Key Takeaways
- Crypto wallet infrastructure forms the backbone of secure digital asset management, directly impacting transaction speed, security, and user trust across global markets.
- Hybrid hosting strategies combining cloud flexibility with on-premise security offer optimal balance for enterprise wallet providers serving regulated markets.
- AWS, GCP, and Azure each offer unique advantages for crypto wallet infrastructure, with region selection critical for latency optimization and compliance.
- Horizontal scaling with auto-scaling capabilities ensures crypto wallets handle traffic spikes during market volatility without performance degradation.
- Redis and Memcached caching layers reduce database load by 70-90%, dramatically improving response times for balance queries and transaction history.
- Hardware Security Modules and secure signing environments are non-negotiable components for protecting private keys in production wallet systems.
- Multi-region deployments with automated failover achieve 99.99% uptime targets essential for maintaining user trust in cryptocurrency platforms.
- Monitoring transaction success rates, RPC latency, and node synchronization status enables proactive identification of infrastructure issues.
- Data residency requirements vary significantly between USA, UK, UAE, and Canada, requiring infrastructure designed for regulatory compliance from inception.
- AI-driven scaling and serverless architectures represent the future of crypto wallet infrastructure, enabling cost optimization and rapid deployment.
1
Introduction to Crypto Wallet Infrastructure
What Crypto Wallet Infrastructure Means in Real-World Systems
Crypto wallet infrastructure encompasses the complete technical ecosystem required to store, manage, and transact digital assets securely. This includes everything from the physical servers hosting your application to the blockchain nodes validating transactions, the databases storing user information, and the security systems protecting private keys. In real-world implementations serving markets across the USA, UK, UAE, and Canada, this infrastructure must handle millions of concurrent users while maintaining sub-second response times and bulletproof security.
Understanding crypto wallet infrastructure requires recognizing that every component plays a critical role in the user experience. When a user in Dubai initiates a transaction at 3 AM local time, your infrastructure must process that request with the same speed and reliability as during peak trading hours in New York. This demands thoughtful architecture decisions, redundant systems, and constant monitoring across all infrastructure layers.
Why Infrastructure Defines Wallet Reliability
The reliability of any cryptocurrency wallet directly correlates with the quality of its underlying infrastructure. Our agency has witnessed firsthand how infrastructure decisions made during initial planning phases echo throughout a platform’s entire lifecycle. Poor infrastructure choices lead to transaction failures during high-volume periods, security vulnerabilities that hackers exploit, and compliance gaps that regulators penalize. Conversely, well-architected crypto wallet infrastructure provides the foundation for scaling to millions of users without compromising performance or security.
Consider the real-world implications: a wallet experiencing 99% uptime sounds impressive until you calculate that 1% downtime translates to over 87 hours annually where users cannot access their funds. In cryptocurrency markets operating 24/7 with significant price volatility, even minutes of downtime can cost users substantial money and permanently damage trust. This is why enterprise-grade crypto wallet infrastructure targets 99.99% availability as a minimum standard[1].
