Key Takeaways
- ▸The upgradability of Solana smart contracts enables direct bytecode replacement through BPF Upgradeable Loader, allowing authorized updates without proxy patterns required in Ethereum, benefiting developers across USA, UK, UAE, and Canada.
- ▸Upgrade authority represents exclusive control over program modifications, transferable to multi-signature wallets or governance systems, providing flexible transition from centralized development to decentralized community control as projects mature globally.
- ▸Program data accounts separate executable code from program state in the upgradability of Solana smart contracts, enabling atomic bytecode replacement while preserving program addresses and existing on-chain integrations seamlessly.
- ▸Security risks include compromised upgrade authority enabling malicious code injection, requiring multi-signature controls, time-locked proposals, comprehensive audits costing $50,000-$200,000, and transparent governance processes protecting user funds effectively.
- ▸Finalization permanently revokes upgradability in Solana smart contracts, making programs immutable after extensive testing and auditing, providing maximum security guarantees appropriate for mature DeFi protocols handling billions in total value locked.
- ▸Best practices combine staged rollouts on devnet before mainnet, comprehensive testing, security audits, transparent communication, and gradual authority decentralization balancing innovation velocity with security requirements across blockchain ecosystems worldwide.
Introduction to Solana Smart Contract Upgradability
The upgradability of Solana smart contracts represents a fundamental design choice distinguishing Solana’s program architecture from traditional blockchain platforms. With over eight years of experience developing blockchain solutions across USA, UK, UAE, and Canada, our agency has witnessed how Solana’s native upgradeability mechanisms enable developers to iterate rapidly while maintaining production deployments. Unlike Ethereum where immutability is default requiring complex proxy patterns for upgrades, Solana provides built-in upgradeability through the BPF Upgradeable Loader, offering flexibility without compromising security when properly implemented.
Understanding program control mechanisms is essential for developers, auditors, and users interacting with Solana’s ecosystem managing over $5 billion in total value locked. The upgradability of Solana smart contracts affects security models, governance structures, and user trust. This comprehensive guide examines technical implementation, security considerations, governance best practices, and strategic decisions around program upgradeability, providing actionable insights for building production-grade Solana applications serving global markets.
What Are Solana Programs and How They Differ from EVM Contracts
Solana programs fundamentally differ from Ethereum Virtual Machine contracts through their account-based architecture and separation of code from data. The upgradability of Solana smart contracts leverages this design where programs represent stateless executable code while data resides in separate accounts owned by programs. This separation enables Solana’s parallel transaction processing achieving 65,000 transactions per second, contrasting with Ethereum’s sequential execution model where contracts store both code and state within single addresses.
