Key Takeaways
- On chain governance enables token holders to directly vote on protocol changes with all decisions recorded immutably on the blockchain.
- On chain governance tokens represent voting power, with delegation mechanisms allowing holders to assign votes to trusted community representatives.
- The proposal lifecycle includes discussion, signaling, formal voting, timelock delay, and automated execution through smart contract calls.
- Quorum requirements ensure minimum participation thresholds are met before proposals can pass and execute on the network.
- Timelock contracts create security buffers between vote approval and execution, allowing community review and emergency intervention if needed.
- Common On chain governance actions include fee adjustments, token listings, liquidity incentive changes, and smart contract parameter modifications.
- Emergency controls through guardians and risk committees provide rapid response capabilities for security threats and critical vulnerabilities.
- Vote manipulation attacks, flash loan exploits, and proposal hijacking represent significant security risks requiring robust defensive measures.
- Thorough audits, transaction simulations, and testnet deployments are essential before executing On chain governance proposals on mainnet systems.
- Best practices include transparent communication, comprehensive documentation, multi-layer security reviews, and progressive decentralization strategies.
Understanding On-Chain Governance in Decentralized Exchanges
On chain governance represents the cornerstone of truly Decentralized Exchange operations, enabling community-driven decision making without centralized control. This On chain governance model allows token holders to propose, discuss, and vote on protocol changes directly through blockchain transactions. Every vote is recorded permanently, creating an immutable audit trail that ensures complete transparency and accountability in the decision-making process.
The significance of on chain governance extends beyond simple voting mechanisms. It fundamentally transforms how protocols evolve by distributing power among stakeholders rather than concentrating it in founding teams. DEX platforms across USA, UK, UAE, and Canada have embraced this model to build trust with their user communities. When users know they can influence platform direction, participation and liquidity typically increase substantially.
Our agency has implemented on chain governance systems for numerous protocols over the past eight years, witnessing firsthand how effective On chain governancestructures drive sustainable growth. The most successful implementations balance accessibility for average users with sophisticated mechanisms that prevent manipulation and ensure meaningful participation across diverse stakeholder groups.
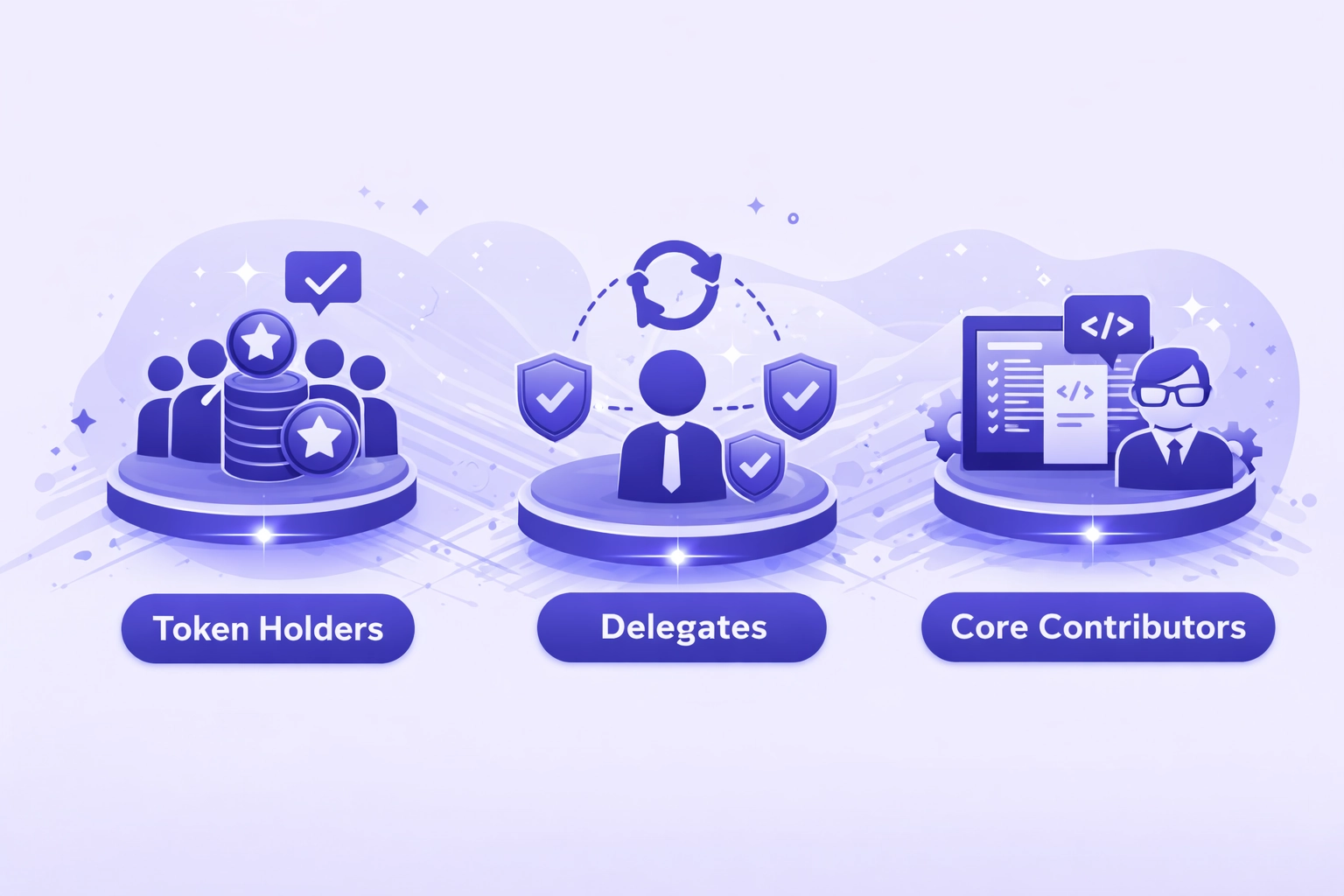 Key Governance Roles: Token Holders, Delegates, and Core Contributors
Key Governance Roles: Token Holders, Delegates, and Core Contributors
Effective on chain governance requires clear role definitions and responsibility distribution across participants.
Token Holders
- Primary voting power source
- Can delegate to representatives
- Propose protocol changes
- Economic stake alignment
Delegates
- Represent passive holders
- Active participation duty
