Key Takeaways
- Smart contract architecture is planning smart contract architecture focuses on structure, connections, security, and management, not just writing code, ensuring systems remain safe and maintainable.
- On-chain vs off-chain logic only critical logic like ownership, balances, permissions, and final settlements should be on-chain. Off-chain components reduce costs, improve speed, and increase flexibility.
- Blockchain selection matters choosing the blockchain early is crucial because each platform has unique rules for storage, security, upgrades, and performance that directly impact contract design.
- State machine design smart contracts should be designed as state machines with clear states and valid transitions to prevent logical errors and unexpected behavior.
- Efficient storage layout a clean storage layout saves gas, avoids bugs, simplifies audits, and makes contracts safer and easier to upgrade over time.
- Clear external interfaces Interfaces should separate read-only, state-changing, and admin functions so users and developers interact safely and correctly.
- Strong permission smart contract architecture using roles, multisig wallets, and timelocks helps avoid single points of failure and reduces the risk of hacks or operational mistakes.
- Planned upgradeability upgrade strategies, immutable contracts or proxy patterns, should be planned from the start to fix bugs and add features without breaking trust.
- Secure external dependencies tokens, oracles, and third-party protocols increase risk and must be carefully validated, tested, and protected with proper limits and checks.
- Testing & monitoring thorough testing and continuous monitoring are essential because smart contracts manage real assets and are difficult to fix after deployment.
Blockchain technology has changed the way digital systems work. Instead of trusting banks, companies, or middlemen, people can now trust code. This is where smart contracts come in. Smart contracts are programs that run on a blockchain and automatically follow predefined rules. Once deployed, they work exactly as written, without human interference.
At first glance, smart contracts look simple. For example, send money when a condition is met, release tokens after a deadline, or record a vote result. But in real products, smart contracts are not small scripts. They are part of large systems that handle real money, real users, and real risks.
This is why smart contract architecture is extremely important. Architecture means how smart contracts are planned, structured, connected, and managed as a system. A well-designed architecture keeps contracts secure, scalable, and easy to maintain. A poor architecture can cause hacks, stuck funds, high gas costs, and loss of user trust.
In this guide, we will explore what smart contract architecture is, the key design principles, the most important smart contract architecture patterns, and how real-world projects use them to build secure blockchain systems.
What Is Smart Contract Architecture?
Smart contract architecture is the way smart contracts are built and organized on a blockchain. It includes the code (logic), where it runs like Ethereum, the data it keeps (state), and how it talks to users or other contracts. Smart contracts work automatically without needing a middleman, like a vending machine that gives out items when you put in money.
The main parts are the code, usually written in Solidity, the contract’s address on the blockchain, the rules for changing data, and ways to interact with other contracts or apps. Everything is secured by the blockchain, so it is safe and trustless.
Good architecture makes the system clean, organized, and strong. Bad architecture makes it confusing, risky, and expensive to fix later.
Why Smart Contract Architecture Matters
Smart contracts are different from traditional software. Once deployed on the blockchain, they cannot be easily changed. This makes planning even more important.
1. Security Is Critical
Smart contracts often handle large amounts of money. A small bug or wrong design can lead to millions of dollars lost. Many famous hacks happened because of poor architecture, not because of advanced hacking skills.
2. Smart Contracts Are Public
Anyone can see and interact with smart contracts. Attackers study them carefully. Good architecture reduces the attack surface and protects critical parts of the system.
3. Scalability Matters
As users increase, contracts must handle more transactions. If architecture is poor, gas fees rise and users leave.[1]
4. Upgradeability Is Needed
Projects evolve over time. New features are added, bugs are fixed, and rules change. Architecture decides whether upgrades are possible or not.
5. Maintenance and Audits Become Easier
Clean architecture makes testing, auditing, and long-term maintenance much simpler.
Smart Contract Architecture
Smart contract architecture is just smart planning. You decide what must be locked on the blockchain for trust and safety, and what can stay off-chain for speed and flexibility. When this balance is right, your contract stays secure, affordable to use, and easy to manage as it grows.[2]

1) Define the Contract Surface Area
Before building any smart contract, one of the most important decisions is defining the contract surface area. This simply means deciding what data and logic should be stored on the blockchain and what should stay off the blockchain.
The blockchain is powerful, but it is also expensive and permanent. Every piece of data stored on-chain costs gas and cannot be easily changed later. Because of this, smart contracts should only handle the most critical parts of your system. Everything else can be managed off-chain in a safer, cheaper, and more flexible way.
What Belongs On-Chain
On-chain components are the parts of your system that must be trustless, transparent, and verifiable by anyone. These are the rules and states that users should never need to trust a third party for.
- Asset ownership and balances
Token balances, NFT ownership, and asset transfers must live on-chain. This ensures that ownership is clear and cannot be manipulated. Users can independently verify who owns what at any time. - Publicly verifiable state
Any data that affects user funds or rights should be on-chain. This includes staking positions, voting power, governance decisions, escrow states, and open positions in DeFi protocols. Keeping this information on-chain builds trust because anyone can verify the state directly. - Permissioned actions and roles
Admin controls, special roles, and allow lists must be defined on-chain. This prevents hidden changes and ensures that only authorized addresses can perform sensitive actions like upgrades, pauses, or fund withdrawals. - Final settlement rules
The logic that decides who receives funds, how much they receive, and when they receive it must be enforced by the smart contract itself. Once conditions are met, the contract should automatically settle without relying on human approval.