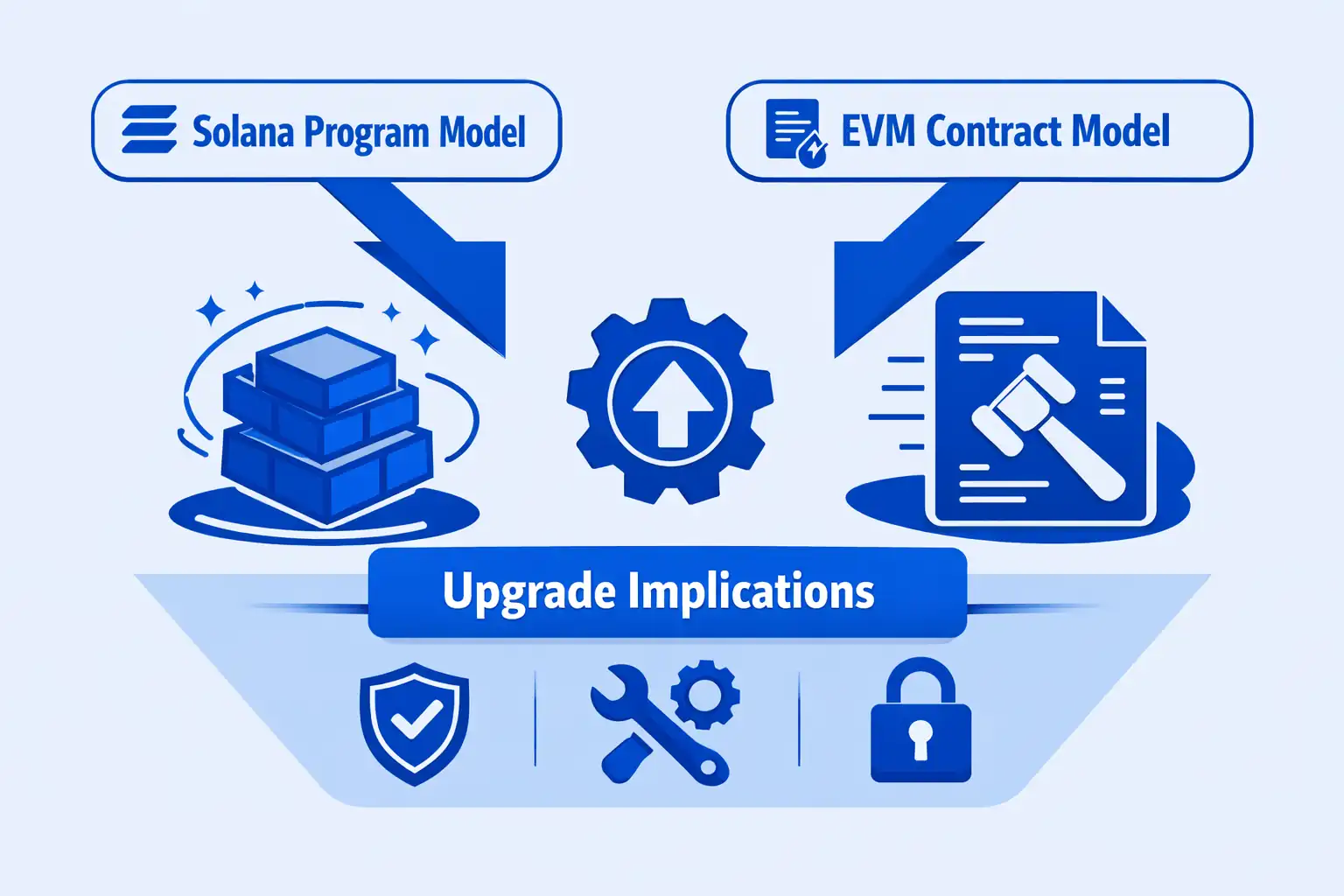
Solana Programs vs EVM Smart Contracts Architecture
Solana Program Model
- Stateless executable code separated from data
- Programs own multiple data accounts
- Native upgradability through BPF Loader
- Parallel transaction execution
- Written in Rust, C, or C++
EVM Contract Model
- Code and state combined in single contract
- Immutable by default after deployment
- Proxy patterns required for upgrades
- Sequential transaction processing
- Written in Solidity or Vyper
Upgrade Implications
- Solana: Direct bytecode replacement possible
- EVM: Requires proxy delegation patterns
- Solana: Maintains original program address
- EVM: Complex storage slot management
- Both: Require careful security consideration
Why Upgradability Matters in Solana Programs
The upgradability of Solana smart contracts provides critical advantages for development velocity, bug fixes, feature additions, and protocol evolution without disrupting user experiences. Early-stage projects benefit from iterating rapidly based on user feedback, fixing discovered vulnerabilities, and improving performance without redeploying new program addresses. This flexibility accelerates innovation cycles enabling Solana’s DeFi ecosystem to compete effectively with established Ethereum protocols while maintaining lower costs and higher throughput benefiting users across USA, UK, UAE, and Canadian markets.
Default Immutability vs Upgradeable Programs on Solana
Solana supports both immutable and upgradeable program deployments, with developers choosing appropriate models based on security requirements and development stage. Programs deployed without specifying upgrade authority become immutable immediately, providing maximum security guarantees. The upgradability of Solana smart contracts through BPF Upgradeable Loader offers flexibility during development while allowing permanent finalization after extensive testing and auditing, balancing innovation needs with security priorities across different protocol maturity levels.
| Program Type | Characteristics | Use Cases | Trust Model |
|---|---|---|---|
| Immutable Programs | No upgrade authority, permanently fixed bytecode | Core protocols, token standards, critical infrastructure | Maximum trust |
| Centralized Upgradeable | Single authority controls all upgrades | Development, testing, early-stage protocols | Requires authority trust |
| Multi-Sig Controlled | Multiple signers required for upgrades | Team-managed protocols, organizational control | Moderate trust |
| DAO Governed | Community voting controls upgrade decisions | Mature protocols, decentralized governance | Decentralized trust |
The BPF Upgradeable Loader Explained
The BPF Upgradeable Loader forms the technical foundation enabling the upgradability of Solana smart contracts through specialized program accounts managing executable bytecode and upgrade permissions. When deploying upgradeable programs, the loader creates three account types: the program account storing the program address, the program data account containing actual executable bytecode, and the buffer account temporarily holding new bytecode during upgrades. This architecture enables atomic bytecode replacement while preserving program addresses and existing integrations across the Solana ecosystem.
