Key Takeaways
- Web3 wallets serve as the primary interface for digital identity in Web3, functioning as identity anchors, authentication tools, and access control mechanisms beyond simple asset storage [1]
- Digital identity in Web3 shifts from platform-controlled accounts to user-owned cryptographic identities, enabling self-sovereign identity Web3 principles where users control their own credentials
- Web3 identity management relies on public-private key cryptography, where wallet addresses become persistent identifiers across the entire decentralized ecosystem
- Web3 authentication eliminates password dependency through cryptographic message signing, providing stronger security while simplifying user experience across applications
- Crypto wallets in Web3 ecosystem enable identity portability, allowing a single wallet to authenticate across thousands of dApps without creating separate accounts
- Decentralized identity Web3 supports verifiable credentials Web3, enabling users to prove claims about themselves without revealing unnecessary personal information
- Web3 identity verification through wallets provides pseudonymity rather than anonymity, with all on-chain activity publicly visible and potentially linkable to real-world identity
- Security in wallet-based identity means key ownership equals identity ownership, making secure key management and backup practices essential for protecting digital existence
- The convergence of wallets, identity, and user experience positions wallets as the foundational layer for all decentralized internet interaction
What Digital Identity Means in the Web3 Ecosystem?
Digital identity in Web3 ecosystem represents a fundamental departure from how we have understood online identity for decades. Rather than accounts created and controlled by platforms, Web3 identity emerges from cryptographic ownership. Understanding this shift is essential for grasping how wallets become central to everything users do in decentralized networks.
Digital Identity as an Access Layer, Not a User Profile
Traditional digital identity centers on user profiles: collections of information that platforms store about you, including your name, email, preferences, and activity history. Web3 digital identity in Web3 functions differently. It is primarily an access layer that proves you have the right to perform certain actions without necessarily revealing who you are in the traditional sense.
Your wallet address does not contain a profile. It contains proof of control: the ability to sign messages that verify you hold the corresponding private key. This proof of control enables authentication, authorization, and interaction across the decentralized ecosystem. Identity becomes about capability rather than personal information.
Why Identity Is a Core Primitive in Web3 Architecture?
Identity in Web3 is not a feature built on top of the system; it is a foundational primitive that the entire architecture depends upon. Every transaction requires identity (a sender address). Every smart contract interaction requires authentication (a valid signature). Every ownership claim requires proof (key control). Without cryptographic identity, blockchain networks simply cannot function.
This architectural centrality means that Web3 identity management cannot be an afterthought. The way identity works shapes everything else: how users onboard, how applications authenticate, how permissions are granted, and how reputation accumulates. Getting identity right is getting Web3 right.
From Accounts to Cryptographic Identity
The transition from accounts to cryptographic identity represents a power shift. In account-based systems, the platform creates your identity, stores your credentials, and can suspend or delete your access at will. In cryptographic identity, you generate your own keys, control your own access, and no single entity can revoke your identity.
This transition requires new mental models. Your wallet is not like a bank account that the bank controls. It is more like a physical key to a lock that no locksmith can open without your permission. The mathematics of public-key cryptography make this possible, creating identity that is truly self-sovereign.
Important: Digital identity in Web3 places full responsibility on users for key management and security. Unlike traditional systems where forgotten passwords can be reset, lost private keys mean permanent loss of identity and all associated assets. This responsibility is the price of self-sovereignty.
Evolution of Identity Systems: Web2 to Web3
Understanding Web3 identity requires appreciating what came before and why change became necessary. The evolution from Web2 to Web3 identity systems reflects broader shifts in how we think about digital ownership and control.
Platform-Centric Identity Models in Web2
Web2 identity is fundamentally platform-centric. When you create a Facebook account, Google account, or Amazon account, the platform owns that identity. They store your credentials, control your access, and can modify or terminate your account based on their policies. Your identity exists only at their pleasure and only within their ecosystem.
This model served the growth of internet platforms well. It allowed companies to build detailed user profiles, target advertising, and create network effects that locked users in. But it also created problems: data breaches exposing millions of credentials, platforms wielding enormous power over users, and identity fragmentation across dozens of separate accounts.
