Key Takeaways
- Web3 architecture separates trustless on-chain logic from scalable off-chain systems.
- Wallet-based signature authentication replaces passwords as the core identity mechanism.
- Smart contracts must be modular, auditable, and designed for irreversible execution.
- ndexing layers are essential for fast reads and complex user-facing queries.
- Backends orchestrate UX, security, automation, and compliance without owning blockchain state.
- Secure key management and multisig controls define real-world Web3 production safety.
- Observability, monitoring, and environment separation determine long-term Web3 system reliability.
Before you design contracts, pick a chain, or plan indexing, you must lock one decision: what part of product needs blockchain guarantees and what part is just a normal application. This boundary is the foundation of Web3 architecture because it decides where trust is removed and where traditional systems remain acceptable. If you do not define this clearly, the architecture will either become too centralized to be Web3, or too on-chain to be usable.
Web3 is not the UI, not the wallet connection button, and not the token. Web3 is the part of a product that must remain correct even if the operator disappears, the backend fails, or the frontend is replaced. A normal app is everything that exists to make the product fast, user-friendly, private, and scalable without needing global consensus.
When you draw this line correctly, smart contracts become smaller and safer, costs stay predictable, and user experience stays competitive. When you draw it incorrectly, you end up paying for slow execution, expensive reads, and weak product adoption.
Before Architecture, Lock This Decision
System boundary should be locked around one simple idea: put only the irreducible truth on-chain, and keep everything else off-chain.
What Should Be On-Chain
On-chain belongs to anything that must be trustless, publicly verifiable, and enforced without discretion. This is the part of the product where users should not need to trust you.
Ownership (NFTs, balances, roles)
Ownership should live on-chain when it defines user rights, transferability, or access control that must be provable to anyone.
Rules that must be trustless (escrow, swaps, staking, reward logic)
Core value rules belong on-chain when breaking them would cause financial loss, manipulation, censorship, or selective enforcement.
Public verifiability (proofs, audit trail, settlement)
Final settlement and auditability belong on-chain when users must verify actions, payouts, and history without relying on database.
What Should Be Off-Chain
Off-chain belongs to everything that exists for usability, performance, privacy, and operational flexibility. Off-chain systems can be fast and dynamic because they are not the settlement layer.
UI/UX, sessions, rate limits
User experience flows and abuse protection belong off-chain because they change often and must remain low-latency.
Search, filters, feeds, analytics
Complex discovery and reporting belong off-chain because blockchains are not designed for sorting, aggregations, or fast historical queries.
Notifications, emails, OTP, push
Communication channels belong off-chain because they coordinate users, but should not define truth or ownership.
Heavy compute (AI, scoring, risk checks)
High-cost computation belongs off-chain because it is probabilistic, evolves frequently, and must stay scalable.
Private data (KYC, PII)
Sensitive data must remain off-chain to avoid permanent exposure, and only hashes or proofs should be anchored when verification is required.
Why This Boundary Matters
If you try to put everything on-chain, you will trade away product usability. Every extra on-chain action increases cost, increases latency, and reduces the ability to iterate. The result is usually a system that is technically decentralized but commercially weak.
Cost pressure increases
Gas fees accumulate quickly when you treat the chain like an application database.
Latency becomes a user experience problem
Block confirmations and network congestion create friction where normal apps feel instant.
UX quality drops under real load
Direct chain reads are slow for complex screens, forcing you to build indexers anyway.
Privacy becomes impossible to recover
Once sensitive data is on-chain, it is permanently visible and cannot be revoked.
The Practical Rule That Works in Production
Put on-chain only what must remain true under adversarial conditions. Put off-chain everything that improves speed, privacy, and usability, and treat it as an orchestration layer that serves the trustless core.
This boundary is step one because every other architectural decision depends on it. Once you lock it, the next step is defining the real Web3 stack components that implement this separation end to end.
2) High-Level System Components -The Real Web3 Stack
Once the Web3 product boundary is clearly defined, the architecture can be expressed as a system of cooperating components. Real Web3 applications are not single deployments or single technologies. They are distributed systems where each layer exists because the blockchain alone cannot deliver usability, performance, or operational reliability.
