Key Takeaways
- A crypto exchange smart contract audit is a systematic, multi-phase review combining automated scanning and expert manual analysis to identify vulnerabilities, logic errors, and compliance gaps in exchange smart contract code before and after deployment.
- The crypto exchange security audit framework encompasses smart contract code review, infrastructure and wallet security assessment, threat modeling, penetration testing, and regulatory compliance verification as an integrated process.
- Common exchange smart contract vulnerabilities include reentrancy attacks, access control failures, oracle manipulation, flash loan vectors, integer overflow errors, and business logic flaws in fee calculation, settlement, and margin systems.
- Effective exchange smart contract testing combines automated tools (Slither, Mythril, Echidna) for broad pattern detection with manual expert review for complex business logic analysis, achieving coverage that neither approach provides alone.
- A blockchain security audit extends beyond smart contracts to cover node security, network configuration, consensus integrity, key management, and the interaction between on-chain and off-chain exchange components.
- Regulatory compliance for crypto exchanges requires demonstrating independent security audits, AML/KYC integration, data protection standards, and ongoing monitoring as prerequisites for licensing across major financial markets.
- Building a secure crypto exchange demands a continuous audit strategy with pre-launch comprehensive audits, post-deployment monitoring, regular re-audits after code changes, and ongoing compliance maintenance.
- Smart contract security is not a one-time checkpoint but a continuous discipline that must be embedded into the platform’s engineering culture, operational processes, and governance framework.
Crypto Exchange Smart Contract Audit: Complete Overview
What Is a Crypto Exchange Smart Contract Audit?
A crypto exchange smart contract audit is a thorough, structured examination of the smart contract code that governs critical functions on a cryptocurrency exchange platform. These functions include token deposits and withdrawals, trade settlement, fee distribution, staking mechanisms, liquidity pool management, and in some cases, matching and clearing logic. The audit evaluates the code for security vulnerabilities, logical correctness, adherence to specifications, gas optimization, and compliance with relevant standards.
The audit process typically involves multiple stages: automated static analysis using specialized tools, dynamic testing through fuzzing and property-based testing, manual line-by-line code review by experienced security researchers, and a comprehensive report that documents all findings, their severity, and recommended remediation. The best audits also include a verification phase where the auditing team confirms that all identified issues have been properly addressed by the engineering team before the code goes live.
For exchange platforms, the scope of a crypto exchange smart contract audit is broader than for simple DeFi contracts because exchange smart contracts interact with complex systems including matching engines, wallet infrastructure, and compliance modules. The audit must evaluate not just individual contract security but also the interactions between contracts and between on-chain and off-chain components.
Why Smart Contract Security Is Critical for Exchanges
Smart contract security is critical for exchanges because smart contracts handle the most sensitive operations on the platform: moving funds, executing trades, and enforcing financial agreements. A vulnerability in an exchange smart contract can be exploited to drain user funds, manipulate prices, bypass access controls, or disrupt trading operations. The immutability of deployed smart contracts means that a bug cannot simply be patched like traditional software; it requires careful upgrade procedures that themselves introduce risk.
The financial stakes are enormous. Exchange smart contracts collectively manage billions of dollars in user assets. A single exploit can result in losses that bankrupt the platform and devastate user trust. Beyond direct financial losses, security failures trigger regulatory scrutiny, lawsuits, and reputational damage that can be impossible to recover from. Investing in comprehensive smart contract security through rigorous auditing is not just best practice; it is a business survival requirement.
From a regulatory perspective, demonstrating robust smart contract security through independent audits is increasingly required for licensing. Regulators across major financial markets expect exchanges to provide evidence that their smart contracts have been thoroughly tested and audited. This regulatory expectation makes the crypto exchange smart contract audit not just a security measure but a compliance obligation. The exchange security checklist provides a comprehensive framework for evaluating platform security readiness.
Key Risks in Exchange Smart Contracts
Exchange smart contracts face a unique set of risks that reflect their complexity and the value they manage. Reentrancy vulnerabilities allow attackers to recursively call functions before state updates are completed, draining funds. Access control flaws enable unauthorized parties to execute privileged functions like withdrawals or parameter changes. Oracle manipulation allows attackers to feed false price data to contracts that depend on external price feeds. Flash loan attacks combine multiple DeFi primitives to exploit economic logic within a single atomic transaction.