Limitations of Account-Based Authentication
Account-based authentication suffers from fundamental limitations that no amount of iteration can fully resolve. Passwords are inherently insecure: users choose weak ones, reuse them across sites, and fall for phishing attacks. Centralized credential databases become attractive targets for attackers. Recovery mechanisms like email reset create additional attack surfaces.
Even improvements like two-factor authentication and password managers address symptoms rather than causes. The underlying model of centralized credential storage remains vulnerable. Web3 authentication through cryptographic keys eliminates many of these vulnerabilities by removing the need for centralized credential storage entirely.
Why Decentralized Networks Require Native Identity Layers?
Decentralized networks cannot rely on centralized identity providers without reintroducing the very centralization they aim to eliminate. If a blockchain required Facebook login to participate, it would not be decentralized. Native identity layers built into the protocol itself are essential for maintaining decentralization while enabling meaningful interaction.
The self-sovereign identity Web3 approach solves this by making identity creation permissionless. Anyone can generate a key pair and begin participating. No gatekeepers approve identities. No central authority maintains a registry. Identity emerges from mathematics rather than administrative processes.
The Role of Wallets Beyond Asset Storage
Web3 wallets are commonly understood as tools for storing cryptocurrency, but this description captures only a fraction of their function. Wallets are the user’s interface to the entire decentralized ecosystem, and their role in identity is arguably more important than their role in asset storage.
Wallets as User Interfaces for Blockchain Interaction
Every interaction with a blockchain requires signing a transaction or message with a private key. Wallets provide the interface for this signing process, presenting users with information about what they are authorizing and enabling them to approve or reject. Without wallets, users would need to manually construct and sign raw cryptographic operations.
Modern Web3 wallets handle connection requests from dApps, display transaction details in human-readable formats, estimate gas costs, and manage multiple accounts and networks. They have evolved from simple key storage into sophisticated applications that mediate all blockchain interaction. Organizations building professional crypto exchange platforms recognize wallets as critical infrastructure for user experience.
Wallets as Identity Anchors in Decentralized Networks
Your wallet address becomes your identity anchor in decentralized identity Web3 systems. It is the persistent identifier that accumulates your transaction history, asset ownership, credential attestations, and reputation signals. Applications recognize you by your wallet address, and your on-chain identity follows you wherever you go.
This anchoring function makes wallets fundamentally different from traditional authentication tokens. A session token expires; a wallet address persists. A login cookie is platform-specific; a wallet address works everywhere. The crypto wallets in Web3 ecosystem serve as portable, permanent identity infrastructure.
How Wallets Replace Traditional Login Mechanisms?
When you connect your wallet to a dApp, you are replacing the entire traditional login flow. There is no username to remember, no password to type, no account to create. The dApp presents a message, your wallet signs it, and authentication is complete. This process takes seconds and requires no trust in the application’s credential storage.
The security improvement is substantial. Phishing attacks become harder because there is no password to steal. Database breaches do not expose credentials because no credentials are stored. The authentication is cryptographically verified rather than dependent on password hashing and comparison.
How Wallets Enable Identity Without Central Authorities?
The elimination of central authorities in Web3 identity is one of its most revolutionary aspects. Understanding the cryptographic mechanisms that make this possible reveals why wallet-based identity is fundamentally more secure and user-controlled than traditional systems.
Public-Private Key Pairs as Identity Foundations
At the heart of Web3 identity is public-key cryptography. You generate a private key (a random number known only to you) and derive a public key (shareable information that identifies you). The mathematical relationship between these keys enables signing and verification without revealing the private key.
This creates identity that no central authority issues or controls. You do not apply for a wallet address; you generate one. No registry approves your identity; mathematics validates it. The security of this identity rests on the computational difficulty of deriving private keys from public information, a problem that current technology cannot solve.
Wallet Addresses as Persistent Digital Identifiers
Your wallet address, derived from your public key, becomes your persistent identifier across the Web3 ecosystem. Unlike usernames that platforms can reassign or email addresses that providers can terminate, a wallet address exists as long as the blockchain exists. No entity can revoke or reassign it.
