Key Takeaways
- Web3 app security requires protecting smart contracts, wallets, frontends, APIs, and infrastructure since vulnerabilities in any layer can cause irreversible losses.
- Smart contract vulnerabilities like reentrancy, overflow, and access control flaws have caused billions in losses across DeFi protocols worldwide.
- Security auditing for Web3 by professional firms is essential before mainnet deployment, catching vulnerabilities that automated tools miss.
- Private key management using hardware wallets, multi-signature authorization, and secure storage prevents the most common Web3 attack vectors.
- Zero-trust security in Web3 means verifying every transaction, input, and user interaction without assuming trust based on previous authentication.
- Frontend security through Content Security Policies, input sanitization, and HTTPS prevents UI-based exploits that trick users into malicious actions.
- Real-time monitoring and incident response playbooks enable rapid detection and response to Web3 attack vectors before significant damage occurs.
- Bug bounty programs incentivize ethical hackers to discover vulnerabilities, providing continuous security testing beyond initial audits.
- User education about phishing, social engineering, and safe transaction habits is critical since human error causes many Web3 security breaches.
- Operational security including CI/CD hardening, secrets management, and least-privilege policies protects the infrastructure supporting Web3 applications.
Security in Web3 applications demands a fundamentally different approach than traditional software. With billions of dollars locked in smart contracts and irreversible transactions, a single vulnerability can result in catastrophic, permanent losses. Teams building web3 platform solutions across the USA, UK, UAE, and Canada must implement comprehensive security practices spanning smart contracts, wallets, frontends, APIs, and operational infrastructure. The Web3 threat landscape evolves rapidly, with attackers constantly discovering new exploit techniques. This guide covers essential security practices for protecting your Web3 applications and users.
Why Security Matters in Web3 Apps?
Web3 app security differs fundamentally from traditional application security due to the immutable nature of blockchain transactions and smart contracts. Once funds are stolen or a contract is exploited, there is typically no way to reverse the damage. This permanence makes security paramount. The decentralized nature of Web3 also means there is no central authority to intervene during incidents, placing full responsibility on builders and users to protect themselves.
Web3 Security vs Traditional App Security
Traditional applications can patch vulnerabilities, roll back databases, and freeze accounts during incidents. Web3 applications cannot. Smart contracts are immutable once deployed, meaning bugs live forever unless upgradability was designed in. Transactions settle in minutes and cannot be reversed by any authority. This shifts security from reactive to proactive. Every line of code must be secure before deployment because post-deployment fixes are either impossible or extremely complex.
Web3 vs Traditional Security Comparison
Web3 Security
- Immutable smart contracts
- Irreversible transactions
- Self-custody of assets
- Public, transparent code
- No central authority
Traditional Security
- Patchable applications
- Reversible operations
- Custodial accounts
- Private, hidden code
- Central authority control
Key Implications
- Security before deployment
- Proactive not reactive
- Multiple audit layers
- User education critical
- No recovery options
Why Web3 Hacks Are More Dangerous?
Web3 hacks result in immediate, permanent financial losses. When attackers exploit a DeFi protocol, they drain funds within minutes. The transparent nature of blockchain means attackers can analyze successful exploits and replicate them instantly across similar protocols. Flash loan attacks enable attackers to borrow millions without collateral, execute complex exploit chains, and repay loans within single transactions. The 2022 crypto hacks resulted in over $3.8 billion stolen, demonstrating the scale of this Web3 threat landscape.[1]
Common Targets
Attackers target multiple layers of Web3 applications. Smart contracts holding valuable assets are primary targets for exploit attacks. User wallets face phishing, social engineering, and malware attacks aimed at stealing private keys. Frontend interfaces can be compromised to trick users into signing malicious transactions. Infrastructure including RPC endpoints, APIs, and DNS can be attacked to intercept or manipulate communications. Comprehensive security must address all these Web3 attack vectors simultaneously.
Core Security Risks in Web3 Applications
Understanding the primary risk categories enables teams to prioritize security efforts effectively. Each risk category requires specific mitigation strategies and ongoing vigilance. The interconnected nature of Web3 means vulnerabilities in one area can cascade into others.