A production-grade Web3 application is not just a smart contract with a UI. It is a distributed system where trust, ownership, execution, data availability, and user experience are handled across multiple specialized layers. Each layer solves a different problem: wallets handle identity, blockchains handle state and settlement, indexers handle queryability, and traditional backend systems handle orchestration and scale.
Frontend dApp (Next.js, React, Flutter Web)
In Web3, the frontend is not just a presentation layer it is the primary interaction gateway with the blockchain. Unlike Web2, where the frontend talks only to a backend server, a Web3 frontend directly communicates with wallets, RPC nodes, indexers, and sometimes even decentralized storage networks. This makes frontend architecture significantly more critical and complex.
React.js is the most widely used framework for Web3 because of its component model, ecosystem maturity, and compatibility with Web3 libraries. However, Next.js has become the industry standard for serious Web3 products because Web3 applications demand performance, SEO, server-side rendering (SSR), and edge-level optimization all of which plain React cannot provide at scale.
Next.js allows you to pre-render pages, stream data, cache responses, and still interact with wallets entirely on the client side. This hybrid rendering model is crucial for Web3 apps where some data (like protocol stats or pool lists) can be public and cached, while wallet-specific data must remain client-side and private.
Web3 integration in React / Next.js
Web3 integration in the frontend is done through provider-based libraries that abstract blockchain communication and wallet handling. The most common stack includes:
-
ethers.js: Low-level Ethereum interaction library (contracts, providers, signers)
-
wagmi: React hooks for wallet connection, chain management, and contract calls
-
WalletConnect: Cross-wallet connectivity (mobile, desktop, QR)
-
thirdweb: Higher-level SDK for rapid dApp development
ethers.js handles raw blockchain interaction — encoding function calls, signing transactions, reading on-chain data. However, using ethers directly in large applications becomes repetitive and error-prone. This is where wagmi comes in. Wagmi provides React hooks like useAccount, useContractRead, and useContractWrite, which make Web3 state reactive and UI-friendly.
For teams that want speed over low-level control, thirdweb offers prebuilt contract interfaces, wallet UIs, and deployment tooling. However, production teams often combine thirdweb for rapid iteration with custom ethers/wagmi logic for core protocol interactions.
Flutter Web in Web3 context
Flutter Web is used when teams want code reuse across mobile and web, especially for wallet-centric applications. Unlike React, Flutter does not have native Web3 tooling, so Web3 integration usually happens via:
-
JavaScript interop (
dart:js) -
Embedded web views
-
Custom wallet bridges
Flutter Web works best when the blockchain interaction is abstracted behind APIs or SDKs, or when the app embeds existing wallet connectors. While React/Next.js dominates pure Web3 dApps, Flutter excels in consumer-facing apps where UX consistency across platforms is more important than direct low-level blockchain access.
Wallet Layer (MetaMask, WalletConnect, Embedded Wallets)
In Web3, wallets replace usernames and passwords. A wallet is not just a payment tool — it is the user’s cryptographic identity. Every action in a Web3 app, from logging in to voting in a DAO, is authorized through wallet signatures.
Browser wallets like MetaMask inject an Ethereum provider into the browser, allowing the frontend to request account access and signatures. WalletConnect extends this functionality to mobile wallets by creating a secure communication bridge between the dApp and the wallet.
Modern applications increasingly use embedded wallets, where key management is abstracted away using MPC (multi-party computation) or secure enclaves. These wallets improve onboarding but introduce custodial or semi-custodial trade-offs that must be carefully designed.
The wallet layer defines the trust boundary of your application. Once a wallet signs a message or transaction, the system assumes user consent. Designing clear, transparent signing flows is critical to prevent phishing and user errors.
Smart Contracts (Solidity, Vyper, Rust on Solana)
Smart contracts are the source of truth in Web3 systems. Anything that must be trustless, verifiable, or immutable belongs here. This includes token balances, NFT ownership, escrow logic, staking rules, and governance mechanisms.
