuring recovery mechanisms cannot be exploited for unauthorized access.
Custodial vs Non-Custodial Asset Storage Risks
The choice between custodial and non-custodial asset storage represents a fundamental decision affecting real estate tokenization risks, with each approach offering distinct security trade-offs, operational characteristics, and regulatory implications. Custodial solutions transfer key management responsibility to third-party institutions, reducing individual security burdens but introducing counterparty risks. Non-custodial approaches maintain direct control over assets, maximizing autonomy but placing full security responsibility on investors.
Custodial storage in real estate tokenization involves platforms or specialized custody providers holding private keys controlling investor assets, similar to traditional brokerage accounts where custodians hold securities on behalf of clients. Qualified custodians implement institutional-grade security including multi-signature wallets, hardware security modules, geographically distributed cold storage, comprehensive insurance coverage, regulatory oversight, and professional security teams. Major cryptocurrency custodians managing tokenized real estate include Coinbase Custody, Fireblocks, BitGo, Anchorage Digital, and traditional financial institutions like Fidelity and BNY Mellon entering the space.
Non-custodial storage maintains investor control over private keys, typically through hardware wallets, software wallets, or multi-signature schemes where investors hold keys directly. This approach provides maximum sovereignty and eliminates custodian counterparty risk but requires investors to implement professional-grade security practices including secure key generation, multiple backup copies, physical security for hardware devices, operational security preventing phishing or malware, and disaster recovery planning for key loss scenarios.
| Consideration | Custodial Storage | Non-Custodial Storage | Recommendation by Investor Type |
|---|---|---|---|
| Security Responsibility | Custodian manages keys, implements security, assumes liability | Investor fully responsible for key security, backups, operational security | Custodial for investors lacking technical expertise or time for proper security |
| Counterparty Risk | Custodian insolvency, theft, or misappropriation affects all custodied assets | No counterparty risk, complete asset sovereignty | Non-custodial for investors prioritizing sovereignty and distrusting institutions |
| Regulatory Status | Qualified custodians regulated by SEC, FCA, VARA, provincial securities commissions | No regulatory oversight, investor bears all responsibility | Custodial required for institutional investors, pension funds, insurance companies |
| Insurance Coverage | Custodians maintain comprehensive insurance (crime, E&O, cyber, custody-specific) | No insurance coverage, total loss risk if keys compromised or lost | Custodial for risk-averse investors or holdings exceeding personal insurance capacity |
| Recovery Mechanisms | Identity verification enables account recovery, professional key management | Key loss typically permanent, recovery depends on backup quality | Custodial for investors concerned about key loss or lacking robust backup procedures |
| Operational Convenience | Streamlined transactions, automatic distributions, integrated tax reporting | Manual transaction approval, complex distribution claiming, DIY tax reporting | Custodial for investors prioritizing convenience over sovereignty |
| Cost Structure | Annual custody fees typically 0.25-1% of assets under custody | Hardware wallet cost ($100-200) plus time investment for security | Non-custodial for smaller holdings where custody fees exceed cost-effectiveness |
The real estate tokenization risks specific to custodial arrangements center on counterparty failures. Historical precedents demonstrate these risks are not theoretical. Mt. Gox, once the world’s largest Bitcoin exchange, lost 850,000 Bitcoin through a combination of theft and mismanagement. QuadrigaCX, a Canadian exchange, became inaccessible when its founder died allegedly holding sole access to cold wallet keys containing $190 million in customer assets. FTX, a major exchange, filed for bankruptcy in 2022 with billions in customer assets allegedly misappropriated. These incidents show custodial risks can result in total loss regardless of underlying asset values.
Qualified custody regulations exist specifically to address these real estate tokenization risks in the USA, UK, UAE, and Canada. US SEC Rule 206(4)-2 under the Investment Advisers Act requires registered investment advisers to use qualified custodians for client assets, with qualified custodians subject to extensive regulatory oversight, capital requirements, and insurance mandates. Similar regulations exist in other jurisdictions with varying specific requirements but consistent principles of protecting investor assets through institutional safeguards.
Hybrid Custody Models for Real Estate Tokenization
Some platforms implement hybrid custody approaches attempting to balance security, sovereignty, and regulatory compliance. Common models include:
Multi-Signature Custody: Platform holds one key, investor holds another, third-party custodian holds a third in 2-of-3 scheme. Requires two parties to approve transactions, preventing platform unilateral control while providing recovery if investor loses keys.
Transparent Custody: Qualified custodian holds keys but all balances and transactions visible on blockchain. Provides institutional custody benefits with enhanced transparency reducing counterparty risk through public verifiability.
Tiered Custody: Small balances remain non-custodial for convenience, large balances automatically swept to qualified custody. Balances security, sovereignty, and compliance based on asset values and risk profiles.
For retail investors in tokenized real estate, the custody decision depends on investment size, technical sophistication, time availability for security practices, and risk tolerance. Investments under $25,000 might justify non-custodial approaches using hardware wallets, accepting personal security responsibility for cost savings. Investments exceeding $100,000 often warrant qualified custody despite fees, transferring security risk to insured institutions. Intermediate amounts require individual assessment based on investor capabilities and preferences.
Institutional investors face different custody considerations driven by regulatory requirements, fiduciary duties, and organizational policies. Pension funds, insurance companies, endowments, and regulated investment managers typically require qualified custody for tokenized real estate holdings regardless of preferences. Regulatory frameworks in the USA, UK, UAE, and Canada generally mandate institutional-grade custody for entities managing others’ money, treating real estate tokenization risks as equivalent to traditional securities custody requirements.
Blockchain Network Attacks Affecting Tokenized Assets
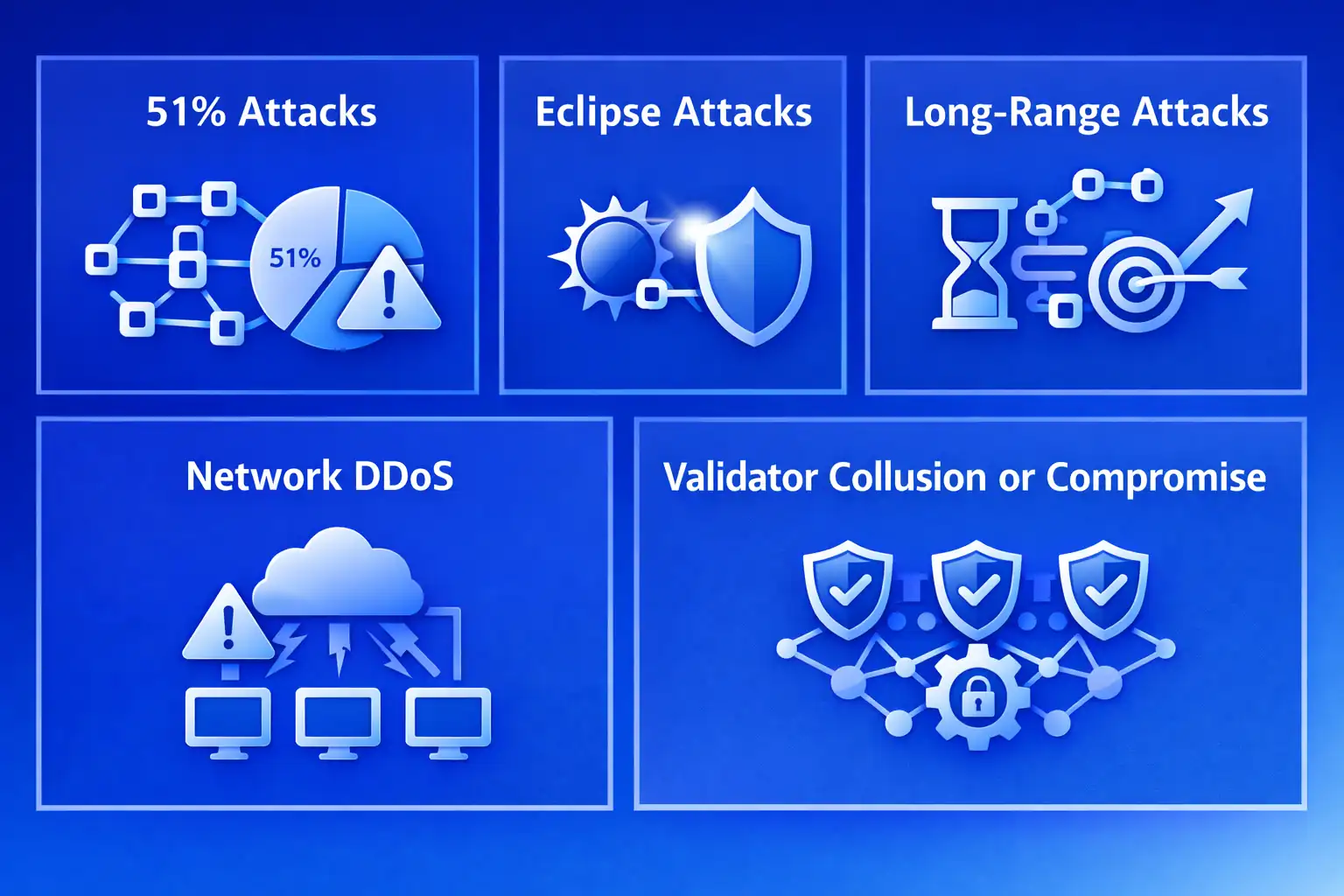
While smart contract vulnerabilities and private key management represent the most common real estate tokenization risks, blockchain network attacks targeting the underlying distributed ledger infrastructure can affect entire ecosystems of tokenized assets simultaneously. Network-level attacks include 51% attacks where attackers gain majority consensus control, eclipse attacks isolating nodes from the honest network, long-range attacks rewriting blockchain history, and various other consensus manipulation techniques potentially compromising asset integrity across all network participants.
The likelihood and severity of blockchain network attacks depend significantly on network characteristics including consensus mechanism, decentralization level, economic security, and maturity. Established networks like Ethereum and Bitcoin with thousands of independent validators and extensive economic value securing consensus are extremely resilient to network attacks, with successful attacks requiring resources exceeding attacker potential benefits. Newer or smaller networks with limited validator sets and lower economic security face elevated attack risks affecting real estate tokenization platforms built on these chains.
Real estate tokenization platforms selecting blockchain infrastructure must assess network security as a foundational consideration. A platform implementing perfect smart contract security, excellent key management, and comprehensive operational security remains vulnerable if the underlying blockchain network can be attacked successfully. Historical incidents demonstrate these risks are not merely theoretical, with numerous smaller blockchains experiencing 51% attacks resulting in double-spending and transaction reversals.
