Key Takeaways
- Hierarchical Deterministic wallet infrastructure enables automated generation of millions of blockchain addresses from single master seeds using standardized derivation paths across multiple cryptocurrency networks.
- Address pool segregation strategies separate hot, warm, and cold storage addresses implementing security tiers that balance accessibility requirements with asset protection needs for operational efficiency.
- Real-time address indexing systems provide instant lookups mapping blockchain addresses to internal accounts enabling high-throughput wallet operations supporting thousands of concurrent transactions.
- Automated address rotation protocols enhance privacy and security by generating fresh addresses for each transaction preventing address reuse that leaks transaction history and user behavior patterns.
- Cross-chain address normalization layers abstract Blockchain Addresses-specific formats behind unified APIs simplifying multi-chain wallet management while maintaining compatibility with diverse address encoding schemes.
- Smart contract signature verification enables on-chain address ownership proof supporting decentralized identity systems and authorization mechanisms without centralized registries or trusted intermediaries.
- Compliance-aware address tagging systems classify addresses based on risk profiles tracking interactions with sanctioned entities enabling regulatory compliance and fraud prevention at scale.
- Multi-Party Computation wallet architectures distribute private key control across multiple parties eliminating single points of compromise while enabling collaborative transaction signing with policy enforcement.
Enterprise Blockchain Addresses operations demand sophisticated address management capabilities handling millions of wallet addresses across multiple cryptocurrency networks simultaneously. Traditional manual address generation and tracking methods collapse under scale requirements where exchanges, payment processors, and institutional custodians serve thousands of users with complex operational workflows. Blockchain technology infrastructure requires automated systems managing address lifecycle from generation through monitoring, reconciliation, and eventual retirement. Modern wallet platforms implement hierarchical deterministic key derivation, programmatic address allocation, intelligent pool management, and real-time monitoring infrastructure supporting institutional-grade operations. These systems must balance security, performance, compliance, and user experience requirements while maintaining compatibility across diverse Blockchain Addresses protocols with different address formats and signature schemes. Organizations successfully managing blockchain addresses at scale report 85% reductions in operational overhead and 60% improvements in security incident response times according to industry surveys conducted throughout 2025 and early 2026.[1]
Automated Blockchain Address Lifecycle Management at Scale
Address lifecycle management encompasses the complete operational workflow from initial generation through active use, monitoring, and eventual deactivation or archival. Automated systems orchestrate these phases without human intervention through policy-driven workflows triggered by events and conditions. Address generation occurs programmatically based on demand forecasting ensuring pools maintain sufficient capacity for new user registrations and transaction flows. Activation processes associate generated addresses with user accounts or organizational wallets establishing ownership mappings in internal databases. Active monitoring tracks inbound transactions, balance changes, and security events throughout the address operational period. Retirement procedures deactivate addresses following security rotations or user account closures while archiving historical data for compliance retention. Automation eliminates manual errors causing fund losses while accelerating operations supporting real-time user experiences. Modern platforms manage address lifecycles across dozens of Blockchain Addresses networks simultaneously handling heterogeneous protocols through abstraction layers. Organizations implement sophisticated state machines tracking address status transitions with audit logging for regulatory compliance and operational debugging requirements.
