The rise of cryptocurrency exchanges has transformed the way individuals and institutions trade digital assets. These platforms, functioning as digital marketplaces, are crucial in connecting buyers and sellers across the world. However, their growth has also made them attractive targets for cyberattacks. Billions of dollars have been lost over the past decade due to poor security frameworks and vulnerabilities within exchange infrastructures. Thus, the central challenge remains: how do we secure crypto exchanges in an environment where attackers are constantly evolving their methods?
The answer lies in cryptography. From digital signatures to Public Key Infrastructure (PKI), cryptography provides the backbone for authenticating users, securing transactions, and protecting sensitive data. This blog takes a deep dive into how cryptography secures exchanges, the technologies at play, and how centralized, decentralized, and hybrid exchange models leverage it. We’ll also examine case studies, compliance implications, and the future of cryptographic security in exchanges.
Introduction: Why Security is Non-Negotiable in Crypto Exchanges
Crypto exchanges serve as gateways to the digital asset economy. They are the platforms where users buy, sell, and trade cryptocurrencies. However, with this central role comes immense risk. Hackers constantly target exchanges, exploiting weaknesses in protocols, coding, or user authentication systems. According to industry reports, billions of dollars worth of cryptocurrencies have been stolen from exchanges since the inception of Bitcoin.
To counter these threats, exchanges leverage cryptography—the science of encoding and securing data. By using methods such as digital signatures, hash functions, and PKI, exchanges ensure confidentiality, authenticity, and non-repudiation of transactions. These elements form the backbone of secure trading ecosystems.
The Role of Cryptography in Cryptocurrency Exchanges
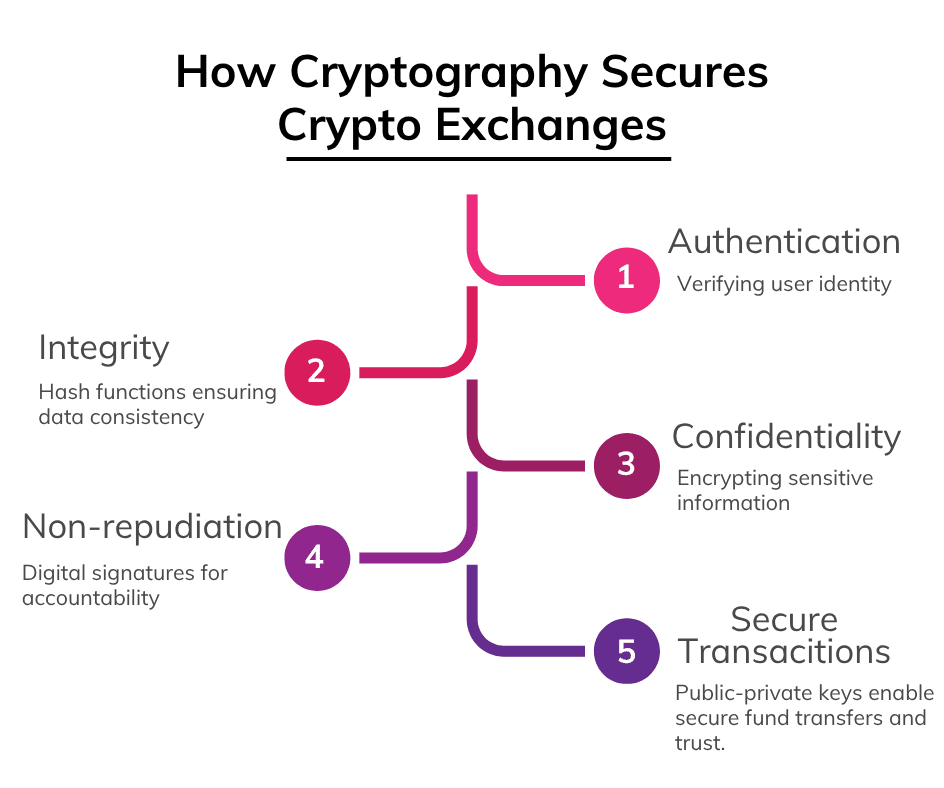
Cryptography is the invisible shield protecting users, platforms, and data in the digital asset market. It ensures:
Authentication confirms that a transaction request truly comes from the rightful owner. Integrity guarantees that data is not altered during transmission, maintaining the trustworthiness of critical financial details. Confidentiality protects sensitive user information from unauthorized access, a necessity in exchanges handling massive volumes of capital. Non-repudiation ensures that once a transaction is signed, the sender cannot later deny it, creating accountability.