2
Core Components of Crypto Wallet Infrastructure
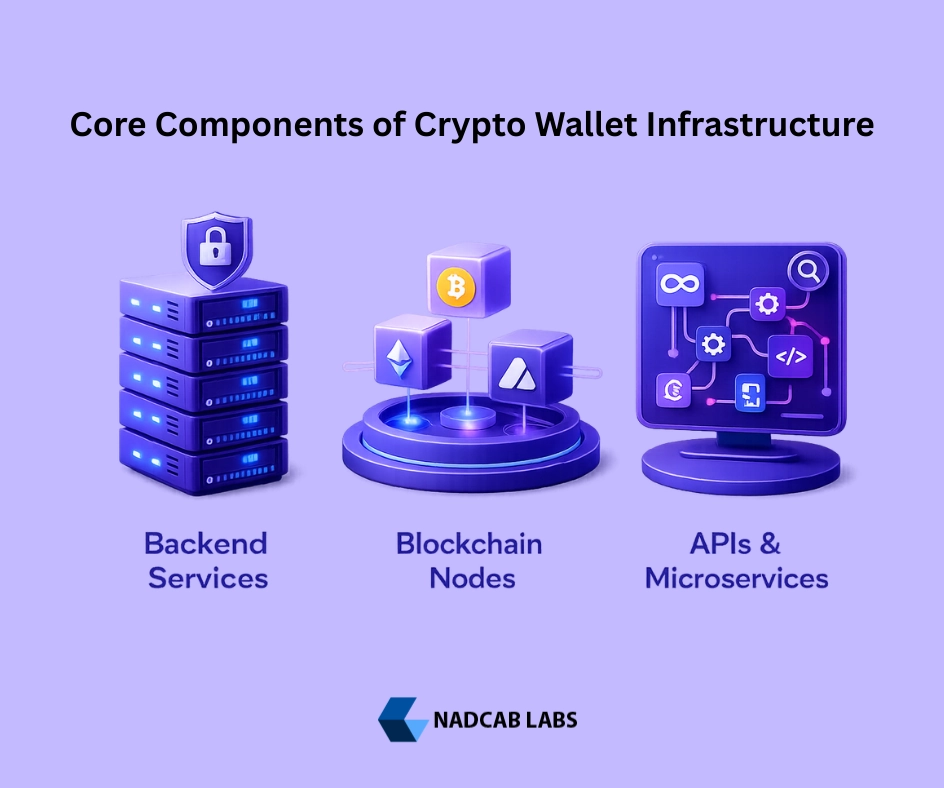
Backend Services
Core processing engine for wallet operations
- ✓ Transaction processing and validation
- ✓ User authentication and session management
- ✓ Balance calculation and portfolio tracking
- ✓ Webhook and notification services
Blockchain Nodes
Direct connection to blockchain networks
- ✓ Transaction broadcasting to networks
- ✓ Block synchronization and validation
- ✓ Address balance verification
- ✓ Smart contract interaction
APIs & Microservices
Modular architecture for scalability
- ✓ RESTful and GraphQL endpoints
- ✓ Rate limiting and request throttling
- ✓ Service mesh for inter-service communication
- ✓ API versioning and deprecation management
The integration of these core components determines how effectively your crypto wallet infrastructure handles real-world demands. Backend services must communicate seamlessly with blockchain nodes while APIs provide the interface for client applications. In our experience building wallet solutions for clients across North America, Europe, and the Middle East, the most successful implementations treat these components as an interconnected ecosystem rather than isolated units. Each service should be independently deployable yet collectively reliable.
3
Hosting Models for Crypto Wallet Infrastructure
Cloud Hosting vs On-Premise
The cloud versus on-premise decision fundamentally shapes your crypto wallet infrastructure strategy. Cloud hosting through providers like AWS, Google Cloud, or Azure offers unparalleled scalability, allowing infrastructure to expand dynamically during market volatility when transaction volumes spike unexpectedly. This elasticity proves invaluable for wallet providers serving global markets where usage patterns vary dramatically across time zones. Cloud platforms also reduce operational overhead by managing hardware maintenance, security patches, and network infrastructure.
On-premise infrastructure provides maximum control over hardware, data, and security configurations. Organizations handling extremely sensitive private key operations often prefer on-premise solutions where they maintain complete physical access to servers. Regulatory requirements in certain jurisdictions, particularly for institutional custody services in the UK and Canada, may mandate specific data sovereignty controls more easily achieved with on-premise deployments. The trade-off involves significantly higher capital expenditure and operational complexity.
Hybrid Hosting Strategies for Wallets
Hybrid hosting represents the optimal approach for most enterprise crypto wallet infrastructure deployments. This strategy places security-critical components like HSMs and key signing services on-premise while leveraging cloud resources for scalable application layers, user-facing APIs, and non-sensitive data processing. The hybrid model enables organizations to satisfy strict security requirements while maintaining the flexibility needed to handle variable workloads efficiently.
