Key Takeaways
✓ Custodial wallet architecture requires strategic fund separation across hot, warm, and cold storage to balance security with operational efficiency
✓ Hot wallets (2-5% of assets) enable instant operations but carry highest risk; cold storage (75-85%) secures bulk assets offline
✓ Multi-signature and MPC technologies eliminate single points of failure in private key management
✓ Defense-in-depth security layers, comprehensive audit trails, and tested disaster recovery procedures are non-negotiable
✓ Architecture must evolve with scale, regulatory requirements, and emerging threats while maintaining security guarantees
What Is Custodial Wallet Architecture?
In the simplest terms, custodial wallet architecture refers to the technical framework and security infrastructure that enables organizations to hold, manage, and secure digital assets on behalf of their users. Unlike keeping cash in your physical wallet, digital assets require complex key management systems, multi-layered security protocols, and strategic fund distribution across different cryptocurrency wallet types.
After working with over 40 exchanges and fintech platforms in the past eight years, we’ve observed that proper custodial wallet architecture is what separates platforms that thrive from those that become security breach headlines. The architecture determines how private keys are generated, stored, and used to authorize transactions while maintaining the delicate balance between accessibility and security.[1]
Custodial vs Non-Custodial Wallets: The Core Difference
Custodial wallets mean a third party (exchange, platform, or service provider) holds the private keys and manages assets on users’ behalf. Users trust the custodian to secure their funds and execute transactions.
Non-custodial wallets give users complete control over their private keys. The principle “not your keys, not your crypto” applies here, where users bear full responsibility for security and recovery.
The architecture matters profoundly for businesses because it directly impacts operational risk, regulatory compliance, insurance eligibility, and customer trust. A single architectural flaw can expose millions of dollars in assets to theft or loss, as we’ve witnessed in numerous exchange hacks over the years.
Why Custodial Wallet Architecture Is Critical for Security
Centralized custody creates an inherent security challenge: aggregating large amounts of value in systems controlled by a single entity creates an attractive target for attackers. Throughout our years of consulting, we’ve analyzed dozens of security breaches, and the pattern is clear poor custodial wallet architecture amplifies risk exponentially.
Real-World Breach Examples
- Mt. Gox (2014): Lost 850,000 BTC due to hot wallet vulnerabilities and inadequate cold storage separation
- Coincheck (2018): $530 million stolen because most funds were kept in a hot wallet without multi-signature protection
- Bitfinex (2016): 120,000 BTC stolen through compromised multi-signature architecture
These incidents weren’t just technical failures they were architectural failures. The custodial wallet architecture didn’t implement proper separation of concerns, defense-in-depth strategies, or appropriate fund distribution models. When attackers compromised one layer, they gained access to everything.
Proper architecture reduces single-point-of-failure risks through segmentation, isolation, and graduated security controls. By distributing funds across hot, warm, and cold storage with different security parameters, platforms ensure that breaching one component doesn’t compromise the entire system.
Core Components of a Custodial Wallet System

Building effective custodial wallet architecture requires understanding four fundamental components that work together to create a secure, functional system. Each component plays a distinct role in the overall infrastructure.
User Accounts & Balance Management
The system maintains an internal database tracking each user’s balance across different assets. This off-chain ledger records deposits, withdrawals, trades, and transfers without requiring blockchain transactions for every internal movement. Users see their balances instantly, while the platform manages actual on-chain assets separately.
On-Chain Wallets vs Off-Chain Ledger
This distinction is crucial. The off-chain ledger is your internal accounting system fast, flexible, and under your complete control. On-chain wallets are actual blockchain addresses holding real assets. The architecture must maintain perfect synchronization between these two systems while minimizing on-chain transactions to reduce costs and latency.
Key Management Layer
This is the security heart of custodial wallet architecture. The key management layer handles generation, storage, rotation, and usage of private keys. It implements hierarchical deterministic (HD) wallet structures, key derivation protocols, and encryption standards that protect keys at rest and in transit.
Transaction Signing & Broadcasting
When transactions need to execute, this component retrieves appropriate keys, signs transactions according to blockchain protocols, and broadcasts them to the network. The architecture must ensure signing happens in secure environments with proper authorization checks and audit trails.
