Key Takeaways
- Sign-in with Ethereum (SIWE) is an EIP-4361 standard enabling passwordless Web3 authentication using wallet signatures instead of traditional credentials.
- SIWE authentication eliminates password vulnerabilities while providing self-custodial identity control for users across USA, UK, UAE, and Canadian markets.
- The SIWE login flow involves wallet connection, server-generated nonce, message signing without gas fees, signature verification, and session creation.
- SIWE nonce generation prevents replay attacks by creating unique single-use tokens that must be validated on the backend before establishing sessions.
- Web3 authentication solutions using SIWE support MetaMask, WalletConnect, and other major wallets for enterprise-grade passwordless Web3 login experiences.
- SIWE session management can utilize JWT tokens or cookie-based approaches with proper CSRF protection and domain binding validation.
- Implementation requires frontend libraries like wagmi and ethers.js combined with backend verification using the official SIWE library from login.xyz.
- SIWE authentication differs from basic wallet connection by requiring cryptographic signature verification to prove address ownership and prevent spoofing.
- Security best practices include nonce validation, domain binding checks, expiration time enforcement, and protection against phishing through wallet domain verification.
- Passwordless authentication through SIWE is optimal for NFT platforms, DeFi dashboards, DAO voting systems, and Web3 gaming applications requiring secure identity.
Web3 authentication represents a fundamental shift in how users prove their identity online. Traditional username and password systems have dominated the internet for decades, but they carry inherent vulnerabilities including data breaches, password reuse, and reliance on centralized identity providers. Sign-in with Ethereum (SIWE) offers a revolutionary alternative that leverages cryptographic signatures to enable secure, passwordless authentication.
Our agency has spent over eight years building web3 platform solutions for clients across the USA, UK, UAE, and Canada. Through this experience, we’ve witnessed the evolution of Web3 authentication from experimental implementations to production-grade standards. SIWE authentication has emerged as the definitive protocol for passwordless Web3 login, standardized through EIP-4361 and adopted by leading platforms worldwide.
This comprehensive guide explores every aspect of SIWE login, from fundamental concepts to advanced implementation strategies. Whether you’re building NFT marketplaces, DeFi protocols, or enterprise Web3 applications, understanding Sign-in with Ethereum is critical for delivering secure, user-friendly authentication experiences that meet modern security standards.
Web2 Authentication vs Web3 Authentication
| Aspect | Web2 Authentication | Web3 Authentication |
|---|---|---|
| Identity Storage | Centralized databases controlled by service providers | Decentralized blockchain addresses with user-controlled keys |
| Authentication Method | Username and password verification against database | Cryptographic signature verification using wallet keys |
| Trust Model | Users trust service providers to secure credentials | Users maintain custody of keys through personal wallets |
| Vulnerability Profile | Database breaches, password reuse, credential stuffing | Phishing attacks, private key compromise, signature requests |
| Recovery Mechanism | Password reset via email or security questions | Seed phrase backup or hardware wallet recovery procedures |
| Interoperability | Limited to OAuth providers or proprietary systems | Universal wallet identity across all SIWE-compatible platforms |
Why Wallets Became the New Identity Layer?
Cryptocurrency wallets evolved beyond simple transaction tools to become comprehensive identity platforms. This transformation occurred because wallets inherently solve the fundamental authentication problem: proving ownership of a unique identifier through cryptographic signatures. Every blockchain address functions as a globally unique identity that cannot be duplicated, forged, or centrally controlled.
The wallet-as-identity model gained traction across USA, UK, UAE, and Canadian markets because it eliminates registration friction while maintaining security. Users no longer create new accounts for each platform; instead, they connect existing wallets that already contain their transaction history, token holdings, and NFT collections. This creates instant personalization opportunities while reducing onboarding complexity.
Furthermore, wallets enable composable identity by linking on-chain credentials, achievements, and reputation across applications. When users authenticate with SIWE, platforms can immediately access verifiable information about token ownership, governance participation, and historical interactions without requiring manual profile creation or third-party verification services.