Ethereum-based chains primarily use Solidity, while Solana uses Rust. Regardless of language, smart contracts must be deterministic, auditable, and gas-efficient. Bugs cannot be patched easily, which makes contract architecture and testing far more important than in Web2 systems.
In real systems, contracts are usually modular: core logic contracts, storage contracts, upgrade proxies, and governance controllers. This separation allows controlled upgrades while preserving on-chain state and user trust.
Ownership and state management
Tracks balances, roles, permissions, and other critical protocol state.
Rule enforcement
Executes swaps, staking, escrows, and rewards without discretionary control.
Final settlement
Commits irreversible state changes and value transfers on-chain.
Event Indexing (The Graph or Custom Indexer)
Blockchains are execution engines, not databases. They are terrible at answering questions like “show my transaction history” or “list pools by TVL.” Event indexing layers solve this problem by listening to on-chain events and storing them in structured databases.
The Graph is the most common indexing protocol, allowing developers to define subgraphs that index contract events. For high-performance or proprietary use cases, teams build custom indexers using Node.js, Kafka, and PostgreSQL.
Without indexing, Web3 apps become unusable. Indexers are what turn deterministic blockchain logs into human-friendly applications.
Event processing
Listens to contract events and normalizes them into application entities.
Historical data reconstruction
Builds complete timelines for users, assets, and protocol activity.
Query optimization
Enables fast searches, filters, and aggregations for frontend consumption.
Backend API (Authentication, Signatures, Orchestration)
Despite the “decentralized” narrative, most Web3 apps still need backends. These backends never custody funds but handle logic that does not belong on-chain: authentication via signed messages, anti-spam checks, notifications, automation, and workflow coordination.
Backend APIs often verify wallet signatures to establish session-like behavior without passwords. They also coordinate interactions between the frontend, indexers, and blockchain — for example, preparing transaction payloads or validating off-chain data before on-chain submission.
This layer acts as the control plane of the system, ensuring smooth operations without compromising decentralization principles.
Signature-based authentication
Verifies wallet ownership and manages sessions without passwords.
Business logic orchestration
Handles off-chain rules that influence user flows but not on-chain truth.
Service coordination
Connects indexers, notification systems, and automation services.
Database and Cache (Postgres, Redis)
Databases in Web3 systems do not replace the blockchain — they mirror and augment it. Indexed events, user metadata, and protocol analytics are stored in relational databases like PostgreSQL for efficient querying.
Redis is used heavily for caching balances, session states, and hot queries. Without caching, Web3 apps become slow and expensive due to repeated RPC calls.
This layer is essential for scalability. Blockchains guarantee correctness; databases guarantee usability.
Indexed data storage
Persists transformed blockchain events and aggregated views.
Session and rate limiting
Controls access patterns to protect system stability.
Caching layer
Reduces load on RPC providers and indexers by serving frequent reads.
Storage and CDN (IPFS, Arweave, S3, R2)
Blockchains are not designed to store large files. Web3 systems therefore rely on decentralized storage networks like IPFS and Arweave for immutable data, and cloud storage like S3 or Cloudflare R2 for performance-optimized delivery.
NFT metadata, images, and documents are typically stored off-chain and referenced by hashes on-chain. CDNs sit in front of these storage layers to ensure fast global access.
Storage architecture determines how “decentralized” and resilient application truly is and how fast it feels to users.
Asset storage
Stores images, files, and metadata that cannot live on-chain.
Integrity anchoring
Uses hashes or URIs to ensure data consistency and verifiability.
Global delivery
Distributes content efficiently through CDN-backed infrastructure.
How These Components Work Together
These eight components form a complete Web3 system. The frontend captures intent, the wallet authorizes actions, the RPC layer communicates with the blockchain, smart contracts enforce rules, indexers prepare data for fast access, the backend coordinates workflows, databases optimize performance, and storage systems deliver assets at scale.
This structure is not theoretical. It is the practical architecture used by production Web3 platforms. With this stack in place, the next step is understanding how identity, transactions, and system automation flow across these layers.

