Key Takeaways
- Function visibility in smart contracts determines access control levels for each function, directly impacting security and contract architecture design.
- Solidity offers four visibility types: public, external, internal, and private, each serving distinct purposes in contract architecture.
- External functions optimize gas consumption for large data inputs by reading directly from calldata instead of copying to memory.
- Private functions provide maximum encapsulation, restricting access to only the defining contract without inheritance exposure.
- Internal functions enable code reuse across inheritance hierarchies while maintaining protection from external unauthorized access.
- Visibility misconfigurations rank among the top security vulnerabilities discovered during professional Function Visibility in Smart Contracts audits worldwide.
- Proxy and upgradeable contract patterns require careful visibility planning to maintain security across implementation versions.
- Following the principle of least privilege means defaulting to the most restrictive visibility that still meets functional requirements.
- Enterprise protocols in USA, UK, UAE, and Canada require rigorous visibility audits before mainnet deployment approval.
- Future-proof architecture combines proper visibility patterns with modular design for sustainable long-term protocol evolution.
Understanding Function Visibility in Smart Contracts
Function visibility in smart contracts represents one of the most critical architectural decisions developers face when building blockchain applications. This fundamental concept determines which entities can invoke specific functions within your smart contract code, establishing the access control framework that protects sensitive operations. Understanding visibility is essential for creating secure, efficient, and maintainable decentralized applications.
Our agency has spent over eight years implementing function visibility patterns for enterprise clients across the USA, UK, UAE, and Canada. This extensive experience has demonstrated that visibility decisions made during initial architecture phases have lasting implications for security, gas efficiency, and system scalability. Getting visibility right from the start prevents costly refactoring and security incidents.
Solidity provides four distinct visibility modifiers that control function access: public, external, internal, and private. Each serves specific purposes within contract architecture, and selecting the appropriate visibility requires understanding both the immediate functional requirements and long-term architectural implications for your blockchain application.
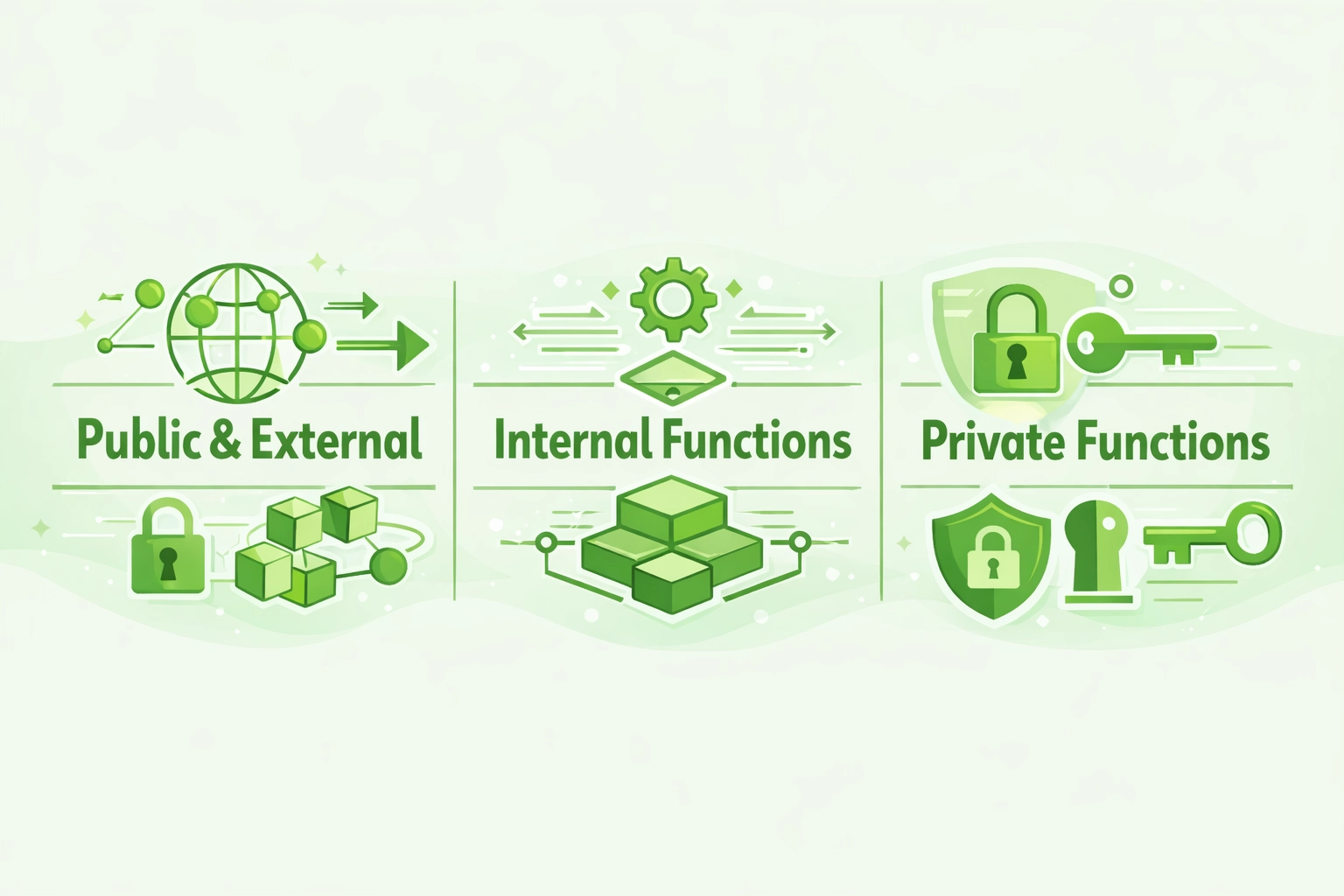
Overview of Visibility Types in Solidity Function Visibility in Smart Contracts
Each visibility type serves distinct purposes in Function Visibility in Smart Contracts architecture and system design.
Public & External
- Accessible from outside the contract
- Public allows internal calls too
- External optimizes calldata reading
- Used for user-facing interfaces