Key Terms: Wallet Address, Private Key, Signature, Session
Wallet Address: A 42-character hexadecimal identifier (0x…) derived from public key cryptography that serves as your unique identity on Ethereum and EVM-compatible blockchains.
Private Key: A cryptographic secret that proves ownership of a wallet address, enabling message signing and transaction authorization without ever being shared with applications.
Signature: A cryptographic proof generated by signing a message with your private key, mathematically verifiable by anyone holding your public address without exposing the key itself.
Session: A temporary authenticated state maintained through cookies or JWT tokens after successful SIWE verification, allowing continued access without repeated signature requests.
SIWE Meaning in Simple Words
Think of SIWE authentication as a digital ID card that you control entirely. When visiting a website that supports Sign-in with Ethereum, you present your wallet address as identification. The site generates a unique challenge message asking you to prove ownership of that address. Your wallet signs this message using cryptography that only the true address owner can produce. The website verifies the signature mathematically without ever seeing your private key, confirming your identity.
This passwordless Web3 login eliminates the need for traditional registration flows. No username selection, password creation, email verification, or security question setup. Users simply connect their wallet and sign a message. The entire process completes in seconds while providing cryptographic security stronger than conventional password-based systems.
For users familiar with Web2 OAuth flows like “Sign in with Google,” SIWE offers similar convenience with fundamentally different security properties. Instead of delegating identity management to Google or Facebook, users maintain complete control through self-custody of their private keys. This creates a truly decentralized authentication mechanism aligned with Web3 principles.
Why SIWE is a Standard (EIP-4361)?
EIP-4361 achieved “Final” status in the Ethereum Improvement Proposal process, signifying widespread consensus and production readiness. This formal standardization ensures that SIWE implementations across different platforms maintain consistent behavior, message formats, and security characteristics. Wallet providers can confidently build SIWE support knowing the specification won’t change arbitrarily.
The standardization process involved extensive security review, user testing, and implementation feedback from major ecosystem participants. The resulting specification uses ABNF grammar to define message structure unambiguously, enabling both human readability and machine parsing. This dual nature allows wallets to present clear signing interfaces while maintaining strict validation rules.
Adoption across USA, UK, UAE, and Canadian markets has accelerated because EIP-4361 provides legal and regulatory clarity. Organizations can reference a formal specification when implementing authentication systems, simplifying compliance documentation and security audits. The standard status also encourages wallet providers to prioritize SIWE support, creating a positive feedback loop of adoption.
SIWE vs “Connect Wallet”
Many applications conflate wallet connection with authentication, creating significant security vulnerabilities. Simply connecting a wallet through protocols like WalletConnect or MetaMask integration does not prove ownership of the connected address. Malicious wallets or man-in-the-middle attacks could provide addresses the user doesn’t control, leading to unauthorized access or impersonation.
SIWE authentication adds a critical verification step: signature-based proof of ownership. After connecting, users must sign a SIWE message with their private key. The application verifies this signature cryptographically, confirming that the person authenticating actually possesses the keys controlling that address. This prevents address spoofing attacks where attackers claim ownership of addresses they don’t control.
For read-only blockchain interactions, simple wallet connection suffices. However, any application handling sensitive data, financial transactions, or privileged actions must implement proper SIWE authentication. The signature verification step is non-negotiable for security, transforming wallet connection from a simple provider interface into a robust authentication mechanism backed by cryptographic proof.
Step 1: User Connects Wallet (MetaMask / WalletConnect)
The authentication journey begins when users click a “Connect Wallet” or “Sign In” button. This triggers wallet detection logic that identifies available providers through EIP-6963 for browser extensions or WalletConnect for mobile wallet connections. Modern implementations should support multiple connection methods simultaneously to maximize compatibility across devices and user preferences.
