Key Takeaways
- Hot Wallets in Blockchain are internet-connected digital wallets that store cryptocurrency private keys online for instant access and transactions
- They offer unmatched convenience for daily crypto trading, DeFi interactions, and NFT management but come with higher security risks
- Understanding the balance between security and convenience is crucial for safe crypto management in 2026
- Only store active trading amounts in hot wallets; keep long-term holdings in cold storage
- Modern hot wallets now feature MPC, biometric authentication, and AI-powered security for enhanced protection
1. Introduction to Hot Wallets in Blockchain
In the rapidly evolving digital asset ecosystem, Hot Wallets in Blockchain have emerged as the cornerstone infrastructure enabling seamless cryptocurrency transactions and decentralized application interactions. As blockchain technology continues its mainstream adoption trajectory, understanding hot wallet mechanisms becomes increasingly critical for both individual users and enterprise operations.
The blockchain landscape in 2026 has witnessed unprecedented growth across decentralized finance platforms, non-fungible token marketplaces, and Web3 applications. This expansion has positioned Hot Wallets in Blockchain as indispensable tools that bridge the gap between user convenience and blockchain accessibility. With over 580 million cryptocurrency users globally and daily transaction volumes exceeding $100 billion, hot wallets have become the primary gateway through which millions interact with digital assets.
As a blockchain development agency with over 8 years of specialized experience in wallet infrastructure and security implementations, we have witnessed firsthand the transformation of hot wallet technology from basic key management systems to sophisticated multi-chain platforms with enterprise-grade security features. Our team has deployed wallet solutions handling billions in cumulative transaction value, giving us unique insights into the practical challenges and solutions in this domain.
Today’s Hot Wallets in Blockchain serve multiple critical functions: they facilitate instant peer-to-peer transfers, enable smart contract interactions, provide access to decentralized exchanges, support NFT trading, and serve as digital identity authenticators across Web3 platforms. The growing adoption in DeFi protocols, where users need immediate access to funds for yield farming, lending, and staking, has made hot wallets essential infrastructure rather than optional tools.
2. What Is a Hot Wallet in Blockchain?
Quick Definition
Hot Wallets in Blockchain are software-based cryptocurrency storage solutions that maintain constant connectivity to the internet and blockchain networks. They store private keys in an online environment, enabling users to quickly send, receive, and manage digital assets while interacting with decentralized applications and services.
Unlike traditional banking systems where financial institutions control your funds, Hot Wallets in Blockchain operate on a fundamentally different paradigm. In blockchain technology, possession of private cryptographic keys equates to ownership of assets. Hot wallets maintain these keys in an internet-connected environment, allowing for immediate transaction signing and blockchain interaction without the need for external hardware devices.
The “hot” designation specifically refers to the crypto wallet‘s online connectivity status. This architectural choice prioritizes accessibility and usability over maximum security, making hot wallets ideal for active trading, daily transactions, and frequent DeFi interactions. Think of Hot Wallets in Blockchain as your everyday spending account, analogous to keeping cash in your physical wallet rather than in a bank vault.
The fundamental difference between hot wallets and traditional financial tools lies in self-custody. With Hot Wallets in Blockchain, users maintain complete control over their private keys and, consequently, their assets. There are no intermediaries, no account freezes, and no geographic restrictions. This sovereignty comes with the responsibility of securing your own keys, understanding that “not your keys, not your coins” is the foundational principle of blockchain custody.
3. How Hot Wallets Work in Blockchain
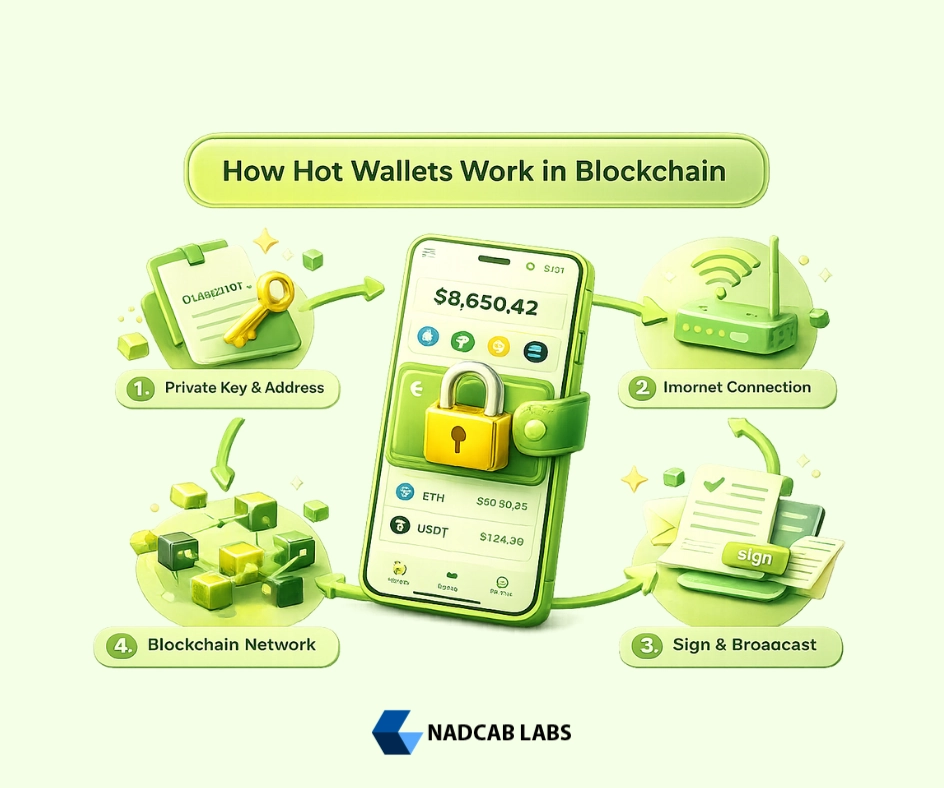
Understanding the operational mechanics of Hot Wallets in Blockchain requires grasping a few fundamental cryptographic concepts. At their core, hot wallets function as secure key management systems combined with blockchain communication interfaces. The process involves four primary components working in harmony to enable cryptocurrency transactions.
Private Keys and Public Addresses
Every Hot Wallet in Blockchain generates a pair of cryptographically linked keys through advanced mathematical algorithms. The private key is essentially a 256-bit number (typically represented as a 64-character hexadecimal string or a 12-24 word seed phrase) that serves as your master password to the blockchain wallet . This key must remain absolutely confidential, as anyone possessing it can control the associated funds.
