Key Takeaways
- Deterministic wallet architecture exists to solve scalability and key-lifecycle fragility, not merely to simplify backups or improve user experience. Its primary value is architectural resilience.
- HD wallet architecture uses derivation trees to organize authority, not just to generate keys. Hierarchy provides structural meaning, isolation boundaries, and long-term recoverability.
- Derivation paths act as formal contracts, encoding intent, chain separation, and account structure. Incorrect or inconsistent path usage creates recovery ambiguity that may surface years later.
- Multi-chain wallets require strict derivation separation. Shared ancestry across chains introduces authority bleed, especially on networks using the same cryptographic curves.
- Recovery restores cryptographic authority, not historical context. Deterministic regeneration brings keys back but labels, intent, and usage semantics are permanently lost without external metadata.
- Determinism centralizes both strength and risk at the root. While it dramatically simplifies recovery, any compromise of the seed results in irreversible, system-wide authority loss.
Deterministic wallets are usually explained in a very narrow way, generate a seed phrase, derive keys, back up once, and you’re done. While this explanation is convenient for beginners, it hides the real reason deterministic wallets exist and the architectural consequences they introduce.
In reality, determinism is not a feature added for user comfort. It is a structural response to deep scalability, security, and lifecycle problems that early wallet designs could not solve. Once you understand this, BIP-32 and BIP-39 stop being “standards to follow” and start looking like architectural constraints that shape everything built on top of them.
According to the Bitcoin Wiki , a deterministic wallet is defined as a system that derives all cryptographic keys from a single seed, enabling easy backup and restoration without storing individual keys. This means users only need to secure the seed to regenerate the entire wallet structure, and modern wallets universally adopt hierarchical deterministic (HD) wallet architecture based on BIP-32 derivation.
This article explores deterministic wallet architecture beyond the basics. It focuses on why determinism exists, how derivation structures behave at scale, and where deterministic models succeed and fail in real-world wallet systems. The discussion is intentionally practical, written in clear language, and grounded in officially defined standards rather than marketing abstractions.
What Is a Deterministic Wallet?
A deterministic wallet is a cryptocurrency wallet in which all private keys and public addresses are mathematically derived from a single master secret, commonly represented as a human-readable seed phrase. Instead of generating and storing independent private keys for each address, deterministic wallet architecture ensures that every key is a predictable output of the original seed.
This means wallet recovery does not depend on backing up individual keys. Restoring the seed allows the entire wallet to be reconstructed, including all past and future addresses, provided the same derivation logic is used. As defined by Bitcoin Wiki, this model eliminates key-by-key backup requirements and dramatically simplifies long-term key management.
Why Determinism Exists as an Architectural Constraint
Before deterministic wallets, most cryptocurrency wallets were non-deterministic. Each new address meant a new private key that had to be generated, stored, and backed up independently. This approach worked for early experimentation but failed almost immediately at scale.
Wallet scalability without persistent key storage
Early wallet systems failed to scale because each newly generated address introduced a new private key that had to be stored, protected, and preserved indefinitely. According to Investopedia [1] , this model significantly increased the risk of irreversible loss as wallet activity grew. Deterministic wallets inverted this relationship by eliminating persistent key storage entirely.
Instead, a single seed becomes the authoritative root from which all keys are mathematically regenerated. Backup size remains constant regardless of address volume, transaction frequency, or wallet lifespan. This property is the reason HD wallet architecture became mandatory for exchanges, custodial services, DeFi platforms, and enterprise treasury systems.