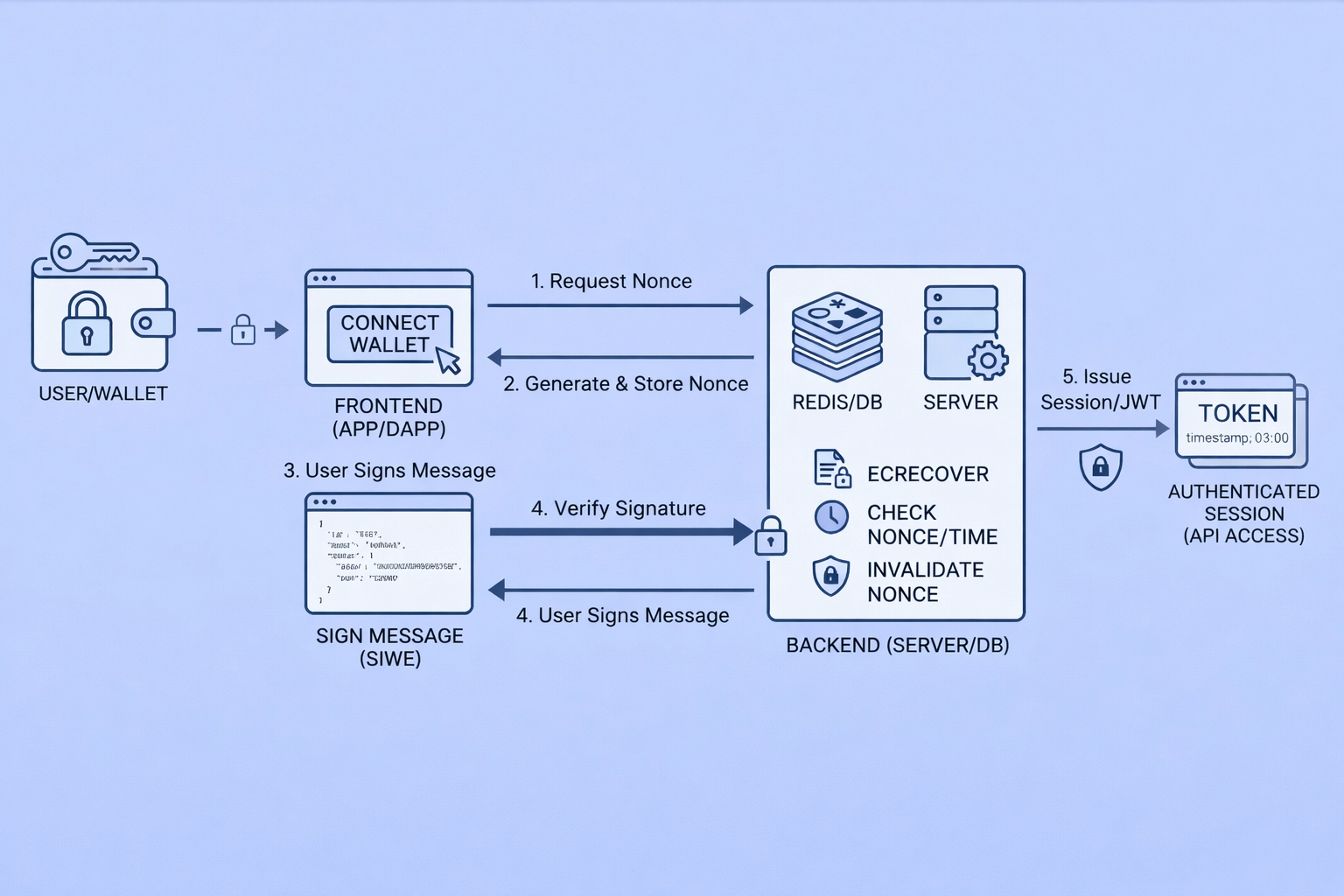
3) Wallet & Identity Architecture (How Users “Log In”)
In Web3, users do not “log in” using email and passwords. Instead, identity is proven through cryptographic ownership of a wallet address. Authentication is performed by signing a message with a private key that never leaves the user’s wallet. This creates a trust model based on proof of control, not stored credentials.