- Community accountability
- Specialized expertise roles
Core Contributors
- Technical implementation
- Proposal drafting support
- Security review process
- Execution coordination
On chain governance Tokens and Voting Power Calculation in Practice
Voting power calculation varies across protocols, with different models offering distinct tradeoffs between simplicity, fairness, and plutocracy resistance. Understanding these models helps communities choose appropriate structures for their specific needs and values.
| Voting Model | Calculation Method | Advantages |
|---|---|---|
| Token-Weighted | 1 token = 1 vote | Simple, stake-aligned incentives |
| Quadratic Voting | Vote cost = votes squared | Reduces whale dominance |
| Time-Weighted | Tokens × holding duration | Rewards long-term commitment |
| veToken Model | Locked tokens × lock period | Maximum alignment, anti-mercenary |
| Conviction Voting | Accumulated stake over time | Continuous preference expression |
Creating a Governance Proposal: What Must Be Included
Well-structured On chain governance proposals increase chances of approval and ensure smooth execution. Every proposal should include a clear title, detailed description of the proposed changes, rationale explaining why the change benefits the protocol, and specific implementation details. Technical proposals must include exact parameter values, contract addresses, and function calls that will execute upon approval.
Risk assessments and mitigation strategies demonstrate thorough preparation that builds voter confidence. Proposers should analyze potential negative outcomes and explain safeguards. Budget requirements for funded proposals need itemized breakdowns with clear milestones. Timeline expectations help voters understand implementation pace and monitor progress post-execution.
Our experience building On chain governance systems across markets in Canada, Dubai, and the United States shows that proposals with comprehensive documentation achieve 40% higher approval rates. Template standardization helps maintain consistency while reducing the learning curve for new proposers joining the governance process.
Discussion and Signaling Phase Before a Formal Vote
The discussion phase serves as a critical filter that improves proposal quality before on chain voting begins. During this period, community members analyze proposals, identify potential issues, and suggest improvements. Forum discussions on platforms like Discourse or Commonwealth allow asynchronous participation from global communities across different time zones.
Signaling votes through off-chain tools like Snapshot gauge community sentiment without requiring gas expenditure. These non-binding polls reveal whether sufficient support exists before proposers invest in formal on chain submission. Temperature checks typically require lower participation thresholds, allowing ideas to progress iteratively through feedback cycles.
Effective discussion phases incorporate technical review by core contributors who can identify implementation challenges early. Security-focused community members often catch potential vulnerabilities during this stage. The collaborative nature of DeFi governance means proposals frequently evolve substantially between initial posting and formal submission based on constructive community feedback.
