Key Takeaways
- DeFi development requires a comprehensive understanding of blockchain architecture, smart contract programming, and security protocols to create robust financial applications that can handle real-world transaction volumes.
- Selecting the appropriate blockchain network is crucial for DeFi success, as factors like transaction speed, gas fees, security features, and ecosystem support directly impact user experience and protocol viability.
- Smart contract security must be prioritized from the initial development phase through multiple auditing layers, as vulnerabilities can lead to significant financial losses and irreversible damage to project reputation.
- Thorough testing methodologies including unit tests, integration tests, and testnet deployments are essential to identify and resolve issues before mainnet launch, reducing the risk of costly post-deployment fixes.
- DeFi protocols must integrate seamlessly with existing ecosystem components such as wallets, oracles, and other protocols to provide users with a fluid and intuitive experience across the decentralized finance landscape.
- The development lifecycle extends beyond initial deployment, requiring continuous monitoring, regular security updates, and protocol upgrades to adapt to evolving market conditions and emerging threats.
- Gas optimization and efficient code structure are critical considerations that directly affect user costs and protocol scalability, particularly on networks with high transaction fees.
- Compliance considerations and regulatory awareness should be integrated into the development process to ensure long-term sustainability and avoid potential legal complications in various jurisdictions.
- Documentation quality and transparency throughout the development process build trust with users, investors, and auditors, establishing credibility in the competitive DeFi marketplace.
- Successful DeFi deployment requires coordination across multiple disciplines including blockchain development, security engineering, frontend design, and community management to deliver a comprehensive financial product.
Decentralized Finance has revolutionized the financial landscape by removing intermediaries and enabling trustless, transparent transactions through blockchain technology. Building a successful DeFi protocol requires more than just writing smart contracts, it demands a comprehensive understanding of blockchain architecture, security best practices, rigorous testing methodologies, and strategic deployment planning. This guide walks you through every critical phase of DeFi development, from initial requirement analysis and blockchain selection to post deployment monitoring and maintenance, ensuring you have the knowledge to build robust, secure, and scalable financial applications.
Whether you’re a blockchain developer looking to enter the DeFi space, a project manager planning your protocol’s technical roadmap, or an entrepreneur seeking to understand the development lifecycle, this comprehensive resource provides actionable insights, best practices, and real world considerations. We’ll explore critical topics including smart contract security vulnerabilities, testing strategies that catch bugs before deployment, integration patterns with existing DeFi protocols, and the importance of continuous monitoring in production environments. By following this structured approach to DeFi development, you’ll be equipped to build financial applications that users can trust with their assets.
Understanding the DeFi Development Execution Process
The DeFi execution lifecycle represents the complete journey from conceptualization to operational deployment of decentralized financial applications. This lifecycle encompasses multiple interconnected phases that demand careful planning, technical expertise, and strategic execution. Understanding this lifecycle is fundamental for developers, project managers, and stakeholders who aim to build sustainable and secure DeFi platforms.
The lifecycle begins with ideation and requirement gathering, where the core problem statement is identified and potential blockchain-based solutions are evaluated. This phase sets the foundation for all subsequent development activities and determines the technical stack, resource allocation, and timeline projections. During this stage, teams must assess market demand, competitive landscape, and regulatory considerations that might impact the project’s viability.
Following the initial planning, the lifecycle progresses through design, development, testing, and deployment phases, each with its distinct challenges and requirements. The iterative nature of DeFi development means that feedback from one phase often necessitates refinements in earlier stages, creating a dynamic development environment. Successful navigation of this lifecycle requires not only technical proficiency but also adaptability, as the blockchain ecosystem continues to evolve rapidly with new standards, tools, and best practices emerging regularly.
Requirement Analysis and DeFi Use Case Validation
Requirement analysis forms the cornerstone of successful DeFi development execution, establishing clear objectives and defining the scope of the project. This phase involves comprehensive stakeholder interviews, market research, and technical feasibility studies to ensure that the proposed solution addresses genuine market needs. Development teams must distinguish between essential features that define the minimum viable product and enhanced functionalities that can be added in subsequent iterations.
Use case validation goes beyond simple feature listing to examine the practical application of the DeFi protocol in real world scenarios. This validation process includes analyzing user workflows, identifying potential edge cases, and ensuring that the proposed solution offers tangible advantages over existing centralized or decentralized alternatives. Teams should conduct competitor analysis to understand market positioning and identify unique value propositions that differentiate their protocol from similar offerings.
The requirement analysis phase also encompasses risk assessment, where potential technical, financial, and regulatory risks are identified and mitigation strategies are developed. This includes evaluating smart contract complexity, potential attack vectors, scalability concerns, and compliance requirements across different jurisdictions. Documentation produced during this phase serves as the reference point for all development activities and helps maintain alignment between technical implementation and business objectives throughout the project lifecycle.
Critical Elements in Requirement Analysis
- Functional requirements definition with clear acceptance criteria
- Non functional requirements including performance, security, and scalability targets
- User persona development and journey mapping
- Technical constraints and blockchain specific limitations
- Regulatory compliance requirements and legal considerations
- Integration requirements with existing DeFi protocols and infrastructure
Selecting the Right Blockchain Network for DeFi Execution
Blockchain network selection represents one of the most critical decisions in DeFi development execution, as it fundamentally impacts performance, cost structure, security model, and ecosystem integration possibilities. Each blockchain network offers distinct characteristics regarding consensus mechanisms, transaction throughput, finality times, and development tooling. Ethereum remains the dominant platform for DeFi applications due to its mature ecosystem, extensive developer resources, and established security track record, despite challenges with scalability and transaction costs during network congestion.
Alternative layer 1 blockchains such as Binance Smart Chain, Solana, Avalanche, and Polygon have emerged as viable options, each offering different trade offs between decentralization, speed, and cost. Binance Smart Chain provides EVM compatibility with lower transaction fees, making it attractive for projects targeting cost sensitive users. Solana offers exceptional transaction speeds through its unique Proof of History consensus mechanism, suitable for high frequency DeFi applications. Avalanche and Polygon present hybrid solutions that balance Ethereum compatibility with enhanced performance characteristics.
| Blockchain Network | Transaction Speed | Average Gas Fees | Smart Contract Language | Ecosystem Maturity |
|---|---|---|---|---|
| Ethereum | 15-30 TPS | $5-$50+ | Solidity, Vyper | Highly Mature |
| Binance Smart Chain | 50-100 TPS | $0.10-$0.50 | Solidity | Mature |
| Solana | 2,000-3,000 TPS | $0.00025 | Rust, C, C++ | Growing |
| Polygon | 7,000+ TPS | $0.01-$0.05 | Solidity | Mature |
| Avalanche | 4,500+ TPS | $0.50-$2.00 | Solidity | Growing |
Layer-2 scaling solutions present another dimension to blockchain selection, offering enhanced throughput while maintaining security guarantees from the underlying layer-1 network. Optimistic rollups such as Arbitrum and Optimism, along with zero-knowledge rollups like zkSync and StarkNet, provide compelling options for DeFi projects seeking Ethereum security with improved performance characteristics. These solutions reduce transaction costs significantly while maintaining composability with the broader Ethereum ecosystem.