Smart Contract Vulnerabilities
Smart contract vulnerabilities represent the highest-impact risks in Web3. Reentrancy attacks allow malicious contracts to recursively call vulnerable functions before state updates complete. Integer overflow and underflow can manipulate token balances or bypass checks. Access control flaws enable unauthorized users to execute privileged functions. Logic errors in complex DeFi protocols create arbitrage opportunities attackers exploit. Oracle manipulation attacks provide false price data to trigger liquidations or steal funds.
Wallet & Key Management Risks
Private key compromise remains the most common cause of individual losses in Web3. Keys stored in insecure locations like plain text files or browser storage are easily stolen. Clipboard hijacking malware replaces copied addresses with attacker addresses. Seed phrase theft through phishing or social engineering gives attackers complete wallet control. Hot wallets connected to the internet face higher risk than cold storage solutions. Poor key rotation practices leave compromised keys active longer than necessary.
Phishing and Social Engineering Attacks
Phishing attacks in Web3 have grown increasingly sophisticated. Attackers create pixel-perfect replicas of popular dApp interfaces with slightly different URLs. Social media impersonation uses verified-looking accounts to distribute malicious links. Discord and Telegram groups are compromised to announce fake airdrops or mints. Deceptive signature requests trick users into approving unlimited token transfers or signing malicious messages. Even experienced users fall victim to well-crafted social engineering attacks.
Frontend & API Exploits
Frontend vulnerabilities enable attackers to manipulate what users see and sign. Cross-site scripting (XSS) can inject malicious code that modifies transaction parameters. DNS hijacking redirects users to fake sites that steal credentials. Compromised CDNs serve malicious JavaScript that intercepts wallet interactions. API vulnerabilities expose sensitive data or enable unauthorized operations. Frontend attacks are particularly dangerous because users trust familiar interfaces.
Infrastructure and Operational Weaknesses
Infrastructure vulnerabilities provide attackers with access to critical systems. Exposed RPC endpoints allow attackers to monitor transactions or inject malicious ones. Weak CI/CD security enables supply chain attacks that compromise deployments. Poor secrets management exposes API keys and private keys. Insufficient access controls allow unauthorized personnel to modify critical systems. Infrastructure attacks often go undetected longer than direct smart contract exploits.
Smart Contract Safety Best Practices
Smart contract security requires multiple layers of protection. No single technique catches all vulnerabilities, making defense in depth essential. Combining battle-tested libraries, automated analysis, manual review, and formal verification creates comprehensive protection for your contracts.
Smart Contract Security Lifecycle
Use OpenZeppelin Libraries
Start with audited, battle-tested implementations for standard functionality like ERC tokens and access control.
Run Static Analysis
Use Slither, MythX, and other tools to automatically detect common vulnerability patterns.
Professional Security Audit
Engage experienced auditors to review code logic, identify edge cases, and verify security assumptions.
Implement Emergency Controls
Add pause mechanisms, timelocks, and guardian addresses for incident response capabilities.
Use Battle-Tested Libraries
OpenZeppelin contracts have been audited multiple times and battle-tested across thousands of production deployments. Use their ERC-20, ERC-721, and ERC-1155 implementations instead of writing from scratch. Their access control, reentrancy guards, and pausable contracts implement security patterns correctly. Upgrading to new OpenZeppelin versions patches discovered vulnerabilities. Avoid reinventing security-critical functionality when proven implementations exist.
Static & Dynamic Testing
Automated security tools catch common vulnerabilities quickly. Slither performs static analysis detecting reentrancy, uninitialized storage, and dangerous patterns. MythX uses symbolic execution to explore execution paths and find exploitable conditions. Echidna performs fuzz testing, throwing random inputs at functions to discover unexpected behaviors. Integrate these tools into CI/CD pipelines to catch issues before they reach production. However, tools have limitations and cannot replace manual review.
Code Audits & Peer Reviews
Professional security audits by firms like Trail of Bits, OpenZeppelin, and Consensys Diligence catch vulnerabilities that automated tools miss. Auditors understand business logic context and can identify subtle flaws in complex interactions. Internal peer reviews before external audits improve code quality and reduce audit findings. Budget for multiple audit rounds since initial audits often reveal issues requiring code changes and re-audit. Never skip audits for contracts handling significant value.