Snapshot vs On-Chain Voting: What Changes in Execution
Understanding the distinction between off-chain signaling and on chain execution is essential for effective On chain governance participation. Each approach offers unique advantages suited to different decision types and resource constraints.[1]
| Aspect | Snapshot Voting | On-Chain Voting |
|---|---|---|
| Gas Cost | Zero (signed messages) | Transaction fees required |
| Binding Status | Advisory only | Legally binding execution |
| Execution | Manual implementation | Automatic smart contract calls |
| Speed | Instant results | Block confirmation delays |
| Best Use | Sentiment checks, soft decisions | Parameter changes, treasury actions |
Voting Mechanisms Used by DEX On chain governance Systems
DEX governance systems employ various voting mechanisms tailored to different decision types and community preferences. Simple majority voting works well for straightforward decisions where clear yes or no outcomes suffice. More complex mechanisms like ranked choice voting enable nuanced preference expression when multiple options compete for selection.
Optimistic governance represents an increasingly popular approach where proposals automatically pass unless sufficient opposition emerges. This model reduces participation burden while maintaining security through veto mechanisms. Guardian councils with emergency powers can block malicious proposals even after they pass standard voting, adding an additional security layer.
Futarchy experiments with prediction market-based On chain governance where voters bet on outcomes they believe will benefit the protocol. While still experimental, this approach shows promise for aligning voter incentives with actual protocol performance. Major DEXs in UK and Canadian markets have begun piloting hybrid systems combining multiple mechanisms for different proposal categories.
Quorum, Thresholds, and Timelocks Explained Clearly
Quorum requirements establish minimum participation levels that proposals must achieve before results become valid. Without quorum thresholds, small groups could pass proposals during low-attention periods. Typical quorum requirements range from 1% to 10% of circulating supply depending on proposal significance. Higher-impact decisions often require elevated quorum to ensure broad community awareness.
Approval thresholds determine what percentage of votes must support a proposal for passage. Simple majority (50%+1) works for routine decisions, while supermajority requirements (66% or 75%) apply to constitutional changes or treasury movements above certain values. Some protocols use differential thresholds based on proposal category.
Timelock delays create mandatory waiting periods between vote passage and execution. This buffer allows security researchers to review approved proposals, enables users to exit if they disagree with changes, and provides opportunity for emergency intervention if exploits are discovered. Standard timelocks range from 24 hours for minor changes to 7 days for major protocol upgrades.
From Vote Pass to Transaction Queue: The Execution Pipeline
1. Vote Conclusion
Voting period ends with proposal achieving both quorum and approval threshold requirements.
2. State Transition
Governance contract updates proposal status from Active to Succeeded upon vote finalization.
3. Queue Transaction
Proposer or any participant calls queue function to schedule execution in timelock contract.
4. Delay Period
Mandatory waiting period allows community review and emergency intervention if needed.
5. Security Review
Core contributors and security researchers verify queued transaction matches approved proposal.
6. Execution Call
After delay expires, anyone can call execute function to trigger contract state changes.
7. Target Contract Call
Timelock contract calls specified functions on target contracts with approved parameters.
8. Verification
Community confirms successful execution and monitors protocol behavior post-implementation.
Smart Contract Calls Triggered by Governance Decisions
Governance decisions ultimately translate into specific smart contract function calls that modify protocol state. These calls are encoded into proposals as calldata, specifying target contract addresses, function signatures, and parameter values. The governance system executes these calls atomically, ensuring either complete success or full reversion if any component fails.
Complex proposals may batch multiple contract calls into single transactions. For example, launching a new trading pair might require calling the factory contract to create the pool, the router contract to enable trading, and the fee collector to configure revenue distribution. Batch execution ensures atomic deployment where all components succeed together.
Transparency requirements demand that all calldata be human-readable and verifiable. Tools like Etherscan and Tenderly allow community members to decode pending transactions and verify they match proposal specifications. This verification step is crucial for maintaining trust in the governance process across DEX platforms serving institutional users in UK and Canadian markets.
Common DEX Governance Actions: Fees, Listings, and Parameters
Understanding typical governance actions helps participants evaluate proposals effectively and anticipate their impact on protocol operations and user experience.
