Key Takeaways
- Byzantine Fault Tolerance is the ability of a distributed system to function correctly even when some nodes act maliciously or fail, making it a pillar of blockchain technology security.
- The Byzantine Generals Problem is a theoretical framework that illustrates the challenge of achieving consensus among untrusted participants in distributed systems.
- Practical Byzantine Fault Tolerance (PBFT) uses a three-phase message protocol (pre-prepare, prepare, commit) to achieve agreement across validators in a structured and verifiable way.
- BFT-based consensus algorithms offer faster finality and greater energy efficiency compared to Proof of Work, making them attractive for enterprise and Web3 infrastructure projects.
- BFT systems can tolerate up to one-third of nodes being faulty or malicious without compromising network integrity, a critical threshold in cryptocurrency fundamentals.
- Real-world blockchains like Cosmos (Tendermint), Hyperledger Fabric, and Zilliqa rely on BFT-based protocols to secure their networks.
- The scalability of BFT is its main limitation, with communication overhead increasing as the validator set grows, prompting ongoing research into advanced algorithms.
- BFT plays a growing role in Layer 2 solutions and next-generation Web3 infrastructure, helping bridge the gap between decentralization and performance.
What is Byzantine Fault Tolerance (BFT)?
At its core, Byzantine Fault Tolerance is a property of a system that allows it to continue operating correctly even when some of its components fail in arbitrary or unpredictable ways. Unlike simple crash failures where a node just stops responding, Byzantine failures can involve nodes sending contradictory information, lying to other participants, or behaving in intentionally destructive patterns. In the world of blockchain technology, this concept is not just academic theory. It is the foundation upon which trustless, decentralized networks are built.
Think of it this way: when you send a transaction on a blockchain, there is no central bank verifying it. Instead, a network of independent validators must agree that the transaction is valid. If some of those validators are compromised or acting dishonestly, the system still needs to arrive at the correct outcome. That is precisely what Byzantine Fault Tolerance enables. It is the reason you can trust a decentralized ledger even though you cannot trust every individual participant in the network.
Understanding the Byzantine Generals Problem
The Byzantine Generals Problem was introduced by Leslie Lamport, Robert Shostak, and Marshall Pease in 1982. The thought experiment imagines a group of generals commanding different divisions of an army surrounding an enemy city. They need to agree on a unified plan of action, either to attack or to retreat. The challenge is that some of the generals may be traitors who send false messages to sabotage the group’s coordination.
This problem maps directly to distributed systems. Each general represents a node in the network, and the messages they exchange represent data packets. The traitors represent faulty or malicious nodes. The question becomes: how can the loyal generals (honest nodes) reach consensus despite the interference of traitors? This is the exact challenge that consensus algorithms in blockchain technology must solve. Without a reliable answer to this question, decentralized networks would be fundamentally unreliable.
Why Byzantine Fault Tolerance is Important in Blockchain
Blockchain networks are, by design, distributed systems that operate without a central authority. This decentralization is their greatest strength, but it also introduces a critical vulnerability: how do you ensure agreement among participants who have no reason to trust each other? Byzantine Fault Tolerance provides the answer. It guarantees that as long as fewer than one-third of the nodes are compromised, the network can still reach correct and consistent consensus.
For anyone involved in cryptocurrency fundamentals, understanding BFT is essential. It is the mechanism that prevents double spending, blocks invalid transactions, and ensures the integrity of the shared ledger. Without it, the promise of trustless finance and decentralized applications would collapse. Whether you are building a token platform, a DeFi protocol, or exploring enterprise blockchain applications, BFT is the silent guardian ensuring everything works as intended.
Fault Tolerance in Distributed Systems Explained
Fault tolerance in distributed systems is a broad concept that covers how a network handles different types of failures. The simplest form is crash fault tolerance, where the system continues working even if some nodes stop functioning entirely. Byzantine Fault Tolerance goes much further. It handles the worst-case scenario: nodes that do not just crash but actively try to undermine the system by sending conflicting, delayed, or fabricated messages.
In practical terms, BFT-enabled distributed systems implement protocols where every decision requires multiple rounds of communication and verification among nodes. This redundancy ensures that no single point of failure or deception can corrupt the outcome. For modern Web3 infrastructure, this level of resilience is non-negotiable. It is what separates a robust, production-ready blockchain from a vulnerable prototype.
