Key Takeaways
- Proof of Activity combines Proof of Work mining with Proof of Stake validation for a two-phase consensus process
- PoA reduces energy consumption by 40 to 60 percent compared to pure Proof of Work systems
- The hybrid model protects against 51 percent attacks by requiring both computational power and stake ownership
- Block rewards are split between miners and validators, promoting fair distribution across network participants
- Real world applications include DeFi platforms, supply chain tracking, and digital identity verification systems
- Implementation requires careful consideration of network parameters, validator selection algorithms, and reward structures
Blockchain technology keeps changing. New ways to reach agreement among network participants continue to emerge. Among these methods, Proof of Activity stands out as a practical solution that addresses limitations found in older consensus mechanisms. If you have worked with Proof of Work or Proof of Stake systems, you probably noticed their individual shortcomings. Proof of Activity was designed to fix those problems.
This article explains what Proof of Activity actually is, how it functions from an execution standpoint, and what developers need to consider when building on PoA networks. We will cover the technical details without unnecessary complexity and provide practical insights based on real implementation experience.
What is Proof of Activity in Blockchain?
Proof of Activity is a hybrid consensus mechanism. It takes the mining component from Proof of Work and combines it with the validation component from Proof of Stake. The result is a system where blocks are created through computational work but confirmed through stake based validation.
The concept was introduced in 2014 by researchers including Iddo Bentov, Charles Lee (creator of Litecoin), Alex Mizrahi, and Meni Rosenfeld. Their paper outlined a method to improve upon the security guarantees of pure PoW while reducing its energy demands. The basic idea was straightforward. Miners do the initial work of creating block headers. Then stakeholders step in to validate and finalize those blocks.
Think of it like a two step verification process for your bank account. The first step might be entering your password. The second step could be confirming through your phone. Neither step alone provides complete security. Together they create a stronger barrier against unauthorized access. Proof of Activity works on a similar principle for blockchain transactions.
At Nadcab Labs, our team has spent over 8 years implementing various consensus mechanisms for clients across industries. We have seen firsthand how PoA addresses the specific pain points that pure PoW and pure PoS systems create. The hybrid approach is not just theoretical. It produces measurable improvements in network performance and security metrics.
How Does Proof of Activity Function?
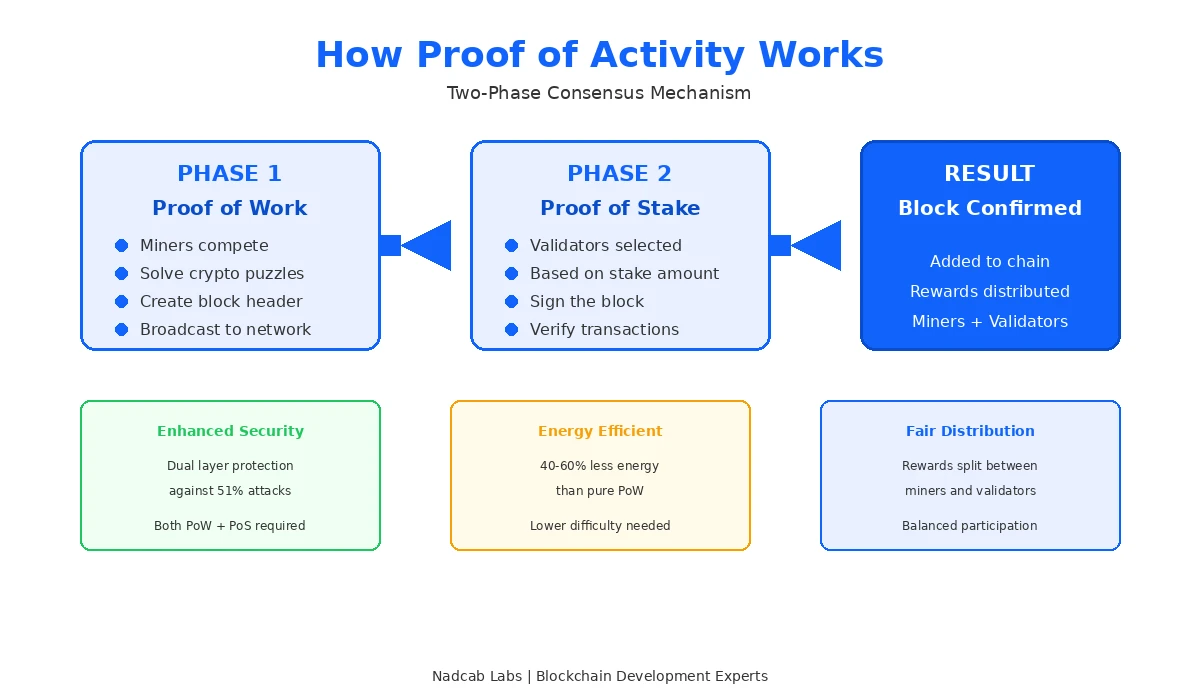
Understanding how PoA works requires breaking down its two distinct phases. Each phase serves a specific purpose in the overall consensus process.
