Key Takeaways
- A Web3 revocation registry enables credential issuers to invalidate verifiable credentials while allowing verifiers to check status in real-time without central authority dependency
- Effective decentralized revocation registry design balances privacy (hiding which credentials are checked), security (preventing unauthorized changes), and scalability (handling millions of credentials)
- Web3 identity revocation can be implemented on-chain (maximum transparency, higher cost) or off-chain (lower cost, requires availability guarantees) with hybrid approaches offering best tradeoffs
- Privacy-preserving verifiable credentials revocation uses cryptographic accumulators, zero-knowledge proofs, or bloom filters to prevent correlation attacks that could track credential holders
- DID revocation mechanism security requires protecting against unauthorized revocation, ensuring registry availability, implementing key management, and maintaining tamper resistance
- Credential revocation in Web3 governance models determine who controls revocation rights: issuers, delegated parties, multi-sig authorities, or decentralized governance structures
- Enterprise revocation registry use cases include employee access management, compliance verification, supply chain credentials, and cross-organizational identity verification
- Choosing between building custom registries or integrating existing solutions depends on privacy requirements, scale needs, governance complexity, and interoperability requirements
Understanding Revocation Registries in Web3
The integrity of any credential system depends on the ability to invalidate credentials when circumstances change. In the Web3 ecosystem, where verifiable credentials enable decentralized identity verification, revocation registries serve as the critical infrastructure that maintains this integrity. Understanding how these registries function and what makes them effective is essential for anyone building or evaluating Web3 identity systems.
What Is a Revocation Registry?
A Web3 revocation registry is a system that tracks the validity status of issued credentials, enabling verifiers to confirm that credentials haven’t been revoked before accepting them. Unlike traditional certificate revocation lists (CRLs) that rely on centralized authorities, Web3 registries leverage blockchain technology, cryptographic proofs, and decentralized infrastructure to provide tamper-resistant, publicly verifiable revocation status without single points of failure.
The registry functions as a shared source of truth that credential issuers update when revoking credentials and that verifiers query during credential verification. This seemingly simple function becomes complex when considering the requirements for privacy, scalability, security, and decentralization that Web3 systems demand. An effective revocation registry in Web3 must address all these concerns while remaining practical for real-world deployment.
Why Revocation Matters in Web3 Identity Systems?
Credentials in Web3 represent real-world attestations: employment status, professional certifications, educational degrees, organizational memberships, and regulatory approvals. These relationships change over time. Employees leave organizations, certifications expire or get suspended, companies lose regulatory approvals, and credentials may be issued in error. Without revocation capability, invalid credentials would remain usable indefinitely, undermining the entire system’s trustworthiness.
The stakes are particularly high in Web3 because credentials often gate access to financial services, organizational resources, and sensitive operations. A revoked credential being accepted could enable unauthorized access to funds, confidential information, or critical systems. Web3 identity revocation provides the mechanism to ensure that only currently valid credentials grant such access.
Role of Revocation in Verifiable Credentials
Verifiable credentials (VCs) include a reference to where their revocation status can be checked. When a verifier receives a credential, the complete verification process includes not only validating the cryptographic signature and checking the credential’s structure but also querying the designated revocation registry to confirm the credential hasn’t been invalidated. This status check is integral to the credential verification workflow defined by W3C standards.
The verifiable credentials revocation mechanism must be specified at issuance time, embedded in the credential itself. This design ensures that verifiers know exactly where and how to check status, maintaining the decentralized nature of the ecosystem where credentials can be verified by anyone without contacting the issuer directly.
Important: Revocation registry design significantly impacts overall system security and privacy. Poorly designed registries can leak information about credential usage, enable denial-of-service attacks on verification, or allow unauthorized parties to revoke valid credentials. The registry is often the most critical infrastructure component in a verifiable credentials deployment.
How Web3 Revocation Registries Work?
Understanding the mechanics of revocation registries helps evaluate their effectiveness and appropriateness for specific use cases. The workflow involves multiple parties and technical components working together to maintain credential validity information.