What Belongs Off-Chain
Off-chain components support the system but do not need blockchain-level trust. Keeping them off-chain reduces costs and improves performance.
- User interface and experience
Forms, input validation, button clicks, and user flows should stay off-chain. These elements change frequently and do not affect core trust logic, so they are better handled in the frontend or backend. - Indexing and search features
Transaction history, dashboards, filters, and analytics are expensive and slow to manage on-chain. Off-chain indexing tools can process blockchain data efficiently and present it in a user-friendly way. - Heavy computation
Complex calculations such as risk models, rankings, pricing logic, or AI-based decisions are not suitable for smart contracts. They consume too much gas and slow down execution. These should be done off-chain, with only final results verified on-chain if needed. - Notifications and automation
Emails, push notifications, alerts, and scheduled tasks do not require trustless execution. These should run off-chain using traditional systems that are faster and easier to maintain.
The Core Rule to Follow
The golden rule of smart contract architecture is simple:
Put only the minimum required state on-chain that still keeps the system trustless.
A well-designed contract does not try to do everything. It focuses on security, ownership, and final outcomes, while letting off-chain systems handle speed, flexibility, and user experience. This balanced approach keeps costs low, reduces risks, and makes your blockchain application easier to scale in the long run.
Smart design is not about adding more code. It is about putting the right code in the right place.
2) Choose the Execution Environment (Your Architectural Constraints)
After defining what should be on-chain and off-chain, the next big decision is choosing the execution environment. This means deciding which blockchain platform your smart contracts will run on. This choice must be made early, because once you start building, changing the environment later is expensive and risky.
Each blockchain has its own rules, limits, and strengths. These rules directly affect how your contracts are written, how secure they are, how fast they run, and how much they cost to use.
EVM-Based Blockchains
Ethereum, Binance Smart Chain, Polygon, and most Layer 2 networks use the EVM model. This is the most widely used smart contract environment today.
In EVM chains, every action costs gas. Storage and call data are expensive, so developers must write efficient code. Reentrancy is a common risk, meaning contracts must be carefully protected against repeated calls. The good part is that the tooling is very mature. Developers have access to strong libraries, testing frameworks, debuggers, and security tools.
EVM chains are a solid choice for most DeFi apps, NFT platforms, DAOs, and enterprise use cases because the ecosystem is well-tested and widely supported.
Solana Execution Environment
Solana follows a very different design. It uses an accounts-based model where data and logic are separated. Programs do not store data internally. Instead, data lives in accounts that are passed into the program during execution.
Solana also introduces ideas like rent and parallel execution. This allows very high transaction speed, but it adds complexity for developers. Contracts must be designed carefully to avoid account conflicts and execution limits.
Solana is great for high-performance applications like trading platforms, games, and real-time apps, but the learning curve is higher compared to EVM chains.
Move-Based Blockchains
Aptos and Sui use the Move programming language, which focuses strongly on safety. Move treats assets as resources that cannot be copied or destroyed accidentally. This reduces many common smart contract bugs.
The composability model is different from EVM, meaning contracts interact in a more controlled way. While this improves safety, it also changes how developers design protocols.
Move-based chains are still growing, but they are attractive for projects that prioritize asset safety, long-term stability, and formal correctness.
How This Decision Affects Your Architecture
Choosing the execution environment decides several core parts of your system.
- How you store state
Each environment handles storage differently. EVM stores state inside contracts. Solana separates state into accounts. Move enforces strict ownership rules. Your data models must match the platform. - How you upgrade contracts
Some environments support proxy patterns easily, while others require redeployment or special upgrade logic. Your upgrade strategy depends heavily on the chain you choose. - How you secure contract calls
Security risks vary by environment. EVM needs protection against reentrancy and gas issues. Solana requires safe account handling. Move reduces many risks but enforces strict rules. - How you test and monitor
Tooling, debuggers, simulators, and monitoring tools differ across platforms. Mature ecosystems make testing easier and reduce production risks.
There is no perfect blockchain for every project. The best choice depends on your use cases, team skills, and long-term goals. Choose early, design around the platform’s strengths, and respect its limits. A smart execution environment choice makes everything else simpler, safer, and more scalable.
3) Model Your State as a Deterministic State Machine
When building smart contracts, one of the smartest habits is to think of every contract as a state machine. This means the contract always exists in one clear state at a time, and it can only move to another state through well-defined actions.
On blockchains, randomness and hidden behavior are dangerous. Everything must be predictable. That is why smart contracts should behave like deterministic systems, where the same input always produces the same result.
