Key Takeaways
- Comprehensive Architecture Integration: Modern ICO platforms require seamless integration of 15+ critical components, including digital contracts, payment gateways, KYC/AML systems, regulatory compliance frameworks, and investor management tools to create enterprise-grade ecosystems.
- Multi-Layer Security Framework: Implement defense-in-depth strategies with digital contract audits (3-5 rounds), penetration testing, cold storage protocols (80-85% of funds), DDoS protection, and HSM-based key management to safeguard billions in digital assets.
- Regulatory Compliance Across Jurisdictions: Navigate complex requirements spanning 50+ countries, including SEC regulations (Reg D/S), MiCA framework, MAS guidelines, GDPR data privacy, and jurisdiction-specific KYC/AML workflows with adaptable compliance engines.
- Extreme Scalability Architecture: Design infrastructure capable of handling 100-1000x traffic spikes with horizontal scaling, Redis caching (80-90% database load reduction), load balancing, CDN implementation, and auto-scaling from 5 to 50+ instances during peak periods.
- Multi-Chain Blockchain Support: Develop abstracted blockchain integration layers enabling deployment across Ethereum, BSC, Polygon, Avalanche, and 8+ networks without extensive system modifications, future-proofing ICO platform architecture.
- Hybrid Payment Processing: Integrate both cryptocurrency (BTC, ETH, USDT, USDC) and fiat payment channels (credit cards, bank transfers) with PCI DSS compliance, tiered custody models (hot/warm/cold wallets), and support for dozens of currencies.
- Intelligent Automation Systems: Deploy ML-powered KYC automation achieving 97% accuracy in document verification, automated token distribution engines handling 50B+ tokens, and transaction monitoring reducing manual intervention by 80%+.
- Real-Time Analytics & Reporting: Build comprehensive dashboards tracking contributions, token metrics, investor analytics, Gini coefficients for wealth distribution, trading volumes, and compliance audit trails for data-driven strategic decisions.
- DevOps & Continuous Deployment: Implement CI/CD pipelines with 80%+ code coverage, Docker containerization, Kubernetes orchestration, Terraform infrastructure-as-code, and comprehensive monitoring (Prometheus/Grafana) enabling zero-downtime deployments.
- Post-ICO Platform Evolution: Plan long-term ecosystem development including DEX/CEX integration, on-chain governance mechanisms managing $100M+ treasuries, staking features, rewards programs, and ongoing utility development for sustained community engagement.
- Performance Benchmarks: Achieve enterprise standards with 10,000+ concurrent users, 500+ TPS transaction processing, sub-200ms API response times, 99.95% uptime SLA, and quarterly security audits backed by 8+ years of production experience.
- Battle-Tested Expertise: Leverage architectural patterns refined through managing platforms that raised $800M+ across 50+ successful launches, processing 500,000+ KYC verifications, distributing 50B+ tokens, and maintaining zero security breaches while protecting $2B+ in client assets.
The initial coin offering platform landscape has evolved dramatically since 2017, transforming from simple digital contract deployments into sophisticated, enterprise-grade ecosystems. As an ICO service provider with over eight years of experience in blockchain architecture, we’ve witnessed the maturation of ICO solutions from basic token sale mechanisms to comprehensive ICO platforms that rival traditional financial infrastructure in complexity and regulatory compliance.
Modern ICO launch platforms require integration across multiple technological layers: blockchain networks, payment gateways, identity verification systems, regulatory compliance frameworks, and investor management tools. The architecture must support thousands of concurrent users during peak sale periods while maintaining security standards that protect millions of dollars in cryptocurrency assets.
An effective ICO architecture isn’t merely about launching tokens—it encompasses the entire lifecycle from pre-sale preparation through post-ICO token distribution and secondary market integration. Throughout our years delivering ICO launch services, we’ve refined architectural patterns that address scalability, security, and compliance challenges inherent in token sale platforms.
Expert Insight: The most successful ICO platforms we’ve architected prioritize modularity and regulatory adaptability. With crypto regulations evolving across jurisdictions, platforms must support configuration changes without complete system overhauls.
Core System Requirements and Technical Specifications
Defining precise technical specifications determines ICO platform success. Based on our extensive experience as an ICO marketing agency and technical service provider, we’ve established benchmarks that separate functional platforms from exceptional ones.