Credential Lifecycle and Revocation Flow
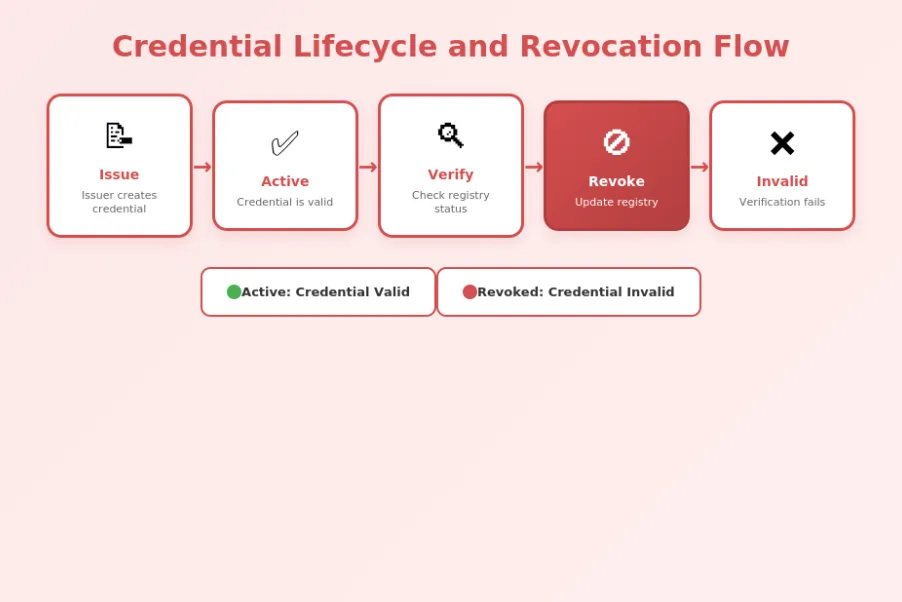
The credential lifecycle begins with issuance, where the issuer creates a credential and assigns it an identifier that links to the revocation registry. The credential enters an “active” state where it can be verified and accepted. When circumstances require revocation, the issuer updates the registry to mark the credential as revoked. Verifiers checking the credential after this point will see the revoked status and reject the credential.
This flow appears simple but involves careful coordination. The credential must contain accurate registry references at issuance. The registry must be available when verifiers check status. The update mechanism must be secure against unauthorized changes. The timing of revocation must be handled appropriately to prevent race conditions where credentials are accepted during the revocation process.
On-Chain vs Off-Chain Revocation Models
On-chain revocation stores status directly on a blockchain through smart contracts. Every revocation becomes a permanent, transparent, tamper-proof record. Verifiers can query the blockchain directly without trusting intermediate services. However, on-chain storage incurs gas costs for every update and exposes revocation events publicly, which may reveal information about credential usage patterns.
Off-chain revocation uses signed documents, databases, or distributed storage with cryptographic proofs that can be verified without blockchain queries. Status lists signed by the issuer can be cached and distributed efficiently. Costs are lower, but the system requires trust in availability infrastructure. Many practical deployments use hybrid models: off-chain status lists with periodic on-chain commitments that provide anchoring and auditability. Organizations building professional crypto exchange platforms carefully evaluate these tradeoffs for their compliance credential systems.
Real-Time Revocation Verification Process
When a verifier receives a credential for verification, the process includes extracting the credential’s status reference, querying the designated registry, interpreting the response, and making an accept/reject decision based on current status. This entire process typically happens in real-time during presentation, adding latency to verification flows.
Effective registries optimize for query performance, often using caching strategies, content delivery networks for off-chain lists, or efficient blockchain query patterns for on-chain data. The verification process must also handle error cases: registry unavailable, credential not found in registry, or ambiguous status responses.
Core Components of an Effective Revocation Registry
Building or evaluating a decentralized revocation registry requires understanding its core technical components and how they contribute to overall effectiveness.
Registry Data Structures and Storage Models
The choice of data structure significantly impacts registry performance and capabilities. Simple approaches use lists or sets of revoked credential identifiers. More sophisticated designs use Merkle trees (enabling efficient proofs of inclusion/exclusion), bloom filters (probabilistic membership testing with no false negatives), or cryptographic accumulators (supporting efficient batch updates and zero-knowledge proofs).
Storage models range from full blockchain storage to IPFS for content-addressed off-chain data, to traditional databases with signed outputs. Each model offers different tradeoffs in terms of cost, availability, decentralization, and query efficiency. The optimal choice depends on specific use case requirements.
Indexing, Lookups, and Verification Speed
Verification speed directly impacts user experience and system throughput. Effective registries implement indexing strategies that enable O(log n) or O(1) lookups even with millions of credentials. For blockchain-based registries, this may involve maintaining indexed views off-chain while using on-chain data as the source of truth.
Caching strategies further improve performance by reducing redundant queries. However, caching introduces staleness risks where recently revoked credentials might still appear valid. Registry designs must specify freshness requirements and cache invalidation strategies that balance performance with security needs.