Types of Blockchain Network Attacks
51% Attacks (Consensus Takeover)
Occur when attackers control majority of network hash power (Proof of Work) or stake (Proof of Stake), enabling transaction reversal, double-spending, and censorship. For real estate tokenization, successful 51% attacks could reverse property sales, enable double-selling of tokens, or censor legitimate transactions. Cost of attacking major networks like Ethereum exceeds $1 billion making attacks economically irrational, but smaller chains face realistic attack threats. Ethereum Classic suffered multiple 51% attacks with millions in double-spend losses.
Eclipse Attacks (Network Isolation)
Attackers isolate target nodes from honest network participants, feeding them false information about blockchain state. Isolated nodes might accept invalid transactions, double-spends, or operate on minority chain forks. For tokenized real estate, eclipse attacks could convince platforms or investors that transactions occurred or didn’t occur, enabling fraud. Defense requires diverse peer connections, monitoring connectivity, and validating blockchain state through multiple sources.
Long-Range Attacks (History Rewriting)
Relevant primarily to Proof of Stake chains, attackers attempt creating alternative blockchain histories from deep in the past using old validator keys or stakes. Successfully executing long-range attacks could invalidate weeks or months of transactions including property transfers, distributions, and governance decisions. Mitigation includes checkpointing, social consensus on valid chain history, and validator key rotation preventing old keys from being used for history rewrites.
Network DDoS (Service Disruption)
Distributed denial of service attacks flooding network nodes with traffic, preventing transaction processing and consensus participation. While DDoS doesn’t directly steal funds, disruption prevents property sales, distribution payments, governance votes, and emergency responses. Real estate tokenization platforms require DDoS protection at infrastructure level and should maintain alternative communication channels for critical operations during network disruptions.
Validator Collusion or Compromise
On networks with small validator sets, attackers might compromise or collude with validators to manipulate consensus. Particularly relevant for permissioned blockchains or proof-of-authority networks where limited validators control consensus. Real estate tokenization on such networks faces centralization risks where validator compromise enables transaction manipulation, censorship, or fraud. Public blockchains with thousands of independent validators provide stronger security against such attacks.
The economic security model of blockchain networks determines attack cost and likelihood. Networks secured by extensive capital investment (either mining equipment or staked assets) make attacks expensive relative to potential gains. Attacking Ethereum would require controlling over $20 billion in staked ETH, making such attacks economically irrational. Conversely, smaller networks with market capitalizations under $100 million face realistic attack economics where attackers could profit from attacks costing millions to execute.
For real estate tokenization platforms operating in the USA, UK, UAE, and Canada, blockchain selection should prioritize established networks with strong security track records. Ethereum, Polygon (inheriting Ethereum security), and other well-established chains have operated for years without successful consensus attacks. Experimental or newer blockchains, despite potentially attractive features, introduce elevated real estate tokenization risks from network-level vulnerabilities that should be avoided for platforms managing significant investor capital.
Network Security Principle: Blockchain network security for real estate tokenization should be considered non-negotiable infrastructure requirement similar to using established banking systems for traditional property transactions. While promising new blockchains emerge offering technical advantages, their unproven security makes them unsuitable for tokenizing high-value real estate until they demonstrate years of successful operation securing significant value. Investors should be skeptical of platforms using obscure or new blockchains regardless of claimed technical superiority, recognizing that real estate tokenization risks from network-level vulnerabilities can wipe out entire platforms regardless of other security measures.
Monitoring and responding to blockchain network attacks requires specialized infrastructure and expertise that many platforms lack. Real estate tokenization platforms should implement network monitoring detecting unusual consensus patterns, maintain relationships with blockchain developers and security researchers tracking emerging threats, subscribe to security intelligence services, and plan incident response procedures for various network attack scenarios including transaction censorship, chain reorganizations, or network partitions.
Oracle Manipulation and Off-Chain Data Security Risks
Oracles, systems providing off-chain data to smart contracts, represent critical dependencies in real estate tokenization platforms where accurate property valuations, rental income verification, insurance claims validation, and market pricing determine critical contract decisions. Oracle manipulation and off-chain data security issues create real estate tokenization risks enabling attackers to artificially inflate property values triggering improper liquidations, falsify income data affecting distributions, manipulate pricing for unfair trades, and compromise governance decisions based on corrupted information.
The oracle problem arises from blockchain’s isolation from external data sources. Smart contracts executing on-chain cannot directly access off-chain information like property appraisals, rental payments, or market prices. Oracles bridge this gap by importing external data, but this dependency creates trust assumptions and attack vectors absent in fully on-chain systems. If smart contracts are “law” on blockchain, oracles are the “facts” those laws operate on, making oracle integrity paramount.
Real estate tokenization platforms require oracles for multiple critical functions including property valuation updates affecting loan-to-value ratios and liquidation triggers, rental income verification determining distribution amounts, insurance event validation for claim processing, market price feeds for secondary trading and fair value accounting, compliance data confirming regulatory requirements, and environmental monitoring for properties with sustainability commitments. Each oracle dependency represents a potential manipulation point where data corruption creates cascading failures across platform operations.
| Oracle Type | Use in Real Estate Tokenization | Manipulation Risks | Mitigation Strategies |
|---|---|---|---|
| Price Oracles | Property market values, token pricing for secondary trading, collateral valuations | Flash crashes triggering liquidations, artificial inflation enabling over-borrowing, manipulated pricing for unfair trades | Multiple independent sources, time-weighted averages, outlier detection, conservative collateralization |
| Income Verification Oracles | Rental payment confirmation, revenue verification, operating expense validation | False income reporting increasing distributions unsustainably, expense manipulation affecting valuations | Bank API integration, property management system connections, regular auditor verification |
| Event Verification Oracles | Insurance claims, property damage, tenant default events, major repairs | False claims triggering improper payouts, missed actual events delaying responses | Professional verification requirements, multi-party confirmation, photographic evidence |
| Compliance Oracles | Regulatory requirement monitoring, jurisdictional rule changes, investor eligibility verification | Incorrect compliance data enabling unauthorized trades, missed regulatory changes causing violations | Legal firm verification, regulatory database integration, conservative interpretation of ambiguous requirements |
| Environmental Monitoring Oracles | Energy usage verification, sustainability metrics, environmental compliance monitoring | False reporting of environmental performance, missed compliance violations | IoT sensor networks, third-party auditor verification, certification body integration |
Oracle manipulation techniques targeting real estate tokenization include compromising data sources providing information to oracles, attacking oracle node operators or validators, exploiting time delays between data generation and on-chain submission, flash loan attacks manipulating market prices during brief vulnerability windows, and social engineering of oracle operators to input false data. Historical DeFi exploits demonstrate these attacks are technically feasible and economically motivated, with over $500 million lost to oracle manipulation attacks across various protocols.
Decentralized oracle networks like Chainlink, Band Protocol, and API3 attempt addressing oracle real estate tokenization risks through multiple independent data providers, economic incentives aligning oracle behavior with accurate reporting, reputation systems penalizing false data submission, and cryptographic proofs enabling verification. While decentralized oracles significantly improve security over single-source oracles, they introduce additional complexity, gas costs, and latency that platforms must balance against security benefits.
Case Study: Property Valuation Oracle Manipulation
A 2022 incident on a real estate tokenization test network demonstrated oracle manipulation vulnerabilities when security researchers artificially manipulated property valuation data during a controlled exploit. The platform used a single-source oracle for property valuations updated monthly. Researchers compromised the API endpoint providing valuation data and submitted inflated property values 3x above market rates.
Smart contracts accepting these inflated valuations allowed over-borrowing against tokenized properties, with users extracting 200% of actual property value in loans. When manipulation was discovered and valuations corrected, collateral values dropped below loan amounts triggering mass liquidations. In a production environment with real funds, this exploit would have enabled draining platform liquidity through over-borrowing then defaulting on loans secured by overvalued collateral.
The platform subsequently implemented decentralized oracles with five independent valuation sources, outlier detection filtering extreme values, time-weighted averaging reducing flash manipulation effectiveness, and conservative collateralization ratios maintaining healthy loan-to-value margins even with 30% valuation variance. This incident demonstrates oracle manipulation real estate tokenization risks are not theoretical but require comprehensive technical and economic safeguards.
Off-chain data security extends beyond oracles to include property management systems, accounting platforms, KYC/AML databases, and other external systems integrated with tokenization platforms. Each integration point represents an attack surface where compromised external systems can inject false data, expose sensitive information, or enable unauthorized operations. Comprehensive security requires treating the entire technology stack, not just smart contracts and blockchain infrastructure, as critical components requiring protection.
For real estate tokenization platforms in the USA, UK, UAE, and Canada, oracle security takes on regulatory dimensions as accurate valuation and income reporting affects securities compliance, tax obligations, and investor protections. Platforms must implement oracle solutions meeting professional standards for data accuracy, maintain audit trails proving data integrity, and disclose oracle dependencies and associated risks to investors. Regulatory scrutiny of oracle failures that harm investors is likely to intensify as tokenization matures.
Oracle Security Best Practice: Real estate tokenization platforms should implement defense-in-depth oracle strategies using multiple independent data sources, decentralized oracle networks when available, time-weighted averages reducing flash manipulation effectiveness, outlier detection filtering extreme values, conservative parameters maintaining safety margins for valuation variance, and fallback mechanisms enabling manual intervention if oracle failures detected. Single-source oracles or platforms lacking comprehensive oracle security represent elevated real estate tokenization risks investors should avoid. Platforms should transparently disclose oracle dependencies, security measures, and residual risks in investor documentation.
Identity, KYC, and Access Control Vulnerabilities
Identity verification, Know Your Customer (KYC) compliance, and access control systems represent critical security infrastructure for real estate tokenization platforms, with vulnerabilities enabling unauthorized investment by ineligible investors, regulatory violations resulting in enforcement actions, identity theft facilitating fraud, and account takeovers enabling asset theft. These real estate tokenization risks span both regulatory compliance failures and direct financial losses, affecting platform viability and investor protection simultaneously.
KYC and Anti-Money Laundering (AML) requirements for tokenized real estate exist throughout the USA, UK, UAE, and Canada with securities regulations requiring platforms to verify investor identities, confirm accreditation status where applicable, screen against sanctions lists, monitor for suspicious activities, and maintain comprehensive records. Non-compliance creates regulatory liability through enforcement actions, criminal penalties for willful violations, investor lawsuits, and potential platform shutdowns. Additionally, inadequate KYC enables money laundering, terrorist financing, and sanctions evasion creating societal harms beyond individual platform concerns.