Internal Functions
- Accessible within contract and children
- Enables inheritance-based reuse
- Hidden from external callers
- Ideal for shared utility logic
Private Functions
- Strictest access restriction
- Only defining contract can call
- Not accessible to child contracts
- Maximum encapsulation achieved
Public Functions and Their Role in Open Blockchain Systems
Public functions form the backbone of user interaction with Function Visibility in Smart Contracts. When a function is declared public, it becomes callable both from external transactions and from within the contract itself. This dual accessibility makes public functions versatile for many use cases, from token transfers to governance voting mechanisms used by protocols across North America and Europe.
The automatic getter generation for public state variables provides convenient read access without requiring explicit function definitions. When you declare a variable as public, Solidity automatically creates a getter function with the same name. This feature simplifies contract interfaces while maintaining transparency about stored data.
However, public visibility should be used deliberately rather than as a default. Every public function represents a potential entry point for interaction, and each entry point must be secured appropriately. Security-conscious teams evaluate whether each function truly requires public access or if a more restrictive visibility would suffice.[1]
Internal Functions for Modular and Maintainable Smart Contracts
Internal functions enable sophisticated code organization through inheritance while maintaining security boundaries. When a function is marked internal, it becomes accessible to the defining contract and any contract that inherits from it. This visibility level supports modular architecture patterns where base contracts provide reusable functionality to specialized implementations.
Function visibility in smart contracts benefits significantly from internal functions when building library-like base contracts. A token contract might define internal helper functions for balance updates that child contracts can use while preventing external actors from calling these sensitive operations directly. This pattern appears throughout major DeFi protocols operating in regulated markets across the UK, UAE, and North America.
The internal keyword also applies to state variables, controlling read access similarly to functions. Internal state variables are readable by derived contracts but not externally. This granularity enables precise control over what information child contracts can access while maintaining encapsulation from external queries.
Private Functions and Their Importance in Access Control
Private functions provide the strictest encapsulation available in Solidity. A private function can only be called from within the exact contract where it is defined. Unlike internal functions, private functions are not accessible to derived contracts, making them ideal for implementation details that should never be exposed or overridden.