Principle: A Byzantine Fault Tolerant system must assume that any node could behave maliciously at any time. Security is not about trusting participants. It is about designing protocols that produce correct outcomes regardless of individual behavior.
How Byzantine Fault Tolerance Works in Blockchain
Understanding how Byzantine Fault Tolerance operates within blockchain technology requires looking at the mechanics of consensus. In a BFT-enabled blockchain, validators do not simply trust each other’s word. Instead, they follow a structured communication protocol that forces agreement through redundancy, verification, and mathematical guarantees.
Consensus Mechanism in Blockchain
A consensus mechanism is the set of rules that dictates how nodes in a blockchain network agree on the current state of the ledger. There are many types of consensus algorithms, including Proof of Work, Proof of Stake, Delegated Proof of Stake, and various BFT-based models. Each takes a different approach to solving the same fundamental problem: how to get a group of independent, potentially adversarial participants to agree on a single truth.
BFT-based consensus algorithms are distinct because they prioritize safety and finality. Once a block is confirmed through a BFT protocol, it is considered final. There is no risk of reorganization or rollback, which is a significant advantage for applications that require certainty, such as financial settlements and regulatory compliance. For teams looking to build a crypto exchange, this deterministic finality is a critical consideration.
How Blockchain Achieves Consensus
In a BFT blockchain, the consensus process typically works through a leader-based proposal system. One validator is selected (often in rotation) to propose a new block. The other validators then review the proposal, exchange messages about its validity, and vote on whether to accept it. If a sufficient number of validators agree (typically more than two-thirds), the block is committed to the chain.
What makes this process robust is the multiple rounds of communication. Validators do not just cast a single vote. They go through several phases of message exchange, ensuring that even if some validators send conflicting messages, the honest majority can identify and discard the inconsistencies. This multi-round process is the heart of how distributed systems achieve reliability in adversarial environments.
Role of BFT in Decentralized Network Security
BFT serves as the security backbone for decentralized networks. Its role extends beyond simple transaction validation. It protects against coordinated attacks, prevents network partitioning from causing inconsistencies, and ensures that the ledger remains immutable even under adversarial conditions.
Validator Communication Process
In a BFT system, validators engage in a structured multi-step communication process. When a new block is proposed, every validator broadcasts its assessment to every other validator. This creates a mesh of confirmations that makes it virtually impossible for a malicious node to deceive the network without being detected. The communication overhead is significant but necessary for maintaining the integrity of the system.
Agreement Rules in BFT Systems
The fundamental agreement rule in most BFT systems is the two-thirds threshold. For a block to be accepted, more than two-thirds of the validators must agree on its validity. This means that the system can tolerate up to one-third of its validators being faulty or malicious. If the number of compromised nodes exceeds this threshold, the network will halt rather than produce incorrect results, prioritizing safety over liveness.
Network Attack Prevention in Blockchain
BFT protocols are specifically designed to prevent various network attacks. Sybil attacks in blockchain environments, where an attacker creates multiple fake identities to gain disproportionate influence, are mitigated through identity verification and stake requirements. BFT also guards against message replay attacks, man-in-the-middle attacks, and coordinated validator collusion.
Practical Byzantine Fault Tolerance (PBFT) Explained
What is Practical Byzantine Fault Tolerance (PBFT)?
Practical Byzantine Fault Tolerance, introduced by Miguel Castro and Barbara Liskov in 1999, was a breakthrough that made BFT feasible for real-world applications. Earlier BFT protocols were theoretically sound but computationally impractical. PBFT reduced the complexity enough to be deployed in actual distributed systems, paving the way for its adoption in blockchain technology.
PBFT works with a fixed set of known validators and uses a primary-backup model. One node acts as the leader (primary), proposing blocks or operations, while the others (backups) validate and vote on the proposals. The protocol guarantees both safety (no incorrect data is committed) and liveness (the system continues to make progress), as long as no more than one-third of the nodes are faulty.
How PBFT Works Step-by-Step
The PBFT consensus process follows a clearly defined lifecycle. Understanding each step reveals why this protocol has become a reference model for many modern consensus algorithms used in blockchain technology and Web3 infrastructure.