Integration with DIDs and Identity Wallets
The DID revocation mechanism must integrate seamlessly with the broader decentralized identity ecosystem. DIDs (Decentralized Identifiers) serve as the anchoring identifiers for both issuers and holders. Identity wallets must understand how to extract and query revocation information. Standards like W3C Verifiable Credentials define how revocation references are embedded in credentials.
Effective integration means wallets can automatically check revocation status during verification without manual intervention. It also means issuers can manage revocation through standard tooling rather than custom implementations. This interoperability is essential for ecosystem growth and adoption.
| Model | Privacy | Cost | Best For |
|---|---|---|---|
| On-Chain Status List | Low (public) | High (gas fees) | Transparency-critical |
| Signed Off-Chain List | Medium | Low | Cost-sensitive |
| Cryptographic Accumulator | High (ZK capable) | Medium | Privacy-critical |
| Hybrid Anchored | Medium-High | Low-Medium | Balanced requirements |
Privacy-Preserving Revocation Mechanisms
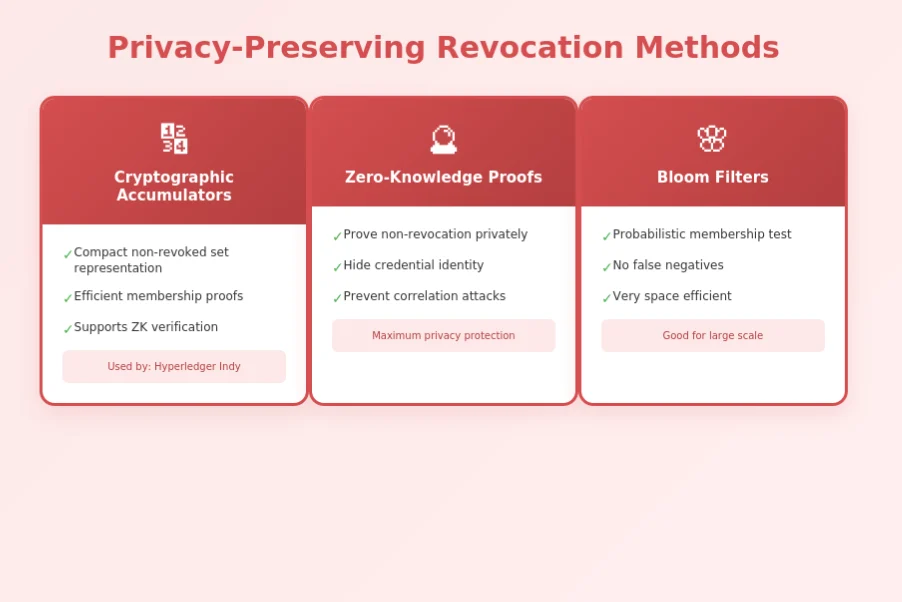
Privacy in revocation registries is often underestimated but critically important. Naive implementations can leak significant information about credential holders and their activities.
Preventing Correlation and Identity Leakage
When a verifier queries a registry for a specific credential ID, that query itself reveals information: someone is presenting that credential at this moment. If registries log queries or if multiple verifiers can observe queries, patterns emerge that can track when and where credential holders use their credentials. This correlation attack undermines the privacy benefits of decentralized identity.
Effective privacy-preserving designs prevent this correlation through techniques like credential unlinkability (where different presentations use different identifiers that can’t be correlated), private query protocols (where the registry can’t see which credential is being checked), or universal witness downloads (where verifiers download entire status sets rather than querying individual credentials).
Zero-Knowledge Proofs for Revocation Status
Zero-knowledge proofs enable a credential holder to prove their credential is not revoked without revealing the credential’s identifier to the verifier or registry. Using cryptographic accumulators with ZK proof systems, the holder can demonstrate membership in the “non-revoked” set without exposing which specific credential they hold.
This approach provides the strongest privacy guarantees but adds computational complexity. The holder must obtain current accumulator witnesses (proofs of non-revocation) and generate ZK proofs during verification. Advances in proof systems like Plonk and recursive SNARKs are making these approaches more practical for real-world deployment.
Selective Disclosure and User Privacy
Selective disclosure allows credential holders to reveal only specific attributes while hiding others. For revocation, this means the holder can prove their credential is valid without revealing which specific credential among many they hold. This capability, combined with privacy-preserving revocation checks, enables truly minimal disclosure where verifiers learn only what they need.