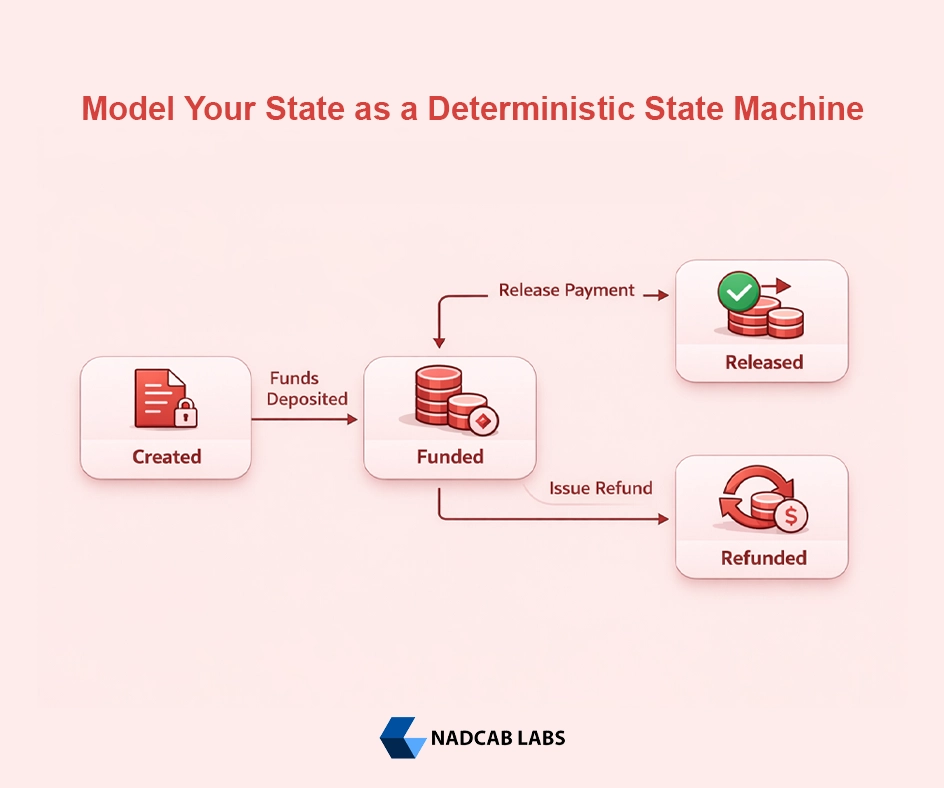
What Is a Finite State Machine
A finite state machine is a model where:
- The system starts in a known state
- Only specific transitions are allowed
- Invalid transitions are rejected
For smart contracts, this approach keeps logic clean, secure, and easy to reason about.
Simple Escrow Example
Consider an escrow contract.
The lifecycle looks like this:
- Created: The escrow is deployed but not funded
- Funded: Funds are deposited into the contract
- Released: Funds are sent to the receiver
- Refunded: Funds are returned to the sender
The valid flows are:
- Created → Funded → Released
- Created → Funded → Refunded
No other transitions should be allowed. You should never be able to release funds before funding or refund after release.
Why This Matters
Without clear state modeling, contracts become messy. Functions start checking random conditions, bugs slip in, and edge cases appear. Many real-world hacks happened because contracts allowed unexpected transitions.
A state machine forces discipline. It ensures that every action is legal, intentional, and verifiable.
Only Specific Transitions Are Allowed
Each function in your contract should move the system from one state to another valid state. If a user tries to perform an action that does not match the current state, the transaction must fail.
For example:
- Deposit funds only when the state is Created
- Release funds only when the state is Funded
- Refund funds only when the state is Funded
This prevents misuse and logical errors.
Emit Events on Every Transition
Every time the state changes, the contract should emit an event. Events act like a public log that off-chain systems can listen to.
Events help with:
- Tracking contract history
- Debugging issues
- Building dashboards and notifications
They make your system transparent and easier to monitor.
Core Deliverables of a State Machine Contract
- State enums
Define all possible states using enums. This makes the contract readable and avoids magic values. - Transition functions
Each state change should happen through a dedicated function. Functions should have a single clear purpose. - Transition guards
Use require checks to ensure transitions happen only from valid states. These guards are your safety locks. - For example, a release function should check that the current state is Funded before executing.
The Golden Rule
If you cannot draw the state diagram on paper, then your smart contract architecture is not ready.
4) Design Storage Layout (What Is Stored, Where, and Why)
Smart contract storage is one of the most important design decisions in blockchain. Storage on-chain is expensive, permanent, and directly affects gas costs. A poor storage layout can make your contract slow, costly, and hard to upgrade. A clean storage layout makes your contract efficient, secure, and easier to maintain.
Before writing code, you should clearly decide what data you need to store, where it should live, and why it must be on-chain.
Key Storage Design Choices
- Use mappings for per-user records
Mappings like mapping(address => uint256) are ideal for storing user-specific data such as balances, stakes, or positions. They provide constant-time access and scale well even with millions of users. Unlike arrays, mappings do not grow in a way that increases gas costs for other users. - Use structs to group related data
When multiple values belong together, store them inside a struct. For example, a user position may include amount, timestamp, and status. Grouping related fields improves readability and reduces mistakes. It also helps keep logic organized when updating or validating state. - Keep storage minimal
Every storage write costs gas. Storing unnecessary values increases transaction costs for users. If something can be calculated off-chain or derived from events, do not store it. Only store data that is required for contract logic or verification. - Avoid unbounded arrays
Arrays that grow endlessly are dangerous. Iterating over large arrays can exceed gas limits and make functions unusable. This can lead to denial-of-service risks. If you need to track many users or items, prefer mappings combined with events and off-chain indexing.
Typical Storage Layout Structure
A well-structured contract usually separates storage into clear sections. This makes audits easier and reduces upgrade risks.