This strict isolation makes private functions valuable for sensitive helper logic. Cryptographic operations, internal accounting adjustments, and other critical computations often belong in private functions. By restricting access completely, developers ensure that future contract modifications or inheritance cannot accidentally expose or alter these protected operations.
Private visibility also signals intent to other developers and auditors. When reviewing code, private functions clearly indicate implementation details not meant for external or inherited use. This clarity improves code comprehension and helps auditors focus their attention on the public and external interfaces where vulnerabilities are most likely to be exploitable.
Function Visibility and Smart Contract Security Best Practices
Security best practices for function visibility in smart contracts follow the principle of least privilege. Every function should use the most restrictive visibility that still allows it to fulfill its purpose. This approach minimizes attack surface and reduces the potential impact of vulnerabilities.
| Practice | Implementation | Security Impact |
|---|---|---|
| Default to Private | Start with private, relax as needed | High Protection |
| Explicit Declaration | Always specify visibility keyword | Prevents Defaults |
| Separate Concerns | Group by visibility level | Easier Auditing |
| Document Intent | Comment why each visibility chosen | Maintains Intent |
| Regular Review | Audit visibility during updates | Ongoing Safety |
Preventing Unauthorized Access Through Proper Visibility Design
Unauthorized access prevention starts with thoughtful visibility architecture during the design phase. Function visibility in smart contracts works alongside other access control mechanisms like modifiers and role-based permissions to create layered security. Visibility represents the first line of defense, determining which functions are even callable before additional checks apply.
Common attack vectors exploit visibility misconfigurations to bypass intended access controls. An administrative function accidentally marked public allows any address to execute privileged operations. A state-changing function meant for internal use only but marked external enables manipulation by malicious contracts. These vulnerabilities have resulted in significant losses for protocols operating across global markets.
Defense in depth combines visibility restrictions with explicit require statements and modifier checks. Even if a function must be public, additional validation ensures only authorized callers can successfully execute sensitive logic. This layered approach protects against both visibility misconfiguration and logic errors in access control code.
How Function Visibility Impacts Smart Contract Scalability
Scalable smart contract architecture requires careful visibility planning that anticipates future growth and integration needs. Function visibility in smart contracts directly affects how systems can be extended, upgraded, and composed with other protocols. Decisions made early in design phases have lasting implications for protocol evolution.
External functions create clean integration interfaces that other protocols can reliably depend upon. Well-defined external surfaces enable composability, allowing your contract to participate in the broader DeFi ecosystem. Protocols in London, Dubai, and Toronto leverage this composability to build sophisticated financial products from interoperable components.
Internal and private functions support scalability through modular code organization. As contracts grow in complexity, private helper functions isolate implementation details while internal functions enable code sharing across inheritance hierarchies. This separation of concerns makes large codebases manageable and facilitates parallel work across distributed teams.
Gas Efficiency Considerations Linked to Function Visibility
Gas optimization through visibility selection can significantly reduce transaction costs for high-frequency operations. Understanding how different visibility levels affect gas consumption enables informed architectural decisions that balance security with efficiency.
| Visibility | Gas Behavior | Best Use Case |
|---|---|---|
| External | Reads calldata directly, most efficient for arrays | Functions receiving large data inputs |
| Public | Copies to memory, higher gas for complex types | Functions needing internal and external access |
| Internal | Jump instruction, no external call overhead | Shared logic across inheritance |
| Private | Jump instruction, may enable inlining | Implementation helpers, sensitive logic |
Function Visibility in Upgradeable and Proxy-Based Smart Contracts
1. Proxy Interface Design
Define external functions that proxy will delegate. These form the public API across all implementation versions.
2. Implementation Visibility
Mark implementation functions external to match proxy expectations. Internal helpers remain protected.
3. Initializer Protection
Use internal initializers with external wrappers. Prevents reinitialization attacks on implementation contracts.
4. Upgrade Function Security
Keep upgrade functions internal with external admin-protected wrappers. Never expose upgrade logic publicly.
5. Storage Compatibility
Maintain consistent internal function signatures across versions to ensure storage slot alignment.
6. Version Testing
Test visibility behavior across implementation versions. Verify proxy correctly delegates to new functions.
7. Security Audit
Audit visibility configurations specifically for proxy patterns. Review delegatecall implications thoroughly.
