
In 2026 cryptocurrencies are no longer a niche technology they are becoming a normal part of global finance. Millions of people use crypto for trading, investing or payments and adoption continues to grow steadily. However many still misunderstand what a “crypto wallet” actually is. Understanding private vs public keys in crypto wallets is essential for securing your funds and managing crypto wallet keys properly. It is not a bank account nor an app that stores money nor a place on the internet. A wallet is simply a tool to manage cryptographic keys that control your funds. Losing access to those keys often means losing your crypto permanently.
Understanding private vs public keys in crypto wallets is essential for anyone serious about protecting their digital assets. This guide provides a realistic easy-to-read explanation of how wallets work, how keys operate, the risks involved and practical advice for keeping your crypto secure. It also incorporates recent 2025 data and projections for 2026 to highlight why proper key management has never been more important.
What Are Private vs Public Keys in Crypto Wallets
In 2026, digital transactions are expanding beyond major cryptocurrencies like Bitcoin and Ethereum, as people now use blockchain for CBDCs (Central Bank Digital Currencies), tokenized assets, digital identities, and Web3 applications. To securely own and transfer these digital assets, crypto wallets do not store coins directly, instead they store two cryptographic keys that control ownership and access, a public key and a private key.
Public Key
A public key in a crypto wallet serves as a receive address that can be safely shared with anyone to accept digital assets, much like sharing a UPI ID or bank account number. It is generated from the private key using one-way cryptography, making it impossible to reverse-engineer the private key. This relationship highlights the importance of private vs public keys in crypto wallets, where the public key enables receiving funds without exposing the private key. In 2026 public keys are becoming more versatile as they are increasingly linked to decentralized identities (DIDs), meaning one public key could soon be used not only to receive crypto but also to log into Web3 platforms, access metaverse assets and interact securely with decentralized applications.
Private Key
How Wallets Use Keys
A crypto wallet doesn’t actually store your cryptocurrency inside your phone, computer or any device. The coins themselves always remain on the blockchain, [1]
which is the public ledger that tracks all transactions. It stores private vs public keys in crypto wallets , which act like access tools that allow you to control and use your crypto. Think of the blockchain as a massive public locker room filled with thousands of lockers, each containing digital money. To open any locker you need a key. Your wallet is the tool that keeps these keys safe and allows you to use them when needed.
Every wallet works using private vs public keys in crypto wallets that complement each other. The first is the public key often represented as a wallet address, which is used to receive money. You can safely share this with anyone, similar to sharing your bank account number. The second is the private key, which must remain secret. This key allows you to send money and authorize transactions, acting much like your ATM PIN or fingerprint. The public key and private key work together like a lock and a key. The public key is used to generate addresses where funds can be received, while the private key provides access to those funds.
Difference Between Private vs Public Keys in Crypto Wallets
| Aspect | Public Key | Private Key |
|---|---|---|
| Definition | Cryptographic code derived from a private key, used to receive funds or information. Safe to share. | Secret cryptographic code that controls and grants access to digital assets. Must remain confidential. |
| Purpose | Allows others to send funds or encrypt data for you identifies you without revealing sensitive information. | Signs transactions, decrypts data and proves ownership, authorizes actions on blockchain. |
| Sharing | Designed to be shared openly, acts as a wallet address. | Must never be shared with anyone who can access your assets. |
| Generation | Derived mathematically from the private key using a one-way function. | Created first, randomly generated, and forms the foundation of the key pair. |
| Function in Security | Verifies digital signatures, ensures transactions/data come from the rightful sender. | Signs transactions/messages, ensures only the owner can authorize actions. |
| Role in Security | Enables trustless verification, visible and verifiable for everyone. | The security anchor of the wallet; controls access to funds and assets. |
| Risk if Exposed | No risk, safe to expose. | High risk, assets can be stolen and access lost permanently. |
| User Interaction | Shared for receiving payments or verification, simple to use. | Requires careful management, secure backup, and minimal direct interaction. |
Private vs public keys in crypto wallets mainly use two ways, receiving crypto and sending crypto. When you receive crypto, you simply share your wallet address and someone can send funds to it. The blockchain records the transaction as belonging to your wallet. Importantly you do not need to use your private key to receive funds only when you want to send them.