- Configuration state
This includes values that control how the contract behaves. Examples are fees, limits, external contract addresses, or time settings. Some values may be immutable, while others can be updated by an admin. Keeping configuration separate avoids accidental changes to core logic. - Core state
This is the heart of the contract. It includes balances, positions, orders, staking data, or escrow information. This state changes frequently and must be carefully protected with proper checks. - Access control state
Roles, permissions, and allow lists should be stored clearly. This ensures that only authorized addresses can perform sensitive actions. Mixing access control data with business logic makes audits harder and increases risk. - Accounting state
This includes fees collected, treasury balances, reward claims, and pending pay outs. Accounting data should be precise and easy to verify to avoid financial mismatches.
Why Storage Layout Matters
Storage layout affects more than gas costs. It impacts:
- Security and auditability
- Upgrade safety in proxy contracts
- Readability for future developers
- Performance at scale
Many real-world bugs happen not because logic is wrong, but because storage was poorly structured.
Final Rule to Remember
Design your storage layout before writing functions. If you know exactly what you store and why, your logic becomes simpler and safer.
Smart contracts are long-lived systems. A clean storage layout is like a strong foundation. You may not see it, but everything depends on it.
5) Define External Interfaces (How Others Will Interact)
External interfaces define how users, apps, and other contracts talk to your smart contract. Think of them as the public API of your blockchain system. If this layer is messy, confusing, or unsafe, even a well-written contract will be hard to use and easy to misuse.
Good interface design is about clarity. Each function should have a clear purpose, predictable behavior, and strict access rules.
Split Functions by Intent
The first rule of interface design is to group functions by what they are meant to do. Mixing everything together creates confusion and increases the chance of bugs.
Read-Only Functions (View)
Read-only functions do not change contract state. They only return data.
Examples include:
- getPosition()
- balanceOf()
- quote()
These functions are free to call and safe for dashboards, analytics tools, and other contracts. They help users understand the current state without any risk. A good contract exposes enough read functions so off-chain systems do not need to guess or recompute important values.
State-Changing Functions (Write)
Write functions change the contract state and usually involve tokens or permissions.
Examples include:
- deposit()
- withdraw()
- swap()
- claim()
These functions must be carefully protected with validation checks, access rules, and state guards. Each write function should do one thing clearly. Avoid functions that perform multiple actions unless absolutely necessary.
Admin Functions
Admin functions control configuration and emergency actions.
Examples include:
- setFee()
- pause()
- setOracle()
These functions should be restricted to specific roles. Admin power must be visible, limited, and easy to audit. Hidden or overly powerful admin functions are a major red flag in security reviews.
Events Are Not Optional
Events are how your contract communicates with the outside world. They act as the source of truth for off-chain systems.
Every important action should emit an event, including:
- Deposits and withdrawals
- State transitions
- Admin changes
Events allow frontends, indexers, and monitoring tools to track what happens without reading storage repeatedly. They also make debugging and analytics much easier.
Use Custom Errors
Custom errors improve both clarity and gas efficiency. Instead of using generic error messages, define clear errors for common failure cases. This helps developers and users understand why a transaction failed. It also reduces gas costs compared to long revert strings.
Clear errors turn silent failures into understandable feedback.
Why Interface Design Matters
Your external interface will likely outlive your frontend and even your development team. Other contracts, bots, and third-party tools will rely on it. Once deployed, changing interfaces is difficult and risky.
A clean interface:
- Reduces user mistakes
- Simplifies audits
- Improves composability
- Makes integrations smoother
Final Rule
If someone unfamiliar with your project cannot understand how to use your contract by reading the interface, the design needs work.
Great smart contracts feel boring to use. Inputs are obvious, outputs are predictable, and nothing surprising happens. That is exactly how trust is built on-chain.
6) Permission in Smart Contract Architecture – Who Can Do What
When building smart contracts, deciding who can do what is crucial for security and smooth operation. This is called the permission architecture. It ensures that only the right people can perform sensitive actions, like updating the contract, pausing operations, or moving funds. Without a proper permission system, a single mistake or hack could compromise the entire contract.
Choosing the Right Permission Pattern
- Ownable Pattern
For simple projects, the Ownable pattern works well. In this pattern, there is usually one owner who controls critical actions. For example, the owner can update settings or withdraw funds. This is easy to implement but has risks. If the owner’s wallet is hacked or lost, the contract may become unsafe or unusable. So, Ownable is better for small, low-risk applications. - Role-Based Access Control (RBAC)
For bigger, production-level systems, RBAC is the safer option. Here, different roles are defined, and each role has specific permissions. Typical roles include:
- Admin: Full access to update contract settings, upgrade logic, or manage key functions.
- Operator: Handles routine actions like managing user transactions or executing regular operations.
- Guardian: Responsible for emergency measures, like pausing the contract if something goes wrong.
Using RBAC ensures that no single wallet or person has full control. It also makes it easier to digital contract audit and manage permissions in complex systems.
- Timelock
Some actions are high-stakes, like upgrading a contract or moving large amounts of funds. A time lock delays such actions for a set period (e.g., 24–72 hours). This gives the community or other stakeholders time to review and react if something seems wrong. Time locks are often used in decentralized finance (DeFi) projects to prevent sudden malicious changes.
