Learn how to implement robust security mechanisms in decentralized multi-level marketing ecosystems using blockchain technology and smart contract auditing
Key Takeaways
- Decentralized MLM platforms operate on fundamentally different security principles than traditional centralized systems, requiring distributed trust mechanisms instead of single-authority controls
- Smart contracts eliminate intermediaries but introduce new vulnerability vectors that demand rigorous third-party auditing before deployment to handle user funds
- Blockchain immutability provides transaction transparency but necessitates privacy-preserving mechanisms to protect sensitive user and referral data from public exposure
- Multi-signature wallets combined with decentralized identity systems significantly reduce account compromise risks by requiring multiple approvals and verified identities
- Regular security audits, community governance structures, and transparent incident response protocols are essential for long-term platform sustainability and user trust
Introduction to Decentralized MLM Security
What Decentralized MLM Platforms Are
Decentralized multi-level marketing platforms represent a significant evolution in how network-based business models operate. Unlike traditional MLM systems where a single company controls all operations, decentralized MLM platforms run on blockchain networks where no single entity has complete control over the system. These platforms use smart contracts to automate commission distributions, verify referral relationships, and process payments without requiring a central authority to manage these functions.
At their core, decentralized MLM platforms allow participants to join networks, build teams, and earn commissions through referrals and product sales. The fundamental difference lies in the infrastructure. Instead of a company’s centralized database storing all information, data is distributed across thousands of network nodes. This distribution creates transparency but also introduces unique security challenges that traditional MLM systems never face.
Why Security Is More Critical in Decentralized Environments
In a centralized MLM system, security relies on a company’s professional infrastructure, dedicated security teams, and legal accountability. If a customer’s funds are stolen from a centralized system, the company can potentially recover them or provide reimbursement. In decentralized systems, once a transaction is recorded on the blockchain, it becomes virtually irreversible. There is no customer support team that can undo a fraudulent transfer or recover stolen assets.
This permanence creates an environment where security failures have immediate and lasting consequences. A vulnerability in a smart contract could result in millions of dollars being stolen with no recovery mechanism available. Private keys stolen from a wallet are lost forever with no password reset option. The burden of security shifts directly from the platform to individual users, making education and proper systems absolutely essential. For platforms managing significant user funds and personal data across distributed networks, security frameworks become the critical foundation of user trust and platform credibility.
How Decentralization Changes MLM Security Models
Centralized vs Decentralized Security Comparison
Security Architecture Comparison: Traditional vs Decentralized MLM
| Security Aspect | Centralized MLM System | Decentralized MLM System |
|---|---|---|
| Control Authority | Single company manages all systems and policies | Distributed across thousands of independent network nodes |
| Data Storage | Centralized database with redundant backups | Replicated across thousands of geographically distributed nodes |
| Transaction Reversal | Company can reverse fraudulent transactions if detected | Transactions are permanent and immutable once recorded |
| Single Point of Failure | Vulnerable to company server compromise or data center attacks | No single point of failure by design, attacks must overcome majority of network |
| Update Management | Controlled exclusively by company development team | Requires consensus from network participants through governance |
| Account Recovery | Support team can reset passwords and restore account access | Users bear responsibility for protecting their own private keys |
| Audit Trail | Controlled and potentially modifiable by company | Immutable and publicly verifiable by any network participant |
Role of Blockchain in Removing Single Points of Failure
Traditional MLM systems depend entirely on company infrastructure to operate. When a company’s servers experience downtime, the entire platform stops functioning. If hackers penetrate the company’s database, millions of customer records become exposed. This creates what security experts call a single point of failure: one successful attack compromises the entire system.
Blockchain technology eliminates this vulnerability through deliberate distribution. Rather than storing information on one database on one server, the identical information is stored on thousands of computers across the network. When a user initiates a transaction, it broadcasts to these thousands of nodes simultaneously. Each node independently verifies the transaction using cryptographic algorithms before adding it to the permanent ledger. To compromise the system, an attacker would need to simultaneously hack a majority of these thousands of computers, which is practically impossible given their geographic distribution and independent operation.
This distributed architecture provides another crucial benefit: complete transparency. Every transaction is publicly visible to anyone on the network. This means fraudulent activity leaves a permanent, unchangeable record that the community can audit and verify. The combination of distributed storage and transparent verification creates a security model fundamentally different from centralized systems where trust relies on a single company’s promises.
Blockchain as the Core Security Layer
Immutability of Transaction Records
One of blockchain’s most powerful security features is immutability. Once data is recorded on a blockchain, it cannot be changed, deleted, or altered without making that tampering immediately obvious to everyone. This works through cryptographic hashing. Each block contains a mathematical fingerprint called a hash of all the data inside it, plus a reference to the previous block’s hash. If someone attempts to change even a single character in an old transaction, the hash of that block changes. This broken chain becomes immediately apparent because the next block still references the old hash, creating a mismatch that the entire network rejects.