Understanding Wallet Separation Models
Wallet separation is the strategic practice of distributing funds across multiple crypto wallet types with different security profiles and accessibility levels. Think of it like managing cash flow in traditional banking—you don’t keep all company money in a cash register accessible to every cashier. Similarly, effective custodial wallet architecture segregates funds based on usage patterns and risk tolerance.
The three-tier model using hot, warm, and cold wallets has emerged as the industry standard because it optimally balances security, liquidity, and operational efficiency. Each tier serves specific purposes and operates under different security assumptions.
How Fund Flow Works Across Wallet Layers
User Deposits → Initially land in hot wallets for immediate credit
Automated Sweep → Excess funds move from hot to warm wallets hourly/daily
Strategic Rebalancing → Warm wallets periodically consolidate to cold storage
Withdrawal Requests → Hot wallet serves immediate needs; warm wallet refills hot wallet; cold storage refills warm wallet when needed
This graduated approach ensures that attackers face increasing security barriers as they attempt to access larger portions of funds. Meanwhile, legitimate operations maintain the liquidity needed for daily business operations.
Hot Wallet Architecture Explained
Hot wallets are internet-connected wallets that enable immediate transaction execution. They’re the operational workhorses of custodial wallet architecture, handling user withdrawals, exchange operations, payment processing, and other activities requiring instant access to funds.
Purpose and Operational Role
In our implementations, hot wallets typically serve as the first point of contact for all user-facing transactions. When a user requests a withdrawal, the hot wallet processes it automatically without human intervention (within pre-set limits). This automation is essential for user experience but creates security challenges.
| Aspect | Details |
|---|---|
| Typical Fund Allocation | 2-5% of total assets (varies by platform size and withdrawal patterns) |
| Connectivity | Always online, connected to application servers |
| Transaction Speed | Immediate (seconds to minutes) |
| Primary Use Cases | User withdrawals, trading operations, automated payments |
| Risk Exposure | Highest – vulnerable to online attacks, API exploits, server compromises |
Advantages and Disadvantages
Pros: Hot wallets enable seamless user experience, support high-frequency operations, allow automated processing, and integrate easily with application logic. They’re essential for competitive platforms where withdrawal speed matters.
Cons: Constant internet connectivity exposes them to remote attacks. Private keys stored on connected servers face risks from malware, unauthorized access, and infrastructure vulnerabilities. Any security breach can result in immediate fund loss.
Security Controls for Hot Wallets
- Strict withdrawal limits per transaction and per time period
- IP whitelisting for servers authorized to request transactions
- Rate limiting to prevent rapid fund drainage
- Anomaly detection monitoring unusual transaction patterns
- Encrypted key storage using hardware security modules (HSMs) when possible
- Multi-signature requirements for transactions above certain thresholds
Warm Wallet Architecture Explained
Warm wallets occupy the middle ground in custodial wallet architecture, serving as a buffer layer between the convenience of hot wallets and the security of cold storage. This intermediate tier is where experienced architects add sophisticated risk management.
The warm wallet concept emerged from practical necessity. Platforms needed more funds available than hot wallets could safely hold, but moving funds from cold storage is operationally expensive and time-consuming. Warm wallets solve this by maintaining moderate liquidity with enhanced security.
Role in Liquidity Management
Warm wallets typically hold 10-20% of total assets, providing a reserve that can refill hot wallets throughout the day without touching cold storage. When hot wallet balances drop below thresholds, automated systems transfer funds from warm wallets. This happens within minutes rather than the hours required for cold storage access.
In high-volume scenarios we’ve managed, warm wallets prevent the operational bottleneck of constantly accessing cold storage while limiting hot wallet exposure. They act as a shock absorber for unexpected withdrawal spikes or trading volume surges.
Security Characteristics
Warm wallets use semi-automated processes with human oversight. Keys might be stored in hardware security modules (HSMs) in secure data centers, with transactions requiring manual approval for amounts above certain thresholds. They’re typically online but behind additional network security layers like VPNs and firewalls.
