Key Takeaways
- Elliptic Curve Cryptography in Web3 provides the mathematical foundation for secure digital signatures, key generation, and identity verification across decentralized networks
- ECC security in blockchain networks delivers equivalent protection to RSA with 10-15x smaller key sizes, enabling faster transactions and reduced storage requirements
- ECC for Web3 network security powers critical functions including wallet protection, transaction signing, consensus validation, and decentralized identity systems
- Web3 cryptographic security through ECC uses curves like secp256k1 (Bitcoin, Ethereum) and Ed25519 (Solana, newer protocols) with distinct performance and security tradeoffs
- ECC-based encryption for Web3 faces future quantum computing threats, making post-quantum cryptography planning essential for long-term security strategies
- Web3 identity security mechanisms built on ECC enable self-sovereign identity, credential verification, and multi-platform authentication without central authorities
- Implementation quality matters more than algorithm choice: poor random number generation, improper key storage, and library vulnerabilities cause most ECC security failures
- Enterprise Web3 adoption benefits from ECC’s performance efficiency, enabling scalable security for high-throughput blockchain applications
Understanding Elliptic Curve Cryptography in Web3
Cryptographic security forms the bedrock of Web3’s trust model. Unlike traditional systems that rely on centralized authorities, Web3 networks use mathematical proofs to establish security, ownership, and identity. Elliptic Curve Cryptography in Web3 provides the mathematical machinery that makes this possible, enabling secure operations without requiring users to trust intermediaries.
What Is Elliptic Curve Cryptography (ECC)?
Elliptic Curve Cryptography is a form of public-key cryptography based on the algebraic structure of elliptic curves over finite fields. An elliptic curve is defined by a mathematical equation (typically y² = x³ + ax + b) where points on the curve have special properties that make certain mathematical operations easy to compute in one direction but practically impossible to reverse.
The security of ECC rests on the elliptic curve discrete logarithm problem (ECDLP): given a point P on an elliptic curve and a point Q = kP (where k is a scalar multiplication), finding k is computationally infeasible even though computing Q from k and P is efficient. This asymmetry enables ECC to create secure key pairs where the public key is derived from the private key, but the private key cannot be computed from the public key.
Why ECC Is Preferred in Web3 Security Models?
Web3 networks chose ECC for several compelling reasons related to efficiency and security. The most significant advantage is key size: a 256-bit ECC key provides security equivalent to approximately 3072-bit RSA key. This 12x reduction in key size translates directly to smaller transactions, faster signature verification, and reduced storage requirements across the network.
For blockchain networks processing millions of transactions, these efficiency gains compound dramatically. Every transaction includes at least one digital signature that nodes must verify. Smaller signatures mean faster verification, lower bandwidth consumption, and reduced blockchain bloat. ECC security in blockchain networks makes high-throughput decentralized systems practically achievable.
ECC vs Traditional Cryptographic Algorithms
Comparing ECC with traditional algorithms like RSA reveals substantial differences in efficiency and scalability. While both provide strong security when properly implemented, ECC achieves equivalent security with dramatically smaller computational overhead. This efficiency becomes critical in decentralized networks where every node must independently verify cryptographic operations.
RSA remains valuable for certain applications, but its key size requirements make it impractical for blockchain signatures. A 256-bit ECC signature fits comfortably in a blockchain transaction, while equivalent RSA security would require signatures several times larger. The performance gap widens further at higher security levels, making ECC the clear choice for Web3 cryptographic security.
Important: ECC security depends entirely on implementation quality. The mathematics are sound, but vulnerabilities arise from poor random number generation, improper key handling, and bugs in cryptographic libraries. Always use audited, well-maintained implementations rather than custom cryptographic code.
How ECC Strengthens Web3 Network Security?
ECC provides the cryptographic primitives that secure every layer of Web3 infrastructure, from individual transactions to network-wide consensus mechanisms. Understanding these applications reveals why ECC for Web3 network security has become the universal standard.