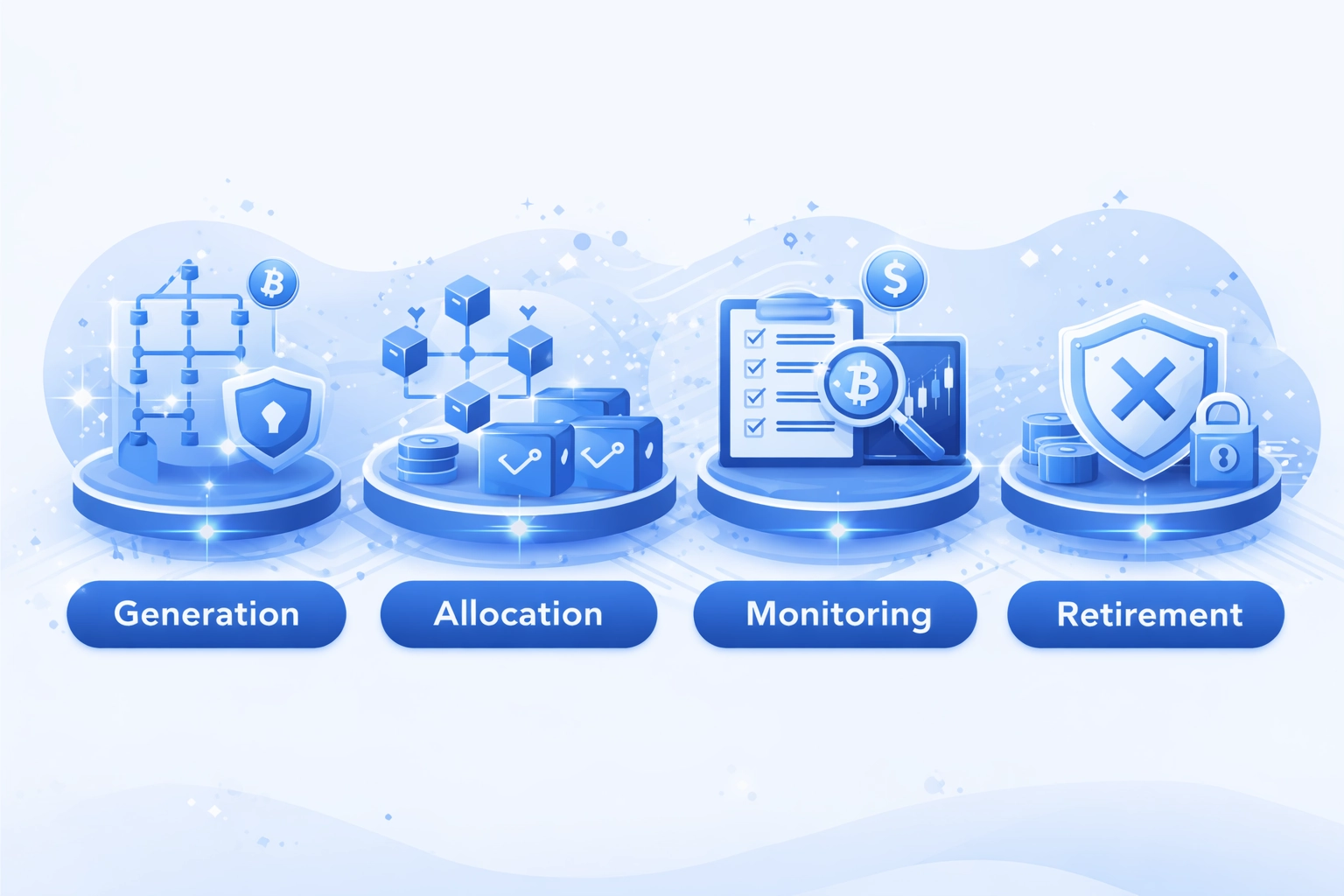 Address Lifecycle Stages
Address Lifecycle Stages
Generation
Programmatic creation of new addresses using HD wallet derivation or random generation with secure key storage in encrypted databases.
Allocation
Assignment of generated addresses to specific users, applications, or operational purposes with metadata tagging for tracking and categorization.
Monitoring
Real-time tracking of Blockchain Addresses activity including incoming transactions, balance changes, and security events requiring operational responses.
Retirement
Controlled deactivation of addresses following security rotations or user account closures with archival of historical data for compliance requirements.
Deterministic Address Generation Using HD Wallet Infrastructure
Hierarchical Deterministic wallets revolutionize address management by generating unlimited addresses from single master seeds through mathematical derivation functions. BIP32 standard defines the hierarchical key derivation algorithm using elliptic curve mathematics to produce child keys from parent keys deterministically. BIP39 specifies mnemonic seed phrase encoding enabling human-readable backup of master seeds through 12 or 24 word sequences. BIP44 establishes multi-account hierarchy with standardized derivation paths organizing addresses by purpose, coin type, account, and index. This architecture enables organizations to generate billions of addresses without storing individual private keys separately. Master seed backup becomes single point of recovery for entire address hierarchies simplifying operational procedures dramatically. Deterministic generation allows re-deriving addresses on-demand from seed material enabling lightweight wallet implementations. Organizations can generate addresses offline for cold storage without network connectivity enhancing security. The derivation path structure enables address segregation where different departments or purposes use distinct branches preventing operational conflicts while maintaining unified backup procedures.
