Smart contract token security has become a critical concern as billions of dollars flow through blockchain networks daily. These self-executing contracts automate transactions and enforce agreements without intermediaries, but their immutable nature means vulnerabilities can lead to permanent losses. Understanding what makes a token smart contract secure helps developers, investors, and project teams make informed decisions about protecting digital assets. This guide explores the essential security features, common vulnerabilities, and best practices for secure smart contract development.
Key Takeaways
- Immutable Code: Once deployed, smart contracts cannot be modified, making security-first design essential before launch.
- Common Vulnerabilities: Reentrancy attacks, overflow/underflow bugs, and front-running represent major security threats to token contracts.
- Rigorous Testing: Comprehensive testing across multiple scenarios identifies potential bugs before deployment to mainnet.
- Security Audits: Third-party smart contract audits provide independent verification of code security and best practice compliance.
- Access Control: Proper permission structures prevent unauthorized functions from being executed by malicious actors.
- Safe Math Libraries: Using established libraries for mathematical operations prevents overflow and underflow vulnerabilities.
- Continuous Monitoring: Post-deployment monitoring detects unusual activity patterns that may indicate security breaches.
Understanding Smart Contract Tokens
A token smart contract is a self-executing program with agreement terms written directly into code, operating on blockchain technology to automatically enforce and execute conditions when predefined criteria are met. Unlike traditional contracts requiring intermediaries, smart contracts eliminate third-party involvement while providing transparent, tamper-proof execution.[1]
Token smart contracts specifically manage the creation, transfer, and behavior of cryptocurrency tokens. They define total supply, transfer rules, balance tracking, and any special functionality like burning, minting, or governance features. The security of these contracts directly impacts every token holder, making smart contract security a foundational requirement for any blockchain project.
The immutable nature of blockchain means that once a smart contract is deployed, its code cannot be changed. This permanence creates both advantages and challenges. While immutability prevents tampering, it also means vulnerabilities in deployed contracts cannot be patched through simple updates. This reality underscores why secure token development practices must be prioritized from the earliest stages of project planning.
Common Smart Contract Vulnerabilities
Understanding common attack vectors helps developers anticipate risks and implement appropriate safeguards during the development process.
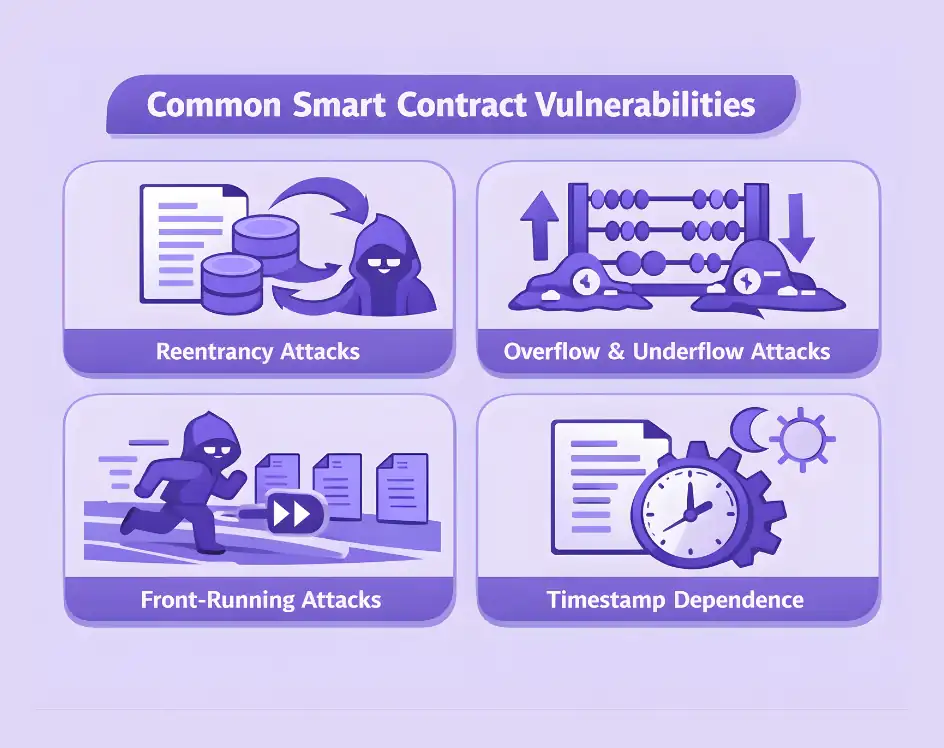
Reentrancy Attacks
Reentrancy attacks occur when a malicious contract repeatedly calls back into the vulnerable contract before the first execution completes. This exploitation can drain funds by manipulating state changes. The infamous DAO hack in 2016 resulted from a reentrancy vulnerability, leading to $60 million in losses and ultimately a hard fork of the Ethereum blockchain.