Essential Features to Include
- Pause/Unpause (Circuit Breaker):
Every production system should include a way to pause operations in emergencies. This is often called a “circuit breaker.” If a bug, attack, or abnormal activity occurs, the pause feature can stop all sensitive operations immediately to prevent losses. - Separate Guardian Role:
The pause function should not be controlled by the main admin alone. A guardian role is recommended for emergencies. This ensures that even if an admin’s wallet is compromised, the system can still be protected. - Avoid Single Hot Wallet Control:
Never let a single wallet have full control in a production system. Instead, spread responsibilities across multiple roles and, if possible, use multi-signature wallets. This reduces the risk of losing everything if one key is hacked or lost.
Best Practices
- Clearly define roles and responsibilities before deployment.
- Use well-tested libraries (like OpenZeppelin) for Ownable or RBAC patterns.
- Document all permission structures so that developers, auditors, and users understand who can do what.
- Test all permission rules thoroughly on test networks to ensure there are no loopholes.
- Combine roles, timelocks, and emergency pause mechanisms for maximum security.
By carefully designing the permission architecture, you make your smart contract architecture are secure, resilient, and easier to manage. It ensures that the right people can act in emergencies while protecting the system from single points of failure. Following these patterns helps prevent hacks, mistakes, and operational risks, which is essential for building trust and confidence among users.
7) Upgradeability Strategy in Smart Contracts: How to Plan Changes
When building smart contracts, one of the key decisions is whether the contract can be upgraded after deployment. Upgradeability allows you to fix bugs, add new features, or adapt to changing requirements. However, it also adds complexity and potential risks, so it must be carefully planned.
Options for Upgradeability
- Immutable Contracts
The simplest and safest option is to make your contract immutable, meaning it cannot be changed after deployment. If you need to update or fix something, you must redeploy a new version of the contract. This approach is easy to implement, secure, and predictable. It is ideal for small projects or contracts where logic is unlikely to change. - Proxy Upgradeable Contracts
For projects that require flexibility, you can use a proxy upgradeable pattern, like UUPS (Universal Upgradeable Proxy Standard) or Transparent proxies. In this setup, the proxy contract stays the same while the logic contract can be replaced. This allows updates without changing the contract address, so users continue interacting with the same contract.
Using proxies requires extra architectural considerations:- Storage Slot Stability: Ensure that storage variables do not get overwritten when logic changes.
- Initialization Control: Use initializer functions instead of constructors to set up the contract.
- Upgrade Authorization: Define who can approve upgrades to prevent malicious or accidental changes.
- Migration Plan: Plan how old state data will map to the new logic to avoid inconsistencies.
- Modular / Facet Upgradeability (Diamond Pattern)
For large systems with many functions, a modular or Diamond pattern is recommended. Here, the contract is divided into multiple smaller facets, each handling a part of the system. This allows upgrading individual facets without affecting the entire contract. It is ideal for complex DeFi platforms, NFT ecosystems, or any system that evolves over time.
Best Practices for Upgradeable Contracts
- Versioned Initialization: Always version your initializer functions so new updates do not overwrite old state or settings.
- Feature Flags: Use feature flags to enable or disable new functionalities safely. This helps test new features without disrupting the live system.
- Backward Compatible Events: Maintain compatibility with events from older versions so analytics, dashboards, and external systems continue working.
- Clear Governance: Only authorized entities should be able to upgrade contracts, often using multi-signature wallets or timelocks for added security.
Deciding “No Upgrades”
Sometimes, the best strategy is to explicitly decide not to allow upgrades. This is the safest choice and eliminates risks associated with upgrade mechanisms. It is especially suitable when:
- The contract logic is simple and unlikely to change.
- Security and trust are more important than flexibility.
- You want users to interact with a completely predictable and unchangeable system.
Choosing the right upgradeability strategy balances flexibility with security. Immutable contracts are safe and simple but require redeployment for changes. Proxy upgradeable contracts allow flexibility but need careful planning for storage, initialization, and migration. Modular patterns are great for large systems but come with higher complexity.
By clearly defining your upgrade strategy upfront, you protect your system from accidental or malicious changes, ensure smooth feature updates, and maintain user trust. Whether you choose no upgrades or a sophisticated proxy/facet system, having a documented plan for versioning, migration, and governance is essential for long-term success.
8) External Dependencies in Smart Contract Architecture
Smart contracts rarely work alone. They often interact with external contracts, such as tokens, oracles, or decentralized exchanges (DEXs). While these interactions add functionality, they also introduce security risks, because anything outside your contract is a potential attack surface. Properly managing these dependencies is essential for safe and reliable smart contract systems.
Common External Dependencies
Tokens
Smart contracts often interact with tokens, including ERC-20 (fungible tokens), ERC-721 (NFTs), and ERC-1155 (multi-token standard). However, not all tokens behave the same way. Some may have special features like:
- Fee-on-transfer: deducting a fee on each transaction.
- Rebasing: changing balances automatically to maintain a target supply.
If your contract assumes a token behaves normally, it could cause unexpected failures or loss of funds.
Oracles
Oracles, like Chainlink, provide external data to your contract (e.g., prices, exchange rates, or weather data). While useful, they come with risks:
- Data may become stale if the oracle stops updating.
- Decimals or formatting may vary, causing miscalculations.
- Heartbeat and fallback mechanisms must be implemented to handle failures.
- DEX Routers and Pools
When interacting with DEXs like Uniswap or PancakeSwap, your contract might swap tokens or provide liquidity. External routers and pools can fail or behave unexpectedly, so extra checks and safeguards are necessary. - Vaults and Lending Protocols
Contracts that deposit funds into vaults or lending platforms must account for interest, withdrawal restrictions, and changes in underlying protocols. Blindly trusting these external systems can lead to losses or locked funds.