Formal Verification Techniques
Formal verification mathematically proves that contracts behave correctly under all possible inputs. Tools like Certora and Solidity’s SMTChecker verify properties such as “balance cannot exceed total supply” or “only owner can pause.” While expensive and time-consuming, formal verification provides the highest assurance level for critical financial logic. Consider formal verification for contracts managing large asset pools or implementing novel mechanisms.
Role-Based Access Controls in Contracts
Implement granular access controls using OpenZeppelin’s AccessControl contract. Define specific roles for different administrative functions rather than single owner addresses. Require multi-signature approval for sensitive operations. Implement timelocks on administrative functions giving users time to react to malicious proposals. Log all administrative actions for transparency. Avoid centralized control that creates single points of failure or trust.
Emergency & Pause Mechanisms
Include circuit breakers that halt contract operations during emergencies. OpenZeppelin’s Pausable contract provides this functionality. Define guardian addresses with emergency powers that bypass timelocks. Implement rate limiting to slow down potential attacks. Create escape hatches that allow users to withdraw funds even when main functionality is paused. Test emergency mechanisms thoroughly before deployment to ensure they work when needed.
Securing Wallets, Keys & User Accounts
Private key security is fundamental to Web3. Unlike passwords, private keys cannot be reset or recovered. Compromise means permanent loss of all associated assets. Both application operators and end users must understand and implement proper key management practices.
Private Key Best Practices
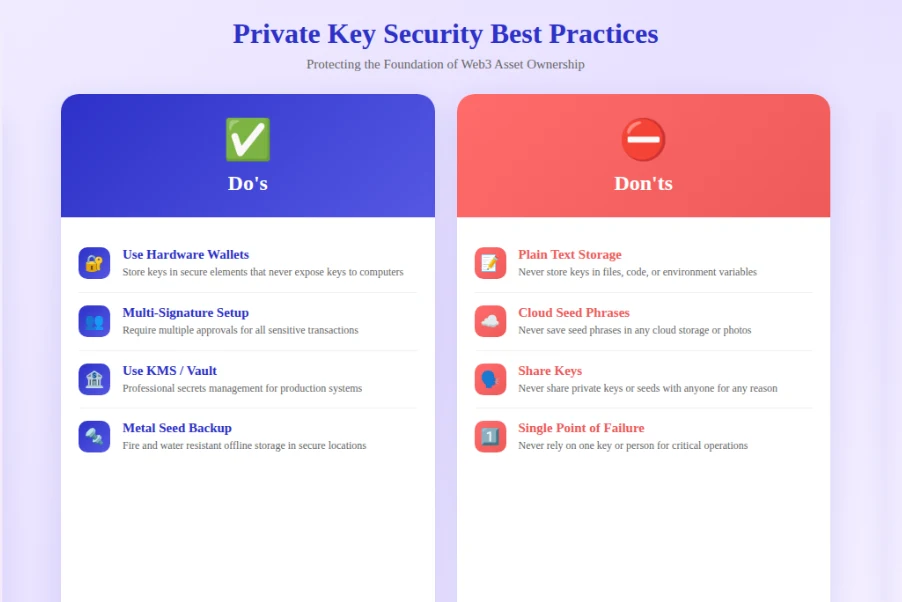
Never store private keys in plain text, environment variables, or version control. Use dedicated key management services like AWS KMS, HashiCorp Vault, or dedicated HSMs for production deployments. Generate keys on air-gapped machines when possible. Implement key rotation policies and procedures. Separate keys by function, using different keys for deployment, operations, and user-facing signatures. Document key custody and recovery procedures clearly.
Hardware Wallets & Cold Storage
Hardware wallets like Ledger and Trezor store private keys in secure elements that never expose keys to connected computers. Use hardware wallets for all high-value operations and administrative functions. Cold storage refers to keys stored completely offline, typically on paper or metal backups in secure locations. For organizational treasury, consider institutional custody solutions with insurance coverage. The extra friction of hardware wallets significantly reduces attack surface.
