Key Takeaways
- Privacy coins in Web3 provide essential financial confidentiality through cryptographic techniques that hide sender addresses, recipient addresses, and transaction amounts from public view
- Core privacy technologies including zero-knowledge proofs, ring signatures, and stealth addresses enable confidential transactions while maintaining blockchain integrity and consensus
- Web3 privacy solutions protect users from transaction surveillance, targeted theft, front-running attacks, and commercial espionage that transparent blockchains enable
- Privacy coins enable censorship-resistant payments where users can transact without third-party approval or the ability for authorities to freeze or seize funds
- Decentralized finance privacy allows confidential lending, borrowing, and trading that protects strategies from competitors and prevents manipulation based on position visibility
- Regulatory challenges require balancing privacy with compliance through selective disclosure mechanisms that allow auditing without compromising everyday transaction privacy
- Privacy-first blockchain infrastructure is becoming essential as Web3 handles increasingly sensitive personal and financial data requiring confidentiality
- The future of Web3 security and privacy points toward privacy layers integrating across mainstream blockchains rather than remaining isolated in specialized coins
Introduction to Privacy Coins in Web3 Ecosystems
The promise of blockchain technology includes decentralization, transparency, and trustless transactions. Yet this transparency creates a paradox: while openness enables verification and trust, it also exposes every transaction to global surveillance. Privacy coins in Web3 resolve this tension by providing financial confidentiality that traditional banking takes for granted while preserving the decentralization and verifiability that make blockchain valuable.
As Web3 ecosystems mature beyond experimental technology into infrastructure for real economic activity, the need for privacy becomes increasingly critical. Individuals require protection from criminals who might target visible wealth. Businesses need confidentiality for competitive transactions. Institutions demand privacy for proprietary trading strategies. Privacy coins and Web3 privacy solutions address these fundamental needs that transparent blockchains cannot satisfy.
Understanding Privacy in Web3
Privacy in decentralized networks differs fundamentally from traditional financial privacy and requires specific technological solutions.
Importance of Privacy in Decentralized Networks
Privacy in decentralized networks protects users from risks that emerge specifically from blockchain transparency. When transaction histories are publicly visible, adversaries can analyze spending patterns, identify high-value targets, and link pseudonymous addresses to real identities through various techniques. Businesses face competitive intelligence threats when competitors can monitor their blockchain activity. Privacy is not merely about hiding information but about maintaining the practical security and commercial confidentiality that functional economies require.
Beyond security, privacy enables the freedom to transact without surveillance that has historically been considered a fundamental right. The ability to make purchases, donations, or investments without creating permanent public records supports personal autonomy that many consider essential to free society.
Privacy Challenges in Transparent Blockchains
Transparent blockchains like Bitcoin and Ethereum record every transaction permanently and publicly, creating comprehensive financial surveillance archives. Blockchain analysis companies have developed sophisticated tools that link addresses, cluster wallets, trace fund flows, and connect blockchain activity to real-world identities. Even without direct identity links, patterns of activity can reveal sensitive information about users’ lives, relationships, and behaviors.
These challenges extend beyond individual privacy to systemic issues. Front-running bots monitor pending transactions to extract value from visible intentions. Traders cannot implement strategies without competitors observing their positions. The very transparency that enables trustless verification becomes a vulnerability when applied to financial activity requiring confidentiality.
What Are Privacy Coins
Privacy coins represent a category of cryptocurrencies specifically designed to provide transaction confidentiality.
Definition of Privacy Coins
Privacy coins are cryptocurrencies that implement cryptographic techniques to hide transaction details including sender addresses, recipient addresses, and transaction amounts. Unlike transparent cryptocurrencies where all data is publicly visible, privacy coins ensure that while transactions are verified and recorded on the blockchain, the specific details remain confidential. This privacy can be mandatory for all transactions or optional based on user preference, depending on the specific coin’s implementation.