Securing Transactions with ECC-Based Digital Signatures
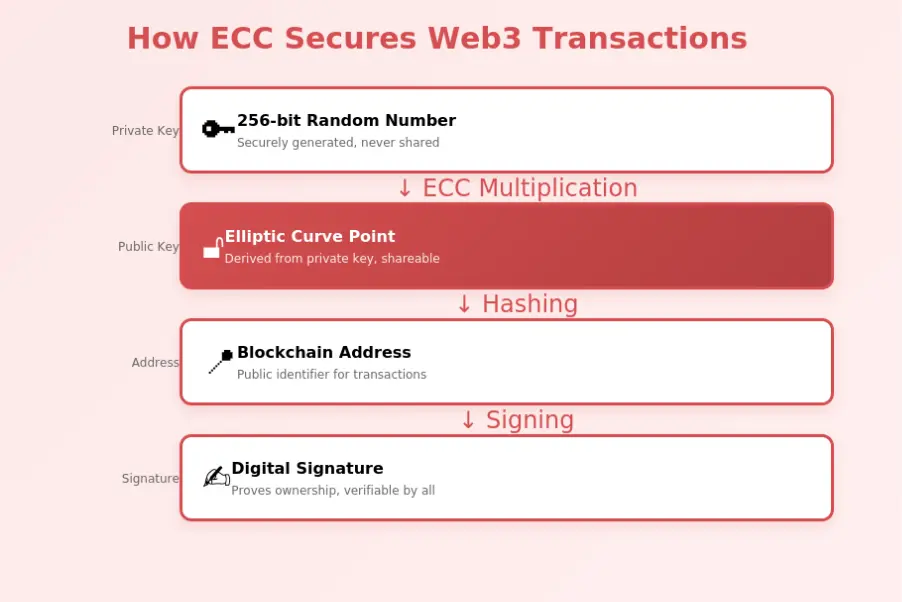
Every Web3 transaction requires cryptographic proof that the sender authorized it. ECC enables this through digital signatures, typically using ECDSA (Elliptic Curve Digital Signature Algorithm) or EdDSA (Edwards-curve Digital Signature Algorithm). When a user sends a transaction, their wallet software creates a signature using their private key that proves ownership without revealing the key itself.
The signature contains mathematical components (typically called r and s in ECDSA) that verifiers can check against the public key. If the signature is valid, the transaction is authentic; if not, nodes reject it. This verification happens on every node independently, ensuring that even a compromised validator cannot forge transactions for accounts they don’t control.
Role of ECC in Public and Private Key Management
ECC generates the key pairs that form Web3 identity. The process begins with a random 256-bit number (the private key), which through elliptic curve multiplication produces a public key point on the curve. From this public key, blockchain addresses are derived using hashing functions. The security of this chain depends on the private key remaining secret and the ECC parameters being correctly chosen.
Key management in Web3 involves generating, storing, backing up, and using these ECC key pairs securely. Hardware wallets implement ECC operations in secure enclaves, preventing private key extraction. Software wallets encrypt keys at rest. The entire Web3 identity security mechanisms infrastructure relies on ECC’s mathematical properties ensuring that public information never compromises private keys.
Preventing Unauthorized Access in Web3 Systems
ECC prevents unauthorized access by making it mathematically infeasible to act without the correct private key. Attackers cannot forge signatures, derive private keys from observed transactions, or impersonate users. Even if an attacker observes thousands of valid signatures from an address, they cannot produce a new valid signature without the private key.
This protection extends to smart contracts, where ECC signatures authorize operations with financial consequences.
ECC and Blockchain Infrastructure
Beyond individual transactions, ECC supports the broader blockchain infrastructure including consensus mechanisms, network validation, and protocol security.
Use of ECDSA in Blockchain Protocols
ECDSA (Elliptic Curve Digital Signature Algorithm) is the most widely deployed signature scheme in blockchain. Bitcoin pioneered its use, and Ethereum followed with the same curve (secp256k1). ECDSA produces signatures from private keys that anyone can verify using the corresponding public key, with security resting on the difficulty of the ECDLP.
The algorithm involves selecting a random nonce k for each signature, computing a curve point kG (where G is the generator point), and combining this with the message hash and private key to produce signature components. Proper nonce handling is critical: reusing or predictably generating nonces can leak the private key entirely, as demonstrated in several high-profile incidents.
ECC in Consensus and Network Validation
Consensus mechanisms use ECC signatures to identify and authorize validator actions. In Proof of Stake systems, validators sign blocks and attestations using their ECC keys. These signatures prove that specific validators approved specific blocks, enabling the protocol to attribute actions and apply rewards or penalties appropriately.
BLS signatures (Boneh-Lynn-Shacham), based on elliptic curve pairings, enable efficient signature aggregation for consensus protocols. Instead of verifying thousands of individual validator signatures, networks can verify a single aggregated signature. This optimization is essential for scalable consensus in networks with many validators.