This shift fundamentally changes identity architecture. There is no centralized password database to breach, no password reset flows, and no credential reuse risk. Instead, Web3 authentication relies on signature-based identity, most commonly implemented using a SIWE-style (Sign-In With Ethereum) flow.
Core Principle: Signature-Based Identity
In Web3, the wallet address is the identity.
If a user can cryptographically sign a message from a given address, they are treated as the legitimate owner of that identity.
This identity model has three defining properties:
-
The private key never leaves the wallet
-
Authentication is stateless and verifiable
-
Trust is derived from cryptography, not secrecy
Standard Web3 Login Flow (SIWE Style)
Step 1: Frontend Requests a Nonce
What happens
When a user clicks “Connect Wallet” or “Login,” the frontend first requests a nonce from the backend.
The backend generates a cryptographically random nonce and temporarily stores it (usually in Redis or a database).
Why this step is critical
The nonce prevents replay attacks.
Without it, an attacker could reuse an old signed message and impersonate the user.
Nonce properties:
-
One-time use
-
Short-lived (e.g., 5–10 minutes)
-
Bound to a wallet address
In architecture terms, this is the anti-replay control layer.
Step 2: User Signs a Login Message
Message structure (SIWE-style)
The frontend now asks the wallet to sign a structured message, for example:
This message is displayed clearly inside the wallet UI.
Tools used at this layer
-
ethers.js →
signer.signMessage() -
wagmi →
useSignMessage() -
SIWE (EIP-4361) → standardized message format
Why structured messages matter
Unstructured messages are dangerous.
SIWE ensures:
-
Domain binding (prevents phishing)
-
Chain binding (prevents cross-chain replay)
-
Time-bound validity
This step converts wallet ownership into cryptographic proof.
Step 3: Backend Verifies the Signature
Verification process
The frontend sends the signed message + signature to the backend.
Backend performs:
-
Reconstructs the signed message
-
Recovers the signer address using
ecrecover -
Confirms it matches the claimed wallet address
-
Verifies nonce, expiry, domain, and chainId
-
Invalidates the nonce immediately
Tools commonly used
-
ethers.js (signature recovery)
-
siwe library (message parsing & validation)
-
Redis (nonce storage & invalidation)
Architecture insight
This step is the identity verification boundary.
If signature verification passes, the backend now trusts that:
“The user controls this wallet address right now.”
No passwords. No secrets stored.
Step 4: Backend Creates a Session or JWT
Once identity is verified, the backend issues a session token.
Common approaches:
-
JWT (JSON Web Token) signed by backend
-
HTTP-only session cookie
-
Short-lived access token + refresh token
What the token represents
The token does not represent the wallet itself.
It represents:
-
Verified wallet address
-
Authentication timestamp
-
Allowed scopes (read/write/admin)
-
Expiry time
This token is now the Web3 equivalent of a login session.
Step 5: Session Is Used for API Calls
Subsequent API requests include the session token:
The backend:
-
Verifies token validity
-
Extracts wallet identity
-
Applies authorization rules
Why this hybrid model is necessary
Direct wallet signing for every API call is:
-
Slow
-
Expensive
-
Terrible UX
So Web3 systems use:
-
Wallet signature for login
-
Session tokens for performance
This is a hybrid Web2 + Web3 identity architecture, and it is intentional.
4) Transaction Architecture (How State Changes Happen)
In Web3, every state change happens through a transaction. Unlike Web2 systems where servers update databases directly, Web3 requires cryptographic signatures and blockchain execution for any write. No transaction means no state change.
All Web3 transactions fall into two clear categories based on who initiates them.
A) User-Triggered Writes (Most Common)
These transactions are initiated directly by users through their wallets.
-
Frontend builds transaction
The dApp prepares the smart contract call, parameters, and gas details. -
Wallet signs transaction
User approves and signs the transaction using their private key. -
Broadcast via RPC
Signed transaction is sent to the blockchain through an RPC provider. -
Mempool → block inclusion
Transaction waits in the mempool until validators include it in a block. -
Confirmations
Each new block increases certainty that the transaction is final. -
Frontend updates UI
UI updates optimistically first, then confirms using on-chain state.