Best Practices for External Dependencies
- Never assume a token is well-behaved: Always account for edge cases like fees, rebasing, or malicious token behavior. Test thoroughly with different token types.
- Wrap external calls with checks: Don’t trust that every external function will succeed. Use try/catch or validation logic to handle failures gracefully.
- Limit approvals: Only approve the exact amount needed when interacting with tokens, and reset approvals to zero when not needed. This reduces the risk of someone exploiting unlimited allowances.
- Oracle safeguards: Ensure your contract handles stale data, correctly interprets decimals, checks heartbeats, and has a fallback plan if the oracle fails.
- Audit external protocols: When interacting with DEXs, vaults, or lending protocols, understand how they work and their risk profile. Only integrate trusted and widely used contracts.
Why This Matters
External dependencies expand your contract’s attack surface, meaning attackers can exploit weaknesses in the systems you rely on. By following strict rules and safeguards, you minimize risks and ensure your contract behaves reliably under different conditions.
9) Security Architecture: Threat Model and Controls
Security is the most critical aspect of smart contract design because contracts handle real funds and operate in a fully public environment. A small bug or oversight can lead to huge financial losses. A strong security architecture starts with understanding possible threats and implementing robust controls to prevent them.
Mandatory Controls for EVM-Style Systems:
- Checks-Effects-Interactions (CEI):
Always perform all necessary checks and update the contract state before interacting with external contracts. This prevents attackers from exploiting reentrancy vulnerabilities, where functions can be repeatedly called before finishing execution. - Reentrancy Guard:
Sensitive functions that handle funds should include a reentrancy guard. This ensures the same function cannot be called multiple times simultaneously, protecting against theft and unexpected behavior. - Input Validation:
Every input must be validated to prevent incorrect or malicious data from affecting the contract. This includes transaction amounts, deadlines, and slippage. Proper input checks keep your contract predictable and secure. - Integer Safety:
Even though Solidity 0.8+ automatically prevents overflows and underflows, you should still carefully handle type casting and arithmetic operations to avoid unexpected results. - Access Control Tests:
Verify that only authorized roles can perform sensitive actions such as pausing the contract, upgrading logic, or withdrawing funds. Testing access paths ensures that no unauthorized actions are possible. - Pause Paths Tested:
Emergency pause mechanisms (circuit breakers) must be fully tested. It’s not enough to just have a pause function; it should work correctly without breaking other functionalities.
Defining Invariants:
Invariants are rules that should always hold to maintain contract integrity:
- Total deposits = sum of user balances ensures all funds are accounted for.
- Treasury fee ≤ maxFee prevents overcharging users.
- Collateral ratio never below X ensures solvency in lending systems.
These controls and invariants make the contract predictable, trustworthy, and resistant to attacks.
10) Event + Indexing Architecture: How the App Knows What Happened
Smart contracts by themselves are not searchable like a database. To make your application aware of important events, you need an event and indexing architecture.
Event Design:
- Emit an event for every meaningful state transition, such as deposits, withdrawals, or trades.
- Create events for configuration changes and admin actions.
- Include indexed parameters like user addresses, token IDs, pool IDs, or transaction amounts to make events easier to query.
Indexing and Listening:
- Use a subgraph (like The Graph) or a custom listener service to process and index events.
- This allows your frontend, dashboards, and analytics tools to query contract activity efficiently.
Event Plan Deliverables:
- One event per state transition: Captures the effect of user actions.
- One event for config changes: Tracks updates to fees, limits, or addresses.
- One event for admin actions: Logs important administrative operations for transparency.
A well-structured event and indexing architecture ensures that your app can reliably track every change, maintain transparency, and provide accurate information to users and other systems.
11) Testing Architecture: What You Validate Before Mainnet
Testing is one of the most critical steps in smart contracts. Unlike regular software, digital contracts handle real funds, so any bug or vulnerability can lead to financial loss. A strong testing architecture ensures your contract is secure, functional, and performs as expected under all conditions.
Layers of Testing
Unit Tests
Unit tests focus on individual functions, checking both normal and edge cases. Each function should be tested for:
- Success paths: Does the function work correctly under normal conditions?
- Revert paths: Does the function handle invalid input or incorrect state gracefully?
- Boundary values: Test extreme or unusual values to ensure no unexpected behavior.
Property / Fuzz Tests
Property or fuzz testing checks that invariants hold under random or unpredictable sequences. Examples include:
- Total deposits always equal the sum of all user balances
- Treasury fees never exceed a set maximum
- Collateral ratios in lending contracts stay above safe levels
Fuzz testing helps detect rare issues that normal unit tests might miss.
Integration Tests
Integration tests ensure the contract works correctly with other systems. These tests include:
- Token mocks: Simulate ERC-20, ERC-721, or ERC-1155 token behavior
- Oracle mocks: Test price feeds, including handling stale or incorrect data
- Router mocks: Check DEX swaps, liquidity operations, and edge cases
Simulation / Adversarial Tests
Simulation tests mimic real-world attacks and unexpected scenarios, such as:
- Front-running
- Reentrancy attacks
- Oracle staleness or malfunction
These tests help ensure the contract is resilient under adversarial conditions.
Additional Checks
- Static Analysis (Slither): Automatically detects coding mistakes and unsafe patterns without executing the contract.