BIP Standards for HD Wallet Implementation
| Standard | Purpose | Key Feature |
|---|---|---|
| BIP32 | Hierarchical deterministic key derivation algorithm | Derives child keys from parent keys using chain codes |
| BIP39 | Mnemonic code for generating deterministic seeds | Converts entropy to 12-24 word phrases for backup |
| BIP44 | Multi-account hierarchy for HD wallets | Standardizes derivation path structure across coins |
| BIP49 | Derivation scheme for P2WPKH-nested-in-P2SH | Supports SegWit addresses with legacy compatibility |
| BIP84 | Derivation scheme for P2WPKH native SegWit | Optimizes transaction fees with Bech32 addresses |
Programmatic Address Allocation Across Multi-Chain Environments
Multi-chain wallet infrastructure requires sophisticated allocation systems distributing addresses across diverse Blockchain Addresses networks with different technical characteristics. Programmatic allocation APIs enable applications to request addresses for specific chains without understanding underlying cryptographic details. Address pools maintain pre-generated reserves for popular chains ensuring instant allocation without generation delays affecting user experience. Smart allocation algorithms predict demand patterns based on historical usage adjusting pool sizes dynamically to prevent exhaustion during traffic spikes. Chain-specific metadata tags each address with network identifiers, derivation paths, and operational parameters enabling proper transaction construction. Organizations implement tiered allocation where user reputation or transaction volume determines address security level from hot wallets to cold storage. Rate limiting prevents abuse where malicious actors request excessive addresses attempting to exhaust system resources. Allocation auditing tracks which addresses went to which users creating accountability for fund movements and security investigations. The architecture abstracts Blockchain Addresses heterogeneity behind unified APIs enabling application developers to support multiple chains without specialized knowledge of each protocol’s address generation mechanisms.
Segregating User, Hot, Warm, and Cold Address Pools
Address pool segregation implements defense-in-depth security by separating addresses based on access requirements and risk profiles. Hot wallets contain addresses for immediate operational needs like customer withdrawals requiring online private key access despite security risks. Warm addresses serve intermediate purposes with delayed access controls implementing time-locks or approval workflows before fund movements. Cold storage addresses hold majority assets offline on air-gapped systems or hardware security modules eliminating network attack vectors. User deposit addresses belong to a separate pool dedicated to receiving customer funds with real-time monitoring for incoming transactions. This segregation limits blast radius where hot wallet compromises affect only small operational balances rather than entire treasury reserves. Organizations implement automated fund sweeping where hot wallet balances exceeding thresholds trigger transfers to warm or cold storage reducing exposure windows. Pool sizing algorithms balance security against operational efficiency ensuring sufficient hot wallet capacity for withdrawal demand without unnecessary exposure. Address rotation between pools occurs periodically where addresses migrate from hot to cold after predetermined usage periods or transaction counts enhancing long-term security posture.
Address Pool Security Tiers
Hot Wallet Pool
Online addresses with immediate access for operational transactions, holding minimal balances to limit exposure during security breaches or system compromises.
Warm Wallet Pool
Semi-online addresses with approval workflows and time-delays balancing accessibility against security for intermediate-risk asset management scenarios and planned operations.
Cold Storage Pool
Offline addresses stored on air-gapped systems or hardware security modules holding majority reserves isolated from network-based attack vectors and unauthorized access attempts.
Deposit Address Pool
User-specific receiving addresses with real-time monitoring for incoming transactions enabling instant deposit detection and automatic fund sweeping to secure storage tiers.
Address Indexing Systems for High-Throughput Wallet Operations
Address indexing infrastructure creates searchable databases enabling instant lookups mapping blockchain addresses to internal entities without scanning entire transaction histories. Traditional Blockchain Addresses nodes maintain transaction databases indexed by block height and transaction hash but lack address-centric indexes critical for wallet operations. Purpose-built indexing systems monitor Blockchain Addresses activity in real-time extracting address-related events and organizing them for rapid retrieval. Database schemas optimize for common query patterns like balance inquiries, transaction history, and deposit detection. Sharding strategies distribute address spaces across multiple database instances scaling horizontally as address counts grow into billions. Caching layers accelerate frequently accessed addresses reducing database load during peak traffic periods. Indexing systems track not just on-chain activity but also off-chain metadata like address labels, user associations, and compliance flags. Consistency protocols ensure indexes remain synchronized with Blockchain Addresses state even during network reorganizations or temporary forks. Organizations implement redundant indexing infrastructure with automatic failover maintaining service availability during component failures or maintenance windows critical for 24/7 operational requirements.