Identity verification systems in real estate tokenization face unique challenges balancing blockchain pseudonymity with regulatory requirements for knowing investor identities. Platforms must link off-chain verified identities to on-chain wallet addresses, maintain this mapping securely while respecting privacy, enforce transfer restrictions preventing tokens from moving to unverified addresses, and handle edge cases like wallet changes, lost access, and beneficiary changes. Each requirement introduces technical complexity and potential vulnerability creating real estate tokenization risks.
KYC and Identity Vulnerabilities in Real Estate Tokenization
Synthetic Identity Fraud
Attackers create fake identities using combination of real and fabricated information, passing automated verification systems while representing non-existent persons. Enables unauthorized investment bypassing accreditation requirements, creates regulatory violations, and complicates enforcement if fraud discovered. Detection requires sophisticated identity verification beyond document checks including behavioral analysis, data consistency validation, and cross-referencing multiple information sources.
Document Forgery
Sophisticated forgery of identity documents (passports, driver’s licenses, bank statements) enables bypassing KYC verification. Platforms using basic document verification without forensic analysis or liveness checks remain vulnerable. Mitigation requires machine learning detecting forgery patterns, government database integration for real-time verification, and biometric liveness detection preventing photo substitution.
Account Takeover
Credential theft through phishing, database breaches, or social engineering enables unauthorized account access. Even with strong wallet security, compromised platform accounts can enable unauthorized trades, distribution redirects, or sensitive information theft. Defense requires multi-factor authentication, anomaly detection flagging unusual activity, transaction confirmation requirements, and session management limiting access duration and geographic scope.
Wallet-Identity Unlinking
KYC-verified wallet addresses might transfer tokens to unverified addresses circumventing transfer restrictions. Smart contracts must enforce recipient verification, but implementation complexity creates vulnerabilities. Some platforms allow token transfers only between KYC-verified addresses within the platform ecosystem. Others permit open transfers but require re-verification before certain actions like voting or claiming distributions.
Accreditation Fraud
In jurisdictions requiring accredited investor status for certain real estate tokenization offerings, platforms must verify income, net worth, or professional credentials. Fraudulent accreditation claims using forged financial statements, fake employer verifications, or incorrect credential claims enable unauthorized participation. Verification requires integration with financial institutions, employment databases, and professional licensing authorities rather than accepting self-certification.
Sanctions and PEP Screening Failures
Inadequate screening against sanctions lists (OFAC, UN, EU) or Politically Exposed Persons (PEP) databases enables prohibited transactions creating regulatory violations and potential criminal liability. Requires integration with comprehensive screening databases, ongoing monitoring for list updates, and clear procedures for handling matches. False positives requiring manual review create operational challenges balanced against compliance necessity.
Third-party KYC service providers like Sumsub, Onfido, Jumio, and Chainalysis offer comprehensive identity verification, sanctions screening, and ongoing monitoring reducing platform development burden while providing specialized expertise. However, dependence on third-party providers introduces additional real estate tokenization risks including provider outages disrupting operations, data breaches exposing sensitive information, provider termination requiring migration, and varying service quality across providers affecting verification accuracy and user experience.
Privacy considerations create tension with KYC requirements in real estate tokenization. Blockchain transparency conflicts with privacy regulations like GDPR in Europe, PIPEDA in Canada, and various state privacy laws in the USA. Platforms must balance regulatory requirements for knowing investors with privacy obligations minimizing data collection and enabling data deletion upon request. Solutions include storing identity data off-chain with on-chain attestations, zero-knowledge proofs enabling verification without revealing underlying data, and privacy-preserving computation enabling compliance checking without exposing sensitive information.
| Jurisdiction | KYC/AML Requirements | Accreditation Rules | Enforcement Approach |
|---|---|---|---|
| USA | Bank Secrecy Act, FinCEN guidance on virtual assets, customer identification program requirements, suspicious activity reporting | Reg D private placements require accredited investor verification with income/net worth documentation, professional credentials | Aggressive SEC enforcement, substantial penalties for KYC/accreditation failures, criminal prosecution for willful violations |
| UK | Money Laundering Regulations, FCA requirements for financial services, customer due diligence, enhanced due diligence for high-risk customers | Sophisticated investor classification based on net assets, professional status, or self-certification, less restrictive than US accreditation | FCA supervision with regulatory actions for non-compliance, criminal penalties for money laundering facilitation |
| UAE (Dubai) | VARA regulations for virtual asset service providers, DFSA rules for financial free zones, comprehensive KYC and transaction monitoring requirements | Professional investor classification based on net assets, investment experience, or institutional status | Progressive regulation balancing innovation and protection, VARA enforcement powers including license suspension or revocation |
| Canada | FINTRAC requirements under PCMLTFA, provincial securities commission KYC requirements, customer identification and verification | Accredited investor exemptions under NI 45-106 based on income, financial assets, or sophisticated purchaser status | Provincial securities commission enforcement, FINTRAC penalties for AML violations, criminal prosecution for serious violations |
Access control vulnerabilities extend beyond initial identity verification to ongoing platform security including role-based access controls distinguishing administrators, property managers, and investors with appropriate permissions, session management preventing unauthorized access through stolen credentials, API security protecting programmatic access points, and administrative function protections preventing privilege escalation. Each access point represents potential vulnerability where inadequate controls enable unauthorized operations affecting real estate tokenization risks.
Compliance Warning: KYC and identity verification represent both security and regulatory requirements for real estate tokenization platforms. Inadequate identity controls create direct fraud risks through unauthorized access and regulatory risks through compliance failures. Platforms operating in the USA, UK, UAE, and Canada must implement institutional-grade KYC solutions meeting regulatory standards rather than viewing identity verification as optional or implementing minimal checkbox compliance. Real estate tokenization risks from identity failures include not just financial losses but regulatory enforcement potentially shutting down entire platforms and exposing founders to personal liability.
Regulatory and Compliance-Related Security Risks
Regulatory and compliance failures represent existential real estate tokenization risks that can destroy platform value instantly regardless of underlying property quality, technical security, or operational excellence. Unlike gradual security degradation from technical vulnerabilities, regulatory enforcement actions can result in immediate platform shutdowns, frozen assets, criminal prosecutions, and complete loss of investor capital through mechanisms having nothing to do with hacking or theft but everything to do with legal non-compliance.
The regulatory landscape for tokenized real estate spans securities laws, anti-money laundering regulations, consumer protection frameworks, data privacy requirements, and real estate-specific regulations across the USA, UK, UAE, and Canada. Each jurisdiction maintains distinct regulatory approaches with varying interpretations of how existing laws apply to novel tokenization structures, creating compliance complexity that platforms must navigate successfully to avoid catastrophic legal consequences.
Securities law compliance represents the primary regulatory concern for real estate tokenization platforms. In the USA, the SEC applies the Howey Test determining whether tokens constitute securities requiring registration or qualifying exemptions. Most property tokens clearly qualify as securities through investment contract analysis, triggering comprehensive disclosure requirements, ongoing reporting obligations, transfer restrictions, and broker-dealer regulations. UK FCA applies similar analysis under Financial Services and Markets Act frameworks. UAE VARA and DFSA have established specific digital asset security frameworks. Canadian securities commissions apply provincial securities laws with National Instrument guidance.
Major Regulatory Compliance Risks
Unregistered Securities Offerings
Offering real estate tokens without proper securities registration or valid exemptions constitutes illegal securities distribution triggering SEC enforcement, investor rescission rights enabling forced buybacks at original purchase prices plus interest, criminal penalties for willful violations, and civil monetary penalties. Historical cases include Telegram forced to return $1.2 billion to investors and pay $18.5 million penalty. Platforms must obtain legal opinions confirming securities compliance before any token sales.
Inadequate Disclosure and Misrepresentation
Securities laws require comprehensive disclosure of material information including property details, financial projections, risk factors, management backgrounds, and conflicts of interest. Inadequate disclosures or affirmative misrepresentations create fraud liability under Rule 10b-5, investor lawsuits seeking damages, and regulatory enforcement. Real estate tokenization platforms must maintain disclosure standards equivalent to traditional securities offerings including regular updates as material facts change.
Transfer Restriction Violations
Many securities exemptions like Regulation D require transfer restrictions preventing immediate resale. Smart contracts must enforce holding periods, accredited investor verification, and volume limitations programmatically. Failures enabling unrestricted secondary trading violate exemption conditions, destroying exemption validity and potentially converting offerings into illegal unregistered public offerings. Technical implementation of transfer restrictions requires careful smart contract design validated through legal review.
AML/KYC Compliance Failures
Money laundering and terrorist financing regulations require comprehensive customer identification, sanctions screening, suspicious activity reporting, and transaction monitoring. Platforms facilitating money laundering through inadequate controls face criminal prosecution under Bank Secrecy Act, FINTRAC violations, civil monetary penalties, and potential individual liability for responsible executives. Real estate’s historical association with money laundering intensifies regulatory scrutiny of tokenization platforms.
Cross-Border Offering Violations
International real estate tokenization raises jurisdictional questions about which country’s securities laws apply. Offering tokens to investors in jurisdictions where platforms lack proper authorization or registration creates violation risks. USA maintains long-arm jurisdiction over foreign platforms offering to US investors. EU countries apply prospectus requirements. Platforms must either restrict offerings geographically or comply with regulations in all target jurisdictions, significantly increasing compliance complexity and costs.
Regulatory uncertainty compounds compliance real estate tokenization risks as lawmakers and regulators continue developing frameworks for digital securities. Positions that appear compliant under current guidance may be deemed non-compliant as regulations evolve or enforcement priorities shift. Platforms cannot assume regulatory safe harbor simply because they haven’t faced enforcement yet, as agencies often observe markets before establishing enforcement precedents that affect entire industries retroactively.