The public key, derived mathematically from the private key through one-way cryptographic functions, creates your blockchain address where others can send you cryptocurrency. The genius of this system is that while the public address can be freely shared, it’s computationally impossible to reverse-engineer the private key from it. Hot Wallets in Blockchain store these private keys in encrypted form within their software environment, protected by password encryption and, in modern implementations, hardware security modules or secure enclaves.
Internet Connectivity and Transaction Signing
The defining characteristic of Hot Wallets in Blockchain is their persistent internet connectivity, which enables real-time blockchain synchronization and immediate transaction broadcasting. When you initiate a transaction, the wallet software creates a transaction message containing the recipient address, amount, and other metadata. This message is then cryptographically signed using your private key, creating a digital signature that proves ownership without revealing the key itself.
The signed transaction is broadcast to the blockchain network through connected nodes. These nodes validate the transaction by verifying the digital signature against the public key, checking for sufficient funds, and ensuring compliance with blockchain protocol rules. Once validated, the transaction enters the mempool awaiting inclusion in a block. Hot Wallets in Blockchain maintain connections with multiple nodes to ensure reliable transaction broadcasting and to receive real-time updates about incoming transactions and balance changes.
Blockchain Node Interaction
Hot Wallets in Blockchain don’t typically run full blockchain nodes due to storage and computational constraints. Instead, they connect to remote nodes via APIs or run lightweight SPV (Simplified Payment Verification) clients. These connections allow wallets to query blockchain state, check transaction status, and retrieve account balances without downloading entire blockchain histories. Modern hot wallets often use multiple node providers for redundancy and censorship resistance, ensuring service availability even if individual providers experience downtime.
4. Key Components of a Hot Wallet Architecture
Modern Hot Wallets in Blockchain comprise sophisticated architectures with multiple layers working together to balance security, usability, and functionality. Understanding these components helps users appreciate the complexity beneath seemingly simple interfaces and makes them better equipped to evaluate wallet security.
| Component Layer | Primary Function | Security Considerations |
|---|---|---|
| User Interface Layer | Transaction initiation, balance display, settings management | Input validation, secure rendering, phishing prevention |
| Application Logic Layer | Transaction construction, fee calculation, validation rules | Business logic security, rate limiting, anomaly detection |
| Key Management Layer | Private key generation, storage, and usage | Encryption at rest, secure key derivation, access control |
| Blockchain Integration Layer | Node communication, transaction broadcasting, state queries | Node authentication, TLS encryption, DDoS protection |
| Security Module Layer | Threat detection, authentication, authorization | Multi-factor authentication, biometrics, device binding |
Wallet Interface Platforms
Hot Wallets in Blockchain deploy across multiple platform types, each optimized for specific use cases. Mobile wallets leverage smartphone hardware features like secure enclaves (iOS Secure Enclave, Android StrongBox) for key storage, biometric authentication for access control, and camera functionality for QR code scanning. Web-based wallets operate as browser extensions or web applications, utilizing browser security features and local storage encryption while maintaining cross-device accessibility.
Desktop applications provide enhanced security through operating system-level protections and more robust encryption implementations. Each platform presents unique security trade-offs that users must understand when selecting Hot Wallets in Blockchain for their needs.
5. Types of Hot Wallets in Blockchain
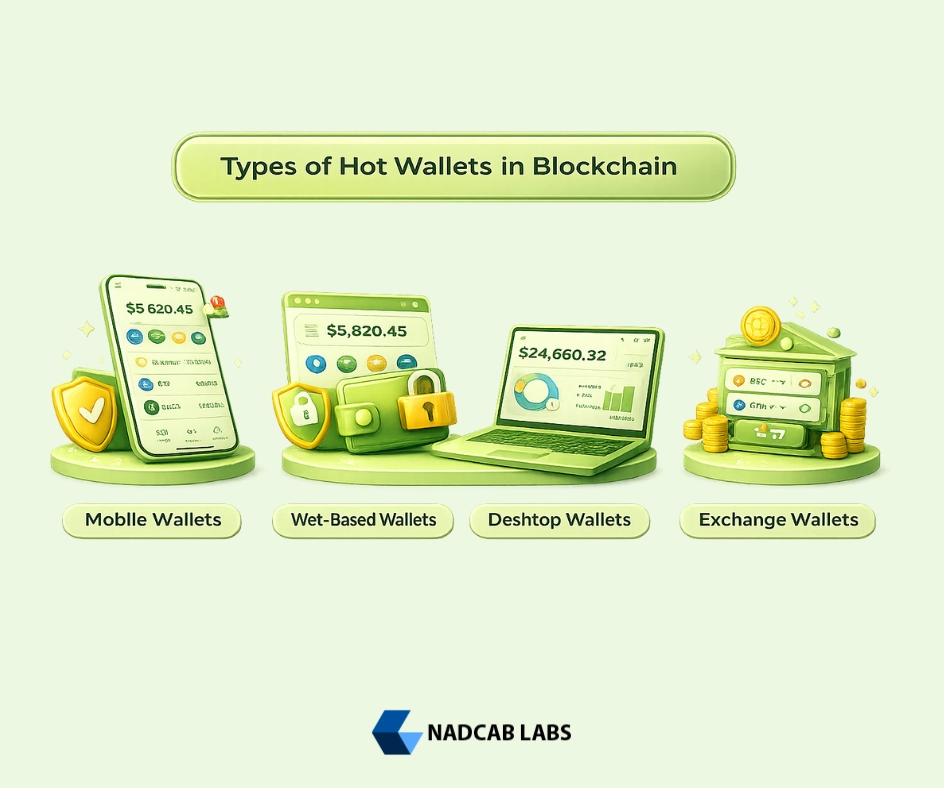
The diverse ecosystem of Hot Wallets in Blockchain offers specialized solutions for different user needs, security requirements, and use cases. Selecting the appropriate wallet type requires understanding these distinctions and aligning them with your specific requirements.
5.1 Mobile Hot Wallets
Mobile Hot Wallets in Blockchain represent the most widely adopted category, with applications like Trust Wallet, MetaMask Mobile, and Coinbase Wallet commanding millions of active users. These wallets leverage smartphone ubiquity to provide cryptocurrency access anywhere, anytime. Advanced implementations utilize hardware-backed keystores on iOS and Android, storing encrypted private keys in dedicated secure hardware that’s isolated from the main operating system.