PBFT Consensus Lifecycle
| Step | Phase | Action | Outcome |
|---|---|---|---|
| 1 | Client Request | A client sends a transaction request to the primary node | Request is received and queued |
| 2 | Pre-Prepare | Primary assigns a sequence number and broadcasts a pre-prepare message | All backup nodes receive the proposal |
| 3 | Prepare | Each backup node validates the proposal and broadcasts a prepare message to all other nodes | Nodes collect 2f+1 matching prepare messages |
| 4 | Commit | Nodes that reach prepared state broadcast commit messages | Nodes collect 2f+1 commit messages |
| 5 | Reply | Nodes execute the operation and send replies to the client | Transaction is finalized and irreversible |
| 6 | View Change (if needed) | If the primary fails, a new primary is elected through a view change protocol | System resumes normal operation with new leader |
PBFT Advantages and Limitations
PBFT offers several compelling advantages. It provides immediate transaction finality, meaning confirmed blocks will never be reversed. It is energy efficient since it does not require computational puzzles. And it can tolerate up to one-third of faulty nodes while maintaining both safety and liveness. These qualities make it a strong choice for permissioned blockchain networks and enterprise applications.
However, PBFT is not without limitations. The communication complexity grows quadratically with the number of nodes (O(n²)), which limits its practical scalability. Networks with hundreds or thousands of validators would face significant message overhead. This is why PBFT is most commonly used in permissioned networks with a smaller, known validator set. Understanding blockchain scalability solutions is essential for teams working with BFT-based protocols at scale.
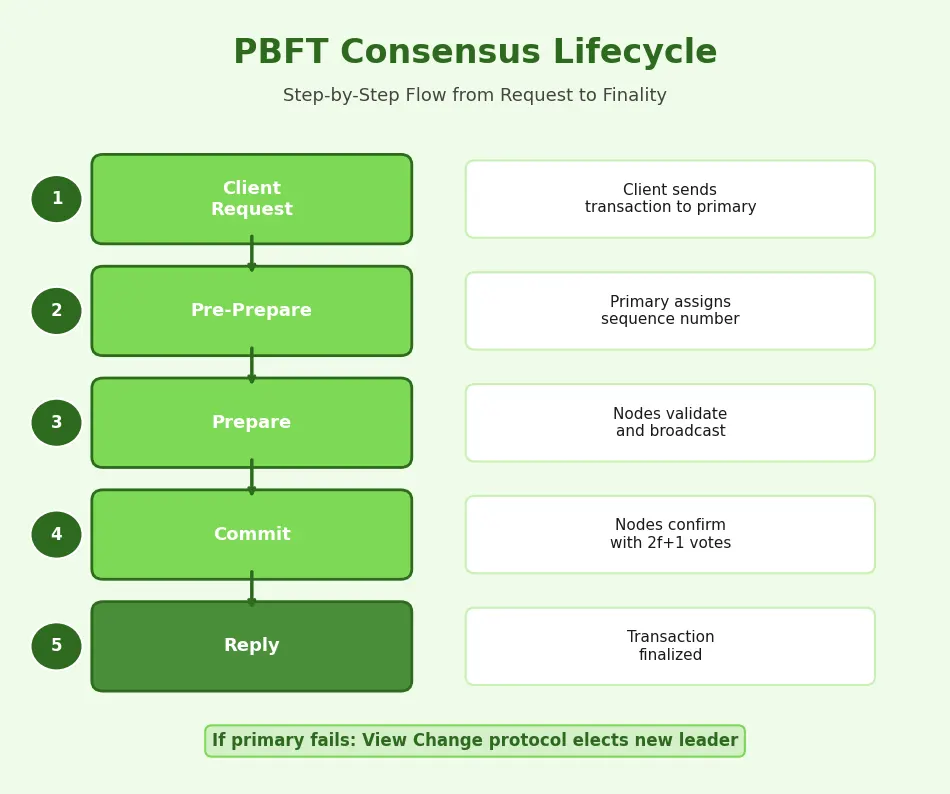
Message Phases (Pre-Prepare, Prepare, Commit)
The three-phase message protocol is the engine of PBFT. During the pre-prepare phase, the primary node assigns an order to incoming requests and multicasts this proposal. In the prepare phase, each node independently verifies the proposal and broadcasts its agreement. Once a node collects enough prepare confirmations, it enters the commit phase, broadcasting its readiness to finalize the operation. This layered verification ensures that even if some nodes try to disrupt the process, the honest majority can reach a consistent decision.
