Key Takeaways
- Reentrancy attacks in smart contracts exploit external call vulnerabilities, allowing attackers to repeatedly withdraw funds before balance updates complete.
- The DAO hack in 2016 demonstrated how reentrancy attacks in smart contracts could drain $60 million, fundamentally changing blockchain security practices.
- Enterprises across USA, UK, UAE, and Canada implement the checks-effects-interactions pattern to prevent reentrancy attacks in smart contracts.
- OpenZeppelin’s ReentrancyGuard modifier provides battle-tested protection against reentrancy attacks in smart contracts for production deployments.
- Reentrancy attacks in smart contracts remain the leading cause of DeFi exploits, accounting for over $1 billion in losses across blockchain history.
- Professional security audits specifically test for reentrancy attacks in smart contracts using tools like Slither, Mythril, and manual code review.
- Cross-function and cross-contract reentrancy attacks in smart contracts require comprehensive analysis beyond single-function vulnerability scanning.
- Future smart contract security will leverage formal verification to mathematically prove absence of reentrancy attacks in smart contracts.
Introduction to Reentrancy Attacks in Smart Contracts
Reentrancy attacks in smart contracts represent one of the most devastating vulnerabilities in blockchain security, responsible for billions of dollars in losses across the cryptocurrency ecosystem. With over eight years of experience securing smart contracts for enterprises across USA, UK, UAE, and Canadian markets, our agency has witnessed how these attacks continue to threaten even sophisticated DeFi protocols. Understanding the mechanics, prevention strategies, and detection methods for reentrancy attacks in smart contracts is essential for any organization building on blockchain technology. This comprehensive guide provides the technical depth and practical insights needed to protect your smart contract deployments.
What Is a Reentrancy Attack in Blockchain Security?
Reentrancy attacks in smart contracts occur when a malicious contract exploits the ability to call back into a vulnerable function before its execution completes. When a contract sends Ether or calls an external contract, execution temporarily passes to the recipient. If the vulnerable contract updates its state after the external call, the attacker can re-enter the same function and execute it repeatedly, draining funds before the balance is properly updated. This fundamental flaw in execution flow creates opportunities for attackers to bypass intended security checks.[1]
The Technical Mechanics Behind Reentrancy Attacks
Understanding the technical mechanics of reentrancy attacks in smart contracts requires examining how the Ethereum Virtual Machine handles external calls. When a contract executes call(), send(), or transfer(), control passes to the recipient address. If that address is a contract with a receive() or fallback() function, that code executes before returning control. The attacking contract can use this execution window to call back into the vulnerable function, creating a recursive loop that exploits the unchanged state.
Technical Note: The gas stipend of 2300 provided by transfer() was designed to prevent reentrancy but is no longer considered sufficient protection.
Types of Reentrancy Attacks in Smart Contracts