Hosting Model Comparison
95%
98%
92%
85%
97%
94%
4
Choosing the Right Cloud Provider for Crypto Wallet Infrastructure
AWS, GCP, Azure Comparison
Selecting the optimal cloud provider for your crypto wallet infrastructure requires careful evaluation of each platform’s strengths relative to your specific requirements. Amazon Web Services dominates market share and offers the most comprehensive service catalog, including specialized blockchain services through Amazon Managed Blockchain. Google Cloud Platform excels in data analytics and machine learning capabilities, valuable for fraud detection and transaction pattern analysis. Microsoft Azure provides superior integration with enterprise systems and maintains strong compliance certifications attractive to institutional clients.
| Feature | AWS | Google Cloud | Azure |
|---|---|---|---|
| Global Regions | 32+ | 37+ | 60+ |
| HSM Support | CloudHSM | Cloud HSM | Dedicated HSM |
| Blockchain Services | Managed Blockchain | Web3 Hosting | Azure Blockchain |
| Kubernetes Support | EKS | GKE | AKS |
| Cost Structure | Pay-as-you-go | Sustained discounts | Enterprise agreements |
Region Selection for Latency Optimization
Geographic region selection directly impacts user experience through network latency. For crypto wallet infrastructure serving North American users, deploying primary resources in US East (Virginia) and US West (Oregon) regions provides optimal coverage. UK-based users benefit from London region deployments, while UAE clients experience best performance from Bahrain or Mumbai regions. Our recommendation involves multi-region deployment with intelligent routing to direct users to the nearest available data center, reducing round-trip times from hundreds of milliseconds to under 50ms for most operations.
5
Blockchain Node Management in Crypto Wallet Infrastructure
Full Nodes vs Light Nodes
Full nodes maintain complete copies of blockchain data and independently validate all transactions, providing maximum security and reliability for crypto wallet infrastructure. However, full nodes require substantial computational resources: Bitcoin full nodes need over 500GB of storage and significant bandwidth, while Ethereum archive nodes can exceed 15TB. Light nodes, also known as SPV (Simplified Payment Verification) nodes, verify transactions using block headers without downloading complete blockchain data. This approach reduces resource requirements dramatically but introduces trust assumptions.
For production crypto wallet infrastructure, we recommend running dedicated full nodes for primary blockchain networks your wallet supports. Light nodes serve well for secondary networks or testing environments where reduced resource consumption outweighs security considerations. The choice significantly impacts infrastructure costs: a multi-chain wallet supporting Bitcoin, Ethereum, and several EVM-compatible networks might require dozens of node instances, each with specific resource profiles.
Dedicated vs Shared Nodes
Dedicated node infrastructure provides guaranteed performance and complete control over configuration, essential for enterprise crypto wallet infrastructure handling significant transaction volumes. Shared node services from providers like Infura, Alchemy, or QuickNode offer cost-effective alternatives for smaller operations or supplementary redundancy. Many organizations adopt hybrid approaches: dedicated nodes for primary operations with shared node providers as failover endpoints ensuring continuous service availability even during maintenance windows.
6
Database Architecture for Scalable Wallet Systems
Relational vs NoSQL
Database architecture decisions profoundly impact crypto wallet infrastructure performance and scalability. Relational databases like PostgreSQL excel at maintaining transactional integrity and handling complex queries involving user accounts, permissions, and financial records. NoSQL databases such as MongoDB or Cassandra provide superior horizontal scaling capabilities for high-volume data like transaction histories and blockchain event logs. Most production wallet systems employ polyglot persistence strategies, using different database technologies for different data types based on access patterns and consistency requirements.