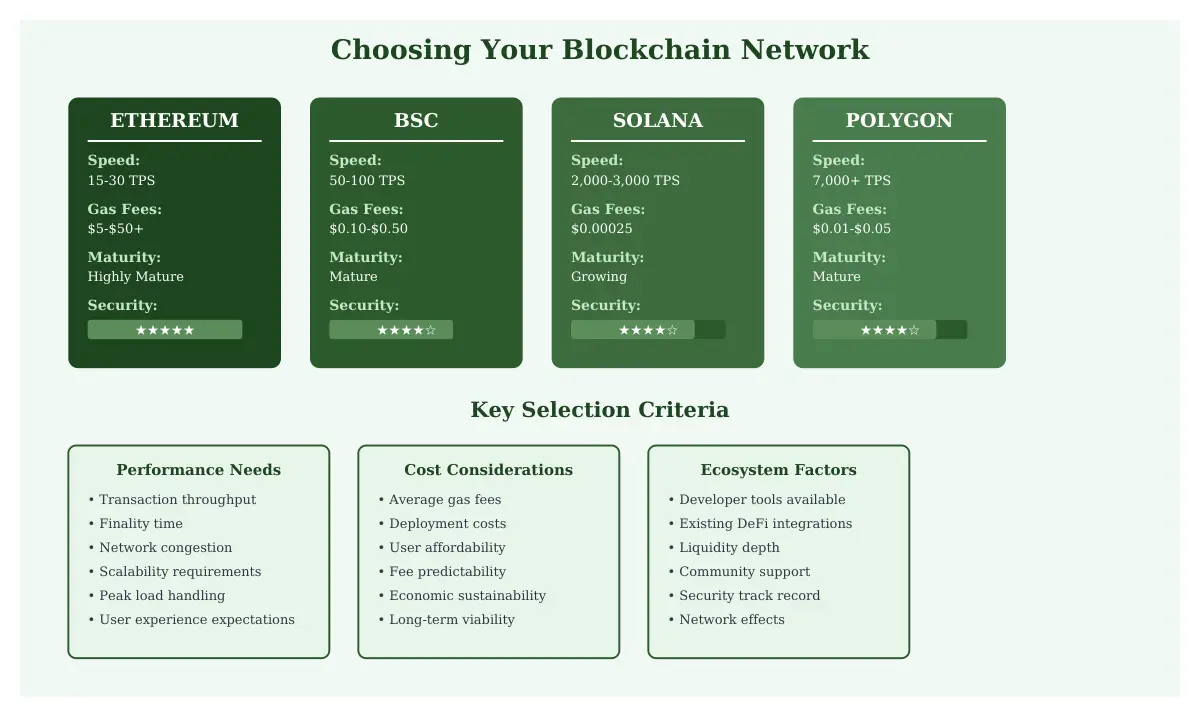
The selection process must consider factors beyond technical specifications, including developer community size, available tooling and infrastructure, liquidity availability, and strategic partnerships. Projects should evaluate the target user demographics and their blockchain preferences, as network effects and user familiarity can significantly impact adoption rates. Additionally, future proofing considerations such as planned network upgrades, cross chain interoperability initiatives, and long term sustainability models should influence the decision making process.
Designing the DeFi Protocol Architecture
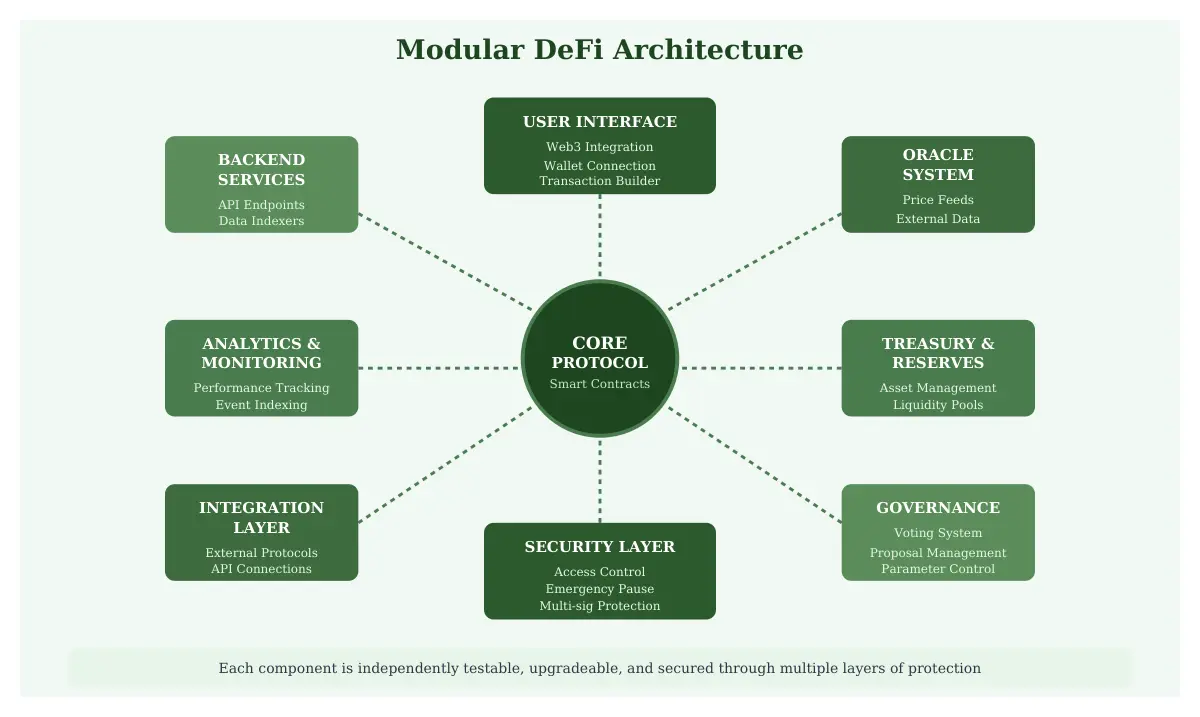
Protocol architecture design establishes the structural foundation that determines how different components interact, how data flows through the system, and how the protocol handles various operational scenarios. Effective architecture balances modularity with efficiency, creating systems that are maintainable, upgradeable, and secure. The architectural design phase requires deep consideration of smart contract interactions, state management patterns, and gas optimization strategies that will impact both user experience and operational costs.