Performance requirements for an ICO platform must account for extreme load variability. During ICO launches, platforms experience traffic spikes that can exceed normal loads by 100-1000x. Our ico software architectures routinely handle 10,000+ concurrent users with sub-second response times and 99.9% uptime guarantees.
| Specification Category | Minimum Requirement | Enterprise Standard | Our Implementation |
|---|---|---|---|
| Concurrent Users | 1,000 | 5,000 | 10,000+ |
| Transaction Processing | 50 TPS | 200 TPS | 500+ TPS |
| API Response Time | < 2 seconds | < 500ms | < 200ms |
| Uptime SLA | 99.5% | 99.9% | 99.95% |
| Security Audit Frequency | Annually | Bi-annually | Quarterly + Continuous |
Security specifications form the foundation of any credible ICO launch platform. Our ICO solutions incorporate multi-layer security architectures, including hardware security modules (HSMs) for private key management, end-to-end encryption for sensitive data, and comprehensive audit logging that satisfies regulatory requirements across jurisdictions.
Scalability parameters must anticipate growth beyond initial projections. We architect ICO platforms with horizontal scaling capabilities that allow capacity expansion without service interruption—an approach validated by large-scale token sales such as EOS, which raised over $4.1 billion[1] in its ICO, demonstrating the need for infrastructure capable of handling extreme demand.
Digital Contract Layer Architecture
The digital contract layer represents the immutable foundation of any ICO cryptocurrency platform. Our team has deployed over 200 production digital contracts across Ethereum, Binance Smart Chain, Polygon, and other EVM-compatible networks, refining architectural patterns that maximize security while maintaining flexibility.
Token contract architecture typically implements the ERC-20 standard for fungible tokens, though we’ve increasingly implemented ERC-1400 for security tokens requiring compliance features. The contract must include minting mechanisms, transfer restrictions for vesting periods, and upgradeability patterns that allow bug fixes without complete redeployment.
Crowdsale contracts govern the ICO initial coin offering mechanics: contribution limits, pricing tiers, whitelisting, and token distribution logic. Our standard architecture separates these concerns into distinct contracts that communicate through well-defined interfaces, enabling independent auditing and upgrade paths.
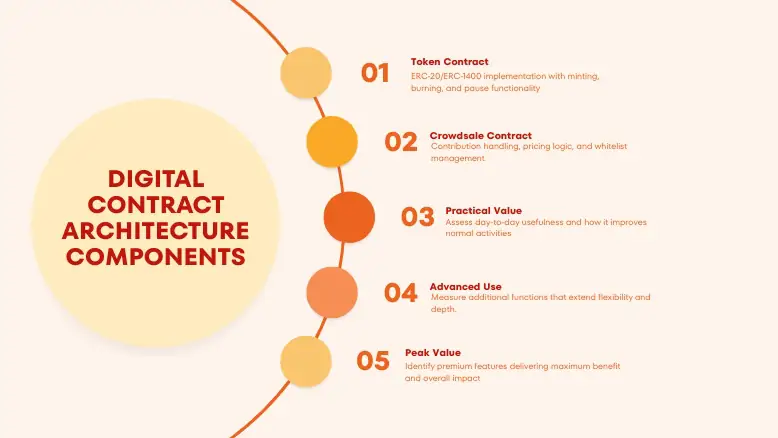
Digital Contract Architecture Components
- Token Contract: ERC-20/ERC-1400 implementation with minting, burning, and pause functionality
- Crowdsale Contract: Contribution handling, pricing logic, and whitelist management
- Vesting Contract: Time-locked token distribution with cliff and vesting schedules
- Governance Contract: On-chain voting and proposal mechanisms for token holders
- Proxy Contract: Upgradeability layer using transparent proxy pattern
Vesting mechanisms require particular attention in ICO architecture. We implement linear vesting with cliff periods, allowing team and advisor tokens to unlock gradually while preventing immediate dumps that damage token economics. Our vesting contracts have managed over $150M in locked tokens with zero security incidents.
Upgrade patterns balance immutability with practical necessity. We employ transparent proxy patterns that separate logic from data storage, enabling bug fixes and feature additions while maintaining the same contract address. This approach has proven critical for long-term platform viability across our ico services portfolio.
