Blockchain networks have grown massive over the years. Bitcoin’s blockchain alone exceeds 500 GB, and Ethereum is not far behind. For someone wanting to interact with these networks using a smartphone or an older laptop, downloading and storing all that data is simply not practical. This is where light clients step in as a game changer.
A light client allows users to access blockchain networks without downloading the entire chain. Instead of storing every transaction ever made, it only keeps what is absolutely necessary. Think of it like reading the summary of a book rather than going through every page. You still get the key information, but without the heavy lifting.
If you are exploring how blockchain technology works or considering building decentralized applications, understanding light clients is essential. They represent a practical solution to one of the biggest barriers in blockchain adoption, which is accessibility.
Key Takeaways
- Light clients download only block headers and essential data, not the full blockchain.
- They enable blockchain access on devices with limited storage and processing power.
- Light clients rely on full nodes to verify transactions using Simplified Payment Verification.
- They improve network scalability by reducing the load on individual participants.
- Security trade offs exist since light clients trust external nodes for data accuracy.
- Future developments include zero knowledge proofs and cross chain compatibility.
Understanding Light Clients at a Basic Level
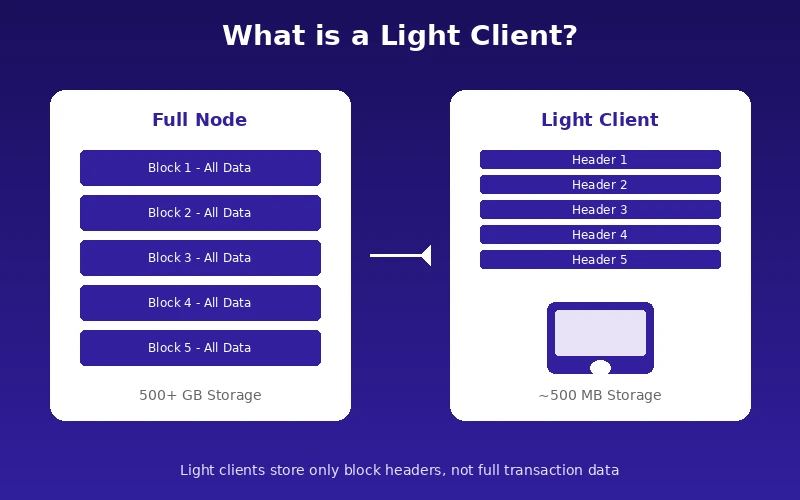
To grasp what a light client does, you first need to understand what a full node does. A full node downloads and validates every single block and transaction on a blockchain. It maintains a complete copy of the ledger and independently verifies everything. This process requires significant storage, bandwidth, and computational resources.
A light client takes a different approach. It downloads only the block headers, which are small summaries containing critical information like timestamps, previous block references, and cryptographic proofs. When a light client needs to verify a specific transaction, it asks a full node for proof that the transaction exists within a block. This proof is called a Merkle proof, named after the data structure that makes it possible.
The result is that light clients can confirm transactions without storing or processing the entire blockchain. They trade some independence for efficiency, which is often an acceptable bargain for everyday users.
How Light Clients Differ from Full Nodes
The distinction between light clients and full nodes goes beyond just storage requirements. Their roles in the network, security guarantees, and use cases are fundamentally different.
| Feature | Light Client | Full Node |
|---|---|---|
| Data Stored | Block headers only | Complete blockchain |
| Storage Required | Few hundred MB | Hundreds of GB |
| Sync Time | Minutes to hours | Days to weeks |
| Verification Method | SPV with Merkle proofs | Full independent validation |
| Trust Requirement | Relies on full nodes | Trustless verification |
| Suitable Devices | Mobile phones, tablets, IoT | Dedicated servers, desktops |
| Network Contribution | Consumer of data | Validates and relays blocks |
Full nodes are the backbone of any blockchain network. They enforce rules, reject invalid transactions, and maintain consensus. Light clients, on the other hand, are participants that trust the network’s full nodes to provide accurate information. Both have their place in a healthy ecosystem.