Pro Tip from Experience: Implement time-based locks on warm wallet transactions. Requiring a 10-30 minute delay before transaction broadcast gives security teams time to detect and prevent unauthorized transactions without significantly impacting operations.
Cold Wallet Architecture Explained
Cold wallets represent the security fortress of custodial wallet architecture, storing the majority of assets in completely offline environments. These wallets prioritize security over accessibility, using air-gapped systems, hardware security modules, and multi-layered approval processes.
After eight years of implementing custody solutions, we consistently recommend that platforms keep 75-85% of assets in cold storage. This allocation protects the bulk of funds from online threats while maintaining sufficient liquidity in hot and warm tiers.
Offline Key Storage Methods
Hardware Security Modules (HSMs): Enterprise-grade HSMs generate and store keys in tamper-resistant hardware that never exposes keys to external systems. These devices perform signing operations internally, outputting only signed transactions. Military-grade facilities often house these HSMs in secure vaults.
Air-Gapped Systems: Completely isolated computers that never connect to any network. Transactions are prepared on online systems, transferred via QR codes or USB drives to the air-gapped machine for signing, then transferred back for broadcasting. This manual process eliminates remote attack vectors entirely.
Multi-Location Geographic Distribution: Advanced implementations distribute key shares across multiple physical locations using Shamir’s Secret Sharing or multi-party computation. This protects against physical theft, natural disasters, and coercion of individual key holders.
Withdrawal Approval Workflows
Cold wallet access involves structured, auditable processes. A typical workflow requires:
- Financial operations team initiates withdrawal request with business justification
- Security team reviews request against transaction patterns and balance thresholds
- Multiple authorized signers (typically 3-5 executives) must approve using separate authentication devices
- Transaction is prepared and transmitted to air-gapped signing infrastructure
- Physical access to secure facility is logged and requires dual authorization
- Transaction signing occurs on offline devices
- Signed transaction is verified, then broadcast from quarantined online system
This process typically takes 6-24 hours, which is acceptable because cold storage should rarely need to move funds. The delay is a security feature, not a bug.
Hot vs Warm vs Cold Wallets: Comprehensive Comparison
Understanding the tradeoffs between wallet types is essential for designing effective custodial wallet architecture. This comparison table synthesizes years of operational data and security analysis:
| Characteristic | Hot Wallet | Warm Wallet | Cold Wallet |
|---|---|---|---|
| Internet Connectivity | Always online | Online but restricted | Completely offline |
| Security Level | Low – highest risk | Medium – moderate risk | High – minimal risk |
| Access Speed | Instant (seconds) | Quick (minutes to 1 hour) | Slow (6-24 hours) |
| Typical Fund Allocation | 2-5% of total assets | 10-20% of total assets | 75-85% of total assets |
| Primary Use Case | User withdrawals, daily operations | Hot wallet replenishment, liquidity buffer | Long-term asset storage, reserves |
| Automation Level | Fully automated | Semi-automated with oversight | Manual, multi-approval process |
| Key Storage | Encrypted on servers, sometimes HSMs | HSMs in secure data centers | Air-gapped HSMs, geographically distributed |
| Attack Surface | Large – exposed to internet threats | Medium – network segmentation reduces exposure | Minimal – only physical security concerns |
| Ideal For | Operational efficiency | Balance of security and liquidity | Maximum security |
This table serves as a decision-making framework when designing your custodial wallet architecture. The key is finding the right balance for your specific operational requirements and risk tolerance.
Fund Flow in Custodial Wallet Architecture
Understanding how funds move through your custodial wallet architecture is critical for both operations and security. The lifecycle of user funds involves multiple transitions across wallet tiers, each with different triggers and security implications.
User Deposit Flow
When users deposit cryptocurrency, it typically flows directly into hot wallet addresses. The platform’s blockchain monitoring system detects the incoming transaction, waits for required confirmations (e.g., 6 confirmations for Bitcoin, 12 for Ethereum), then credits the user’s account balance in the internal ledger. This deposit remains in the hot wallet until automated sweeping mechanisms trigger.