| Data Type | Recommended DB | Scaling Strategy | Consistency Model |
|---|---|---|---|
| User Accounts | PostgreSQL | Vertical + Read Replicas | Strong |
| Transaction History | Cassandra | Horizontal Sharding | Eventual |
| Session Data | Redis | Cluster Mode | Eventual |
| Blockchain Events | TimescaleDB | Time-based Partitioning | Strong |
| Analytics Data | ClickHouse | Column-based Sharding | Eventual |
Handling Transaction History and Balances
Transaction history storage represents one of the most challenging aspects of crypto wallet infrastructure database design. Active wallets can accumulate thousands of transactions over time, and users expect instant access to their complete history. Implementing efficient pagination, time-based partitioning, and intelligent indexing strategies ensures historical queries remain performant regardless of data volume. Balance calculations require careful consideration of confirmation requirements, pending transactions, and potential blockchain reorganizations that might invalidate previously confirmed transactions.
7
Scaling Strategies for Crypto Wallet Infrastructure
Horizontal vs Vertical Scaling
Scaling strategies determine how your crypto wallet infrastructure responds to growing user demands. Vertical scaling involves upgrading individual server resources like CPU, memory, and storage to handle increased load. While straightforward to implement, vertical scaling has inherent limits and creates single points of failure. Horizontal scaling distributes workload across multiple servers, enabling theoretically unlimited capacity expansion and improving fault tolerance. Modern crypto wallet infrastructure predominantly relies on horizontal scaling for application layers while strategically applying vertical scaling to specialized components like primary databases.
Implementing horizontal scaling requires designing stateless services where any server instance can handle any request. This involves externalizing session state to distributed caches, using shared message queues for background processing, and ensuring database connections support connection pooling across multiple application instances. Container orchestration platforms like Kubernetes simplify horizontal scaling by automatically distributing workloads and managing instance lifecycles.
Auto-Scaling for Traffic Spikes
Cryptocurrency markets operate continuously and experience dramatic volatility that directly correlates with wallet usage patterns. Price movements, major announcements, and market events can spike traffic 10x or more within minutes. Auto-scaling configurations automatically provision additional resources when predefined thresholds are exceeded, then scale down during quieter periods to optimize costs. Effective auto-scaling for crypto wallet infrastructure requires careful tuning of scaling policies, appropriate cooldown periods, and pre-warming strategies that prepare instances before they receive traffic.
8
Load Balancing & Traffic Distribution
API Gateway Role
API gateways serve as the front door to your crypto wallet infrastructure, handling request routing, authentication, rate limiting, and protocol translation. Solutions like Kong, AWS API Gateway, or NGINX Plus provide sophisticated traffic management capabilities essential for production wallet systems. The gateway layer implements crucial protections including DDoS mitigation, request validation, and API versioning that prevent malicious traffic from reaching backend services while ensuring legitimate requests route efficiently to appropriate handlers.
Preventing Bottlenecks in Wallet Infrastructure
Bottlenecks in crypto wallet infrastructure typically emerge at connection points between components: database connection pools, blockchain node RPC endpoints, and inter-service communication channels. Identifying and eliminating bottlenecks requires comprehensive monitoring and load testing under realistic conditions. Connection pooling, request queuing, circuit breakers, and bulkhead patterns help isolate failures and prevent cascading issues that could impact the entire system. Regular capacity planning exercises ensure infrastructure growth stays ahead of user adoption.
9
Performance Optimization Techniques
Caching Layers (Redis, Memcached)
Caching represents the single most impactful optimization for crypto wallet infrastructure performance. Redis and Memcached store frequently accessed data in memory, reducing database queries by 70-90% for common operations. Wallet balances, user session data, exchange rates, and recently fetched transaction details are ideal caching candidates. Implementing intelligent cache invalidation strategies ensures users always see accurate information while maximizing cache hit rates. Our implementations typically achieve sub-10ms response times for cached data compared to 100-500ms for uncached database queries.
Reducing RPC Call Latency
Blockchain node RPC calls often constitute the slowest operations in crypto wallet infrastructure. Each balance check, transaction broadcast, or smart contract query requires network communication with blockchain nodes. Optimization strategies include batching multiple requests into single RPC calls, implementing request coalescing for identical concurrent queries, and maintaining persistent connections to reduce handshake overhead. Geographic proximity between application servers and node infrastructure minimizes network latency, while redundant node endpoints ensure continuous availability.