Modern DeFi architecture typically employs a modular approach where distinct functionalities are separated into specialized contracts that communicate through well-defined interfaces. This separation of concerns enhances security by limiting the scope of individual contracts, facilitates independent testing and auditing, and enables selective upgrades without disrupting the entire system. Core protocol contracts handle fundamental operations such as asset deposits, withdrawals, and state updates, while peripheral contracts manage auxiliary functions like governance, rewards distribution, and external integrations.
Essential Architectural Components
- Core Protocol Contracts: Fundamental business logic implementation including asset management, transaction processing, and state transitions
- Access Control Layer: Permission management system defining administrative roles, user privileges, and operational authorization mechanisms
- Oracle Integration Module: External data feed connections providing real time price information and off chain data verification
- Treasury and Reserve Management: Asset custody mechanisms, liquidity pool management, and financial reserve protocols
- Governance Framework: Decentralized decision making structures enabling community driven protocol evolution and parameter adjustments
- Emergency Response System: Circuit breakers, pause mechanisms, and emergency withdrawal procedures for crisis management
Upgradeability patterns represent a crucial architectural consideration, as protocols must balance immutability benefits with the practical need for bug fixes and feature enhancements. Proxy patterns such as the transparent proxy pattern, UUPS (Universal Upgradeable Proxy Standard), and beacon proxies enable contract logic updates while preserving state and contract addresses. However, upgradeability introduces additional complexity and potential security vulnerabilities that must be carefully managed through comprehensive testing and governance mechanisms.
State management design decisions significantly impact gas costs and system performance. Architects must determine optimal data structures for storing user balances, protocol parameters, and historical records, considering trade-offs between storage costs, retrieval efficiency, and computational overhead. Techniques such as state compression, event-based data retrieval, and off-chain indexing can dramatically reduce on-chain storage requirements while maintaining necessary functionality and transparency.
Smart Contract Planning and Functional Specifications
Smart contract planning transforms architectural designs into detailed functional specifications that guide implementation efforts. This phase requires meticulous documentation of contract interfaces, function signatures, state variables, events, and modifiers that comprise the protocol’s executable logic. Specifications should include precise descriptions of input validation requirements, expected outputs, state transition rules, and error handling procedures for each function, creating a comprehensive blueprint for development teams.
Function-level specifications must address access control requirements, defining which actors can execute particular operations under what conditions. This includes establishing role-based permissions, implementing multi-signature requirements for critical operations, and creating time-lock mechanisms for sensitive protocol changes. Clear specification of these security parameters during the planning phase prevents authorization vulnerabilities and ensures consistent security policies across the protocol.
Gas optimization considerations should be integrated into the planning phase rather than addressed retroactively during implementation. Specifications should identify computational bottlenecks, evaluate alternative algorithmic approaches, and establish gas budgets for critical user-facing functions. Planning for batch operations, efficient data structure utilization, and strategic use of events versus storage can yield significant cost savings for protocol users.
| Contract Component | Primary Functions | Security Considerations | Gas Optimization Priority |
|---|---|---|---|
| Vault Contract | Deposit, Withdraw, Balance Tracking | Reentrancy protection, Access control | High |
| Lending Pool | Borrow, Repay, Liquidation | Oracle manipulation prevention, Flash loan protection | High |
| Governance Contract | Propose, Vote, Execute | Time-locks, Quorum requirements | Medium |
| Reward Distributor | Stake, Claim Rewards, Unstake | Accurate reward calculation, Fair distribution | High |
| Price Oracle | Update Price, Get Price | Data validation, Manipulation resistance | Medium |
Event emission strategies should be specified during planning to ensure comprehensive off-chain monitoring capabilities. Events serve as the primary mechanism for tracking protocol activity, enabling frontend applications to provide real-time updates and allowing analytics platforms to construct historical records. Specifications should define which state changes trigger events, what data those events should contain, and how event parameters facilitate efficient filtering and indexing.
Choosing the Appropriate Smart Contract Standards
Smart contract standards provide proven interfaces and implementation patterns that ensure interoperability, reduce development time, and leverage community-tested security practices. The most widely adopted standard in DeFi is ERC-20, which defines a common interface for fungible tokens enabling seamless integration with wallets, exchanges, and other protocols. ERC-20 compliance ensures that tokens can be easily listed on decentralized exchanges, used in lending protocols, and integrated into portfolio tracking applications without custom integration work.
Beyond basic token functionality, advanced standards like ERC-777 offer enhanced capabilities including operator mechanisms and hooks that execute custom logic during token transfers. However, these advanced features introduce additional complexity and potential attack vectors that must be carefully evaluated against project requirements. ERC-4626 has emerged as the standard for tokenized vaults, providing a unified interface for yield-bearing tokens that facilitates composability across DeFi protocols and simplifies integration for aggregators and analytical tools.
For non-fungible assets, ERC-721 and ERC-1155 standards enable representation of unique items and semi-fungible tokens respectively. These standards find application in DeFi contexts such as NFT-backed loans, fractional ownership protocols, and position tokens that represent specific yield farming stakes or liquidity provision positions. Selection of appropriate standards must balance standardization benefits against specific protocol requirements, as overly restrictive adherence to standards might limit innovative functionality.
Governance-related standards such as ERC-2612 (permit functionality) and ERC-5805 (voting delegation) enhance user experience by enabling gasless approvals and flexible voting mechanisms. These standards reduce friction in governance participation and transaction execution, contributing to higher engagement rates and improved protocol decentralization. Standards for access control (such as OpenZeppelin’s AccessControl) and upgradeability (EIP-1967 proxy patterns) provide battle-tested implementations of critical security mechanisms.
Smart Contract Development and Coding Practices
Smart contract development demands exceptional attention to detail, security awareness, and gas efficiency, as deployed contracts operate in an immutable environment where bugs can result in irreversible financial losses. Development practices should emphasize code clarity, comprehensive documentation, and adherence to established security patterns. Solidity development for EVM-compatible chains dominates the DeFi landscape, though alternative languages like Vyper offer enhanced security through deliberate simplification and Rust serves as the primary language for Solana development.