Fault Tolerance Threshold in PBFT
PBFT requires a minimum of 3f+1 total nodes to tolerate f faulty nodes. For example, to withstand one faulty node, you need at least four validators. To tolerate two faulty nodes, you need seven. This formula is a core principle in distributed systems design. It means that the system can handle up to approximately 33% of its validators being malicious without any impact on correctness. If this threshold is exceeded, the protocol prioritizes stopping over producing incorrect results.
Risk Warning: While PBFT provides strong guarantees within its fault threshold, exceeding the one-third limit of compromised validators can cause the network to halt entirely. System designers must carefully vet and monitor their validator sets to maintain network health.
Byzantine Fault Tolerance vs Proof of Work
One of the most frequently discussed comparisons in blockchain technology is between BFT-based consensus algorithms and Proof of Work. Both aim to solve the same fundamental problem, achieving consensus in a trustless environment, but they approach it from very different angles.
BFT vs Proof of Stake
Proof of Stake (PoS) and BFT are not mutually exclusive. In fact, many modern blockchain platforms combine them. In a PoS system, validators are chosen based on their economic stake in the network. BFT protocols can then be layered on top to determine how those chosen validators reach agreement. Ethereum’s transition to Proof of Stake, for example, incorporated BFT-inspired finality gadgets (Casper FFG) to provide deterministic finality on top of its PoS validator selection.
Pure PoS without BFT can suffer from finality delays and potential chain reorganizations. Adding a BFT layer addresses these weaknesses by ensuring that once a block reaches supermajority agreement, it is permanently settled. This hybrid approach represents the current state of the art in consensus algorithms for public blockchain networks.
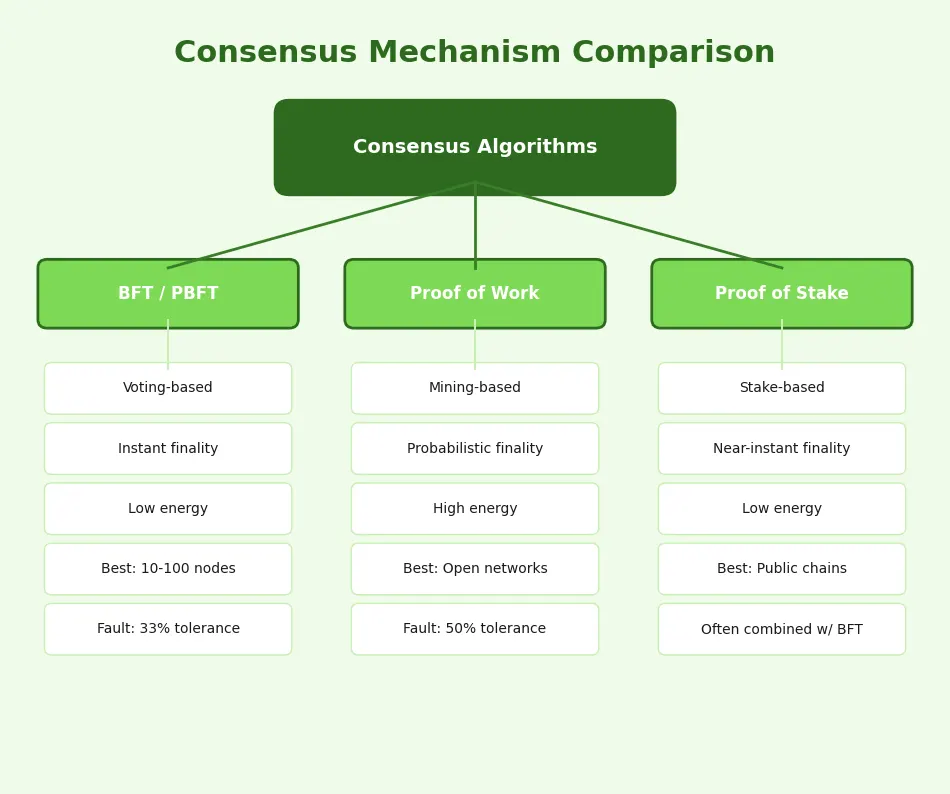
PBFT vs Proof of Work Comparison
| Feature | PBFT | Proof of Work |
|---|---|---|
| Finality | Immediate and deterministic | Probabilistic (increases with confirmations) |
| Energy Usage | Minimal (no mining) | Very high (computational puzzles) |
| Scalability | Limited by O(n²) messaging | Better with large node counts |
| Fault Threshold | Tolerates up to 33% malicious nodes | Tolerates up to 50% hash power |
| Throughput | High (thousands of TPS possible) | Low (7-15 TPS for Bitcoin) |
| Network Type | Best for permissioned/smaller validator sets | Suitable for large, open networks |
| Attack Resistance | Strong against Byzantine faults | Strong against 51% attacks |
Which Consensus Mechanism is More Secure?