Multi-Signature Authorization
Multi-signature wallets like Gnosis Safe require multiple parties to approve transactions. A 3-of-5 configuration means three out of five keyholders must sign. This prevents single points of failure from compromised keys or malicious insiders. Use multi-sig for contract ownership, treasury management, and all sensitive operations. Distribute signers across geographic locations and organizational roles. Test recovery procedures regularly.
Two-Factor Authentication (2FA)
Enable 2FA on all accounts related to Web3 operations including email, exchanges, cloud providers, and code repositories. Use hardware security keys like YubiKey rather than SMS-based 2FA which is vulnerable to SIM swapping. Authenticator apps provide moderate protection. Store 2FA recovery codes securely. 2FA prevents account takeover even when passwords are compromised through phishing or data breaches.
Protecting Against Infinite Approvals and Spurious Signatures
Token approvals granting unlimited spending permissions create significant risk. If an approved contract is compromised, attackers can drain all approved tokens. Implement limited approvals matching intended transaction amounts. Use permit functionality (EIP-2612) where available for gasless, one-time approvals. Warn users about approval requests clearly. Implement EIP-712 typed data signing so users can verify what they sign. Never request blind signatures.
User Education Around Phishing & Social Attacks
User education is critical because many attacks target human behavior rather than technical systems. Teach users to verify URLs carefully, never share seed phrases, and be suspicious of urgent requests. Provide official communication channels and teach users to verify announcements. Create documentation about common scam patterns. Consider implementing warning systems that alert users to potentially dangerous interactions.
Securing Frontends and User Interfaces
Frontend security protects users from attacks that exploit the interface between users and blockchain. Even with secure smart contracts, a compromised frontend can trick users into signing malicious transactions. Apply traditional web security practices plus Web3-specific protections.
Content Security Policies (CSP)
Content Security Policies restrict which resources browsers can load, preventing cross-site scripting attacks. Configure strict CSP headers that allow only necessary scripts, styles, and connections. Disable inline scripts and require script-src nonces or hashes. Report CSP violations to monitor attack attempts. CSP prevents attackers from injecting malicious scripts even if they find XSS vulnerabilities in your application.
Safe DOM Handling & Input Sanitization
Sanitize all user inputs before rendering to prevent XSS attacks. Use frameworks with automatic escaping like React which prevents most injection attacks by default. Avoid dangerouslySetInnerHTML and similar bypass mechanisms. Validate and sanitize data on both client and server. Be especially careful with wallet addresses and transaction data displayed to users since attackers may attempt address substitution attacks.
HTTPS & Secure Cookie Practices
Enforce HTTPS for all connections to prevent man-in-the-middle attacks. Configure HSTS headers to prevent protocol downgrade attacks. Use secure, httpOnly, and sameSite flags on all cookies. Implement certificate pinning where appropriate. HTTPS ensures that attackers cannot intercept or modify communications between users and your frontend, protecting transaction signing and wallet interactions.
Preventing UI-Level UX Exploit Tricks
UI exploits trick users through deceptive interfaces. Clickjacking overlays invisible elements over legitimate buttons. Address spoofing uses similar-looking characters to substitute wallet addresses. Fake transaction confirmations show incorrect amounts or recipients. Implement frame-busting to prevent embedding. Display addresses with consistent formatting and checksums. Show full transaction details before signing. Test UX for potential confusion or manipulation.
Network, API & Protocol Security
The network layer connects users to blockchain and backend services. Securing these connections prevents interception, manipulation, and denial of service attacks. Apply zero-trust security in Web3 principles to all network communications.
Security Tool Selection Criteria
Step 1: Assess Needs
- Identify critical assets
- Map attack surfaces
- Evaluate threat models
- Define compliance needs
Step 2: Evaluate Tools
- Compare capabilities
- Check integrations
- Review track record
- Test with your code
Step 3: Implement
- Integrate into CI/CD
- Train team members
- Monitor continuously
- Iterate and improve
Secure RPC, API, and Node Connections
RPC endpoints connect frontends to blockchain nodes. Use authenticated RPC providers like Infura or Alchemy with API keys. Implement rate limiting to prevent abuse and denial of service. Consider running your own nodes for sensitive operations. Never expose administrative RPC methods publicly. Monitor RPC usage for anomalies indicating potential attacks or misuse.