Security-focused coding practices form the foundation of responsible digital contract development. This includes consistent use of the checks-effects-interactions pattern to prevent reentrancy attacks, proper access control implementation through modifiers and role-based permissions, and careful handling of external calls that might fail or consume excessive gas. Developers must avoid common pitfalls such as unchecked external calls, integer overflow/underflow vulnerabilities (mitigated in Solidity 0.8+ through automatic checks), and timestamp dependence for critical logic.
Essential Development Best Practices
Code Organization: Maintain clear separation between core logic, helper functions, and administrative operations. Use inheritance appropriately to promote code reuse while avoiding excessive complexity that hampers auditability.
Input Validation: Implement rigorous validation for all external inputs, including range checks for numerical parameters, address validation to prevent zero-address interactions, and sanity checks for economic parameters that might destabilize the protocol.
Error Handling: Use custom errors (introduced in Solidity 0.8.4) for gas-efficient error reporting, provide descriptive error messages that facilitate debugging, and ensure all failure modes are explicitly handled rather than relying on implicit behavior.
Gas Optimization: Employ storage packing to minimize storage slots, use events rather than storage for historical data when appropriate, leverage immutable and constant variables where possible, and batch operations to amortize fixed costs.
Documentation Standards: Follow NatSpec documentation format for all public and external functions, maintain comprehensive inline comments explaining complex logic, and document all assumptions and invariants that the code relies upon.
Version control practices and collaborative development workflows contribute significantly to code quality and project maintainability. Development teams should implement comprehensive code review processes where multiple developers examine changes before integration, use automated linting and formatting tools to maintain consistency, and establish clear branching strategies that separate feature development from stable releases. Continuous integration pipelines should automatically execute test suites and security analysis tools on every code change.
Library utilization accelerates development while leveraging community-vetted code. OpenZeppelin Contracts provides extensively audited implementations of common patterns including token standards, access control, security utilities, and upgradeability mechanisms. However, developers must understand the implications of imported libraries, including their gas costs, potential security considerations, and version compatibility, rather than blindly incorporating external code into critical financial applications.
Integrating DeFi Protocols and External APIs
Protocol integration enables DeFi applications to leverage existing infrastructure, tap into established liquidity pools, and provide users with comprehensive financial services through composable building blocks. Integration patterns vary from simple token swaps through DEX aggregators to complex multi-protocol strategies that optimize yield across various platforms. Successful integration requires deep understanding of target protocol interfaces, their economic mechanisms, and potential failure modes that might impact the integrating application.
Oracle integration represents one of the most critical external dependencies for DeFi protocols, as accurate price data underpins lending protocols, derivatives platforms, and algorithmic stablecoins. Chainlink[1] dominates the oracle landscape with its decentralized network of data providers, though alternatives like Band Protocol, API3, and Pyth Network offer different trust assumptions and latency characteristics. Oracle integration must implement safeguards against manipulation, stale data, and extreme price movements through mechanisms like time-weighted average prices, multiple oracle sources, and circuit breakers triggered by volatility thresholds.
DEX integration allows protocols to execute token swaps, provide liquidity, and access deep liquidity pools without building exchange functionality from scratch. Uniswap, SushiSwap, and Curve represent major integration targets, each with distinct interfaces and optimization characteristics. Integration strategies should consider factors like slippage protection, deadline parameters, and optimal routing paths to ensure users receive favorable execution prices while protecting against front-running attacks.
| Integration Type | Key Protocols | Primary Use Cases | Risk Considerations |
|---|---|---|---|
| Price Oracles | Chainlink, Band, Pyth | Lending collateral, Derivatives pricing | Data manipulation, Network failures |
| DEX Protocols | Uniswap, Curve, 1inch | Token swaps, Liquidity provision | Slippage, Front-running |
| Lending Protocols | Aave, Compound, MakerDAO | Yield optimization, Leverage | Liquidation risks, Rate volatility |
| Bridge Protocols | Wormhole, LayerZero, Axelar | Cross-chain transfers, Asset bridging | Bridge exploits, Transaction finality |
| Stablecoin Protocols | USDC, DAI, USDT | Value stability, Payment processing | De-pegging events, Regulatory risks |
Cross-chain integration through bridge protocols extends DeFi applications beyond single-chain limitations, enabling multi-chain strategies and broader user accessibility. However, bridge integration introduces additional complexity and security considerations, as bridge exploits have resulted in some of the largest losses in DeFi history. Integration strategies should implement defensive programming practices including thorough validation of cross-chain messages, understanding bridge security models, and potentially limiting exposure to bridge protocols through transaction caps.
Wallet Integration and Transaction Flow Execution
Wallet integration forms the primary interface between users and DeFi protocols, enabling transaction signing, balance queries, and network interactions. Modern web3 applications support multiple wallet types including browser extensions like MetaMask, mobile wallets such as Trust Wallet and Rainbow, hardware wallets like Ledger and Trezor, and smart contract wallets including Gnosis Safe and Argent. Integration libraries such as Web3.js, Ethers.js, and Wagmi abstract wallet connectivity complexities while providing consistent interfaces across different wallet implementations.
Transaction flow design significantly impacts user experience and protocol security. Well-designed flows provide clear feedback at each stage, estimate gas costs accurately before submission, and handle various failure scenarios gracefully. Applications should implement transaction simulation capabilities that predict outcomes before committing changes to the blockchain, helping users avoid costly mistakes and providing confidence in complex multi-step operations.
Multi-step transaction flows, common in DeFi operations, require careful UX consideration to maintain user engagement while ensuring security. Operations like depositing into a yield aggregator might require token approval followed by the actual deposit transaction. Modern approaches using ERC-2612 permit functionality enable gasless approvals through off-chain signatures, reducing the number of on-chain transactions and improving user experience. However, implementations must balance convenience with security, ensuring users understand what they’re signing and maintaining appropriate safeguards.
Error handling and transaction failure management distinguish professional DeFi applications from amateur implementations. Applications should monitor pending transactions, detect failures, provide actionable error messages rather than cryptic revert codes, and offer recovery options when appropriate. Transaction history tracking, including failed transactions, helps users understand their interaction history and troubleshoot issues. Gas price management features that suggest appropriate gas settings based on network conditions or allow users to adjust gas parameters enhance reliability during network congestion.
Security-First Development Approach in DeFi
Security-first development philosophy recognizes that decentralized finance applications handle valuable assets in adversarial environments where attackers actively search for vulnerabilities. This approach integrates security considerations into every development phase rather than treating security as an afterthought addressed through late-stage auditing. Development teams must cultivate security awareness, understand common attack vectors, and implement defensive programming practices that minimize vulnerability surface area.