Program Authority and Upgrade Authority Roles
Authority management in the upgradability of Solana smart contracts distinguishes between program authority controlling program accounts and upgrade authority specifically managing bytecode modifications. The upgrade authority keypair must sign all upgrade transactions, providing exclusive control over program evolution. This authority can be transferred to different accounts including multi-signature wallets, governance programs, or revoked entirely through finalization. Proper authority management is critical for security, with leading protocols transitioning from developer control to decentralized governance as projects mature across global blockchain ecosystems.
Secure Your Upgradability of Solana Smart Contracts
Protect your protocol with expert security audits, governance design, and upgrade management. Ensure your Solana programs meet industry security standards and best practices.
How Program Data Accounts Enable Upgrades
Program data accounts provide the mechanism enabling the upgradability of Solana smart contracts by separating mutable bytecode storage from immutable program addresses. During upgrades, the BPF Upgradeable Loader replaces bytecode within program data accounts atomically, ensuring transactions either execute against old or new versions without intermediate states. This architecture maintains program address consistency enabling seamless upgrades without breaking existing integrations, front-ends, or on-chain references across Solana’s ecosystem serving USA, UK, UAE, and Canadian users.
Deployment Process for Upgradeable Solana Programs
Deploying upgradeable programs through the upgradability of Solana smart contracts involves compiling Rust code to BPF bytecode, writing compiled output to buffer accounts, and deploying buffer contents to program data accounts with designated upgrade authority. Developers use Solana CLI commands or Anchor framework utilities specifying upgrade authority during initial deployment. The process requires sufficient SOL for rent-exempt account balances, transaction fees, and comprehensive testing on devnet before mainnet deployment ensuring code quality and security across production environments.
Program Upgrade Deployment Lifecycle
Compile and Buffer Creation
Compile updated program code to BPF bytecode, create buffer account with sufficient rent-exempt SOL, write compiled bytecode to buffer.
Authority Verification and Upgrade
Verify upgrade authority signature, execute upgrade instruction replacing program data account bytecode, validate successful deployment.
Testing and Monitoring
Execute comprehensive testing suite, monitor program execution on-chain, communicate upgrade to users, close buffer account reclaiming rent.
Changing or Revoking Upgrade Authority
Authority transfer in the upgradability of Solana smart contracts enables transitioning control from individual developers to multi-signature wallets or governance systems as projects mature. The current upgrade authority executes set-upgrade-authority instructions specifying new authority addresses or null values for permanent finalization. Common patterns include transferring authority to Squads multi-sig requiring 3-of-5 signatures, Realm governance enabling token holder voting, or custom governance programs implementing project-specific control mechanisms balancing security with operational flexibility across development stages.