Security is not a one-dimensional measure. Proof of Work has been battle-tested for over a decade in Bitcoin, proving its resilience against large-scale attacks through sheer computational requirements. Byzantine Fault Tolerance, on the other hand, provides mathematically provable safety guarantees within its fault threshold. The “better” choice depends entirely on the use case, network size, performance requirements, and threat model.
For small to medium-sized validator sets where finality and speed matter, BFT-based consensus algorithms are generally superior. For large, open, and permissionless networks where maximum decentralization is the priority, Proof of Work or PoS with BFT finality layers may be more appropriate. This is a fundamental decision in cryptocurrency fundamentals that shapes the architecture of every blockchain project.
Is Byzantine Fault Tolerance Secure?
Security Strength of BFT in Crypto Networks
Byzantine Fault Tolerance offers one of the strongest security models available in blockchain technology. Its mathematical foundation provides provable guarantees: as long as fewer than one-third of nodes are malicious, the system will produce correct results. This is not a heuristic or a probabilistic claim. It is a formal guarantee backed by decades of research in distributed systems theory.
In crypto networks, this translates to tangible security benefits. Transactions confirmed through BFT protocols cannot be reversed or altered. There is no need to wait for multiple block confirmations to be confident in a transaction’s permanence. For applications like financial services, supply chain verification, and digital asset management, this level of certainty is invaluable. Understanding how state is managed in these systems, such as through state trie structures, adds another layer of insight into BFT’s security model.
Handling Malicious Nodes in Blockchain
BFT protocols handle malicious nodes through redundancy and verification. When a node sends conflicting messages, the multi-round communication process allows other nodes to detect the inconsistency. Honest nodes can compare the messages they have received and identify which nodes are behaving dishonestly. The protocol then proceeds based on the agreement of the honest majority, effectively neutralizing the malicious actors.
Many modern BFT implementations also include slashing mechanisms, where validators who are caught acting dishonestly lose their staked tokens. This economic penalty adds a powerful deterrent layer on top of the protocol’s inherent fault tolerance, creating a dual defense of mathematical guarantees and financial incentives.
Real-World Examples of BFT-Based Blockchains
Several prominent blockchain platforms rely on variations of Byzantine Fault Tolerance for their consensus mechanisms. These real-world implementations demonstrate that BFT is not just a theoretical construct but a proven approach powering active networks across global markets.
BFT-Based Blockchain Platforms
| Platform | BFT Variant | Use Case | Notable Feature |
|---|---|---|---|
| Cosmos (Tendermint) | Tendermint BFT | Inter-chain communication | Instant finality, modular architecture |
| Hyperledger Fabric | PBFT / Raft | Enterprise solutions | Permissioned, pluggable consensus |
| Zilliqa | PBFT + Sharding | High-throughput dApps | Combines BFT with network sharding |
| NEO | dBFT (Delegated BFT) | Smart economy | Single block finality |
| Algorand | Pure PoS + BA* | Financial infrastructure | Byzantine agreement with VRF selection |
Advantages of Byzantine Fault Tolerance in Web3 Security
The advantages of Byzantine Fault Tolerance extend well beyond theoretical security guarantees. For Web3 infrastructure, BFT provides practical benefits that directly impact user experience, operational costs, and system reliability.