This persistence enables new patterns impossible in Web2: reputation that accumulates over years, credentials that remain verifiable indefinitely, and identity that survives the failure of any particular platform. Web3 identity verification does not depend on any service remaining operational.
Trust Minimization Through Cryptographic Proofs (High-Level)
Traditional authentication requires trusting multiple parties: the application storing credentials, the authentication service verifying them, and the network transmitting them. Cryptographic authentication in Web3 minimizes this trust requirement. The mathematics proves identity without requiring trust in any particular service.
When you sign a message with your private key, anyone with your public key can verify that signature came from you. They do not need to contact any server, check any database, or trust any authority. The proof is self-contained and mathematically verifiable. This trust minimization is foundational to Web3’s security model.
| Aspect | Web2 Authentication | Web3 Wallet Authentication |
|---|---|---|
| Identity Creation | Platform creates account | User generates keys |
| Credential Storage | Centralized database | User device only |
| Verification Method | Password comparison | Cryptographic signature |
| Portability | Platform-specific | Works everywhere |
| Recovery | Email/phone reset | Seed phrase only |
| Control | Platform-controlled | User-controlled |
Authentication in Web3 Using Wallets
Web3 authentication represents a paradigm shift from credential-based to signature-based verification. Understanding this flow clarifies why wallet-based authentication is both more secure and more user-friendly than traditional methods.
Wallet-Based Authentication Flow Explained
The Web3 authentication flow begins when a user clicks “Connect Wallet” on a dApp. The application generates a unique challenge message (often including a timestamp and nonce to prevent replay attacks). The user’s wallet displays this message and asks for approval to sign it. Upon approval, the wallet creates a cryptographic signature using the private key.
The dApp receives this signature and verifies it against the wallet’s public key. If verification succeeds, the user is authenticated. The entire process happens client-side without transmitting any secret information. The dApp never sees the private key, only the proof that the user controls it.
Message Signing vs Username-Password Systems
Message signing fundamentally differs from username-password authentication. Passwords are shared secrets: both the user and the service know them, creating opportunities for interception and database theft. Signatures prove knowledge of a secret without revealing it, maintaining security even if the verifier is compromised.
This asymmetry provides significant security benefits. A compromised dApp cannot extract your private key from signatures you have provided. Phishing sites cannot capture credentials because you never transmit them. The mathematical properties of digital signatures make this security possible.
Eliminating Password Dependency in Web3 Apps
Web3 applications that fully embrace wallet-based authentication have no passwords at all. Users do not create accounts; they connect wallets. There is nothing to remember, nothing to store securely, nothing to reset when forgotten. The wallet is the credential.
This elimination of passwords removes entire categories of vulnerabilities and support burdens. No more password reset emails. No more credential stuffing attacks. No more users locked out of accounts. The simplification is both a security improvement and a user experience enhancement.
Authorization and Access Control Using Wallet Identity
Beyond authentication (proving who you are), Web3 wallet identity enables sophisticated authorization (determining what you can do). The ownership model of blockchain enables access control mechanisms impossible in traditional systems.
Ownership-Based Access in Decentralized Applications
Web3 applications can grant access based on what you own rather than who you are. Holding a particular token might grant access to a community. Owning a specific NFT might unlock premium features. Having a certain amount of stake might enable governance participation. This ownership-based model is native to blockchain.
The verification is trustless: the application checks on-chain state to confirm ownership. No API calls to authorization servers. No database queries to permission tables. The blockchain itself serves as the source of truth for access rights.
Role of Tokens and NFTs in Identity-Based Permissions
Tokens and NFTs extend wallet identity with verifiable attributes. A “KYC Passed” soulbound token might enable access to regulated services. A “DAO Member” NFT might grant voting rights. A “Course Completed” credential might prove qualification. These attestations are portable, verifiable, and user-controlled.
This model supports verifiable credentials Web3 approaches where credentials are cryptographically signed attestations that users store and present. The credentials follow the user across applications, creating a portable reputation and qualification system.