Phase One: The Mining Stage
The process begins with miners competing to solve cryptographic puzzles. This part resembles traditional Bitcoin mining. Miners use specialized hardware to perform millions of calculations per second. They are searching for a hash value that meets the network difficulty requirements.
However, here is where PoA differs from standard PoW. Miners do not create complete blocks. They only generate block headers. These headers contain basic information like the previous block hash, a timestamp, and a nonce value. The header is essentially a template for a block rather than a finished product.
Once a miner finds a valid header, they broadcast it to the network. This header serves as a seed for the next phase. The miner has done their job at this point. They have provided proof that computational work was performed.
Phase Two: The Validation Stage
The block header now enters the Proof of Stake phase. The network uses the header data to randomly select validators from the pool of stakeholders. The selection process is deterministic. Given the same header data, any node can calculate which validators should sign the block.
Selected validators check the header and the pending transactions. If everything looks correct, they add their digital signatures. The number of required signatures varies by implementation. Some networks require three validators. Others might require five or more.
The last validator to sign typically adds the actual transaction data to complete the block. This completed block is then broadcast to the network. Nodes verify that both the mining work and validator signatures are valid before adding the block to their local copy of the blockchain.
This two phase approach means that attacking a PoA network requires controlling both significant mining power and a large stake. Understanding related concepts like orphan blocks in blockchain helps developers anticipate edge cases that might occur when validators go offline during the signing process.
The Proof of Activity Block Lifecycle
Every block in a PoA network goes through a defined lifecycle. Understanding this sequence helps developers build applications that interact correctly with the network at each stage.
| Stage | Actor | Action | Duration |
|---|---|---|---|
| Header Creation | Miner | Solve cryptographic puzzle and broadcast header | Variable based on difficulty |
| Validator Selection | Network Protocol | Deterministically choose validators from stake pool | Milliseconds |
| Signature Collection | Validators | Review header and add digital signatures | 1 to 5 seconds |
| Block Completion | Final Validator | Append transaction data and broadcast full block | Under 1 second |
| Network Propagation | All Nodes | Verify and add block to local chain | Network dependent |
| Reward Distribution | Protocol | Split rewards between miner and validators | Immediate |
The lifecycle shows why PoA achieves both security and reasonable transaction times. The mining phase provides the initial security barrier. The validation phase adds a second layer while keeping processing efficient. Networks that need even faster processing might consider state channels as a complementary scaling solution.
Technical Architecture for PoA Implementation
Building a PoA network requires careful architecture decisions. The choices made at the design stage affect everything from network security to validator economics.
Validator Selection Algorithm
The method for choosing validators is critical. Most implementations use a pseudo random selection weighted by stake amount. The randomness comes from the block header data, which cannot be predicted before the miner creates it. This prevents validators from knowing in advance when they will be selected.