The Technical Mechanism Behind Light Clients
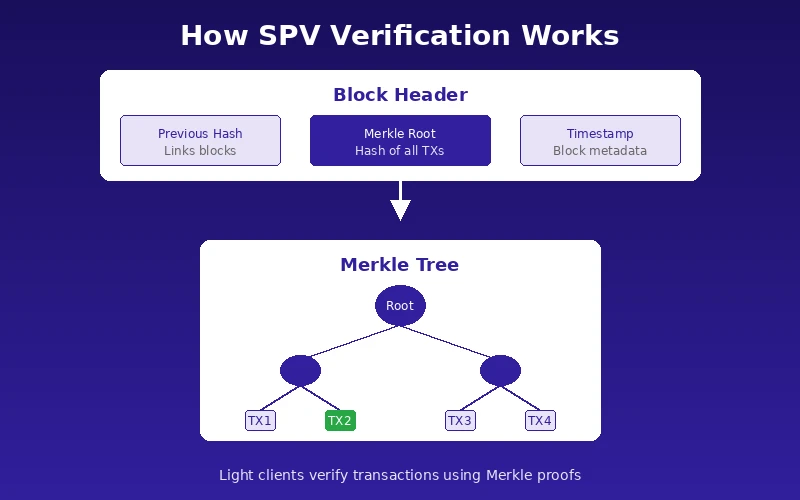
Light clients operate using a process called Simplified Payment Verification, commonly abbreviated as SPV. Satoshi Nakamoto described this concept in the original Bitcoin whitepaper. The idea is straightforward but clever.
Every block in a blockchain contains a Merkle root, which is a cryptographic hash derived from all transactions in that block. When a light client wants to verify a transaction, it requests the relevant Merkle branch from a full node. By hashing through this branch and comparing the result to the Merkle root in the block header, the light client can confirm that the transaction was included in the block without seeing any other transactions.
This approach works because of the mathematical properties of hash functions. Any attempt to forge a Merkle proof would require an attacker to break the underlying cryptography, which is computationally infeasible with current technology.
Understanding this mechanism helps explain both the strengths and limitations of light clients. They can verify inclusion proofs efficiently, but they cannot detect all types of fraud that a full node would catch.
Why Light Clients Matter for Blockchain Adoption
Blockchain technology promises decentralization, but true decentralization requires broad participation. If only organizations with expensive hardware can run nodes, the network becomes centralized in practice even if the protocol is decentralized in theory.
Light clients lower the barrier to entry dramatically. A farmer in a rural area can verify crop insurance payments on a smartphone. A small business can accept cryptocurrency without investing in server infrastructure. A mobile gaming application can integrate blockchain features without forcing users to download gigabytes of data.
The history of blockchain shows that accessibility has always driven growth. Light clients continue this tradition by bringing blockchain capabilities to billions of devices that would otherwise be excluded.
Build Scalable Blockchain Solutions Today
Looking to integrate light clients or develop custom blockchain infrastructure? Partner with experts who understand the technical details and business implications.
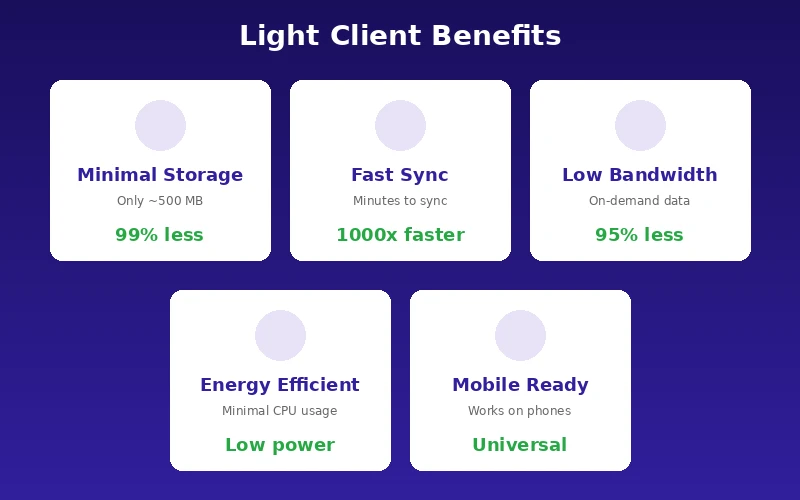
Benefits That Make Light Clients Practical
The advantages of light clients extend across multiple dimensions. Users, developers, and network operators all benefit from their existence.
| Benefit | Description | Real World Impact |
|---|---|---|
| Minimal Storage | Only block headers are stored locally | Works on devices with 1 GB free space |
| Fast Synchronization | Downloads megabytes instead of gigabytes | Ready to use within minutes |
| Low Bandwidth | Fetches only required data on demand | Usable on metered connections |
| Energy Efficient | Minimal processing requirements | Preserves battery life on mobile |
| Network Scalability | Reduces load on infrastructure | Supports millions of users |
These benefits compound when you consider the global context. Internet connectivity varies widely around the world. Storage costs money. Processing power generates heat and consumes electricity. Light clients address all of these constraints simultaneously.