Program Control Risks and Security Considerations
Security risks in the upgradability of Solana smart contracts include compromised upgrade authority enabling malicious bytecode injection, insider threats from corrupted team members, and rug pulls where developers upgrade programs draining user funds. Centralized upgrade control creates single points of failure vulnerable to hacking, social engineering, or coercion. Users across USA, UK, UAE, and Canada must verify upgrade authority status before depositing significant value, with transparent governance and multi-signature controls providing risk mitigation appropriate for protocol risk profiles.
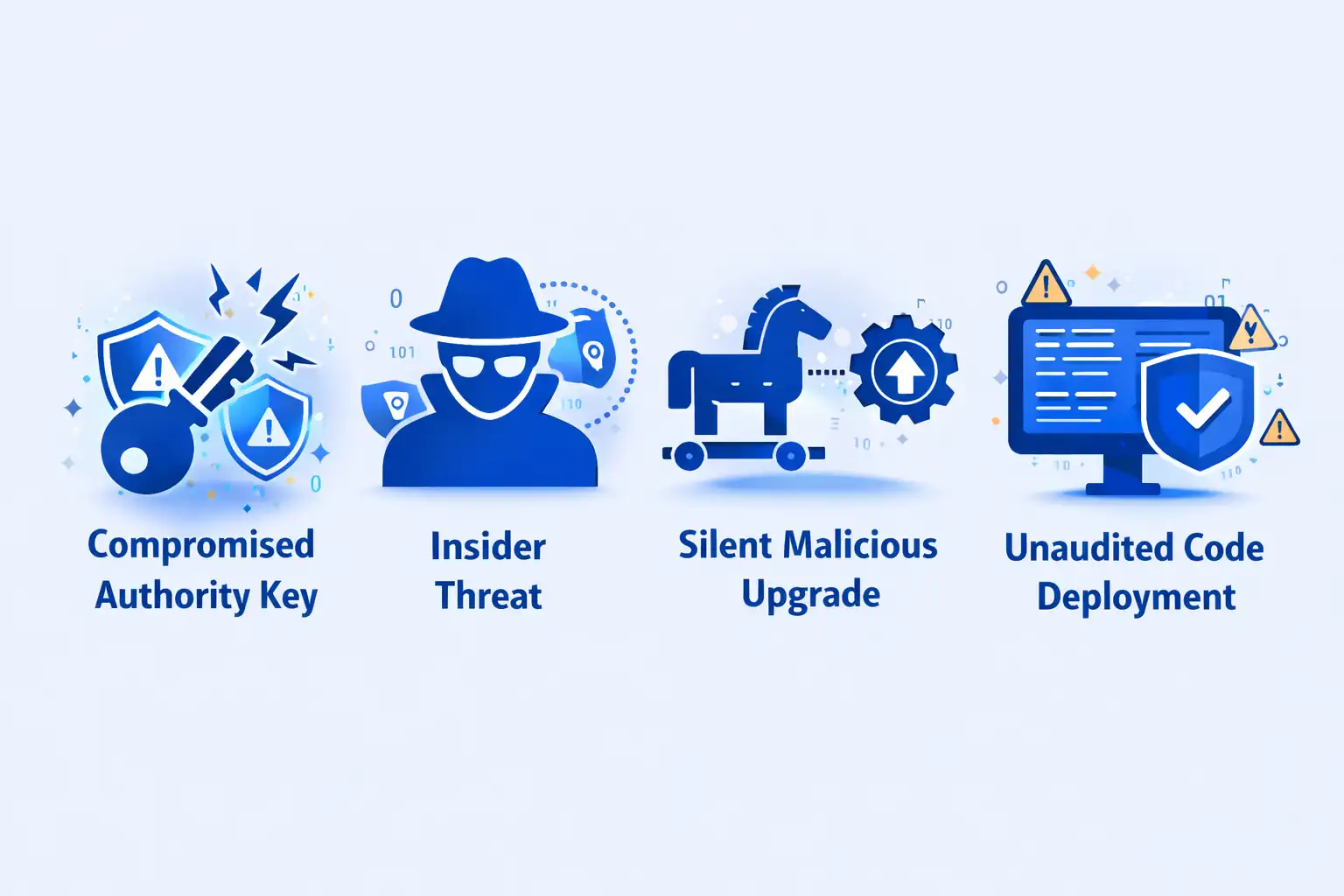
| Security Risk | Impact | Mitigation Strategy |
|---|---|---|
| Compromised Authority Key | Malicious code injection, fund theft | Multi-sig, hardware wallets, time locks |
| Insider Threat | Rug pull, unauthorized changes | DAO governance, transparency, audits |
| Silent Malicious Upgrade | User funds at risk, trust loss | Public proposals, time delays, monitoring |
| Unaudited Code Deployment | Bugs, vulnerabilities, exploits | Mandatory audits, bug bounties, testing |
Best Practices for Managing Program Upgradability
Professional management of the upgradability of Solana smart contracts requires comprehensive testing on devnet before mainnet deployment, security audits costing $50,000-$200,000 from specialized firms, transparent communication about upgrade schedules, and staged rollouts enabling rapid rollback if issues emerge. Leading protocols implement time-locked upgrades providing 24-48 hours for community review, maintain public repositories with upgrade proposals, and conduct post-mortem analyses after upgrades ensuring continuous improvement across development cycles serving global users.[1]
Governance Models for Program Control in Solana
Governance frameworks for the upgradability of Solana smart contracts range from simple multi-signature wallets to sophisticated token-weighted voting systems enabling decentralized control. Popular implementations include Squads multi-sig requiring multiple team approvals, Realm governance providing on-chain voting with configurable thresholds, and custom governance programs implementing project-specific rules. Effective governance balances security, operational efficiency, and community participation through mechanisms like proposal submission periods, voting durations, execution delays, and emergency procedures for critical fixes across protocol lifecycles.
Auditing and Monitoring Upgradeable Programs
Continuous monitoring of the upgradability of Solana smart contracts involves tracking upgrade authority changes, monitoring program modifications, and alerting users about pending updates. Tools like Solana Beach and Solscan enable users to verify current upgrade authority status. Professional auditing before upgrades identifies vulnerabilities, validates business logic, and ensures gas optimization. Post-deployment monitoring detects anomalous behavior, tracks usage metrics, and identifies potential exploits enabling rapid response. This comprehensive oversight protects protocols managing billions in total value locked across USA, UK, UAE, and Canadian markets.