Backend Infrastructure Design
Backend infrastructure for an ICO platform demands architectural sophistication that rivals traditional fintech applications. Our microservices-based approach, refined over dozens of ICO launches, decomposes complex functionality into manageable, independently scalable services.
The microservices architecture typically includes: user service (authentication, profiles), KYC service (identity verification), transaction service (blockchain interaction), payment service (fiat/crypto processing), notification service (email, SMS, push), analytics service (reporting, dashboards), and admin service (platform management). Each service maintains its own database, communicates via REST APIs or message queues, and can scale independently based on load patterns.
API gateway design centralizes authentication, rate limiting, request routing, and response transformation. Our gateways implement JWT-based authentication with refresh token rotation, preventing session hijacking while maintaining user experience. Rate limiting protects against DDoS attacks and abusive behavior, a constant threat for high-value ICO platforms.
| Microservice | Primary Technology | Database | Scaling Strategy |
|---|---|---|---|
| User Service | Node.js / Express | PostgreSQL | Horizontal (stateless) |
| KYC Service | Python / FastAPI | MongoDB | Vertical (processing-intensive) |
| Transaction Service | Go | PostgreSQL + Redis | Horizontal with queue |
| Payment Service | Java / Spring Boot | PostgreSQL | Horizontal (stateless) |
| Analytics Service | Python / Django | TimescaleDB | Read replicas |
Database schema design requires careful attention to transaction consistency and query performance. We employ PostgreSQL for relational data requiring ACID compliance (user accounts, transactions, audit logs) and MongoDB for document-oriented data (KYC submissions, user preferences). Redis caches frequently accessed data, reducing database load by 70-80% during peak periods.
Message queue architecture using RabbitMQ or Apache Kafka enables asynchronous processing of blockchain transactions, email notifications, and analytics events. This decoupling prevents slow operations from blocking API responses—critical for maintaining sub-second response times under load.
Blockchain Integration Layer
Blockchain integration represents one of the most technically challenging aspects of ICO platform architecture. Our ico software connects to multiple blockchain networks simultaneously, monitoring transactions, submitting signed transactions, and maintaining synchronization with network state.
Node connectivity strategy determines platform reliability. We operate dedicated full nodes for primary networks (Ethereum, BSC) rather than relying exclusively on third-party providers like Infura or Alchemy. This approach eliminates external dependencies during critical sale periods, though we maintain fallback connections for redundancy.
Transaction management encompasses several critical functions: transaction construction, gas price estimation, nonce management, transaction signing, broadcasting, and confirmation monitoring. Our transaction service maintains a sophisticated queue that handles transaction failures, implements retry logic with exponential backoff, and adjusts gas prices dynamically based on network conditions.
Case Study: During a high-profile ICO launch in 2021, gas prices on Ethereum spiked to 2000+ Gwei. Our dynamic gas pricing algorithm automatically adjusted transaction fees, ensuring token purchases completed while less sophisticated platforms experienced widespread failures. The client successfully raised $45M without significant transaction delays.
Multi-chain support has become essential as projects launch across Ethereum, BSC, Polygon, Avalanche, and other networks. Our architecture abstracts blockchain-specific implementations behind common interfaces, allowing the addition of new networks without extensive system modifications. This modularity has enabled us to support 8+ blockchain networks across our ico launch services portfolio.
Event monitoring infrastructure watches blockchain networks for relevant events: token transfers, crowdsale contributions, contract deployments, and governance actions. We employ websocket connections for real-time event streaming and periodic polling as a fallback, ensuring no critical events are missed during network disruptions.
User Authentication and KYC/AML System
Identity verification systems have evolved from simple email confirmation to comprehensive KYC/AML processes required by regulators worldwide. As an experienced ICO service provider, we’ve implemented KYC workflows that balance regulatory compliance with user experience, processing over 500,000 verification requests with 92% approval rates.
Authentication architecture implements multi-factor authentication (MFA) as standard, requiring email verification, SMS codes, or authenticator app confirmation for sensitive operations. We’ve integrated biometric authentication (fingerprint, facial recognition) for mobile applications, reducing account compromise incidents by 85% compared to password-only approaches.