Frontend Code: Connect Wallet with wagmi
import { useAccount, useConnect } from 'wagmi'
import { MetaMaskConnector } from 'wagmi/connectors/metaMask'
import { WalletConnectConnector } from 'wagmi/connectors/walletConnect'
function ConnectButton() {
const { address, isConnected } = useAccount()
const { connect } = useConnect()
const connectMetaMask = () => {
connect({
connector: new MetaMaskConnector(),
})
}
const connectWalletConnect = () => {
connect({
connector: new WalletConnectConnector({
options: {
projectId: 'YOUR_PROJECT_ID',
},
}),
})
}
if (isConnected) {
return Connected: {address}
}
return (
)
}MetaMask connections utilize the browser extension’s injected ethereum provider, requesting account access through the eth_requestAccounts RPC method. WalletConnect establishes connections via QR code scanning or deep linking, creating encrypted communication channels between applications and mobile wallets. Both methods return the user’s wallet address, which becomes the foundation for subsequent SIWE authentication.
Step 2: Server Generates SIWE Message + Nonce
Once wallet connection completes, the frontend requests a SIWE nonce from the backend API. SIWE nonce generation must use cryptographically secure random number generation to produce at least 8 alphanumeric characters with sufficient entropy. This nonce serves as a unique session identifier preventing replay attacks where attackers reuse previously captured signatures.
Backend Code: Generate Nonce (Node.js)
import crypto from 'crypto'
import { SiweMessage } from 'siwe'
// Nonce generation endpoint
app.get('/api/siwe/nonce', async (req, res) => {
const nonce = crypto.randomBytes(16).toString('hex')
// Store nonce in Redis with 10 minute expiration
await redis.setex(`siwe:nonce:${nonce}`, 600, '1')
res.json({ nonce })
})
// Create SIWE message endpoint
app.post('/api/siwe/message', async (req, res) => {
const { address, chainId, nonce } = req.body
const message = new SiweMessage({
domain: req.hostname,
address: address,
statement: 'Sign in with Ethereum to the app.',
uri: `https://${req.hostname}`,
version: '1',
chainId: chainId,
nonce: nonce,
issuedAt: new Date().toISOString(),
expirationTime: new Date(Date.now() + 600000).toISOString() // 10 min
})
res.json({ message: message.prepareMessage() })
})The backend constructs a complete SIWE message incorporating the nonce, connected wallet address, application domain, request URI, protocol version, chain ID, and current timestamp. The message follows strict ABNF grammar defined in EIP-4361, ensuring consistent formatting across implementations.
Step 3: User Signs the Message (No Gas Fee)
The frontend presents the SIWE message to the user’s wallet for signature using the personal_sign RPC method. This off-chain signing operation occurs locally within the wallet without broadcasting any blockchain transactions. Users pay zero gas fees for SIWE authentication, removing economic friction from the login process.
Frontend Code: Sign SIWE Message
import { useSignMessage, useAccount, useNetwork } from 'wagmi'
import { useState, useEffect } from 'react'
function SignInWithEthereum() {
const { address } = useAccount()
const { chain } = useNetwork()
const { signMessageAsync } = useSignMessage()
const [nonce, setNonce] = useState(null)
const [loading, setLoading] = useState(false)
// Fetch nonce when component mounts
useEffect(() => {
const fetchNonce = async () => {
const response = await fetch('/api/siwe/nonce')
const data = await response.json()
setNonce(data.nonce)
}
fetchNonce()
}, [])
const handleSignIn = async () => {
try {
setLoading(true)
// Get SIWE message from backend
const messageResponse = await fetch('/api/siwe/message', {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
body: JSON.stringify({
address,
chainId: chain?.id,
nonce
})
})
const { message } = await messageResponse.json()
// Sign the message
const signature = await signMessageAsync({ message })
// Send to backend for verification
await verifySignature(message, signature)
} catch (error) {
console.error('Sign-in failed:', error)
} finally {
setLoading(false)
}
}
const verifySignature = async (message, signature) => {
const response = await fetch('/api/siwe/verify', {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
credentials: 'include', // Important for cookies
body: JSON.stringify({ message, signature })
})
if (response.ok) {
console.log('Authentication successful!')
window.location.href = '/dashboard'
}
}
return (
)
}The resulting signature is a cryptographic proof that can only be generated by the private key controlling the specified wallet address. This signature, typically 132 hexadecimal characters representing an ECDSA signature, gets transmitted back to the frontend application for backend verification.