Automated Rebalancing Process
Typical Rebalancing Schedule
Hot → Warm (Every 6-24 hours): When hot wallet exceeds 5% of total assets, excess automatically transfers to warm wallet. These transactions use multi-signature requirements but execute without human intervention.
Warm → Cold (Daily or weekly): When warm wallet exceeds 20% threshold, consolidation to cold storage occurs. This requires manual approval but follows standardized procedures.
Cold → Warm (As needed): When warm wallet drops below operational minimum (usually 8-10% of assets), manual process initiates cold storage withdrawal to refill warm tier.
Warm → Hot (Hourly): Automated monitoring checks hot wallet levels every hour. If below minimum operational threshold (typically 2%), warm wallet automatically transfers predetermined amounts.
Withdrawal Execution Path
User withdrawal requests follow a priority waterfall. The system first checks hot wallet balance. If sufficient funds exist and the withdrawal meets automated approval criteria (amount, user verification level, withdrawal frequency), it executes immediately from hot wallet.
For larger withdrawals or when hot wallet liquidity is insufficient, the request queues until the next warm-to-hot transfer occurs. In rare cases of extreme withdrawal pressure, emergency procedures allow expedited warm or even cold wallet access, but these trigger additional security reviews.
Private Key Management in Custodial Wallets
Private key management represents the most critical security component of custodial wallet architecture. How you generate, store, access, and eventually retire keys determines whether your system remains secure or becomes the next cautionary tale.
Single-Key vs Multi-Key Custody
Traditional single-key custody means one private key controls wallet assets. While simpler to implement, this creates catastrophic single-point-of-failure risk. If that key is compromised, lost, or the key holder becomes unavailable, consequences are severe.
Multi-key custody distributes control across multiple parties. A 3-of-5 multi-signature configuration, for example, requires any three of five designated key holders to authorize transactions. This eliminates single-point vulnerabilities while maintaining operational flexibility.
Key Sharding Concepts
Advanced custodial wallet architecture implements Shamir’s Secret Sharing, which mathematically splits keys into multiple shares. You might create 7 shares where any 4 can reconstruct the key. Individual shares reveal nothing about the key. Distributing shares across geographic locations, different security personnel, and even different legal jurisdictions provides robust protection against coercion, disaster, and insider threats.
Role-Based Access Controls
Not everyone in your organization needs access to all wallet functions. Implementing role-based access control (RBAC) ensures people only have permissions necessary for their responsibilities. Junior operations staff might initiate withdrawal requests but can’t approve them. Security teams monitor transactions but can’t create them. Executive key holders can approve cold storage access but don’t handle daily operations.
Separation of duties is fundamental to custodial security. The person who creates a transaction shouldn’t be the person who approves it. The team monitoring security shouldn’t be the same team with key access. These controls prevent both insider fraud and reduce social engineering attack surfaces.
Multi-Signature and MPC in Custodial Wallet Architecture
Multi-signature (multisig) and Multi-Party Computation (MPC) represent two sophisticated approaches to distributed key management. Both technologies eliminate single points of failure, though they work quite differently under the hood.
How Multi-Signature Works
Multi-signature creates specialized blockchain addresses that require multiple signatures for transaction authorization. A 2-of-3 multisig address needs two out of three associated private keys to sign any transaction. This happens natively at the blockchain level—the blockchain itself enforces the multi-party requirement.
In our custodial implementations, we typically use multisig for warm and cold wallets. Hot wallets sometimes use 2-of-2 or 2-of-3 configurations, though this adds latency. The security benefit usually justifies this cost for high-value platforms.
Multi-Party Computation Advantages
MPC takes a different approach. Instead of creating multi-signature addresses, MPC distributes key generation and signing across multiple parties mathematically. Each party holds a key share that’s useless alone. When signing transactions, parties engage in cryptographic protocols that collectively create signatures without ever reconstructing the complete private key.