The reentrancy attack represents one of the most notorious vulnerabilities in smart contract history, exemplified by the 2016 DAO hack that resulted in a contentious Ethereum hard fork. Reentrancy occurs when external contract calls allow attackers to re-enter calling functions before state updates complete, potentially draining funds through recursive execution. Prevention strategies include the checks-effects-interactions pattern, reentrancy guards that prevent recursive calls, and using transfer methods that limit gas forwarding to external contracts.
Critical Security Considerations
- Access Control Vulnerabilities: Improperly configured permissions allowing unauthorized users to execute privileged functions, including ownership transfer functions without proper safeguards
- Oracle Manipulation: Attackers exploiting price oracle weaknesses to manipulate collateral valuations, trigger inappropriate liquidations, or extract value through arbitrage
- Front-Running Attacks: Transaction ordering manipulation where attackers observe pending transactions and submit competing transactions with higher gas prices to profit at others’ expense
- Flash Loan Attacks: Exploiting uncollateralized borrowing to manipulate protocol states, drain reserves, or profit from protocol logic vulnerabilities within single transactions
- Integer Overflow/Underflow: Arithmetic operations exceeding variable limits resulting in unexpected values, though mitigated in recent Solidity versions through automatic checks
- Denial of Service: Resource exhaustion attacks, block gas limit exploitation, or logic bombs that render protocols inoperable under specific conditions
Economic security considerations extend beyond code vulnerabilities to protocol mechanism design. Incentive structures must be analyzed for potential exploitation vectors where rational economic actors might profit from actions harmful to the protocol. This includes examining governance token distribution for plutocracy risks, analyzing liquidity mining programs for mercenary capital problems, and stress-testing collateralization requirements under extreme market conditions.
Time-dependent vulnerabilities arise when contracts rely on block timestamps or block numbers for critical logic. Miners possess limited ability to manipulate block timestamps, creating opportunities for exploitation in time-sensitive operations like option expiration or auction endings. Protocols should use time values primarily for coarse-grained operations with tolerance for minor variations rather than precise timing-critical logic where manipulation could be profitable.
Smart Contract Testing and Automated Test Execution
Comprehensive testing strategies form the backbone of reliable smart contract deployment, catching bugs and vulnerabilities before they reach production environments. Testing methodologies should encompass unit tests for individual function validation, integration tests for multi-contract interactions, and end-to-end tests simulating complete user workflows. Test coverage metrics, while not guaranteeing security, provide quantitative indicators of testing thoroughness and identify untested code paths that might harbor vulnerabilities.
Unit testing frameworks such as Hardhat, Truffle, and Foundry provide development environments for writing and executing smart contract tests. Tests should verify not only happy-path scenarios where functions behave as intended but also edge cases, boundary conditions, and failure modes. Negative testing that verifies proper handling of invalid inputs, unauthorized access attempts, and unexpected state transitions proves equally important to positive testing of intended functionality.
Fuzz testing introduces randomized inputs to discover unexpected behavior that manual test cases might miss. Property-based testing frameworks like Echidna and Foundry’s fuzzing capabilities automatically generate diverse input combinations, searching for invariant violations or unexpected state transitions. This automated exploration proves particularly valuable for complex protocols with large state spaces where exhaustive manual testing becomes impractical.
| Testing Methodology | Purpose | Tools | Coverage Target |
|---|---|---|---|
| Unit Testing | Individual function validation | Hardhat, Foundry, Truffle | 95%+ code coverage |
| Integration Testing | Multi-contract interactions | Hardhat, Foundry | All integration points |
| Fuzz Testing | Random input exploration | Echidna, Foundry | Invariant verification |
| Fork Testing | Mainnet state simulation | Hardhat, Tenderly | Production scenarios |
| Gas Profiling | Cost optimization analysis | Hardhat Gas Reporter | All user functions |
Fork testing enables validation against real mainnet state, allowing developers to test integration with existing protocols using actual contract addresses and live data. This approach catches integration issues that might not surface in isolated test environments, such as unexpected protocol behavior, changed contract states, or deprecated interfaces. Fork testing proves particularly valuable when protocols depend on external DeFi primitives whose behavior might differ from simplified test implementations.
Continuous integration pipelines automate test execution on every code change, ensuring that new features don’t introduce regressions or break existing functionality. Automated testing workflows should include static analysis tools like Slither and Mythril that identify potential vulnerabilities through code pattern matching, gas consumption analysis to detect efficiency regressions, and automated coverage reporting to maintain testing standards. Integration with version control systems enables automated testing on pull requests, preventing untested code from merging into main branches.
Auditing and Vulnerability Assessment Process
Professional security auditing represents a critical milestone before mainnet deployment, providing independent expert review of smart contract code, architecture, and economic mechanisms. Auditing firms employ specialized security researchers who systematically analyze code for vulnerabilities, review architectural decisions, and assess protocol mechanisms for potential exploitation vectors. Multiple audit rounds from different firms provide defense-in-depth, as different auditors bring varied perspectives and may identify distinct vulnerability classes.
The auditing process typically begins with protocol documentation review where auditors familiarize themselves with intended functionality, security assumptions, and trust models. This contextual understanding allows auditors to evaluate whether implementation matches specifications and identify logic flaws that might not constitute technical vulnerabilities but could enable economic exploitation. Auditors examine both individual contract security and system-level interactions, looking for vulnerabilities that emerge from component composition rather than isolated contracts.
Leading audit firms include Trail of Bits, ConsenSys Diligence, OpenZeppelin Security, Certora, and Chain Security, each with proven track records in identifying critical vulnerabilities. Audit reports detail discovered issues categorized by severity, provide exploitation scenarios, and recommend remediation strategies. Critical issues demand immediate resolution before deployment, while lower-severity findings might be addressed in subsequent updates. However, audit completion doesn’t guarantee absolute security, as audits examine code at specific points in time and cannot predict all possible attack vectors.
Bug bounty programs complement formal audits by incentivizing ongoing security research from the broader community. Platforms like Immunefi and Code4rena facilitate bug bounty programs where security researchers earn rewards for responsibly disclosing vulnerabilities. Bounty programs should establish clear scope definitions, payout structures correlated with vulnerability severity, and transparent disclosure processes. Continuous bug bounty programs recognize that security represents an ongoing process rather than one-time audit completion.
Formal verification provides mathematical proof of contract correctness for critical components, though practical limitations currently restrict formal verification to relatively simple contracts or specific properties. Tools like Certora Prover and K Framework enable specification of formal properties that contracts must maintain, with automated verification checking that no execution path violates these invariants. While formal verification cannot replace comprehensive testing and auditing, it provides additional confidence for high-value or security-critical contract components.