The convenience factor of mobile hot wallets is unparalleled for everyday transactions. Users can scan QR codes for instant payments, interact with mobile-optimized DeFi protocols, and manage NFT collections from their pockets. However, the always-connected nature and exposure to mobile malware, phishing applications, and SIM-swapping attacks require users to implement additional security measures including app-based authentication and backup strategies.
5.2 Web-Based Hot Wallets
Browser extension Hot Wallets in Blockchain like MetaMask, Phantom, and Rabby have become the standard interface for Web3 wallet interaction. These wallets inject blockchain connectivity into web browsers, allowing users to interact with decentralized applications without leaving their browsing environment. The seamless integration enables one-click connection to DeFi protocols, NFT marketplaces, and blockchain games.
Web wallets store encrypted key material in browser local storage, relying on the browser’s security model for protection. While convenient for frequent dApp users, they’re vulnerable to browser-based attacks including malicious extensions, compromised websites, and clipboard hijacking. Best practices include using dedicated browsers for crypto activities and regularly auditing connected applications and token approvals.
5.3 Desktop Hot Wallets
Desktop applications provide enhanced security compared to mobile and web alternatives, though with reduced mobility. Hot Wallets in Blockchain like Exodus, Electrum, and Atomic Wallet offer full-featured interfaces with advanced capabilities including portfolio tracking, built-in exchanges, and detailed transaction histories. Desktop implementations can leverage more robust encryption algorithms and implement additional security layers unavailable in browser environments.
These wallets suit users managing larger portfolios who require advanced features like custom transaction fees, coin control, and detailed analytics. The desktop environment allows for better malware protection through antivirus software and operating system security features, though users must still maintain proper computer hygiene and avoid downloading suspicious software.
5.4 Exchange-Integrated Hot Wallets
Exchange-provided Hot Wallets in Blockchain represent a custodial model where private keys are managed by the exchange rather than individual users. Platforms like Binance, Coinbase, and Kraken offer integrated wallet services with seamless trading functionality, instant liquidity access, and comprehensive security teams managing backend infrastructure.
While convenient for active traders, these wallets contradict the self-custody principle fundamental to blockchain philosophy. Users don’t control private keys, making them vulnerable to exchange hacks, regulatory seizures, and platform insolvency. The appropriate use case for exchange wallets is temporary storage during active trading, not long-term holdings. As the crypto community emphasizes, “not your keys, not your coins” remains valid advice regardless of exchange reputation.
6. Hot Wallets vs Cold Wallets in Blockchain
The fundamental distinction between Hot Wallets in Blockchain and cold wallets centers on the security-convenience spectrum. Understanding when to use each type is essential for effective cryptocurrency management and risk mitigation.[1]
| Feature | Hot Wallets in Blockchain | Cold Wallets |
|---|---|---|
| Internet Connectivity | Always online, constant blockchain sync | Offline storage, air-gapped security |
| Transaction Speed | Instant transaction signing and broadcasting | Requires hardware connection, manual signing |
| Security Level | Moderate – vulnerable to online attacks | Maximum – isolated from network threats |
| DeFi Interaction | Seamless dApp connectivity and smart contracts | Limited, requires transaction approval steps |
| Best Use Case | Active trading, daily transactions, Web3 use | Long-term holdings, large amounts, savings |
| Cost | Free (software-based) | $50-$300 (hardware device required) |
| Setup Complexity | Minimal – download and start | Moderate – device setup and learning curve |
| Recovery Process | Quick restore with seed phrase | Requires new hardware device |
The Security-Convenience Trade-off
Hot Wallets in Blockchain optimize for accessibility at the expense of maximum security. Their online nature creates an attack surface that sophisticated hackers can potentially exploit through various vectors including phishing, malware, supply chain compromises, and protocol vulnerabilities. However, for users actively participating in the crypto economy—trading on decentralized exchanges, providing liquidity, minting NFTs, or engaging in play-to-earn gaming the convenience factor of hot wallets is irreplaceable.
Cold wallets, conversely, eliminate online attack vectors by maintaining complete air-gap isolation. Private keys never touch internet-connected devices, making remote hacking virtually impossible. The trade-off is reduced usability: every transaction requires physically connecting the hardware device, navigating its interface, and manually approving operations. For investors holding cryptocurrency as long-term investments or managing substantial portfolios, this additional friction is worthwhile for the security benefits.
When to Use Hot Wallets vs Cold Wallets
The optimal strategy involves using both wallet types strategically. Keep operational funds in Hot Wallets in Blockchain—amounts you can afford to lose or need for immediate trading and transactions. This typically represents 5-20% of total holdings depending on your activity level. The majority of long-term holdings should reside in cold storage, accessed only for significant transactions or portfolio rebalancing.
Active DeFi users might maintain multiple Hot Wallets in Blockchain with different risk profiles: one for high-frequency trading with minimal balances, another for yield farming with moderate amounts, and cold storage for profits and core holdings. This layered approach balances accessibility needs with security requirements, ensuring that even if one hot wallet is compromised, losses remain contained.
7. Common Use Cases of Hot Wallets in Blockchain
The versatility of Hot Wallets in Blockchain enables participation across the entire spectrum of blockchain applications. Understanding these use cases helps users select appropriate wallets and implement corresponding security measures.
Daily Cryptocurrency Transactions
Hot Wallets in Blockchain excel at facilitating everyday cryptocurrency payments and peer-to-peer transfers. Whether splitting restaurant bills, paying freelancers, or purchasing goods from crypto-accepting merchants, hot wallets enable instant transactions with low friction. Mobile wallets particularly shine in this context, offering QR code scanning for point-of-sale payments and quick address entry for online purchases. The transaction finality speed on modern blockchains, combined with hot wallet accessibility, makes cryptocurrency payments competitive with traditional payment methods.
DeFi Staking and Yield Farming
Decentralized finance protocols require constant wallet connectivity for optimal operation. Hot Wallets in Blockchain enable users to deposit assets into lending protocols like Aave and Compound, provide liquidity on decentralized exchanges like Uniswap and Curve, and participate in yield farming strategies across multiple protocols. The ability to quickly respond to market conditions, rebalance positions, and claim rewards makes hot wallets essential infrastructure for DeFi participants. Advanced users employ Hot Wallets in Blockchain to interact with complex DeFi strategies involving flash loans, arbitrage opportunities, and automated market-making positions.