Reentrancy attack prevention requires careful ordering of operations. The checks-effects-interactions pattern ensures that state changes occur before external calls, preventing attackers from exploiting intermediate states. Using reentrancy guards that lock functions during execution provides additional protection.
Overflow and Underflow Attacks
Integer overflow and underflow protection is essential for Solidity smart contract security. When arithmetic operations exceed variable limits, values can wrap around unexpectedly. An overflow might turn a large number into zero, while underflow could transform zero into an enormous value.
Modern Solidity versions (0.8.0+) include built-in overflow and underflow protection that reverts transactions when these conditions occur. For older codebases, SafeMath libraries provide similar protection through checked arithmetic operations that fail safely rather than producing incorrect results.
Front-Running Attacks
Front-running occurs when malicious actors observe pending transactions and submit their own transactions with higher gas fees to execute first. In token contexts, this might involve detecting large buy orders and purchasing tokens beforehand to profit from the subsequent price increase.[2]
Mitigating front-running requires design-level considerations including commit-reveal schemes, transaction ordering protections, and limiting the profitability of front-running through mechanism design. These protections should be considered during initial contract development rather than as afterthoughts.
Timestamp Dependence
Contracts relying on block timestamps for critical logic face manipulation risks. Miners have limited ability to adjust timestamps, which can be exploited when contracts use time for random number generation or deadline enforcement. Secure development practices minimize timestamp dependence for security-critical functions.
Essential Security Features for Token Smart Contracts
Implementing comprehensive security features protects token contracts from known attack vectors and establishes trust with users and investors.
Access Control Mechanisms
Proper access control ensures only authorized addresses can execute sensitive functions. Role-based permissions separate administrative capabilities from user functions, limiting potential damage from compromised accounts. Common patterns include owner-only functions, multi-signature requirements for critical operations, and timelocks on administrative changes.
Development teams should implement the principle of least privilege, granting minimal necessary permissions to each role. This approach limits attack surfaces and contains potential breaches to smaller portions of contract functionality.
Safe Mathematical Operations
Using established mathematical libraries prevents arithmetic vulnerabilities. While Solidity 0.8+ includes native overflow protection, explicit SafeMath usage documents security intentions and maintains compatibility across compiler versions. All arithmetic operations involving user-supplied values require particular attention during smart contract testing.
Pausability and Emergency Functions
Including circuit breaker patterns allows administrators to pause contract functionality during emergencies. While seemingly contradicting decentralization principles, pausability provides crucial protection when vulnerabilities are discovered post-deployment. Transparent governance around pause functionality maintains user trust while enabling emergency response.
Upgrade Patterns
Proxy patterns and upgradeable contracts balance immutability with the ability to fix issues. These patterns separate logic from storage, allowing new implementation contracts while preserving state. However, upgradeability introduces its own risks and governance requirements. Projects must carefully consider whether upgradeability benefits outweigh centralization concerns for their specific use case.
Smart Contract Testing Best Practices
Rigorous smart contract testing identifies vulnerabilities before deployment when fixes remain possible and inexpensive.