Address Indexing Database Schema Optimization
| Index Type | Query Pattern | Performance Impact |
|---|---|---|
| Address to Balance | Current balance queries for user interfaces | Sub-millisecond lookups with proper indexing |
| Address to User | Internal account mapping for deposit attribution | Instant association without Blockchain Addresses scanning |
| Address to Transactions | Transaction history display and export | Paginated results for large transaction counts |
| Transaction to Address | Input and output address resolution | Essential for deposit detection workflows |
| User to Addresses | List all addresses for specific account | Aggregated balance calculations across wallets |
Automated Address Rotation for Security and Compliance
Address rotation policies systematically replace active addresses with fresh ones according to predetermined schedules or usage thresholds enhancing security and privacy. Automated rotation eliminates long-lived addresses that accumulate transaction history revealing usage patterns and fund flows to external observers. Security rotations replace hot wallet addresses periodically reducing exposure windows where compromised keys could drain funds before detection occurs. Compliance rotations retire addresses flagged for suspicious activity or regulatory concerns preventing continued use for potentially illicit transactions. Organizations implement rotation triggers based on time elapsed, transaction count, cumulative volume, or manual administrative actions. Graceful rotation procedures notify users of address changes while maintaining backward compatibility for in-flight transactions. Database migrations update user associations from old to new addresses preserving account continuity despite underlying address changes. Audit trails track rotation events documenting reasons and responsible parties for compliance investigations. Rotation scheduling avoids operational disruptions by coordinating with low-traffic periods and maintaining sufficient address capacity throughout transitions. Organizations balance rotation frequency against operational complexity where excessive rotation creates user confusion while infrequent rotation compromises security benefits.
Implement Enterprise Address Management
Build scalable wallet infrastructure with automated address lifecycle management, security rotation policies, and real-time monitoring capabilities.
Managing Deposit Address Reuse Without Privacy Leakage
Address reuse creates privacy vulnerabilities where multiple transactions to same address link user activities revealing financial patterns and account balances. Bitcoin and UTXO-based chains particularly suffer from address reuse as all transactions become publicly linkable through shared addresses. Best practices recommend generating unique addresses for each incoming transaction preventing transaction graph analysis. Organizations implement automatic address generation providing new deposit addresses per transaction request or user session. Database systems track which addresses belong to which users enabling proper fund attribution despite unique address proliferation. Some implementations use extended public keys allowing users to generate unlimited receiving addresses without server interaction. Payment processors balance privacy against user experience where address reuse simplifies recurring payments but compromises anonymity. Deterministic address generation from user identifiers enables stateless systems but leaks information through predictable patterns. Organizations implement address expiration where old deposit addresses refuse new funds after predetermined periods forcing address rotation. Compliance considerations sometimes require address reuse for transaction tracking despite privacy costs. Advanced implementations use stealth addresses or payment codes enabling reusable identifiers without on-chain address reuse.
Address Reuse Prevention Strategies
Generate unique addresses for every incoming transaction preventing linkability through on-chain transaction graph analysis and maintaining user privacy.
Implement address expiration policies that deactivate old deposit addresses after predetermined periods forcing users to obtain fresh addresses.
Use stealth address protocols allowing reusable payment codes without on-chain address reuse through cryptographic derivation techniques.
Educate users about privacy implications of address reuse through interface warnings and best practice documentation.
Monitor address usage patterns detecting anomalies indicating privacy violations or potential security compromises requiring investigation.
On-Chain and Off-Chain Address Mapping Architectures
Address mapping systems bridge on-chain blockchain addresses with off-chain internal identifiers linking public addresses to users, accounts, or organizational entities. Database architectures store these mappings enabling rapid lookups translating blockchain addresses to internal representations during transaction processing. Bidirectional indexes support both address-to-user and user-to-address queries serving different operational workflows. Encrypted storage protects sensitive mapping data preventing unauthorized access revealing user identities associated with public addresses. Backup procedures ensure mapping data survives system failures as lost mappings make funds effectively unrecoverable without extensive Blockchain Addresses analysis. Some organizations implement deterministic mappings deriving addresses from user identifiers enabling stateless reconstructions. Smart contract registries provide on-chain mapping alternatives where ownership associations exist publicly on Blockchain Addresses verifiable by all parties. Hybrid approaches combine on-chain ownership proofs with off-chain metadata providing public verifiability while maintaining operational efficiency. Multi-signature addresses complicate mappings requiring tracking of multiple key holders and signing policies. Organizations implement access controls limiting which systems and personnel can query address mappings protecting user privacy and preventing internal abuse.