NFT Minting and Trading
The non-fungible token ecosystem relies heavily on Hot Wallets in Blockchain for both creation and commerce. Artists mint NFTs through platforms like OpenSea and Rarible using hot wallets to pay gas fees and sign creation transactions. Collectors use hot wallets to bid on auctions, purchase instant-buy listings, and transfer NFTs between wallets. The real-time nature of NFT drops and competitive bidding environments makes hot wallet speed advantages critical. Additionally, many NFT wallet communities use token-gated access systems that verify wallet holdings, requiring users to connect their Hot Wallets in Blockchain to authenticate membership and access exclusive content.
Web3 Gaming and dApp Access
Blockchain gaming has emerged as a major use case for Hot Wallets in Blockchain, with play-to-earn games requiring frequent microtransactions, in-game asset transfers, and reward claims. Games like Axie Infinity, The Sandbox, and Decentraland rely on seamless wallet integration to enable players to buy, sell, and trade in-game items as NFTs. Hot wallets serve as the bridge between gaming experiences and blockchain value, allowing players to maintain true ownership of digital assets while enjoying fluid gameplay experiences. Beyond gaming, countless decentralized applications across categories from social media to supply chain tracking utilize Hot Wallets in Blockchain as authentication and interaction mechanisms.
DAO Participation and Governance Voting
Decentralized autonomous organizations utilize Hot Wallets in Blockchain to enable member participation in governance decisions. Token holders connect their wallets to voting platforms like Snapshot to propose initiatives, cast votes, and delegate voting power. The wallet serves both as proof of stake in the organization and as the mechanism for submitting votes to governance smart contracts. Major protocols including Uniswap, Aave, and Compound rely on wallet-based governance systems that require active Hot Wallets in Blockchain connectivity to participate in shaping protocol evolution.
8. Advantages of Using Hot Wallets in Blockchain
The widespread adoption of Hot Wallets in Blockchain stems from numerous practical advantages that make them the preferred choice for active cryptocurrency users. These benefits extend beyond mere convenience to enable entirely new categories of blockchain applications.
Key Advantage: Instant Fund Access
Hot Wallets in Blockchain provide immediate transaction capabilities without hardware device dependencies. Users can respond to market opportunities, execute trades, and claim rewards within seconds rather than minutes. This speed advantage is crucial in fast-moving cryptocurrency markets where prices can swing significantly in short timeframes. The ability to act quickly on information or opportunities often makes the difference between profitable and missed trades.
Seamless decentralized application connectivity represents another major advantage. Hot Wallets in Blockchain integrate directly with browser-based dApps through standardized connection protocols like WalletConnect and Web3 providers. Users can interact with multiple protocols simultaneously, switching between DeFi platforms, NFT marketplaces, and blockchain games without disconnecting and reconnecting hardware devices. This frictionless experience is essential for productive Web3 participation.
Multi-chain asset support has become increasingly important as blockchain ecosystems fragment across multiple layer-1 and layer-2 networks. Modern Hot Wallets in Blockchain support dozens of blockchain networks, allowing users to manage Ethereum, BSC, Polygon, Arbitrum, Optimism, Avalanche, and Solana assets from a single interface. This consolidation simplifies portfolio management and reduces the cognitive overhead of tracking assets across multiple wallet applications.
The user-friendly experience of Hot Wallets in Blockchain lowers barriers to cryptocurrency adoption for newcomers. Intuitive interfaces, guided setup processes, and integrated educational resources help beginners navigate complex blockchain concepts. Features like address books, transaction history visualizations, and portfolio analytics make cryptocurrency management accessible to users without technical backgrounds. This accessibility is essential for mainstream adoption and expanding the blockchain user base beyond early adopters.
Cost-effectiveness provides another significant advantage. Hot Wallets in Blockchain are typically free to use, requiring no hardware purchases beyond the devices users already own (smartphones, computers). This zero upfront cost makes cryptocurrency accessible to users worldwide, regardless of economic circumstances. While hardware wallets offer superior security, the $50-$300 price point can be prohibitive for users with smaller portfolios or those in developing economies where Hot Wallets in Blockchain serve as the primary cryptocurrency gateway.
9. Security Risks of Hot Wallets in Blockchain
While Hot Wallets in Blockchain offer unmatched convenience, their online nature creates multiple attack vectors that malicious actors continuously exploit. Understanding these risks is crucial for implementing appropriate protective measures and making informed decisions about fund allocation.
Phishing Attacks and Social Engineering
Phishing remains the most prevalent threat to Hot Wallets in Blockchain users. Attackers create convincing replicas of popular wallet interfaces, DeFi platforms, and NFT marketplaces to trick users into entering seed phrases or approving malicious transactions. These attacks have become increasingly sophisticated, utilizing identical visual designs, SSL certificates, and even hijacked social media accounts of legitimate projects to appear authentic. In 2025 alone, phishing attacks accounted for over $1.2 billion in cryptocurrency losses, with the majority targeting hot wallet users.
Social engineering attacks exploit human psychology rather than technical vulnerabilities. Attackers pose as customer support representatives, impersonate project developers, or create urgent scenarios requiring immediate wallet interaction. Users are manipulated into revealing seed phrases, approving token approvals, or signing transactions that drain funds. The effectiveness of these attacks demonstrates that Hot Wallets in Blockchain security depends as much on user awareness as technical implementation.
Malware and Browser Exploits
Malicious software targeting Hot Wallets in Blockchain has evolved from simple keyloggers to sophisticated trojans that monitor blockchain transactions and modify them in real-time. Clipboard hijackers replace copied wallet addresses with attacker-controlled addresses, causing users to send funds to wrong recipients. Screen overlays present fake transaction details while the actual transaction sends funds elsewhere. Browser extensions masquerading as legitimate tools inject malicious code into web3 interactions, stealing private keys or manipulating smart contract calls.
The rise of supply chain attacks has introduced new risks where legitimate software downloads are compromised at the source. Attackers have infiltrated npm packages used by wallet developers, injected backdoors into browser extensions through compromised developer accounts, and distributed malware-infected wallet applications through official app stores. These sophisticated attacks bypass traditional security measures, making even cautious users vulnerable.