8. Deployment Validation
Verify all visibility settings match design specifications before mainnet deployment across production environments.
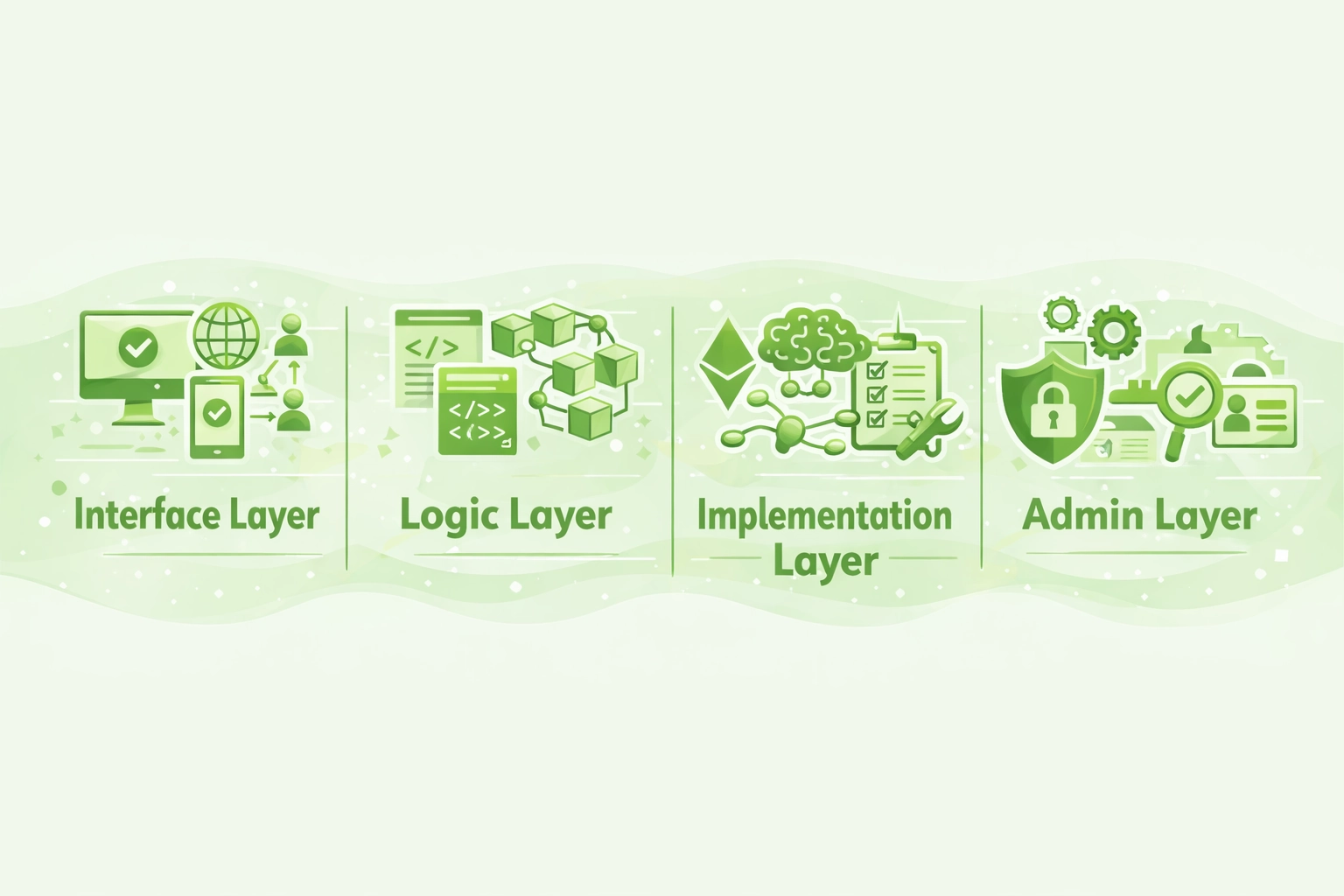
Designing Scalable Function Visibility in Smart Contracts Systems Using Visibility Patterns
Select the appropriate visibility pattern based on your system architecture requirements and scalability goals.