Encrypted Communication & TLS
Encrypt all communications using TLS 1.3 with strong cipher suites. Configure proper certificate validation to prevent man-in-the-middle attacks. Use certificate transparency logging to detect unauthorized certificates. Implement mutual TLS for service-to-service communication where appropriate. Regularly rotate certificates and monitor for expiration. Encryption ensures communication integrity and confidentiality.
Identity and Access Management (IAM)
Implement robust IAM for all backend systems. Use OAuth 2.0 or similar standards for API authentication. Implement role-based access control limiting permissions to minimum required. Audit all access and changes to permissions. Integrate with identity providers for centralized management. Remove access promptly when team members depart. IAM prevents unauthorized access to critical systems and data.
Secure Third-Party Service Integrations
Third-party services introduce supply chain risk. Vet providers carefully for security practices. Use minimal permissions when integrating external services. Monitor third-party service health and security announcements. Have contingency plans for service failures or compromises. Review third-party code and dependencies regularly. The 2022 crypto hacks included several supply chain attacks through compromised dependencies.
Monitoring, Incident Preparedness & Response
Even with strong preventive measures, incidents can occur. Rapid detection and response limit damage. Prepare incident response capabilities before they are needed. Regular drills ensure team readiness.
Real-Time Monitoring & Alerts
Monitor on-chain activity for suspicious patterns. Services like Tenderly, Forta, and OpenZeppelin Defender provide monitoring and alerting. Configure alerts for large transactions, unusual function calls, and contract state changes. Monitor governance proposals and administrative actions. Set up 24/7 on-call rotation for critical alerts. Fast detection enables rapid response before attackers complete their exploits.
Logging and Anomaly Detection
Comprehensive logging enables incident investigation and anomaly detection. Log all API requests, authentication events, and administrative actions. Use centralized log aggregation for analysis. Implement anomaly detection using machine learning to identify unusual patterns. Retain logs according to compliance requirements. Regular log review helps identify attack attempts before they succeed.
Incident Response Playbooks
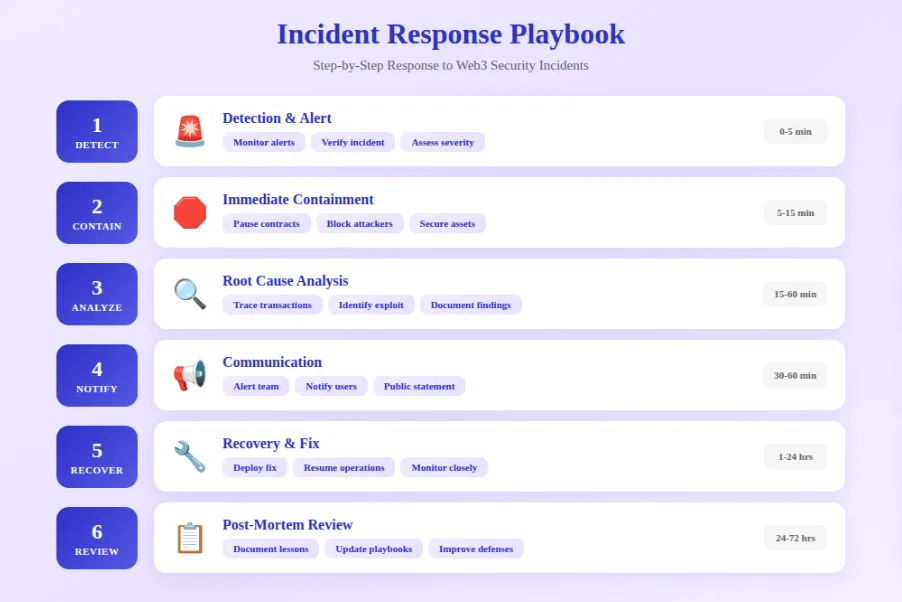
Create detailed incident response playbooks before incidents occur. Define incident severity levels and escalation procedures. Document steps for common scenarios like contract exploits, phishing campaigns, and infrastructure compromises. Establish communication protocols including user notification templates. Practice incident response through tabletop exercises. Post-incident reviews improve future response capabilities.