Without these core properties, crypto exchanges would become playgrounds for fraud, manipulation, and theft, leading to instability in the ecosystem.
Digital Signatures: The Heart of Transaction Security
Definition and Purpose
Digital signatures are cryptographic mechanisms that validate the authenticity and integrity of transactions. For exchanges, they ensure that only authorized users can initiate trades, that transactions cannot be tampered with once signed, and that each action can be traced back to its rightful owner.
Process Flow
The process of using digital signatures in exchanges involves several steps. First, the trader initiates a transaction on the exchange. This transaction is then hashed to produce a unique identifier, which ensures data integrity. Next, the trader’s private key is used to encrypt the hash, creating the digital signature. Finally, the exchange or receiving party uses the trader’s public key to verify the signature, ensuring the transaction’s authenticity.
Application in Exchanges
Digital signatures are essential across all exchange models. On centralized platforms, signatures protect user login data and withdrawal requests. In decentralized platforms, they validate direct transactions between users, which is particularly important for peer to peer crypto exchange operations. Hybrid models leverage digital signatures to maintain integrity across both centralized servers and decentralized blockchain records. By providing verifiable proof of ownership, digital signatures play a pivotal role in preventing fraud and establishing trust.
Protect Your Crypto Exchange with Digital Signatures & PKI
Crypto Exchange Security with PKIHash Functions: Guarding Data Integrity
While digital signatures ensure authenticity, hash functions guarantee integrity. A hash function takes any input—such as a transaction message—and converts it into a fixed-length string of characters, commonly referred to as the hash. Even the slightest change in the input data produces an entirely different hash, making tampering immediately noticeable.
Each transaction recorded on a blockchain is hashed, creating immutable records that cannot be altered retroactively. Exchanges also use hashing for password protection, storing only hashed versions of user credentials so that even if a database is compromised, raw passwords are never exposed. Fraud detection mechanisms further rely on hashes, as any attempt to alter transaction data results in a mismatched hash, instantly flagging suspicious activity. This makes hashing indispensable for both centralized exchange development and peer-to-peer crypto exchange models.
Public Key Infrastructure (PKI): The Framework of Trust
Public Key Infrastructure is a framework of technologies, policies, and standards that manage encryption and digital certificates. PKI enables secure communication between users and platforms by verifying identities and encrypting data. It brings structure and scalability to cryptographic security within large trading ecosystems.
In crypto exchanges, PKI ensures that every user has a verified cryptographic identity, which is crucial for preventing impersonation and fraud. SSL/TLS certificates deployed through PKI encrypt web traffic, protecting sensitive user data such as login credentials and private keys. APIs that connect trading engines, wallets, and payment processors are also secured through PKI-based certificates, preventing unauthorized access. Furthermore, PKI helps exchanges meet compliance standards by maintaining auditable cryptographic logs, ensuring regulators can trace and verify activities without compromising user privacy.
Cryptographic Applications in Different Exchange Models
Centralized exchanges are often the entry point for newcomers. They provide liquidity, user-friendly interfaces, and customer support, but also carry the immense responsibility of safeguarding vast amounts of user funds. Cryptography ensures that user private keys are securely stored in hardware security modules, that databases holding sensitive information are encrypted, and that all transactions are signed and verified before execution. These measures collectively prevent breaches and mitigate insider threats.
On the other hand, decentralized crypto trading platforms allow users to interact directly with smart contracts without intermediaries. Cryptography ensures that these contracts execute only when valid signatures are provided, maintaining immutability and transparency of data on the blockchain. Advanced methods like zero-knowledge proofs further enhance privacy, allowing users to prove their rights or balances without revealing underlying details.
Peer-to-peer crypto exchange models empower individuals to trade directly, without relying on centralized infrastructure. In such systems, cryptographic protections include secure escrow services using multi-signature wallets, encrypted communication between buyers and sellers, and verification of trades using hashed digital receipts. These mechanisms preserve trust and fairness even in the absence of intermediaries.
