Key Takeaways
- Web3 identity proofing enables users to verify claims about themselves using cryptographic credentials without relying on centralized identity providers
- Web3 decentralized identity is built on DIDs (Decentralized Identifiers) and VCs (Verifiable Credentials) that give users ownership and control
- Self-sovereign identity eliminates dependency on third-party identity providers while enabling portable, user-controlled credentials
- Zero-knowledge proofs enable privacy-preserving verification, allowing users to prove claims without revealing underlying personal data
- Web3 identity solutions support regulatory compliance through reusable KYC credentials that satisfy requirements while protecting privacy
- Identity wallets provide user-friendly interfaces for managing credentials, making complex cryptography accessible to mainstream users
- Cross-chain and cross-platform interoperability is essential for Web3 identity management to achieve widespread adoption [1]
- The future of digital identity in Web3 includes biometric proofs, tokenized identity, and seamless integration across decentralized applications
Introduction to Identity Proofing in Web3
Identity is fundamental to trust, yet the internet was built without a native identity layer. Web3 is finally addressing this gap, creating infrastructure for Web3 identity verification that gives users control while enabling applications to verify claims reliably. This transformation affects everything from financial access to governance participation to digital ownership.
What Is Identity Proofing?
Identity proofing is the process of verifying that a person is who they claim to be, establishing confidence that identity attributes are accurate and belong to the claiming individual. Traditional proofing involves document verification, biometric matching, and database checks. Web3 identity proofing achieves similar confidence through cryptographic verification of credentials issued by trusted parties, without requiring centralized infrastructure.
The goal isn’t merely to identify individuals but to verify specific claims relevant to particular interactions. Proving you’re over 18 to access content, proving you’re a qualified professional to offer services, or proving you’re a unique human for fair distribution all represent different proofing requirements that Web3 identity can address.
Why Identity Proofing Matters in Web3?
Web3’s permissionless nature creates both opportunities and challenges. Anyone can participate, but this openness enables Sybil attacks, fraud, and abuse. Web3 identity proofing provides accountability without sacrificing decentralization. It enables reputation systems, compliant financial services, fair governance, and trusted marketplaces while preserving the privacy and user control that define Web3’s value proposition.
Evolution of Digital Identity
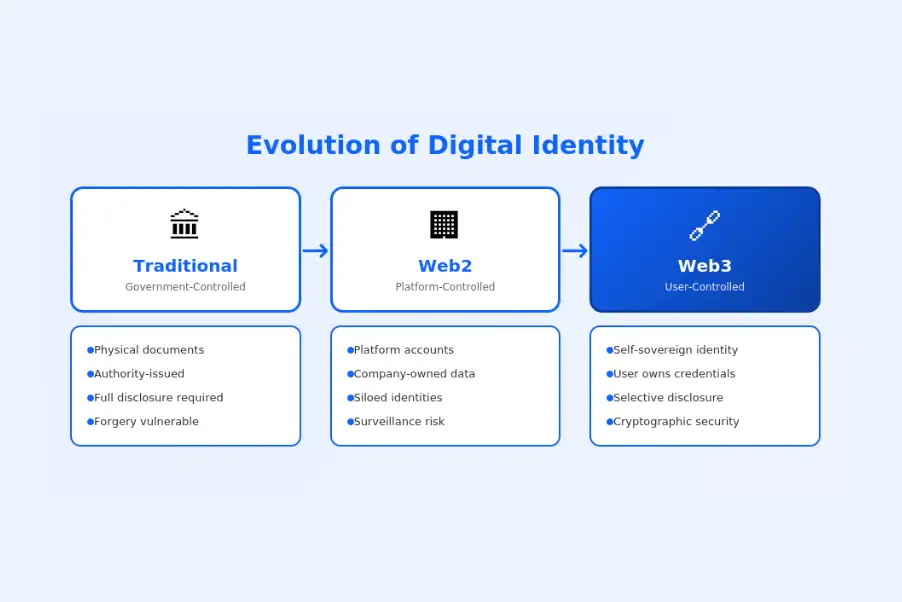
Understanding where digital identity came from clarifies where it’s heading.
Traditional Identity Proofing Systems
Traditional identity proofing relies on centralized authorities: governments issue identity documents, credit bureaus maintain financial identity, and platforms verify users through proprietary systems. This model creates data honeypots that attract hackers, fragments identity across siloed providers, and leaves users without control over their own information. Every service maintains its own copy of user data, multiplying privacy risks.