A common approach uses the follow the satoshi method. Imagine all coins in the network laid out in a line. The algorithm picks random points along this line. Whoever owns the coin at each point becomes a validator. Larger stakeholders have more coins in the line, giving them proportionally higher selection chances.
The selection must be verifiable by any node. Given the same inputs, every node should calculate the same validator set. This determinism prevents disputes about who should have signed a particular block.
Network Parameter Configuration
Several parameters need configuration when deploying a PoA network. The number of required validator signatures affects both security and block time. More signatures mean better security but longer waits for block completion.
The timeout period for validator signatures also matters. If a selected validator is offline, the network needs a fallback. Some implementations select backup validators. Others simply wait for the next block attempt if signatures time out.
Mining difficulty adjustment follows similar principles to pure PoW networks. The network monitors block times and adjusts difficulty to maintain a target interval. However, PoA networks can use lower difficulty targets since validators provide additional security.
Node synchronization presents unique challenges in PoA networks. New nodes must verify both the mining work and validator signatures for every historical block. This can make initial sync slower than pure PoW or PoS networks.
Proof of Activity Compared to Other Consensus Mechanisms
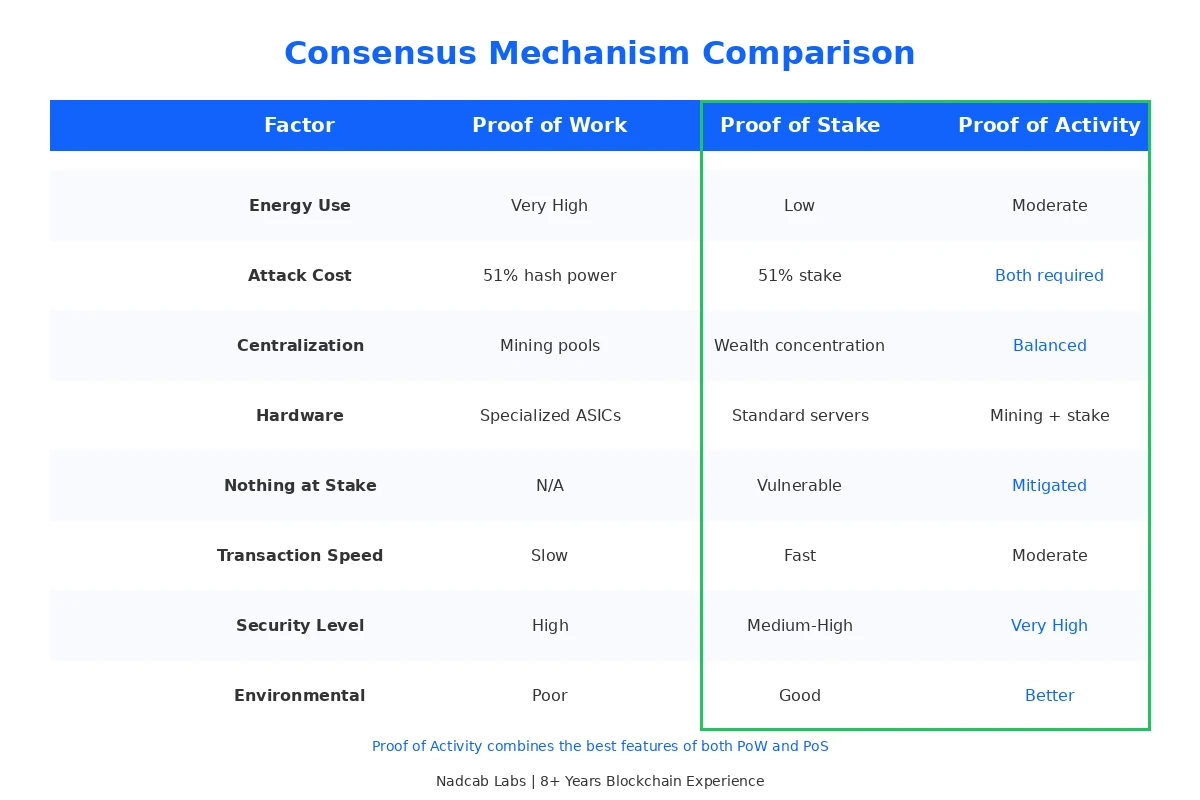
Choosing the right consensus mechanism depends on your specific requirements. This comparison helps clarify where PoA fits among the alternatives.