Fake dApps and Approval Scams
Malicious decentralized applications specifically target Hot Wallets in Blockchain by requesting excessive token approvals during connection. Users unknowingly grant smart contracts unlimited spending permission on their tokens, allowing attackers to drain wallets at any future time. These “approval scams” exploit the trust users place in dApp interfaces and their limited understanding of smart contract permissions. The prevalence of this attack vector has led to the development of approval management tools, but many users remain unaware of the accumulated permissions in their wallets.
Centralized Service Vulnerabilities
Even self-custodial Hot Wallets in Blockchain often depend on centralized infrastructure components that introduce single points of failure. Wallet applications may rely on centralized servers for transaction broadcasting, blockchain data queries, or backup services. Compromises of these backend systems can lead to widespread data breaches, transaction manipulation, or service outages affecting thousands of users simultaneously. The 2022 LastPass breach, which exposed encrypted vault data for a password manager also used for crypto seed phrase storage, illustrates how centralized dependencies create cascade risks.
Human Error and Poor Key Management
The majority of Hot Wallets in Blockchain losses stem not from sophisticated hacks but from user mistakes. Seed phrases stored in cloud services, sent via email, or photographed on phones become accessible to attackers through account compromises or device theft. Users reusing passwords across multiple services expose their wallets when unrelated platforms suffer data breaches. Simple mistakes like sending funds to wrong addresses or incorrect networks result in permanent loss due to blockchain transaction irreversibility. The self-custody model, while empowering, places full responsibility on users who may lack the technical knowledge to implement proper security practices.
10. Real-World Hot Wallet Hacks and Lessons Learned
Examining historical Hot Wallets in Blockchain security incidents provides invaluable insights into vulnerability patterns and the importance of robust security practices. Through our 8+ years in the industry, we’ve analyzed countless incidents to help our clients avoid similar fates.
Notable Incidents and Attack Patterns
The 2022 Ronin Network hack, which resulted in $625 million in losses, exemplified the risks when Hot Wallets in Blockchain managing bridge funds lack proper security controls. Attackers compromised validator private keys stored in hot wallets, allowing them to approve fraudulent transactions. This incident highlighted that even institutional-grade infrastructure can fail when fundamental security principles are neglected. The attack succeeded not through blockchain protocol vulnerabilities but through poor operational security in hot wallet key management.
The 2023 Euler Finance exploit demonstrated how smart contract interactions with Hot Wallets in Blockchain can enable flash loan attacks that drain protocol funds. While the attack targeted the protocol’s code, it required a hot wallet with sufficient assets to execute the complex attack sequence. The incident underscored that hot wallet security extends beyond key protection to include careful vetting of smart contract interactions and approval management.
What Typically Goes Wrong
Analysis of Hot Wallets in Blockchain security breaches reveals recurring patterns: insufficient access controls allowing single points of compromise, inadequate monitoring systems failing to detect suspicious activity, and delayed incident response enabling attackers to maximize damage. Many breaches involve social engineering targeting employees with privileged access, highlighting that technological security measures must be complemented by human-focused security training and protocols.
The user-related losses with Hot Wallets in Blockchain typically involve phishing attacks, malware infections, and poor seed phrase management rather than blockchain protocol flaws. This reality emphasizes that for most users, security depends more on personal operational security practices than wallet software choice. Even the most secure wallet application cannot protect against users who willingly enter seed phrases into fraudulent websites or approve malicious smart contract calls.
Key Takeaway: User Responsibility
Our analysis shows that 95% of Hot Wallets in Blockchain losses are user-related rather than technology failures. This statistic underscores the critical importance of security education, careful operational practices, and appropriate risk management through fund allocation between hot and cold storage.
11. Best Practices for Securing a Hot Wallet in Blockchain (2026)
Implementing comprehensive security practices transforms Hot Wallets in Blockchain from vulnerable convenience tools into reasonably secure operational infrastructure. Based on our 8+ years of wallet security implementation experience, these practices represent the minimum security baseline for responsible hot wallet usage.
Seed Phrase Protection Rules
The seed phrase represents absolute control over your Hot Wallets in Blockchain, making its protection paramount. Write seed phrases on durable physical media—metal backup plates are ideal—and store them in secure locations like safes or safety deposit boxes. Never store seed phrases digitally in any form: no cloud services, password managers, encrypted files, or photographs. The permanent nature of blockchain transactions means a compromised seed phrase results in immediate and irreversible fund loss.
Consider geographic distribution for backup seed phrases. Store copies in multiple secure locations to protect against localized disasters like fires or floods. However, avoid excessive distribution that increases exposure risk. For high-value Hot Wallets in Blockchain, investigate multi-signature schemes or Shamir’s Secret Sharing, which splits seed phrases into multiple shares requiring a threshold to reconstruct, adding protection against single-point compromises.
Hardware Wallet Integration
The optimal security model uses hardware wallets alongside Hot Wallets in Blockchain in a hybrid approach. Connect hardware wallets to hot wallet interfaces like MetaMask or Rabby to gain DeFi accessibility while maintaining private key isolation on hardware devices. This configuration provides hot wallet convenience for smart contract interactions while preserving the security benefits of offline key storage. Users can interact with dApps seamlessly while knowing their keys never touch the internet-connected computer.
Token Approval Management
Regular auditing and revocation of token approvals is essential for Hot Wallets in Blockchain security. Use tools like Revoke.cash or the built-in approval management features in modern wallets to review all active smart contract permissions. Revoke unlimited approvals and replace them with specific amount approvals when possible. Set calendar reminders to conduct approval audits quarterly, removing permissions for protocols you no longer actively use. This practice limits the potential damage from compromised dApps or smart contract exploits.
Multi-Factor Authentication Implementation
Enable all available authentication layers for Hot Wallets in Blockchain and related services. Use authenticator applications rather than SMS-based 2FA, which is vulnerable to SIM-swapping attacks. For wallet applications offering biometric authentication, enable fingerprint or face recognition as an additional access barrier. Protect email accounts associated with wallet recovery with strong, unique passwords and hardware security keys. Remember that wallet security is only as strong as the weakest authentication factor in the chain of access.
Safe Browser and Network Habits
Dedicate a separate browser profile or even a separate browser exclusively for Hot Wallets in Blockchain and DeFi activities. Avoid installing unnecessary extensions that could compromise wallet security. Never use public WiFi networks for cryptocurrency transactions without a trusted VPN. Verify website URLs meticulously before connecting wallets—bookmark legitimate sites and access them exclusively through bookmarks rather than search engines or links. Consider using a dedicated device for high-value transactions to minimize exposure to malware from everyday computing activities.