When you send crypto, the private key becomes your digital signature. The transaction starts when you enter the receiver’s wallet address and amount, after which the wallet uses your private key to sign the request securely. The key itself never leaves your device. Once signed, the transaction is broadcast to the blockchain, where nodes verify the signature using your public key. After the network confirms it as valid, the transfer is completed. This proves that private vs public keys in crypto wallets work together to authorize transactions while keeping your private key safely hidden.
The key function of a wallet is not to store your digital coins, but to secure the private key, which acts as your access tool to digital assets. A wallet uses this private key to sign transactions safely while protecting it from hackers, malware or accidental exposure. When understanding private vs public keys in crypto wallets, the main focus is that the public key (or address) allows others to send funds to you, while the private key must remain secret to control and spend those funds. Different wallets whether mobile apps, exchange wallets, hardware devices or multisignature solutions are designed to protect this private key in different ways. Your choice of wallet affects convenience, security and ownership control, but the core principle always stays the same: safeguard the private key and use it correctly to manage crypto securely.
Different Types of Wallets and Where Your Key Lives
Not all wallets are created equal. Understanding private vs public keys in crypto wallets will help you choose the right wallet type and manage your crypto wallet keys safely. The main difference between private vs public keys in crypto wallets depends on who controls the private key, as this control decides how secure your crypto will be, how easily you can use the wallet and who is responsible if anything goes wrong.
| Wallet Type | Who Holds the Private Key? / Where Is It Stored? | What This Means for You |
|---|---|---|
| Custodial Wallets (e.g., Exchange Wallets) | The exchange or company controls the private key not you. | Very easy to use (like a bank) but you don’t truly own your crypto. If the platform blocks withdrawals or gets hacked, you can lose funds. |
| Non-Custodial Software Wallets (Mobile/Desktop) | The private key is created and stored on your phone or computer. You control it. | You fully own your crypto. Good for daily use. But if your device is lost, damaged or hacked, you may lose access unless backed up. |
| Hardware Wallets (USB-like Devices) | The private key is stored inside a secure hardware device and never leaves it. | Extremely secure even if your phone/computer has a virus. Best for large savings. Requires buying a device and learning how to use it. |
| Paper / Air-Gapped Wallets | The private key is written or engraved on paper/metal and kept completely offline. | Completely offline and hacker-proof. But easy to lose, tear, burn, or misplace. One mistake can permanently lose funds. |
| Multiset / Smart-Contract Wallets | Multiple private keys are required or smart rules control access. | Very secure. Ideal for companies, teams, or high-value crypto. Harder to set up but reduces risk—no single key can lose everything. |
2026 Crypto Wallet Adoption and Risks
As of 2025, there were approximately 716 million [2] cryptocurrency users globally. Analysts project that by 2026, the number of crypto holders will surpass 820 million, driven by adoption in emerging markets, mobile wallets, and decentralized finance (DeFi).
The wealth within the crypto ecosystem has grown dramatically. In 2025, an estimated 241,700 individuals worldwide became crypto millionaires and this number is projected to reach around 320,000 by 2026. As more wealth enters blockchain markets, the security of digital assets becomes increasingly important. This rise makes understanding private vs public keys in crypto wallets essential, because the private key ultimately decides who truly owns that wealth.