Step 4: Backend Verifies Signature
Backend verification represents the most critical security operation in SIWE authentication. The server receives the signed message and signature from the frontend, then performs multiple validation steps including nonce verification, timestamp checking, and cryptographic signature validation.
Backend Code: Verify SIWE Signature
import { SiweMessage } from 'siwe'
app.post('/api/siwe/verify', async (req, res) => {
try {
const { message, signature } = req.body
// Parse the SIWE message
const siweMessage = new SiweMessage(message)
// Verify the signature
const fields = await siweMessage.verify({
signature,
domain: req.hostname,
nonce: siweMessage.nonce,
time: new Date().toISOString()
})
// Check if nonce exists and hasn't been used
const nonceExists = await redis.get(`siwe:nonce:${siweMessage.nonce}`)
if (!nonceExists) {
return res.status(401).json({
error: 'Invalid or expired nonce'
})
}
// Mark nonce as used (delete it)
await redis.del(`siwe:nonce:${siweMessage.nonce}`)
// Verify domain matches
if (siweMessage.domain !== req.hostname) {
return res.status(401).json({
error: 'Domain mismatch'
})
}
// Additional validation: check expiration
if (new Date(siweMessage.expirationTime) < new Date()) {
return res.status(401).json({
error: 'Message expired'
})
}
// Verification successful - create session
const address = fields.data.address
// Store user session
req.session.siwe = {
address: address,
chainId: siweMessage.chainId,
authenticatedAt: new Date().toISOString()
}
res.json({
success: true,
address: address
})
} catch (error) {
console.error('Verification error:', error)
res.status(401).json({
error: 'Signature verification failed',
details: error.message
})
}
})The cryptographic verification process uses elliptic curve cryptography to recover the signer’s address from the signature and message hash. If the recovered address matches the address claimed in the SIWE message, verification succeeds. Libraries like the official SIWE package handle this complex cryptographic operation.
Step 5: Session Creation (Cookies / JWT)
Upon successful signature verification, the backend establishes an authenticated session for the user. This can be implemented using either cookie-based sessions with server-side storage or JWT tokens for stateless authentication.
Backend Code: Session Management Options
import session from 'express-session'
import RedisStore from 'connect-redis'
import jwt from 'jsonwebtoken'
// Option 1: Cookie-based session with Redis
app.use(session({
store: new RedisStore({ client: redis }),
secret: process.env.SESSION_SECRET,
resave: false,
saveUninitialized: false,
cookie: {
secure: true, // HTTPS only
httpOnly: true, // Prevent JavaScript access
sameSite: 'lax', // CSRF protection
maxAge: 24 * 60 * 60 * 1000 // 24 hours
}
}))
// Option 2: JWT-based authentication
function createJWT(address, chainId) {
return jwt.sign(
{
address: address,
chainId: chainId,
type: 'siwe'
},
process.env.JWT_SECRET,
{
expiresIn: '24h',
issuer: 'your-app-name'
}
)
}
// In verification endpoint (JWT approach)
app.post('/api/siwe/verify', async (req, res) => {
// ... verification code from Step 4 ...
// After successful verification:
const token = createJWT(address, siweMessage.chainId)
res.json({
success: true,
token: token,
address: address
})
})
// Middleware to protect routes
function requireAuth(req, res, next) {
// Cookie-based
if (req.session.siwe) {
return next()
}
// JWT-based
const token = req.headers.authorization?.replace('Bearer ', '')
if (token) {
try {
const decoded = jwt.verify(token, process.env.JWT_SECRET)
req.user = decoded
return next()
} catch (error) {
return res.status(401).json({ error: 'Invalid token' })
}
}
res.status(401).json({ error: 'Not authenticated' })
}
// Protected route example
app.get('/api/dashboard', requireAuth, (req, res) => {
res.json({
address: req.session.siwe?.address || req.user?.address,
message: 'Welcome to your dashboard!'