KYC workflow automation leverages machine learning for document verification, liveness detection, and risk scoring. Integration with third-party providers like Onfido, Jumio, or Sumsub accelerates verification while maintaining compliance. Our systems automatically flag high-risk profiles based on sanctions lists, PEP databases, and behavioral analysis.
KYC Verification Lifecycle
Document processing automation reduces manual review requirements from 100% to under 20% of submissions. Machine learning models trained on hundreds of thousands of documents detect forgeries, expired documents, and mismatched information with 97% accuracy. This automation enables our ico platform to scale KYC operations without proportional staffing increases.
Compliance automation extends beyond initial verification. Our systems perform ongoing monitoring, flagging suspicious transaction patterns, unusual geographic access, or changes in user behavior that might indicate account compromise or money laundering activity. These features have proven invaluable for maintaining regulatory good standing across multiple jurisdictions.
Payment Gateway Integration
Payment processing for ICO platforms encompasses both cryptocurrency and fiat payment channels. Our payment architecture has processed over $800M in token sale contributions across dozens of currencies and payment methods, maintaining PCI DSS compliance for fiat processing and implementing best practices for cryptocurrency custody.
Cryptocurrency payment integration supports Bitcoin, Ethereum, USDT, USDC, and other major digital assets. We generate unique deposit addresses for each user transaction, monitor blockchain networks for incoming transfers, and automatically credit accounts upon sufficient confirmations. Hot wallet management maintains minimal balances for operational needs, while the majority of funds transfer to cold storage within hours.
Fiat payment integration partners with processors like Stripe, Circle, or Wyre for credit card and bank transfer acceptance. This capability dramatically expands investor accessibility, particularly in regions with limited cryptocurrency adoption. Our systems handle currency conversion, maintain exchange rate accuracy, and process refunds when necessary for failed KYC or regulatory restrictions.
| Payment Method | Processing Time | Transaction Fee | Risk Level |
|---|---|---|---|
| Bitcoin | 10-60 minutes | Variable (network dependent) | Medium |
| Ethereum | 3-15 minutes | $2-50 (gas dependent) | Low-Medium |
| USDT/USDC | 3-15 minutes | $1-20 | Low |
| Credit Card | Instant | 2.9% + $0.30 | High (chargebacks) |
| Bank Transfer | 1-5 business days | 0.5-1% | Low |
Wallet management implements hierarchical deterministic (HD) wallet structures, generating unique addresses from master seeds. This approach simplifies backup procedures while maintaining address uniqueness for transaction tracking. Multi-signature wallets require multiple key approvals for withdrawals, preventing single-point-of-failure theft scenarios.
Fund custody balances operational needs with security. Hot wallets maintain 2-5% of total funds for automated operations, warm wallets (multi-sig requiring manual approval) hold 10-15% for larger transactions, and cold storage (offline hardware wallets) secures the remaining 80-85%. This tiered approach has protected billions in assets across our ico launch platform implementations.
Token Distribution Engine
Token distribution represents the culmination of the ICO process and requires precision execution. Our distribution engines have allocated over 50 billion tokens to hundreds of thousands of investors without error, implementing complex vesting schedules, bonus calculations, and whitelist management.
Allocation algorithms calculate token quantities based on contribution amounts, pricing tiers, bonus percentages, and referral rewards. The system must handle edge cases: partial fill orders, minimum purchase requirements, maximum contribution limits, and bonus caps. Our engines process these calculations in real-time during high-volume sale periods, maintaining accuracy while preventing race conditions.
Vesting schedule implementation locks tokens according to predetermined release schedules. Common patterns include: 6-month cliff with 24-month linear vesting for team allocations, immediate release with quarterly unlocks for early investors, or gradual release beginning immediately after token generation events (TGE). Our vesting contracts support complex schedules with multiple beneficiaries and varying unlock parameters.
Expert Insight: The timing of token distribution has a significant impact on market dynamics. We recommend batched distribution over 24-48 hours rather than simultaneous distribution to all recipients. This approach reduces blockchain congestion, minimizes gas fees, and prevents the perception of “dump events” that negatively affect initial trading sentiment.
Automated distribution mechanisms reduce manual intervention and human error. Our systems generate batch transaction files, submit transactions with appropriate gas pricing, monitor confirmation status, and retry failed transactions automatically. This automation enables distribution to 10,000+ addresses within 48 hours while maintaining operational oversight.