Infrastructure Design for Millions of Managed Wallet Addresses
Scaling wallet infrastructure to millions or billions of addresses requires careful architectural planning addressing storage, indexing, monitoring, and operational concerns. Database sharding distributes address data across multiple instances preventing single database bottlenecks as address counts grow exponentially. Horizontal scaling adds compute capacity through clustered servers handling increased transaction processing loads. Caching layers reduce database pressure storing frequently accessed addresses in memory for microsecond retrieval. Asynchronous processing handles non-critical operations like historical data updates without blocking real-time transaction flows. Load balancing distributes incoming requests across server pools maintaining consistent response times despite traffic variations. Geographic distribution places infrastructure near users reducing network latency for international operations. Microservices architectures decompose monolithic systems into specialized components scaling independently based on specific resource requirements. Message queues buffer between system components allowing temporary throughput mismatches without cascading failures. Organizations implement capacity planning models forecasting infrastructure requirements based on user growth projections and transaction volume trends. Monitoring systems track performance metrics alerting operators to degradation before user impacts occur. Regular load testing validates infrastructure capacity under simulated peak conditions identifying bottlenecks requiring optimization.
Infrastructure Scaling Strategies
Database Sharding: Partition address data across multiple database instances distributing load and enabling horizontal scaling as address counts grow beyond single server capacity.
Caching Layers: Store frequently accessed addresses in memory-based caches reducing database queries and accelerating response times for balance lookups and transaction processing operations.
Asynchronous Processing: Handle non-critical operations like historical updates through background jobs preventing blocking of real-time transaction flows requiring immediate responses.
Microservices Architecture: Decompose monolithic systems into specialized services enabling independent scaling of address generation, monitoring, and transaction processing components based on specific demands.
Address Ownership Verification via Smart Contract Signatures
Smart contract signature verification enables provable address ownership without revealing private keys through cryptographic challenge-response protocols. Applications request users to sign specific messages with private keys controlling addresses generating signatures verifiable on-chain or off-chain. Smart contracts implement signature verification functions checking whether provided signatures match expected addresses without needing trusted intermediaries. This mechanism supports decentralized identity where users prove address ownership during authentication without centralized registries. Multi-signature addresses complicate verification requiring threshold signatures from multiple parties proving collective ownership. Time-locked signatures implement temporary ownership proofs expiring after predetermined periods preventing replay attacks. Organizations use signature verification for account recovery where users prove ownership of backup addresses before resetting credentials. Compliance systems require signature-based proofs demonstrating control over addresses before processing high-value transactions. Standardized signing formats like EIP-191 and EIP-712 provide structure enabling consistent verification across applications. However, signature-based verification faces usability challenges as users must interact with wallets generating signatures rather than simple password authentication. Organizations balance security benefits against user experience friction when implementing signature-based ownership verification systems.
Signature Verification Standards Comparison
| Standard | Format | Use Case |
|---|---|---|
| EIP-191 | Signed data standard for Ethereum messages | Simple ownership verification and authentication |
| EIP-712 | Typed structured data hashing and signing | Complex transaction authorization and meta-transactions |
| EIP-1271 | Standard signature validation for contracts | Smart contract wallet signature verification |
| Bitcoin Message | Sign message with Bitcoin address format | Bitcoin address ownership proof systems |
| SIWE | Sign-In with Ethereum specification | Web3 authentication replacing password systems |
Automated Reconciliation of Inbound Funds by Address
Reconciliation systems match incoming Blockchain Addresses transactions to internal accounts automating deposit detection and credit allocation. Real-time monitoring watches managed addresses detecting new transactions within seconds of Blockchain Addresses confirmation. Address mapping lookups determine which user or account owns the receiving address enabling proper fund attribution. Amount verification ensures transaction values match expected deposits flagging discrepancies requiring manual investigation. Confirmation tracking monitors transaction finality across different Blockchain Addresses consensus mechanisms crediting accounts after sufficient security thresholds. Multi-chain reconciliation handles heterogeneous protocols with different confirmation requirements and transaction formats through protocol-specific adapters. Partial payments split across multiple transactions aggregate toward total expected amounts through sophisticated matching algorithms. Failed reconciliation queues transactions for manual review when automated matching fails due to unknown addresses or suspicious patterns. Audit logging tracks all reconciliation events creating compliance trails demonstrating proper fund handling. Organizations implement redundant reconciliation systems with cross-checking between independent implementations preventing systematic errors causing fund misallocations. Performance optimization handles thousands of concurrent deposits through parallel processing and efficient database operations maintaining sub-second latencies critical for user experiences.
Optimize Your Wallet Operations
Deploy automated reconciliation systems with real-time deposit detection, multi-chain support, and comprehensive audit trails for regulatory compliance.