Shift from Web2 Identity to Web3 Identity
Web2 identity is platform-centric: your Facebook identity exists only on Facebook, your LinkedIn profile only on LinkedIn. Platforms own your digital presence and can delete it unilaterally. Web3 decentralized identity inverts this model, making users the center. Identity becomes portable across applications, controlled by users rather than platforms, and cryptographically secured rather than protected only by platform security practices.
| Aspect | Traditional Identity | Web2 Identity | Web3 Identity |
|---|---|---|---|
| Control | Government/Institution | Platform | User |
| Portability | Limited | Platform-locked | Fully portable |
| Privacy | Full disclosure | Platform surveillance | Selective disclosure |
| Security | Document forgery risk | Centralized breaches | Cryptographic |
| Revocation | Authority decision | Platform decision | User control |
Core Technologies Powering Web3 Identity Proofing
Several foundational technologies enable Web3 identity solutions.
Decentralized Identifiers (DIDs)
Decentralized Identifiers are globally unique identifiers that users create and control without any central registration authority. A DID might look like “did:ethr:0x123…” and resolves to a DID Document containing public keys and service endpoints. Unlike usernames tied to specific platforms, DIDs are portable, permanent (unless the user chooses otherwise), and cryptographically controlled.
DIDs can anchor to various backends: blockchains like Ethereum, decentralized storage like IPFS, or even web domains. This flexibility allows different trust and cost tradeoffs while maintaining the core property of user control.
Verifiable Credentials (VCs)
Verifiable Credentials are tamper-proof digital attestations about a subject, signed by an issuer, that can be verified by anyone without contacting the issuer. A VC might attest that someone is over 18, holds a specific degree, or passed KYC verification. The cryptographic signature proves the credential came from the claimed issuer and hasn’t been modified.
VCs follow W3C standards, ensuring interoperability across different systems. They can be stored in user wallets and presented selectively, sharing only the claims relevant to each interaction.
Important: The security of Web3 identity depends on proper key management. Lost private keys mean lost identity access, and compromised keys allow identity theft. Implement robust key recovery mechanisms and educate users on security practices before deploying identity systems.
Role of Self-Sovereign Identity (SSI)
Self-sovereign identity represents the philosophical foundation of Web3 identity management.
User Ownership and Control of Identity
Self-sovereign identity means users truly own their digital identity rather than renting it from platforms. This ownership includes creating identifiers without permission, accumulating credentials from multiple issuers, deciding what to share with whom, and maintaining identity even if any single service disappears. SSI treats identity as a fundamental right rather than a service privilege.
Eliminating Centralized Identity Providers
Traditional identity flows through centralized providers who can revoke access, sell data, or get breached. SSI eliminates this dependency. Credentials exist in user wallets, not provider databases. Verification happens cryptographically, not through API calls to identity providers. This architecture removes single points of failure and control from identity infrastructure.
Privacy-Preserving Identity Proofing
Privacy is central to Web3 identity verification, not an afterthought.
Selective Disclosure Mechanisms
Selective disclosure allows users to share only the specific claims needed for each interaction. Instead of showing an entire driver’s license to prove age, users can prove just “over 21” while hiding name, address, and exact birthdate. This minimizes data exposure, reducing privacy risks and the value of potential data breaches.
Zero-Knowledge Proofs for Identity Verification
Zero-knowledge proofs take privacy further, proving claims without revealing any underlying data. Users can prove their credit score exceeds a threshold without revealing the actual score, or prove group membership without revealing which specific member they are. This mathematical approach enables verification with minimal information leakage.
| Phase | Stage | Actions | Output |
|---|---|---|---|
| 1 | DID Creation | User generates key pair, creates DID | Decentralized identifier |
| 2 | Credential Request | User requests credential from issuer | Proofing requirement |
| 3 | Verification | Issuer verifies user claims | Verified identity data |
| 4 | Issuance | Issuer signs and issues credential | Verifiable credential |
| 5 | Storage | User stores in identity wallet | Wallet credential |
| 6 | Presentation | User presents credential to verifier | Verified access |
How Identity Proofing Works in Web3
Understanding the mechanics clarifies how Web3 identity proofing trends will reshape verification.
Issuers, Holders, and Verifiers
Web3 identity operates through a trust triangle. Issuers are trusted entities that verify claims and issue credentials, such as governments, universities, or KYC providers. Holders are users who store credentials in their wallets and control when to share them. Verifiers are services that request and validate credentials to make trust decisions. This separation of roles enables flexible trust networks.
On-Chain and Off-Chain Identity Proofing
Identity proofing can occur on-chain or off-chain. On-chain proofing stores credentials or proofs directly on blockchain, enabling smart contract access and maximum transparency but incurring costs and privacy limitations. Off-chain proofing keeps credentials in user wallets, presenting them as needed while optionally anchoring proofs on-chain. Most systems use hybrid approaches optimized for their specific requirements.