Implementing selective disclosure with revocation requires careful cryptographic design. The credential must be structured to support both attribute hiding and status verification. BBS+ signatures and similar schemes are commonly used because they naturally support these combined requirements.
Security Requirements for Web3 Revocation Registries
Security failures in revocation registries can have severe consequences: unauthorized revocation disrupts legitimate users, compromised registries enable credential fraud, and unavailable registries prevent verification entirely.
Protecting Against Unauthorized Revocation
Only authorized parties should be able to revoke credentials. This typically means only the original issuer (or their delegates) can update revocation status. Protection mechanisms include cryptographic signatures on revocation transactions, smart contract access controls, multi-signature requirements for sensitive operations, and audit logging of all revocation actions.
Key management is critical: if an issuer’s revocation key is compromised, attackers could revoke valid credentials (denial of service) or potentially un-revoke credentials if the registry supports that operation. Hardware security modules, key rotation policies, and threshold signatures help protect these critical keys.
Registry Integrity and Tamper Resistance
Registry integrity ensures that revocation status accurately reflects issuer intentions and hasn’t been maliciously modified. Blockchain-based registries inherit the tamper resistance of their underlying chain. Off-chain registries rely on cryptographic signatures and potentially periodic on-chain commitments for auditability.
Tamper resistance also means protecting historical records. In some use cases, verifiers need to know the revocation status at a specific point in time (e.g., “was this credential valid when this transaction occurred?”). Effective registries maintain auditable history that enables such temporal queries.
Attack Vectors and Failure Scenarios
Common attack vectors include denial-of-service attacks on registry infrastructure, key compromise enabling unauthorized updates, replay attacks using outdated status information, and eclipse attacks isolating verifiers from accurate status. Failure scenarios include registry unavailability (preventing verification), data corruption, and cascading failures when registries depend on other infrastructure.
Effective registries implement defense-in-depth: redundant infrastructure, monitoring and alerting, graceful degradation when components fail, and clear operational procedures for incident response. The registry’s availability and security often exceed the requirements of the credentials it serves.
Security Checklist for Revocation Registries
- Access Control: Only authorized parties can update revocation status
- Key Management: Revocation keys are protected by HSMs or threshold schemes
- Availability: Redundant infrastructure ensures continuous access
- Audit Trail: All revocation actions are logged and auditable
- Tamper Resistance: Historical records cannot be modified
Scalability and Performance Considerations
Real-world deployments must handle significant scale: millions of credentials, thousands of revocations per day, and verification queries at high throughput. Scalability is often the practical constraint that determines which registry approaches are viable.
Handling Large-Scale Credential Revocation
Large-scale revocation presents challenges across storage, update, and query operations. Storage must accommodate growing credential counts. Updates (revocations) must be processed without blocking queries. Queries must remain fast even as the revoked set grows. Batch operations become essential: revoking credentials in groups rather than individually reduces overhead.
Data structure choices significantly impact scalability. Merkle trees enable efficient proofs but require re-computation on updates. Bloom filters offer fast queries but have size/accuracy tradeoffs. Accumulators support efficient updates and proofs but require careful parameter selection. Teams building comprehensive trading platform infrastructure evaluate these tradeoffs for their credential management needs.
Cost Optimization and Gas Efficiency
For on-chain registries, gas costs directly impact operational budgets. Each revocation transaction costs gas, and query operations (if on-chain) add further costs. Optimization strategies include batching multiple revocations in single transactions, using efficient data encodings, and choosing cost-effective blockchains or Layer 2 solutions.
The tradeoff between cost and decentralization is real: more centralized approaches (off-chain registries) are cheaper but sacrifice some trustlessness. Hybrid designs that anchor off-chain registries to on-chain commitments provide a middle ground with periodic, amortized on-chain costs.
Layer 2 and Off-Chain Scaling Strategies
Layer 2 scaling brings blockchain benefits (tamper resistance, decentralization) at reduced cost. ZK-Rollups and Optimistic Rollups can host registry contracts with significantly lower transaction costs than L1. Validium approaches store data off-chain while maintaining on-chain validity proofs.