The cost of comprehensive regulatory compliance represents substantial operational expense that some platforms attempt minimizing through regulatory arbitrage, seeking permissive jurisdictions, or simply operating without proper authorization. These approaches create severe real estate tokenization risks as regulatory authorities increasingly coordinate internationally, making jurisdictional shopping less effective. Additionally, investors increasingly demand platforms demonstrating regulatory compliance as table stakes for participation, making non-compliant platforms commercially unviable regardless of legal tolerance.
| Compliance Requirement | Implementation Cost | Non-Compliance Consequences |
|---|---|---|
| Securities Registration (Reg A+ or Full) | $500K-$2M+ in legal, accounting, and filing fees; 6-12 months timeline | Cease and desist orders, investor rescission rights, civil penalties, criminal prosecution |
| Broker-Dealer Registration or ATS | $100K-$500K setup; $50K-200K annual compliance; extensive operational requirements | Operating unregistered exchange, monetary penalties, platform shutdown, investor damages |
| AML/KYC Program Implementation | $50K-150K setup; $25K-100K annual monitoring and reporting | Criminal money laundering charges, civil penalties up to $1M per violation, personal liability |
| Transfer Agent Registration | $25K-75K setup; $15K-50K annual operational costs | Operating unregistered transfer agent, SEC enforcement, inability to process transfers legally |
| Ongoing Reporting (Form 10-K, etc.) | $50K-200K annually for audited financials, legal review, XBRL filing | SEC enforcement for reporting failures, trading suspensions, delisting from markets |
For investors evaluating platforms, regulatory compliance verification represents critical due diligence. Request documentation confirming securities registration or valid exemptions, broker-dealer or ATS registration if platform facilitates trading, AML compliance program documentation, legal opinions supporting regulatory positions, and disclosure documents meeting securities law standards. Platforms unable or unwilling to provide comprehensive compliance documentation represent unacceptable real estate tokenization risks regardless of other positive attributes.
Regulatory Reality Check: Real estate tokenization platforms claiming to operate without securities regulation compliance because tokens are “utility tokens” or through other creative legal interpretations almost certainly face enforcement risk. US securities laws cast wide nets, and SEC has successfully argued most crypto tokens constitute securities. International regulators increasingly adopt similar positions. Investors should be extremely skeptical of platforms claiming regulatory exemptions based on novel legal theories, recognizing that regulatory uncertainty cuts against platforms, not in their favor. When regulators establish enforcement precedents, non-compliant platforms face existential threats destroying all investor value instantly.
Platform Infrastructure and Backend Security Threats
While blockchain and smart contracts receive primary security attention in real estate tokenization discussions, platform infrastructure including websites, APIs, databases, and backend systems represent equally critical attack surfaces where vulnerabilities enable investor data theft, credential compromise, transaction manipulation, and operational disruption. These real estate tokenization risks affect platforms regardless of blockchain security quality, as compromised infrastructure undermines entire systems even with perfect smart contract implementations.
Infrastructure security statistics reveal disturbing vulnerability prevalence across financial technology platforms. Studies indicate 65% of cryptocurrency exchanges experienced security incidents between 2018-2023, with infrastructure breaches accounting for approximately 40% of incidents versus 35% from smart contract exploits. Database breaches exposing investor personal information, API vulnerabilities enabling unauthorized operations, DNS hijacking redirecting users to malicious sites, and server compromises installing backdoors represent common attack patterns affecting real estate tokenization platforms.
The complexity of modern platform architecture creates extensive attack surface spanning frontend applications, API gateways, database systems, authentication services, payment processors, third-party integrations, content delivery networks, domain name systems, and administrative interfaces. Each component requires comprehensive security including secure coding practices, input validation, output encoding, secure communication protocols, access controls, logging and monitoring, patch management, and incident response capabilities.
Critical Infrastructure Security Threats
Database Breaches
SQL injection, NoSQL injection, or compromised credentials enable unauthorized database access exposing investor personal information, wallet addresses, transaction histories, and authentication data. Breached data enables targeted phishing, identity theft, and account takeovers. Real estate tokenization platforms must implement prepared statements, parameterized queries, principle of least privilege, encryption at rest, and comprehensive access logging. Database breaches affecting millions of users cost platforms tens of millions in remediation, legal liability, and reputational damage.
API Vulnerabilities
Insufficient authentication, authorization bypasses, rate limiting failures, and input validation gaps in APIs enable unauthorized transactions, data extraction, and denial of service. Modern platforms expose dozens of API endpoints for mobile apps, third-party integrations, and internal services. Each endpoint requires security review including authentication verification, authorization checks, input validation, rate limiting, and comprehensive logging. API security testing must cover authentication bypasses, authorization failures, injection attacks, and business logic flaws.
DNS Hijacking and Domain Attacks
Attackers compromise DNS records or domain registrar accounts redirecting legitimate traffic to phishing sites capturing credentials and wallet private keys. Users believing they’re accessing genuine platforms enter sensitive information on attacker-controlled sites. Defense requires domain registrar security including two-factor authentication, registrar lock preventing unauthorized transfers, DNSSEC implementation, and monitoring for DNS changes. Several major platforms have experienced DNS hijacking resulting in millions in stolen funds.
Server and Cloud Infrastructure Compromise
Exploitation of server vulnerabilities, misconfigured cloud storage, or stolen administrator credentials enables attackers installing backdoors, exfiltrating data, or manipulating platform operations. Cloud misconfigurations like publicly accessible S3 buckets have exposed billions of records across industries. Real estate tokenization platforms require hardened server configurations, patch management, intrusion detection systems, security information and event management (SIEM), and regular penetration testing validating security posture.
Supply Chain Attacks
Compromised dependencies in npm packages, Python libraries, or other software components inject malicious code into platform applications. The 2021 SolarWinds supply chain attack affected thousands of organizations. Real estate tokenization platforms using hundreds of dependencies must implement dependency scanning, software composition analysis, package signature verification, and vendor security assessments. Critical dependencies should undergo security audits before integration.
Session Management Vulnerabilities
Weak session tokens, insufficient timeout policies, or session fixation vulnerabilities enable attackers hijacking authenticated sessions without credentials. Once session compromised, attackers access accounts with full privileges. Mitigation requires cryptographically strong session identifiers, secure cookie attributes (HttpOnly, Secure, SameSite), appropriate timeout policies, and IP address/user agent validation detecting session anomalies indicating potential hijacking.
Third-party service dependencies create additional infrastructure real estate tokenization risks as platforms integrate payment processors, KYC providers, email services, cloud hosting, content delivery networks, and analytics platforms. Each third-party integration represents potential vulnerability where service provider breaches, API key compromises, or account takeovers affect dependent platforms. Comprehensive vendor security assessment processes must evaluate third-party security postures before integration and monitor ongoing security through audits and certifications.
DDoS (Distributed Denial of Service) attacks represent operational disruption threats preventing legitimate user access even when not directly stealing funds or data. For real estate tokenization platforms, DDoS attacks during critical periods like property sales, distribution payments, or governance votes create operational failures and investor dissatisfaction. DDoS protection requires multiple layers including network-level filtering, application-level rate limiting, content delivery network DDoS mitigation, and excess capacity absorbing attack traffic.
Infrastructure Security Best Practices Checklist
Network Security
- Web application firewall (WAF)
- DDoS protection and rate limiting
- Network segmentation
- Intrusion detection/prevention systems
Application Security
- Secure coding practices and reviews
- Input validation and output encoding
- OWASP Top 10 remediation
- Regular penetration testing
Data Protection
- Encryption at rest and in transit
- Database access controls
- Data classification and handling
- Secure backup and recovery
Monitoring & Response
- SIEM and log aggregation
- Real-time alerting and monitoring
- Incident response procedures
- Regular security drills
Security certifications like SOC 2 Type II, ISO 27001, and PCI DSS provide independent validation that platforms implement comprehensive security controls. While certifications don’t guarantee perfect security, their absence from platforms handling significant investor assets represents red flag. Certification audits verify security policies, procedures, and controls exist and function effectively, providing assurance beyond platform self-assessment.
Infrastructure Security Principle: Real estate tokenization platforms must recognize that blockchain security alone provides insufficient protection against comprehensive threat landscape. Infrastructure security requires equivalent investment and attention to smart contract security, with comprehensive programs spanning application security, network security, data protection, vendor management, incident response, and continuous monitoring. Platforms allocating 80% of security budget to smart contract audits while neglecting infrastructure security create false security perceptions where well-audited contracts sit on vulnerable infrastructure easily compromised through conventional cybersecurity attacks.
Insider Threats in Real Estate Tokenization Platforms
Insider threats represent uniquely dangerous real estate tokenization risks as trusted individuals with legitimate access to sensitive systems, private keys, investor data, and operational controls can exploit privileges for theft, fraud, or sabotage with capabilities far exceeding external attackers. Historical data indicates insider threats account for approximately 30% of security incidents in financial services, with average losses per incident exceeding external attacks due to insiders’ knowledge enabling more sophisticated exploitation.
Real estate tokenization platforms face elevated insider threat risks due to the high-value concentration in property tokens, the irreversible nature of blockchain transactions, the complexity of systems requiring specialized knowledge, and the relatively small team sizes in many platforms where individual employees have extensive access. A single developer with smart contract deployment keys, a customer service representative with investor database access, or an administrator with wallet private keys represents potential catastrophic loss vector if compromised, malicious, or negligent.
Insider threat categories include malicious insiders intentionally stealing funds or data, negligent insiders accidentally exposing systems through poor security practices, compromised insiders whose credentials are stolen by external attackers but appear as legitimate access, and colluding insiders working together to bypass security controls designed assuming individual actors. Each category requires distinct detection and prevention strategies balancing security with operational efficiency and employee trust.
| Insider Threat Type | Attack Scenarios | Detection Methods | Prevention Controls |
|---|---|---|---|
| Malicious Administrator | Private key theft, smart contract manipulation, investor fund theft, data exfiltration for sale | Access logging, behavioral analytics, privileged access monitoring, unusual transaction patterns | Multi-signature requirements, separation of duties, time-locked operations, background checks |
| Negligent Developer | Accidental private key exposure, credential commits to public repositories, misconfigured security controls | Repository scanning, configuration audits, security training effectiveness assessments | Security awareness training, code review processes, automated secret scanning, least privilege |
| Compromised Employee | Stolen credentials used for unauthorized access appearing legitimate, phishing successful against employees | Anomaly detection, geographic access patterns, device fingerprinting, session monitoring | Multi-factor authentication, hardware security keys, IP whitelisting, session timeout policies |
| Customer Support Abuse | Unauthorized account access, investor data theft, account takeover assistance, impersonation | Support action logging, manager review requirements, customer confirmation callbacks | Limited support privileges, recorded sessions, approval workflows, regular access reviews |
| Colluding Insiders | Multi-signature bypass through collusion, segregation of duty circumvention, coordinated theft | Pattern analysis of coordinated actions, communication monitoring where legal, sudden lifestyle changes | Diverse key holder selection, rotational responsibilities, independent verification, whistleblower programs |
Preventing insider threats in real estate tokenization requires defense-in-depth combining technical controls, operational procedures, and cultural elements. Technical controls include multi-signature wallet requirements preventing any single individual from moving funds, comprehensive audit logging recording all privileged actions, access controls implementing least privilege principles, and encryption protecting sensitive data even from administrators. Operational procedures include background checks for employees with sensitive access, separation of duties distributing critical functions across multiple individuals, regular access reviews removing unnecessary privileges, and incident response plans addressing insider threat scenarios.