Smart Contracts as Automated Identity Gatekeepers
Smart contracts can enforce access control rules automatically and trustlessly. A contract might require ownership of a specific NFT before allowing function calls. It might check token balances before enabling withdrawals. It might verify credentials before granting permissions. These rules execute deterministically without human gatekeepers.
This automation removes arbitrary discretion from access control. Either you meet the on-chain criteria or you do not. The rules are transparent and equally applied. This transparency and fairness are core benefits of Web3 identity management systems.
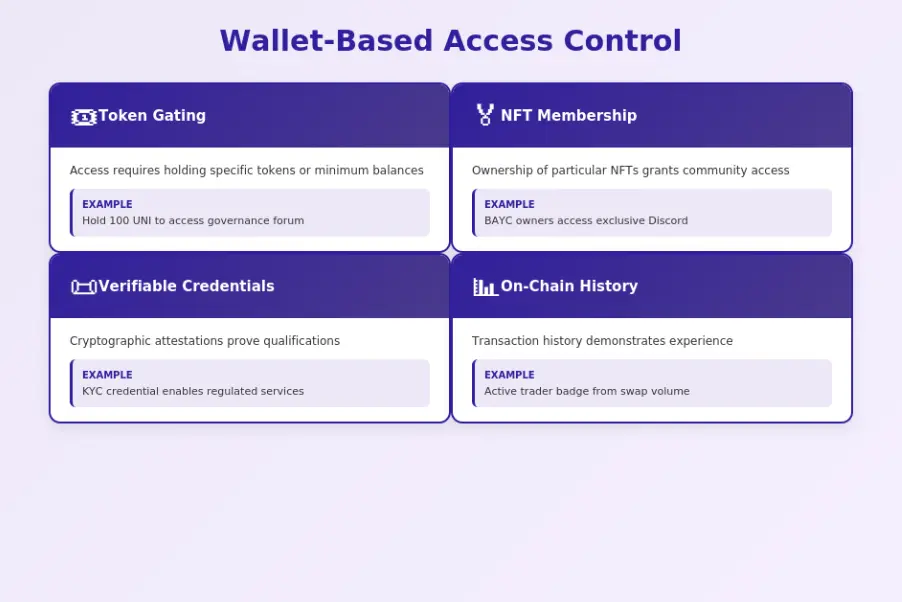
Wallet-Based Access Control Methods
- Token Gating: Access requires holding specific tokens or minimum balances
- NFT Membership: Ownership of particular NFTs grants community access
- Credential Verification: Verifiable credentials attest to qualifications
- On-Chain History: Transaction history demonstrates experience or reputation
- Multi-Sig Requirements: Actions require approval from multiple wallets
Digital Identity Portability Across Web3 Applications
Identity portability is one of Web3’s most powerful features. The ability to carry your identity, reputation, and credentials across applications creates network effects and user experiences impossible in siloed Web2 platforms.
Single Wallet Identity Across Multiple dApps
A single wallet address works across every dApp on its blockchain. Your Ethereum address authenticates you to DeFi protocols, NFT marketplaces, DAOs, games, and social platforms. No new accounts, no new passwords, no verification processes. One identity serves the entire ecosystem.
This portability eliminates friction that Web2 users experience constantly: creating accounts, verifying emails, setting up profiles, remembering yet another password. Web3 users connect once and access everything. The reduction in friction supports adoption and engagement.
Identity Persistence Across Chains and Platforms
Multi-chain ecosystems extend portability further. Tools and standards enable identity to work across different blockchains. The same seed phrase can generate addresses on Ethereum, Polygon, Arbitrum, and other networks. Your identity conceptually persists even as you interact with different chains.
Cross-chain identity standards are still evolving, but the trajectory points toward seamless multi-chain identity. Users will increasingly expect their Web3 identity to work everywhere, just as they expect their email address to work with any providers servers.
Why Portability Is Essential for Open Ecosystems?