Evolution of Privacy-Focused Cryptocurrencies
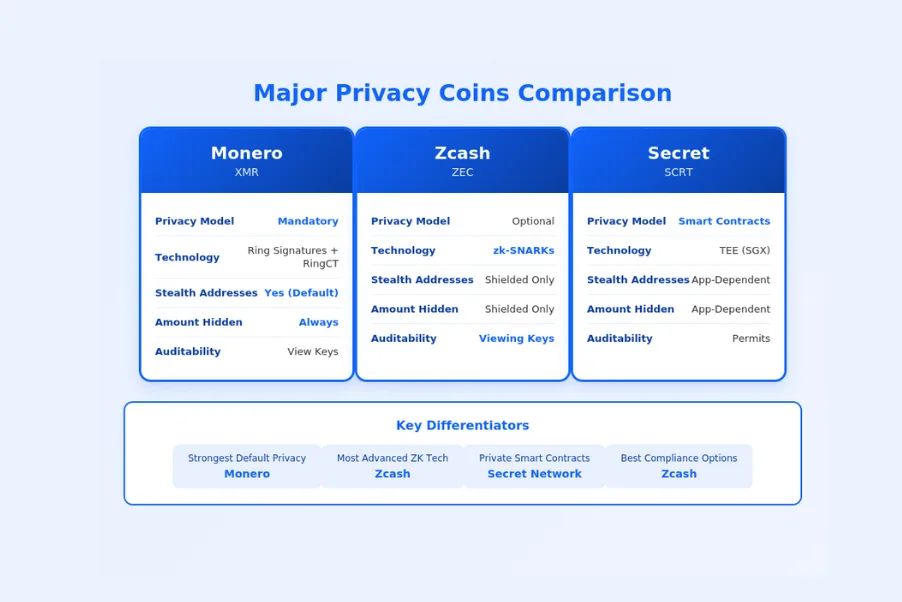
Privacy-focused cryptocurrencies evolved from early recognition that Bitcoin’s transparency created serious privacy limitations. Early solutions like coin mixing services provided limited privacy through transaction obfuscation. Dedicated privacy coins emerged with Monero in 2014, implementing ring signatures and stealth addresses for default privacy. Zcash followed in 2016 with zero-knowledge proof technology enabling mathematically provable privacy. Subsequent developments continue advancing privacy technology while addressing usability, performance, and regulatory considerations.
How Privacy Coins Work in Web3
Privacy coins employ sophisticated cryptographic mechanisms to achieve transaction confidentiality while maintaining blockchain integrity.
Core Technologies Behind Privacy Coins
Several foundational technologies enable privacy in cryptocurrency transactions.
Zero-Knowledge Proofs (ZKPs)
Zero-knowledge proofs represent the most powerful privacy technology available, allowing verification that a statement is true without revealing any information beyond the validity itself. In privacy coins, ZKPs prove that a transaction is valid, that the sender has sufficient funds, and that no double-spending occurs, all without revealing who sent what amount to whom. This mathematical approach provides the strongest privacy guarantees currently achievable, though it requires significant computational resources for proof generation.[1]
Different ZKP implementations offer various tradeoffs. zk-SNARKs provide compact proofs with fast verification but require trusted setup ceremonies. zk-STARKs eliminate trusted setup and resist quantum attacks but generate larger proofs. Ongoing research continues improving efficiency and accessibility of ZKP technology for broader application.
Ring Signatures and Stealth Addresses
Ring signatures enable a user to sign a transaction on behalf of a group, making it computationally infeasible to determine which group member actually signed. In privacy coins like Monero, each transaction includes multiple possible signers from the blockchain, obscuring the actual sender among decoy inputs. Observers cannot determine which input represents the real spend, providing plausible deniability for all transactions.[2]
Stealth addresses generate unique one-time addresses for each transaction, preventing observers from linking multiple payments to the same recipient. Even when sending to a published address, the actual on-chain transaction uses a derived address that only the recipient can identify and spend from. This technique breaks the link between public addresses and transaction history.
| Technology | What It Hides | Privacy Level | Notable Coins |
|---|---|---|---|
| Zero-Knowledge Proofs | Sender, receiver, amount | Highest | Zcash, Iron Fish, Aleo |
| Ring Signatures | Sender identity | High | Monero |
| Stealth Addresses | Receiver linkability | High | Monero, Haven |
| RingCT | Transaction amounts | High | Monero |
| CoinJoin/Mixing | Transaction graph | Medium | Dash, Wasabi |
Privacy Mechanisms in Blockchain Transactions
Understanding how privacy mechanisms operate at the transaction level reveals their practical implications.