Faster Transaction Finality
One of the most significant advantages of BFT-based consensus algorithms is immediate transaction finality. In Proof of Work systems like Bitcoin, users typically wait for six confirmations (about an hour) before considering a transaction final. With BFT protocols, once a block is committed, it is permanent. There is no waiting period, no risk of reorganization, and no uncertainty. This is transformative for applications in finance, e-commerce, and real-time trading, where delayed confirmations introduce friction and risk.
For businesses looking to build crypto exchange platforms or integrate blockchain-based payment systems, faster finality translates directly to better user experience and reduced operational complexity.
Improved Blockchain Security Mechanism
Byzantine Fault Tolerance provides a mathematically rigorous security mechanism that does not rely on economic assumptions alone. While PoW security depends on the cost of computational power and PoS security depends on the cost of acquiring stake, BFT security is grounded in formal proofs about the behavior of distributed systems under adversarial conditions.
This makes BFT particularly valuable for high-stakes applications where security guarantees must be absolute rather than probabilistic. Healthcare data management, government records, cross-border settlement systems, and defense applications all benefit from the deterministic assurances that BFT provides.
Energy Efficiency Compared to PoW
Unlike Proof of Work, which consumes vast amounts of electricity through competitive mining, BFT-based consensus algorithms require only the energy needed for network communication and basic computation. This makes BFT one of the most environmentally sustainable approaches to achieving consensus in blockchain technology. As regulatory pressure around energy consumption increases in major markets, this efficiency advantage becomes a strategic benefit for projects choosing their consensus model.
Build with Confidence: Whether you are launching a token, a DeFi protocol, or a crypto exchange, choosing the right consensus mechanism is one of the most consequential architectural decisions you will make. BFT provides a strong foundation for projects prioritizing security and finality.
Consensus Model Selection Criteria
Choosing the right consensus mechanism is not a one-size-fits-all decision. It requires careful evaluation of your project’s specific requirements, constraints, and long-term goals. Here are the key factors to consider when selecting between BFT-based protocols, Proof of Work, Proof of Stake, and hybrid approaches.
Consensus Selection Framework
| Selection Criteria | BFT / PBFT | Proof of Work | Proof of Stake |
|---|---|---|---|
| Network Size | Small to medium (10-100 validators) | Unlimited (thousands of miners) | Medium to large (hundreds of validators) |
| Finality Need | Immediate / deterministic | Probabilistic (minutes to hours) | Near-instant with BFT finality layer |
| Energy Priority | Very low consumption | Very high consumption | Low consumption |
| Access Model | Permissioned (best fit) | Fully permissionless | Permissionless or permissioned |
| Ideal For | Enterprise chains, consortium networks, exchanges | Public chains prioritizing censorship resistance | General-purpose public and private chains |
Before committing to a consensus model, assess your validator governance structure, the regulatory environment in your target markets, your performance benchmarks, and your long-term scalability roadmap. An experienced blockchain solutions partner can help you navigate these decisions and avoid costly architectural mistakes.
Future of Byzantine Fault Tolerance in Web3 Infrastructure
The role of Byzantine Fault Tolerance in Web3 infrastructure is expanding rapidly. As blockchain technology matures and enters more demanding enterprise and consumer applications, the need for robust, efficient, and scalable consensus algorithms has never been greater.
Role of BFT in Layer 2 Solutions
Layer 2 solutions are designed to increase blockchain throughput by processing transactions off the main chain while still inheriting its security guarantees. Many Layer 2 protocols incorporate BFT-based consensus to ensure that their off-chain operations are secure and finalized. Rollups, sidechains, and state channels can all benefit from BFT’s deterministic finality, which simplifies the process of settling transactions back to the main chain.
As Layer 2 adoption grows, BFT’s role as a security layer within these architectures will become increasingly important. The ability to achieve consensus quickly and with certainty is exactly what Layer 2 operators need to deliver the speed and cost savings that users expect from Web3 infrastructure.
Evolution of Advanced BFT Algorithms
Research into next-generation BFT algorithms is one of the most active areas in distributed systems science. Protocols like HotStuff, Tendermint, Narwhal-Tusk, and DAG-based BFT are pushing the boundaries of what is possible in terms of scalability, latency, and communication efficiency. HotStuff, for example, reduces communication complexity to O(n) per view, a significant improvement over classical PBFT’s O(n²).