| Attack Type | Mechanism | Complexity |
|---|---|---|
| Single-Function | Recursive calls to same function | Low |
| Cross-Function | Calls between related functions | Medium |
| Cross-Contract | Exploits multiple contracts | High |
| Read-Only | Manipulates view during callback | High |
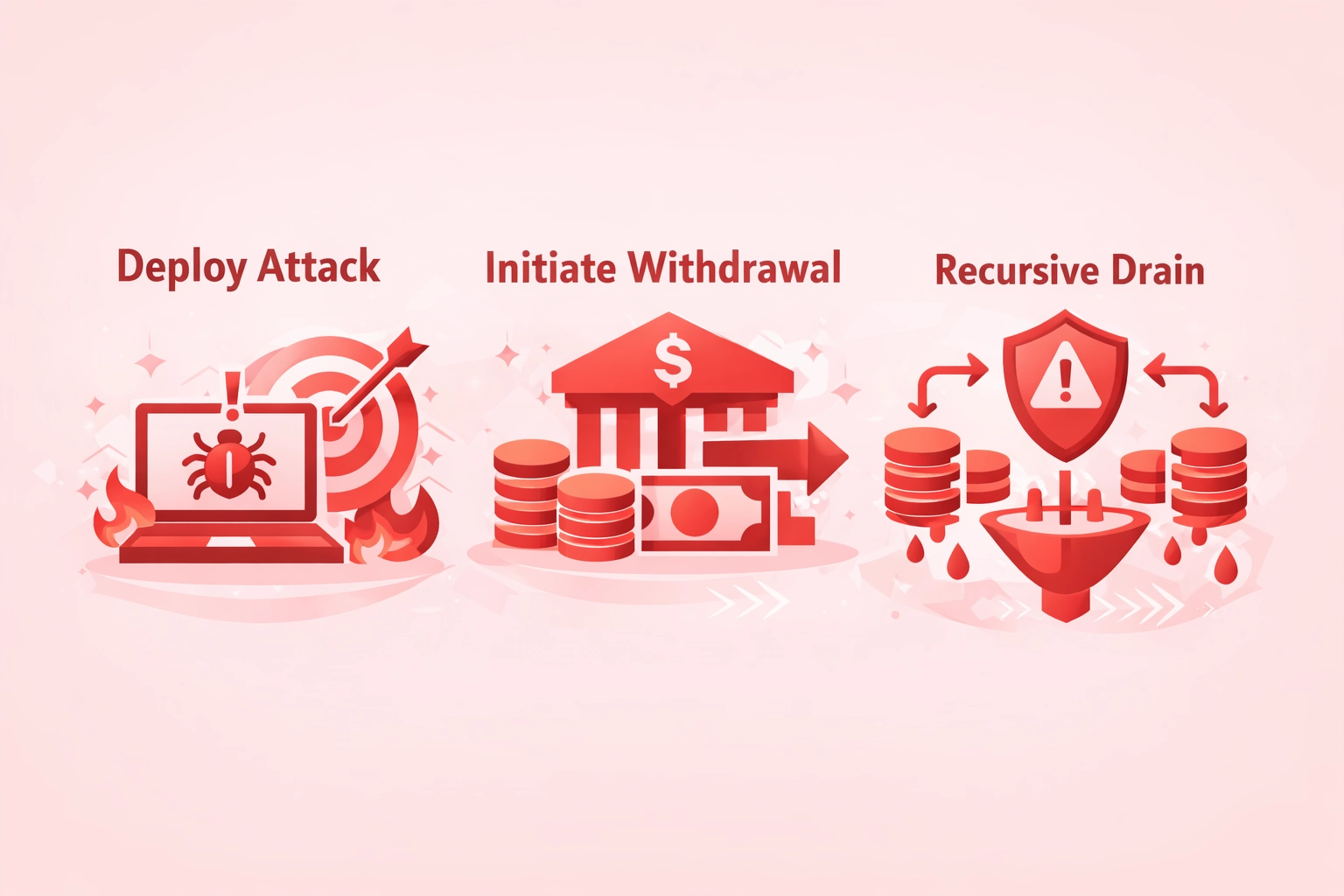
Step-by-Step Breakdown of a Reentrancy Exploit
Step 1: Deploy Attack
- Create malicious contract
- Implement fallback function
- Fund with initial deposit
- Target vulnerable contract
Step 2: Initiate Withdrawal
- Call withdraw function
- Pass balance checks
- Trigger Ether transfer
- Receive callback control
Step 3: Recursive Drain
- Fallback calls withdraw again
- Balance not yet updated
- Repeat until drained
- Extract all funds
Real-World Examples of Reentrancy Attacks in Blockchain History
| Incident | Year | Loss | Impact |
|---|---|---|---|
| The DAO | 2016 | $60 Million | Ethereum hard fork |
| Uniswap/Lendf.Me | 2020 | $25 Million | Protocol shutdown |
| Cream Finance | 2021 | $130 Million | Multiple exploits |
| Grim Finance | 2021 | $30 Million | Vault drainage |
Impact of Reentrancy Attacks on Blockchain Security
Reentrancy attacks in smart contracts have fundamentally shaped blockchain security practices. The DAO incident led to Ethereum’s controversial hard fork, creating Ethereum Classic as a separate chain. These attacks have driven the adoption of security standards, audit requirements, and secure coding patterns. Enterprises across USA, UK, UAE, and Canada now mandate reentrancy testing before any smart contract deployment.
Total Losses
Major Incidents
Vulnerability Type
Financial and Trust Risks Caused by Reentrancy Vulnerabilities
Beyond immediate financial losses, reentrancy attacks in smart contracts cause lasting damage to protocol reputation and user trust. Projects experiencing reentrancy exploits often see permanent user exodus, difficulty raising future capital, and regulatory scrutiny. Insurance providers now specifically evaluate reentrancy protection when underwriting DeFi protocols, making these vulnerabilities a direct business risk for organizations operating in USA, UK, UAE, and Canadian markets.[2]
How Reentrancy Attacks Affect DeFi Protocols
DeFi protocols face heightened exposure to reentrancy attacks in smart contracts due to their composable nature and high-value transactions. Lending protocols, decentralized exchanges, and yield aggregators all process external calls that create reentrancy opportunities. Flash loan attacks frequently combine with reentrancy to amplify damage, allowing attackers to borrow millions, exploit vulnerabilities, and repay loans in single transactions without capital requirements.
Reentrancy Vulnerability Detection Lifecycle
Code Review Initiation
Identify all external call points and state-changing functions in the smart contract codebase.
Static Analysis
Run automated tools like Slither and Mythril to detect potential reentrancy patterns.
Call Graph Analysis
Map execution flows to identify cross-function and cross-contract reentrancy vectors.
Fuzzing Tests
Use Echidna or Foundry to generate random inputs testing for unexpected reentrancy behavior.
Manual Verification
Expert auditors manually verify findings and search for complex attack scenarios.
Proof of Concept
Create exploit demonstrations to validate severity and confirm vulnerability existence.