Advanced Cryptographic Techniques in Exchange Security
The growing sophistication of threats has pushed exchanges to adopt advanced cryptographic methods beyond basic hashing and signing. Multi-signature wallets, for instance, require multiple private keys to authorize a transaction, reducing the risk associated with a single compromised key. Hardware Security Modules (HSMs) are specialized devices that securely generate and store private keys, making it virtually impossible for attackers to extract them.
Zero-knowledge proofs represent another breakthrough, enabling users to prove they possess certain information—such as account balances—without disclosing the actual data. This strengthens both privacy and security in decentralized platforms. Homomorphic encryption also shows promise, allowing computation on encrypted data without decrypting it first. This could allow exchanges to process transactions securely without exposing sensitive information.
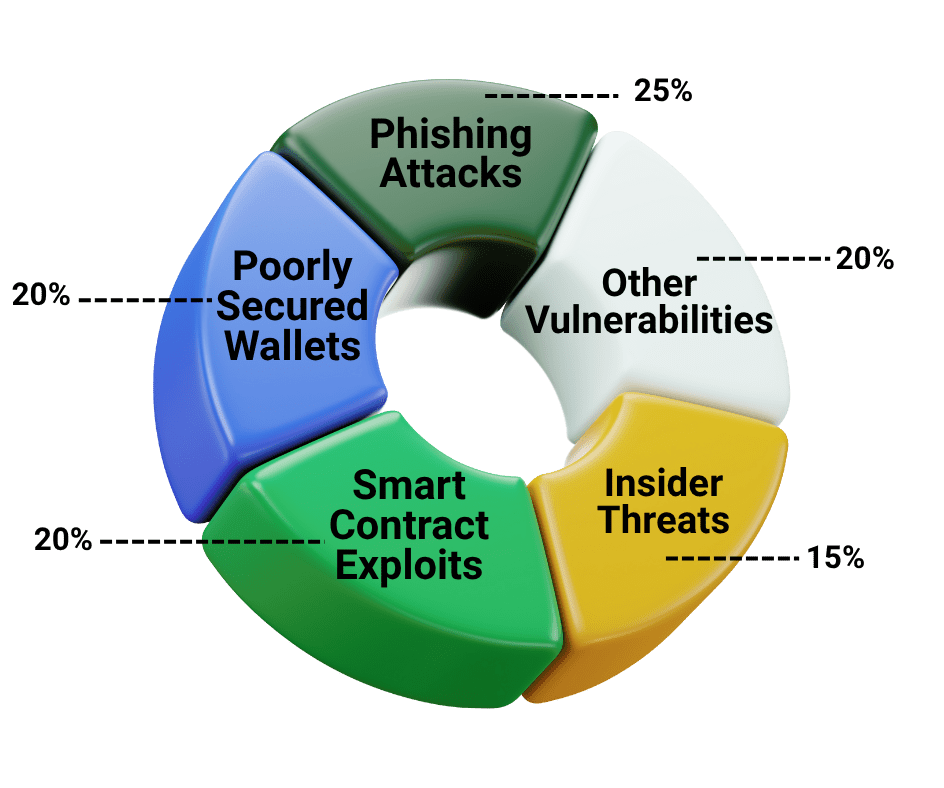
Common Threats to Crypto Exchanges
Cryptographic Algorithms and Security Protocols
Security in cryptocurrency exchanges is not limited to digital signatures and PKI. Multiple cryptographic algorithms and protocols strengthen overall resilience:
- SHA-256: A cryptographic hash function used for transaction integrity in Bitcoin and other coins.
- Elliptic Curve Cryptography (ECC): Provides strong security with smaller keys, improving efficiency.
- AES Encryption: Protects sensitive data stored in wallets and exchange databases.
- TLS/SSL: Ensures encrypted communication between users and exchange servers.
These protocols are vital for all types of exchanges, from centralized to decentralized crypto trading platforms.
Real-World Case Studies: Cryptography in Action
Mt. Gox (2014)
Mt. Gox, once the world’s largest Bitcoin exchange, collapsed due to poor wallet management and the absence of multi-signature systems. Hackers stole approximately 850,000 Bitcoins, causing massive financial losses and shaking trust in crypto exchanges. This incident highlighted the critical need for proper cryptographic safeguards and regular security audits. It remains a cautionary tale for centralized exchange security.