Lightweight Cryptography for Decentralized Networks
Decentralized networks include resource-constrained nodes ranging from full nodes to light clients to embedded IoT devices. ECC’s compact key sizes and efficient operations make cryptographic verification feasible across this spectrum. Light clients can verify transaction inclusion proofs and block headers without dedicating excessive resources to cryptographic operations.
ECC-based encryption for Web3 applications enables secure communication channels between nodes, encrypted storage of sensitive data, and privacy-preserving protocols that would be impractical with larger key algorithms. This lightweight nature supports the decentralized ideal where anyone can participate in network validation.
| Algorithm | Curve Type | Used By | Key Feature |
|---|---|---|---|
| ECDSA (secp256k1) | Koblitz | Bitcoin, Ethereum | Established, efficient verification |
| EdDSA (Ed25519) | Edwards | Solana, Cardano | Deterministic, fast signing |
| BLS | Pairing-friendly | Ethereum 2.0 | Signature aggregation |
| Schnorr | Various | Bitcoin (Taproot) | Multi-sig efficiency, privacy |
Protecting Web3 Identities and Wallets Using ECC
Web3 identity revolves around cryptographic key pairs rather than usernames and passwords. ECC provides the security foundation for wallets, identity systems, and credential verification throughout the decentralized ecosystem.
ECC-Based Wallet Security Mechanisms
Every Web3 wallet is fundamentally an ECC key pair management system. The wallet generates and stores private keys, signs transactions on user request, and derives addresses from public keys. Security depends on protecting the private key from extraction while making it available for signing operations when authenticated.
Hardware wallets implement ECC operations within tamper-resistant secure elements. The private key never leaves the device; instead, transactions are signed internally after user confirmation. This architecture protects against malware, phishing, and remote attacks. Software wallets use encryption and secure storage APIs to protect keys, though they remain more vulnerable than hardware alternatives.
Cryptographic Identity Verification in Web3
Decentralized identity systems use ECC to prove identity ownership and attribute possession. A user can sign a challenge with their private key to prove they control an identity, issue verifiable credentials that others can verify, and delegate authentication across multiple platforms without centralized identity providers.
Web3 identity security mechanisms enable scenarios impossible in traditional systems: users can prove they’re over 18 without revealing their birth date, demonstrate membership in organizations without exposing their complete profile, and authenticate to services while maintaining privacy. ECC signatures on selective disclosures make these cryptographic proofs possible.
Reducing Key Exposure Risks with ECC
ECC enables several techniques that reduce private key exposure. Hierarchical Deterministic (HD) wallets derive unlimited child keys from a single seed using ECC multiplication, allowing address generation without accessing the master private key. Multi-signature schemes require multiple ECC signatures to authorize transactions, distributing trust across parties.
Threshold signatures using ECC (like those based on Shamir’s Secret Sharing combined with curve operations) split a key into shares where any threshold number can sign but fewer reveal nothing. These advanced techniques, built on ECC primitives, provide defense in depth against key compromise.
Security Risks and Limitations of ECC in Web3
While ECC provides strong security when properly implemented, risks arise from implementation flaws, emerging threats, and operational mistakes. Understanding these vulnerabilities enables effective mitigation.
Common Implementation Mistakes in ECC
The most dangerous ECC vulnerabilities come from implementation errors rather than mathematical weaknesses. Nonce reuse in ECDSA signatures can expose private keys entirely, as demonstrated when the PlayStation 3 signing key was recovered after Sony used a constant nonce. Poor random number generation produces predictable keys that attackers can guess or enumerate.
Other implementation risks include timing side-channels that leak information through computation time variations, improper curve parameter validation that enables invalid curve attacks, and insecure encoding/decoding of curve points. Using audited, well-maintained cryptographic libraries (like libsecp256k1 for Bitcoin operations) mitigates these risks.
Threats from Quantum Computing
Quantum computers of sufficient scale could break ECC using Shor’s algorithm, which solves the discrete logarithm problem efficiently on quantum hardware. Current estimates suggest that a quantum computer with thousands of error-corrected qubits could break common ECC parameters. Such machines don’t exist today, but represent a future threat to current cryptographic systems.
The blockchain community is actively researching post-quantum cryptography alternatives. NIST has standardized several post-quantum algorithms, and blockchain projects are evaluating migration paths. The challenge is balancing urgency against the immaturity of post-quantum schemes, which have larger keys and less real-world testing than ECC.