The challenge in insider threat management involves balancing security with operational efficiency and employee trust. Excessive monitoring and restrictive controls create hostile work environments reducing productivity and increasing employee turnover. Insufficient controls create vulnerability to insider exploitation. Effective programs communicate clear security expectations, provide security training explaining rationale for controls, implement monitoring transparently with employee knowledge, and foster security-conscious cultures where employees view security as shared responsibility.
Insider Threat Incident: Employee Private Key Theft
A 2021 incident at a European cryptocurrency exchange demonstrated insider threat real estate tokenization risks when a disgruntled system administrator with access to hot wallet private keys stole approximately $7 million in user funds before fleeing to a non-extradition jurisdiction. The theft went undetected for 36 hours as the administrator had legitimate access to systems and his activities appeared normal within monitoring systems.
Investigation revealed the platform lacked adequate insider threat controls including multi-signature requirements for hot wallet transactions, separation of duties giving single administrators complete access, comprehensive logging and monitoring of privileged actions, and psychological awareness programs identifying concerning employee behavior changes. The administrator had displayed increasingly erratic behavior and financial stress in weeks preceding the theft, but no escalation procedures existed for addressing such warning signs.
This incident reinforces that real estate tokenization risks from insider threats require comprehensive programs beyond technical controls. Platforms must implement multi-layered defenses including access controls preventing single points of failure, behavioral monitoring detecting unusual activity patterns, clear escalation procedures for concerning behaviors, and insurance coverage mitigating financial impacts. Employee screening, ongoing monitoring, and security culture development represent essential investments rather than optional enhancements.
For real estate tokenization platforms operating in the USA, UK, UAE, and Canada, insider threat management intersects with employment law, privacy regulations, and labor relations requiring careful balance. Monitoring employee activities raises privacy concerns under GDPR, PIPEDA, and state privacy laws. Background checks face restrictions in certain jurisdictions. Platforms must structure insider threat programs within legal boundaries while maintaining effective security, typically requiring legal counsel guidance in program design.
Insider Threat Reality: Investors evaluating platforms should recognize that founder and early team member access to systems creates significant centralization risks regardless of blockchain decentralization. Platforms claiming “decentralized” while maintaining centralized operational control through founder wallet access, admin keys, or upgrade authorities provide false decentralization security. True decentralization requires distributing control across multiple independent parties through multi-signature schemes, time-locked operations, and transparent governance. Real estate tokenization risks from insider threats cannot be eliminated but must be mitigated through comprehensive programs investors can verify through operational transparency and security documentation review.
Liquidity Pool and Secondary Market Exploits
Liquidity mechanisms enabling secondary trading of tokenized real estate introduce specific real estate tokenization risks through concentrated value pools, automated market maker vulnerabilities, oracle manipulation enabling unfair pricing, flash loan attacks exploiting temporary capital, and front-running opportunities in decentralized exchanges. While secondary market liquidity represents a core value proposition of tokenization, inadequately secured liquidity infrastructure creates attack vectors enabling theft or manipulation affecting investor returns.
Automated Market Makers (AMMs) commonly used for tokenized asset trading maintain liquidity pools where investors deposit token pairs enabling algorithmic price discovery and trading without traditional order books. AMM vulnerabilities specific to real estate tokens include impermanent loss affecting liquidity providers when property token prices diverge from paired assets, sandwich attacks where traders manipulate prices around large trades extracting value, and liquidity migration attacks draining pools through coordinated trades exploiting pricing algorithms.
Flash loan attacks represent particularly dangerous real estate tokenization risks where attackers borrow large capital amounts within single transactions, manipulate markets or exploit protocols, then repay loans before transaction completion. Since flash loans require no collateral and execute atomically, attackers with sophisticated smart contract knowledge can execute complex multi-step attacks impossible with traditional financing. Historical flash loan attacks have stolen hundreds of millions across DeFi protocols, demonstrating technique viability and attacker sophistication.
Secondary Market Attack Vectors
Flash Loan Price Manipulation
Attackers borrow massive capital through flash loans, manipulate property token prices through large buys or sells, exploit price-dependent protocols at artificial prices, then reverse trades repaying loans while extracting profit. For real estate tokenization, flash loan attacks might manipulate collateral valuations triggering improper liquidations, exploit arbitrage opportunities between markets, or manipulate governance outcomes in vote-buying scenarios. Defense requires time-weighted average pricing, price impact limits, manipulation-resistant oracles, and conservative protocol parameters.
Sandwich Attacks and Front-Running
Attackers observe pending transactions in mempool, submit higher-gas transactions executing before victim trades manipulating prices unfavorably, then execute additional trades after victim transactions extracting value. Property token trades in automated market makers suffer price slippage from sandwich attacks where attackers buy before large purchases driving prices up, then sell after purchases complete at elevated prices. Mitigation includes transaction privacy through private mempools, slippage protection limiting execution price variance, and batch auction mechanisms processing orders simultaneously.
Liquidity Pool Drain Attacks
Exploiting AMM algorithm vulnerabilities enables draining liquidity pools through sequences of trades manipulating pool ratios. Constant product formula pools (x * y = k) face reentrancy vulnerabilities where attackers recursively call swap functions before state updates, curve manipulation exploiting specific pool configurations, and economic attacks where large trades create profitable arbitrage for attackers while harming liquidity providers. Real estate tokenization platforms must thoroughly audit AMM implementations, implement reentrancy guards, and use established battle-tested protocols rather than custom AMM development.
Market Manipulation and Wash Trading
Coordinated trading creating false volume and price movement misleads investors about true market conditions. Wash trading where same party controls both sides of trades inflates volume statistics. Pump and dump schemes coordinate purchases driving prices artificially high before coordinated selling crashes markets. Real estate tokenization platforms must implement transaction monitoring detecting suspicious patterns, volume analysis identifying wash trading, and if operating exchanges, surveillance systems meeting regulatory standards for market manipulation detection and prevention.
Impermanent Loss Exploitation
Liquidity providers in AMMs suffer impermanent loss when pooled asset price ratios diverge from deposit ratios. For property tokens paired with stablecoins, significant property appreciation creates impermanent loss for liquidity providers as arbitrageurs extract value rebalancing pools. While impermanent loss represents inherent AMM characteristic rather than exploit, understanding and mitigating effects requires sophisticated liquidity provider strategies, fee structures compensating for impermanent loss risk, and alternative market making approaches like concentrated liquidity or dynamic fees.
Alternative trading venues for tokenized real estate including order book exchanges, alternative trading systems (ATS), and over-the-counter platforms face different security challenges. Order book exchanges must prevent wash trading, spoofing, and layering manipulation tactics common in traditional markets. ATS platforms require comprehensive surveillance systems detecting suspicious activity patterns. OTC platforms face counterparty risk where trades settle outside automated protocols relying on trust between parties.
Regulatory frameworks in the USA, UK, UAE, and Canada impose specific requirements on platforms facilitating secondary market trading. US platforms operating as exchanges must register as alternative trading systems under Reg ATS requiring comprehensive market surveillance, reporting obligations, and fair access provisions. UK platforms require FCA authorization as trading venues with similar surveillance and reporting requirements. UAE and Canadian frameworks impose licensing and oversight for platforms enabling secondary trading. These regulations exist specifically to prevent market manipulation and protect investors from exploits.
Liquidity Security Principle: Real estate tokenization platforms promising “enhanced liquidity” through secondary markets must recognize that liquidity infrastructure introduces significant security risks requiring comprehensive protection. Platforms should prioritize using established, audited AMM protocols like Uniswap or Curve rather than developing custom market making logic unless they have expertise and resources for thorough security auditing. Transaction monitoring, manipulation detection, and regulatory compliance represent non-negotiable requirements for platforms facilitating trading. Real estate tokenization risks from inadequately secured liquidity mechanisms can destroy investor value through theft, manipulation, or regulatory enforcement regardless of underlying property performance.
Cross-Chain Bridge Risks in Tokenized Property Transfers
Cross-chain bridges enabling tokenized real estate transfers between different blockchains represent critical single points of failure where vulnerabilities have resulted in over $2 billion in stolen assets historically, making bridge security among the highest-priority real estate tokenization risks for platforms operating across multiple chains. Bridge exploits typically result in complete loss of bridged assets with no recovery mechanisms, affecting all users of compromised bridges regardless of individual security practices.
Bridge architecture fundamentally creates security challenges as bridges must lock assets on origin chains while minting equivalent representations on destination chains, maintaining accurate accounting across chains, and enabling bidirectional transfers. This architecture introduces trust assumptions and attack vectors including bridge smart contract vulnerabilities, validator compromise or collusion in multi-signature bridges, oracle manipulation providing false cross-chain information, and economic attacks exploiting bridge mechanism design flaws.
Major bridge hacks demonstrate real estate tokenization risks from cross-chain infrastructure. The Ronin Network bridge attack in 2022 resulted in $625 million theft when attackers compromised validator keys. Poly Network lost $610 million in 2021 through contract vulnerability exploitation, though funds were returned. Wormhole bridge lost $325 million in 2022. Nomad bridge was drained of $190 million in 2022. These incidents affected established bridges with professional security audits, highlighting that comprehensive auditing provides insufficient protection against sophisticated bridge attacks.
Don’t Let Security Risks Stop Your Tokenization Journey!