For MLM platforms, immutability provides crucial security benefits. Once a commission is paid to a participant, that record cannot be altered by a hacker or corrupted by a system error. Referral relationships cannot be retroactively changed to steal credit from one person and give it to another. Every transaction that has occurred remains exactly as it was recorded, creating an auditable history that participants can independently verify personally.
This immutability also prevents a common fraud pattern in traditional MLM systems: the company altering commission records to reduce payouts to distributors. In a decentralized system, the company simply cannot do this because changing the records would require recomputing the entire blockchain’s cryptographic proofs, which is computationally infeasible with current technology.
Distributed Ledger Transparency and Verification
A distributed ledger is a database that multiple independent parties maintain and verify simultaneously. Rather than trusting one company’s records, participants can run their own nodes and verify data themselves. If the central company claims a participant earned 100 tokens last month, that participant can independently check the blockchain and confirm this claim is true. If someone disputes referral relationships, the blockchain provides cryptographic proof of exactly when the relationship was established.
This transparency creates accountability that doesn’t exist in traditional systems. Every participant effectively becomes an auditor capable of verifying transactions. The network’s consensus mechanism ensures that before any transaction is added to the permanent ledger, the majority of participants have independently verified it is legitimate. This prevents fraudulent transactions from being recorded in the first place.
However, transparency comes with important trade-offs. In a completely transparent system, everyone can see everyone else’s transactions, account balances, and referral relationships. For MLM platforms where privacy concerns exist around referral networks and earnings visibility, this requires additional privacy-preserving mechanisms, which we discuss in detail in later sections.
Smart Contracts and Automated Trust
How Smart Contracts Enforce MLM Rules
Smart contracts are self-executing computer programs that run on blockchain networks. They automatically perform predetermined actions when specified conditions are met. In an MLM context, a smart contract might be programmed to automatically execute a commission payout whenever a participant’s referral completes a purchase. Rather than waiting for a company to manually process the payment through their systems, the smart contract instantly and automatically transfers the commission to the correct participant’s wallet.
This automation eliminates several traditional trust requirements. Participants don’t need to trust that a company will pay them correctly because the payment happens automatically according to rules encoded in the contract. The rules are transparent and immutable, visible to everyone on the network, and execute identically every single time. If a smart contract specifies that a level-1 referral earns 10 percent commission, that rule applies consistently to every transaction across the entire network without exception.
Smart contracts also enable complex MLM structures to function without human intervention. Multi-level commission distributions, bonus calculations based on team performance metrics, and tiered rewards can all be calculated and distributed automatically. This reduces operational costs significantly and eliminates delays in payment processing that plague traditional MLM systems.
Security Risks from Poorly Written Smart Contracts
Despite their benefits, smart contracts are not automatically secure. They are computer programs written by humans, and like all software, they can contain bugs. Unlike traditional software where bugs can be fixed with an update, smart contract bugs often cannot be fixed once deployed because of blockchain immutability. A vulnerability in the code can be exploited immediately to steal user funds, and stolen funds cannot be recovered.
Common smart contract vulnerabilities include reentrancy attacks where a contract is called recursively to drain funds before security checks execute, integer overflow and underflow errors in mathematical calculations, and access control flaws where incorrect users gain permission to sensitive functions. In 2016, the DAO (a decentralized organization on the Ethereum network) was hacked due to a smart contract reentrancy vulnerability, resulting in the loss of approximately 50 million dollars worth of cryptocurrency that could never be recovered.
For MLM platforms, poorly written smart contracts could result in commission calculations being incorrect, user funds being transferred to wrong addresses, or entire platform wallets being drained by attackers. This is why professional security audits from reputable firms are critical before deployment, which we discuss in detail later in this article.