})
})Session expiration policies should balance security and user experience. Cookie-based sessions provide strong security by keeping session data on the server, while JWT tokens enable stateless authentication. Both approaches work effectively for SIWE authentication when properly configured with appropriate security measures.
Complete Implementation Example
Frontend Stack: React/Next.js with wagmi hooks for wallet connection and message signing, managing authentication state through context.
Backend Stack: Node.js/Express with siwe library for verification, Redis for nonce storage, and session management middleware.
Security Layer: HTTPS enforcement, CSRF protection via SameSite cookies, domain binding validation, and nonce replay prevention.
Domain, Address, Statement, URI, Version
The domain field specifies the RFC 3986 authority requesting authentication, typically the hostname of the application. This field enables wallet verification that signature requests originate from legitimate sources rather than phishing sites. Wallets implementing proper SIWE support compare the domain field against the actual requesting origin, warning users about mismatches that indicate potential attacks.
Address represents the Ethereum wallet address performing authentication, formatted as a 42-character hexadecimal string beginning with 0x. Statement provides optional human-readable context about the authentication request, often containing terms of service acceptance or purpose descriptions. The URI field identifies the resource scope for authentication, typically matching the application’s base URL but potentially specifying particular paths or resources.
Version indicates the SIWE specification version, currently always “1” for EIP-4361 compliance. Future specification revisions may increment this version number, allowing backward compatibility while introducing new features. Applications should validate version numbers during signature verification, rejecting messages claiming unsupported specification versions to maintain security consistency.
Chain ID, Nonce, Issued At, Expiration Time
Chain ID specifies the EIP-155 network identifier binding the session to a particular blockchain. Ethereum mainnet uses chain ID 1, while networks like Polygon (137), Arbitrum (42161), and Base (8453) have unique identifiers. Including chain ID prevents signature reuse across networks and ensures proper contract verification for smart contract wallets that rely on chain-specific logic.
The nonce field contains the cryptographically random string generated by the server, typically 16+ characters of hexadecimal data. SIWE nonce generation quality directly impacts security against replay attacks. Weak random number generation enabling nonce prediction would allow attackers to forge valid authentication messages. Backend systems must use cryptographic random number generators and track nonce usage to prevent reuse.
Issued At records the RFC 3339 timestamp when the message was created, typically the current server time. Expiration Time sets an optional deadline after which the signature becomes invalid, commonly 10-30 minutes from issuance. Together, these timestamps create a validity window preventing both premature and expired signature acceptance. Backend verification must validate current time falls within this window using timezone-aware comparison.