Authority regeneration vs authority duplication
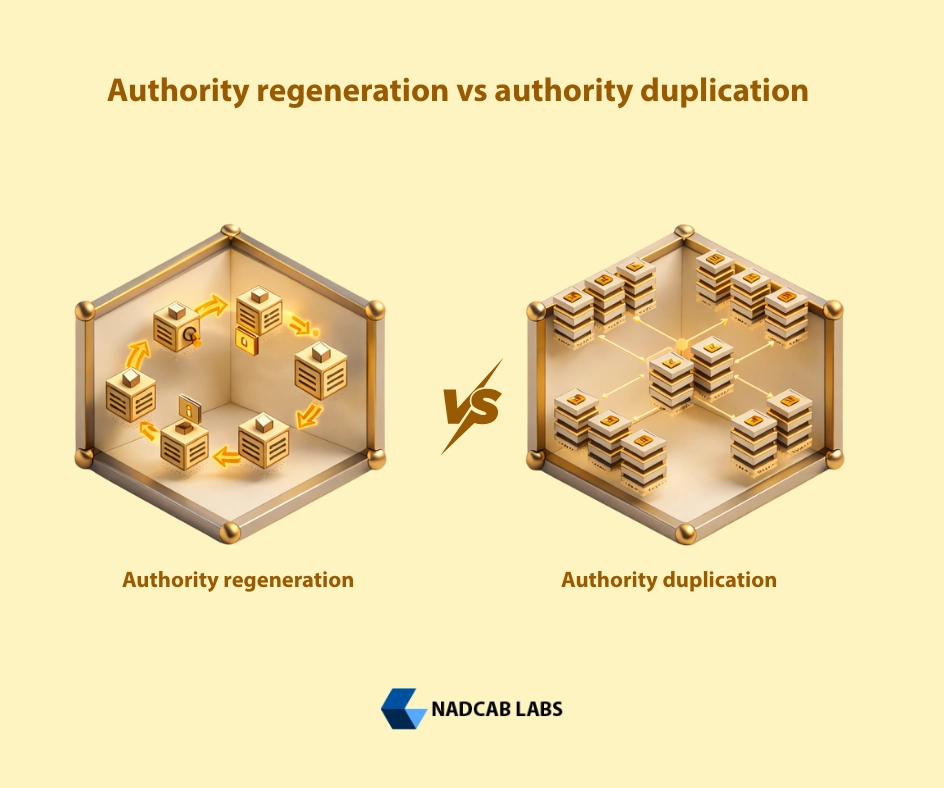
Non-deterministic wallets duplicate authority by creating independent private keys that must each survive indefinitely. Every additional key expands the failure surface.
BIP-32 formalized a fundamentally different model, authority is not stored, it is re-derived. As defined in the official BIP-32 specification, hierarchical deterministic wallets allow selective derivation of child keys while maintaining a mathematically reconstructable root of authority. This regeneration-based model provides resilience that duplication-based systems cannot achieve.
Determinism as a response to key lifecycle fragility
Academic cryptography research supports deterministic wallet architecture as a response to key lifecycle complexity. A 2019 paper published on arXiv explains that managing independent cryptographic keys across creation, backup, recovery, and retirement stages dramatically increases failure probability.
Deterministic wallets compress the entire lifecycle into a single critical security event: seed generation. After this point, all keys are deterministic outputs rather than independent secrets. This structural simplification is one of the most underappreciated strengths of HD wallet architecture.
| Dimension | Deterministic Wallet | Non-Deterministic Wallet |
|---|---|---|
| Backup size | Constant | Grows over time |
| Recovery model | Mathematical regeneration | Archival restoration |
| Scalability | High | Operationally limited |
| Failure surface | Concentrated at root | Distributed across keys |
The Derivation Tree as a Structural System
A common misunderstanding is to think of derivation trees as simple key generators. Architecturally, they are much more than that. A derivation tree is a formal system for organizing authority.
Hierarchical key spaces and namespace partitioning
Hierarchical derivation is not merely a convenience mechanism but a deliberate authority-partitioning strategy. BIP-44 defines how derivation paths encode logical boundaries between blockchains, accounts, and address roles.
Each hardened layer reduces the scope of authority exposure and prevents cross-domain inference. This structure allows deterministic wallet architecture to scale horizontally (many addresses) while preserving vertical isolation (distinct purposes).
Depth, breadth, and collision containment
Depth in a derivation tree represents specialization. Breadth represents scale. Increasing depth reduces semantic ambiguity, while controlled breadth limits discovery cost and scanning complexity.
A well-designed tree localizes mistakes. A poorly designed one spreads them.