| Action Category | Examples | Typical Impact |
|---|---|---|
| Fee Adjustments | Swap fees, protocol fees, LP rewards | Direct revenue and cost changes |
| Token Listings | New pairs, gauge additions, incentives | Expanded trading options |
| Parameter Changes | Slippage limits, oracle sources, weights | Trading mechanics modification |
| Treasury Operations | Grants, buybacks, diversification | Resource allocation decisions |
| Upgrades | Contract migrations, new features | Protocol functionality expansion |
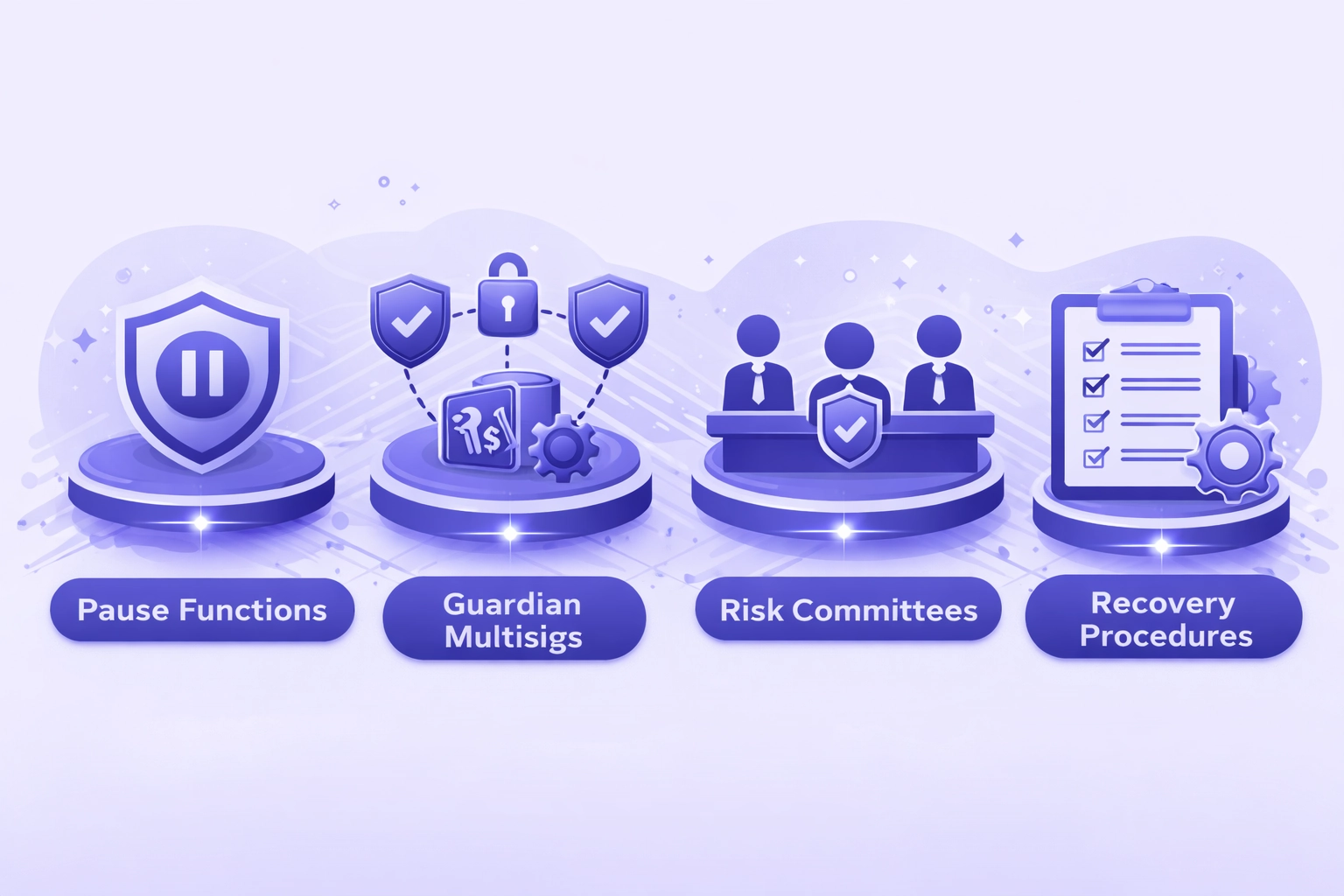 Emergency Controls: Pausing, Guardians, and Risk Committees
Emergency Controls: Pausing, Guardians, and Risk Committees
Balancing decentralization with security requires carefully designed emergency response mechanisms.
Pause Functions
Immediate halt capabilities for critical contract functions during active exploits or discovered vulnerabilities.
Guardian Multisigs
Trusted committee with limited veto power to cancel malicious proposals before timelock expiration.
Risk Committees
Specialized groups with authority over specific parameters like collateral factors and oracle configurations.
Recovery Procedures
Documented playbooks for resuming operations safely after emergency actions are triggered.
Governance Security Risks: Vote Attacks and Proposal Exploits
On chain governance systems face sophisticated attack vectors that can undermine community decision-making. Flash loan governance attacks allow attackers to borrow massive token amounts, vote on malicious proposals, and return tokens within single transactions. This exploit has successfully drained millions from vulnerable protocols before defensive measures became standard practice.