Partner with tokenization experts who understand real estate security. We’ve secured $2.3B+ in digital properties across USA, UK, UAE markets for 8+ years.
| Bridge Type | Architecture | Security Characteristics | Risk Profile |
|---|---|---|---|
| Lock-and-Mint Bridges | Lock assets on origin chain, mint wrapped tokens on destination chain, reverse process for return transfers | Security depends on custody mechanism for locked assets, typically multi-signature or validator consensus | High – validator compromise enables theft of all locked assets; contract bugs can enable unlimited minting |
| Liquidity Pool Bridges | Liquidity pools on each chain enable asset swaps without locking, liquidity providers facilitate transfers | Distributed risk across liquidity providers rather than centralized custody, but vulnerable to pool manipulation | Moderate-High – flash loan attacks, impermanent loss, slippage issues; lower single-point-of-failure risk |
| Native Chain Bridges | Built into blockchain protocol enabling native cross-chain communication, no third-party bridge required | Security inherited from underlying blockchain consensus, no additional trust assumptions beyond chain security | Low-Moderate – best security profile but limited availability, only works within specific ecosystems |
| Optimistic Bridges | Assume transfers valid unless fraud proofs submitted during challenge period, delayed finality for security | Enhanced security through fraud proof mechanisms, but slower transfer times (hours to days) | Low-Moderate – security-latency tradeoff; acceptable for property tokens given infrequent transfers |
| Zero-Knowledge Bridges | Use ZK-proofs validating cross-chain state without trust assumptions, cryptographic security guarantees | Strongest security model with mathematical proofs of correctness, but complex implementation | Low – emerging technology with limited production deployment; complexity creates implementation risks |
For real estate tokenization specifically, cross-chain transfers introduce additional legal complexities beyond technical risks. Tokens representing property interests must maintain legal enforceability across bridge transfers, with clear documentation that bridged representations preserve original ownership rights. Jurisdictional questions arise about which chain’s “version” of tokens represents authoritative ownership for legal purposes. Regulatory compliance must extend across chains ensuring all token representations satisfy applicable securities laws.
Bridge risk mitigation for real estate tokenization platforms includes minimizing cross-chain transfers to essential use cases only, using only established bridges with comprehensive security audits and substantial value secured over time, implementing transfer value limits preventing catastrophic single-transaction losses, maintaining monitoring detecting unusual bridge activity indicating potential exploits, and considering insurance coverage for bridge failures where available from specialized providers.
Bridge Security Incident: Multi-Chain Property Token Loss
A hypothetical scenario illustrates real estate tokenization risks from bridge vulnerabilities: A platform tokenizes properties on Ethereum mainnet but bridges tokens to Polygon for lower transaction costs. Investors hold $50 million in bridged property tokens on Polygon representing 25 commercial properties. The bridge experiences a validator compromise enabling attackers to mint unlimited wrapped tokens on Polygon without corresponding locked tokens on Ethereum.
Attackers mint millions of fake wrapped tokens, sell them in secondary markets crashing token prices, and extract real value from liquidity pools. Legitimate token holders on Polygon see their property token values collapse as markets cannot distinguish genuine bridged tokens from attacker-minted fakes. While Ethereum-side tokens retain value, Polygon tokens become worthless, and investors lacking clear documentation about which chain represents authoritative ownership face legal uncertainty about property rights.
This scenario, similar to actual bridge hacks, demonstrates how cross-chain architecture creates systemic risks affecting entire investor cohorts. Real estate tokenization platforms should carefully evaluate whether multi-chain benefits justify bridge risks, potentially restricting operations to single chains eliminating bridge dependencies or using only native chain bridges with strongest security guarantees.
Investor recommendations regarding cross-chain real estate tokenization focus on risk avoidance rather than mitigation. Given bridge security track record, investors should strongly prefer platforms operating on single chains eliminating bridge risks entirely. When cross-chain exposure is unavoidable, minimize bridged asset amounts, verify comprehensive insurance covering bridge failures exists, understand which chain represents authoritative ownership for legal purposes, and monitor bridge security developments adjusting positions if concerning vulnerabilities disclosed.
Bridge Risk Warning: Cross-chain bridges represent among the most dangerous components in cryptocurrency infrastructure with consistent track record of catastrophic failures despite professional security auditing and substantial resources. Real estate tokenization platforms should avoid bridge dependencies where possible, recognizing that enhanced theoretical liquidity from multi-chain presence provides poor risk-reward given bridge vulnerability history. Investors should treat cross-chain property tokens as significantly higher risk than single-chain alternatives, demanding substantial risk premiums or avoiding entirely given limited ability to evaluate bridge security and impossibility of recovering funds after bridge exploits.
Governance Attacks and DAO Manipulation Risks
Decentralized governance through DAOs (Decentralized Autonomous Organizations) enabling token holder participation in property management decisions introduces real estate tokenization risks through voting power concentration, low participation enabling small groups to control outcomes, flash loan governance attacks enabling temporary voting power acquisition, proposal manipulation, and inadequate minority protections. While democratic governance represents attractive philosophical principle, implementation challenges create attack vectors enabling value extraction from minority token holders.
Governance attack patterns in real estate tokenization include hostile takeover attempts where attackers accumulate sufficient tokens to control voting outcomes enabling disadvantageous decisions, bribery attacks where attackers pay token holders for voting rights without permanent token acquisition, flash loan governance attacks borrowing massive token amounts temporarily to pass proposals then returning tokens, and collusion where seemingly independent token holders coordinate to extract value from minority holders through governance actions.
Real estate governance decisions carry high stakes given property asset values and long-term investment horizons. Governance votes might determine property sales, refinancing terms, major capital improvements, distribution policy changes, and platform operational decisions. Malicious governance outcomes can destroy investor value through unfavorable property sales, excessive leverage, deferred maintenance reducing property values, or distribution reductions harming income-focused investors. Unlike typical cryptocurrency governance where worst case involves protocol parameter changes, real estate governance directly affects high-value physical assets.
Governance Attack Vectors in Property Tokenization
Voting Power Concentration
Early investors, founders, or large institutions accumulating significant token percentages control governance outcomes without need for broader community support. For property tokenization, major holders might vote for decisions benefiting themselves at minority expense like forcing property sales at disadvantageous timing, approving favorable refinancing terms for major holders, or reducing distributions while increasing capital reserves. Mitigation includes voting power caps, quadratic voting reducing whale influence, or hybrid governance combining token voting with property-manager veto rights protecting all investors.
Flash Loan Governance Attacks
Attackers borrow massive token amounts through flash loans, vote on proposals, then return tokens before transaction completion. This enables governance control without permanent capital commitment or economic stake in outcomes. Real estate DAO defense requires vote locking where tokens must be held through execution periods preventing flash loan voting, delegation delays requiring advance commitment before voting, and snapshot-based voting capturing token holdings at proposal creation rather than voting time.
Low Participation Exploitation
Governance participation rates in cryptocurrency average 5-15%, enabling small coordinated groups to control outcomes despite holding minority token stakes. Attackers proposing unfavorable changes during low-attention periods or immediately after large token distributions capitalize on participation asymmetry. Real estate tokenization governance requires minimum participation quorums ensuring proposals receive sufficient review, participation incentives encouraging voting, and extended voting periods providing adequate time for community engagement.
Proposal Obfuscation
Complex technical proposals hiding exploitative terms within legitimate-appearing governance actions. Token holders lacking technical expertise or time for comprehensive analysis approve proposals containing hidden value extraction mechanisms. For property governance, proposals ostensibly addressing routine maintenance might include terms enabling major expenditures benefiting specific parties. Clear proposal templates, plain-language summaries, professional review requirements, and community discussion periods help prevent proposal obfuscation exploitation.
Vote Buying and Bribery
Attackers offer payments to token holders for voting specific ways without requiring permanent token transfer. Bribery platforms enable anonymous vote buying at scale. For real estate governance, vote buying might enable forcing property sales, approving disadvantageous refinancing, or changing distribution policies favoring specific holders. Combating vote buying requires social consensus against bribery, transparent voting processes exposing unusual patterns, and legal frameworks treating governance bribery as securities fraud where applicable.
Governance Deadlock
While not direct attack, governance systems requiring high approval thresholds risk deadlock preventing timely decisions. Properties requiring emergency repairs, refinancing with time-limited offers, or market-timing-sensitive sales might miss opportunities through governance delays. Balanced governance implements tiered decision making with higher thresholds for major decisions, professional property management authority for routine operations, and emergency procedures enabling rapid response to time-sensitive situations while maintaining oversight.
Regulatory frameworks in the USA, UK, UAE, and Canada impose requirements on governance in tokenized securities that constrain pure DAO models. Securities laws may require professional management fiduciary duties superseding token holder voting in certain contexts. Investment Company Act in USA limits investor participation in management decisions for certain structures. These regulatory requirements create tension with decentralized governance ideals, requiring hybrid models balancing regulatory compliance with token holder participation.
Best practices for real estate tokenization governance balance decentralization benefits against real estate tokenization risks from governance exploits. Recommendations include tiered governance with different approval thresholds for routine versus major decisions, professional property management handling day-to-day operations with token holder oversight for major decisions, time-locked implementation providing abort windows if problems discovered, minority protections preventing majority from extracting unfair value, and hybrid models combining token voting with professional oversight ensuring regulatory compliance and protecting all investors.
Governance Security Principle: Real estate tokenization platforms should recognize that pure DAO governance creates significant security and operational risks for property management. Properties require professional expertise, timely decision-making, and regulatory compliance difficult achieving through decentralized voting. Successful platforms implement hybrid governance where token holders maintain oversight and vote on major decisions while professional managers handle operations. Platforms claiming complete decentralization while managing high-value real estate create false impressions about governance reality, as practical property management requires professional involvement regardless of philosophical preferences for decentralization.
Data Privacy and Investor Information Leakage
Data privacy represents critical concern in real estate tokenization where platforms must collect sensitive personal information for KYC compliance, securities regulation adherence, and operational purposes while protecting investor privacy against breaches, unauthorized access, and blockchain transparency revealing financial positions. Privacy real estate tokenization risks include identity theft from breached KYC data, financial surveillance through blockchain analysis, competitive intelligence from visible investment patterns, and regulatory violations through inadequate data protection under GDPR, PIPEDA, and state privacy laws.
The fundamental tension between blockchain transparency and privacy requirements creates architectural challenges for real estate tokenization. Public blockchains expose all transaction data including wallet addresses, token amounts, and transaction timing. While addresses provide pseudonymity rather than anonymity, sophisticated blockchain analysis can link addresses to real identities through exchange interactions, IP address correlation, transaction pattern analysis, and cross-referencing with other data sources. For real estate investors, this transparency enables competitors, business partners, or malicious actors monitoring investment positions and strategies.