Common Security Threats in Decentralized MLM
 Smart Contract Exploits
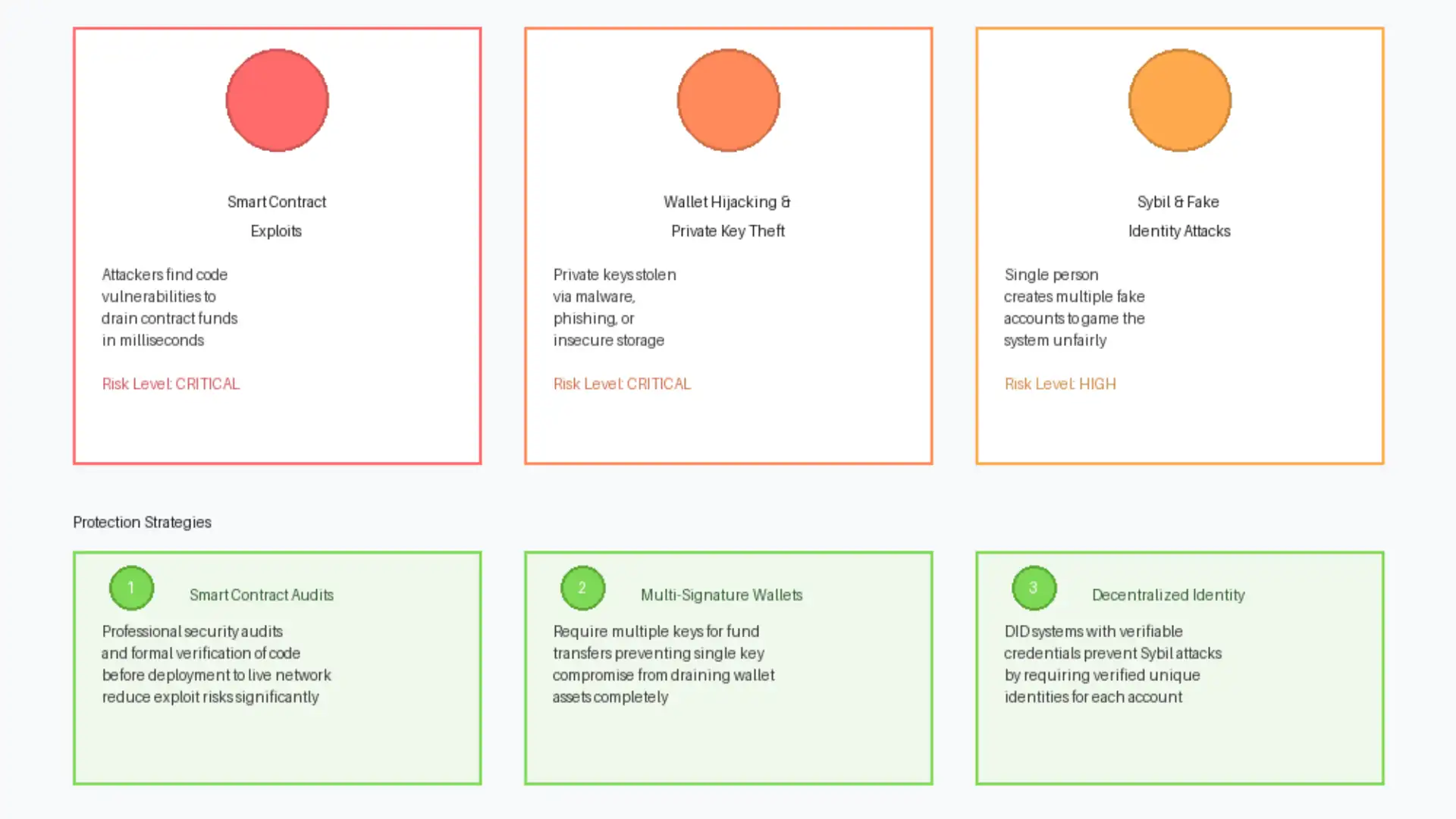
Smart Contract Exploits
Smart contract exploits are carefully designed programs that target vulnerabilities in contract code to manipulate its behavior or extract funds. An attacker might discover that a reentrancy vulnerability allows them to withdraw funds multiple times before the contract records the transaction on the ledger. Or they might find that the contract’s access control is weak, allowing anyone to call a sensitive function that should only be restricted to authorized administrators.
These exploits can execute within milliseconds, and a single well-executed attack can drain an entire contract of its available funds instantly. In 2022, the Ronin bridge (a cross-chain transfer system) was exploited for 625 million dollars due to compromised validator keys and weak security controls in place. This incident demonstrates that even high-value systems with significant user funds can be vulnerable to well-designed attacks.
Wallet Hijacking and Private Key Theft
A blockchain wallet is secured by a private key: a long string of characters that grants exclusive access to all funds in that wallet. Anyone who possesses the private key can transfer all the funds to any address. If an attacker steals a user’s private key, they gain complete access to that user’s wallet and all their assets. Unlike a traditional bank account, there is no way to recover access or dispute the theft.
Private keys are stolen through several methods. Malware on a user’s computer can capture keystrokes or read files where keys are stored in plain text. Phishing websites trick users into entering their private keys on fake sites. Hardware wallets that are improperly secured can be physically accessed by thieves. Many users store private keys in unsecured locations like email screenshots, cloud services, or plain text files, making them easy targets for hackers.
Once stolen, a private key cannot be changed or reset. The user loses access to their wallet and all its contents permanently. Unlike a bank account where customers can dispute unauthorized transactions, blockchain transactions are final and irreversible. This makes wallet security one of the most critical elements of decentralized platform safety.
Sybil and Fake Identity Attacks
A Sybil attack occurs when one person creates multiple fake identities to gain unfair advantages or manipulate the system. In a decentralized MLM, someone could create hundreds of fake accounts and claim they are different people. They could then claim to have built a massive referral network, earning commissions from fake sales that never actually occurred anywhere.
Sybil attacks are particularly dangerous in decentralized systems because there is no central authority to verify that an identity is genuinely unique. On the Ethereum blockchain, for example, anyone can create a new wallet address in seconds for completely free. Without identity verification mechanisms in place, someone could create thousands of addresses and use them to manipulate the entire MLM structure.