Beyond these well-known attack vectors, exchange-specific risks include business logic errors in fee calculations (allowing fees to be bypassed or inflated), settlement timing vulnerabilities (enabling exploitation of the gap between trade execution and settlement), margin calculation flaws (enabling under-collateralized positions), and upgrade mechanism vulnerabilities (allowing unauthorized contract modifications through proxy patterns). Each of these risks must be systematically evaluated during the blockchain security audit process.
Risk Warning: The cost of a smart contract exploit far exceeds the cost of a comprehensive audit. Exchanges that deploy unaudited or inadequately audited smart contracts expose their users, their business, and their regulatory standing to catastrophic risk. Every dollar saved by cutting corners on security auditing can multiply into millions in potential losses.
Crypto Exchange Security Audit Framework
Components of a Crypto Exchange Security Audit
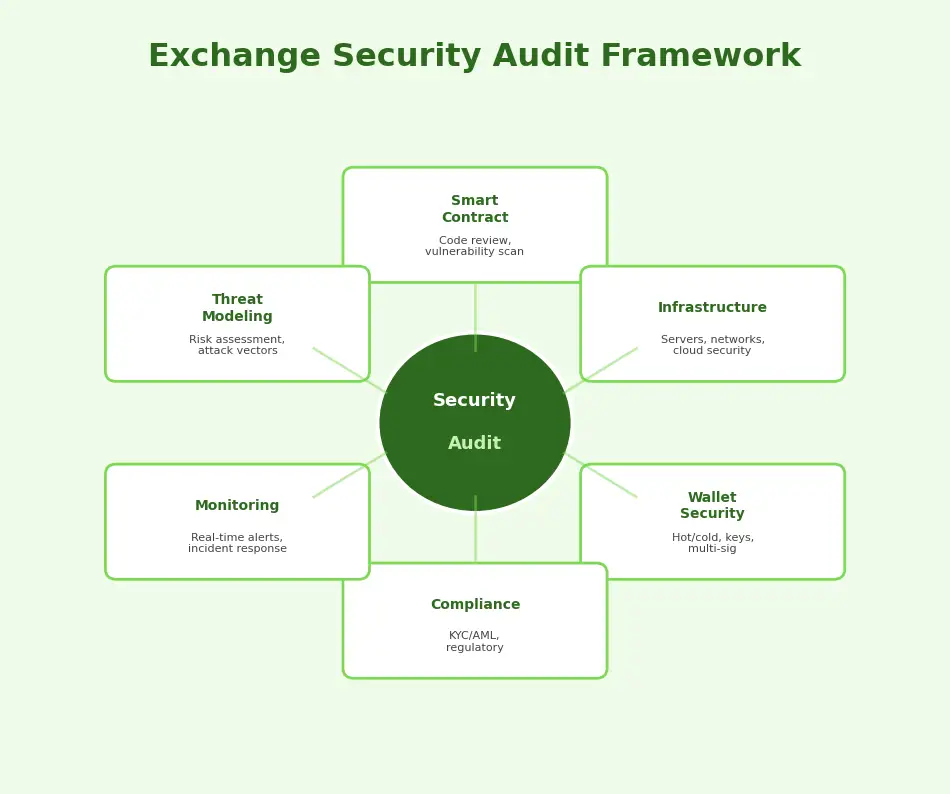
Infrastructure and Wallet Security
Infrastructure security covers the servers, networks, databases, and cloud environments that host the exchange platform. The audit evaluates network segmentation, access controls, encryption standards, DDoS protection, and disaster recovery capabilities. Wallet security focuses specifically on the key management system, hot/cold wallet architecture, multi-signature configurations, and the automated fund transfer mechanisms between wallet tiers. Infrastructure vulnerabilities can compromise the entire platform regardless of smart contract quality.
Exchange Smart Contract Testing Process
The exchange smart contract testing process follows a structured methodology. It begins with automated static analysis using tools like Slither and Solhint that scan for known vulnerability patterns. Next, dynamic analysis through fuzzing tools like Echidna generates random inputs to find edge cases. Symbolic execution tools like Mythril explore all possible execution paths. Manual review by experienced auditors then examines business logic, economic incentive alignment, and complex interaction patterns. Finally, integration testing validates that contracts interact correctly with each other and with off-chain systems.
Risk Assessment and Threat Modeling
Threat modeling identifies potential attackers (external hackers, malicious insiders, rival exchanges), their capabilities (technical skill, financial resources, market access), and the attack vectors they might use. Risk assessment quantifies the potential impact of each threat and prioritizes security investments accordingly. For exchange platforms, threat modeling must consider both technical attacks (smart contract exploits, infrastructure breaches) and economic attacks (market manipulation, arbitrage exploitation, flash loan attacks). Teams building crypto exchanges must embed threat modeling into their design process from day one.