Example of a Real SIWE Message
Here is exactly what a SIWE message looks like when it appears in your wallet:
example.com wants you to sign in with your Ethereum account: 0x742d35Cc6634C0532925a3b844Bc9e7595f8aB2C Sign in to access your dashboard and manage your NFTs. URI: https://example.com/login Version: 1 Chain ID: 1 Nonce: n4bQgYhMfWWaL28eGT2J8w Issued At: 2024-01-15T10:30:00.000Z Expiration Time: 2024-01-15T10:45:00.000Z
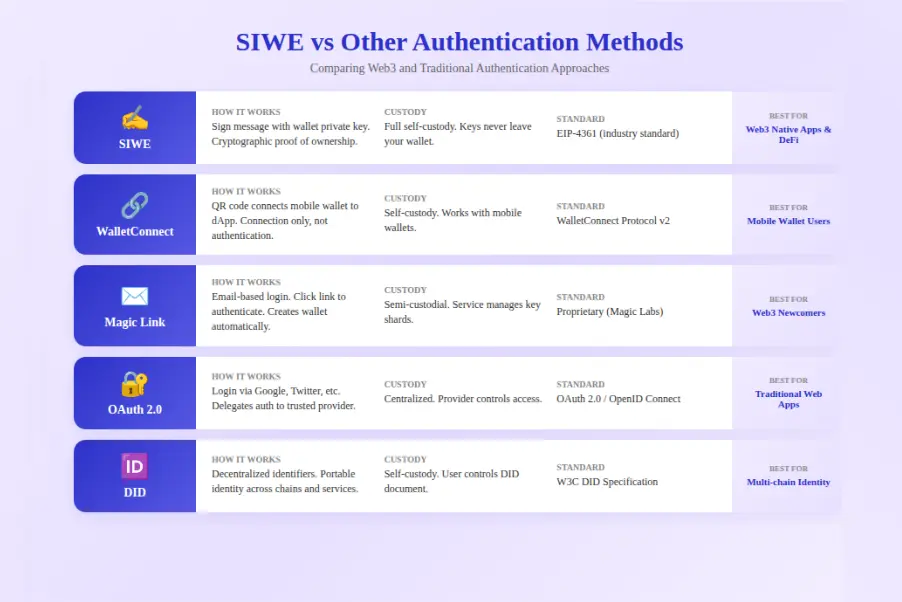
SIWE vs WalletConnect Login
WalletConnect and SIWE are complementary, not competing. WalletConnect is a connection protocol that helps mobile wallet users connect to desktop websites via QR code. But connection alone is not authentication. You should use WalletConnect FOR the connection step, then SIWE FOR the authentication step. Together they provide mobile-friendly, fully authenticated Web3 login.
SIWE vs Magic Link / Email Login
Magic Link creates a wallet for users automatically when they sign up with email. This is great for mainstream users who do not have wallets yet. However, Magic Link is semi-custodial because the service manages key shards. Users do not have full self-custody. SIWE requires existing wallets but provides true self-custody. Choose based on your audience: crypto-natives prefer SIWE, mainstream users may prefer Magic Link.
SIWE vs OAuth (Google Login)
OAuth with Google, Apple, or other providers is familiar and trusted. But it is completely centralized. Google controls your identity. They can disable your account. Your identity is not portable. SIWE provides decentralized, self-sovereign identity. You own your wallet forever. Many applications support both, letting users choose their preference.
SIWE vs DID (Decentralized Identity)
DIDs (Decentralized Identifiers) are a broader identity standard that works across multiple blockchains and systems. SIWE is specifically for Ethereum wallet authentication. DIDs are more portable but also more complex and still early stage. For Ethereum-focused applications, SIWE is simpler and more mature. DIDs make sense for applications requiring cross-chain or cross-platform identity.
8 Essential SIWE Security Standards
1. Cryptographic Nonces: Generate nonces using crypto.randomBytes(32) or equivalent. Never use predictable values like timestamps or counters.
2. Single-Use Nonces: Delete or invalidate each nonce immediately after successful verification. Never allow any nonce to be used twice.
3. Domain Validation: Always verify the domain in signed messages matches your application exactly. Reject mismatched domains even with valid signatures.
4. Short Expiration: Set message expiration to 5-15 minutes maximum. Shorter windows mean less time for attackers to exploit intercepted messages.
5. Secure Sessions: Use HTTP-only cookies with Secure and SameSite flags. If using JWT, store in memory or HTTP-only cookies, never localStorage.
6. CSRF Protection: Implement CSRF tokens for all authentication endpoints. Validate Origin and Referer headers on sensitive requests.
7. Chain ID Check: Validate the chain ID matches your supported networks. Reject signatures from unexpected chains to prevent confusion.
8. Logging & Monitoring: Log all authentication attempts (success and failure) for security monitoring and incident investigation.