Open ecosystems require portable identity to function. If each dApp required its own identity system, the ecosystem would fragment into silos like Web2. Portable identity enables the composability that makes Web3 powerful: protocols building on protocols, applications integrating with applications, all recognizing the same users.
This portability also protects users from platform risk. If a dApp shuts down, your identity persists. If a platform changes policies, you take your reputation elsewhere. Identity portability is the foundation of user sovereignty in decentralized systems.
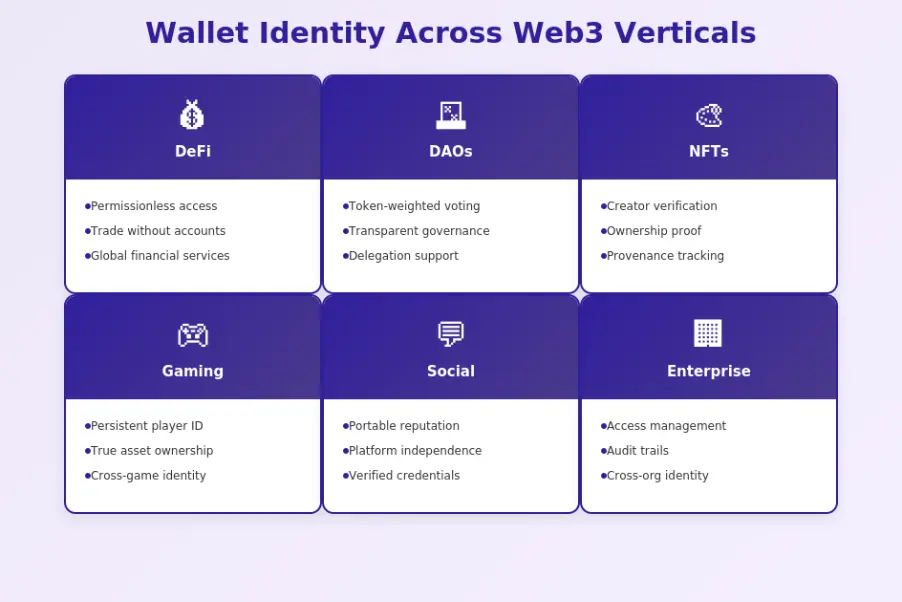
Wallet-Based Identity in Key Web3 Verticals
Different Web3 verticals leverage wallet-based identity in distinctive ways, each demonstrating the flexibility and power of decentralized identity approaches.
DeFi Platforms and Permissionless User Access
DeFi platforms epitomize permissionless access through wallet identity. Anyone with a wallet can trade on decentralized exchanges, provide liquidity, borrow and lend, or participate in yield strategies. No applications, no credit checks, no approval processes. The wallet is your passport to global financial services.
This permissionless model has enabled financial access for millions who lack traditional banking relationships. Teams building comprehensive trading platform infrastructure understand how wallet-based access transforms user onboarding and global reach.
DAOs and Wallet Identity in Governance
Decentralized Autonomous Organizations use wallet identity for governance participation. Token holders vote on proposals using their wallets. Voting power typically corresponds to token holdings, verifiable on-chain. This creates transparent governance where participation and influence are visible to all.
Wallet identity also enables delegation, where token holders assign their voting power to trusted representatives. The delegation is on-chain and revocable, creating accountability in governance that traditional systems struggle to achieve.
NFTs, Gaming, and Virtual Worlds Identity
Gaming and virtual worlds use wallet identity to create persistent player identities that own in-game assets. Your game achievements, virtual property, and digital collectibles are tied to your wallet, not a game account. If a game shuts down, you retain ownership of portable assets.
This ownership model enables new economic possibilities: trading game items across platforms, using NFTs as identity in multiple virtual worlds, and building reputation that follows you across gaming experiences. Wallet-based identity makes true digital ownership possible.
| Vertical | Identity Use | Key Benefit |
|---|---|---|
| DeFi | Permissionless access to financial services | Global access without gatekeepers |
| DAOs | Token-weighted governance voting | Transparent, verifiable participation |
| NFT Markets | Creator and collector identity | Provenance and ownership proof |
| Gaming | Persistent player identity and assets | True digital ownership |
| Social | Portable profiles and reputation | Platform-independent identity |
Privacy Considerations in Wallet-Centric Identity
Privacy in Web3 identity is nuanced. The system provides pseudonymity but not anonymity, creating privacy properties that users must understand to manage their exposure appropriately.