Monitoring Dormant and High-Risk Addresses in Real Time
Address monitoring infrastructure tracks suspicious activity patterns identifying security threats and compliance violations requiring immediate responses. Dormant address detection flags accounts showing no activity for extended periods potentially indicating compromised credentials or abandoned accounts. High-risk address screening compares managed addresses against sanctions lists, known fraud addresses, and blacklisted entities preventing illicit fund transfers. Transaction pattern analysis detects anomalies like sudden large withdrawals, unusual timing, or interactions with flagged addresses suggesting potential security breaches. Real-time alerting notifies security teams within seconds of suspicious events enabling rapid investigation and intervention before significant losses occur. Machine learning models identify subtle patterns indicating emerging threats invisible to rule-based detection systems. Organizations implement graduated response procedures where low-risk alerts trigger automated controls while high-risk scenarios require immediate manual intervention. Integration with Blockchain Addresses analytics services enriches internal monitoring with external threat intelligence tracking fund flows across addresses outside direct management. Performance optimization handles monitoring overhead for millions of addresses through efficient event processing and selective scanning strategies. Regular audit reviews verify monitoring effectiveness identifying false positives and false negatives requiring system tuning.
Address Monitoring Workflow
Event Detection
Real-time Blockchain Addresses monitoring identifies transactions involving managed addresses capturing events within seconds of network confirmation.
Risk Assessment
Automated scoring evaluates transaction characteristics against risk models classifying events by threat level and required response urgency.
Alert Generation
High-risk events trigger immediate notifications to security teams through multiple channels ensuring rapid awareness and response initiation.
Response Execution
Automated controls freeze affected addresses while manual investigation determines appropriate remediation actions based on threat analysis.
Incident Documentation
Comprehensive logging captures investigation details and remediation actions creating audit trails for compliance reporting and system improvement.
Model Refinement
Continuous learning incorporates incident outcomes improving risk models and detection accuracy reducing false positives over time.
Secure Address Exposure Control for dApps and APIs
Address exposure management controls which addresses external applications and API consumers can access preventing unauthorized address enumeration. API authentication verifies client identities before exposing address information through token-based access controls. Rate limiting prevents abuse where malicious clients attempt to enumerate large address sets through rapid API queries. Scoped permissions restrict clients to specific address subsets relevant for their operational needs following least-privilege principles. Address obfuscation techniques display partial addresses or pseudonyms in user interfaces preventing full address exposure. Time-limited address tokens expire after predetermined periods requiring re-authentication for continued access. Audit logging tracks all address exposure events identifying suspicious access patterns indicating potential security breaches. Organizations implement graduated disclosure where basic address information appears publicly while sensitive metadata requires elevated permissions. Smart contract interfaces expose only necessary address data avoiding unnecessary on-chain storage of sensitive associations. Privacy-preserving architectures use zero-knowledge proofs enabling address verification without revealing actual address values. Organizations balance transparency requirements against privacy and security concerns when designing address exposure policies for different stakeholder groups and use cases.
Address Management in MPC and Threshold Wallet Systems
Multi-Party Computation wallets revolutionize address management by distributing private key control across multiple parties without single complete keys existing anywhere. MPC protocols use cryptographic secret sharing generating key shares distributed to participants who collaborate during transaction signing. Address generation occurs through distributed key generation ceremonies where participants collectively create addresses without reconstructing complete private keys. Threshold signatures enable transactions requiring only subset of participants rather than unanimous cooperation improving availability. Address management complexity increases substantially as organizations must coordinate multiple parties, manage participant availability, and maintain protocol state. Infrastructure requirements expand to support secure communication channels between MPC participants and persistent storage for key shares. Backup and recovery procedures differ fundamentally from traditional wallets requiring threshold participant coordination rather than simple seed phrase restoration. Organizations implement participant rotation policies replacing key share holders periodically without regenerating addresses. Policy enforcement occurs during signing ceremonies where transaction approval logic executes collaboratively across participants. MPC systems provide superior security eliminating single points of compromise but introduce operational complexity and coordination overhead requiring careful architectural planning and robust infrastructure.