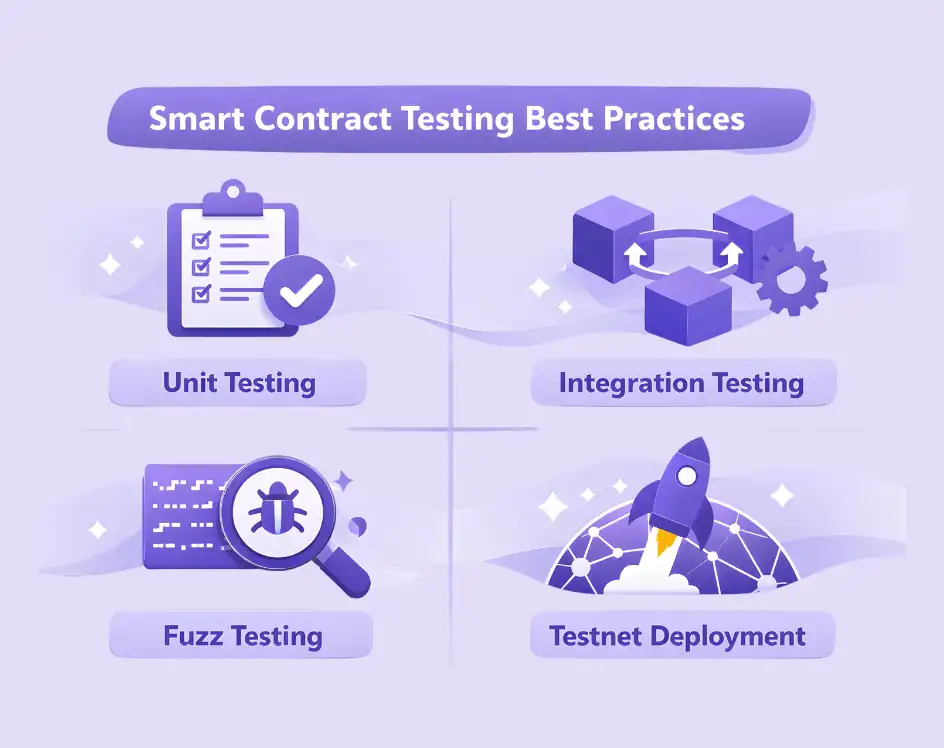
Unit Testing
Unit tests verify individual functions behave correctly under various conditions. Each function should have tests covering normal operation, edge cases, and failure scenarios. Comprehensive unit test coverage provides confidence that basic functionality works as intended and documents expected behavior for future development.
Integration Testing
Integration tests examine how contract components interact with each other and external dependencies. These tests reveal issues arising from component interactions that unit tests miss. Testing token contracts alongside their intended ecosystem integrations ensures compatibility before mainnet deployment.
Fuzz Testing
Fuzzing involves supplying random inputs to discover unexpected behaviors. Automated fuzzing tools generate thousands of test cases that human testers might overlook. This approach particularly excels at finding edge cases and overflow conditions in complex logic.
Testnet Deployment
Deploying to testnets provides real blockchain environment testing without financial risk. Testnet deployment reveals issues specific to blockchain execution that local testing environments cannot replicate. Extended testnet operation allows community testing and feedback before committing to mainnet.[3]
Smart Contract Security Audits
Smart contract audits by reputable firms provide independent security validation that internal reviews cannot match.
What Audits Cover
Professional smart contract security audit services examine code for known vulnerabilities, logic errors, gas optimization opportunities, and best practice adherence. Auditors review access controls, economic attack vectors, and integration risks. Comprehensive reports detail findings with severity ratings and remediation recommendations.
Choosing Audit Providers
Selecting reputable audit firms requires evaluating their track record, methodology transparency, and expertise with relevant blockchain platforms. Established firms have discovered vulnerabilities in major protocols and maintain research teams tracking emerging threats. Cost should not be the primary selection criterion given the potential losses from inadequate security review.
Audit Limitations
Audits provide point-in-time assessments and cannot guarantee absolute security. New attack vectors emerge continuously, and auditors may miss novel vulnerabilities. Audits should be considered one component of comprehensive security strategy rather than complete protection. Post-audit changes require additional review to maintain security assurances.
Platform-Specific Security Considerations
Different blockchain platforms present unique security considerations for token development.
Ethereum and EVM-Compatible Chains
Solidity smart contract security on Ethereum requires attention to gas optimization, reentrancy protection, and proper use of visibility modifiers. The extensive tooling ecosystem provides development frameworks, testing suites, and static analysis tools. Binance Smart Chain smart contract security follows similar patterns given its EVM compatibility, though lower gas costs may change economic attack calculations.
Solana
Solana’s Rust-based programs face different vulnerability patterns than Solidity contracts. Account validation, program-derived addresses, and cross-program invocation security require specialized knowledge. Teams planning to list token on Raydium or other Solana DEXs must address platform-specific security requirements.