10
Security Layer in Crypto Wallet Infrastructure
HSMs & Key Management
Hardware Security Modules form the security foundation of enterprise crypto wallet infrastructure. These specialized devices store cryptographic keys in tamper-resistant hardware, ensuring private keys never exist in software memory where they might be extracted through attacks. HSMs provide FIPS 140-2 Level 3 or higher certification required by many regulatory frameworks in the USA, UK, and Canada. Cloud-based HSM offerings from major providers make enterprise-grade key security accessible without significant capital investment, though organizations handling substantial assets often deploy dedicated on-premise HSMs for maximum control.
Secure Signing Environments
Transaction signing requires isolated environments where private keys are accessed exclusively for creating cryptographic signatures. Secure signing environments implement multiple defense layers including network isolation, restricted access controls, comprehensive audit logging, and anomaly detection. Multi-signature schemes requiring multiple independent approvals for high-value transactions provide additional protection against both external attacks and insider threats. MPC (Multi-Party Computation) technology enables distributed key management where no single party ever possesses complete private keys.
Security Model Selection Criteria
Asset Value Assessment
Evaluate total assets under management to determine appropriate security investment. Wallets managing over $10M require HSM-grade protection with multi-signature policies and formal security audits.
Regulatory Requirements
Identify compliance obligations across target jurisdictions. USA, UK, UAE, and Canada each impose specific security standards that influence infrastructure architecture and key management approaches.
Operational Complexity
Balance security strength against operational overhead. Advanced solutions like MPC and threshold signatures provide excellent protection but require sophisticated operational procedures and specialized expertise.
11
High Availability & Fault Tolerance
Multi-Region Deployments
Multi-region deployment strategies ensure crypto wallet infrastructure survives entire data center failures. Distributing services across geographically diverse regions eliminates single points of failure while improving latency for users worldwide. Active-active configurations where all regions handle production traffic provide the highest availability, though they require sophisticated data synchronization and conflict resolution mechanisms. Active-passive approaches maintain standby infrastructure ready to assume operations if primary regions fail, offering simpler implementation with slightly longer recovery times.
Disaster Recovery Planning
Comprehensive disaster recovery planning defines how crypto wallet infrastructure responds to catastrophic failures. Recovery Time Objective (RTO) specifies maximum acceptable downtime, while Recovery Point Objective (RPO) determines acceptable data loss. Wallet providers typically target RTO under 15 minutes and RPO near zero for critical financial data. Regular disaster recovery drills validate that documented procedures work as expected and that team members can execute recovery operations under pressure. Automated failover mechanisms reduce human error during stressful incidents.
Disaster Recovery Implementation Lifecycle
Risk Assessment
Identify potential failure scenarios and assess business impact of each disaster type across all infrastructure components.
Strategy Definition
Define RTO and RPO targets based on business requirements and establish recovery strategies for each critical system.
Infrastructure Setup
Provision standby infrastructure in secondary regions with appropriate replication and synchronization mechanisms.
Automation Build
Create automated failover scripts and runbooks that minimize manual intervention during actual disaster events.
Testing Phase
Conduct tabletop exercises and actual failover tests to validate recovery procedures work correctly under pressure.
Team Training
Train operations teams on recovery procedures and ensure 24/7 coverage for incident response capabilities.
Documentation
Maintain comprehensive documentation including contact lists, vendor information, and step-by-step recovery guides.
Continuous Improvement
Review and update DR plans quarterly, incorporating lessons learned from tests and actual incidents.
12
Monitoring & Performance Metrics
Uptime Monitoring
Comprehensive uptime monitoring provides visibility into crypto wallet infrastructure health across all components. External synthetic monitoring from multiple geographic locations verifies user-facing services remain accessible and responsive. Internal monitoring tracks individual service health, database performance, and blockchain node synchronization status. Alerting configurations ensure operations teams receive immediate notification of issues before they impact users. Our recommended approach combines tools like Datadog, New Relic, or Prometheus with PagerDuty or Opsgenie for alert management.