Nonce Validation
The nonce is your primary defense against replay attacks. A replay attack is when an attacker intercepts a valid signature and tries to use it again. With proper nonce handling, this is impossible. Generate each nonce using cryptographically secure randomness. Store it server-side with the user’s address and an expiration timestamp. When verifying a signature, check the nonce exists, belongs to that address, and has not expired. Most importantly, delete the nonce immediately after successful verification. This ensures every signature can only be used exactly once.
Domain Binding & URI Validation
Domain binding prevents cross-site signature theft. Imagine a phishing site that looks exactly like yours. They trick users into signing SIWE messages for their domain. Without domain validation, they could use those signatures on your real site. With domain binding, signatures for “fake-site.com” are useless on “real-site.com.” Always check the domain field matches your exact domain. Also validate the URI if you have multiple applications. Reject any signature where these fields do not match perfectly.
Session Security (JWT vs Cookie Sessions)
After SIWE verification, you need to maintain the user’s session. HTTP-only cookies are the most secure option because JavaScript cannot access them, preventing XSS attacks from stealing tokens. Set the Secure flag so cookies only transmit over HTTPS. Set SameSite to Strict or Lax to prevent CSRF. If you use JWT tokens, store them in memory (not localStorage) or in HTTP-only cookies. Implement token refresh mechanisms so users do not need to re-sign frequently. Set reasonable session durations balancing security with user convenience.
CSRF Protection in SIWE
Cross-Site Request Forgery (CSRF) attacks trick your browser into making requests to sites where you are logged in. Implement CSRF tokens that must be included with requests to authentication endpoints. Check Origin and Referer headers match your domain. The SIWE nonce mechanism provides some CSRF protection since attackers cannot predict valid nonces. However, adding dedicated CSRF tokens provides defense in depth for comprehensive protection.
Preventing Phishing & Fake Sign Requests
Phishing remains a threat even with SIWE. Attackers create fake websites that look identical to legitimate ones. They request SIWE signatures hoping users will not check the domain carefully. Educate your users to always verify the domain in the SIWE message matches the website they are visiting. Use clear, recognizable statements in your messages. Never request signatures from unexpected popups. Consider displaying verification information users can check. Remember that user education is as important as technical security.
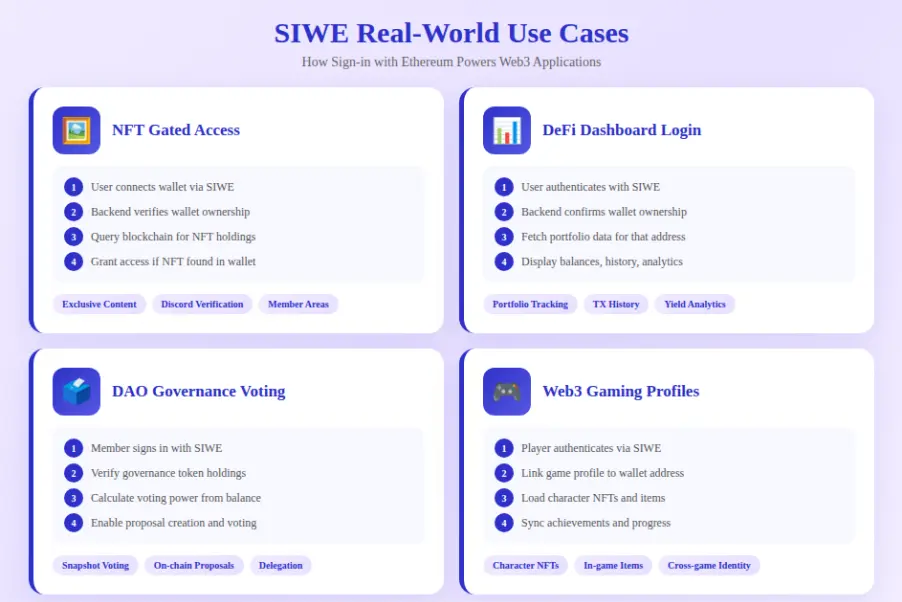
When SIWE is the Best Choice?