Pure off-chain strategies using IPFS, Arweave, or similar systems provide cost-effective storage with content addressing that enables verification. Combined with signed status lists and periodic on-chain commitments, these approaches scale to millions of credentials while maintaining auditability.
| Approach | Scale | Cost per Revocation | Decentralization |
|---|---|---|---|
| Ethereum L1 | 10K-100K | $5-50 | Maximum |
| L2 Rollups | 100K-1M | $0.10-1 | High |
| Off-Chain + Anchoring | 1M-100M | $0.001-0.01 | Medium |
| Pure Off-Chain | Unlimited | Minimal | Lower |
Governance and Trust Models in Revocation Registries
Technical implementation is only part of effective revocation. Governance determines who can revoke credentials and under what circumstances, establishing the trust model that users and verifiers rely upon.
Who Controls Revocation Rights?
The default model grants revocation rights to the credential issuer, which makes intuitive sense since issuers attest to credential validity and should be able to withdraw that attestation. However, other models exist: delegated revocation (issuer authorizes another party), holder-requested revocation (credential holder can request their own credential be revoked), and automated revocation (based on triggers or expiration logic).
Some scenarios require more complex governance: credentials issued by organizations that no longer exist, credentials for which the issuer’s keys have been compromised, or credentials that multiple parties have legitimate interest in revoking. Governance frameworks must anticipate these scenarios and define clear procedures.
Decentralized Governance vs Central Issuers
Fully decentralized governance might use DAOs or multi-sig schemes to control revocation, distributing trust across multiple parties. This prevents single points of failure and abuse but adds complexity and latency to revocation decisions. Central issuer control is simpler and faster but concentrates power.
The appropriate model depends on the credential type and trust requirements. Government-issued credentials naturally have centralized issuers. Community credentials might benefit from decentralized governance. Professional credentials might use organizational governance with oversight mechanisms.
Trust Frameworks and Compliance Alignment
Credential revocation in Web3 solutions must align with regulatory and compliance requirements. Financial credentials may need to meet specific revocation timeline requirements. Healthcare credentials might have privacy constraints on revocation visibility. Educational credentials might need to maintain certain records for accreditation purposes.
Trust frameworks like EBSI (European Blockchain Services Infrastructure) or specific industry standards define revocation requirements that registries must satisfy. Alignment with these frameworks is essential for credentials to be accepted within their ecosystems.
Enterprise and Real-World Use Cases
Understanding practical use cases helps evaluate which registry features matter most and how different designs serve different needs.
Identity Verification and Access Control
Organizations issue credentials to employees, contractors, and partners that grant access to systems and resources. When these relationships end, credentials must be revoked immediately to prevent unauthorized access. The registry must support real-time revocation and verification to ensure that access is terminated promptly.
Cross-organizational scenarios add complexity: credentials issued by one organization and verified by another require shared revocation infrastructure or interoperable registry protocols. This is common in federated identity scenarios and supply chain relationships.
Compliance, KYC, and Regulatory Use Cases
KYC (Know Your Customer) credentials attest that identity verification has been completed. These credentials may need revocation when customer status changes, when the verification becomes outdated, or when regulatory requirements change. Compliance credentials for organizations face similar lifecycle management needs.
Regulatory use cases often have specific requirements: audit trails, retention periods, geographic restrictions, and notification requirements. Effective registries must support these compliance needs while maintaining the benefits of decentralized verification.
Cross-Platform and Cross-Organization Revocation
Web3’s promise includes credentials that work across platforms and organizations. This requires revocation registries that multiple parties can query and trust. Standards compliance, clear governance, and broad accessibility become essential requirements.
Interoperability challenges include different registry formats, query protocols, and trust assumptions across ecosystems. Work on standards like W3C Verifiable Credentials Status List aims to address these challenges by defining common approaches that different implementations can support.
Common Challenges and Design Trade-Offs
Every revocation registry design involves trade-offs between competing requirements. Understanding these trade-offs helps make informed decisions appropriate for specific use cases.
Privacy vs Transparency Trade-Off
Transparency enables anyone to verify revocation status independently, supporting the trustless nature of Web3. However, transparency can compromise privacy by revealing which credentials exist, when they were revoked, and potentially when they’re being used. Privacy-preserving approaches add complexity and often computational overhead.
The appropriate balance depends on use case requirements. Public professional certifications may prioritize transparency. Personal identity credentials may prioritize privacy. Financial credentials may need both depending on the specific context.
UX Challenges in Revocation Handling
From a user experience perspective, revocation introduces friction. Verification takes longer when status must be checked. Credential holders may face confusion when their credentials are revoked unexpectedly. Verifiers must handle revoked credentials gracefully without exposing users to confusing error messages.
Good UX design includes clear communication about credential status, proactive notification when revocation approaches (for expiring credentials), and graceful degradation when revocation checks fail due to connectivity or availability issues.