Why flat derivation models fail at scale
Flat derivation models lack semantic structure, making it difficult to reason about ownership, recovery boundaries, or address purpose at scale. Documentation from the HD Wallet open-source project explains that flat models increase the risk of index reuse, complicate recovery scans, and reduce compatibility across wallet implementations. Hierarchical derivation introduces intentional structure, allowing wallets to infer meaning from position rather than external metadata. At scale, hierarchy becomes a necessity rather than an optimization.
Path Semantics and Authority Segmentation
Derivation paths are not arbitrary strings. They encode meaning.
Logical meaning encoded into derivation paths
A standard path such as m / purpose’ / coin_type’ / account’ / change / address_index exists because each level narrows authority scope. This structure is formally defined in BIP-44 and extended by later standards.
Isolation of chains, accounts, and purposes
Correct path semantics allow wallets to isolate:
- Blockchains (via coin_type)
- User accounts
- Change and external addresses
This isolation is enforced structurally, not by application logic, which is why HD wallet architecture remains robust across implementations.
Consequences of ambiguous or reused path segments
Improper path reuse rarely causes immediate loss. Instead, it causes delayed recovery ambiguity. These failures often surface years later, when users attempt restoration on new wallet software.
Multi-Chain Derivation Without Authority Bleed
Modern wallets almost always support multiple blockchains. This dramatically increases architectural risk.
Chain-specific branches vs shared ancestry
The SLIP-0044 registry, assigns unique coin type identifiers to blockchains to prevent cross-chain derivation collisions. This registry ensures that identical address indices on different networks do not share cryptographic ancestry. Without this enforced separation, wallets risk authority bleed where compromise on one chain may expose assets on another, particularly on networks that reuse elliptic curves such as secp256k1.
Address collision risk across heterogeneous protocols
Some chains reuse cryptographic curves or address encodings. Without strict derivation separation, the same public key may be valid on multiple networks.
Why naïve multi-chain derivation compromises isolation
Deriving multiple chains from the same non-hardened branch can cause authority bleed. A compromise in one context may expose others.
Deterministic Expansion and Unbounded Address Space

Deterministic wallets provide effectively infinite address space. Practically, this introduces discoverability constraints.
Forward derivation guarantees and discoverability limits
Wallets must know how far to scan the derivation tree during recovery. BIP-44 defines a gap limit to balance completeness and performance.
Address gap management and scan boundaries
Wallet recovery is constrained by discoverability limits rather than cryptographic loss. Cardano [2] and Ledger documentation highlight that deterministic wallet architecture relies on disciplined address usage. Funds can remain on-chain yet become invisible if wallets exceed tracked gap limits. Typically 20 unused addresses, to determine when scanning should stop during recovery. This boundary balances performance and completeness but introduces architectural risk if wallets generate addresses beyond tracked usage. Funds remain on-chain but may become invisible during recovery, underscoring that determinism assumes disciplined derivation tracking.
Failure modes when derivation space grows untracked
These failures are architectural, not cryptographic. They break assumptions, not keys.
Determinism Vs Privacy and Observability
Determinism improves recoverability but introduces observability risks.
Linkability introduced by shared roots
All derived addresses share a common ancestor. Predictable path structures can allow observers to correlate activity.
Structural leakage through predictable paths
Industry analysis from blockchain research firms highlights that deterministic derivation introduces observability risks due to shared ancestry across addresses. It standardized derivation paths improve interoperability but also enable behavioral clustering when address usage patterns are predictable. Wallet designers must consciously balance recoverability against privacy by segmenting accounts or altering derivation strategies.
Architectural trade-offs between recoverability and privacy
Some wallets mitigate linkability by segmenting accounts or varying derivation usage, at the cost of recovery simplicity.
Recovery Is a Structural Assumption, Not a Feature
Recovery is often marketed as functionality. Architecturally, it is assumed.
Deterministic regeneration versus historical knowledge loss
Recovered wallets regenerate keys but not context. Labels, intent, and usage history may be permanently lost.
Why derivation correctness matters more than backups
If derivation logic is wrong, backups are useless. Determinism amplifies implementation errors.
Inability to infer intent from regenerated keys
Recovered keys are indistinguishable without metadata. Authority returns, meaning does not.