12. Hot Wallet Security Features to Look for in 2026
The evolution of Hot Wallets in Blockchain has introduced sophisticated security features that significantly enhance protection without sacrificing usability. When selecting wallets in 2026, prioritize implementations incorporating these advanced security technologies.
| Security Feature | Description | Security Benefit |
|---|---|---|
| Multi-Party Computation (MPC) | Distributes private key generation and signing across multiple parties | Eliminates single point of key compromise |
| Biometric Authentication | Uses fingerprint, face recognition, or iris scanning for access | Prevents unauthorized device access |
| Encrypted Key Storage | Hardware-backed encryption in secure enclaves | Protects keys even if device is compromised |
| Session Isolation | Separates wallet operations from browser context | Prevents malicious website access to keys |
| Permission-Based Signing | Granular transaction approval with spending limits | Limits damage from approved malicious dApps |
| Transaction Simulation | Preview transaction outcomes before execution | Reveals malicious intent in smart contracts |
Multi-Party Computation (MPC)
MPC represents the cutting edge of Hot Wallets in Blockchain security technology. Instead of a single private key stored in one location, MPC distributes key material across multiple parties or devices. Transaction signing requires combining these distributed key shares through cryptographic protocols without ever reconstructing the complete key in any single location. Leading implementations in 2026 use threshold signature schemes where, for example, any 2 of 3 key shares can sign transactions, providing redundancy against loss while maintaining security against compromise.
Biometric Authentication
Modern Hot Wallets in Blockchain leverage device-native biometric capabilities for access control. Fingerprint sensors, facial recognition cameras, and even iris scanners provide strong authentication that’s difficult to phish or steal compared to passwords. Crucially, these implementations store biometric data in secure hardware enclaves on the device, never transmitting it to servers or storing it in software-accessible memory. This local biometric verification adds a significant barrier against unauthorized wallet access even if devices are stolen.
Transaction Simulation and Security Warnings
Advanced Hot Wallets in Blockchain in 2026 incorporate transaction simulation engines that analyze the potential outcomes of smart contract interactions before execution. These systems detect suspicious patterns like unlimited token approvals, asset transfers to unknown addresses, or interactions with flagged malicious contracts. They present users with clear warnings and predicted outcomes, helping even non-technical users identify potentially harmful transactions. This proactive security approach prevents many common attack vectors by intercepting them at the moment of user approval.
13. Hot Wallets in Blockchain for Businesses and Enterprises
Enterprise adoption of Hot Wallets in Blockchain requires addressing unique challenges around compliance, access control, audit trails, and institutional-grade security. Our experience deploying wallet infrastructure for businesses ranging from cryptocurrency exchanges to traditional financial institutions has revealed critical considerations for enterprise implementations.
Custodial vs Non-Custodial Models
Businesses must decide whether to implement custodial Hot Wallets in Blockchain where the organization controls private keys on behalf of users, or non-custodial wallet models where users retain key control. Custodial implementations offer superior operational control, easier compliance with regulations, and the ability to assist users with lost credentials. However, they assume massive liability for security breaches and face stricter regulatory oversight including potential licensing requirements as money transmitters or trust companies.
Non-custodial Hot Wallets in Blockchain shift security responsibility to users, reducing regulatory burden but complicating customer support and recovery processes. Hybrid models are emerging where businesses provide optional backup and recovery services without maintaining ongoing custody of keys. The choice between these models fundamentally shapes security architecture, operational procedures, and regulatory compliance strategies.
Treasury Management Use Cases
Corporate Hot Wallets in Blockchain enable businesses to manage cryptocurrency treasuries, execute payroll in digital assets, pay suppliers, and conduct cross-border transactions. Multi-signature wallets with role-based access controls allow companies to require multiple approvers for transactions exceeding certain thresholds. Automated spending policies can enforce compliance rules, restrict transaction types, and maintain audit logs for accounting purposes. Integration with enterprise resource planning systems and accounting software enables businesses to incorporate cryptocurrency operations into existing financial workflows.
Compliance and Access Control
Enterprise Hot Wallets in Blockchain must implement robust compliance frameworks including Know Your Customer verification, Anti-Money Laundering monitoring, and sanctions screening. Transaction monitoring systems analyze blockchain activity for suspicious patterns, automatically flagging transactions requiring manual review. Access control systems implement principle of least privilege, granting employees only the permissions necessary for their roles. Comprehensive audit logging records all wallet operations for regulatory reporting and forensic analysis when incidents occur.
14. How Hot Wallets Power Web3, DeFi, and NFT Ecosystems
Hot Wallets in Blockchain serve as the fundamental infrastructure enabling the Web3 revolution. Their role extends far beyond simple cryptocurrency storage to become the primary interface between users and decentralized digital economies.
Wallets as Web3 Identity
In Web3 architecture, Hot Wallets in Blockchain function as portable digital identities that users carry across platforms. Rather than creating separate accounts on each website, users authenticate by connecting their wallet, which serves as their universal login. This wallet-based identity carries reputation scores, token-gated access permissions, and ownership credentials that persist across the decentralized web. The shift from platform-owned identities to user-owned wallet identities represents a fundamental restructuring of digital identity toward user sovereignty.
Token-Gated Access
Communities increasingly use Hot Wallets in Blockchain to verify membership and control access through token ownership verification. NFT collections grant access to exclusive Discord servers, private events, and premium content. DeFi protocols verify wallet holdings to qualify users for governance participation or premium features. Content creators use wallet-based access control to monetize through NFT sales rather than traditional subscriptions. This token-gated access model creates new business models and community structures impossible under traditional web infrastructure.
Smart Contract Interactions
The ability of Hot Wallets in Blockchain to seamlessly interact with smart contracts enables the entire DeFi ecosystem. Users deposit assets into lending protocols, provide liquidity to decentralized exchanges, stake tokens in validator systems, and participate in complex multi-protocol strategies through simple wallet interactions. The wallet abstracts the underlying smart contract complexity, presenting intuitive interfaces while maintaining the security guarantees of user-approved transactions. This abstraction makes DeFi accessible to users without smart contract development knowledge.