Use Cases of Identity Proofing in Web3
Practical applications demonstrate the future of digital identity in Web3.
Identity Proofing in DeFi Platforms
DeFi protocols use identity proofing for compliance, reputation, and risk management. KYC credentials enable access to regulated services. Creditworthiness attestations support undercollateralized lending. Proof of unique personhood enables fair token distributions. Teams building Web3 identity solutions and verification systems help protocols transform from purely anonymous to selectively accountable.
NFT, Gaming, and Metaverse Identity
Digital worlds need identity for meaningful social interaction. Verified creator credentials prevent impersonation in NFT markets. Gaming identities track achievements and reputation across platforms. Metaverse identities enable persistent presence across virtual environments. Identity proofing makes digital experiences more trustworthy and socially valuable.
DAO Membership and Governance
DAOs use identity proofing to create more nuanced governance. Expertise credentials can weight votes on relevant proposals. Contribution attestations recognize active participants. Proof of unique personhood enables quadratic voting without Sybil manipulation. Identity enriches governance beyond simple token-weighted voting.
Identity Wallets and User Experience
User experience determines whether Web3 identity achieves mainstream adoption.
Digital Identity Wallets in Web3
Identity wallets store DIDs, credentials, and keys while providing interfaces for managing and presenting identity information. Good wallets hide cryptographic complexity behind intuitive interfaces, making identity management accessible to non-technical users. They handle backup, recovery, and security while presenting simple flows for common identity interactions.
Improving UX with Seamless Identity Proofing
The best identity proofing feels invisible. Rather than explicit verification steps, credentials present automatically when needed. Progressive disclosure requests only necessary information. Smart defaults protect privacy while enabling smooth experiences. Achieving this seamlessness requires careful design that balances security, privacy, and convenience.
Selecting Web3 Identity Solutions: Key Criteria
When evaluating identity proofing solutions, consider these factors:
- Standards Compliance: W3C DID and VC compatibility for interoperability
- Privacy Features: Selective disclosure and zero-knowledge proof support
- User Experience: Wallet quality and onboarding simplicity
- Issuer Ecosystem: Availability of credential issuers you need
- Recovery Options: Key recovery mechanisms for lost access
- Regulatory Support: Compliance with relevant KYC/AML requirements
Security Benefits of Web3 Identity Proofing
Web3 identity fundamentally improves security compared to traditional approaches.
Fraud Prevention and Sybil Resistance
Cryptographic credentials make forgery practically impossible. Proof of unique personhood attestations prevent one person from creating multiple fake accounts. Reputation systems built on verified identities create accountability for bad behavior. These mechanisms address fraud vectors that plague traditional and Web2 systems.
Secure Authentication Without Passwords
Web3 identity enables passwordless authentication through cryptographic signatures. Users prove identity by signing challenges with private keys, eliminating password databases that can be breached and phishing attacks that steal credentials. This approach provides stronger security with better user experience than traditional passwords.
Interoperability and Cross-Chain Identity
Identity must work across the fragmented Web3 landscape.
Cross-Platform Identity Proofing
Decentralized identity future depends on portability. Credentials earned on one platform should work on others. Identity verified for one protocol shouldn’t require re-verification elsewhere. Achieving this portability requires standard formats, common trust frameworks, and technical bridges between different systems.
Interoperable Identity Standards
W3C standards for DIDs and VCs provide foundation for interoperability. DIF (Decentralized Identity Foundation) develops protocols for credential exchange. Specific ecosystems like Ethereum have ERC standards for identity. Adoption of common standards enables credentials from any issuer to work with any verifier.
| Feature | Centralized Identity | Federated Identity | Self-Sovereign Identity |
|---|---|---|---|
| User Control | None | Limited | Full |
| Privacy | Provider sees all | IdP tracks usage | Selective disclosure |
| Single Point of Failure | Yes | Yes (IdP) | No |
| Portability | None | IdP-dependent | Full |
| Example | Bank KYC | Login with Google | Web3 identity wallets |
Compliance and Regulation in Identity Proofing
Regulatory compliance shapes practical identity implementation.
Web3 Identity and KYC Requirements
Regulated services must verify user identity under KYC (Know Your Customer) requirements. Web3 identity enables “portable KYC” where users complete verification once and reuse the resulting credential across multiple services. This reduces friction for users and costs for services while maintaining regulatory compliance.
Balancing Privacy with Regulatory Compliance
Privacy and compliance aren’t mutually exclusive. Zero-knowledge proofs can verify KYC completion without revealing personal data. Selective disclosure shares only necessary information. Proper credential design satisfies regulators while protecting user privacy. This balance is essential for Web3 identity to serve both regulated and permissionless contexts.