Remediation
Implement fixes using reentrancy guards and checks-effects-interactions pattern.
Re-Audit Verification
Confirm all reentrancy vulnerabilities are resolved before deployment approval.
Best Practices to Prevent Reentrancy Attacks
CEI Pattern
- Checks first
- Effects second
- Interactions last
- State before calls
Reentrancy Guards
- OpenZeppelin modifier
- Mutex locking
- State flag checking
- Function-level protection
Pull Payments
- User-initiated withdrawals
- Escrow patterns
- Claim mechanisms
- Reduced attack surface
Secure Smart Contract Design Patterns Against Reentrancy
Designing contracts resistant to reentrancy attacks in smart contracts requires architectural patterns that eliminate vulnerability by design. The withdrawal pattern separates accounting from transfers, maintaining user balances that they must explicitly claim. The commit-reveal pattern for sensitive operations prevents attackers from exploiting transaction ordering. These patterns, combined with OpenZeppelin’s tested implementations, provide robust protection against reentrancy attacks in smart contracts.

Reentrancy Protection Selection Criteria
Contract Complexity
- External call count
- Cross-contract interactions
- Callback implementations
- Composability level
Value at Risk
- Total Value Locked
- Transaction volumes
- Asset types managed
- User fund exposure
Gas Considerations
- Guard overhead
- Pattern efficiency
- User experience
- Cost optimization
Tools and Auditing Techniques for Reentrancy Protection
| Tool | Type | Reentrancy Detection |
|---|---|---|
| Slither | Static Analysis | Built-in detectors |
| Mythril | Symbolic Execution | Path analysis |
| Echidna | Fuzzing | Property testing |
| Securify | Formal Verification | Pattern matching |
Industry Standards for Preventing Reentrancy Attacks in Smart Contracts
Standard 1: Always update state variables before making external calls to eliminate reentrancy opportunities.
Standard 2: Implement OpenZeppelin ReentrancyGuard on all functions that make external calls or transfer value.
Standard 3: Use pull payment patterns instead of push payments to minimize external call risks.
Standard 4: Require professional security audits with explicit reentrancy testing before any mainnet deployment.
Standard 5: Test cross-function and cross-contract reentrancy scenarios beyond simple single-function analysis.
Standard 6: Monitor deployed contracts for suspicious recursive call patterns indicating potential attack attempts.
Future of Smart Contract Security and Reentrancy Mitigation
The future of preventing reentrancy attacks in smart contracts lies in advanced formal verification, language-level protections, and automated security tooling. New smart contract languages like Vyper include built-in reentrancy protection. Formal verification tools are becoming more accessible, allowing mathematical proofs of reentrancy absence. AI-powered audit tools will detect complex attack patterns beyond current static analysis capabilities.
With eight years of experience protecting smart contracts across USA, UK, UAE, and Canadian markets, our agency anticipates that reentrancy attacks in smart contracts will remain a threat requiring vigilant attention. However, improved tooling, standardized patterns, and mandatory audits are significantly reducing successful exploits. Organizations prioritizing security from the design phase will best protect their users and assets.
Protect Your Smart Contracts from Reentrancy Attacks
Our security experts identify and eliminate reentrancy vulnerabilities before attackers can exploit your smart contracts.
Frequently Asked Questions
Reentrancy attacks in smart contracts occur when a malicious contract repeatedly calls back into a vulnerable function before the original execution completes. This exploit allows attackers to drain funds by manipulating state updates that happen after external calls, bypassing balance checks.
Reentrancy attacks in smart contracts pose severe threats because they can drain entire contract balances in single transactions. The DAO hack lost $60 million through this vulnerability. These attacks undermine user trust and can devastate DeFi protocols managing billions in assets.
Protection against reentrancy attacks in smart contracts requires implementing the checks-effects-interactions pattern, using reentrancy guards, and updating state variables before external calls. OpenZeppelin’s ReentrancyGuard modifier provides tested protection used by enterprises across USA, UK, UAE, and Canada.
The checks-effects-interactions pattern prevents reentrancy attacks in smart contracts by ordering operations: first validate conditions (checks), then update state (effects), and finally make external calls (interactions). This ensures state changes complete before any callback opportunity exists.
Notable reentrancy attacks in smart contracts include The DAO hack (2016, $60M), Uniswap/Lendf.Me attack (2020, $25M), and Cream Finance exploit (2021, $130M). These incidents demonstrate the persistent threat reentrancy poses to blockchain protocols regardless of market maturity.
Yes, reentrancy attacks in smart contracts remain possible in Solidity 0.8.0 and newer. While these versions include overflow protection, they do not automatically prevent reentrancy. Secure coding patterns and reentrancy guards remain essential for all Solidity versions.
Tools detecting reentrancy attacks in smart contracts include Slither, Mythril, Securify, and Echidna. Professional auditors use these alongside manual review. Enterprises should combine automated scanning with expert analysis for comprehensive protection against reentrancy vulnerabilities.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