The advantage? MPC works with standard blockchain addresses, avoiding the complexity and sometimes limited support for multi-signature addresses. It’s also more flexible—you can dynamically change threshold requirements or add/remove parties without creating new blockchain addresses.
| Aspect | Multi-Signature | MPC |
|---|---|---|
| Address Type | Special multisig addresses | Standard addresses |
| Blockchain Support | Must be natively supported | Works with any blockchain |
| Key Storage | Complete keys distributed | Key shares never form complete key |
| Visibility | Publicly visible on blockchain | Looks like single-signature |
| Flexibility | Fixed at address creation | Can change thresholds dynamically |
Implementation Strategy
Many modern custodial wallet architectures combine both approaches. Hot wallets might use MPC for speed and flexibility. Cold wallets use multisig for transparency and auditability. The choice depends on your security requirements, supported blockchains, and operational workflows.
Security Layers in Custodial Wallet Architecture
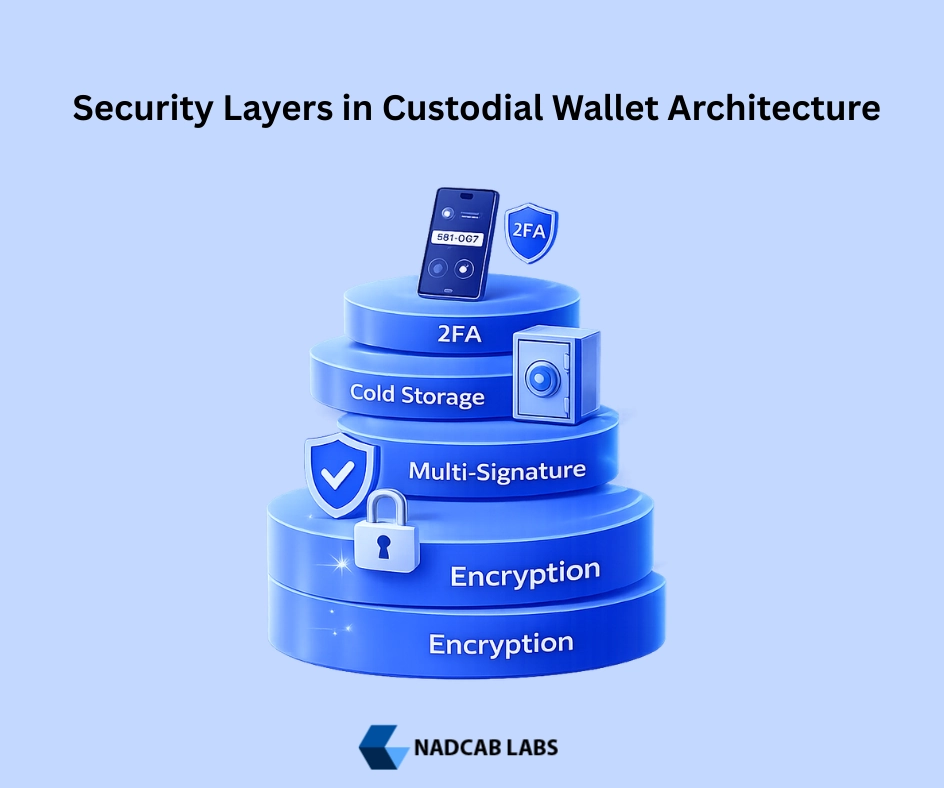
Defense-in-depth is not just a buzzword it’s a survival strategy. Effective custodial wallet architecture implements multiple overlapping security layers so that breaching one layer doesn’t compromise the entire system.[2]
Essential Security Controls
Hardware Security Modules (HSMs)
FIPS 140-2 Level 3 or higher certified HSMs generate and store cryptographic keys in tamper-evident, tamper-resistant hardware. These devices physically destroy keys if tampering is detected. For custodial platforms holding significant assets, HSMs are non-negotiable.
Network Segmentation & IP Whitelisting
Wallet infrastructure operates on isolated network segments with strict firewall rules. Only specific IP addresses from authorized servers can communicate with wallet services. VPNs with certificate-based authentication provide additional access control layers.
Withdrawal Limits & Velocity Controls
Per-transaction limits, daily/hourly velocity limits, and user-tier-based restrictions prevent rapid fund drainage. If someone compromises hot wallet access, they can’t instantly withdraw everything—rate limits give security teams time to respond.