| Factor | Proof of Work | Proof of Stake | Proof of Activity |
|---|---|---|---|
| Energy Consumption | Very High | Low | Moderate |
| Attack Resistance | 51% hash power | 51% stake | Both required |
| Decentralization | Mining pool risk | Wealth concentration risk | Balanced distribution |
| Transaction Finality | Probabilistic | Often deterministic | Probabilistic with faster confidence |
| Hardware Requirements | Specialized ASICs | Standard servers | Mining hardware plus stake |
| Nothing at Stake Problem | Not applicable | Vulnerable | Mitigated |
| Long Range Attacks | Not applicable | Vulnerable | Partially mitigated |
The comparison shows that PoA occupies a middle ground. It does not eliminate all weaknesses from either parent mechanism. Instead, it reduces the severity of problems from both. For projects prioritizing security over pure efficiency, this tradeoff often makes sense. Related consensus mechanisms like Delegated Proof of Stake take different approaches to similar problems.
Security Analysis: Why PoA Resists Attacks
Security is the primary reason teams choose PoA over simpler alternatives. The dual requirement for mining power and stake creates meaningful barriers against common attack vectors.
Protection Against 51 Percent Attacks
In a pure PoW network, controlling 51 percent of hash power lets an attacker rewrite transaction history. They can create an alternate chain faster than honest miners and eventually overtake the main chain.
PoA makes this attack substantially harder. An attacker would need majority hash power to consistently create block headers. They would also need significant stake to frequently appear in validator sets. Controlling both simultaneously requires a much larger investment than attacking either system alone.
The math works in defenders favor. If the attacker controls 51 percent of hash power and 30 percent of stake, they can create headers reliably. But they only appear in about 30 percent of validator selections. Most of their headers would need honest validators to complete blocks. This creates natural resistance to chain manipulation.
Mitigating the Nothing at Stake Problem
Pure PoS systems face the nothing at stake dilemma. Validators have no cost for signing multiple competing chains. If a fork occurs, rational validators sign all branches to maximize potential rewards. This behavior makes reaching consensus difficult.
PoA addresses this through the PoW component. Creating competing chains requires mining alternate headers. This costs real computational resources. A validator cannot simply sign multiple branches without a miner providing alternative headers for each branch. The energy cost of mining provides economic finality that pure stake lacks.
Defending Against Long Range Attacks
Long range attacks exploit historical stake distributions. An attacker acquires keys that held stake in the past. They then rewrite history from that point forward, creating an alternate chain where their old stake validates their fraudulent blocks.
PoA partially mitigates this threat. Rewriting history requires mining all headers from the branch point forward. This represents substantial computational work that grows linearly with the depth of the rewrite. While not impossible, the attack becomes expensive enough to deter most adversaries.
Understanding these security properties helps when evaluating blockchain projects. Projects that need maximum security against well-funded attackers benefit from PoA. Those prioritizing speed above all else might prefer mechanisms like Plasma or other layer 2 solutions.
Build Secure Blockchain Solutions with PoA
Ready to implement Proof of Activity for your blockchain project? Our team brings 8+ years of consensus mechanism expertise to deliver secure, scalable networks tailored to your requirements.
How Block Rewards Work in Proof of Activity
Block rewards incentivize participation in any consensus mechanism. PoA splits rewards between miners and validators, creating a dual incentive structure.
The Reward Split Model
Most PoA implementations divide block rewards into portions. The miner who creates the valid header receives one share. Each validator who signs the block receives another share. The exact percentages vary by network configuration.