Key Management and Storage Vulnerabilities
Even perfect ECC implementation cannot protect poorly managed keys. Users who store private keys in plaintext files, reuse keys across services, or back up keys insecurely expose themselves to theft. Organizational key management failures, including inadequate access controls and missing audit trails, compound individual risks at scale.
| Risk Category | Threat | Mitigation |
|---|---|---|
| Implementation | Nonce reuse, poor RNG | Use audited libraries, deterministic nonces |
| Future Threat | Quantum computing | Monitor PQC progress, plan migration |
| Operational | Key theft, exposure | Hardware wallets, multi-sig |
| Human | Phishing, social engineering | Education, transaction verification |
ECC Security Checklist
- Use established libraries: Don’t implement ECC from scratch
- Hardware protection: Use HSMs or hardware wallets for high-value keys
- Proper randomness: Cryptographically secure random number generation
- Multi-signature: Distribute trust across multiple keys
- Regular audits: Review cryptographic implementations
ECC Best Practices for Web3 Applications
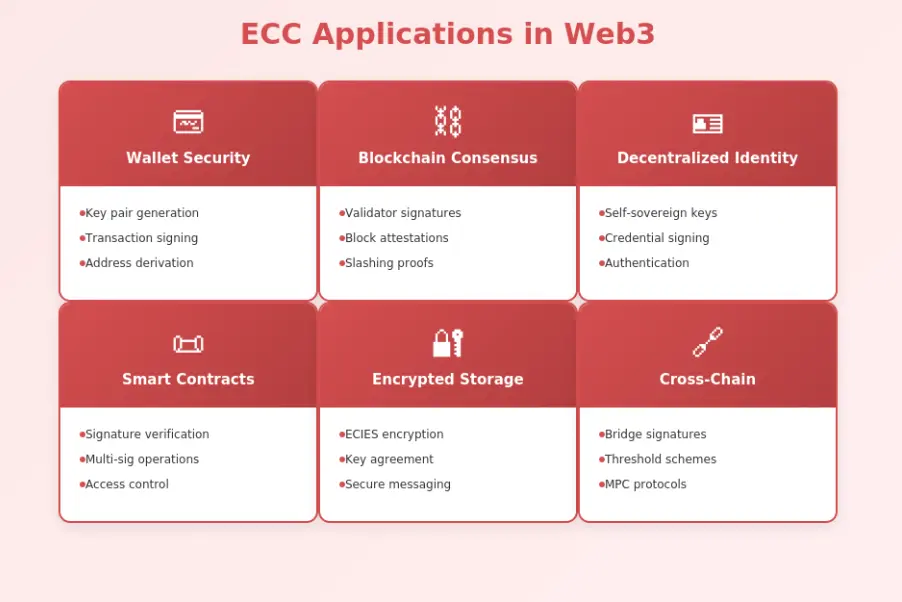
Implementing ECC securely requires following established best practices for key generation, curve selection, and compliance with security standards. Teams building comprehensive trading platform solutions must master these fundamentals.
Secure Key Generation and Storage Strategies
Key generation must use cryptographically secure random number generators (CSPRNGs) with adequate entropy. Operating system APIs like /dev/urandom on Unix or CryptGenRandom on Windows provide suitable randomness. Additional entropy sources (hardware random number generators, user input timing) can strengthen key generation further.
Key storage strategies vary by security requirements. Production systems should use Hardware Security Modules (HSMs) that generate and store keys in tamper-resistant hardware. Consumer applications should leverage platform secure storage APIs (Keychain on iOS, KeyStore on Android). Encryption at rest using strong symmetric algorithms protects keys even if storage is compromised.
Choosing the Right Elliptic Curves
Curve selection impacts security, performance, and interoperability. For Ethereum and Bitcoin compatibility, secp256k1 is mandatory. For new protocols with flexibility, Ed25519 offers faster signing, deterministic signatures that eliminate nonce risks, and simpler implementation. BLS curves enable signature aggregation valuable for consensus protocols.
Avoid deprecated or suspicious curves. NIST curves (P-256, P-384) have faced scrutiny over parameter selection, though no practical attacks are known. Curves with unexplained parameters or those designed by entities with conflict of interest warrant caution. The cryptographic community’s consensus on curve trustworthiness guides safe selection.
Compliance with Web3 Security Standards
Web3 security standards are emerging through organizations like the Ethereum Foundation, Web3 Foundation, and various industry consortia. Standards cover key derivation paths (BIP-32, BIP-44), signature formats, and interoperability requirements. Compliance ensures that implementations work correctly across wallets, dApps, and protocols.
Business Value of ECC in Web3 Security
Beyond technical security, ECC provides business advantages that support enterprise Web3 adoption and competitive positioning in the decentralized economy.