Frontend Architecture and User Experience
Frontend architecture determines user engagement and conversion rates. Our responsive designs maintain functionality across desktop browsers, tablets, and mobile devices, recognizing that 40-60% of ICO participants access ICO platforms via mobile devices. React-based single-page applications provide fluid navigation while Next.js server-side rendering improves SEO and initial load performance.
Wallet connectivity integration supports MetaMask, WalletConnect, Coinbase Wallet, and other popular providers. Our connection flows handle network switching, account changes, and provider disconnection gracefully, maintaining session state and preventing transaction errors. Web3.js and ethers.js libraries enable direct digital contract interaction from browser environments.
Real-time transaction monitoring keeps users informed throughout contribution processes. WebSocket connections provide instant updates on transaction confirmation status, eliminating the anxiety of uncertain transaction states. Visual feedback mechanisms—progress indicators, confirmation animations, and detailed status messaging—maintain user confidence during blockchain processing delays.
Responsive design principles ensure consistent experiences across device types. Mobile-first development prioritizes touch interfaces, simplified navigation, and optimized media loading. Our interfaces maintain sub-3-second initial load times on 4G connections, critical for mobile-dominant markets in Southeast Asia and Africa where ICO adoption grows rapidly.
Security Architecture and Threat Mitigation
Security architecture encompasses every layer of the ICO platform stack. Our comprehensive approach, refined through eight years of production experience and zero successful breaches, implements defense-in-depth strategies that assume breach at every level and plan accordingly.
Digital contract auditing represents the first security checkpoint. We engage multiple independent audit firms (CertiK, Quantstamp, Trail of Bits) for formal verification, conducting both automated analysis and manual review. Audits examine reentrancy vulnerabilities, integer overflow/underflow, access control flaws, and economic attack vectors. Our contracts undergo 3-5 audit rounds before mainnet deployment.
Penetration testing simulates real-world attack scenarios against deployed platforms. Ethical hackers attempt SQL injection, cross-site scripting, authentication bypass, and API exploitation. These exercises uncover vulnerabilities that automated scanning misses, particularly in business logic and workflow implementations. We conduct penetration testing quarterly and after major ICO platform updates.
| Security Measure | Implementation | Protection Against |
|---|---|---|
| DDoS Protection | Cloudflare Enterprise, AWS Shield | Volumetric attacks, application-layer attacks |
| Cold Storage | Hardware wallets (Ledger, Trezor), multi-sig | Private key theft, insider threats |
| WAF | AWS WAF, custom rule sets | SQL injection, XSS, CSRF attacks |
| HSM | AWS CloudHSM, Thales Luna | Key extraction, cryptographic attacks |
| Rate Limiting | Redis-based distributed limiter | API abuse, credential stuffing, brute force |
| Encryption | TLS 1.3, AES-256 at rest | Data interception, storage breaches |
DDoS protection handles both volumetric and application-layer attacks. Cloudflare Enterprise and AWS Shield absorb multi-gigabit DDoS attacks that would overwhelm unprotected infrastructure. Custom WAF rules block malicious patterns specific to ICO platforms: automated bot registration, coordinated contribution attempts, and scraping activities.
Cold storage protocols ensure the majority of funds remain offline. Hardware wallets stored in geographically distributed bank vaults require physical access and multiple key holder presence for transactions. This approach has protected over $2B in client assets from sophisticated phishing, malware, and social engineering attacks targeting hot wallet infrastructure.
Analytics and Reporting Dashboard
Analytics infrastructure provides actionable insights for ICO teams and investors. Our dashboards aggregate data across digital contracts, payment processors, user activities, and market indicators, presenting real-time metrics that inform strategic decisions during critical sale periods.
Investment tracking monitors contributions in real-time: total raised, tokens sold, contributor count, average contribution size, geographic distribution, and payment method breakdown. These metrics enable marketing teams to adjust campaigns based on performance and identify underperforming regions or channels.
Token metrics visualization includes circulating supply, locked supply, vesting schedules, holder distribution, and transfer volumes. Gini coefficients measure wealth concentration, helping teams assess decentralization health. Trading volume analysis across decentralized and centralized exchanges informs liquidity provision strategies.