B) System-Triggered Writes (Automation)
These transactions are executed automatically by the protocol, not by users.
They are required to keep the system functioning without manual action.
Executor Layer (Required for Automation)
An executor is a trusted component that submits transactions on behalf of the system.
-
Keeper / automation network
Monitors conditions and triggers transactions automatically. -
Relayer
Submits transactions for gas abstraction or protocol actions. -
Cron worker / bot
Custom backend service that runs scheduled or event-based logic.
5) Typical Web3 Contract Modules
A production Web3 protocol is not a single contract but a collection of specialized modules. Each module has a clear responsibility and interacts with others through well-defined interfaces. This modular design improves security, auditability, and long-term maintainability.
Token (ERC20 / ERC721 / ERC1155)
Handles fungible tokens, NFTs, or multi-token assets.
Implements ownership, transfers, approvals, and supply rules using standard interfaces.
Treasury / Vault
Stores and manages protocol funds securely.
Centralizes asset custody and reduces exposure of core contracts.
Staking / Rewards
Manages token locking, reward calculation, and distribution.Keeps incentive logic isolated from core protocol operations.
Marketplace / Exchange / AMM
Executes trades, swaps, pricing logic, or liquidity management.
Requires strict math correctness and protection against MEV and manipulation.
Access Control / Permissioning
Defines who can call sensitive functions.
Enforces roles like admin, operator, pauser, or governance executor.
Fee Router / Revenue Split
Collects protocol fees and distributes them to stakeholders.
Separates financial flows from business logic for clarity and safety.
Registry (Addresses / Configuration)
Stores contract addresses and system parameters.
Allows upgrades and configuration changes without redeploying everything.
Oracle Adapter (If Needed)
Fetches external data such as prices or rates.
Isolates oracle dependency to minimize risk to core contracts.
Web3 Architecture Insight
Each contract module should:
-
Do one job only
-
Expose minimal interfaces
-
Trust as little as possible
This modular approach turns smart contracts into a coordinated system, not a fragile monolith.
6) Indexing Architecture (How App Reads Blockchain Fast)
Blockchains are optimized for secure execution, not fast or complex queries. Direct RPC reads become slow, expensive, and unreliable when building real user interfaces. To solve this, Web3 applications introduce an indexing layer that converts raw on-chain events into fast, queryable data.
Why Direct RPC Reads Don’t Scale
-
High latency and cost
Each UI action may require multiple RPC calls. -
No query capability
Blockchains cannot filter, sort, or aggregate data. -
Poor UX for complex screens
Dashboards and lists become slow or unusable.
The Indexing Layer (Core Concept)
-
Listens to smart contract events
-
Transforms logs into structured data
-
Stores data in databases
-
Serves fast APIs to the frontend
This layer acts as the read engine of Web3 app.
Option 1: The Graph (Fast to Ship)
-
Subgraph listens to events
Automatically indexes events emitted by contracts. -
Stores structured entities
On-chain data is saved in a query-friendly format. -
Frontend queries via GraphQL
UI fetches data using simple, flexible GraphQL queries.
Best for teams that want speed and low infrastructure overhead.
Option 2: Custom Indexer (Most Control)
-
Event listener (WebSocket RPC)
Backend listens to blockchain events in real time. -
Normalizer → queues
Events are validated, ordered, and processed safely. -
Writes to Postgres / Elastic
Data is stored for fast querying and analytics. -
Exposes REST or GraphQL APIs
Frontend consumes indexed data efficiently.
Best for large systems needing custom logic and performance tuning.
What Should Use Indexers For
-
Portfolio views
Wallet balances, positions, NFTs, and holdings. -
User history
Searchable and paginated transaction activity. -
Leaderboards
Rankings based on volume, rewards, or participation. -
Marketplace listings
Active items, prices, and availability. -
Analytics dashboards
TVL, volume, fees, and protocol metrics.
7) Storage Architecture (Metadata & Off-Chain Files)
Blockchains are not designed to store large files. On-chain storage is expensive and inefficient, so Web3 systems store only references on-chain, while actual content lives off-chain. This separation keeps costs low while preserving verifiability.