Anonymous Transaction Flows
Anonymous transaction flows in privacy coins break the sender-receiver link that enables tracing in transparent blockchains. When Alice sends to Bob in a privacy coin, observers see a valid transaction but cannot determine that Alice was the sender or Bob the receiver. Multiple decoys, one-time addresses, or encrypted data make tracing mathematically infeasible rather than merely difficult. This anonymity persists even against adversaries with complete blockchain data and sophisticated analysis tools.
Confidential Transaction Amounts
Confidential transactions hide transfer amounts while still proving that inputs equal outputs to prevent inflation. Techniques like Pedersen commitments mathematically commit to amounts without revealing them, while range proofs demonstrate that committed values are positive without disclosure. This amount privacy prevents observers from knowing how much value any transaction transfers, protecting financial privacy beyond mere identity hiding.
Important: Privacy technologies provide strong protections when used correctly, but implementation details matter significantly. User errors, metadata leakage, and integration with transparent systems can compromise privacy even when underlying cryptography is sound. Understanding privacy models and their limitations is essential for effective use.
Role of Privacy Coins in Web3 Ecosystems
Privacy coins fulfill essential functions within Web3 that transparent alternatives cannot address.
Enhancing Financial Privacy
Financial privacy represents the most fundamental role of privacy coins in Web3.
Protecting User Identity and Transaction Data
Privacy coins protect user identity by breaking the links between real-world identities and blockchain activity that transparent systems expose. This protection extends beyond individual transactions to aggregate patterns that reveal sensitive information about users’ lives, relationships, and behaviors. Individuals holding significant value gain protection against targeted attacks, while ordinary users maintain practical anonymity for everyday transactions.
Enabling Censorship-Resistant Payments
Web3 payment privacy enables transactions that cannot be blocked, frozen, or seized by third parties including governments, payment processors, or other centralized authorities. This censorship resistance matters for legitimate uses including donations to unpopular causes, payments in regions with authoritarian governments, and commerce that payment processors refuse to support regardless of legality. Privacy coins combine cryptocurrency’s permissionless nature with confidentiality that prevents identification of parties to block.
Strengthening Web3 Security
Beyond privacy itself, confidential transactions improve overall Web3 security.
Reducing On-Chain Data Exposure
Reducing on-chain data exposure eliminates attack vectors that require visibility into transaction patterns and holdings. Without knowing who holds what value or who transacts with whom, attackers cannot efficiently target high-value wallets, cannot front-run transactions, and cannot build profiles for social engineering attacks. This reduction in exposed data improves security for the entire ecosystem, not just individual privacy coin users.
Preventing Transaction Tracking and Surveillance
Preventing transaction tracking protects against both targeted surveillance and mass data collection that creates future risks. Today’s public transactions become tomorrow’s surveillance archive as analysis techniques improve. Privacy coins ensure that even future advances in blockchain analysis cannot compromise historical transaction privacy, providing forward security that transparent blockchains cannot offer.
Privacy Coins vs Transparent Cryptocurrencies
Understanding the contrast between privacy and transparent approaches clarifies the unique value of privacy coins.
Limitations of Transparent Blockchains
Transparent blockchains carry inherent privacy limitations that cannot be fully addressed without protocol-level changes.
Public Ledger Privacy Risks
Public ledger architectures create permanent, immutable records of all transaction activity accessible to anyone worldwide. This transparency, valuable for verification and auditing, becomes a liability when applied to personal financial activity. Every transaction ever made on transparent blockchains remains visible forever, creating historical records that cannot be deleted or hidden regardless of future privacy needs or risks that emerge.