SIWE excels in applications where wallet addresses serve as primary user identifiers and where on-chain credentials or token holdings inform authorization decisions. DeFi protocols, NFT marketplaces, DAO platforms, and blockchain gaming applications benefit from SIWE’s tight integration between authentication and blockchain identity. Users already possess wallets for these applications, eliminating onboarding friction while providing security through cryptographic verification.
Organizations prioritizing decentralization and user sovereignty should implement SIWE as it aligns authentication architecture with broader Web3 principles. Self-custody, censorship resistance, and protocol standardization make SIWE the natural choice for applications committed to decentralized values. The EIP-4361 specification provides regulatory clarity valuable for enterprises across USA, UK, UAE, and Canadian markets implementing blockchain authentication systems.
Technical teams with blockchain expertise find SIWE implementation straightforward using established libraries and clear documentation. The active ecosystem of wallet providers, authentication libraries, and tooling from wagmi, ethers.js, and login.xyz reduces integration risk. Mature security patterns and extensive production deployments provide confidence in SIWE’s robustness for mission-critical authentication requirements.
What’s Next for Web3 Authentication?
The Web3 authentication landscape continues evolving with several emerging trends building upon SIWE foundations. Account abstraction through ERC-4337 enables sophisticated wallet architectures supporting social recovery, gasless transactions, and enhanced security features while maintaining SIWE compatibility. Smart contract wallets using EIP-1271 signature verification become increasingly prevalent, requiring continued SIWE implementation attention to proper contract wallet support.
Cross-chain authentication represents growing focus as users maintain identities across multiple blockchain networks. SIWE’s chain ID parameter supports multi-chain scenarios, but applications need infrastructure tracking authenticated addresses across different networks. Unified authentication experiences spanning Ethereum, Layer 2s, and alternative chains will become increasingly important as blockchain ecosystem fragmentation continues.
Integration between SIWE and traditional identity systems through standards like OpenID Connect enables hybrid authentication architectures. These bridges help enterprises adopt Web3 authentication incrementally, maintaining compatibility with existing identity infrastructure while adding wallet-based authentication capabilities. Such hybrid approaches will likely define enterprise Web3 adoption patterns across regulated industries in USA, UK, UAE, and Canadian markets.[1]
Ready to Implement SIWE Authentication?
Partner with our experienced team to build secure, production-grade Web3 authentication systems. We’ve implemented SIWE solutions for clients worldwide over 8+ years.
Frequently Asked Questions
Sign-in with Ethereum (SIWE) is an EIP-4361 standard that lets users prove wallet ownership using cryptographic signatures. Users connect a wallet, receive a nonce-based message, sign it without gas fees, and the backend verifies it before creating a session.
Yes. SIWE is generally more secure than passwords because it avoids storing shared secrets in databases. It uses signatures, nonces to prevent replay attacks, and domain validation. Security depends on correct nonce handling, timestamps, sessions, and phishing protection.
Yes, SIWE supports smart contract wallets using EIP-1271 verification. Instead of standard ECDSA recovery, the backend calls the wallet contract’s isValidSignature method. Most SIWE libraries support this automatically with correct chain configuration.
If you lose wallet access, you can’t sign messages again, so you may lose account access permanently. Unlike passwords, SIWE has no default reset. Apps can offer recovery via linked wallets, email backup login, or migration options.
Yes. SIWE includes a chain ID, so it supports Ethereum, Polygon, Arbitrum, and other EVM networks. Apps must validate chain IDs properly, handle network switching, and ensure smart contract wallet verification happens on the correct chain.
Generate secure random nonces (preferably 16+ characters) using cryptographic functions like crypto.randomBytes. Store them with short expiry (5-10 minutes), validate before signature checks, and mark them as used atomically to prevent reuse or race conditions.
Yes. SIWE can integrate with Auth0, Firebase, or custom identity systems using hybrid login models. Wallet signatures are verified first, then the system issues sessions or tokens. This enables Web3 login while keeping traditional email/social authentication.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.