Frontend and Backend Development Execution
Frontend development transforms smart contracts into accessible user interfaces that enable non-technical users to interact with DeFi protocols. Modern DeFi frontends employ React, Next.js, or Vue.js frameworks combined with Web3 integration libraries to create responsive, performant applications. User interface design must balance feature richness with simplicity, presenting complex financial operations in intuitive workflows that guide users through multi-step processes while clearly communicating risks and expected outcomes.
State management in DeFi applications handles blockchain connection status, account information, transaction states, and protocol data updates. Libraries like Redux, Zustand, or React Context manage application state, while Web3 integration libraries maintain blockchain connection state and synchronize on-chain data. Real-time updates through WebSocket connections or periodic polling ensure users see current balances, transaction confirmations, and protocol state changes without manual refreshing.
Backend infrastructure, though DeFi protocols primarily execute on-chain, supports frontend functionality through indexing services, caching layers, and analytical computations. The Graph Protocol enables efficient querying of blockchain data through GraphQL endpoints, providing historical data access without expensive on-chain queries. Custom indexers using tools like Ethers.js or Web3.py process blockchain events and maintain databases of protocol activity, enabling features like transaction history, portfolio analytics, and performance tracking.
Essential Frontend Components
- Wallet Connection Interface: Multi-wallet support, network switching, account display, and disconnect functionality
- Transaction Builder: User input forms, transaction preview, gas estimation, slippage configuration, and confirmation dialogs
- Dashboard and Analytics: Portfolio overview, position tracking, historical performance, and real-time protocol statistics
- Transaction History: Pending transaction monitoring, confirmed transaction display, and failure diagnostics
- Risk Indicators: Health factors, liquidation thresholds, impermanent loss estimates, and exposure breakdowns
- Documentation Access: Integrated help content, FAQ sections, tutorial guides, and external documentation links
Performance optimization ensures responsive user experiences despite blockchain latency and potentially slow RPC endpoints. Strategies include optimistic UI updates that immediately reflect expected state changes pending transaction confirmation, aggressive caching of blockchain data that changes infrequently, lazy loading of non-critical components, and code splitting to reduce initial bundle sizes. Progressive Web App capabilities enable offline functionality for certain features and improve perceived performance through app-like experiences.
Security considerations extend to frontend applications despite smart contracts handling critical financial logic. Frontend applications must validate user inputs before constructing transactions, implement content security policies preventing XSS attacks, use secure communication channels for all API interactions, and avoid exposing sensitive information through client-side code or error messages. Supply chain security through dependency auditing and lock file management prevents compromise through malicious package updates.
Deployment Strategy for DeFi Smart Contracts
Deployment strategy orchestrates the transition from development to production, requiring careful planning of contract initialization, dependency management, and configuration. Deployment scripts automate contract deployment sequences, ensure proper initialization, and verify deployment success. Tools like Hardhat Deploy and Foundry Scripts provide reproducible deployment workflows that maintain consistency across different networks and deployment contexts.
Multi-stage deployment through testnet validation precedes mainnet launch, allowing teams to validate functionality in production-like environments without risking real assets. Testnets such as Goerli, Sepolia, or Mumbai mirror mainnet architecture while providing free test tokens for experimentation. Testnet deployment should replicate mainnet procedures exactly, including contract verification, oracle integration, and frontend connectivity, to identify deployment issues before mainnet execution.
Contract verification through block explorers like Etherscan publishes source code and enables public scrutiny, building trust and transparency. Verification proves that deployed bytecode matches published source code, allowing users and auditors to review contract logic. Automated verification through deployment scripts ensures that verification occurs immediately after deployment, maintaining the connection between deployed contracts and their source code.
Deployment Checklist
- Complete audit remediation and obtain final audit reports
- Execute comprehensive testnet deployment validating all functionality
- Configure deployment scripts with production parameters
- Prepare contract initialization data and access control settings
- Verify sufficient ETH balances for deployment gas costs
- Execute deployment with appropriate gas price settings
- Verify all deployed contracts on block explorer
- Test protocol functionality through frontend interface
- Configure monitoring and alert systems
- Prepare communication materials and launch announcements
Gradual rollout strategies mitigate risks through controlled exposure increase. Initial launch might limit deposit caps, restrict functionality to whitelisted users, or implement conservative risk parameters that gradually relax as protocol operation demonstrates stability. Time-locked parameter adjustments through governance mechanisms prevent immediate changes to critical settings, providing community oversight and preventing rapid configuration changes that might compromise security.
Post-deployment configuration includes setting up multisig administrative controls, transferring ownership from deployer addresses to governance structures, configuring oracle feeds with production parameters, and establishing emergency response procedures. Documentation of deployed contract addresses, initialization parameters, and administrative key locations ensures that operational teams can effectively manage the protocol and respond to incidents.
Mainnet Launch and Post-Deployment Validation
Mainnet launch represents the culmination of development efforts, introducing the protocol to real users and real value. Launch preparation includes final security reviews, operational readiness assessments, and communication strategy development. Teams should establish 24/7 monitoring during the initial launch period, maintain rapid response capabilities for potential issues, and prepare contingency plans for various failure scenarios.
Post-deployment validation confirms that deployed contracts function as intended in the production environment. This includes executing test transactions covering major user flows, verifying correct event emission and off-chain indexing, confirming frontend-contract integration, and validating oracle feed accuracy. Smoke testing through small-value transactions before announcing broader availability allows teams to identify deployment issues with minimal user impact.
Transaction monitoring during the launch phase tracks protocol usage patterns, identifies unusual activity that might indicate exploitation attempts, and validates that economic mechanisms function as designed. Automated monitoring systems should alert on anomalies such as unexpectedly large transactions, rapid balance changes, unusual gas consumption patterns, or failed transaction clusters that might indicate emerging issues.
Community engagement during launch builds user confidence and provides feedback channels for issue reporting. Clear communication about protocol capabilities, risk factors, and known limitations helps users make informed decisions. Establishing support channels through Discord, Telegram, or dedicated support systems enables users to report issues and receive assistance, creating feedback loops that identify problems and guide product improvements.
Performance metrics collection during the launch period establishes baselines for protocol health monitoring. Key metrics include total value locked, transaction volumes, unique user counts, gas consumption patterns, and error rates. Establishing normal operating parameters allows teams to detect deviations that might indicate problems or exploitation attempts, enabling proactive response before issues escalate.