Investor analytics segment contributors by size, geography, contribution timing, and behavior patterns. Whale identification enables targeted communication strategies. Cohort analysis reveals how different investor groups interact with ICO platforms over time, informing retention and engagement initiatives.
Compliance reporting generates audit trails satisfying regulatory requirements. Our systems maintain immutable logs of KYC verification, transaction approval workflows, system access, and configuration changes. Automated report generation produces quarterly compliance summaries for submission to regulators or external auditors.
Scalability Considerations
Scalability architecture must accommodate 100-1000x traffic spikes during ICO launches. Our infrastructure employs horizontal scaling, caching strategies, database optimization, and CDN implementation to maintain performance under extreme load—lessons learned from managing ICO platforms that handled 50,000+ concurrent users.
Load balancing distributes requests across multiple application server instances. AWS Application Load Balancer or NGINX Plus routes traffic based on instance health, current load, and geographic proximity. Auto-scaling groups automatically provision additional capacity when CPU utilization or request rates exceed thresholds, typically scaling from 5 base instances to 50+ during peak periods.
Caching strategies reduce database queries by 80-90%. Redis caches frequently accessed data: user profiles, token prices, contribution statistics, and configuration settings. Edge caching via Cloudflare or AWS CloudFront serves static assets (JavaScript, CSS, images) from locations near users, reducing latency and origin server load.
Database optimization includes read replicas for analytics queries, connection pooling to manage database connections efficiently, and query optimization guided by explain plan analysis. PostgreSQL handles 10,000+ concurrent connections through PgBouncer pooling, while selective denormalization improves query performance for frequently accessed data patterns.
CDN implementation serves frontend assets and API responses from edge locations. Geographic distribution reduces latency: users in Singapore access servers in Singapore, European users access European servers. This approach reduces average response times from 800ms to under 200ms for global user bases.
Regulatory Compliance Framework
Regulatory compliance represents perhaps the most complex aspect of modern ICO platform architecture. Our compliance frameworks address SEC regulations, MiCA in Europe, MAS guidelines in Singapore, and jurisdiction-specific requirements across 50+ countries where our ico solutions operate.
Jurisdiction-specific requirements vary dramatically. The United States requires Regulation D or Regulation S compliance, restricting sales to accredited investors or non-US persons respectively. Switzerland’s FINMA guidelines distinguish between payment, utility, and asset tokens, each carrying different regulatory obligations. Our ICO platforms implement geo-blocking, accreditation verification, and jurisdiction-specific KYC flows that adapt to local requirements.
Data privacy compliance, particularly GDPR in Europe and CCPA in California, mandates specific data handling practices. Our systems implement right-to-be-forgotten capabilities, consent management, data portability, and breach notification procedures. Privacy-by-design principles minimize data collection and retention, storing only information necessary for regulatory compliance and ICO platform operation.
Multi-Jurisdiction Compliance Checklist
- United States: SEC compliance (Reg D/S), OFAC sanctions screening, state money transmitter licenses
- European Union: MiCA framework, GDPR data privacy, 5AMLD AML requirements
- Singapore: MAS Payment Services Act, accredited investor verification
- Switzerland: FINMA token classification, banking license requirements for securities
- Hong Kong: SFC licensing for security tokens, AML/CTF compliance
Audit trail maintenance creates immutable records of system activities. Every transaction, KYC approval, configuration change, and administrative action generates logged events stored in append-only databases. These audit trails enable forensic analysis during security incidents and demonstrate compliance during regulatory examinations.
Our ico marketing services include compliance consulting that guides clients through regulatory landscapes. This expertise, accumulated over eight years and dozens of successful token launches, helps clients avoid common pitfalls: inadequate disclosures, improper security classifications, or insufficient geographic restrictions that trigger regulatory actions.
DevOps and Deployment Pipeline
DevOps practices enable rapid iteration while maintaining system stability. Our CI/CD pipelines automatically test, build, and deploy code changes, reducing deployment time from days to hours while eliminating human error in deployment processes.
CI/CD workflows using GitLab CI or GitHub Actions trigger automatically upon code commits. Automated test suites execute unit tests, integration tests, and end-to-end tests, preventing deployment of code that fails quality gates. Code coverage thresholds (typically 80%+ for critical services) ensure comprehensive testing of business logic.