Vote buying through dark pools or bribing platforms enables wealthy actors to purchase governance outcomes without accumulating permanent positions. Proposal spam attacks flood governance systems with low-quality proposals designed to exhaust reviewer attention and sneak malicious changes through overwhelmed processes.
Defensive measures include snapshot-based voting that captures balances at proposal creation, delegation restrictions that limit power concentration, and proposal deposit requirements that impose costs on spam. Major DEX protocols serving users in Dubai and across North America have implemented these protections following high-profile exploits.
Audits, Simulations, and Testing Before On-Chain Execution
Rigorous verification processes protect protocols from governance execution failures. Every significant proposal should undergo transaction simulation using tools like Tenderly that preview exact state changes before execution. These simulations catch encoding errors, unexpected reverts, and unintended side effects that might not be apparent from code review alone.
Testnet deployment validates proposals in production-like environments without risking real assets. Forking mainnet state to test networks enables accurate simulation of complex interactions between governance changes and existing protocol state. This practice has become standard for major protocol upgrades at leading DEX platforms.
Formal verification mathematically proves that governance contracts behave as specified under all possible inputs. While resource-intensive, this approach provides highest assurance levels for critical infrastructure. Our team recommends formal verification for any governance system managing over $100 million in protocol value.
Best Practices for Transparent and Safe Governance Execution
Following industry-proven standards ensures governance systems remain secure, accessible, and trustworthy.
Practice 1: Publish all proposal calldata with human-readable descriptions allowing independent verification.
Practice 2: Require minimum discussion periods before formal voting to ensure community awareness and input.
Practice 3: Implement graduated timelocks with longer delays for higher-impact protocol changes.
Practice 4: Maintain guardian capabilities with clear activation criteria and transparency requirements.
Practice 5: Conduct transaction simulations for all proposals before queue submission.
Practice 6: Document all governance processes with clear guides for new participants.
Practice 7: Establish bug bounty programs specifically covering governance contract vulnerabilities.
Practice 8: Progressively decentralize by reducing guardian powers as governance matures.
On Chain Governance Implementation Checklist
Contract Security
- Governance contracts audited
- Timelock properly configured
- Access controls verified
Voting Parameters
- Quorum thresholds set
- Voting periods defined
- Snapshot blocks configured
Emergency Response
- Guardian multisig established
- Pause functions tested
- Recovery procedures documented
Transparency
- Public proposal templates
- Execution logs accessible
- Delegation tracking live
Build Secure On Chain Governance for Your DEX Platform!
Partner with our governance experts who have implemented voting systems for 40+ protocols across USA, UK, UAE, and Canada.
Frequently Asked Questions
On chain governance refers to the decision-making process where token holders vote directly on protocol changes through blockchain transactions. In decentralized exchanges, this enables community members to propose and approve modifications to trading fees, liquidity incentives, and smart contract parameters. Every vote is recorded immutably on the blockchain, ensuring transparency and preventing manipulation. This democratic approach gives stakeholders direct control over platform evolution.
On chain governance tokens represent voting power within decentralized exchange ecosystems. Token holders can vote on proposals proportionally to their holdings, with one token typically equaling one vote. Many protocols also support delegation, allowing holders to assign voting power to trusted representatives. These tokens are often earned through liquidity provision or purchased on secondary markets. The token-weighted voting model ensures those with significant protocol investment have corresponding influence over decisions.
Snapshot voting captures token balances at a specific block height and conducts votes off-chain, reducing gas costs while maintaining verifiable results. On chain voting executes the entire process through smart contracts, including vote recording and proposal execution. Snapshot is preferred for gauging community sentiment, while on chain voting is essential for binding decisions that modify protocol parameters. Many DEXs use both methods in sequential On chain governance stages.
The complete On chain governance cycle typically spans 7 to 14 days depending on protocol design. Initial discussion phases last 3 to 5 days, followed by formal voting periods of 3 to 7 days. After approval, timelock delays of 24 to 72 hours provide security buffers before execution. Emergency proposals may have expedited timelines, while major protocol upgrades often require extended deliberation periods to ensure thorough community review and participation.
On chain governance systems employ multiple security layers including quorum requirements, timelock delays, and guardian multisigs. Quorum thresholds ensure sufficient participation before proposals pass. Timelocks create windows for security review and emergency intervention. Guardian committees can pause suspicious proposals. Additional protections include vote delegation limits, proposal spam prevention through deposit requirements, and formal verification of On chain governance contract code before deployment.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