Transaction Success Rates
Transaction success rate monitoring directly measures wallet effectiveness from the user perspective. Track submission success, confirmation rates, and average confirmation times across different blockchain networks. Identify patterns in failure rates that might indicate infrastructure issues, blockchain congestion, or integration problems with specific networks. Setting appropriate alerting thresholds enables proactive response before minor issues escalate into significant user-impacting problems.
Critical Metrics Dashboard
45ms
99.7%
100%
94%
88%
99.99%
13
Cost Optimization for Wallet Infrastructure
Infrastructure Cost Breakdown
Understanding crypto wallet infrastructure costs enables informed optimization decisions. Major cost categories include compute resources for application servers, storage for databases and blockchain data, network bandwidth for node communication, and specialized services like HSMs. Enterprise wallets typically allocate 30-40% of infrastructure budget to compute, 20-25% to storage, 15-20% to networking, and 20-30% to security and compliance tooling. Regular cost analysis identifies optimization opportunities without compromising performance or security.
| Cost Category | Small Scale | Mid Scale | Enterprise |
|---|---|---|---|
| Compute (Servers) | $2,000-5,000/mon | $15,000-30,000/mon | $50,000+/mon |
| Blockchain Nodes | $500-2,000/mon | $5,000-15,000/mon | $20,000+/mon |
| Database Services | $500-1,500/mon | $3,000-8,000/mon | $15,000+/mon |
| Security (HSM, etc.) | $1,000-3,000/mon | $5,000-12,000/mon | $25,000+/mon |
| Total Estimate | $5,000-15,000/mon | $30,000-70,000/mon | $100,000+/mon |
Optimizing Node and Cloud Usage
Strategic optimization reduces crypto wallet infrastructure costs without sacrificing quality. Reserved instances provide 30-60% savings for predictable baseline workloads. Spot instances handle batch processing and non-critical background tasks at 70-90% discounts. Right-sizing ensures resources match actual requirements rather than over-provisioned estimates. Shared node services supplement dedicated infrastructure for lower-priority requests. Implementing these optimizations typically reduces total infrastructure costs by 25-40% compared to naive configurations.
14
Compliance & Infrastructure Readiness
Data Residency Requirements
Data residency requirements vary significantly across jurisdictions where crypto wallet infrastructure operates. The European Union’s GDPR imposes strict rules about processing EU citizen data outside approved regions. Canada’s PIPEDA establishes similar controls for Canadian personal information. UAE’s data protection framework requires certain data categories to remain within national borders. US regulations vary by state and industry, with New York’s BitLicense imposing specific requirements for cryptocurrency businesses. Designing infrastructure with data residency compliance from inception prevents costly architectural changes later.
Infrastructure for Regulated Wallets
Regulated wallet providers face additional infrastructure requirements beyond standard best practices. Comprehensive audit logging must capture all system access, configuration changes, and transaction activities with tamper-evident storage. Segregation of duties enforces that no single individual can unilaterally access sensitive systems or approve significant transactions. Regular third-party audits verify controls operate effectively. Infrastructure must support compliance monitoring tools that detect potential regulatory violations and generate required reports for supervisory authorities.
Infrastructure Compliance Checklist
Multi-region data replication configured
Encryption at rest and in transit enabled
Audit logging with tamper-evident storage
Access controls with MFA enforcement
Network segmentation implemented
Vulnerability scanning scheduled
Disaster recovery plan documented
Third-party audit certification current
15
Future Trends in Crypto Wallet Infrastructure
AI-Driven Scaling
Artificial intelligence is transforming how crypto wallet infrastructure scales and optimizes itself. Machine learning models predict traffic patterns based on market conditions, social sentiment, and historical usage data, enabling proactive scaling before demand spikes occur. AI-powered anomaly detection identifies potential security threats and performance issues faster than traditional monitoring approaches. Natural language processing automates incident response by analyzing alerts and executing appropriate remediation actions. These capabilities reduce operational overhead while improving system reliability and security posture.