Tron
Tron smart contract security shares similarities with Ethereum given its Solidity support, but platform-specific features like energy and bandwidth require consideration. Tron’s delegated proof-of-stake consensus affects certain security assumptions compared to proof-of-work or proof-of-stake systems.
Post-Deployment Security Practices
Security responsibilities extend beyond deployment through ongoing monitoring and response capabilities.
Continuous Monitoring
Monitoring contract activity detects unusual patterns potentially indicating attacks or exploitation attempts. Alert systems notify teams of large transactions, unusual function calls, or rapid state changes. Early detection enables faster response and potential damage limitation.
Bug Bounty Programs
Bug bounty programs incentivize security researchers to report vulnerabilities rather than exploit them. Offering rewards proportional to severity encourages responsible disclosure. Active bug bounty programs demonstrate security commitment and tap into broader security community expertise.[4]
Incident Response Planning
Prepared incident response plans enable rapid action when security issues arise. Plans should outline communication protocols, technical response procedures, and decision-making authorities. Regular drills ensure teams can execute plans effectively under pressure.
Building a Secure Token Smart Contract?
Professional development teams combine security best practices with extensive testing to create robust token contracts that protect user assets.
Best Practices for Secure Token Development
Following established best practices throughout the development lifecycle produces more secure token contracts.
Start with Security
Security considerations should inform design decisions from project inception rather than being added later. Threat modeling during design identifies potential attack vectors that architecture can address. Working with experienced crypto development company teams provides security expertise from the earliest development stages.
Use Established Patterns
Relying on battle-tested code libraries and design patterns reduces risk compared to custom implementations. OpenZeppelin contracts provide audited, community-reviewed implementations of common token standards and security features. Custom logic should be minimized and thoroughly reviewed.
Document Thoroughly
Comprehensive documentation aids security review by explaining intended behavior. Comments within code clarify complex logic and security assumptions. External documentation helps auditors and community reviewers understand design decisions.
Plan for the Unexpected
Building in emergency response capabilities provides options when issues arise. Whether through pausability, governance mechanisms, or upgrade paths, having response options available improves resilience. Before you launch crypto token projects, ensure adequate security infrastructure exists for post-launch challenges.
Conclusion
Smart contract token security requires comprehensive attention throughout the entire development lifecycle. From initial design through deployment and ongoing operation, security considerations must inform every decision. The immutable nature of blockchain means vulnerabilities cannot be patched after deployment, making prevention through careful development essential.
Understanding common vulnerabilities like reentrancy, overflow attacks, and front-running enables developers to implement appropriate protections. Rigorous testing, professional audits, and ongoing monitoring provide layers of defense against both known and emerging threats. Following established best practices and using battle-tested code libraries reduces risk compared to custom implementations.
For projects undertaking crypto token development, security expertise should be prioritized alongside functionality goals. The costs of proper security measures are minimal compared to potential losses from exploitation. Whether working with internal teams or external crypto token solution providers, ensuring comprehensive security protects both project assets and user trust in the broader blockchain ecosystem.
Frequently Asked Questions
A smart contract token is a cryptocurrency token managed by self-executing code on a blockchain. The smart contract defines token behavior including supply, transfers, and special functionality without requiring intermediaries.
Smart contract security is critical because deployed contracts are immutable and vulnerabilities can lead to permanent, irreversible losses. Billions have been lost to smart contract exploits throughout blockchain history.
Reentrancy attacks occur when malicious contracts repeatedly call back into vulnerable contracts before initial execution completes, potentially draining funds by exploiting intermediate states.
Smart contract audit costs vary based on complexity, typically ranging from $5,000 for simple contracts to $50,000+ for complex protocols. Costs should be weighed against potential losses from unaudited code.
Standard smart contracts cannot be modified after deployment. However, proxy patterns and upgradeable contracts allow logic updates while preserving state, though these introduce their own security considerations.
Common vulnerabilities include reentrancy attacks, integer overflow/underflow, front-running, improper access control, and timestamp dependence. Each requires specific prevention strategies during development.
Evaluate auditors based on track record, methodology transparency, platform expertise, and research contributions. Established firms with documented vulnerability discoveries provide stronger assurances.
This pattern orders operations to prevent reentrancy: first check conditions, then update state, finally interact with external contracts. This ordering ensures state changes complete before potentially dangerous external calls.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.