Cross-Chain Usability
Modern Hot Wallets in Blockchain support multiple blockchain networks, enabling users to manage diverse digital asset portfolios from unified interfaces. Cross-chain bridges integrate directly into wallets, allowing asset transfers between networks without leaving the wallet application. This multi-chain support is essential as blockchain activity fragments across layer-1 and layer-2 networks optimized for different use cases. Wallets that aggregate liquidity and functionality across chains provide significant user experience advantages over single-chain alternatives.
15. Limitations of Hot Wallets in Blockchain
Despite their advantages, Hot Wallets in Blockchain have inherent limitations that users must understand to make informed security decisions and implement appropriate risk management strategies.
Unsuitability for Large Holdings
The security trade-offs of Hot Wallets in Blockchain make them inappropriate for storing significant wealth. While acceptable for operational amounts needed for trading and transactions, concentrating large holdings in hot wallets creates unacceptable risk exposure. The potential for sudden total loss through compromise exceeds the convenience benefits. Financial advisors and security experts recommend limiting hot wallet holdings to amounts users can afford to lose completely, typically suggesting no more than 5-10% of total cryptocurrency holdings.
Internet Security Dependencies
Hot Wallets in Blockchain inherit all vulnerabilities of internet-connected devices and networks. Compromised WiFi routers, man-in-the-middle attacks, DNS hijacking, and network-level surveillance create attack surfaces absent in cold storage solutions. Users must maintain vigilance about network security, implement VPNs for sensitive transactions, and recognize that any internet-connected device represents a potential compromise vector. The perpetual connectivity that enables hot wallet convenience simultaneously creates persistent vulnerability.
Device-Level Risks
The devices hosting Hot Wallets in Blockchain become single points of failure for wallet security. Lost or stolen smartphones containing wallet applications give attackers physical access to encrypted key material. While device encryption and authentication provide protection, determined attackers with physical device access can employ advanced extraction techniques. Additionally, device failures resulting in data loss can cause permanent fund loss if seed phrase backups are inadequate. This device dependency creates vulnerability absent in hardware wallet solutions where private keys never touch general-purpose computing devices.
Regulatory Exposure
Custodial Hot Wallets in Blockchain operated by businesses face increasing regulatory scrutiny globally. Regulations may require license acquisition, extensive compliance programs, and regular audits, significantly increasing operational costs. Future regulations might mandate insurance requirements, force geographic restrictions on service availability, or impose transaction monitoring requirements that compromise user privacy. Even non-custodial wallet providers face potential regulatory pressure regarding their role in facilitating cryptocurrency usage. This regulatory uncertainty represents a significant limitation for both wallet providers and users in certain jurisdictions.
16. When Should You Use a Hot Wallet vs Cold Wallet?
Making informed decisions about Hot Wallets in Blockchain versus cold wallet usage requires understanding your specific use case, risk tolerance, and operational requirements. The optimal strategy typically involves using both wallet types strategically rather than exclusively relying on either.
Practical Decision Framework
Use Hot Wallets in Blockchain When:
- Conducting frequent transactions (multiple times per day or week)
- Actively trading on decentralized exchanges
- Participating in DeFi protocols requiring constant rebalancing
- Interacting with NFT marketplaces and Web3 applications
- Managing amounts representing less than 20% of total holdings
- Needing mobile access for point-of-sale or peer-to-peer payments
Use Cold Wallets When:
- Storing long-term investment holdings
- Managing amounts exceeding your risk tolerance for potential loss
- Holding cryptocurrency as retirement savings or major wealth
- Transactions are infrequent (monthly or less often)
- Maximum security is prioritized over convenience
- Managing institutional or business treasury holdings
Portfolio Allocation Strategy
Implement a tiered security model for cryptocurrency holdings. Maintain 5-20% of total portfolio value in Hot Wallets in Blockchain for operational needs. This operational tier supports active trading, DeFi participation, and regular transactions. The majority of holdings (60-80%) should reside in cold storage as long-term investment positions. An intermediate tier using hardware wallets connected to hot wallet interfaces can hold 15-25% for occasional DeFi interactions requiring security beyond pure hot wallets but more accessibility than deep cold storage.
Regularly rebalance between tiers based on activity levels and market conditions. During high-volatility periods requiring active trading, slightly increase the hot wallet allocation. When market activity slows or after profitable trades, sweep excess funds to cold storage. This disciplined approach maintains the convenience benefits of Hot Wallets in Blockchain while limiting maximum potential losses from security incidents.
Risk-Based Decision Making
Personal risk tolerance should ultimately determine Hot Wallets in Blockchain usage patterns. Conservative investors comfortable with the hot wallet risk for only small amounts should maintain minimal hot wallet balances and conduct most operations through hardware wallet interfaces. Aggressive DeFi participants willing to accept higher risk for yield opportunities might justify larger hot wallet allocations. The key is honest self-assessment of both risk tolerance and technical competence to implement proper security measures.
17. Future of Hot Wallets in Blockchain
The trajectory of Hot Wallets in Blockchain development points toward increasingly sophisticated security implementations combined with improved user experiences. Several emerging technologies and trends will reshape the hot wallet landscape over the coming years.
Account Abstraction
Account abstraction (ERC-4337 and similar standards) transforms how Hot Wallets in Blockchain interact with blockchains by enabling smart contract wallets with programmable security features. Users can implement recovery mechanisms allowing trusted contacts to help recover lost wallets, set spending limits that require additional authentication for large transactions, and enable session keys that permit specific applications limited access without exposing master keys. Account abstraction also enables gas-less transactions where third parties sponsor transaction fees, improving user experience for newcomers.
Smart Wallets and Automation
Next-generation Hot Wallets in Blockchain will incorporate AI-powered automation capabilities. Wallets will automatically rebalance DeFi positions based on user-defined strategies, harvest yield farming rewards at optimal times, and execute complex multi-protocol transactions atomically. Predictive security features will analyze transaction patterns to identify anomalous behavior, alerting users to potentially compromised wallets before significant damage occurs. These smart capabilities will make advanced DeFi strategies accessible to users without deep technical knowledge.
Enhanced UX with Stronger Security
The historical trade-off between security and usability in Hot Wallets in Blockchain is diminishing as new technologies emerge. Biometric authentication, hardware security module integration in consumer devices, and advanced cryptographic protocols like zero-knowledge proofs enable strong security without compromising user experience. Social recovery mechanisms allow wallet restoration through trusted contacts without storing seed phrases anywhere. These developments will make secure cryptocurrency usage accessible to mainstream audiences unfamiliar with traditional security practices.