These attacks undermine the fundamental fairness of the MLM system. Legitimate participants who are building networks through actual relationships are disadvantaged compared to someone creating fake identities. Sybil attacks can also be used to manipulate network-level consensus decisions in governance systems, allowing attackers to control platform upgrades and changes.
User Identity and Access Control
Decentralized Identity (DID) Systems
Decentralized identity systems address the Sybil attack problem by allowing users to prove their identity without relying on a single central authority. A DID is a unique identifier that a person controls directly. Unlike a username assigned by a company, a person owns their DID completely and can use it across multiple platforms without permission from any central authority.
A DID is typically backed by cryptographic proof and data stored on a blockchain or similar distributed system. When someone creates a DID, they link it to verifiable credentials: digital documents that cryptographically prove facts about them. A credential might be a government ID verification, a social media account verification, or a verification from another trusted party that confirms the person is unique and genuine.
For MLM platforms, DIDs and verifiable credentials can prevent Sybil attacks effectively. A platform could require that users link their accounts to verified identities before earning commissions. If someone tries to create a hundred accounts, they would need a hundred verified identities, which would require that many unique government IDs or other credentials. This makes Sybil attacks impractical while still preserving user privacy because the platform can verify identity without collecting sensitive personal information.
The advantage of a DID system is that the user remains in complete control. Rather than giving a company their government ID, they can use a DID system to share only the specific verification needed without revealing their actual identifying information.
Multi-Signature Authentication Mechanisms
Multi-signature (multi-sig) authentication requires multiple private keys to authorize transactions. Instead of a wallet being controlled by a single key, it might require the approval of three out of five designated keyholders. This provides significant protection against private key theft because stealing one key doesn’t grant full access to the wallet.
In practice, a user might store one key on their personal computer, one on a hardware wallet kept in a safe, and one with a trusted family member or professional custodian. To transfer funds, keys from at least two of these locations must be used. An attacker who steals the computer-based key cannot move funds because they don’t have the other required keys. This significantly increases security because an attacker would need to compromise multiple separate systems simultaneously.
For MLM platforms, multi-signature wallets are particularly useful for managing platform treasury accounts and escrow accounts that hold commission payments. A transaction moving large amounts of funds might require approval from multiple platform administrators, preventing any single compromised account from authorizing a fraudulent transfer of funds.
Data Privacy in Decentralized MLM Networks
On-Chain vs Off-Chain Data Storage Risks
Blockchains are fundamentally transparent by design. Every transaction and piece of data recorded on-chain is visible to everyone on the network. While this transparency provides security and auditability benefits, it creates significant problems for privacy-sensitive information. If every referral relationship, earnings amount, and purchase history is visible on-chain, this creates a permanent, public record that anyone can analyze.
Off-chain storage means keeping data on traditional databases or cloud services rather than the blockchain. An MLM platform might store a user’s personal information, email address, and phone number off-chain for privacy reasons, while recording only the cryptographic hash of that information on-chain. The hash serves as a fingerprint proving the data hasn’t been altered, but the actual personal information remains private.
However, off-chain storage creates new risks. If the database containing off-chain data is hacked, personal information could be stolen immediately. The platform operator controls this off-chain data, potentially undermining the privacy benefits of decentralization. A balance must be carefully struck between transparency, which provides security, and privacy, which protects users from having their information exposed publicly.
Protecting User and Referral Data
Several techniques can effectively protect user data while maintaining decentralization principles. Encryption is the most fundamental approach: data is scrambled using mathematical algorithms so that only people with the correct decryption key can read it. A platform could store encrypted user information on a decentralized database where even the storage nodes cannot access the unencrypted data. Only the user and authorized parties have the key to decrypt their information.
Another practical approach is data minimization: collect and store only the information absolutely necessary for the platform to function properly. If the platform doesn’t need to know a user’s full name, it might only store an anonymous identifier. If it doesn’t need transaction history older than six months, older data can be deleted from systems.
Zero-knowledge proofs are an emerging technology that allows one party to prove something to another without revealing the underlying information. A platform could prove to a regulator that it has verified user identities without actually revealing the user data itself. This provides regulatory compliance while protecting privacy completely.
Financial Security and Fund Protection
Secure Handling of Commissions and Payouts
In a decentralized MLM, commissions are often held in smart contracts temporarily before being paid out to participants. The key security challenge is ensuring that these funds are not stolen or misused before reaching their intended recipients. If a smart contract holds 100 million dollars in pending commissions, attackers have significant motivation to find vulnerabilities.
Secure commission handling requires multiple layers of protection. The smart contract code must be professionally audited by reputable firms to ensure it correctly calculates and stores commission amounts. Access controls must be implemented so that only authorized functions can move funds. Formal verification techniques can mathematically prove that the contract will behave as intended under all conditions. Integration with hardware security modules can ensure that critical functions require physical approval.