Traceability of Wallet Addresses
Wallet address traceability enables linking of pseudonymous addresses to real identities through various techniques including exchange deposits, payment metadata, timing analysis, and cross-referencing with off-chain data. Once any address links to an identity, all connected transactions become attributed. This traceability means that even careful users cannot guarantee privacy on transparent blockchains because future address links can retroactively compromise historical activity.
Advantages of Privacy-Focused Coins
Privacy coins address transparent blockchain limitations through fundamental architectural differences.
Anonymous and Unlinkable Transactions
Anonymous and unlinkable transactions ensure that observers cannot connect senders to receivers or link multiple transactions to the same user. This unlinkability is cryptographically enforced rather than depending on user behavior or operational security. Even with complete blockchain data and unlimited analysis resources, adversaries cannot trace properly constructed privacy coin transactions.
Improved User Data Protection
User data protection in privacy coins extends beyond transaction confidentiality to include resistance against metadata analysis, timing attacks, and network-level surveillance. Comprehensive privacy implementations consider the full range of information leakage vectors, not just the blockchain record itself. This holistic approach provides stronger practical privacy than selective hiding of specific data fields.
| Aspect | Transparent Cryptocurrencies | Privacy Coins |
|---|---|---|
| Transaction Visibility | Fully public and permanent | Encrypted or obscured |
| Address Linkability | All addresses linkable | Unlinkable by design |
| Amount Visibility | All amounts public | Amounts hidden |
| Tracing Resistance | Traceable with analysis | Cryptographically untraceable |
| Auditability | Fully auditable by anyone | Selective disclosure options |
Use Cases of Privacy Coins in Web3
Privacy coins enable specific applications that require transaction confidentiality.
Privacy Coins in DeFi Applications
Decentralized finance privacy enables sophisticated financial applications that transparent systems cannot support.
Confidential DeFi Transactions
Confidential DeFi transactions protect trading strategies, lending positions, and yield farming activities from observation and exploitation. On transparent chains, large trades can be front-run, liquidation targets can be identified, and trading patterns reveal proprietary strategies. Privacy-enabled DeFi allows institutions and sophisticated traders to participate without exposing their positions to competitors or predatory actors.
Privacy-Preserving Yield and Payments
Privacy-preserving yield generation allows users to earn returns on their assets without broadcasting their financial positions to the world. Payment privacy enables commercial transactions where parties prefer confidentiality about business relationships, pricing, and volumes. These capabilities enable DeFi to support legitimate business needs that currently require traditional financial privacy.
Web3 Payments and Cross-Border Transfers
Payment applications represent core privacy coin use cases.
Secure Peer-to-Peer Payments
Secure peer-to-peer payments through privacy coins provide the confidentiality of cash transactions in digital form. Users can pay for goods and services without creating permanent records that link their identity to their purchases. This privacy matches or exceeds what traditional cash provides while enabling digital convenience and global reach that cash cannot offer.
Private Global Transactions
Private global transactions enable cross-border value transfer without surveillance by governments, financial institutions, or intermediaries along the payment path. This capability matters for remittances, international business payments, and support to individuals in regions with capital controls or surveillance states. Privacy coins enable financial globalization without the surveillance that traditional correspondent banking enables.
DAOs and Governance Privacy
Decentralized governance benefits from privacy protections that prevent manipulation and protect participants.
Anonymous Voting Mechanisms
Anonymous voting in DAOs prevents vote buying, coercion, and retaliation against voters who oppose powerful interests. When votes are publicly visible, vote buyers can verify compliance and powerful parties can identify and punish opposition. Private voting enables honest preference expression that public systems cannot guarantee, improving governance quality and participation.
Identity Protection in DAO Participation
Identity protection allows DAO members to participate without exposing their involvement or positions to the public. Members may have legitimate reasons to keep their DAO activities private, whether from employers, competitors, or personal preference. Privacy coins enable contribution and participation in decentralized organizations without requiring public disclosure of involvement.