- Formal-ish Checks (Echidna / Foundry): Validate invariants and properties using automated tools to ensure the contract behaves correctly in all scenarios.
- Gas Snapshots: Track gas usage to prevent regression and ensure the contract remains efficient after updates.
A well-planned testing architecture helps catch issues early, reduces risk, and builds trust before mainnet deployment.
12) Deployment + Operations Architecture: Production Reality
Deploying a smart contract to production requires careful planning. Even well-tested contracts can fail if operational procedures are not in place.[3]
Production Requirements:
Versioned Deployments:
Use tags and verified source code for each release. This ensures transparency and helps track which version is running on the mainnet.
Admin Key Management:
Secure administrative actions using multisig wallets and timelocks. This reduces the risk of single points of failure or misuse of admin privileges.
Monitoring:
Continuously monitor the contract for unusual activity or issues:
- Paused state: Ensure emergency pause functions are operational
- Abnormal event rates: Detect unusual user activity or spikes in transactions
- Failed transaction spikes: Monitor errors that could indicate bugs or attacks
Oracle staleness: Check if external data sources are not updating properly
Runbooks:
Define step-by-step procedures for operational events:
- Pause procedure: How to halt the contract in emergencies
- Upgrade procedure: How to safely deploy new versions or fix bugs
- Incident response steps: How to respond to hacks, failures, or abnormal behavior
A robust deployment and operations architecture combines version control, secure key management, proactive monitoring, and clear operational procedures. This ensures your smart contract system is not only secure but also manageable, resilient, and auditable in production. Proper planning and operational discipline help maintain user trust and reduce the risk of costly mistakes.
Build Strong & Secure Smart Contract Architecture
Nadcab Labs explains smart contract architecture in a clear and practical way, helping you design secure, scalable, and maintainable blockchain solutions from the ground up.
Smart Contract Blueprint – Typical Modules for Production
A well-structured smart contract system is easier to manage, maintain, and secure. In production, contracts are usually modular, separating concerns into different components so that each module has a clear responsibility. This makes upgrades, auditing, and debugging simpler and safer.
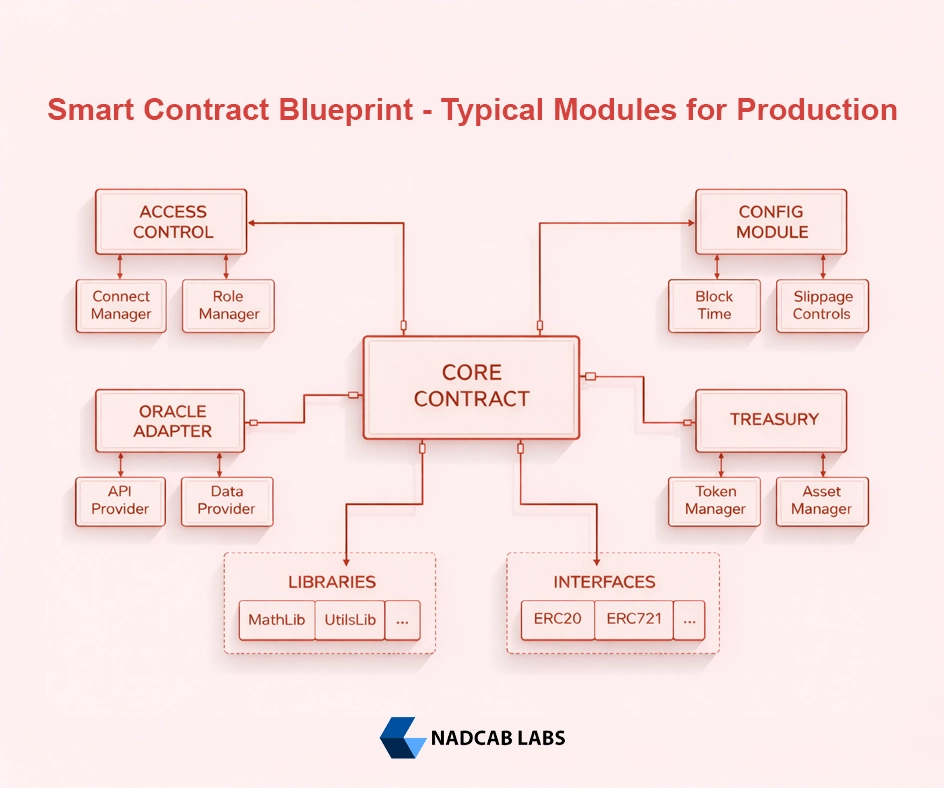
1. Core Contract (State Machine + Accounting)
The core contract is the heart of the system. It handles the main logic, tracks balances, and enforces rules. Often designed as a state machine, it defines how the contract transitions from one state to another (e.g., deposit → stake → withdraw). Accounting functions track user balances, deposits, rewards, or any other on-chain assets. Keeping core logic separate ensures clarity and minimizes errors.
2. AccessControl Module (Roles)
Permissions are essential for security. The AccessControl module manages roles like Admin, Operator, or Guardian. Roles determine who can perform sensitive actions, such as pausing the contract, upgrading logic, or updating fees. Using a dedicated module for roles makes it easier to add or remove roles safely without touching core logic.