Another best practice is rate limiting: restricting how much can be withdrawn in a single transaction or time period. If a smart contract allows withdrawals of up to 10,000 dollars per day from a wallet, then even if the wallet is compromised, the attacker can steal at most 10,000 dollars per day. This gives the legitimate owner time to detect the theft and transfer the remaining funds to safety.
Escrow Mechanisms and Locked Smart Contracts
Escrow is a traditional financial mechanism where a neutral third party holds funds during a transaction. In blockchain terms, a smart contract can act as an escrow agent. When a participant wants to sell tokens to another participant, the smart contract receives the payment and holds it until both parties confirm the transaction is complete. Only then does the contract release the funds to the seller.
Locked smart contracts are contracts where certain functions cannot be modified after deployment. The contract code is permanent and cannot be changed, providing absolute certainty that the contract will behave exactly as programmed. Some platforms take this further by implementing time-locks: functions that can be called, but changes don’t take effect for a specified period. If a security vulnerability is discovered, there is time to cancel the change before it goes live.
For MLM platforms, escrow mechanisms can be used for commission distributions between levels. When a sale occurs, the commission is temporarily held in escrow, ensuring it reaches the correct recipients. This prevents situations where a commission is transferred to the wrong address or intercepted by fraudsters.
Network Level Security Considerations
Consensus Mechanisms and Attack Resistance
A consensus mechanism is the process by which a blockchain network agrees on what transactions are valid and should be added to the ledger. Different consensus mechanisms provide different levels of security. Proof of Work, used by Bitcoin, requires participants to solve complex mathematical puzzles to validate blocks. This makes it computationally expensive to attack the network because an attacker would need to control more computing power than the rest of the network combined.
Proof of Stake, used by Ethereum 2.0, requires participants to hold cryptocurrency as collateral. If someone acts dishonestly, their collateral is seized. This creates economic incentives for honest behavior because attacking the network costs money directly. The choice of consensus mechanism affects how much computational or financial resources an attacker needs to compromise the network.
A Proof of Work network on a popular blockchain like Ethereum would be extremely expensive to attack. A smaller blockchain with fewer participants might be vulnerable to attacks from someone with moderate resources. MLM platforms must consider whether to use an existing blockchain which inherits its security, or build their own which gives them control but requires significant security investment.
Protection Against 51% and Network Attacks
A 51 percent attack occurs when someone gains control of more than half the computing power or stake in a blockchain network. With this majority, they could theoretically rewrite transaction history, prevent transactions from being confirmed, or double-spend coins. However, in practice, a 51 percent attack on a large network is extremely expensive. The Bitcoin network would require someone to purchase more than 300 billion dollars worth of mining equipment to conduct a 51 percent attack.
Smaller blockchains or those with lower security budgets are vulnerable to 51 percent attacks. If a platform launches its own blockchain with limited participants, an attacker with moderate resources might gain majority control. This is why many MLM platforms choose to build on established blockchains rather than creating their own, inheriting the security of the much larger network.
Eclipse attacks are a different network threat where attackers control many nodes and surround a target node, preventing it from communicating with the rest of the network. This doesn’t compromise the blockchain itself, but it can prevent specific users from participating. Protection requires geographic distribution of nodes and connection diversity so that nodes maintain connections to the broader network.
Smart Contract Audits and Code Verification
Importance of Third-Party Security Audits
Before deploying smart contracts that will manage user funds, professional security audits are absolutely essential. An audit is a detailed examination of the code by security experts looking for vulnerabilities. A reputable security firm will review the contract line by line, test edge cases, simulate realistic attacks, and produce a detailed report of any vulnerabilities found.
Third-party audits are critical because the developers who wrote the code are often too close to it to spot problems objectively. They know what the code is intended to do, so they miss cases where it might do something unintended. An external auditor approaches the code fresh, asking “what could go wrong?” rather than assuming it works as intended.
The cost of an audit is significant, often ranging from tens of thousands to hundreds of thousands of dollars depending on the contract’s complexity. However, this cost is minimal compared to the cost of a vulnerability being exploited. If a 100 million dollar smart contract is hacked due to poor code, the financial loss is devastating. An audit that costs 100,000 dollars is a worthwhile investment to prevent that.