Performance and Cost Benefits of ECC
ECC’s efficiency translates to lower operational costs. Smaller signatures reduce blockchain storage and bandwidth consumption. Faster verification enables higher transaction throughput without proportional hardware scaling. These performance benefits compound across millions of transactions, reducing infrastructure costs significantly.
Scalability Advantages for Enterprise Web3 Networks
Enterprise adoption requires security systems that scale with business growth. ECC’s computational efficiency enables this scaling without prohibitive costs. Networks handling millions of daily transactions can verify signatures economically, supporting high-throughput applications like payment processing, supply chain tracking, and IoT device authentication.
Enhancing Trust in Decentralized Platforms
Trust in Web3 platforms ultimately rests on cryptographic guarantees. ECC’s mathematical foundation provides provable security properties: signatures cannot be forged, private keys cannot be derived from public information, and transactions cannot be repudiated once signed. These guarantees support user trust without requiring trust in intermediaries.
Selecting ECC-Based Web3 Security Solutions
Choosing the right ECC-based security solutions requires evaluating providers, understanding when specialized services add value, and considering future cryptographic evolution
Evaluating Cryptographic Security Providers
When evaluating security providers, consider their track record with ECC implementations, audit history, incident response capabilities, and compliance certifications. Providers should use established libraries with known security properties rather than proprietary implementations. Transparency about cryptographic architecture and third-party security audits demonstrates commitment to security.
When to Invest in ECC-Focused Web3 Security Services
Investment in specialized ECC security services is justified when: handling significant financial value, requiring regulatory compliance, lacking in-house cryptographic expertise, or needing advanced features like threshold signatures or HSM integration. The cost of security incidents typically far exceeds investment in proper security implementation.
Future of ECC in Web3 Security Architecture
ECC will remain central to Web3 security for the foreseeable future, though the landscape will evolve. Post-quantum cryptography will eventually supplement or replace ECC as quantum computing advances. Hybrid schemes combining ECC with post-quantum algorithms may provide transitional security.
New ECC-based protocols will continue emerging, addressing specific use cases like privacy-preserving signatures, efficient multi-party computation, and improved threshold schemes.
| Phase | Stage | Activities | Output |
|---|---|---|---|
| 1 | Requirements | Define security needs, compliance scope | Security specification |
| 2 | Design | Select curves, libraries, key management | Architecture design |
| 3 | Implement | Integrate ECC libraries, build features | Working system |
| 4 | Audit | Security review, penetration testing | Audit report |
| 5 | Deploy | Production deployment, monitoring | Secure production system |
Secure Your Web3 Platform
Implement robust ECC-based security with expert cryptographic architecture guidance.
Elliptic Curve Cryptography in Web3 provides the mathematical foundation for secure, efficient, and scalable decentralized systems. From transaction signing to identity management to consensus mechanisms, ECC enables the trust model that makes Web3 possible. Understanding ECC’s capabilities and limitations empowers organizations to build secure systems today while preparing for the cryptographic evolution that lies ahead. As Web3 adoption grows, the demand for properly implemented ECC-based security will only increase.
Frequently Asked Questions
Elliptic Curve Cryptography is a public-key cryptography approach based on the algebraic structure of elliptic curves over finite fields. In blockchain, ECC enables secure digital signatures for transaction verification, key generation for wallets, and identity authentication. It provides equivalent security to RSA with much smaller key sizes, making it ideal for resource-constrained blockchain environments.
ECC offers equivalent security strength with significantly smaller keys: a 256-bit ECC key provides security comparable to a 3072-bit RSA key. This reduces storage requirements, speeds up cryptographic operations, and lowers bandwidth consumption for transaction signing and verification. These efficiency gains are critical for blockchain networks processing millions of transactions.
ECDSA (Elliptic Curve Digital Signature Algorithm) creates unique digital signatures using a private key that can be verified using the corresponding public key. When signing a transaction, the algorithm generates a signature proving the sender owns the private key without revealing it. Nodes verify this signature mathematically, ensuring transaction authenticity and preventing forgery.
ECC generates the public-private key pairs that form the foundation of Web3 wallet security. The private key, derived from elliptic curve mathematics, signs transactions while the public key verifies them. The mathematical properties of elliptic curves make it computationally infeasible to derive private keys from public keys, protecting wallet funds.
Key security risks include poor random number generation during key creation (which can expose private keys), implementation bugs in cryptographic libraries, side-channel attacks that leak information through timing or power consumption, and improper key storage. These are implementation failures rather than weaknesses in ECC mathematics itself.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