Continuous Monitoring, Upgrades, and Maintenance
Continuous monitoring ensures ongoing protocol health through automated systems that track contract state, transaction patterns, and ecosystem interactions. Monitoring infrastructure should include real-time dashboards displaying critical metrics, automated alerting for anomalous conditions, and comprehensive logging of all protocol interactions. Services like Tenderly, Defender, and custom monitoring solutions built with tools like Prometheus and Grafana provide visibility into protocol operations.
Security monitoring specifically focuses on detecting potential exploits, unusual transaction patterns, or emerging vulnerabilities. This includes tracking large withdrawals, monitoring for oracle manipulation attempts, detecting unusual access control usage, and identifying patterns consistent with known attack vectors. Integration with blockchain security services provides early warning of potential threats and enables rapid response to emerging vulnerabilities.
Protocol upgrades introduce new features, fix bugs, and adapt to evolving ecosystem conditions. Upgrade procedures for protocols implementing upgradeability patterns must follow rigorous processes including upgrade proposal creation, community review periods, testing on staging environments, and gradual rollout strategies. Even for immutable protocols, “upgrades” might involve deploying new contract versions and migrating liquidity, requiring coordination with users and integrated protocols.
| Monitoring Category | Key Metrics | Alert Thresholds | Response Priority |
|---|---|---|---|
| Security Events | Large withdrawals, Admin actions | Immediate | Critical |
| Financial Health | TVL changes, Utilization rates | 30% deviation | High |
| Technical Performance | Transaction success rate, Gas usage | 20% increase | Medium |
| Oracle Reliability | Price feed updates, Data freshness | Missed updates | Critical |
| User Activity | Active users, Transaction volume | 50% decrease | Medium |
Incident response procedures establish clear protocols for handling security events, system failures, or unexpected protocol behavior. Response plans should define severity classifications, escalation procedures, communication templates, and decision-making authority. Incident response drills help teams practice coordinated responses, identify procedural gaps, and build muscle memory for high-stress situations where rapid, coordinated action proves essential.
Long-term maintenance encompasses regular security reviews as the threat landscape evolves, dependency updates as underlying infrastructure improves, and adaptation to regulatory developments that might impact protocol operations. Maintaining active development and security teams beyond initial launch ensures protocols can address emerging challenges and maintain competitiveness in the rapidly evolving DeFi ecosystem.
From DeFi Development to Secure Deployment
Explore our structured DeFi development workflow, from smart contract execution to production-ready deployment.
With over 8 years of specialized experience in blockchain and DeFi protocol engineering, Nadcab Labs has established itself as a leading authority in the decentralized finance space. Our team of expert blockchain developers, security engineers, and DeFi architects has successfully delivered numerous high-value DeFi projects across multiple blockchain networks, demonstrating deep technical expertise and a comprehensive understanding of the DeFi ecosystem.
Our expertise encompasses the entire DeFi development lifecycle from initial requirement analysis and architecture design through smart contract development, rigorous security testing, and production deployment. We specialize in building lending protocols, decentralized exchanges, yield aggregators, liquidity mining platforms, and algorithmic stablecoins, bringing proven methodologies and best practices honed through years of real-world implementation experience.
Security forms the cornerstone of our development philosophy. Our protocols undergo multiple internal security reviews throughout development, comprehensive testing including fuzz testing and formal verification where appropriate, and coordination with leading audit firms for independent security assessment. We maintain ongoing relationships with bug bounty platforms and security researchers, ensuring continuous security vigilance even after deployment.
Nadcab Labs brings authoritative knowledge of smart contract standards, integration patterns, and gas optimization techniques that deliver superior user experiences. Our development practices emphasize code quality, comprehensive documentation, and transparent communication, building protocols that inspire confidence among users, investors, and ecosystem participants.
Whether you’re launching a novel DeFi primitive, building a multi-protocol yield strategy, or creating cross-chain financial infrastructure, Nadcab Labs provides the technical expertise, security focus, and execution capability to bring your vision to reality. Our track record of successful deployments and satisfied clients demonstrates our commitment to excellence in DeFi development.
FAQs: DeFi Development Process
The timeline for DeFi development varies significantly based on protocol complexity, feature scope, and team experience. A relatively simple DeFi application like a basic staking protocol might require 3-4 months from initial design to mainnet deployment, including development, testing, and auditing. More complex protocols such as lending platforms, decentralized exchanges with automated market makers, or multi-asset yield aggregators typically require 6-12 months for comprehensive development. This timeline includes architecture design and specification, smart contract development, extensive testing phases, multiple security audits, testnet deployment and validation, and careful mainnet launch procedures. Additional time should be allocated for post-launch monitoring and potential issue resolution during the critical initial operating period.
DeFi development costs vary dramatically based on protocol complexity, team composition, and security requirements. Development costs for a competent blockchain development team typically range from $150,000 to $500,000 for moderately complex protocols, with more sophisticated platforms potentially exceeding $1,000,000. Security audit costs from reputable firms range from $50,000 to $300,000 depending on code complexity and audit depth, with many projects commissioning multiple audits for enhanced security assurance. Additional costs include infrastructure expenses for node access, monitoring services, and frontend hosting, bug bounty program funding for ongoing security research, legal consultation for regulatory compliance assessment, and marketing expenses for user acquisition and community building. Deployment gas costs vary by network but can range from a few hundred dollars on layer-2 networks to tens of thousands of dollars on Ethereum mainnet during high congestion periods.
Solidity remains the dominant programming language for DeFi development on EVM compatible blockchains including Ethereum, Binance Smart Chain, Polygon, and Avalanche. Vyper serves as an alternative EVM language emphasizing security through simplicity and reduced feature complexity. For Solana development, Rust combined with the Anchor framework represents the standard approach. Beyond programming language proficiency, DeFi developers require deep understanding of blockchain fundamentals including consensus mechanisms, transaction lifecycle, and gas economics. Smart contract security knowledge proves essential, encompassing common vulnerability patterns, attack vectors, and defensive programming techniques. Financial protocol understanding including lending mechanics, automated market maker mathematics, and tokenomics design enables creation of economically sound protocols. Development tooling proficiency with frameworks like Hardhat, Foundry, or Truffle, testing methodologies, and deployment procedures rounds out essential technical skills for successful DeFi development.