A typical distribution might give 50 percent to the miner and split the remaining 50 percent among validators. With five validators, each would receive 10 percent of the block reward. This creates clear economic incentives for both roles.
Transaction fees also need distribution. Some networks include fees in the same split as block rewards. Others direct all fees to the miner or the final validator. The choice affects which role earns more during periods of high network activity.
Economic Implications for Participants
The dual reward structure creates interesting market dynamics. Mining profitability depends on hardware costs and electricity prices. Validation profitability depends on the amount staked and token price. These factors move somewhat independently.
Participants must decide how to allocate capital. Investing in mining equipment offers one return profile. Purchasing tokens for staking offers another. Some participants do both, balancing their exposure to each reward stream.
The economic model of Proof of Activity promotes long term holding. Validators earn returns on their staked tokens. This encourages accumulation rather than immediate selling, potentially supporting token price stability.
Development Considerations for PoA Networks
Building applications on PoA networks requires understanding their specific characteristics. Developers familiar with pure PoW or PoS systems may need to adjust their approaches.
Transaction Confirmation Strategy
Block times in PoA networks tend to be longer than pure PoS but shorter than Bitcoin style PoW. The validation phase adds latency beyond mining. Applications should account for this when designing user experiences.
Confirmation depth recommendations also differ. The dual security layer means fewer confirmations may provide equivalent safety compared to single mechanism chains. However, this depends heavily on the specific network parameters and threat model.
Smart contract developers should consider the validator selection timing. Contracts that depend on block proposer identity may behave unexpectedly. The miner creates the header but validators complete the block. Which actor should the contract consider as the block creator?
Handling Validator Availability
Selected validators might be offline when chosen. Applications must handle delayed block completion gracefully. User interfaces should indicate that a transaction is pending validation, not just mining.
Validator uptime requirements create operational demands. Stakers cannot simply lock tokens and walk away. They need infrastructure to respond to signature requests promptly. Many choose to run validators themselves or delegate to professional operators.
These operational requirements parallel challenges in other consensus systems. Projects implementing Proof of Elapsed Time face similar infrastructure decisions around validator availability.
Real World Applications of Proof of Activity
PoA has found adoption across multiple industry sectors. Each application leverages the mechanism’s particular strengths.
Decentralized Finance Platforms
DeFi applications handle significant value transfers. Security cannot be compromised. PoA provides stronger guarantees than pure PoS for preventing double spend attacks. Lending protocols, decentralized exchanges, and derivative platforms benefit from this enhanced security.
The moderate energy cost also matters for DeFi. Pure PoW would make transaction fees prohibitively expensive for frequent trading. PoA balances security with economic accessibility.
Supply Chain Management
Supply chain networks track goods across multiple parties. Each party has incentive to record transactions honestly but may not trust others. PoA creates alignment through the stake requirement while preventing any single party from controlling the chain through mining.
The hybrid model works well when participants include both resource rich organizations (who can mine) and smaller operators (who can stake). Neither group dominates consensus.
Digital Identity Systems
Identity verification requires high security standards. Compromised identity records cause lasting damage. PoA provides the security layer needed for sensitive personal data management.
Identity systems also need decentralization. No single entity should control the identity database. PoA prevents both mining centralization and stake centralization from enabling such control. For teams facing common implementation hurdles, understanding blockchain adoption challenges helps anticipate and address integration difficulties.
Step by Step Implementation Guide
Implementing PoA requires methodical planning. The following steps outline a practical path from concept to deployment.