Smart Contract Audit Lifecycle
| Phase | Activities | Timeline | Deliverables |
|---|---|---|---|
| 1. Scoping | Define contracts in scope, gather documentation, understand business logic | 2-3 days | Scope document, engagement agreement |
| 2. Automated Analysis | Static analysis, fuzzing, symbolic execution | 3-5 days | Automated findings report |
| 3. Manual Review | Line-by-line code review, logic verification, economic analysis | 1-3 weeks | Vulnerability assessment report |
| 4. Report | Compile findings, assign severity, provide remediation guidance | 3-5 days | Comprehensive audit report |
| 5. Remediation | Engineering team fixes identified issues | 1-2 weeks | Updated codebase |
| 6. Verification | Re-review fixed code, confirm remediation | 3-5 days | Final audit certificate |
Common Vulnerabilities Found During Audits
Common Exchange Smart Contract Vulnerabilities
| Vulnerability | Severity | Impact | Detection Method |
|---|---|---|---|
| Reentrancy | Critical | Fund drainage through recursive calls | Static analysis + manual review |
| Access Control | Critical | Unauthorized privileged operations | Manual review + permission testing |
| Oracle Manipulation | High | Price feed exploitation for profit | Economic analysis + simulation |
| Integer Overflow | High | Balance manipulation, incorrect calculations | Automated tools + fuzzing |
| Flash Loan Vectors | High | Single-transaction economic exploits | Economic modeling + scenario testing |
| Front-Running | Medium | Transaction ordering exploitation | MEV analysis + architecture review |
Blockchain Security Audit for Exchange Platforms
Blockchain-Level Risk Analysis
A blockchain security audit for exchange platforms extends beyond smart contract code to examine the underlying blockchain infrastructure. This includes evaluating the security properties of the chains the exchange integrates with, the reliability of blockchain node connections, the handling of chain reorganizations and forks, and the security of cross-chain bridges if the exchange supports multi-chain assets. Each blockchain introduces unique security considerations that must be understood and mitigated.
For exchanges that operate across multiple chains, the blockchain security audit must evaluate chain-specific risks: Ethereum’s MEV (Maximal Extractable Value) exposure, potential bridge vulnerabilities for cross-chain operations, and the different finality guarantees of each network. The audit should verify that the exchange waits for sufficient block confirmations before crediting deposits and that the system handles chain-specific edge cases correctly.
Node, Network, and Consensus Security
Node security involves ensuring that the blockchain nodes the exchange operates or connects to are properly configured, up to date, and protected against known attacks. This includes validating node software versions, reviewing RPC endpoint security, evaluating network exposure, and testing failover mechanisms. For exchanges running their own validator nodes, the audit must also evaluate consensus participation security, slashing risk, and key rotation procedures.
Monitoring and Incident Response Planning
No audit can identify every possible vulnerability, which is why continuous monitoring and incident response planning are essential components of a blockchain security audit. The monitoring system should detect anomalous on-chain activity (unusual transaction patterns, unexpected contract interactions, large fund movements), alert the security team in real time, and trigger automated protective actions (pausing contracts, freezing withdrawals) when thresholds are breached. The incident response plan defines roles, communication protocols, and technical procedures for responding to a security event.
Ensuring Smart Contract Security in Trading Engines
Code Review and Logic Verification
Code review for exchange smart contracts goes beyond identifying standard vulnerability patterns. It requires understanding the business logic of trading operations and verifying that the code correctly implements the intended behavior. This means checking that fee calculations are accurate across all edge cases, that settlement logic handles partial fills correctly, that margin calculations account for all collateral types, and that withdrawal procedures enforce proper authorization and rate limits.
Logic verification also includes formal verification for the most critical functions. Formal verification uses mathematical proofs to demonstrate that a function behaves correctly for all possible inputs, providing the strongest possible guarantee of correctness. While formal verification is expensive and time-consuming, it is increasingly applied to the highest-value functions in exchange smart contracts, such as fund transfer and balance management logic. The crypto exchange platform guide outlines the broader architectural context in which these smart contracts operate.