Time Locks & Delayed Transactions
Implementing mandatory delays before transaction broadcast (10-30 minutes for warm wallets, several hours for cold storage) creates intervention windows. Automated monitoring can flag suspicious transactions during delay periods.
Manual Approval Workflows
High-value transactions or cold storage access requires human approval from multiple authorized parties. Approval requests include business context, and approvers verify legitimacy through separate communication channels.
Compliance & Audit Considerations
Custodial wallet architecture must support regulatory compliance and enable comprehensive auditing. These requirements influence system design from day one—retrofitting compliance is expensive and risky.
Transaction Monitoring Requirements
Regulators increasingly expect custodians to monitor for suspicious activity, money laundering, and sanction violations. Your architecture must log every transaction with sufficient metadata for investigation: user identifiers, transaction amounts, blockchain addresses, timestamps, approval chains, and risk scores.
Advanced implementations integrate with blockchain analytics providers to screen addresses against sanctions lists and known criminal entities. These checks happen before transaction execution, blocking transfers to flagged addresses.
Immutable Audit Trails
Every action affecting wallets must be logged immutably. Who accessed which systems when? Who approved what transactions? What key management operations occurred? These logs should be tamper-evident, ideally stored in append-only databases or even anchored to blockchains for cryptographic proof of integrity.
Proof of Reserves
Proving you actually hold the assets you claim requires carefully designed custodial wallet architecture. Platforms implement Proof of Reserves by creating cryptographic attestations that on-chain holdings match user balances without revealing sensitive information. This typically involves Merkle tree proofs allowing users to verify their specific balance is included in total reserves without exposing other users’ data.
Common Custodial Wallet Architecture Mistakes
Learning from others’ mistakes is cheaper than making them yourself. These are the most common architectural failures we’ve observed and remediated over the years.
Critical Mistake #1: Excessive Hot Wallet Holdings
Platforms often keep 15-30% of assets in hot wallets for operational convenience. This is dangerous. Every percentage point in hot wallets multiplies risk. We’ve seen exchanges lose months of revenue because they prioritized convenience over security.
Solution: Keep hot wallets at 2-5% maximum. Implement efficient warm wallet automation to maintain liquidity without hot wallet bloat.
Critical Mistake #2: Inadequate Access Controls
Giving too many people too much access creates insider risk and expands social engineering attack surfaces. We’ve investigated breaches where attackers simply asked employees for access credentials.
Solution: Implement strict least-privilege access. Regular access audits. Multi-factor authentication for all wallet operations. Separation of duties between transaction creation, approval, and execution.
Critical Mistake #3: No Withdrawal Throttling
Platforms that allow unlimited withdrawal rates enable attackers to drain wallets within minutes of compromise. Rate limiting is an essential safety mechanism.
Solution: Implement per-transaction limits, velocity controls, and anomaly detection. Unusual withdrawal patterns should trigger automatic holds and manual reviews.
Critical Mistake #4: Insufficient Key Backup
Losing private keys means losing assets permanently. Yet we’ve consulted for companies with inadequate backup procedures, single points of failure in key storage, or no tested recovery procedures.
Solution: Geographic distribution of encrypted key backups. Multiple independent backup methods. Regular recovery testing. Document and drill disaster recovery procedures.
Best Practices for Designing Custodial Wallet Architecture
After eight years of building and securing custodial systems handling billions in assets, these practices consistently separate successful platforms from compromised ones.
Optimal Fund Distribution
Based on extensive operational data and risk analysis, we recommend this allocation for most platforms:
- Hot Wallets: 2-5% – Sufficient for 24-48 hours of normal withdrawal activity
- Warm Wallets: 10-18% – Buffer for 1-2 weeks of elevated withdrawal activity
- Cold Storage: 77-88% – Bulk of assets secured offline
Adjust these ratios based on your withdrawal patterns, user base, and insurance coverage. High-frequency trading platforms might need slightly higher hot wallet allocations. Long-term custody providers can safely operate with lower hot/warm allocations.