Bug Bounty and Responsible Disclosure Programs
Bug bounty programs incentivize security researchers to report vulnerabilities rather than exploit them. Platforms like Immunefi specialize in Web3 bug bounties. Define clear scope, reward tiers, and submission processes. Respond quickly to reports and pay bounties promptly
. Public bug bounty programs demonstrate security commitment. Many major exploits were preceded by ignored or underpaid bug reports.
Operational Security
Operational security protects the infrastructure and processes supporting Web3 applications. Even secure code can be compromised through weak operational practices. Apply enterprise security standards to all supporting systems.
Key Lifecycle & CI/CD Security
Secure the entire software delivery pipeline. Require code review and approval before merging changes. Sign commits to verify author identity. Run security scanning in CI/CD pipelines. Protect deployment credentials with secrets management. Implement deployment approvals for production changes. Monitor pipeline executions for anomalies. Supply chain attacks through compromised CI/CD have affected major protocols.
Least-Privilege Policies
Grant minimum permissions required for each role and system. Avoid shared accounts and credentials. Implement just-in-time access for sensitive operations. Regularly audit and revoke unnecessary permissions. Apply least privilege to both human users and automated systems. Privilege escalation often enables attackers to expand initial compromises into full breaches.
Infrastructure Patch and Update Strategies
Keep all infrastructure components updated with security patches. Establish patching schedules balancing security urgency with stability testing. Monitor security advisories for critical vulnerabilities. Maintain system inventories to ensure complete patch coverage. Test patches in staging environments before production deployment. Unpatched vulnerabilities provide easy entry points for attackers.
Secrets Management & Environment Hardening
Use dedicated secrets management systems like HashiCorp Vault or AWS Secrets Manager. Never store secrets in code, configuration files, or environment variables. Rotate secrets regularly and after any potential compromise. Implement secret access auditing. Harden operating systems by disabling unnecessary services and applying security configurations. Regular vulnerability scanning identifies weaknesses before attackers find them.
Web3 Security Industry Standards
Standard 1: Always use audited, battle-tested libraries like OpenZeppelin for standard contract functionality.
Standard 2: Require professional security audits before deploying contracts handling significant value.
Standard 3: Implement multi-signature authorization for all administrative and treasury operations.
Standard 4: Use hardware wallets for all high-value operations and administrative functions.
Standard 5: Enable real-time monitoring and alerts for suspicious on-chain activity patterns.
Standard 6: Include emergency pause mechanisms and guardian addresses for incident response.
Standard 7: Run bug bounty programs to incentivize responsible vulnerability disclosure.
Standard 8: Test extensively on testnets and conduct gradual mainnet rollouts with monitoring.
Secure Deployment & Post-Launch Practice
Security does not end at deployment. Ongoing vigilance, testing, and improvement maintain security posture over time. Attackers continuously evolve techniques, requiring continuous security efforts.
Canary Releases & Gradual Rollouts
Deploy new contracts and updates gradually. Start with limited value exposure and expand as confidence grows. Use feature flags to control rollout pace. Monitor closely during initial deployment phases. Canary releases catch issues affecting production that testing missed. Gradual rollouts limit damage from unforeseen vulnerabilities while enabling quick response if problems emerge.
Post-Launch Penetration Testing
Conduct regular penetration testing after launch to discover new vulnerabilities. Penetration testers simulate real attacker behavior including social engineering attempts. Schedule periodic assessments, especially after significant changes. Consider red team exercises that test organizational response capabilities. Production environment testing often reveals issues that testing environments miss.
User Activity Monitoring
Monitor user activity patterns to detect compromised accounts or unusual behavior. Track login attempts, transaction patterns, and API usage. Implement velocity limits that trigger review for unusual activity spikes. Balance security monitoring with privacy considerations. User activity data helps identify attack attempts and compromised accounts early.
Continuous Smart Contract Re-Verification
Verify deployed contract bytecode matches source code regularly. Monitor for contract upgrades or unexpected changes in upgradeable contracts. Re-run security analysis when dependencies update. Track emerging vulnerability patterns that may affect your contracts. Continuous verification ensures contracts remain in expected state and catches any tampering or unauthorized modifications.
User & Ecosystem Safety Practices
Empowering users to protect themselves strengthens overall ecosystem security. Education, tools, and guidelines help users avoid common pitfalls and recognize threats.