Automated vs Manual Exchange Smart Contract Testing
Automated vs Manual Testing Comparison
| Dimension | Automated Testing | Manual Testing |
|---|---|---|
| Speed | Minutes to hours | Days to weeks |
| Coverage | Broad pattern matching | Deep logic analysis |
| Vulnerability Types | Known patterns (reentrancy, overflow) | Business logic, economic attacks, novel vectors |
| False Positives | Higher (requires triage) | Lower (expert judgment) |
| Cost | Lower per run | Higher (expert time) |
| Best For | CI/CD integration, regression testing | Pre-launch audits, critical logic review |
The most effective approach to exchange smart contract testing combines both methods: automated tools run continuously as part of the CI/CD pipeline, catching known patterns with every code change, while manual expert review is conducted at key milestones (pre-launch, major updates, annual reviews). This combined approach provides the breadth of automated scanning with the depth of expert analysis.
Security Best Practices for a Secure Crypto Exchange
Building a secure crypto exchange requires security practices that extend well beyond auditing. Smart contracts should follow established patterns (OpenZeppelin libraries, checks-effects-interactions pattern, reentrancy guards). Access control should use role-based permission systems with timelocks on critical operations. Upgrade mechanisms should require multi-signature approval with mandatory delays. Emergency pause functionality should be built into all contracts with funds under management. And comprehensive event logging should record every state change for monitoring and forensic analysis.
Additionally, bug bounty programs complement formal audits by incentivizing the broader security community to find vulnerabilities. The most effective programs offer rewards proportional to the severity and impact of discovered vulnerabilities, with top payouts for critical issues. Engaging an experienced team of cryptocurrency exchange engineers who understand these security patterns is foundational to building a platform that withstands real-world attacks.
Principle: Security auditing is not a checkbox. It is a continuous process that must keep pace with evolving threats, changing codebases, and new regulatory requirements. The most secure crypto exchange platforms treat every code change as an opportunity to re-evaluate smart contract security and every audit finding as an opportunity to strengthen their defenses.
Crypto Exchange Compliance and Regulatory Standards

Understanding Crypto Exchange Compliance Requirements
Crypto exchange compliance encompasses the full range of regulatory obligations that a trading platform must meet to operate legally in its target markets. These obligations include financial licensing, anti-money laundering (AML) programs, know-your-customer (KYC) procedures, transaction monitoring, suspicious activity reporting, data protection, and in many jurisdictions, specific requirements around technology security including smart contract auditing. Crypto exchange compliance is not static; requirements evolve as regulators develop more sophisticated frameworks for digital asset markets.
Regulatory Compliance for Crypto Exchanges Across Jurisdictions
AML and KYC Integration
AML and KYC integration must be embedded into both the exchange’s operational processes and its technical architecture. Smart contracts that handle deposits and withdrawals should integrate with KYC verification status, preventing unverified users from accessing certain functions. Transaction monitoring systems should analyze on-chain activity patterns for indicators of money laundering, including structuring (splitting transactions to avoid thresholds), layering (complex transaction chains to obscure fund origins), and integration (converting illicit funds into legitimate assets). The KYC/AML compliance guide for exchanges covers the full spectrum of compliance integration requirements.
Data Protection and Reporting Standards
Data protection requirements affect how the exchange stores and processes personal information collected during KYC. Smart contracts themselves should not store personal data on-chain (a common privacy violation). Off-chain systems that handle personal data must comply with applicable data protection regulations. Reporting standards require exchanges to file regular reports with regulators, including suspicious activity reports, transaction volume reports, and in some jurisdictions, detailed records of all trades and participants. Regulatory compliance for crypto exchanges must address each of these obligations systematically.
Audit Model Selection Criteria
Choosing the right audit approach depends on your exchange’s complexity, regulatory requirements, budget, and timeline. Here is a framework for evaluation.
Audit Approach Selection
| Criteria | Single Audit Firm | Multiple Auditors | Continuous Audit Program |
|---|---|---|---|
| Best For | Simpler exchanges, initial launch | Complex platforms, high TVL | Rapidly evolving codebases |
| Coverage | Single perspective | Multiple perspectives | Ongoing, evolving coverage |
| Cost | $20K-$100K | $50K-$300K+ | $100K-$500K+ annually |
| Regulatory | Meets basic requirements | Exceeds most requirements | Maximum compliance posture |
Understanding the evolving regulatory landscape is critical for choosing the right audit strategy. The crypto exchange regulatory evolution guide provides context on how compliance requirements are shaping exchange operations across global markets.