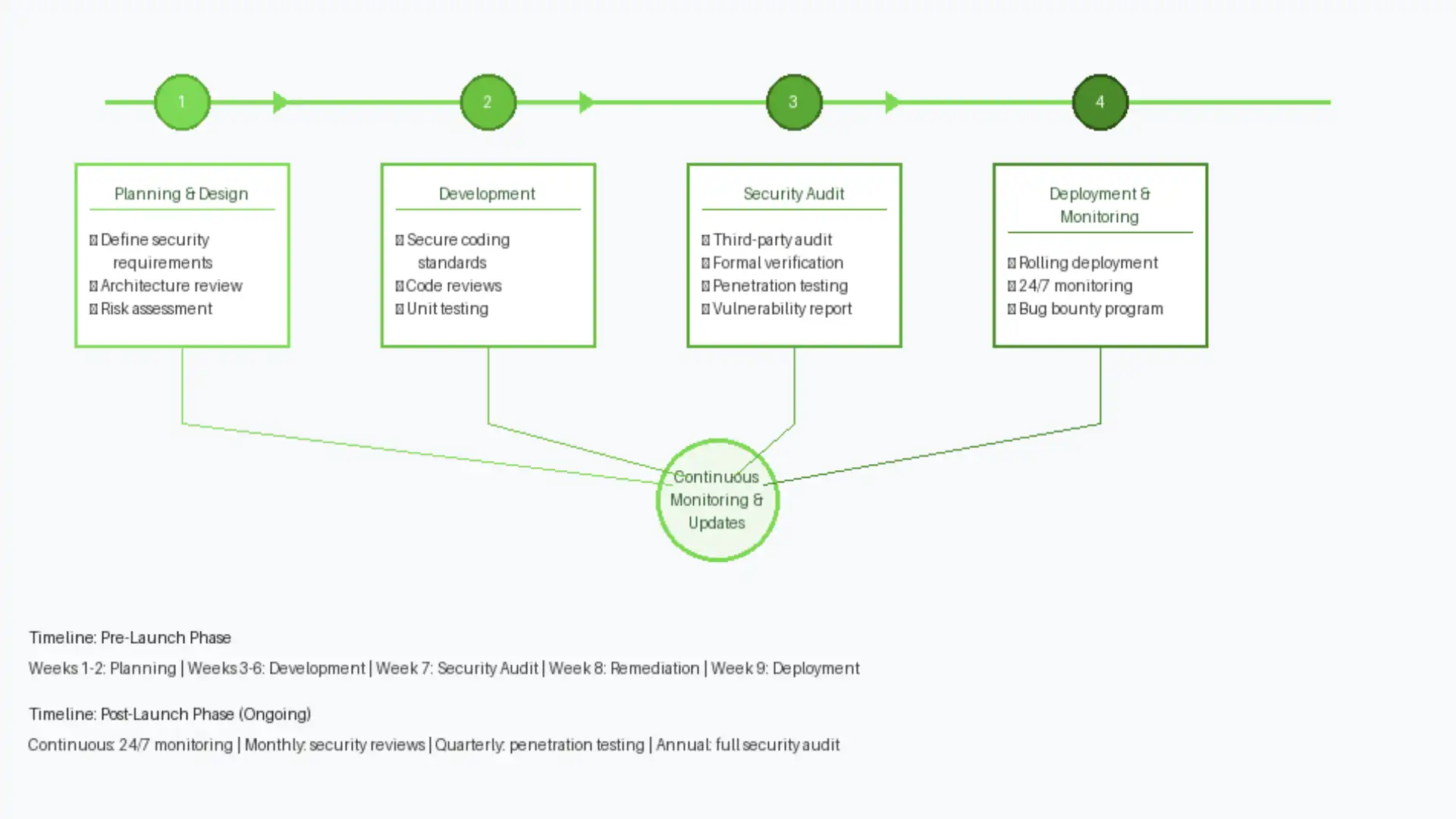
For MLM platforms, audits should occur before launch and whenever the smart contract code is updated. Even minor changes to contract code can introduce vulnerabilities, so each change should be audited by professionals before deployment.
Continuous Monitoring and Vulnerability Testing
Security doesn’t end when a smart contract is deployed. Continuous monitoring detects unusual activity that might indicate an attack in progress. If a smart contract suddenly receives thousands of transactions per second or funds start flowing to unexpected addresses, automated monitoring systems alert administrators to investigate immediately.
Vulnerability testing involves periodically running security tests against the live contract to catch new vulnerabilities that might have been missed in the initial audit. This includes running formal verification tools that mathematically prove the contract’s behavior under different conditions, and conducting penetration tests where security experts actively try to exploit the contract.
Bug bounty programs invite the public to find vulnerabilities and report them responsibly in exchange for financial rewards. This harnesses the global security community to find issues before malicious attackers do. Platforms should establish clear policies for how security researchers can report vulnerabilities without accidentally triggering legal liability.
Governance and Security Oversight
Role of DAOs in Managing Security Updates
A DAO (Decentralized Autonomous Organization) is a governance structure where token holders vote directly on decisions about the platform. Rather than a company’s board making all decisions, community members participate directly in governance. For security decisions, a DAO structure can be both beneficial and challenging simultaneously.
The benefit is that security updates cannot be imposed without community approval. If the platform’s governing company tried to make changes that undermined security, token holders could vote against it. This prevents a scenario where central authority acts in bad faith and prioritizes profit over security.
The challenge is that security decisions often require speed. If a critical vulnerability is discovered, waiting for a DAO vote might not be feasible. The vulnerability could be exploited while the community is voting on whether to apply a patch. This is why many platforms use a hybrid approach: a security council has authority to implement emergency security patches without a vote, but must report to the DAO afterward and can be overruled if they abuse this power.