AI-Driven Transaction Risk Detection
Machine learning models integrated into Hot Wallets in Blockchain will provide real-time transaction risk assessment. These systems analyze smart contract code, evaluate contract interaction history, assess token contract legitimacy, and detect phishing patterns to warn users before approving potentially harmful transactions. By learning from blockchain-wide attack patterns, these AI systems can identify novel threats that static rule-based security systems miss. The result is proactive security that evolves alongside emerging attack vectors.
18. Frequently Asked Questions About Hot Wallets in Blockchain
Are hot wallets safe in 2026?
Hot Wallets in Blockchain have become significantly safer through improved security features like MPC, biometric authentication, and transaction simulation. However, their online nature creates inherent vulnerabilities absent in cold storage. Safety depends heavily on user security practices: proper seed phrase management, regular approval audits, and limiting stored amounts to operational needs. For active cryptocurrency users implementing best practices, modern hot wallets provide acceptable security for appropriate use cases while recognizing they should never store majority holdings.
Can hot wallets be hacked?
Yes, Hot Wallets in Blockchain can be compromised through various attack vectors including phishing, malware, browser exploits, and social engineering. However, most “hacks” result from user error rather than technical vulnerabilities in wallet software. Sophisticated attackers can potentially exploit weaknesses in wallet implementations, but the vast majority of losses stem from users revealing seed phrases, approving malicious smart contracts, or falling for phishing attacks. Proper security practices dramatically reduce hack risk even though complete elimination is impossible given the online nature of hot wallets.
How much crypto should be kept in a hot wallet?
Conservative security guidance suggests limiting Hot Wallets in Blockchain to amounts representing 5-20% of total cryptocurrency holdings, focusing on funds needed for active trading and transactions. The specific percentage depends on your activity level, risk tolerance, and technical competence implementing security measures. Active DeFi participants might justify higher percentages, while long-term holders should minimize hot wallet holdings. The fundamental principle: only keep amounts in hot wallets that you could afford to lose completely without significant financial impact.
Are hot wallets suitable for beginners?
Hot Wallets in Blockchain are actually ideal starting points for cryptocurrency beginners due to their intuitive interfaces, zero upfront costs, and immediate accessibility. The user-friendly experience helps newcomers understand blockchain concepts without hardware wallet complexity. However, beginners must invest time learning security fundamentals including seed phrase protection, phishing recognition, and transaction verification before handling significant amounts. Starting with small amounts in it allows learning through experience while limiting potential losses from inevitable beginner mistakes.
19. Conclusion: Are Hot Wallets in Blockchain Worth Using?
Hot Wallets in Blockchain represent essential infrastructure for active cryptocurrency participation in 2026. Their combination of accessibility, multi-chain support, and seamless DeFi integration makes them indispensable for users seeking meaningful engagement with blockchain ecosystems. The question is not whether to use it, but how to use them responsibly within a comprehensive security framework.
The security concerns surrounding Hot Wallets in Blockchain are real and must be taken seriously. However, implementing proper security practices—seed phrase protection, approval management, limiting stored amounts, and using modern wallets with advanced security features—transforms hot wallets from dangerous liabilities into acceptable tools for their intended purpose. The key insight from our 8+ years of wallet infrastructure experience is that security depends more on user behavior than wallet technology itself.
For cryptocurrency users across the spectrum from beginners to DeFi power users, Hot Wallets in Blockchain serve critical functions that justify their risks when used appropriately. Beginners benefit from the accessible onboarding experience and intuitive interfaces. Active traders require the instant access and transaction speed that only hot wallets provide. DeFi participants need seamless smart contract interaction impossible with cold storage alone. NFT collectors and Web3 enthusiasts rely on hot wallets as their digital identity and access mechanism.
The optimal approach views Hot Wallets in Blockchain as one component within a layered security strategy. Use it for their strengths operational convenience, rapid access, and blockchain interaction while acknowledging their limitations by keeping majority holdings in cold storage. This balanced perspective, combined with vigilant security practices and ongoing education about emerging threats, enables safe it usage that unlocks the full potential of blockchain technology.
As the blockchain ecosystem continues evolving, Hot Wallets in Blockchain will remain central to cryptocurrency adoption and utilization. Understanding their capabilities, limitations, and proper usage patterns empowers users to navigate the digital asset landscape confidently and securely. The future of finance is decentralized, and hot wallets are the primary gateway through which individuals access this transformative technology.
Ready to Build Your Secure Crypto Solution?
Partner with blockchain experts who understand the perfect balance between security and usability. Let’s create your next-generation wallet solution together!
Frequently Asked Questions
A hot wallet in blockchain is a crypto wallet connected to the internet that allows users to store, send, receive, and interact with digital assets instantly. It is commonly used for daily transactions, DeFi, NFTs, and Web3 applications.
It works by storing private keys in a software environment connected to the internet. When a user initiates a transaction, the wallet signs it using the private key and broadcasts it to the blockchain network.
It is safe for everyday use when best security practices are followed, such as seed phrase protection, trusted dApps, and limited fund exposure. However, they are less secure than cold wallets for storing large crypto holdings.
The main risks include phishing attacks, malware, fake dApps, compromised browsers, and accidental approval of malicious smart contracts. Most hot wallet losses occur due to user error rather than blockchain flaws.
It is connected to the internet and designed for convenience and fast access, while a cold wallet remains offline and offers maximum security. It is ideal for transactions, whereas cold wallets are better for long-term storage.
Only the amount needed for regular transactions, trading, or dApp usage should be kept in a hot wallet. Large or long-term holdings should be stored in cold wallets to reduce security risks.
Yes, It can be compromised through phishing, malware, or unsafe approvals. The blockchain itself is secure, but It depend heavily on user behavior and device security.
Yes, It is beginner-friendly due to their simple interfaces and ease of use. They are ideal for learning blockchain transactions, exploring DeFi, and using NFTs, provided basic security guidelines are followed.
It support DeFi platforms, NFT marketplaces, Web3 games, DAO governance, and multi-chain networks, making them essential tools for interacting with the blockchain ecosystem.
Best practices include never sharing seed phrases, using hardware wallets with hot wallets, verifying dApps before connecting, managing token approvals regularly, and avoiding public Wi-Fi or unknown browser extensions.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