The core rule is simple:
store hashes and pointers on-chain, store data off-chain.
Why Big Data Should Not Be On-Chain
-
High gas cost
Storing large data directly on-chain is extremely expensive. -
Poor scalability
Blockchains are not optimized for file storage. -
Unnecessary permanence
Not all data needs full on-chain immutability.
Typical Web3 Storage Pattern
-
Images / files → IPFS / Arweave / S3 / R2
Large assets are stored outside the blockchain. -
Metadata JSON → IPFS / Arweave
Structured metadata remains content-addressed. -
Smart contract stores references
Contract mapstokenId → tokenURIas a pointer.
This keeps the blockchain lightweight and verifiable.
Storage Options Explained
IPFS
-
Content-addressed storage using hashes.
-
Cheap and flexible, but requires pinning for persistence.
Arweave
-
Permanent, immutable storage paid once.
-
Best when data must exist forever.
S3 / Cloudflare R2
-
Centralized but fast and cheap storage.
-
Often used behind a CDN for performance.
Choosing the Right Storage
-
If content must be immutable forever
Use Arweave. -
If you want cheap + fast with optional permanence
Use IPFS with a pinning service. -
If performance matters more than decentralization
Use S3 or R2 with CDN.
8) Backend Architecture (Why Web3 Still Needs a Backend)
Even fully decentralized applications rely on backend services. Web3 removes custodial trust, not infrastructure needs. Backends exist to improve UX, performance, and safety, while the blockchain remains the source of truth.
The key rule is clear:
the backend must never own balances or define ownership.
Why Web3 Apps Still Use Backends
-
Signature authentication + sessions
Verifies wallet signatures and issues short-lived sessions. -
Rate limiting & abuse prevention
Protects APIs from spam, bots, and denial-of-service attacks. -
Notifications (email / push)
Sends transaction alerts, confirmations, and system messages. -
Off-chain business logic
Handles calculations like quotes, scoring, or eligibility checks. -
Compliance flows (if required)
Manages KYC or verification without touching on-chain assets. -
Webhook receiver
Listens to events from indexers, relayers, or automation services. -
Caching expensive reads
Reduces RPC and indexer load for better performance.
9) Key Management & Security Architecture
This is the most critical layer in any Web3 system. Most projects fail not because of smart contract bugs, but because private keys are compromised or mismanaged. Key management defines who can control upgrades, funds, and automation—and mistakes here are usually irreversible.
In Web3, losing a key means losing the system.
Types of Keys You May Have
-
Deployer key
Used once to deploy contracts and set initial configuration. -
Upgrade admin key
Controls contract upgrades and critical system changes. -
Treasury key
Manages protocol funds and large transfers. -
Relayer / executor key
Used by automation systems to submit transactions.
Minimum Production-Grade Setup
-
Put admin roles behind a multisig (Safe)
Prevents a single compromised key from taking over the protocol. -
Use hardware wallets for privileged keys
Protects admin and treasury keys from malware and phishing. -
Relayer key in HSM or Vault
Stores automation keys securely with strict access policies. -
Key rotation policies
Limits long-term damage if a key is exposed.
Monitoring & Alerting (Non-Negotiable)
-
Admin function calls
Alerts when upgrades or critical changes are attempted. -
Large fund transfers
Detects unusual or high-value movements early. -
Unusual gas spikes
Signals potential attacks or failed automation loops. -
Failed transaction bursts
Indicates broken logic, RPC issues, or exploit attempts.
10) Observability & Reliability (Web3 Production Rules)
Web3 systems fail silently if you don’t monitor them. Transactions can stall, indexers can lag, relayers can break, and users will only see “something is wrong.” Observability is what turns a fragile protocol into a reliable production system.
What You Must Monitor
-
RPC latency & error rate
Detects slow nodes, rate limits, or provider outages. -
Contract event gaps (missed blocks)
Ensures indexers are not skipping blockchain events. -
Indexer lag (block height difference)
Measures how far indexed data is behind the chain. -
Relayer queue depth
Shows whether automation transactions are backing up. -
Failed transaction reasons
Decode reverts to identify logic errors or gas issues. -
Database performance
Tracks slow queries, locks, and storage pressure. -
Frontend error tracking
Captures user-facing crashes and broken flows.