Pseudonymity vs Real-World Identity
Wallet addresses are pseudonymous: they identify accounts without inherently revealing real-world identity. You can participate in Web3 under a wallet address that no one connects to your legal name. This pseudonymity provides meaningful privacy for many use cases.
However, pseudonymity can be pierced. If you ever link your wallet to your identity (through KYC, doxxing, or behavioral analysis), that link becomes permanent. The entire history of that wallet is then associated with you. Maintaining pseudonymity requires consistent operational security.
On-Chain Transparency and User Awareness
Every transaction on public blockchains is visible to everyone, forever. Your wallet’s entire history of transfers, interactions, and holdings is public information. Blockchain explorers make this data easily accessible. Anyone can analyze your financial activity if they know your address.
This transparency is a feature for accountability but a challenge for privacy. Users must understand that blockchain activity is not confidential. Privacy-preserving techniques exist but require deliberate effort and often additional complexity.
Identity Exposure Risks Through Wallet Activity
Even without explicit doxxing, wallet activity can reveal identity through correlation. Patterns of transactions, timing of activity, connections to known addresses, and on-ramp/off-ramp transactions can all contribute to identification. Sophisticated analysis can often link pseudonymous addresses to real identities.
Users concerned about privacy should understand these risks and take appropriate measures: using multiple wallets for different purposes, understanding when activities create linkable patterns, and considering privacy-enhancing tools when available.
Security Implications of Wallet-Based Identity
The security model of wallet-based identity differs fundamentally from centralized authentication. Understanding these implications helps users protect their digital existence in Web3.
Key Ownership as Identity Ownership
In Web3, owning your private key means owning your identity. There is no separation between “controlling an account” and “being the account holder.” Whoever holds the key is the identity. This creates both empowerment and responsibility: true ownership, but also true accountability for security.
This model eliminates certain attack vectors (no passwords to steal from databases) while creating others (direct theft of keys). The security focus shifts from protecting centralized systems to protecting individual key storage.
Risks of Key Loss and Wallet Compromise
Losing access to your private key means losing your identity permanently. Unlike forgetting a password, there is no recovery process, no customer support, no reset mechanism. The mathematical nature of cryptographic keys makes recovery impossible without the original key or seed phrase.
Wallet compromise is equally devastating. An attacker with your private key becomes you for all blockchain purposes. They can transfer assets, sign messages, and interact with applications as your identity. The irreversibility of blockchain transactions means stolen assets are rarely recoverable.
Importance of Secure Wallet Design for Identity
Given these stakes, secure wallet design becomes critical. Hardware wallets that keep keys offline provide stronger security than software wallets. Multi-signature configurations distribute risk across multiple keys. Social recovery mechanisms offer middle-ground approaches between self-custody and traditional account recovery.
The wallet industry continues innovating on security while maintaining usability. Account abstraction, smart contract wallets, and other advances aim to provide the security of self-custody with the recovery options users expect from traditional services.
Interoperability and Standards Supporting Wallet Identity
Standards and interoperability enable wallet-based identity to work across the fragmented Web3 ecosystem. These shared conventions create the seamless experience users increasingly expect.
Role of Open Standards in Wallet-Based Identity
Open standards like EIP-1193 (provider API), EIP-4361 (Sign-In with Ethereum), and W3C Verifiable Credentials define how wallets and applications communicate. These standards ensure that any compliant wallet works with any compliant application, creating the interoperability that makes portable identity practical.
Standard adherence also improves security by reducing implementation variation. Well-vetted standards have been scrutinized by the community, reducing the risk of security flaws that might exist in proprietary approaches.