Serverless Wallet Backends
Serverless architectures offer compelling advantages for certain crypto wallet infrastructure components. Functions-as-a-Service platforms like AWS Lambda, Google Cloud Functions, and Azure Functions automatically scale to handle any request volume while charging only for actual compute consumption. This model works exceptionally well for sporadic workloads like webhook processing, notification delivery, and background analytics. However, serverless approaches face challenges with cold start latency and stateful operations, making hybrid architectures that combine serverless functions with traditional services the most practical approach for production wallet systems.
Authoritative Industry Standards for Crypto Wallet Infrastructure
Standard 1:
Deploy infrastructure across minimum three availability zones within each region to ensure service continuity during zone-level failures.
Standard 2:
Implement end-to-end encryption using TLS 1.3 for all network communications and AES-256 for data at rest across all storage systems.
Standard 3:
Maintain blockchain node synchronization within 10 blocks of network head to ensure transaction validity and accurate balance reporting.
Standard 4:
Store all private keys exclusively in FIPS 140-2 Level 3 certified Hardware Security Modules for assets exceeding $1M in custody.
Standard 5:
Conduct quarterly penetration testing by certified third-party security firms and remediate critical findings within 72 hours.
Standard 6:
Implement automated scaling policies that provision additional capacity within 60 seconds of threshold breach detection.
Standard 7:
Retain immutable audit logs for minimum seven years with cryptographic integrity verification to meet regulatory requirements.
Standard 8:
Execute disaster recovery drills semi-annually with documented results demonstrating RTO under 15 minutes and RPO near zero.
Conclusion: Building for Scale and Security
Crypto wallet infrastructure represents the technical foundation upon which successful digital asset platforms are built. Throughout this guide, we have explored the essential components, hosting strategies, scaling approaches, and security measures that distinguish enterprise-grade infrastructure from basic implementations. The decisions you make regarding cloud providers, database architecture, node management, and security layers will determine your platform’s ability to serve users reliably across the USA, UK, UAE, Canada, and global markets.
Success requires balancing multiple competing priorities: performance versus cost, security versus usability, and compliance versus operational flexibility. The hybrid approaches we have recommended throughout this guide offer practical paths forward that satisfy these competing demands. Whether you are building a new wallet platform or optimizing existing infrastructure, the principles and standards outlined here provide a roadmap for achieving operational excellence.
As the cryptocurrency industry matures and regulatory frameworks solidify, infrastructure quality becomes an increasingly important competitive differentiator. Organizations that invest in robust, scalable, and secure crypto wallet infrastructure position themselves to capture market opportunities while managing risks effectively. The future belongs to platforms built on solid technical foundations, and the time to invest in that foundation is now.
Frequently Asked Questions
Crypto wallet infrastructure refers to the backend systems, blockchain nodes, hosting, and security layers that power wallet applications.
A well-designed crypto wallet infrastructure ensures fast transactions, low latency, high uptime, and smooth user experience.
Core components include backend services, blockchain nodes, APIs, databases, security modules, and cloud hosting environments.
Hosting affects wallet speed, availability, scalability, and data security, making cloud and hybrid hosting popular choices.
Blockchain nodes enable wallets to read, validate, and broadcast transactions directly to the blockchain network.
Common scaling strategies include horizontal scaling, load balancing, auto-scaling, and microservices architecture.
Security is ensured using HSMs, encrypted key storage, secure APIs, multi-factor authentication, and isolated signing environments.
High transaction volumes are managed through caching, optimized RPC calls, distributed databases, and traffic throttling.
APIs connect the wallet frontend with backend services, blockchain nodes, and third-party integrations like exchanges or DeFi apps.
Future trends include AI-driven scaling, serverless infrastructure, multi-chain support, and advanced monitoring automation.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