Interoperability Across Web3 Standards
Multiple standards and approaches exist for revocation: W3C Status List, Hyperledger Indy accumulators, EIP-based on-chain registries, and various proprietary implementations. A credential issued using one approach may not be verifiable by systems expecting another approach.
Addressing interoperability requires either converging on standards (ongoing but slow), building adapters between systems (complex but practical), or designing for flexibility (supporting multiple approaches). Most practical deployments currently work within specific ecosystems while monitoring standards evolution.
Choosing or Building the Right Revocation Registry
The decision between building custom revocation infrastructure and integrating existing solutions depends on specific requirements, resources, and strategic considerations.
Build vs Integrate Decision Factors
Building custom registries provides maximum control and customization but requires significant expertise and ongoing maintenance. Integration with existing solutions (like Veramo, Spruce, or other identity platforms) provides faster time-to-market with established implementations but may not meet all requirements.
Factors favoring custom builds include: unique privacy requirements, specific governance models, scale exceeding existing solutions, and strategic importance of owning core infrastructure. Factors favoring integration include: standard use cases, limited resources, desire for interoperability, and need for proven implementations.
Evaluation Criteria for Revocation Solutions
When evaluating existing solutions, key criteria include: supported standards and interoperability, privacy features and options, scalability demonstrated at similar scale, security posture and audit history, governance flexibility, operational requirements, and total cost of ownership including gas fees.
Proof-of-concept testing with realistic scenarios helps validate that solutions meet requirements in practice. Edge cases around revocation timing, error handling, and recovery scenarios often reveal limitations not obvious from documentation.
When to Use Managed Identity Infrastructure
Managed identity infrastructure providers offer revocation as part of comprehensive identity platforms. This approach suits organizations that want to focus on their core use case rather than identity infrastructure, have standard requirements that managed platforms address, prefer operational simplicity, and can accept the platform’s governance and privacy model.
Teams at professional digital asset infrastructure providers often evaluate managed versus custom solutions based on specific compliance and security requirements that vary by jurisdiction and use case.
| Phase | Stage | Activities | Output |
|---|---|---|---|
| 1 | Requirements | Define privacy, scale, governance needs | Specification |
| 2 | Evaluation | Assess build vs integrate options | Decision |
| 3 | Implementation | Build or integrate chosen solution | Working registry |
| 4 | Testing | Security audit, performance testing | Validated system |
| 5 | Operations | Deploy, monitor, maintain | Production system |
Build Identity Infrastructure
Implement secure, scalable revocation registries with expert Web3 identity guidance.
Effective Web3 revocation registries combine thoughtful technical design with appropriate governance and operational excellence. The choice of registry approach significantly impacts privacy, scalability, security, and interoperability. By understanding the trade-offs between different models and carefully evaluating requirements, organizations can implement revocation infrastructure that maintains credential integrity while supporting the decentralized identity ecosystem’s growth and adoption.
Frequently Asked Questions
Verifiable credentials need revocation because real-world circumstances change: employees leave organizations, certifications expire, licenses get suspended, and credentials may be issued in error. Without revocation capability, invalid credentials would remain usable forever, creating security and compliance risks. Revocation ensures the credential ecosystem maintains integrity by allowing issuers to invalidate credentials when necessary.
In decentralized identity, credential revocation typically involves the issuer updating a registry entry that verifiers can check. The registry may be on-chain (smart contract) or off-chain (signed status lists). When a verifier receives a credential, they query the registry using the credential’s identifier to confirm it hasn’t been revoked. This check happens in real-time during verification.
On-chain revocation stores revocation status directly on a blockchain, providing maximum transparency and tamper resistance but incurring gas costs for every update. Off-chain revocation uses signed documents or databases with cryptographic proofs, reducing costs but requiring trust in availability. Many systems use hybrid approaches, posting periodic on-chain commitments to off-chain data.
Key security risks include unauthorized revocation (attackers revoking valid credentials), registry unavailability (preventing verification), key compromise (allowing malicious updates), and replay attacks (using old revocation status). Effective registries implement access controls, redundancy, key management protocols, and cryptographic proofs to mitigate these risks.
Typically, the credential issuer controls revocation rights since they originally issued the credential and are responsible for its validity. However, governance models vary: some systems allow delegation to authorized parties, others implement multi-signature requirements, and some enable credential holders to request revocation. The control model should align with trust requirements and use case needs.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