Interface Layer
Design external functions as stable public APIs. These form integration points other protocols depend upon.
Logic Layer
Use internal functions for business logic shared across contract hierarchies and modules.
Implementation Layer
Keep implementation helpers private. These details should never leak to derived contracts or external callers.
Admin Layer
Protect administrative functions with restricted visibility plus additional modifier-based access controls.
Future-Proof Function Visibility in Smart Contracts Architecture with Proper Function Visibility
Follow these industry standards to ensure your visibility architecture remains robust as protocols evolve.
Standard 1: Always explicitly declare visibility for every function, never rely on compiler defaults.
Standard 2: Start with the most restrictive visibility and relax only when requirements demand it.
Standard 3: Document the rationale for each visibility choice in code comments for future maintainers.
Standard 4: Group functions by visibility level in source code to simplify security review processes.
Standard 5: Use external over public for functions that will only be called from outside the contract.
Standard 6: Review visibility configurations during every upgrade cycle to prevent regression vulnerabilities.
Standard 7: Include visibility testing in automated CI/CD pipelines to catch misconfigurations early.
Standard 8: Require professional security audits that specifically verify visibility configurations before mainnet launch.
Function Visibility Compliance and Governance Checklist
Code Standards
- All functions have explicit visibility
- Visibility follows least privilege principle
- Comments explain visibility rationale
Security Review
- Admin functions properly restricted
- State modifiers protected appropriately
- No unintended public exposure
Testing Coverage
- Visibility behavior tested per function
- Access control scenarios validated
- Inheritance visibility verified
Documentation
- Public API documented completely
- Internal interface specs for devs
- Upgrade visibility guidelines noted
Build Secure Function Visibility in Smart Contracts with Expert Visibility Design!
Partner with our experienced team to implement proper function visibility patterns that protect your protocol and optimize gas efficiency.
Frequently Asked Questions
Function visibility in smart contracts defines who can call specific functions within the contract code. Solidity provides four visibility types: public, external, internal, and private. Each type controls access differently, determining whether functions are callable from outside the contract, only within it, or by derived contracts. Proper visibility selection is fundamental for security and gas optimization.
Public functions can be called both internally within the contract and externally by other contracts or transactions. External functions are only callable from outside the contract and cannot be invoked internally without using the this keyword. External functions consume less gas when receiving large data arrays because they read directly from calldata instead of copying to memory.
Private functions restrict access exclusively to the contract where they are defined, preventing derived Function Visibility in Smart Contracts from calling them. This provides the strictest encapsulation for sensitive logic and helper functions that should never be exposed. Using private visibility reduces attack surface area and makes security audits more straightforward by limiting potential entry points for malicious actors.
Yes, internal functions are accessible within the defining contract and all contracts that inherit from it. This visibility type enables code reuse across contract hierarchies while preventing external access. Internal functions are ideal for shared utility logic in modular contract systems where child Function Visibility in Smart Contracts need access to parent functionality without exposing it publicly.
Incorrect function visibility is among the most common Function Visibility in Smart Contracts vulnerabilities. Functions marked public when they should be private or internal can expose critical operations to unauthorized callers. Security auditors consistently find visibility misconfigurations that could lead to fund theft or Function Visibility in Smart Contracts manipulation. Following the principle of least privilege by defaulting to restrictive visibility significantly reduces attack vectors.
Reviewed & Edited By

Aman Vaths
Founder of Nadcab Labs
Aman Vaths is the Founder & CTO of Nadcab Labs, a global digital engineering company delivering enterprise-grade solutions across AI, Web3, Blockchain, Big Data, Cloud, Cybersecurity, and Modern Application Development. With deep technical leadership and product innovation experience, Aman has positioned Nadcab Labs as one of the most advanced engineering companies driving the next era of intelligent, secure, and scalable software systems. Under his leadership, Nadcab Labs has built 2,000+ global projects across sectors including fintech, banking, healthcare, real estate, logistics, gaming, manufacturing, and next-generation DePIN networks. Aman’s strength lies in architecting high-performance systems, end-to-end platform engineering, and designing enterprise solutions that operate at global scale.