Cross-dApp Compatibility and Ecosystem Growth
Cross-dApp compatibility through standards creates positive network effects. Users can choose any wallet that meets their needs, knowing it will work with applications they want to use. Applications can focus on their core functionality without building custom authentication for each wallet.
This compatibility accelerates ecosystem growth by reducing fragmentation. New applications immediately have access to the entire user base of compatible wallets. New wallets immediately work with the entire ecosystem of compatible applications.
Identity as Shared Infrastructure, Not Platform Feature
Web3 positions identity as shared infrastructure that no single platform owns or controls. Unlike Web2 where identity is a platform feature (often used for lock-in), Web3 identity is a public good that benefits the entire ecosystem. This framing supports the open, permissionless nature of decentralized networks.
Why Wallet-Centric Digital Identity Is Critical for Web3 Adoption?
Wallet-centric identity is not just technically elegant; it is essential for Web3’s mainstream adoption. The user experience improvements it enables will determine whether decentralized applications reach beyond early adopters.
Improving User Experience in Decentralized Applications
Wallet-based authentication dramatically improves user experience compared to traditional account creation. One-click connection replaces lengthy signup forms. No email verification, no password requirements, no profile creation. Users go from interested to interacting in seconds rather than minutes.
This streamlined experience is especially valuable for applications where users want to try before committing. Lower friction means higher conversion and engagement. Wallet-centric identity makes dApps more accessible and usable.
Reducing Friction for New Web3 Users
New user onboarding remains Web3’s biggest challenge. Wallet-centric identity, while requiring initial wallet setup, ultimately reduces ongoing friction. Once users have a wallet, they are authenticated across the ecosystem. The investment in learning wallet usage pays dividends across every subsequent interaction.
Improved wallet UX continues closing the gap with traditional authentication. Better mobile wallets, social recovery options, and embedded wallet solutions make the initial hurdle lower while preserving the benefits of self-sovereign identity.
Enabling Trust in Permissionless Environments
Permissionless environments face unique trust challenges. Without gatekeepers, how do users know who they are dealing with? Wallet-based identity, combined with on-chain history and verifiable credentials, provides trust signals that work in trustless environments.
A wallet’s transaction history demonstrates experience. Verified credentials attest to qualifications. Token holdings prove stake. These signals, all anchored to wallet identity, enable trust without centralized verification. This trust infrastructure is essential for permissionless systems to function effectively.
The Expanding Role of Wallets in the Future Web3 Stack
The role of wallets continues expanding as Web3 matures. What began as key storage has evolved into identity infrastructure and is converging toward becoming the primary interface for decentralized internet use.
Wallets as Identity, Access, and Interaction Hubs
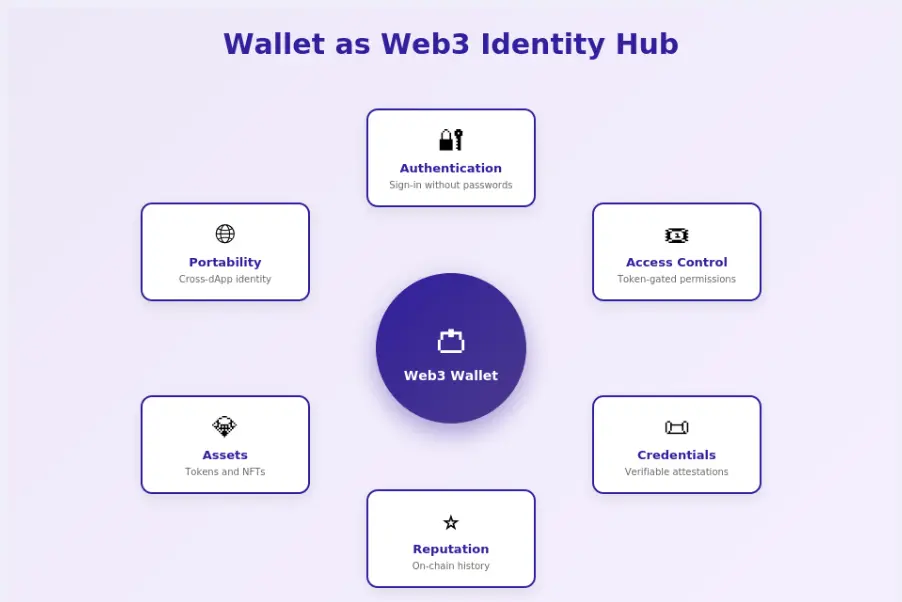
Modern wallets are becoming comprehensive hubs that manage identity, control access, and mediate interactions. They display credentials, manage permissions, show activity history, and provide interfaces for complex multi-application workflows. The wallet becomes the control center for your digital existence.