Community-Driven Incident Response
When a security incident occurs, rapid response is critical to minimize damage. Community-driven incident response means that multiple independent parties contribute to understanding and fixing the problem. If one party is compromised or not trustworthy, others can verify the facts and escalate concerns appropriately.
This requires transparent communication from the start. When an incident happens, the platform should immediately disclose what is known, what remains unknown, and what steps are being taken. This allows security researchers and community members to contribute ideas and verify that the response is effective. Transparency also prevents rumors and panic that would occur if information was withheld.
A clear incident response plan should be documented before any incident occurs. Who has authority to make decisions? How are emergency patches deployed? How are affected users notified? Having these procedures decided in advance allows rapid response when incidents happen.
Regulatory and Compliance Security Risks
Legal Exposure Due to Jurisdictional Ambiguity
Blockchain networks operate across borders globally. A participant in Japan can transact with someone in Brazil instantaneously without involvement from either country’s banks. This creates complex legal questions: which country’s laws apply to transactions? Who has authority to regulate the platform?
Different jurisdictions have different requirements for MLM systems, cryptocurrency exchanges, and financial services. Some countries prohibit pyramid schemes entirely. Others allow MLMs under specific conditions. Some restrict cryptocurrency transactions while others embrace them. A decentralized MLM platform operating globally faces potential legal conflicts because it operates under different rules in different jurisdictions simultaneously.
| Jurisdiction | MLM Status | Crypto Stance | KYC Requirements |
|---|---|---|---|
| United States | Regulated but allowed with restrictions | Regulated as commodity | Strict KYC/AML required |
| European Union | Restricted in some countries | Increasingly regulated | GDPR privacy requirements apply |
| China | Prohibited and banned | Crypto trade banned | Strict controls and prohibition |
| Singapore | Regulated framework exists | Progressive stance | Moderate KYC requirements |
| Japan | Regulated and allowed | Regulated framework | Strict KYC compliance |
KYC/AML Balance with Decentralization
KYC (Know Your Customer) and AML (Anti-Money Laundering) requirements mandate that financial institutions identify users and monitor for suspicious activity. These regulations exist to prevent money laundering and terrorist financing. However, implementing KYC requires collecting personal information, which conflicts with privacy principles of decentralization.
A platform must implement identity verification sufficient to comply with regulations while minimizing personal data collection. One approach is to use decentralized identity systems where verifications happen off-chain and only minimal data is stored on the blockchain. Another is to implement selective disclosure: the platform can verify that a user is a unique individual without collecting unnecessary personal details.
AML compliance requires monitoring for unusual transactions. In a decentralized system where the platform has no central authority, this monitoring must happen through algorithmic analysis rather than manual review. The platform can flag suspicious transaction patterns and require additional verification before transactions complete, without requiring a human reviewer to examine every transaction.
Best Practices for Building Secure Decentralized MLM Platforms
Secure Coding Standards
Secure coding practices prevent vulnerabilities from being introduced during development. Code reviews are essential: another developer examines all code changes before they are deployed. Code reviews catch bugs that the original developer missed. Industry standards like OpenZeppelin’s security guidelines establish best practices for blockchain development.
Developers should use formal verification tools when possible. These tools mathematically prove that code behaves correctly under all conditions. Testing should be extensive: unit tests verify individual functions, integration tests verify that functions work together, and stress tests verify that the system handles extreme loads.
Documentation should be clear and detailed. Security vulnerabilities often exist because developers made incorrect assumptions about how the system works. Good documentation prevents misunderstandings and makes it easier for auditors to understand the code.
Wallet Safety Education for Users
In decentralized systems, users bear responsibility for protecting their own private keys. If a user loses their private key or it is stolen, their assets are lost permanently. Platforms must educate users extensively about wallet security. This includes clear guidance on how to store private keys safely, how to identify phishing attacks, and how to use hardware wallets effectively.
Platforms should provide tools that make safe practices easy. Hardware wallet integration allows users to approve transactions without exposing their private keys to their computers. Key recovery mechanisms allow users to restore access to their wallets if devices are lost. Educational resources should be easily accessible and regularly updated as new threats emerge.
Upgrade and Patch Management
When security vulnerabilities are discovered, patches must be deployed quickly. However, deploying patches to a decentralized system is challenging because no single authority can force all nodes to update. Instead, platforms must implement gradual upgrade mechanisms where new code is tested extensively before being rolled out.
A rolling deployment strategy updates a percentage of nodes at a time, monitoring for problems before updating the rest. Backwards compatibility ensures that nodes running older versions can still communicate with nodes running newer versions, preventing network fragmentation during upgrades. Version pinning allows users to choose when to upgrade rather than forcing automatic updates.
Future Trends in Decentralized MLM Security
AI-Driven Threat Detection
Machine learning algorithms can analyze blockchain transaction patterns to detect suspicious activity more effectively than rule-based systems. These algorithms learn to recognize normal transaction patterns and flag anomalies that might indicate fraud, Sybil attacks, or other malicious activity. As platforms accumulate more transaction data, AI systems become increasingly accurate at distinguishing legitimate activity from attacks.