3. Config Module (Fees, Addresses)
Configuration parameters like fees, addresses of external contracts, or system limits are stored in a Config module. Separating configuration allows updates without modifying core logic, reducing the risk of introducing bugs during routine changes. This module is usually controlled by admin roles with proper safeguards like timelocks.
4. Oracle Adapter (Normalize Decimals/Staleness)
Contracts often rely on external data, like price feeds. An Oracle Adapter standardizes this data for your contract, handling differences in decimal precision and checking for stale or invalid updates. By isolating oracle logic, you reduce the risk of corrupted or outdated data affecting the main contract.
5. Treasury / FeeCollector
A separate Treasury or FeeCollector module manages protocol funds, fees, or reward distributions. This isolation ensures that fund handling is transparent, auditable, and easy to monitor. It also makes emergency interventions simpler if needed.
6. Library (Math, Validation)
Common calculations and validations, like safe math operations, percentage calculations, or input checks, are kept in a library module. Using libraries avoids duplicating code across contracts and ensures consistent behavior. Popular choices include OpenZeppelin libraries for safe math, role handling, and ERC interfaces.
7. Interfaces (ERC20, Oracle, Router)
Interfaces define how your contract communicates with external contracts like ERC20 tokens, oracles, or DEX routers. Keeping interfaces separate improves readability, allows easier upgrades, and ensures that changes in external contracts don’t unintentionally break your system.
Final Words
Smart contract architecture is the blueprint that defines how contracts are built, how they interact, and how they handle data, security, and upgrades. A well-designed architecture ensures the system is safe, efficient, and scalable. It carefully decides what should be on-chain and off-chain, uses proven patterns like proxy, factory, singleton, and oracle, and separates logic, storage, access control, and interfaces.
Security is built-in through proper permission management, state machines, and checks for external dependencies. Upgradeability is planned with patterns like proxy or modular contracts, while storage layout and event design make the system predictable and easy to maintain. Testing at multiple levels ensures reliability before deployment, and operational planning keeps contracts running safely in production.
In short, smart contract architecture is about planning and organizing contracts so they are secure, maintainable, and user-friendly. Proper architecture prevents hacks, reduces costs, and ensures the system works as intended even as it grows or evolves.
FAQs - Smart Contract Architecture
Smart contract architecture is the way a smart contract is organized and structured on the blockchain. It shows how different parts like logic, data, security, and interaction layers work together. A good architecture makes contracts easy to use, secure, and efficient, and ensures that they can handle more users, integrate with other systems, and be maintained or upgraded in the future.
Smart contract architecture is important because it determines the security, efficiency, and reliability of the contract. Poor architecture can lead to bugs, hacks, or high transaction costs. A well-designed structure ensures smooth operations, easy upgrades, and better performance. It also makes development easier, reduces risks, and allows contracts to handle complex interactions without breaking or losing funds.
The main components of smart contract architecture include: logic layer (where rules and functions are written), data/storage layer (where information is stored), interaction layer (how users and other contracts interact), security layer (protection against attacks), and upgrade layer (allowing safe updates). Together, these components create a secure, scalable, and reliable contract that works efficiently on the blockchain and can evolve with new features.
Some of the best platforms for building smart contracts are Ethereum, Binance Smart Chain, Solana, Polygon, and Avalanche. These platforms provide tools, documentation, and strong community support. They also support smart contract languages like Solidity, Rust, or Vyper, and offer high security and scalability. Choosing the right platform depends on the project’s requirements, speed, fees, and ecosystem compatibility.
Popular tools for developing smart contract architecture include: Remix (online Solidity editor), Hardhat and Truffle (for testing and deployment), OpenZeppelin (secure contract libraries), Ganache (local blockchain testing), and Chainlink (for oracles). These tools help developers write, test, debug, deploy, and upgrade contracts efficiently while ensuring security and compatibility across platforms.
On-chain data includes critical contract logic, balances, ownership, and transaction records because it needs transparency, security, and immutability. Off-chain data can be large files, media, metadata, or external information like APIs, which are too costly or unnecessary to store on the blockchain. Storing data off-chain reduces costs and improves performance while keeping sensitive and important rules and records secure on-chain.
Testing architecture should include unit tests (to check each function), integration tests (to see how parts work together), and system tests (to check the whole contract). Testing should also include security tests for vulnerabilities and simulation on testnets before deployment. Using automated scripts, test networks, and mock data ensures contracts behave correctly, reduce bugs, and handle unexpected scenarios efficiently.
A typical smart contract blueprint shows layers like logic, storage, interaction, security, and upgrade paths. It also includes function flowcharts, access controls, events, and external calls. The blueprint documents how the contract will operate, how data will be stored, and how users and other contracts interact. This serves as a roadmap for developers to implement, test, and maintain contracts efficiently and securely.
External dependencies, like oracles or other contracts, should be verified, trusted, and limited. Contracts should validate input from external sources, use fallback mechanisms, and have access control to prevent misuse. Dependency failures should not break the contract. Testing with mocks and simulating real-world scenarios ensures contracts can safely interact with outside systems without compromising security or performance.
Smart contracts are improving, but full self-upgradability is still evolving. Currently, proxy patterns and modular designs allow safe upgrades while keeping data intact. In the future, with better blockchain standards, contracts may include automated upgrade mechanisms, AI-assisted patches, or governance-driven upgrades. However, full automation must balance flexibility with security to prevent hacks or misuse.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