This hub model centralizes user control while maintaining decentralization at the protocol level. Users have one place to manage their presence across the ecosystem, while no single entity controls the underlying infrastructure.
Convergence of Wallets, Identity, and User Experience
The lines between wallets, identity systems, and user experience layers are blurring. Wallets are becoming browsers for the decentralized web. Identity protocols are integrating wallet functionality. User experience frameworks are building wallet-native interfaces. This convergence creates more seamless experiences.
The future likely sees wallet functionality embedded throughout digital experiences, sometimes visible as explicit wallet applications and sometimes invisible as authentication happens automatically. The identity layer becomes ambient rather than explicit.
Wallets as the Foundation of Decentralized Internet Use
Wallets are positioning to become as fundamental to the decentralized internet as browsers were to the traditional web. Just as browsers became the window through which users experienced the web, wallets are becoming the window through which users experience Web3. They are the essential piece of user-side infrastructure.
This foundational role makes wallet innovation critically important. Better wallets mean better Web3 adoption. Secure wallets mean secure users. User-friendly wallets mean broader accessibility. The wallet layer will largely determine Web3’s success or failure as a mainstream technology.
| Phase | Stage | User Action | Identity Outcome |
|---|---|---|---|
| 1 | Wallet Creation | Generate keys, secure seed phrase | Identity established |
| 2 | First Connection | Connect to dApp, sign message | Authentication proven |
| 3 | Activity Building | Transact, collect, participate | History accumulated |
| 4 | Credential Collection | Receive attestations, badges, credentials | Reputation formed |
| 5 | Cross-Platform Use | Use same identity across ecosystem | Portable identity realized |
Build Web3 Identity Solutions
Integrate wallet-based authentication and identity into your decentralized applications.
Web3 wallets have evolved from simple cryptocurrency storage to become the foundation of digital identity in decentralized ecosystems. They enable authentication without passwords, authorization without gatekeepers, and identity that users truly own. As the Web3 ecosystem matures, wallets will continue expanding their role as the primary interface between users and the decentralized internet. Understanding this expanding role is essential for anyone building or participating in the Web3 future.
Frequently Asked Questions
Digital identity in Web3 is based on cryptographic key pairs rather than usernames and passwords stored by centralized services. Your wallet address becomes your persistent identifier across the decentralized ecosystem. When you connect your wallet to a dApp, you prove your identity by signing a message with your private key, eliminating the need for traditional authentication systems.
Self-sovereign identity (SSI) is an identity model where individuals own and control their digital identities without depending on centralized authorities. In Web3, your wallet gives you complete control over your identity: you decide which applications can access your information, you can prove claims about yourself without revealing unnecessary data, and your identity persists across platforms.
Web3 wallets replace username-password authentication with cryptographic signature verification. Instead of creating accounts on each platform, users connect their wallet and sign a challenge message. The dApp verifies the signature against the wallet’s public key, confirming identity without passwords, databases of credentials, or centralized authentication servers.
Yes, one of Web3’s key benefits is identity portability. A single wallet address works across thousands of dApps on the same blockchain and can be used on multiple chains. Your identity, reputation, assets, and credentials follow you wherever you go, eliminating the need to create separate accounts for each application.
NFTs can represent identity-related information including membership badges, credentials, achievements, and access rights. Ownership of specific NFTs can grant access to exclusive communities, unlock features in applications, or prove qualifications. NFTs effectively turn identity attributes into portable, verifiable digital assets.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