Privacy Coins and Regulatory Considerations
Regulatory dynamics significantly impact privacy coin adoption and design.
Compliance Challenges for Privacy Coins
Privacy features create tension with regulatory frameworks designed for transparent financial systems.
Regulatory Scrutiny and Legal Frameworks
Regulatory scrutiny of privacy coins varies significantly across jurisdictions, with some countries implementing outright bans while others permit use with standard cryptocurrency regulations. The Financial Action Task Force (FATF) has expressed concerns about privacy coins in its guidance, though specific requirements remain subject to national implementation. This regulatory uncertainty creates challenges for exchanges, businesses, and users seeking clear compliance guidance.
AML and KYC Concerns
Anti-money laundering and know-your-customer regulations traditionally require transaction monitoring that privacy coins intentionally prevent. Regulators and financial institutions express concern that privacy features could facilitate money laundering, tax evasion, and sanctions violations. These concerns have led some exchanges to delist privacy coins and some jurisdictions to restrict their use, regardless of the legitimate privacy needs they serve.
Selecting Privacy Coins: Key Criteria
When evaluating privacy coins for specific use cases, consider these essential factors:
- Privacy Model: Mandatory privacy provides stronger guarantees; optional privacy offers flexibility but may compromise anonymity sets
- Technology Foundation: Zero-knowledge proofs offer strongest privacy; ring signatures provide good privacy with simpler technology
- Exchange Availability: Consider listing status on exchanges you need for liquidity and fiat conversion
- Regulatory Status: Evaluate legal status in relevant jurisdictions for compliance requirements
- Transaction Performance: Assess confirmation times, fees, and scalability for intended use patterns
- Ecosystem Maturity: Consider wallet options, integration support, and community activity
Balancing Privacy and Compliance
Emerging approaches seek to preserve privacy while enabling legitimate regulatory requirements.
Selective Disclosure Mechanisms
Selective disclosure mechanisms allow users to prove specific claims about their transactions without revealing full details. A user might prove that funds originated from a compliant exchange without revealing which exchange or exact amounts. These mechanisms leverage zero-knowledge proofs to provide auditability for regulatory purposes while maintaining privacy for everyday transactions.
Privacy Coins with Compliance Features
Privacy coins with compliance features implement optional transparency or view key systems that allow designated auditors to inspect transactions when required. Zcash’s viewing keys allow selective disclosure to chosen parties. These approaches acknowledge that complete privacy from all parties may not be practical for all use cases while preserving privacy from general surveillance.
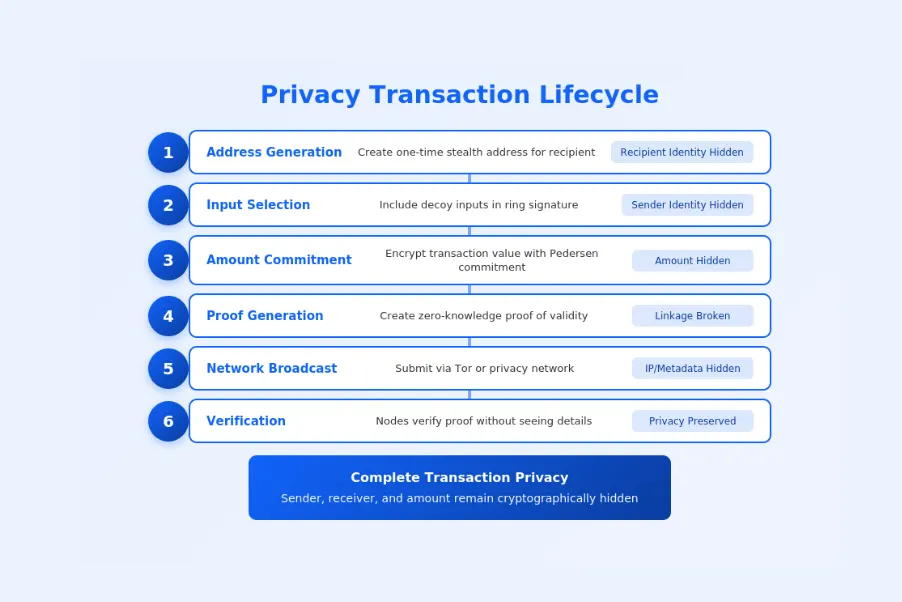
| Phase | Stage | Privacy Actions | What Gets Hidden |
|---|---|---|---|
| 1 | Address Generation | Create stealth or one-time address | Recipient identity |
| 2 | Input Selection | Include decoy inputs in ring | Sender identity |
| 3 | Amount Commitment | Encrypt or commit amounts | Transaction value |
| 4 | Proof Generation | Create ZKP or ring signature | Transaction linkage |
| 5 | Broadcast | Submit via privacy network | IP and metadata |
| 6 | Verification | Verify proof without decryption | All details remain private |
Challenges and Risks of Privacy Coins in Web3
Privacy coins face significant challenges that affect their adoption and utility.