Tools Commonly Used
-
Sentry
Error tracking for frontend and backend services. -
Prometheus + Grafana
Metrics collection and real-time dashboards. -
Custom block height health checks
Compare chain head vs indexer height continuously. -
Log pipeline (ELK / OpenSearch)
Centralized logs for debugging and audits.
11) Deployment Architecture (Environments)
Web3 systems must be deployed across multiple environments to avoid costly mistakes. A single wrong deployment on mainnet can permanently lock funds or break the protocol. Proper environment separation is a core production discipline, not a convenience.
Use Three Environments
Dev Environment (Local Chain)
-
Uses local blockchains like Anvil or Hardhat.
-
Fast iteration, debugging, and contract testing.
Staging Environment (Testnet)
-
Deployed on testnets like Sepolia or Amoy.
-
Mirrors production behavior without real funds.
Production Environment (Mainnet)
-
Runs on mainnet with real value at risk.
-
Requires full monitoring, alerts, and safeguards.
12) End-to-End Web3 Architecture Flow
A Web3 application works as a coordinated system where wallets, smart contracts, indexers, and backend services each play a specific role. The user experiences a smooth interface, but under the hood, multiple layers interact to ensure security, correctness, and performance.
This flow shows how a single user action travels through the entire Web3 stack.
Step-by-Step Flow
-
User opens the dApp
Frontend loads and initializes Web3 providers. -
User connects wallet
Wallet establishes identity and chain context. -
User signs login message (optional)
Signature-based auth creates a backend session. -
App reads data from indexer / cache
UI fetches fast, queryable blockchain data. -
User initiates a transaction
Frontend builds the contract call. -
Wallet signs → RPC broadcasts
Transaction is authorized and sent to the network. -
Contract emits events
On-chain state changes and logs are produced. -
Indexer consumes events → updates DB
Indexed data is refreshed for fast reads. -
Backend triggers notifications
Emails, push alerts, or webhooks are sent. -
UI shows confirmed state
Frontend reconciles optimistic state with on-chain truth.
FAQ : Web3 Architecture
Web3 refers to the next generation of the internet where applications run on blockchain networks instead of centralized servers. In Web3, users control their assets, identities, and data through cryptographic wallets rather than relying on a single company or platform.
A common example of Web3 is a decentralized exchange (DEX) where users trade tokens directly from their wallets without depositing funds into a centralized platform. NFT marketplaces, blockchain wallets, and decentralized finance (DeFi) apps are also typical Web3 examples.
For beginners, Web3 can be understood as an internet where you log in using a wallet instead of a username and password, and where digital assets like tokens or NFTs are owned directly by you. Transactions and rules are enforced by code on the blockchain rather than by a central authority.
Web2 platforms store user data on centralized servers and control access, monetization, and rules. Web3 shifts ownership and control to users by using blockchains, smart contracts, and decentralized storage, reducing reliance on intermediaries.
Yes, most real Web3 applications still use a backend for tasks like authentication, indexing blockchain data, notifications, rate limiting, and business logic. However, the backend does not control asset ownership or core protocol rules, which remain on-chain.
No, cryptocurrency is just one part of Web3. Web3 also includes decentralized identity, NFTs, DAOs, blockchain-based gaming, data ownership systems, and trustless financial and governance applications beyond simple payments.
Users typically log in by connecting a crypto wallet and signing a message to prove ownership of their address. This signature replaces traditional passwords and allows identity verification without sharing personal credentials.
Smart contracts are self-executing programs stored on the blockchain that define rules, permissions, and asset movement. They act as the core logic layer of Web3 applications, ensuring transparency and trustless execution.
Most Web3 systems are partially decentralized. While core logic and asset ownership may be on-chain, components like frontends, indexing services, and notifications often rely on centralized infrastructure for performance and usability.
Web3 can be safe, but it requires users to manage private keys and understand basic security practices. Unlike traditional apps, there is usually no password recovery, so users must be careful with wallets, approvals, and signing permissions.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