Defense-in-Depth Approach
Layer security controls so multiple failures must occur simultaneously for breach success. Combine technical controls (HSMs, encryption, network segmentation) with procedural controls (approval workflows, access reviews) and personnel controls (background checks, separation of duties).
Automation vs Human Approval Balance
Automate routine, low-risk operations to maintain efficiency. Require human judgment for high-risk activities. The threshold varies by platform, but generally: automate hot wallet operations under $50K-$100K per transaction, require approval for warm wallet movements, and mandate multi-party approval for all cold storage access.
Disaster Recovery Planning
Test your custodial wallet architecture’s resilience regularly. Simulate key loss scenarios. Practice cold storage recovery procedures. Conduct tabletop exercises for security breaches. Document runbooks for every emergency scenario. The time to discover your disaster recovery plan doesn’t work is not during an actual disaster.
Scalability Challenges in Custodial Wallet Systems
As platforms grow, custodial wallet architecture faces increasing technical and operational challenges. What works for 10,000 users managing $10 million doesn’t scale to 1 million users and $1 billion in assets.
Multi-Blockchain Support Complexity
Modern platforms support dozens of blockchains and hundreds of tokens. Each blockchain has unique characteristics—different confirmation requirements, gas mechanisms, transaction formats, and security considerations. Your custodial wallet architecture must abstract these differences while maintaining security guarantees across all supported assets.
We’ve built systems managing 50+ blockchains simultaneously. The key is creating a unified wallet abstraction layer that handles blockchain-specific details internally while presenting consistent interfaces to application logic.
High Withdrawal Volume Handling
Peak withdrawal periods stress wallet infrastructure. Black swan market events can trigger 10-50x normal withdrawal volumes. Your architecture must handle these spikes without manual intervention or service degradation. This requires over-provisioning hot wallet capacity, robust warm wallet automation, and prioritization algorithms for withdrawal queue management.
Gas Optimization Strategies
Transaction fees significantly impact profitability at scale. Custodial wallet architecture should implement UTXO consolidation for Bitcoin-like chains during low-fee periods. For Ethereum, batch user withdrawals into single transactions when possible. Monitor mempool conditions and dynamically adjust gas prices to optimize for cost vs. confirmation speed.
Custodial Wallet Architecture for Different Use Cases
Different business models require customized approaches to custodial wallet architecture. A payment processor has different requirements than a trading exchange or institutional custody provider.
Exchange-Specific Requirements
Cryptocurrency exchanges need extremely high liquidity for market making, user trading, and withdrawals. Their architecture emphasizes hot and warm wallet capacity with sophisticated liquidity management. Exchanges typically maintain higher hot wallet percentages (4-7%) due to 24/7 trading operations and instant withdrawal expectations. They also require specialized infrastructure for market making wallets that interact directly with trading engines.
Payment & Remittance Platforms
Payment platforms prioritize transaction speed and integration with point-of-sale systems or payment gateways. Their custodial wallet architecture emphasizes automation, webhook integrations, and real-time balance updates. Security requirements focus on preventing transaction fraud rather than protecting large asset reserves. These platforms often maintain 10-15% in hot wallets for operational velocity.
Institutional Custody Differences
Institutional custodians serving hedge funds, family offices, and corporate treasuries prioritize security, compliance, and auditability over transaction speed. Their custodial wallet architecture heavily emphasizes cold storage (often 90-95% of assets), comprehensive audit trails, and white-glove service for client withdrawals. Multi-signature and MPC implementations are standard, with institutional clients often participating directly in key management protocols.
Future of Custodial Wallet Architecture
The field continues evolving rapidly. Emerging technologies and regulatory developments shape where custodial wallet architecture is heading.
Zero-Trust Custody Models
Next-generation architectures assume every component is potentially compromised. Zero-trust designs require continuous verification, microsegmentation, and cryptographic attestation at every layer. Rather than traditional perimeter security, these systems verify every access request as if it originates from an untrusted network.
AI-Driven Risk Detection
Machine learning models increasingly monitor transaction patterns, detecting anomalies that rules-based systems miss. Advanced implementations use behavioral biometrics, analyzing user transaction patterns to identify account takeovers or fraudulent activity. AI systems can dynamically adjust security levels based on real-time risk assessment.