Security Considerations and Trade Offs
Nothing comes free in engineering. Light clients gain efficiency by accepting certain security compromises that users should understand.
The primary concern is trust. A light client cannot independently verify that a block follows all consensus rules. It trusts that the block headers it receives represent valid blocks accepted by the network. If a malicious full node provides false information, the light client might accept an invalid transaction as confirmed.
Several attack vectors exist. An eclipse attack could isolate a light client from honest nodes, feeding it a fabricated view of the blockchain. A 51 percent attack on the network would affect light clients more severely than full nodes, since light clients cannot detect invalid state transitions.
Mitigation strategies include connecting to multiple full nodes, using trusted node lists, and implementing fraud proofs where possible. Modern light client protocols are evolving to address these vulnerabilities while maintaining efficiency.
For most consumer use cases, these risks are acceptable. The amounts involved are typically small, and the convenience outweighs the theoretical attack possibilities. High value transactions should still use full node verification when possible.
The Light Client Lifecycle
Understanding how a light client operates from start to finish helps clarify its role in the network.
Phase 1: Initialization. When first launched, the light client connects to the blockchain network and downloads all block headers from genesis to the current tip. This initial sync establishes a verified chain of proof of work or proof of stake that the client can trust.
Phase 2: Ongoing Sync. After initialization, the light client maintains connection to full nodes and downloads new block headers as they are produced. This keeps it current without requiring full block downloads.
Phase 3: Transaction Verification. When the user initiates or receives a transaction, the light client requests a Merkle proof from connected full nodes. It verifies this proof against the stored block header to confirm transaction inclusion.
Phase 4: Broadcasting. For outgoing transactions, the light client broadcasts to connected full nodes, which then propagate the transaction to the rest of the network.
This lifecycle repeats continuously, with the light client maintaining a minimal but sufficient view of the blockchain state.
Where Light Clients Are Used Today
Light client technology already powers many blockchain applications that people use daily.
Mobile cryptocurrency wallets are the most common example. Apps like Electrum for Bitcoin implement SPV to let users manage funds without running a full node. Most Ethereum wallets rely on services like Infura that abstract away full node requirements, though truly decentralized light clients are still developing.
Internet of Things devices present another compelling use case. Smart locks, supply chain sensors, and payment terminals can verify blockchain transactions without embedded storage capable of holding full chains.
Browser extensions that connect to decentralized applications also typically function as light clients. They query external nodes for blockchain state rather than maintaining local copies.
As a blockchain based company with over 8 years of experience, Nadcab Labs has implemented light client solutions across these and other verticals. The practical considerations vary significantly depending on the specific blockchain, target devices, and security requirements of each project.
Light Clients Across Different Blockchains
Each major blockchain has its own approach to light client implementation, reflecting different design philosophies and technical constraints.
| Blockchain | Light Client Protocol | Notable Characteristics |
|---|---|---|
| Bitcoin | SPV (BIP 37, BIP 157/158) | Compact block filters improve privacy |
| Ethereum | Portal Network, Helios | State verification more complex than UTXO |
| Polkadot | Smoldot | Runs directly in browser via WASM |
| Cosmos | IBC Light Clients | Enables cross chain communication |
| Solana | Under Development | High throughput creates unique challenges |
Bitcoin’s SPV implementation is the oldest and most battle tested. However, early versions using Bloom filters had privacy weaknesses that newer compact block filters address.
Ethereum’s transition to proof of stake opened new possibilities for light clients. The Helios project aims to create a trust minimized light client that can verify the beacon chain and execution layer with minimal resources.
Future Developments in Light Client Technology
The next generation of light clients will be smarter, more secure, and more capable than current implementations.
Zero knowledge proofs represent perhaps the most exciting development. These cryptographic techniques allow proving statements without revealing underlying data. Applied to light clients, they could enable verification of state transitions without trusting any external party. A light client could cryptographically confirm that the entire blockchain history is valid using a single compact proof.
Fraud proofs offer another path forward. In optimistic systems, light clients assume blocks are valid unless proven otherwise. If a full node detects an invalid block, it can generate a fraud proof that light clients can verify cheaply. This shifts the security model from trust to verification.
Cross chain light clients are becoming increasingly important as blockchain ecosystems fragment. The ability to verify transactions across multiple chains without running full nodes for each enables new interoperability patterns.
Data availability sampling is a technique where light clients download random samples of block data to probabilistically verify that full data is available. This is crucial for systems using data sharding to scale.
Ready to Implement Light Client Solutions?