Smart contracts themselves are immutable once deployed to blockchain networks, meaning their code cannot be directly modified. However, developers can implement upgradeability patterns that enable controlled modifications while maintaining the same contract address from user perspectives. Proxy patterns including transparent proxies, UUPS proxies, and beacon proxies separate contract logic from data storage, allowing logic updates while preserving state and contract interfaces. Upgradeability introduces trade-offs between flexibility and security, as upgrade mechanisms create potential attack vectors if improperly secured. Many protocols implement governance-controlled upgrades requiring community approval through token voting, time-locked upgrade procedures providing review periods before implementation, and multi-signature authorization requiring multiple administrators to approve changes. Some projects deliberately choose immutability for maximum trust minimization, accepting that bug fixes would require deploying new contract versions and migrating user funds, prioritizing security through unchangeable code over operational flexibility.
Reentrancy attacks where malicious contracts exploit callback functions to recursively execute state-changing operations remain among the most dangerous vulnerabilities, demonstrated by historical exploits including the DAO hack. Oracle manipulation attacks exploit price feed vulnerabilities to manipulate collateral valuations or trigger profitable liquidations. Flash loan attacks leverage uncollateralized borrowing to manipulate protocol states within single transactions, exploiting complex interactions between DeFi protocols. Access control failures where unauthorized users execute privileged functions can compromise entire protocols. Integer overflow and underflow vulnerabilities, though largely mitigated in recent Solidity versions through automatic checks, remain concerns in older contracts or alternative languages. Front-running attacks exploit transaction ordering to extract value from pending user transactions. Logic errors in complex financial calculations can lead to incorrect interest accrual, reward distribution, or collateral evaluation. Timestamp manipulation where miners influence block timestamps can affect time dependent protocol operations. Each vulnerability class requires specific defensive programming techniques, comprehensive testing, and multiple layers of security review.
Interoperability within single blockchain ecosystems relies on standardized interfaces allowing contracts to interact seamlessly through function calls and shared token standards. Protocols implement standard interfaces like ERC-20 for fungible tokens, ERC-721 for NFTs, and specialized standards like ERC-4626 for yield-bearing vaults, enabling automatic compatibility with ecosystem tools and protocols. Cross-chain interoperability proves more complex, typically implemented through bridge protocols that lock assets on source chains and mint representative tokens on destination chains. Bridge architectures include hash time-locked contracts for atomic swaps, validator networks that attest to cross-chain events, and optimistic bridges that assume transaction validity unless challenged. Cross-chain messaging protocols like LayerZero, Axelar, and Wormhole enable arbitrary data and value transfer between different blockchain networks. However, bridges introduce security assumptions and potential vulnerabilities, with bridge exploits representing some of the largest DeFi losses. Projects must carefully evaluate bridge security models and implement defensive measures including transaction limits, multi-signature controls, and potentially insurance coverage.
Storage optimization represents the most impactful gas reduction technique, as storage operations consume substantially more gas than memory or stack operations. Packing multiple variables into single storage slots through appropriate data type sizing reduces storage costs dramatically. Using events rather than storage for historical data that doesn’t require on-chain queries eliminates unnecessary storage writes. Immutable and constant variables cost zero gas to read after deployment compared to storage variables. Batch operations that process multiple user actions in single transactions amortize fixed costs across multiple operations. Short-circuiting logic with require statements early in functions prevents unnecessary computation for invalid inputs. Using custom errors instead of string revert messages reduces deployment costs and runtime gas consumption. Optimizing loop structures to minimize storage reads within iterations, implementing efficient data structures like mappings instead of arrays for lookups, and leveraging bit manipulation for compact data representation all contribute to meaningful gas reductions. However, gas optimization must balance with code clarity and security, as overly optimized code might introduce vulnerabilities or maintenance challenges.
Governance mechanisms enable decentralized decision-making about protocol parameters, upgrades, treasury management, and strategic direction, transitioning control from founding teams to token holder communities. Effective governance systems balance accessibility with security, allowing community participation while preventing malicious proposals or hasty decisions. Token-based voting remains the dominant governance model where voting power correlates with token holdings, though this creates plutocracy risks where large holders dominate decisions. Delegation mechanisms allow token holders to delegate voting power to active participants or specialized experts, improving participation rates and decision quality. Time-locked execution requires delays between proposal approval and implementation, providing review periods and enabling community exits if disagreeable changes pass. Quorum requirements ensure sufficient participation before proposals execute, preventing small minorities from enacting major changes. Governance should control sensitive parameters including protocol fees, interest rate models, collateralization ratios, and treasury fund allocation, while critical security features might remain outside governance control to prevent attack vectors. Emergency response mechanisms might enable rapid parameter adjustments during crises, balanced against governance principles through subsequent community ratification.
Oracle reliability represents a critical dependency for DeFi protocols as inaccurate price data can trigger inappropriate liquidations, enable manipulation attacks, or cause protocol insolvency. Multi-oracle architectures that aggregate data from multiple independent sources reduce single points of failure and manipulation risks. Chainlink’s decentralized oracle networks aggregate data from numerous node operators, while alternatives like Band Protocol and Pyth Network offer different decentralization and latency characteristics. Time-weighted average prices smooth out short-term volatility and manipulation attempts by considering historical price data rather than spot prices vulnerable to flash loan manipulation. Deviation thresholds trigger oracle updates only when prices move significantly, balancing data freshness with update costs. Circuit breakers automatically pause protocol operations if oracle prices deviate dramatically from expected ranges or historical patterns. Backup oracle configurations enable automatic failover if primary data sources become unavailable. Protocols should implement heartbeat mechanisms ensuring regular oracle updates even during stable price periods, preventing stale data from affecting critical operations. Understanding oracle trust assumptions, update frequencies, and failure modes enables appropriate defensive measures protecting protocols against oracle-related vulnerabilities.
Regulatory frameworks for DeFi remain evolving across global jurisdictions, creating compliance uncertainty for protocol developers. Securities law considerations arise when tokens exhibit investment contract characteristics, potentially requiring registration or exemptions. Know Your Customer and Anti-Money Laundering requirements might apply depending on protocol function, geographic operation, and degree of decentralization, though fully decentralized protocols face implementation challenges for traditional compliance mechanisms. Some jurisdictions classify certain DeFi activities as money transmission requiring specific licenses. Tax reporting obligations might require protocols to issue tax forms or provide transaction data to users and authorities. Geographic restrictions might prohibit access from specific jurisdictions with restrictive cryptocurrency regulations. Developer teams should consult legal specialists familiar with blockchain regulations, implement geographic restrictions if necessary through frontend interfaces, consider decentralized governance structures that limit centralized control, and maintain comprehensive documentation demonstrating legitimate protocol purposes. While complete regulatory certainty remains elusive, proactive legal consultation and thoughtful protocol design can mitigate regulatory risks while advancing DeFi’s decentralization mission.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