Building a Secure Crypto Exchange with Continuous Audit Strategy
Pre-Launch Crypto Exchange Smart Contract Audit
The pre-launch crypto exchange smart contract audit is the most critical audit in the platform’s lifecycle. It establishes the security baseline and catches the most fundamental vulnerabilities before user funds are at risk. The pre-launch audit should be comprehensive, covering all smart contracts, their interactions, integration with off-chain systems, and alignment with business specifications. Multiple independent auditors should review the code for maximum coverage. No exchange should go live without completing this phase and remediating all critical and high-severity findings.
Post-Deployment Security Audit and Monitoring
After deployment, the crypto exchange security audit transitions from periodic to continuous. Monitoring systems track on-chain contract activity, detecting anomalous patterns that may indicate exploitation. Automated scanners run against every code change before deployment. Regular re-audits (quarterly or after significant updates) ensure that new code meets the same security standards as the original. Bug bounty programs provide an additional layer of continuous review by incentivizing the security community to find and responsibly disclose vulnerabilities.
Post-deployment monitoring should also track the broader ecosystem for threats: new attack techniques published by security researchers, exploits of similar protocols that could indicate transferable risks, and changes in the blockchain infrastructure that affect the exchange’s security posture. This proactive approach to smart contract security ensures that the platform adapts to the evolving threat landscape.
Maintaining Ongoing Regulatory Compliance for Crypto Exchanges
Maintaining ongoing regulatory compliance for crypto exchanges requires a systematic approach that integrates compliance monitoring into daily operations. This includes maintaining up-to-date KYC records, continuously monitoring transactions for suspicious activity, filing required reports on schedule, keeping audit documentation current, and tracking regulatory changes across all jurisdictions where the exchange operates. Compliance is not a one-time achievement; it is an ongoing obligation that must be actively managed.
The most effective compliance strategies automate as much of the monitoring and reporting process as possible, reducing human error and ensuring consistency. Smart contract-level compliance controls (such as automatic enforcement of withdrawal limits for unverified accounts) provide an additional layer of assurance that the platform operates within regulatory boundaries. Combining technical controls with operational processes creates a robust crypto exchange compliance posture that satisfies both regulators and users.
Frequently Asked Questions
A crypto exchange smart contract audit is a systematic review of the smart contract code that powers critical exchange functions such as token swaps, liquidity pools, staking mechanisms, and settlement logic. The audit involves both automated scanning and manual code review by security experts who identify vulnerabilities, logic errors, and compliance gaps before the code is deployed to production. A thorough audit covers reentrancy attacks, access control flaws, integer overflow risks, and business logic vulnerabilities specific to exchange operations.
Crypto exchanges need smart contract audits because deployed smart contracts are immutable and handle significant financial value. A single vulnerability can result in millions of dollars in losses, as demonstrated by numerous high-profile exploits. Beyond financial risk, audits are increasingly required by regulators as part of licensing processes. A crypto exchange security audit validates that the platform’s code meets both security best practices and regulatory compliance for crypto exchanges operating in major financial markets.
Smart contract audit costs vary based on code complexity, the number of contracts, the depth of review, and the reputation of the auditing firm. Basic audits for simple contracts may start around $5,000-$15,000, while comprehensive audits for complex exchange platforms with multiple interacting contracts can range from $50,000 to $250,000 or more. The cost should be viewed as an investment: it is a fraction of the potential losses from an exploit and often a prerequisite for regulatory approval and institutional partnerships.
Common vulnerabilities include reentrancy attacks (where a contract can be called recursively before completing its first execution), access control failures (where unauthorized users can call privileged functions), integer overflow/underflow errors, front-running vulnerabilities, oracle manipulation risks, flash loan attack vectors, improper handling of token standards, and business logic errors specific to exchange operations like incorrect fee calculations, settlement timing issues, or margin calculation flaws.
A comprehensive crypto exchange security audit typically takes 2-8 weeks depending on the scope. Simple contract audits may be completed in 1-2 weeks, while full platform audits covering multiple contracts, infrastructure, wallet security, and compliance review can take 6-8 weeks or longer. The timeline includes initial scoping, automated analysis, manual review, report generation, remediation by the engineering team, and verification of fixes. Rushing an audit compromises quality and can miss critical vulnerabilities.
Automated testing uses tools like Slither, Mythril, and Echidna to scan code for known vulnerability patterns, achieving broad coverage quickly. Manual testing involves human security experts reviewing code line by line, understanding business logic, and identifying complex vulnerabilities that automated tools miss. The most effective approach combines both: automated tools for comprehensive pattern detection and manual review for logic-level analysis. Exchange smart contract testing requires both to achieve thorough coverage.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