Challenges Facing Identity Proofing in Web3
Significant challenges must be addressed for widespread adoption.
Scalability and Adoption Barriers
On-chain identity faces scalability limits and gas costs. Key management complexity challenges mainstream users. The chicken-and-egg problem requires both credential issuers and accepting verifiers to achieve value. User experience remains difficult compared to centralized alternatives that hide complexity.
Standardization and Governance Issues
Multiple competing standards fragment the ecosystem. Governance of trust frameworks remains unclear. Legal recognition of decentralized identity varies by jurisdiction. Establishing widely accepted standards and governance structures is essential for interoperability and trust.
Future Trends in Web3 Identity Proofing

Emerging trends point toward Web3 identity proofing trends that will reshape verification.
Biometric Proofs and Proof of Uniqueness
Biometric proofs can verify unique personhood without storing biometric data. Projects like Worldcoin use iris scans to create proof-of-personhood credentials. Privacy-preserving biometrics could solve Sybil resistance while maintaining anonymity. This technology remains controversial but represents a significant direction for identity proofing.
Tokenized Identity and Data Ownership
Identity attributes may become tokenized assets that users control and potentially monetize. Data markets could enable users to selectively sell access to verified attributes. This shifts value from data aggregators to individuals who generate the data. Tokenized identity represents the economic dimension of self-sovereign identity.
Impact of Identity Proofing on Web3 Adoption
Identity infrastructure determines Web3’s trajectory.
Building Trust in Decentralized Ecosystems
Trust enables economic activity. Identity proofing creates accountability that makes decentralized interactions trustworthy. Reputation built on verified credentials enables strangers to transact confidently. This trust layer is essential for Web3 to support meaningful economic and social activity beyond speculation.
Enabling Mass Adoption of Web3 Applications
Mainstream users expect identity experiences similar to what they know from Web2 while gaining Web3’s benefits. Identity proofing that’s both powerful and user-friendly bridges this gap. Seamless identity enables the applications, from compliant finance to trusted marketplaces, that can attract mainstream adoption.
Prepare for the Identity Shift
Learn how Web3 identity models replace centralized verification with user-controlled credentials.
Why Identity Proofing Is Critical for the Future of Web3
Web3 identity proofing represents a fundamental reimagining of how digital identity works.
The future of digital identity in Web3 solutions will determine whether decentralized systems can support the rich interactions that require trust. Identity proofing provides the accountability layer that enables reputation, compliance, access control, and fair governance while preserving the user control and privacy that define Web3’s value proposition.
Web3 identity management is still early but evolving rapidly. Standards are maturing, tooling is improving, and real applications are deploying. Organizations that understand and implement Web3 identity solutions position themselves for the decentralized future. Those who ignore this transformation risk building on foundations that cannot support trustworthy interactions.
The path forward requires balancing technical capability with user experience, privacy with compliance, and decentralization with practical utility. Success means identity infrastructure that’s invisible to users while enabling the verified, private, portable identity that Web3 promises. This is the critical infrastructure upon which Web3’s broader vision depends.
Frequently Asked Questions
Self-sovereign identity (SSI) is a model where individuals own and control their digital identity without depending on centralized authorities like governments or corporations. Users create their own decentralized identifiers, store credentials in personal wallets, and decide what information to share with whom. SSI eliminates the need for third-party identity providers while giving users true ownership of their digital presence.
Verifiable credentials are tamper-proof digital certificates that prove claims about a person, such as age, citizenship, or qualifications, without exposing unnecessary personal data. They’re cryptographically signed by trusted issuers and can be verified instantly without contacting the issuer. VCs enable privacy-preserving identity verification that’s faster, cheaper, and more secure than traditional document checking.
Zero-knowledge proofs allow someone to prove a claim is true without revealing the underlying data. For identity, this means proving you’re over 21 without revealing your birthdate, or proving you’re a citizen without showing your passport. The mathematical proof convinces verifiers of the claim’s validity while keeping actual identity data private, enabling verification with minimal disclosure.
Yes, Web3 identity can satisfy KYC requirements through verified credentials issued by compliant identity providers. Users complete KYC once, receive a verifiable credential, and can prove their verified status to multiple services without repeating the process. This approach maintains regulatory compliance while reducing friction and protecting user privacy better than centralized KYC databases.
Web3 identity prevents fraud through cryptographic verification that makes credential forgery practically impossible. For Sybil resistance, identity proofing can verify unique personhood, ensuring one person cannot create multiple fake accounts. Reputation systems built on verified identities create accountability, while privacy-preserving proofs enable verification without creating honeypots of personal data that attract hackers.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