With 8+ years in blockchain development, Nadcab Labs delivers custom light client implementations tailored to your specific requirements and security standards.
Common Misconceptions About Light Clients
Several misunderstandings circulate about what light clients can and cannot do.
Some believe light clients compromise the security of the entire network. This is not accurate. Light clients do not weaken the consensus layer. They simply choose a different security model for their own verification. The network remains as secure as its full node operators make it.
Others assume light clients cannot be used for serious applications. In reality, with proper implementation and risk management, light clients serve production workloads handling significant value. The key is matching the verification level to the use case requirements.
A third misconception is that light clients are just for poor people who cannot afford better hardware. This framing misses the point. Light clients exist because requiring everyone to run full nodes is impractical and unnecessary for most interactions. Even well resourced organizations use light clients when appropriate.
How Nadcab Labs Approaches Light Client Development
With over 8 years of focused experience in blockchain technology, Nadcab Labs has developed deep expertise in light client architecture and implementation. The approach combines theoretical understanding with practical deployment experience across diverse use cases.
Every light client project begins with a thorough analysis of requirements. What blockchain or blockchains need support? What devices will run the client? What security guarantees are non negotiable? What performance metrics matter most? These questions shape the technical decisions that follow.
Security receives particular attention. Nadcab Labs implements multiple node connections, trusted node bootstrapping, and where available, fraud proof verification. The goal is to achieve the best possible security within the constraints of the light client model.
Performance optimization ensures that light clients run smoothly even on constrained devices. This includes efficient data structures, intelligent caching, and careful management of network requests to minimize bandwidth consumption.
Ongoing support matters because blockchain protocols evolve. Hard forks, protocol upgrades, and new security research all require light client updates. Nadcab Labs provides maintenance and enhancement services to keep light client deployments current and secure.
Conclusion
Light clients solve a fundamental challenge in blockchain technology: how to give everyone access to decentralized networks without requiring everyone to maintain complete infrastructure. By storing only essential data and verifying transactions through cryptographic proofs, they enable blockchain participation on smartphones, tablets, and embedded devices.
The trade offs involved are real but manageable for most applications. Understanding these trade offs allows developers and users to make informed decisions about when light clients are appropriate and when full node verification is worth the extra resources.
As blockchain technology continues maturing, light clients will only become more capable. Zero knowledge proofs, fraud proofs, and cross chain protocols are all advancing rapidly. The future of light clients is a future where blockchain becomes as accessible as the web is today.
For organizations looking to leverage light client technology, working with experienced blockchain developers makes a significant difference. The nuances of implementation, security hardening, and performance optimization require hands on expertise that only comes from years of focused work in this space.
Frequently Asked Questions
A light client is a simplified blockchain node that downloads only block headers instead of the complete blockchain data. While full nodes store hundreds of gigabytes of data and independently verify every transaction, light clients rely on full nodes to provide transaction proofs. This design allows light clients to operate on devices with limited storage and processing capabilities like smartphones and tablets. The trade-off is that light clients trust full nodes for accurate information rather than verifying everything independently.
Simplified Payment Verification is the mechanism light clients use to confirm transactions without downloading the entire blockchain. When a light client needs to verify a transaction, it requests a Merkle proof from a full node. This proof demonstrates that the transaction is included in a specific block by providing a cryptographic path from the transaction to the Merkle root stored in the block header. The light client can then verify this proof mathematically without seeing any other transactions in the block.
Light clients provide adequate security for most consumer use cases and everyday transactions. They can verify that transactions are included in valid blocks through Merkle proofs and connect to multiple full nodes to reduce the risk of receiving false information. However, they cannot detect all types of fraud that full nodes would catch. For high-value transactions or situations requiring maximum security, using full node verification is recommended. Most mobile wallets successfully use light client technology for routine payments.
Light clients offer several practical advantages including minimal storage requirements measured in megabytes rather than gigabytes, fast synchronization times of minutes instead of days, reduced bandwidth usage since they only download essential data, and lower energy consumption suitable for battery-powered devices. These benefits enable blockchain access on smartphones, IoT devices, and browser extensions. Light clients also improve overall network scalability by reducing infrastructure demands.
Major blockchains have different light client implementations. Bitcoin uses SPV with BIP 37 Bloom filters or newer BIP 157/158 compact block filters. Ethereum is developing the Portal Network and Helios client for trust-minimized verification. Polkadot offers Smoldot which runs directly in browsers using WebAssembly. Cosmos uses IBC light clients for cross-chain communication. Each implementation reflects the unique architecture and requirements of its respective blockchain network.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