These advancements are making it possible to use BFT-based consensus in larger, more open networks, gradually eroding the traditional limitation that confined BFT to smaller validator sets. As these algorithms mature, we can expect to see Byzantine Fault Tolerance playing an even larger role in public blockchain networks and mainstream Web3 infrastructure.
The Growing Importance of Decentralized Security
As digital assets, decentralized identity, and on-chain governance become more prevalent, the security guarantees provided by Byzantine Fault Tolerance become more consequential. A compromise in a consensus protocol does not just affect a blockchain. It can impact financial systems, personal data, supply chains, and democratic processes built on top of that chain.
The growing importance of decentralized security means that BFT will continue to evolve, adapt, and integrate with other security mechanisms. For organizations and teams building in the Web3 space, investing in a deep understanding of Byzantine Fault Tolerance and its implications is not optional. It is a strategic necessity. Projects like the EverRise ecosystem case study demonstrate how thoughtful consensus and security design can create lasting, resilient platforms.
Launch Your BFT-Powered Blockchain Today
We develop secure and scalable blockchain solutions using advanced consensus mechanisms like Byzantine Fault Tolerance. Let’s build your platform the right way.
Launch Your Exchange Now
Conclusion
Byzantine Fault Tolerance is far more than a computer science curiosity. It is the foundational security principle that makes blockchain technology trustworthy. From the theoretical elegance of the Byzantine Generals Problem to the practical rigor of PBFT and its modern successors, BFT ensures that decentralized networks can operate reliably in a world where not every participant can be trusted.
For anyone working with cryptocurrency fundamentals, building decentralized applications, or architecting Web3 infrastructure, understanding BFT is essential. It informs every decision from consensus algorithm selection to validator governance to scalability planning. The consensus algorithms that protect today’s most valuable blockchain networks are rooted in Byzantine Fault Tolerance, and the next generation of protocols will push its principles even further.
As distributed systems continue to reshape how we build and interact with technology, the importance of Byzantine Fault Tolerance will only grow. Whether you are launching a new blockchain protocol, building an exchange, or evaluating consensus models for an enterprise solution, BFT remains the gold standard for achieving trustworthy agreement in a trustless world.
The future belongs to systems that can withstand adversity without centralized control. Byzantine Fault Tolerance is what makes that future possible.
Frequently Asked Questions
Byzantine Fault Tolerance (BFT) is the ability of a distributed system to continue functioning correctly even when some of its participants behave maliciously or fail unpredictably. In the context of blockchain technology, BFT ensures that honest nodes can still reach agreement on the state of the ledger, even if a portion of the network is compromised. It is one of the most critical properties that any decentralized system must have to remain trustworthy and secure.
The Byzantine Generals Problem illustrates the fundamental challenge of achieving reliable consensus among distributed parties who cannot fully trust each other. For blockchain technology, solving this problem is essential because it ensures that all participants agree on a single version of the truth without relying on a central authority. Consensus algorithms inspired by this problem form the backbone of cryptocurrency fundamentals and Web3 infrastructure.
PBFT operates through a multi-phase voting process where nodes exchange messages to agree on the validity of transactions. The protocol involves pre-prepare, prepare, and commit phases, allowing nodes to verify and confirm each transaction block before it is finalized. This structured approach ensures that up to one-third of faulty or malicious nodes can be tolerated without disrupting the network.
BFT-based consensus algorithms rely on voting and message-passing among validators to achieve agreement, while Proof of Work requires miners to solve computationally intensive puzzles. BFT systems are typically faster and more energy efficient, whereas Proof of Work offers a different security model that has been proven at scale in networks like Bitcoin. Each approach addresses the challenge of maintaining integrity in distributed systems differently.
Yes, Byzantine Fault Tolerance provides a strong security foundation suitable for enterprise-grade blockchain platforms. Its ability to tolerate up to one-third malicious participants, combined with deterministic finality, makes it ideal for financial services, supply chain management, and other mission-critical applications. Many enterprise blockchain solutions operating across global markets rely on BFT-based protocols.
Several major blockchain platforms implement BFT-based consensus mechanisms. Tendermint (used by Cosmos), Hyperledger Fabric, Zilliqa, and NEO all leverage variations of Byzantine Fault Tolerance. These networks demonstrate how BFT consensus algorithms can be adapted for different use cases, from public cryptocurrency networks to private enterprise solutions.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