| Step | Activity | Key Decisions | Typical Duration |
|---|---|---|---|
| 1. Requirements Analysis | Define security needs, throughput targets, decentralization goals | Target TPS, validator count, reward structure | 2 to 4 weeks |
| 2. Protocol Design | Specify validator selection algorithm and signature requirements | Selection method, timeout handling, fallback procedures | 4 to 6 weeks |
| 3. Core Development | Build consensus module, integrate with blockchain client | Programming language, existing codebase modifications | 8 to 12 weeks |
| 4. Testing | Unit tests, integration tests, simulated attack scenarios | Test coverage targets, attack simulation scope | 4 to 8 weeks |
| 5. Testnet Deployment | Launch public testnet, recruit validators, stress test | Incentive programs for testers, bug bounty amounts | 6 to 10 weeks |
| 6. Security Audit | External review of consensus code and cryptographic implementation | Audit firm selection, scope definition | 4 to 6 weeks |
| 7. Mainnet Launch | Deploy production network, monitor for issues | Genesis block parameters, initial validator set | 2 to 4 weeks |
At Nadcab Labs, our blockchain development services cover every phase of this implementation process. We have guided dozens of projects through PoA deployments, refining our methodology with each engagement.
Common Mistakes When Implementing PoA
Learning from others saves time and resources. These mistakes appear repeatedly in PoA projects.
Insufficient Validator Pool Size
Some projects launch with too few potential validators. When selected validators are offline, blocks cannot be completed. The network stalls or experiences long delays. Planning for validator availability from day one prevents this issue.
Imbalanced Reward Structure
If mining rewards far exceed staking rewards, validators lose incentive to participate. The reverse causes miners to abandon the network. Either imbalance threatens network security. Economic modeling before launch helps set appropriate ratios.
Ignoring Edge Cases in Validator Selection
What happens when the same address is selected multiple times? What if no addresses have sufficient stake? Edge cases in the selection algorithm can create exploits or network failures. Thorough testing of boundary conditions prevents surprises.
Understanding how other blockchain mechanisms handle similar challenges provides useful perspective. Concepts like atomicity in blockchain transactions inform how PoA implementations should handle partially completed blocks.
The Future of Proof of Activity
Consensus mechanism research continues to advance. PoA itself may evolve or inspire new hybrid approaches.
One direction involves integrating additional factors into validator selection. Reputation systems could weight selection by past validator behavior. Storage proof could add another dimension beyond computation and stake. These extensions would create even more robust hybrid mechanisms.
Energy efficiency improvements in mining hardware also affect PoA economics. As mining becomes cheaper, the balance between PoW and PoS components may shift. Networks might adjust their parameters to maintain optimal security ratios.
Layer 2 solutions like sidechains can work alongside PoA base layers. The secure foundation of PoA supports faster processing on secondary layers. This combination may become a common architecture pattern.
New blockchain platforms continue entering the market. Some may adopt PoA as their consensus mechanism. Others may use modified versions that suit specific use cases. The core idea of combining work and stake will likely influence blockchain design for years to come.
Why Nadcab Labs for Your PoA Implementation
Choosing the right development partner matters as much as choosing the right consensus mechanism. Nadcab Labs brings specific advantages to PoA projects.
Our team has worked with blockchain technology since its early days. Over 8 years of hands on experience means we have seen consensus mechanisms succeed and fail. We know which design choices lead to robust networks and which create problems down the road.
We understand that PoA is not always the right choice. Sometimes pure PoS suffices. Sometimes specialized mechanisms like newer blockchain platforms offer better fits. Our role is to assess your requirements and recommend the optimal solution, not to push any particular technology.
For projects where PoA makes sense, we provide end to end support. From initial protocol design through mainnet launch and beyond, our team handles technical implementation while you focus on building your application.
Our development process emphasizes thorough testing and security review. Consensus mechanisms protect significant value. Cutting corners creates unacceptable risk. We build systems that withstand real world attacks, not just theoretical ones.
Tools for Monitoring PoA Networks
Running a PoA network requires ongoing monitoring. Several metrics indicate network health.
Block time variance shows whether validators respond promptly. High variance suggests validator availability problems. Consistent times indicate a well functioning validator pool.
Hash rate distribution reveals mining centralization trends. If a few mining pools dominate, the PoW security assumptions weaken. Healthy networks show distributed mining participation.
Stake distribution among validators matters equally. Excessive concentration undermines the PoS security layer. Monitoring tools should flag concerning distribution patterns.