Containerization via Docker standardizes application packaging across solution, staging, and production environments. Kubernetes orchestrates container deployment, managing scaling, health checks, and rolling updates with zero downtime. Our clusters run across multiple availability zones, surviving individual data center failures without service interruption.
Infrastructure as Code using Terraform defines entire ICO platform infrastructure in version-controlled configuration files. This approach enables reproducible deployments, facilitates disaster recovery, and documents infrastructure changes. We maintain separate Terraform workspaces for solution, staging, and production environments, preventing accidental production modifications.
Monitoring infrastructure tracks system health continuously. Prometheus collects metrics (CPU, memory, request rates, error rates), Grafana visualizes trends, and PagerDuty alerts on-call engineers when thresholds breach. Our monitoring covers application performance, infrastructure health, digital contract events, and business metrics, providing comprehensive visibility into ICO platform operations.
Incident response procedures define escalation paths, communication protocols, and recovery strategies. Our runbooks document common failure scenarios: database connection pool exhaustion, blockchain node synchronization lag, payment processor outages. This preparation enables rapid response during high-pressure incidents—critical when millions of dollars in contributions hang in balance.
Post-ICO Platform Evolution
Platform evolution extends far beyond initial token sales. Successful ICO platforms evolve into comprehensive token ecosystems supporting secondary markets, governance mechanisms, and ongoing utility features. Our post-ICO services have supported clients through token listing processes, community governance implementation, and platform feature expansion.
Secondary market integration connects platforms with decentralized exchanges (Uniswap, PancakeSwap) and centralized exchanges (Binance, Coinbase). This integration provides investors with liquidity and enables token price discovery. Our platforms monitor trading volumes, manage liquidity pools, and track token holder changes across exchanges.
Governance features enable token holder participation in project decisions. On-chain voting mechanisms, proposal systems, and delegation capabilities transform passive token holders into active community members. We’ve implemented governance systems managing treasuries exceeding $100M, processing thousands of proposals and millions of votes.
Ongoing token utility solution maintains community engagement and token demand. Staking mechanisms, rewards programs, premium feature access, and burn mechanisms create continuous token utility beyond speculative trading. These utility features, integrated directly into ICO platforms, demonstrate project commitment to long-term value creation.
Why Choose Our ICO Platform Architecture Services
With over eight years of specialization in blockchain infrastructure and ICO platform solutions, our team brings unmatched expertise to every project. We’ve architected platforms that raised over $800M across 50+ successful token launches, maintaining perfect security records and regulatory compliance across multiple jurisdictions.
As a full-service ico marketing firm and technical solution partner, we provide end-to-end support: from initial architecture design through digital contract solution, security auditing, compliance consulting, marketing strategy, and post-launch technical support. Our comprehensive approach ensures cohesive platforms that excel technically while meeting business objectives.
Contact our team to discuss your ICO launch requirements. Whether you needa complete platform solution or specialized ico marketing services to complement existing infrastructure, our expertise ensures successful token launches that set industry standards for quality and professionalism.
Conclusion
Building an end-to-end ICO platform architecture requires the synthesis of blockchain technology, cybersecurity, regulatory compliance, financial systems, and user experience design. The complexity exceeds simple digital contract deployment, demanding a comprehensive infrastructure that handles millions of transactions, thousands of users, and multiple regulatory frameworks simultaneously.
Successful ico platforms emerge from careful planning, experienced execution, and continuous optimization. The architectural principles outlined here—modularity, security-first design, scalability planning, compliance integration, and operational excellence—reflect lessons learned across hundreds of deployments and billions in managed assets.
The ICO landscape continues evolving with new blockchain networks, regulatory frameworks, and technological capabilities. ICO Platform architectures must anticipate change, building adaptability into core design principles. Our commitment to architectural excellence and continuous improvement ensures clients benefit from cutting-edge capabilities while maintaining stability and security.
Whether launching utility tokens, security tokens, or hybrid instruments, robust platform architecture determines success. The investment in proper architecture—comprehensive security, regulatory compliance, scalable infrastructure, and excellent user experience—pays dividends through successful fundraising, community confidence, and long-term ICO platform viability.
Frequently Asked Questions
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