Safe Transaction Habits (Verify Addresses, Amounts)
Teach users to verify transaction details carefully before signing. Double-check recipient addresses, especially when copying from clipboard. Verify transaction amounts match expectations. Review approval permissions before confirming. Use hardware wallets that display transaction details for final verification. Most user losses result from approving malicious transactions that careful review would catch.
Wallet Recovery and Backup Guidelines
Provide clear guidance on seed phrase backup and recovery. Never store seed phrases digitally or in cloud storage. Use metal backup solutions resistant to fire and water damage. Store backups in geographically separated secure locations. Test recovery procedures periodically. Lost seed phrases result in permanent loss of access to assets.
Staying Aware of Emerging Threats in Web3
The Web3 threat landscape evolves rapidly as attackers develop new techniques. Follow security researchers and auditors for emerging vulnerability disclosures. Monitor incident reports from other protocols for lessons learned. Participate in security communities sharing threat intelligence. Regular security training keeps teams current on evolving attack patterns. Proactive awareness prevents falling victim to known attack techniques.
Conclusion
Web3 app security requires comprehensive protection across smart contracts, wallets, frontends, APIs, and operational infrastructure. The irreversible nature of blockchain transactions makes proactive security essential since post-incident recovery is often impossible. Implement defense in depth combining security auditing for Web3, automated tools, monitoring, and user education. Apply zero-trust security in Web3 principles throughout your architecture. Teams across the USA, UK, UAE, and Canada must stay vigilant against evolving Web3 attack vectors while maintaining robust incident response capabilities. Security is not a one-time effort but an ongoing commitment to protecting users and assets.
Need Expert Web3 Security Services?
Partner with our experienced team for comprehensive security auditing, implementation, and ongoing protection.
Frequently Asked Questions
Web3 applications face multiple security risks including smart contract vulnerabilities like reentrancy and overflow attacks, wallet and private key management issues, phishing attacks targeting users, frontend exploits through malicious scripts, and infrastructure weaknesses in RPC endpoints and APIs. Unlike traditional apps, Web3 security breaches often result in immediate, irreversible financial losses since transactions cannot be reversed once confirmed on blockchain.
Secure smart contracts through multiple layers: use battle-tested libraries like OpenZeppelin for standard functionality, run static analysis tools like Slither and MythX to detect vulnerabilities, conduct thorough unit and integration testing, perform professional security audits for critical contracts, and implement access controls with emergency pause mechanisms. Always test extensively on testnets before mainnet deployment to catch issues early.
Protect private keys using hardware wallets for cold storage, never storing keys in plain text or environment variables in production, implementing multi-signature authorization for high-value operations, using secure key management services like AWS KMS or HashiCorp Vault, and educating users about phishing attacks. Never share private keys or seed phrases with anyone under any circumstances.
Web3 phishing attacks trick users into signing malicious transactions or revealing seed phrases through fake websites, social media impersonation, and deceptive signature requests. Prevent them by verifying website URLs carefully, using hardware wallets that display transaction details, never signing blind messages, implementing EIP-712 typed signatures, and educating users to recognize common attack patterns and suspicious requests.
Security auditing for Web3 is critical because smart contract vulnerabilities can result in immediate, permanent loss of funds. Audits by professional firms identify vulnerabilities that automated tools miss, verify business logic correctness, ensure compliance with standards, and provide confidence to users and investors. Major DeFi hacks often involve unaudited or poorly audited contracts, making audits essential for any serious project.
Zero-trust security in Web3 means verifying every interaction without assuming trust based on network location or previous authentication. This includes validating all transaction parameters on-chain, implementing role-based access controls, requiring multi-signature for sensitive operations, encrypting all communications, monitoring all activities for anomalies, and treating every user input as potentially malicious until verified.
Implement emergency measures through pause mechanisms that halt contract operations during incidents, timelocks on sensitive functions giving time to react, upgradeable proxy patterns allowing bug fixes, rate limiting to prevent rapid draining, guardian addresses with emergency powers, and circuit breakers that trigger automatically when unusual activity is detected. Test these mechanisms thoroughly before deployment.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