Personal data collected by real estate tokenization platforms includes identity documents (passports, driver’s licenses), financial information (bank statements, tax returns), accreditation verification, residential addresses, employment details, and investment histories. This data concentration creates attractive targets for cybercriminals enabling identity theft, financial fraud, phishing attacks, and physical security risks if residential addresses linked to high-value investment positions become publicly known.
| Privacy Risk Category | Data Exposure Vectors | Consequences | Mitigation Strategies |
|---|---|---|---|
| KYC Data Breaches | Database hacks, insider theft, third-party KYC provider compromises, insecure data transmission | Identity theft, financial fraud, phishing attacks, regulatory penalties under data protection laws | Encryption at rest/transit, access controls, third-party security audits, breach notification procedures, minimal data retention |
| Blockchain Transparency | Public blockchain transaction data, address clustering analysis, exchange data correlation, pattern recognition | Investment strategy exposure, competitive intelligence leakage, financial surveillance, targeting by criminals | Privacy-preserving chains, zero-knowledge proofs, mixing services where legal, multi-address strategies |
| Investor Registry Exposure | Platform breaches, regulatory filings, legal discovery, third-party marketing partnerships | Unsolicited marketing, competitive profiling, social engineering, physical security risks | Confidential investor lists, data sharing restrictions, secure registry systems, opt-out marketing |
| Transaction Metadata | IP addresses, device fingerprints, timing patterns, geographic location, browsing behavior | Investor profiling, behavior tracking, de-anonymization, surveillance | Minimal logging, anonymization, VPN/Tor support, metadata stripping |
| Communication Privacy | Email interception, platform messages, customer support interactions, unencrypted communications | Sensitive information disclosure, phishing material, social engineering data | End-to-end encryption, secure messaging, PGP email options, security awareness training |
Regulatory privacy frameworks significantly affect real estate tokenization platforms operating internationally. EU GDPR imposes strict requirements on data collection, processing, storage, and deletion with substantial penalties for violations reaching 4% of global revenue. UK maintains similar standards through UK GDPR and Data Protection Act. Canada’s PIPEDA requires consent for data collection and provides individual rights to access and correct personal information. US lacks comprehensive federal privacy law but states like California (CCPA/CPRA), Virginia, and others impose specific requirements. Platforms must comply with strictest applicable standard when serving international investors.[2]
Privacy-preserving technologies offer potential solutions balancing regulatory requirements with investor privacy preferences. Zero-knowledge proofs enable proving investor eligibility without revealing underlying personal data. Homomorphic encryption allows computations on encrypted data without decryption. Secure multi-party computation enables collaborative analysis without exposing individual data. However, these technologies remain complex to implement and may not satisfy all regulatory requirements demanding platforms maintain actual identity records rather than cryptographic proofs.
Privacy Best Practices for Investors
- Minimize personal information disclosure to platforms, providing only legally required data
- Use dedicated email addresses and phone numbers for cryptocurrency activities
- Review platform privacy policies and data sharing practices before investing
- Request data deletion when exiting platforms where regulations permit
- Use fresh wallet addresses for each platform avoiding address reuse enabling tracking
- Consider VPN usage for platform access protecting IP addresses and geographic location
- Monitor credit and identity for signs of data breach affecting KYC information
- Verify platforms implement encryption, access controls, and security certifications protecting data
- Recognize that blockchain transparency means transaction privacy is limited on public chains
Privacy Reality: Complete privacy in real estate tokenization remains impossible given regulatory requirements for identity verification, blockchain transparency exposing transactions, and operational necessities requiring data collection. Investors must accept privacy compromises inherent in regulated securities tokenization, focusing efforts on minimizing unnecessary disclosures and ensuring platforms implement professional data protection standards. Real estate tokenization risks from privacy failures include not just personal inconvenience but potential identity theft, financial fraud, and physical security threats if high-net-worth investors become targets through exposed investment data. Platforms and investors share responsibility for privacy protection through comprehensive security practices and minimal data disclosure policies.
Recovery, Upgrade, and Contract Immutability Risks
Smart contract immutability creating security through preventing unauthorized modifications simultaneously creates real estate tokenization risks when bugs are discovered, business logic requires updates, or regulatory changes demand functionality modifications. The tension between immutability providing security against tampering and upgradeability enabling bug fixes and improvements represents fundamental challenge in tokenization platform architecture requiring careful balance through technical mechanisms and governance procedures.
Immutable smart contracts deployed with vulnerabilities present permanent risks that cannot be remediated through traditional software patching. When critical bugs are discovered in immutable property tokenization contracts, platforms face limited options including migrating to new contracts requiring all token holders to exchange tokens creating friction and potential losses, implementing workarounds in external systems introducing centralization risks, or accepting ongoing vulnerability exposure hoping for benign outcomes. Each option creates significant real estate tokenization risks affecting platform viability and investor security.
Upgradeability patterns enabling smart contract modifications introduce their own vulnerabilities and trust assumptions. Proxy patterns where logic contracts can be replaced maintain storage in separate contracts enabling upgrades, but misconfigured proxies or compromised upgrade keys enable malicious contract replacements. Transparent proxy patterns, UUPS (Universal Upgradeable Proxy Standard), and Diamond pattern implementations each balance upgradeability with security through different mechanisms and trade-offs requiring careful evaluation.
Upgrade Mechanism Security Considerations
Access Control for Upgrades
Upgrade authority represents ultimate control over platform functionality, enabling complete contract logic replacement including removing restrictions, redirecting funds, or installing backdoors. Single-key upgrade authority creates centralization risk where key compromise enables malicious upgrades. Real estate tokenization platforms must implement multi-signature upgrade requirements, time-locked operations providing abort windows, governance approval requirements engaging token holders, and transparent upgrade procedures with advance notice enabling community review before implementation.
Storage Collision Risks
Upgradeable contracts using proxy patterns must maintain storage layout compatibility across versions. Storage collisions where new contract versions alter storage slot meanings can corrupt data including token balances, ownership records, and configuration parameters. For property tokenization, storage corruption could reassign token ownership, modify distribution amounts, or corrupt governance state. Comprehensive testing, automated storage layout verification, and formal verification of upgrade compatibility help prevent storage collision risks.
Function Selector Clashes
Proxy contracts route function calls to implementation contracts through function selectors (first 4 bytes of function signature hash). Collisions where different functions produce identical selectors enable calling unintended functions with potential security implications. While rare, function selector clashes must be checked during upgrades, and platforms should implement selector collision detection preventing deployment of contracts with clashing signatures.
Initialization Vulnerabilities
Upgradeable contracts cannot use constructors due to proxy pattern constraints, instead requiring initialization functions setting initial state. Unprotected initialization functions enable anyone initializing contracts taking ownership or setting malicious parameters. Multiple initialization attempts or front-running initialization transactions create risks. Real estate tokenization platforms must implement initialization protection through modifiers preventing repeat initialization, immediately initializing after deployment, and using CREATE2 for deterministic deployment addresses enabling verification.
Upgrade Path Dependencies
Complex platforms with multiple interdependent contracts face challenges upgrading individual components without breaking integrations. Upgrade sequencing matters when contracts depend on specific interface versions or state assumptions. Real estate tokenization platforms must document upgrade dependencies, test upgrade procedures comprehensively including partial failure scenarios, implement version compatibility checks, and maintain rollback capabilities if upgrades cause unexpected issues.
Recovery mechanisms for catastrophic failures represent additional consideration in real estate tokenization where high asset values justify extraordinary recovery procedures. Some platforms implement emergency pause functionality enabling administrators freezing operations when attacks detected, providing time for analysis and mitigation before damage completion. However, pause mechanisms create centralization concerns where administrators gain significant control over investor assets. Circuit breakers limiting transaction sizes or velocities provide automated protection without human intervention but may interfere with legitimate large transactions.
The regulatory perspective on contract immutability and upgradeability varies across USA, UK, UAE, and Canada jurisdictions. Securities regulations generally expect platforms maintaining ability to address compliance violations, security vulnerabilities, or operational issues, viewing complete immutability skeptically for platforms managing investor assets. Conversely, pure decentralization advocates criticize upgradeability as introducing centralization undermining blockchain benefits. Platforms must balance regulatory expectations with decentralization philosophy through governance-controlled upgrades, transparent procedures, and limited upgrade authority scope.
| Approach | Immutable Contracts | Upgradeable Contracts | Hybrid Approach |
|---|---|---|---|
| Security | High – no upgrade attack vector, tamper-proof | Moderate – upgrade mechanisms introduce risks | High – critical components immutable, flexible components upgradeable |
| Flexibility | Low – cannot fix bugs or adapt to changes | High – can fix bugs, add features, adapt to regulations | Moderate – flexibility where needed, security where critical |
| Complexity | Low – simpler architecture, easier to audit | High – proxy patterns, storage management, upgrade procedures | Moderate – complexity where upgradeability needed |
| Trust Model | Minimized – code is law, no admin control | Increased – trust upgrade authority, governance | Balanced – critical functions trustless, operational flexibility trusted |
| Real Estate Suitability | Low – properties require adaptability | Moderate-High – enables necessary adaptations but introduces risks | High – balances security with operational needs |
For investors evaluating platforms, understanding upgrade mechanisms and governance over contract modifications represents important due diligence. Platforms should transparently document whether contracts are immutable or upgradeable, who controls upgrade authority if upgradeable, what governance procedures govern upgrades, and what protections exist preventing malicious upgrades. Completely immutable contracts create bug fix risks; single-key-controlled upgradeable contracts create centralization risks. Optimal approaches use multi-signature governance-controlled upgrades with time locks providing security against malicious modifications while maintaining necessary flexibility.
Immutability Principle: Real estate tokenization platforms must carefully balance immutability benefits against upgrade necessity given long investment horizons and evolving regulatory requirements. Pure immutability creates risks where discovered vulnerabilities cannot be remediated, but unlimited upgrade authority creates centralization undermining blockchain benefits. Best practices implement immutability for critical security-sensitive components like token ownership records while maintaining controlled upgradeability for operational components like distribution logic or fee structures. Real estate tokenization risks from both extremes excessive immutability preventing necessary adaptations and excessive upgradeability enabling malicious modifications requires nuanced middle path through governance-controlled limited-scope upgrades with transparent procedures and community oversight.
Emerging Security Risks as Real Estate Tokenization Scales
As real estate tokenization moves from experimental implementations toward mainstream adoption, scaling introduces emerging security challenges qualitatively different from current small-scale deployments. These scaling-related real estate tokenization risks include concentrated systemic risks where platform failures affect thousands of investors across hundreds of properties, regulatory evolution potentially invalidating existing structures, quantum computing threats to cryptographic security, sophisticated attack economics where multi-billion-dollar platforms justify advanced persistent threats, and integration complexity as tokenization platforms interconnect with traditional financial systems.
Systemic risk concentration represents perhaps the most concerning scaling challenge as successful platforms grow to manage tens of billions in tokenized property assets. A platform controlling $50 billion in real estate through tokenization represents systemically important infrastructure where catastrophic failure through security exploits, regulatory enforcement, or operational collapse creates economy-wide repercussions affecting millions of investors, real estate markets, and financial stability. Current fragmented tokenization with dozens of small platforms limits systemic risk; consolidation toward platform oligopolies concentrates risks dangerously.