Block explorers like Bitcoin blockchain explorer implementations can be adapted for PoA networks. They need additional displays for validator signatures and stake information beyond standard PoW explorer features.
Conclusion
Proof of Activity represents a practical solution to real problems in blockchain consensus. It does not promise perfection. It delivers measurable improvements in security and efficiency through a thoughtful combination of proven mechanisms.
For projects that need strong security without pure PoW energy costs, PoA deserves serious consideration. The dual barrier against attacks provides meaningful protection for valuable networks.
Implementation requires expertise in both PoW and PoS systems. The hybrid nature creates complexity that inexperienced teams may underestimate. Working with developers who have successfully deployed PoA networks reduces risk significantly.
Whether you are exploring PoA for a new project or evaluating it against alternatives like Avalanche blockchain solutions, understanding the mechanism’s strengths and limitations enables better decisions. The blockchain space offers many consensus options. Choosing wisely requires looking beyond marketing claims to technical reality.
Frequently Asked Questions
Proof of Activity combines mining with stake based validation while Proof of Work relies solely on computational power for block creation. In PoA, miners create block headers through computational work, but validators selected based on their token holdings must sign the blocks before they become valid. This two phase approach means attackers need both significant hash power and substantial stake to compromise the network. The hybrid model reduces energy consumption compared to pure PoW since mining difficulty can be lower when validators provide additional security. Block rewards are split between miners and validators rather than going entirely to miners.
Validator selection in PoA uses a deterministic process based on block header data that miners produce. Once a valid header is broadcast, the network applies an algorithm to identify which stakeholders should validate that block. The selection typically weights probability by stake amount so larger stakeholders get chosen more often. The randomness from the unpredictable header prevents validators from knowing their selection in advance. Multiple validators usually must sign each block with common implementations requiring three to five signatures. If a selected validator is offline, protocols either wait for timeout then select alternatives or abandon that block attempt.
Proof of Activity typically reduces energy consumption by 40 to 60 percent compared to equivalent pure Proof of Work networks. This reduction comes from the ability to set lower mining difficulty targets since validator signatures provide additional security guarantees. Miners still perform computational work but the network does not need the same difficulty levels that pure PoW requires for security. The energy savings make PoA more environmentally sustainable while maintaining strong attack resistance. However, PoA still consumes more energy than pure Proof of Stake systems since mining remains part of the consensus process. The tradeoff is improved security characteristics.
Proof of Activity significantly increases the difficulty and cost of 51 percent attacks compared to single mechanism chains. An attacker would need to control majority hash power to consistently create valid headers and also hold substantial stake to appear frequently in validator selections. Controlling only one resource is insufficient since both phases must be compromised. For example, an attacker with 60 percent hash power but only 10 percent stake would create most headers but struggle to validate them. The dual requirement creates multiplicative rather than additive security. However, no consensus mechanism completely eliminates attack risk if adversaries have unlimited resources.
Block rewards in Proof of Activity are split between miners and validators according to network configured ratios. A common distribution gives 50 percent to the miner who created the valid header and divides the remaining 50 percent among validating stakeholders. With five validators this means each validator receives 10 percent of the block reward. Transaction fees may follow the same split or be handled differently based on implementation. This shared reward structure incentivizes participation in both mining and staking. Participants can choose whether to invest in mining hardware or purchase tokens for staking based on expected returns from each activity.
Proof of Activity has found adoption in decentralized finance platforms where security against double spending is paramount for handling valuable transactions. Supply chain management networks use PoA because the hybrid model prevents any single participant from dominating consensus while ensuring honest record keeping. Digital identity verification systems benefit from the strong security guarantees PoA provides for sensitive personal data. Healthcare data exchange networks have explored PoA for protecting patient records while enabling authorized access. Financial settlement systems find value in the mechanism’s resistance to long range attacks that could reverse historical transactions. Each industry values the balanced security efficiency tradeoff PoA offers.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.