Binance (2019)
In 2019, Binance suffered a breach where hackers exploited API vulnerabilities to withdraw 7,000 Bitcoins. The exchange’s layered cryptographic security, multi-signature verification, and cold storage minimized the impact. Binance quickly reimbursed users and enhanced security protocols. The event demonstrated the importance of robust cryptography and proactive risk management.
KuCoin (2020)
KuCoin experienced a hack due to compromised private keys, affecting large amounts of cryptocurrencies. Advanced cryptographic recovery mechanisms and multi-signature wallets enabled recovery of a significant portion of assets. The breach emphasized disaster recovery planning and cryptographic resilience. KuCoin’s response reinforced the role of strong cryptography in maintaining trust.
These cases show that cryptography is essential for securing exchanges and protecting user assets against potential threats.
Challenges and Limitations of Cryptographic Security
Despite its strengths, cryptography is not without limitations. The looming rise of quantum computing presents a major threat, as quantum algorithms could potentially break current encryption methods. User errors, such as losing private keys or falling victim to phishing attacks, can bypass even the most secure cryptographic defenses. Advanced cryptographic techniques also introduce scalability challenges, as they may increase computational load and affect exchange performance. Balancing regulatory compliance with privacy and decentralization remains another complex challenge. Addressing these issues will require continuous research, innovation, and collaboration across the industry.
The Future of Cryptographic Security in Exchanges
The evolution of cryptographic techniques points toward an even safer future for crypto trading. Post-quantum cryptography is being actively developed to defend against potential quantum threats. Biometric integration with cryptographic systems may soon enhance user authentication by tying transactions to unique physical traits. Decentralized identity solutions powered by blockchain and PKI could lead to exchanges that are fully self-sovereign, eliminating reliance on centralized verification authorities.
As these advancements take shape, the next generation of exchanges will likely blend cutting-edge security with a seamless user experience, further strengthening user trust in the global digital asset ecosystem.
Final Words
From the simplest Bitcoin transfers to advanced decentralized ecosystems, cryptography remains the cornerstone of security. Digital signatures guarantee authenticity, hash functions safeguard integrity, and PKI establishes scalable trust. Whether in centralized platforms, decentralized crypto trading systems, or peer-to-peer crypto exchange models, cryptography ensures that users can trade, invest, and innovate without fear.
As threats grow more sophisticated, so too will the cryptographic defenses guarding this digital frontier. By embracing these advancements, exchanges not only protect assets but also preserve the core promise of cryptocurrency: trust without intermediaries.
What does PKI do?
Public Key Infrastructure (PKI) manages keys and digital certificates, enabling secure communication and user verification. It protects APIs, wallets, and trading engines while ensuring compliance through auditable cryptographic logs, making it essential for all types of exchanges.
What is cryptography’s role?
Cryptography is the backbone of security in crypto exchanges. It protects transactions from tampering, keeps sensitive user data safe, and ensures authenticity and integrity. Both centralized and decentralized platforms rely on cryptography to prevent hacks, fraud, and unauthorized access, making secure trading possible.
Why are hash functions important?
Hash functions generate unique digital fingerprints for data, instantly detecting any tampering. They secure transaction records, passwords, and blockchain entries, ensuring integrity across both centralized exchange development and decentralized trading platforms.
How do digital signatures build trust?
Digital signatures validate the authenticity of transactions using private and public keys. They prevent unauthorized changes, prove ownership, and create accountability. This is crucial for peer-to-peer crypto exchange operations as well as maintaining trust on centralized exchanges.
What’s next for cryptography in exchanges?
Exchanges face future threats from quantum computing. Emerging solutions like post-quantum cryptography, zero-knowledge proofs, biometric authentication, and decentralized identity systems will improve security, privacy, and trust in both centralized and peer-to-peer crypto exchange models.
How did Mt. Gox, Binance, and KuCoin show cryptography’s importance?
- Mt. Gox (2014): Theft of 850,000 Bitcoins due to poor wallet management and lack of multi-signature systems.
- Binance (2019): Hackers exploited API vulnerabilities, but layered cryptography, cold storage, and multi-signature verification minimized losses.
- KuCoin (2020): Private key compromise was mitigated with advanced multi-signature wallets and recovery mechanisms, demonstrating cryptographic resilience.