Quantum computing poses existential long-term threat to blockchain cryptography underlying real estate tokenization. Current public key cryptography used for digital signatures relies on computational hardness assumptions that quantum computers could break using Shor’s algorithm, enabling quantum attackers to forge signatures and steal funds from any address. While practical quantum threats remain years away, properties tokenized today might still be held decades when quantum computing matures, creating forward-looking security concerns requiring preparation through quantum-resistant cryptography adoption.
Emerging Risk Categories for Scaled Real Estate Tokenization
AI-Powered Attack Sophistication
Artificial intelligence enables increasingly sophisticated attacks including AI-generated phishing campaigns achieving unprecedented success rates, automated vulnerability discovery in smart contracts identifying flaws human auditors miss, deepfake social engineering impersonating platform executives, and adaptive attacks evolving in real-time based on defense responses. Real estate tokenization platforms must implement AI-powered defenses matching attacker capabilities through anomaly detection, behavior analysis, automated threat response, and continuous security monitoring leveraging machine learning identifying attack patterns.
Supply Chain Complexity
Scaled platforms integrate dozens of third-party services for KYC, custody, oracles, analytics, and infrastructure creating extensive supply chains where compromising any component enables attacks. SolarWinds demonstrated supply chain vulnerability severity. Real estate tokenization platforms must implement comprehensive vendor security assessment, dependency scanning, software bill of materials (SBOM) management, zero-trust architectures assuming potential compromise, and rapid incident response when supply chain breaches discovered.
Regulatory Fragmentation
As platforms scale internationally across USA, UK, UAE, Canada, and dozens of additional jurisdictions, conflicting regulatory requirements create compliance complexity where satisfying one jurisdiction violates another. Regulatory fragmentation risks include platforms forced choosing between markets, compliance costs consuming operational margins, and structural decisions made for one jurisdiction limiting global expansion. International regulatory harmonization efforts progress slowly while tokenization adoption accelerates, creating persistent regulatory real estate tokenization risks.
Composability Cascade Failures
DeFi composability enabling protocols building on others creates value but also correlation risk where single protocol failures cascade through dependent systems. Real estate tokenization platforms integrating with lending protocols, yield aggregators, or liquidity networks face cascade failure risks where exploits in one system affect interconnected platforms. 2022 Terra/Luna collapse demonstrated how interconnected failures propagate system-wide. Mitigation requires careful integration design, circuit breakers limiting contagion, diversification across protocols, and conservative risk parameters.
State-Sponsored Threats
As real estate tokenization platforms manage billions in assets, they become attractive targets for state-sponsored attackers with resources exceeding typical cybercriminals. Nation-state threats include advanced persistent threats maintaining long-term access, zero-day exploits unknown to security community, supply chain compromises at scale, and regulatory weaponization for geopolitical purposes. Defense requires nation-state threat modeling, advanced threat intelligence, separation of concerns preventing single compromise catastrophe, and geopolitical risk assessment in strategic planning.
Quantum Computing Preparation
While practical quantum threats remain years away, preparation must begin now given long investment horizons in real estate. Quantum computers breaking current cryptography would enable forging signatures and stealing funds from any address. Migration to quantum-resistant cryptography requires blockchain protocol updates, wallet software modifications, and user education. Platforms tokenizing properties investors will hold for decades must plan quantum-resistant cryptography transitions proactively rather than waiting for quantum threats to materialize.
Scaling challenges extend beyond technical security to operational and organizational dimensions. Platforms managing billions in assets require professional security teams, comprehensive monitoring infrastructure, 24/7 incident response capabilities, and mature operational security programs far exceeding startup capabilities. The transition from small experimental platforms to institutional-grade operations creates growing pains where inadequate scaling of security capabilities relative to asset growth creates elevated real estate tokenization risks during transition periods.
The emergence of institutional custody, lending, and derivatives markets for tokenized real estate creates financial system integration bringing both benefits and risks. Integration enables deeper liquidity, sophisticated investment products, and institutional participation accelerating adoption. However, it also creates contagion vectors where real estate tokenization platform failures could affect broader financial systems, and conversely where traditional financial system crises could cascade into tokenization markets through interconnections.
Scaling Security Imperative: Real estate tokenization platforms must recognize that security requirements scale super-linearly with assets under management. A platform managing $100 million requires more than 10x the security investment of one managing $10 million due to increased attacker motivation, regulatory scrutiny, systemic importance, and operational complexity. Platforms experiencing rapid growth must scale security capabilities proactively ahead of asset growth rather than reactively after incidents. Real estate tokenization risks from inadequate security scaling during growth phases create vulnerability windows where platforms become attractive targets before implementing commensurate defenses. Investors should favor platforms demonstrating mature security programs scaling appropriately with managed assets over those claiming security adequacy based on small-scale deployment experience.
For investors, emerging risks as real estate tokenization scales reinforce need for ongoing monitoring and periodic reassessment rather than set-and-forget investment approaches. Platforms appropriate for small experimental investments may prove unsuitable as they scale without proportional security maturity. Regulatory changes, technological threats, and evolving attack sophistication require active engagement with platform security posture evolution. Investors should maintain diversification across platforms and traditional real estate reducing concentration risk as scaled platforms potentially create systemic vulnerabilities.
Success in real estate tokenization requires treating security not as checkbox compliance but as continuous investment proportional to assets managed and threats faced. Investors must demand transparency, verify security implementations, and maintain vigilant monitoring throughout investment lifecycles.
People Also Ask
The main security risks include smart contract vulnerabilities that can be exploited by hackers, private key theft leading to loss of digital property ownership, platform infrastructure breaches exposing investor data, oracle manipulation affecting property valuations, regulatory non-compliance resulting in legal penalties, liquidity risks in secondary markets, and custodial failures where third-party storage providers lose or misappropriate tokenized assets. These risks stem from the intersection of traditional real estate complexities with emerging blockchain technology vulnerabilities.
Tokenized real estate introduces unique digital security risks absent in traditional property investment, including smart contract bugs, blockchain network vulnerabilities, and private key management challenges. However, it also offers enhanced transparency through immutable blockchain records and potentially better regulatory compliance through automated enforcement. The safety depends significantly on platform maturity, security auditing rigor, regulatory compliance, custodial arrangements, and investor due diligence. Traditional real estate has decades of established legal frameworks, while tokenization is still evolving regulatory clarity.
Yes, tokenized real estate can be compromised through multiple attack vectors including smart contract exploits that drain funds, private key theft through phishing or malware, platform breaches exposing wallet credentials, oracle manipulation affecting property valuations, and bridge hacks during cross-chain transfers. While blockchain itself is highly secure, the surrounding infrastructure including wallets, platforms, and smart contracts contains vulnerabilities. Proper security measures like multi-signature wallets, hardware key storage, audited smart contracts, and qualified custodians significantly reduce but cannot eliminate these risks.
If a tokenization platform shuts down, the impact depends on the underlying legal structure and custody arrangements. Well-structured platforms separate token ownership rights from platform operations, with tokens representing legally enforceable property claims that survive platform closure. However, investors may face challenges accessing secondary markets, receiving distributions, or exercising governance rights. Custodial arrangements, backup service providers, and legal documentation determine whether investors can recover their assets. Platforms using non-custodial models and decentralized infrastructure provide better continuity than centralized platforms.
Yes, tokenized real estate is regulated as securities in these jurisdictions. In the USA, the SEC requires compliance with securities laws including registration or exemptions. The UK’s FCA regulates security tokens under existing financial services frameworks. The UAE, particularly Dubai’s DFSA and VARA, has established specific digital asset regulations. Canada’s securities regulators treat tokens as securities requiring prospectus or exemption compliance. Each jurisdiction has distinct requirements for offerings, trading, custody, and reporting. Investors should verify platform regulatory compliance in their specific jurisdiction before investing.
Smart contract bugs can result in permanent loss of funds, frozen assets preventing transfers or sales, incorrect distribution calculations affecting investor returns, unauthorized access enabling theft, and failed governance mechanisms preventing collective decision-making. Once deployed, bugs in immutable contracts cannot be easily fixed without complex upgrade mechanisms. Historical incidents include The DAO hack losing $60 million and various DeFi exploits draining hundreds of millions. Real estate tokenization platforms must conduct comprehensive security audits, formal verification, bug bounties, and implement upgradeable contract patterns with appropriate safeguards.
Losing private keys results in permanent, irreversible loss of access to tokenized property assets with no recovery mechanism in truly decentralized systems. Unlike traditional finance where institutions can verify identity and restore access, blockchain private key loss means funds are unrecoverable. Estimates suggest 20% of Bitcoin has been permanently lost due to key loss. For real estate tokenization, this risk is mitigated through qualified custodians, multi-signature wallets requiring multiple keys, social recovery mechanisms, hardware wallet storage, and institutional custody solutions with insurance and backup procedures.
Oracles provide off-chain data like property valuations, rental income verification, and market prices to smart contracts. Malicious oracle manipulation can artificially inflate property values triggering improper loan liquidations, provide false rental income data affecting distributions, manipulate pricing for unfair secondary market trades, and trigger incorrect governance actions. Since smart contracts rely on oracle data for critical decisions, compromised oracles undermine entire platform integrity. Mitigation includes using multiple independent oracle sources, decentralized oracle networks, time-weighted averages, and conservative collateralization ratios.
Cross-chain bridges enabling tokenized property transfers between blockchains represent significant security vulnerabilities, with over $2 billion stolen from bridge hacks historically. Risks include bridge smart contract exploits draining locked assets, validator collusion or compromise in bridge consensus mechanisms, replay attacks executing transfers multiple times, and liquidity imbalances preventing asset redemption. For real estate tokens, bridge failures can result in assets locked on one chain with duplicate tokens on another, creating ownership disputes. Investors should minimize cross-chain transfers and use only well-audited, established bridge protocols.
Investors should conduct comprehensive due diligence including verifying platform regulatory compliance in their jurisdiction, reviewing independent security audit reports, confirming qualified custodial arrangements or using hardware wallets for self-custody, starting with small investments to test platform reliability, diversifying across multiple properties and platforms, understanding legal structures underlying tokens, verifying team credentials and track records, monitoring platform governance and security practices, maintaining secure operational security including unique passwords and two-factor authentication, and consulting legal and financial advisors before significant investments.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