When to Freeze or Make a Program Immutable
Strategic finalization of the upgradability of Solana smart contracts occurs when protocols achieve feature completeness, undergo comprehensive security auditing, demonstrate production stability, and build sufficient community trust. Core infrastructure components like token standards, oracle feeds, and foundational protocols typically finalize early prioritizing security over flexibility. Application-layer protocols may maintain upgradeability longer enabling feature iterations and market adaptations. The decision balances innovation velocity against security guarantees, with transparent communication and gradual transition building user confidence across development phases.
Future of Program Upgradability in the Solana Ecosystem
The evolution of the upgradability of Solana smart contracts continues advancing with improved governance tools, enhanced security mechanisms, and sophisticated authority management systems. Emerging patterns include gradual finalization strategies where peripheral modules remain upgradeable while core logic becomes immutable, transparent upgrade proposals with mandatory review periods, and insurance protocols covering upgrade-related risks. The Solana ecosystem is developing standardized governance frameworks, automated security verification, and user-friendly interfaces enabling broader community participation in program control decisions.
Our eight years of blockchain development experience across USA, UK, UAE, and Canada demonstrates that proper program upgradability management is essential for sustainable protocol development. As Solana’s ecosystem matures, best practices around authority management, governance structures, security auditing, and community transparency will become increasingly standardized. The convergence of technical capabilities, governance innovations, and security improvements will enable the upgradability of Solana smart contracts to balance flexibility with security, supporting the next generation of decentralized applications serving global markets with institutional-grade reliability and user protection.
Frequently Asked Questions
The upgradability of Solana smart contracts differs fundamentally from Ethereum through the BPF Upgradeable Loader mechanism that separates program logic from program data accounts. Solana programs deployed with this loader can be modified by authorized upgrade authorities without changing the program’s address. Unlike Ethereum’s proxy patterns requiring complex contract architectures, Solana’s native upgradeability enables direct bytecode replacement when proper authority is maintained. This design allows developers across USA, UK, UAE, and Canada to fix bugs, add features, and improve performance while preserving program addresses and existing integrations seamlessly.
Upgrade authority in the upgradability of Solana smart contracts represents a specific account with exclusive permissions to modify program bytecode through the BPF Upgradeable Loader. When deploying upgradeable programs, developers designate an upgrade authority keypair that must sign all future program modifications. This authority can be transferred to different accounts, revoked entirely to make programs immutable, or assigned to multi-signature wallets and governance systems. The upgrade authority model provides flexible control enabling individual developers to manage early-stage programs while transitioning to decentralized governance as projects mature across global blockchain ecosystems.
Yes, the upgradability of Solana smart contracts can be permanently revoked by finalizing programs, making them immutable like traditional blockchain smart contracts. Program authorities execute the finalize command through Solana CLI or programmatic instructions, removing upgrade authority completely. Once finalized, no entity can modify the program bytecode regardless of circumstances, providing maximum security guarantees and trust for users. Major DeFi protocols often finalize core programs after extensive auditing and testing, while maintaining upgradeability for peripheral modules. This flexibility allows projects to balance innovation velocity with security requirements appropriate for their development stage and risk profile.
Security risks in the upgradability of Solana smart contracts include unauthorized upgrades if private keys are compromised, malicious code injection by corrupted authorities, and rug pulls where developers upgrade programs to drain user funds. Centralized upgrade authority creates single points of failure vulnerable to hacking, social engineering, or insider threats. Users across USA, UK, UAE, and Canada must verify upgrade authority status before depositing significant value. Best practices include multi-signature control, time-locked upgrades enabling user exits, transparent governance processes, and gradual transition to immutability after protocols mature, balancing flexibility with security.
Upgrading through the upgradability of Solana smart contracts involves compiling updated program code, deploying new bytecode to buffer accounts, and executing upgrade instructions signed by authorized upgrade authority. Developers use Solana CLI commands or SDK functions to write new program data, verify compilation, and atomically replace existing bytecode. The process requires sufficient SOL balance for transaction fees and buffer account rent, proper authority credentials, and comprehensive testing on devnet before mainnet deployment. Professional development teams follow formal change management procedures including code reviews, security audits, and staged rollouts minimizing risks across production environments.
Effective governance for the upgradability of Solana smart contracts employs multi-signature wallets, time-locked proposals, and token-weighted voting systems providing decentralized control over program modifications. Popular models include Squads multi-sig requiring multiple team members to approve upgrades, Realm governance enabling token holder voting on program changes, and custom governance programs implementing project-specific rules. Leading protocols often combine multiple mechanisms like 48-hour time locks allowing user review before execution, emergency multi-sig for critical fixes, and full community votes for major changes. These governance frameworks balance security, efficiency, and decentralization appropriate for protocol maturity stages.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