Adoption and Usability Barriers
Practical challenges limit privacy coin usage beyond technical and regulatory concerns.
Complexity of Privacy Technologies
Privacy technologies introduce complexity that makes privacy coins harder to use than transparent alternatives. Longer transaction times for proof generation, larger transaction sizes, and more complex key management create friction. Users must understand privacy models to use them effectively, as mistakes can compromise privacy even when underlying technology is sound. This complexity barrier limits adoption to more sophisticated users.
Limited Exchange Support
Limited exchange support restricts privacy coin accessibility as major exchanges delist them to avoid regulatory complications. Users in some jurisdictions cannot easily acquire or liquidate privacy coins through traditional fiat gateways. This reduced liquidity and accessibility creates practical barriers that technical excellence cannot overcome, limiting privacy coins to users willing to accept these inconveniences.
Security and Network Risks
Privacy features introduce specific security considerations.
Potential Exploitation and Abuse
The same privacy features that protect legitimate users can also shield illicit activity including ransomware payments, darknet market transactions, and money laundering. While privacy is neutral technology serving legitimate needs, this potential for abuse drives regulatory concern and public perception challenges. Privacy coin communities must acknowledge these risks while advocating for the much larger legitimate use cases.
Protocol and Smart Contract Vulnerabilities
Privacy implementations involve complex cryptography where subtle bugs can compromise privacy or even enable theft or inflation. Privacy coins cannot rely on transparency for security verification, making auditing harder. Several privacy coins have discovered and patched serious vulnerabilities, highlighting the ongoing security maintenance required for complex privacy systems.
Future of Privacy Coins in Web3 Ecosystems
The trajectory of privacy in Web3 points toward broader integration and improved technology.
Emerging Trends in Privacy Technologies
Technical advances continue improving privacy capabilities and accessibility.
Advanced Zero-Knowledge Proof Systems
Advanced zero-knowledge systems including recursive proofs, more efficient proving systems, and hardware acceleration are making ZKP technology faster and more accessible. Improvements like PLONK, Halo, and Nova reduce proof generation time and size, making privacy practical for more applications. These advances enable privacy features that would have been computationally prohibitive with earlier technology.
Privacy Layers for Web3 Applications
Privacy layers are emerging that add confidentiality to existing transparent blockchains rather than requiring entirely new chains. Solutions like Aztec on Ethereum and various cross-chain privacy protocols enable private transactions within established ecosystems. This layer approach allows users to maintain existing holdings and relationships while gaining privacy when needed.
Role of Privacy Coins in Web3 Mass Adoption
Privacy will likely prove essential for Web3 to achieve mainstream adoption.
Privacy-First Web3 Infrastructure
Privacy-first blockchain infrastructure may become necessary as Web3 handles increasingly sensitive applications. Healthcare data, personal identity, financial records, and business operations all require confidentiality that transparent blockchains cannot provide. Privacy coins and privacy layer technology provide the foundation for Web3 applications requiring the same confidentiality guarantees that traditional systems provide.