MPC Wallet vs Traditional Wallet Comparison
| Aspect | MPC Threshold Wallet | Traditional HD Wallet |
|---|---|---|
| Key Storage | Distributed shares across multiple parties | Single seed phrase or private key |
| Security Model | Requires threshold compromise for fund access | Single key compromise enables full access |
| Transaction Signing | Collaborative protocol among participants | Single device signs independently |
| Operational Complexity | High due to participant coordination requirements | Low with straightforward key management |
| Recovery Process | Threshold participants collaborate for restoration | Single seed phrase restores all addresses |
Cross-Chain Address Normalization and Abstraction Layers
Cross-chain address management requires normalization layers abstracting diverse blockchain address formats behind unified interfaces. Bitcoin uses base58 encoding while Ethereum uses hexadecimal with EIP-55 checksums creating incompatible formats. Cosmos chains support human-readable Bech32 addresses while Solana uses base58 variants with different validation rules. Address normalization libraries convert between formats enabling consistent storage and processing across multi-chain platforms. Validation logic differs substantially where Bitcoin addresses verify through base58 decoding while Ethereum addresses check EIP-55 checksum correctness. Organizations implement protocol-specific adapters handling chain-unique requirements like Ethereum nonce management or Bitcoin UTXO selection. Unified APIs abstract complexity where application developers request addresses by chain identifier without understanding underlying cryptographic details. Address derivation paths vary across chains requiring careful hierarchy management preventing key reuse across incompatible protocols. Some chains like Polkadot use generic address formats transcoding to chain-specific representations at runtime. Organizations maintain address format registries documenting validation rules and encoding schemes for each supported Blockchain Addresses enabling consistent implementation across infrastructure components.
Gas Optimization Strategies for Address-Based Operations
Gas optimization becomes critical for address management systems processing thousands of transactions daily where inefficiencies accumulate substantial costs. Batch processing combines multiple address operations into single transactions amortizing base gas costs across operations. Address clustering groups related addresses enabling efficient multi-recipient transactions through smart contract batch transfers. UTXO consolidation merges fragmented Bitcoin balances reducing future transaction sizes and fees. Dynamic fee estimation algorithms predict optimal gas prices balancing confirmation speed against cost minimization. Organizations implement transaction queuing during high-fee periods waiting for favorable network conditions before broadcasting. Address selection algorithms choose inputs minimizing transaction size through coin selection optimization strategies. Smart contract gas profiling identifies expensive operations requiring optimization or architectural redesign. Layer-2 solutions reduce gas costs by processing address operations off-chain with periodic settlement to main chains. Organizations monitor gas expenditure tracking costs by operation type identifying optimization opportunities through detailed analytics. Automated cost controls pause non-critical operations when gas prices exceed predetermined thresholds preventing excessive spending during network congestion. Regular optimization reviews ensure infrastructure keeps pace with evolving Blockchain Addresses protocols and emerging efficiency techniques.
Reduce Operational Costs
Implement gas optimization strategies reducing transaction costs by 60% through batch processing, intelligent fee estimation, and layer-2 integration.
Compliance-Aware Address Tagging and Risk Classification
Compliance systems classify managed addresses based on risk profiles implementing controls proportional to threat levels. Address tagging associates metadata labels indicating characteristics like source country, user verification status, or transaction history patterns. Risk scoring algorithms evaluate addresses against multiple factors including transaction velocity, counterparty reputation, and behavioral anomalies. Organizations implement tiered controls where high-risk addresses face enhanced monitoring, withdrawal limits, or mandatory manual approvals. Sanctions screening compares addresses against regulatory lists blocking transactions involving prohibited entities or jurisdictions. Behavioral analytics detect unusual patterns like structuring attempts or layering behaviors indicating potential money laundering. Source of funds documentation requirements vary by risk classification with high-risk addresses requiring additional verification before fund acceptance. Automated controls enforce compliance rules consistently across address populations preventing selective application vulnerabilities. Regular risk reassessment updates classifications as addresses accumulate transaction history changing risk profiles over time. Integration with Blockchain Addresses analytics services enriches internal data with external intelligence tracking fund flows beyond directly managed addresses. Organizations maintain compliance audit trails documenting risk assessment decisions and control applications for regulatory examination requirements.
Resilience Strategies for Address Management System Failures
Resilience engineering ensures address management systems maintain availability despite component failures through redundancy and failover mechanisms. Database replication maintains synchronized copies across geographic regions enabling automatic failover during outages. Load balancing distributes requests across multiple servers isolating failures to individual instances without service disruptions. Circuit breakers prevent cascading failures by isolating malfunctioning components from healthy systems. Backup procedures ensure critical address mapping data survives catastrophic failures through encrypted off-site storage. Disaster recovery planning documents procedures for restoring operations from backups under various failure scenarios. Regular failover testing validates resilience mechanisms actually work under real conditions rather than theoretical assumptions. Organizations implement degraded mode operations where systems continue core functions despite auxiliary component failures. Monitoring and alerting provide early warning of degrading performance before complete failures occur enabling proactive intervention. Chaos engineering deliberately injects failures testing system resilience and identifying weaknesses requiring architectural improvements. Post-incident reviews analyze failures extracting lessons improving future resilience through systematic learning. Organizations balance resilience investments against costs recognizing perfect availability proves economically impractical requiring pragmatic risk acceptance for rare scenarios.