Zero-Knowledge Proofs for Privacy
Zero-knowledge proofs allow one party to prove a statement to another without revealing the information that backs up the statement. A platform could prove to a regulator that it has verified users without revealing user identities. Users could prove they earned commissions without revealing their entire transaction history. As zero-knowledge proof technology matures, it will enable privacy and compliance to coexist.
Cross-Chain Security Challenges
As decentralized platforms expand to multiple blockchains, security challenges multiply. Bridging between blockchains requires locking assets on one chain and releasing equivalent assets on another. If a bridge is poorly designed, attackers can exploit the bridge to steal assets. Cross-chain atomic swaps (where transactions on multiple chains succeed together or fail together) are complex to implement securely.
Related Resources and Further Reading
To understand the broader context of MLM systems and their evolution toward decentralization, explore these complementary articles from NADCAB’s comprehensive blog:
- ► Why Semi-Decentralized MLM Systems Are Gaining Traction – Discover the advantages and implementation strategies of semi-decentralized models that balance transparency with practical control mechanisms
- ► MLM Meaning, Types, Benefits, and Global Regulation – Understand the fundamentals of MLM structures and how different countries regulate these systems
Conclusion: Building Trust Through Security
Decentralized MLM platforms represent a fundamental shift in how network marketing operates. By removing central intermediaries and leveraging blockchain technology, these platforms can provide greater transparency and fairer compensation structures. However, this decentralization comes with profound security challenges that traditional centralized MLMs simply do not face.
The security framework for decentralized MLM must address threats at multiple levels simultaneously. At the smart contract level, rigorous auditing and formal verification prevent code vulnerabilities from being exploited. At the network level, robust consensus mechanisms resist attacks and ensure immutability of records. At the user level, education and tools like hardware wallets and decentralized identity systems protect against account compromise. At the governance level, transparent decision-making and community oversight ensure that security measures are maintained and updated.
No security framework is perfect or permanent. New attack vectors emerge as technology evolves and attackers develop new techniques. Platforms that succeed in the long term are those that treat security not as a one-time implementation, but as an ongoing commitment. This means continuous monitoring for threats, regular smart contract audits, rapid response to incidents, and transparent communication with users about security measures.
For participants in decentralized MLM systems, understanding these security mechanisms is essential for safe operation. Rather than trusting a company to protect them, users share responsibility for their own security. Protecting private keys, using multi-signature wallets, and verifying transactions before approving them are no longer optional practices. They are fundamental to operating safely in a decentralized ecosystem.
The future of decentralized MLM platforms depends on building trust through robust security. Platforms that invest in security infrastructure, prioritize user education, and maintain transparency about vulnerabilities and incidents will earn the trust necessary for long-term sustainability. In contrast, platforms that cut corners on security or obscure security issues will eventually be exploited, losing user funds and destroying their credibility. For platform builders and participants alike, security is not an afterthought. It is the foundation upon which trust is built.
With over 8 years of expertise in decentralized systems and MLM architecture, Nadcab Labs has helped numerous organizations implement secure, compliant, and user-friendly blockchain-based network marketing platforms. Our experience spans security architecture, smart contract development, regulatory compliance, and platform governance across multiple jurisdictions and blockchain networks.
Frequently Asked Questions
Decentralized MLM platforms use blockchain technology, which removes the need for a central authority to control data or transactions. This reduces risks like data tampering, insider fraud, and single-point failures. Transactions are recorded on an immutable ledger, making them transparent and verifiable, which helps build trust and improves overall platform security.
Smart contracts automatically execute MLM rules such as commission distribution and referral validation without human intervention. This prevents manipulation, delayed payouts, and unauthorized changes. Once deployed, smart contracts cannot be altered easily, ensuring predictable behavior. However, their security depends on clean coding and proper audits before deployment.
Despite decentralization, risks still exist. Common threats include smart contract vulnerabilities, private key theft, phishing attacks, fake wallet connections, and poor user security practices. Network-level attacks and unverified third-party integrations can also pose risks. Strong audits, user education, and secure wallet management help reduce these issues significantly.
Most decentralized MLM platforms avoid storing sensitive user data directly on the blockchain. Instead, they use encrypted off-chain storage combined with blockchain verification. Wallet-based identities reduce the need for personal data. Advanced techniques like zero-knowledge proofs can further enhance privacy while still allowing secure participation in the MLM network.
No system is completely hack-proof, including decentralized MLM platforms. While blockchain itself is highly secure, vulnerabilities usually come from poorly written smart contracts, insecure front-end applications, or compromised user wallets. Regular audits, secure APIs, and educating users about wallet safety are essential to minimize hacking risks.
Security audits are critical for identifying vulnerabilities in smart contracts and system architecture before attackers can exploit them. Third-party blockchain security firms review code logic, permissions, and fund-handling mechanisms. Regular audits increase platform credibility, prevent financial loss, and ensure that decentralized MLM systems operate as intended.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