Architectural Limits of Deterministic Wallets
Determinism is powerful, but limited.
What determinism cannot protect against
- Malware on compromised devices
- Social engineering attacks
- Root seed exposure
Irreversible damage from root compromise
If the root seed is leaked, all derived authority is compromised permanently.
When deterministic structure amplifies failure
Because authority is centralized at the root, failures propagate instantly.
Downstream Architectural Consequences of Derivation Design
Derivation decisions affect everything built on top of wallets.
Impact on address abstraction models
Smart wallets and account abstraction systems must align with or intentionally bypass deterministic assumptions.
Constraints imposed on multi-chain wallet cores
Wallet cores must reconcile multiple derivation standards under one recovery model.
Why derivation mistakes propagate system-wide
Once funds exist under flawed derivation rules, migration becomes expensive or impossible.
To summarize the structural components involved, the following table consolidates the critical elements discussed throughout the article.
| Component | Architectural Role | Failure Impact |
|---|---|---|
| Seed (BIP-39) | Root entropy source | Total authority loss |
| Master key (BIP-32) | Authority root | Global compromise |
| Derivation path | Structural contract | Recovery ambiguity |
| Gap limit | Discoverability boundary | Hidden funds during recovery |
The Future of Deterministic Wallet Architecture
Industry research indicates that hierarchical deterministic wallets dominate modern key management. Estimates suggest over 85% of actively maintained wallets rely on BIP-32-based HD wallet architecture for scalability and recovery.
Build My Crypto wallet Now!
Turn your dream into reality with a powerful, secure crypto wallet built just for you. Start building now and watch your idea come alive!
As account abstraction, smart wallets and contract-based authority models evolve, wallet architecture remains the foundational recovery mechanism that newer systems must either extend or intentionally replace. This makes HD wallet architecture not just a legacy standard, but a structural baseline for the next generation of blockchain wallet design.
Frequently Asked Questions
A Deterministic Wallet is a cryptocurrency wallet that generates all private keys and addresses from a single master seed. Instead of storing multiple private keys, the wallet mathematically derives every key from that seed, making backup and recovery simpler and more reliable.
An HD Wallet is a type of Deterministic Wallet that organizes derived keys into a hierarchical tree structure. While all HD wallets are deterministic, not all wallets are hierarchical. HD wallets follow standards like BIP-32 and BIP-44, enabling better account separation and scalability.
It works by using a cryptographic seed to generate a master key. From this master key, child keys and addresses are derived using predefined mathematical functions. As long as the seed is secure, the entire wallet can be regenerated on any compatible device.
An HD Wallet improves security by eliminating the need to store multiple private keys. Instead, only the seed must be protected. Additionally, hierarchical derivation allows wallets to isolate accounts and addresses, reducing the risk of key reuse and limiting exposure if one branch is compromised.
If you lose the seed phrase of your HD Wallet, you permanently lose access to all derived private keys and funds. Because deterministic wallets regenerate keys mathematically, there is no recovery mechanism without the seed. This makes secure seed backup critical.
Yes, it can support multiple blockchains when combined with HD wallet architecture. Using standards like BIP-44 and SLIP-0044, different blockchains are separated into distinct derivation paths, preventing cross-chain key conflicts and authority leakage.
It improves usability but introduces privacy trade-offs. Since all addresses share a common root, blockchain observers may link addresses through behavioral patterns. HD wallets mitigate this risk by using multiple accounts and structured derivation paths.
A derivation path in an HD Wallet defines how keys are generated from the master seed. Paths like m/44’/0’/0’/0/0 encode information such as blockchain type, account number and address role. This structure allows deterministic recovery and logical authority separation.
The gap limit defines how many unused addresses an HD Wallet will scan during recovery. If addresses are generated beyond this limit without activity, funds may not appear during recovery. This is an architectural limitation, not a cryptographic failure.
Yes, in most cases an HD Wallet is superior to a non-deterministic wallet. HD wallets offer constant backup size, easier recovery, better scalability and structured key management, whereas non-deterministic wallets require backing up every individual private key.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.