Managing blockchain addresses at enterprise scale demands comprehensive infrastructure encompassing automated lifecycle management, deterministic generation through HD wallets, programmatic multi-chain allocation, and intelligent pool segregation balancing security tiers. High-performance indexing systems enable instant lookups supporting thousands of concurrent operations while automated rotation policies enhance security and privacy through systematic address replacement. Organizations implement sophisticated reconciliation matching incoming transactions to internal accounts, real-time monitoring detecting threats and compliance violations, and controlled exposure management protecting sensitive address associations. Multi-Party Computation wallets provide enhanced security through distributed key control while cross-chain normalization layers abstract Blockchain Addresses heterogeneity behind unified APIs. Gas optimization strategies reduce operational costs substantially through batch processing and intelligent fee management while compliance-aware tagging implements risk-proportional controls. Resilience engineering ensures system availability despite component failures through redundancy, failover mechanisms, and comprehensive disaster recovery planning. As Blockchain Addresses adoption accelerates across industries, robust address management infrastructure becomes critical enabling organizations to operate securely and efficiently at scale supporting millions of users and transactions across evolving multi-chain ecosystems requiring continuous adaptation and optimization maintaining competitive advantage in rapidly changing technological landscapes.
Frequently Asked Questions
Hierarchical Deterministic wallets use a single master seed to generate unlimited addresses through mathematical derivation following BIP32, BIP39, and BIP44 standards. This automation eliminates manual key generation while enabling deterministic recovery. Organizations can create billions of addresses from one seed phrase, with each address cryptographically linked yet independently secure. The derivation path structure allows segregating addresses by purpose, currency, or user account. HD wallets streamline backup procedures since one seed phrase recovers all derived addresses. This architecture scales efficiently for enterprises managing millions of customer deposit addresses across multiple blockchain networks.
Address security requires multi-layered protection including cold storage segregation, hardware security modules for key storage, address rotation policies, and real-time monitoring for suspicious activity. Hot wallets serving immediate withdrawal needs hold minimal funds while cold addresses store majority assets offline. Multi-signature schemes distribute control requiring multiple parties for transaction authorization. Encryption protects address databases and private key materials at rest and in transit. Regular security audits identify vulnerabilities in address management infrastructure. Compliance systems flag high-risk addresses interacting with sanctioned entities, enabling proactive risk mitigation before fund transfers complete.
Address indexing creates searchable databases mapping blockchain addresses to internal user accounts, transaction histories, and metadata enabling instant lookups without scanning entire Blockchain Addresses. Indexing systems track address balances, pending transactions, and historical activity through real-time Blockchain Addresses monitoring. This architecture supports high-throughput operations where exchanges and payment processors manage millions of addresses serving thousands of concurrent users. Efficient indexing reduces latency for deposit detection, balance inquiries, and withdrawal processing. Database sharding and caching layers scale indexing performance horizontally as address counts grow into billions across multi-chain environments.
Different Blockchain Addresses use incompatible address formats, key derivation paths, and signature algorithms requiring specialized handling for each network. Bitcoin uses base58 encoding while Ethereum uses hexadecimal with checksums. Address validation rules vary preventing unified input handling. Some chains like Cosmos support human-readable addresses while others use cryptographic hashes. Managing private keys across chains demands careful derivation path selection avoiding key reuse. Normalization layers abstract chain-specific complexities behind unified APIs but add architectural complexity. Organizations must maintain separate infrastructure components for each supported blockchain while providing seamless user experiences.
Multi-Party Computation wallets eliminate single private key storage by distributing key shares across multiple parties using cryptographic secret sharing. Address management becomes collaborative requiring threshold participants cooperating for transaction signing without reconstructing complete keys. This architecture enhances security as compromising one party doesn’t expose funds. MPC protocols enable policy enforcement where transaction rules execute during signing ceremonies. Distributed key generation creates addresses without any party knowing complete private keys. However, MPC systems require complex coordination infrastructure, participant availability management, and protocol-specific implementations for each supported Blockchain Addresses network.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.