Long-Term Sustainability of Privacy Coins
Long-term sustainability depends on privacy coins maintaining security, adapting to regulatory requirements, and delivering practical privacy for real use cases. The most sustainable approach may involve privacy becoming a standard feature across Web3 rather than isolated in specialized coins. Privacy coins that survive will likely be those that successfully balance strong privacy with practical usability and acceptable compliance approaches.
Explore Privacy Coins in Web3
Learn how privacy coins enhance security, anonymity, and decentralized transactions within modern Web3 ecosystems.
Why Privacy Coins Are Essential to Web3 Ecosystems
Privacy represents a fundamental requirement for Web3 to fulfill its promise of user sovereignty and decentralized control.
Final Thoughts on Privacy-Driven Web3 Innovation
The privacy coins ecosystem provides essential capabilities that transparent blockchains cannot offer, enabling financial confidentiality, censorship resistance, and protection from surveillance that users and businesses require. While regulatory challenges and technical complexity create adoption barriers, the fundamental need for privacy in financial transactions ensures continued demand for privacy-preserving solutions.
As Web3 evolves from experimental technology toward infrastructure for real economic activity, privacy will transition from optional feature to essential requirement. The technologies pioneered by privacy coins, including zero-knowledge proofs, ring signatures, and confidential transactions, will likely spread throughout Web3 rather than remaining isolated in specialized coins. Organizations and individuals who understand privacy coin technology position themselves to navigate this privacy-first future effectively.
The role of privacy coins in Web3 ecosystems extends beyond enabling anonymous transactions to establishing the principle that financial privacy is a legitimate requirement that technology should serve. This principle, combined with the technical innovations privacy coins have pioneered, ensures their lasting influence on Web3 evolution regardless of which specific coins or technologies ultimately prevail.
Frequently Asked Questions
Privacy coins are cryptocurrencies designed to provide anonymous and untraceable transactions by hiding sender addresses, recipient addresses, and transaction amounts. They use advanced cryptographic techniques like zero-knowledge proofs, ring signatures, and stealth addresses to obscure transaction details on the blockchain. Unlike transparent cryptocurrencies where all transaction data is publicly visible, privacy coins ensure that financial activities remain confidential while still maintaining blockchain integrity.
Privacy in Web3 is essential because transparent blockchains expose all transaction data publicly, allowing anyone to analyze wallet balances, track spending patterns, and link addresses to real identities. This exposure creates risks including targeted theft, commercial surveillance, price manipulation based on trading patterns, and personal safety concerns for high-value holders. Privacy enables users to maintain financial autonomy and protects sensitive business transactions from competitors and malicious actors.
Bitcoin operates on a transparent blockchain where all transactions, addresses, and amounts are publicly visible and permanently recorded, making it pseudonymous rather than anonymous. Privacy coins like Monero, Zcash, and others implement mandatory or optional privacy features that hide transaction details from public view. While Bitcoin transactions can be traced and linked through blockchain analysis, privacy coins use cryptographic techniques that make tracing transactions mathematically infeasible or impossible.
Zero-knowledge proofs allow one party to prove a statement is true without revealing any information beyond the validity of the statement itself. In privacy coins, ZKPs prove that a transaction is valid, follows network rules, and the sender has sufficient funds without revealing who sent what to whom. This cryptographic technique enables validators to confirm transaction legitimacy while keeping actual transaction details completely private and unrecoverable.
Most properly constructed privacy coin transactions are designed to be mathematically untraceable, though the degree of privacy varies by implementation. Monero’s mandatory privacy makes systematic tracing extremely difficult, while Zcash’s optional privacy means transparent transactions are fully traceable. Law enforcement has developed various analytical techniques and sometimes offers bounties for breaking privacy protocols, but well-implemented privacy mechanisms have generally resisted systematic tracing attempts.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.