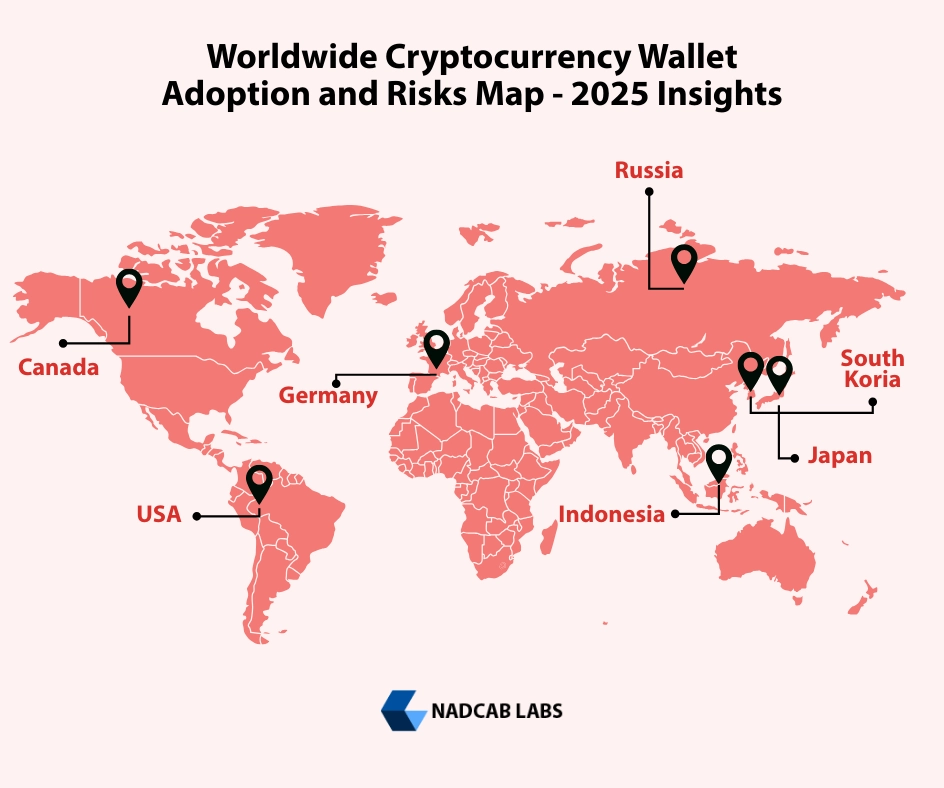
However, with growth comes risk. In 2025 alone, over US$ 2.17 billion [3]was stolen from exchanges and wallet services, with the largest single hack (ByBit breach) accounting for US$ 1.5 billion roughly 69% of total losses. It notes that many stolen-fund victims are concentrated in the USA, Germany, Russia, Canada, Japan, Indonesia, and South Korea. Attacks on personal wallets also increased, with 23% of stolen value coming from individual user wallets.
Projections for 2026 indicate that crypto theft could exceed US$2.5 billion, with hackers increasingly targeting both centralized exchanges and users managing their own keys. As more people adopt digital assets, attacks like phishing, malware injections and address-poisoning exploits are expected to rise. This highlights why understanding Private vs Public Keys in Crypto Wallets is becoming more critical than ever users who fail to protect their private keys may lose full control of their assets.
Best Practices for Secure Key Management
If you hold (or plan to hold) crypto even small amounts, adopting a few basic habits can greatly reduce risk. Here are recommended practices:
- If your holdings are significant, use a hardware wallet to protect your private vs public keys in crypto wallets. Think of it as a secure, safe private key that resides offline, in a tamper-resistant device, and Never store your wallet private key online.
- Avoid storing your seed phrase or private key in plaintext on device, in email drafts, screenshots, notes, cloud storage, or copy/paste. These are very common ways keys are compromised, especially in phishing and malware attacks.
- Use offline backups to secure your wallet public key and seed phrase wallet or metal and ideally keep more than one copy, stored in different secure physical locations (for example: one at home safe, another in a bank’s safe deposit, or a trusted relative’s house).
- Separate your funds by purpose: treat part of your holdings as “hot funds” (small amounts, for frequent use) in software wallets, and the rest as “cold funds” (long-term savings) stored in more secure wallets (hardware, offline). This reduces exposure for your main investments.
- Always manually verify the recipient address before sending funds. Avoid relying on autofill, history, or pre-saved addresses attackers often exploit to trick users into sending to wrong addresses.
- Once you create a backup (seed phrase), test the recovery immediately, restore the wallet using the backup on a separate device and do a small test transfer. This ensures your backup is valid and usable, not a forgotten or mistyped phrase.
- If you manage high-value holdings, or run a business/family fund, consider multisig wallets or smart-contract wallets. Spreading control across multiple keys (or requiring multiple approvals) reduces risk of single-point failure and adds a layer of security.
- Finally stay alert. Keep device OS and wallet software updated. Don’t install suspicious apps or browser extensions. Avoid sharing sensitive information. Treat crypto like a serious financial asset not a “toy”.
The Future of Security Starts With Your Keys
A crypto wallet is a digital safe-box controlled by your private vs public keys in crypto wallets. Where and how you store your keys defines your wallet key security. Where and how you store your keys on exchanges, software wallets, hardware devices, or offline backups defines the balance between security, convenience, and control.
In its report, the exchange said it found that 40.8% [4] of all crypto security incidents this year involved fraudsters deceiving victims through fake investment offers or impersonation tactics. The best way to protect yourself is through responsible key management, secure backups, layered security, and awareness of emerging threats. Your private key is your power. Your public address is your identity. Your security depends entirely on how you handle those keys.