Policy-Based Transaction Execution
Future custodial wallet architecture will implement sophisticated policy engines that evaluate transactions against complex rule sets. These policies can consider transaction amount, destination address reputation, user verification level, current market conditions, and historical patterns to automatically approve, flag, or reject transactions.
On-Chain Proof-of-Solvency Systems
Regulatory pressure and user demand drive development of real-time, cryptographically verifiable proof of reserves systems. Next-generation architectures will integrate proof-of-solvency as core functionality, allowing continuous, automated attestation that on-chain holdings match user balances without compromising privacy.
Build My Crypto wallet Now!
Turn your dream into reality with a powerful, secure crypto wallet built just for you. Start building now and watch your idea come alive!
When to Choose Custodial Wallet Architecture
Understanding when custodial architecture makes sense versus alternatives helps businesses make informed platform decisions.
Ideal Use Cases for Custodial Models
- Exchanges and trading platforms where users expect instant liquidity and trading execution
- Payment processors requiring fast transaction settlement and business integrations
- Institutional custody services providing regulated asset management
- Mass-market apps where key management complexity would harm user experience
- Business treasuries needing multi-approval workflows and compliance integration
When Non-Custodial Is Better
Non-custodial architectures suit applications where users value sovereignty and decentralization over convenience. DeFi protocols, privacy-focused applications, and platforms serving cryptocurrency-native users often adopt non-custodial models. These architectures eliminate custodian risk but transfer security responsibility entirely to users.
Hybrid Custody Models
Increasingly, platforms implement hybrid approaches. Users can choose between custodial convenience and non-custodial control. Some platforms use custodial architecture for smaller balances while encouraging users to move larger holdings to non-custodial storage. Others implement smart contract-based custody where users retain ultimate control through recovery mechanisms while enjoying platform convenience.
Building secure custodial wallet architecture requires balancing competing demands security vs. convenience, automation vs. control, cost vs. redundancy. With eight years of experience implementing these systems for platforms managing billions in assets, we’ve learned that successful architecture isn’t about choosing perfect solutions but rather implementing layered protections that fail gracefully and maintain security even when individual components are compromised. The principles outlined in this guide provide a foundation for building custodial systems that protect user assets while enabling the operational efficiency modern platforms require.
Frequently Asked Questions
Custodial wallet architecture is the system design where a platform manages users’ private keys and funds using a structured setup of hot, warm, and cold wallets to balance security, liquidity, and operational efficiency.
Wallet separation minimizes risk by limiting internet exposure. Hot wallets handle daily transactions, warm wallets act as a buffer for liquidity, and cold wallets store the majority of funds offline for maximum security.
Most custodial platforms keep only 1–5% of total funds in hot wallets. This amount is carefully calculated to support withdrawals while minimizing potential losses from online security threats.
A warm wallet serves as an intermediate layer between hot and cold wallets, enabling controlled fund transfers, rebalancing liquidity, and reducing the frequency of direct access to cold storage systems.
Cold wallets significantly reduce online attack risks, but they are not risk-free. Proper access controls, multi-signature approvals, secure backups, and operational procedures are essential to maintain cold wallet security.
Private keys are managed using secure key management systems such as Hardware Security Modules (HSMs), multi-signature setups, or Multi-Party Computation (MPC) to prevent single-point key compromise.
Multisig requires multiple private keys to approve transactions on-chain, while MPC splits a single private key into encrypted shares that never fully exist in one place, improving security and flexibility.
Withdrawals typically involve internal ledger checks, risk scoring, withdrawal limits, multi-layer approvals, and transaction signing through hot or warm wallets, with cold wallets used only for controlled fund replenishment.
Yes, modern custodial wallet architectures are designed to be multi-chain, supporting assets across Ethereum, Bitcoin, Solana, and other networks through unified key management and transaction processing layers.
Custodial wallet architecture is widely used by regulated exchanges and fintech platforms because it supports compliance, audit trails, transaction monitoring, and policy-based controls required by financial regulators.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.






